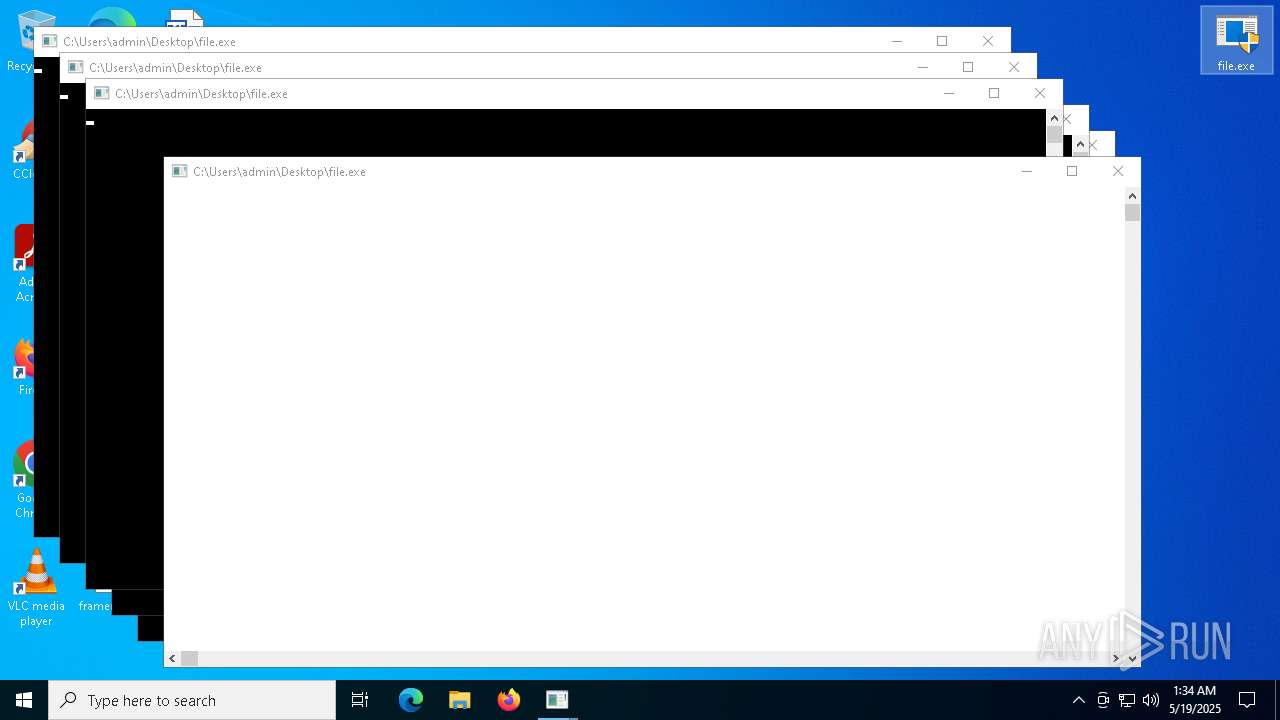
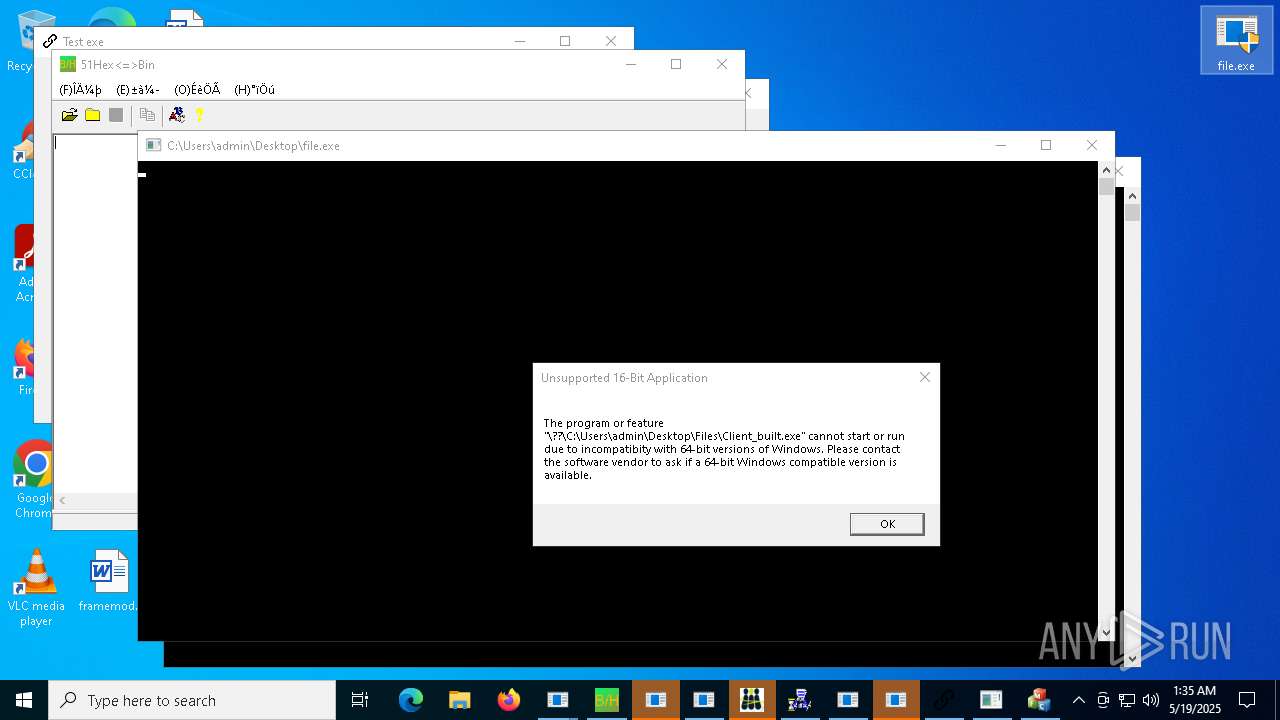
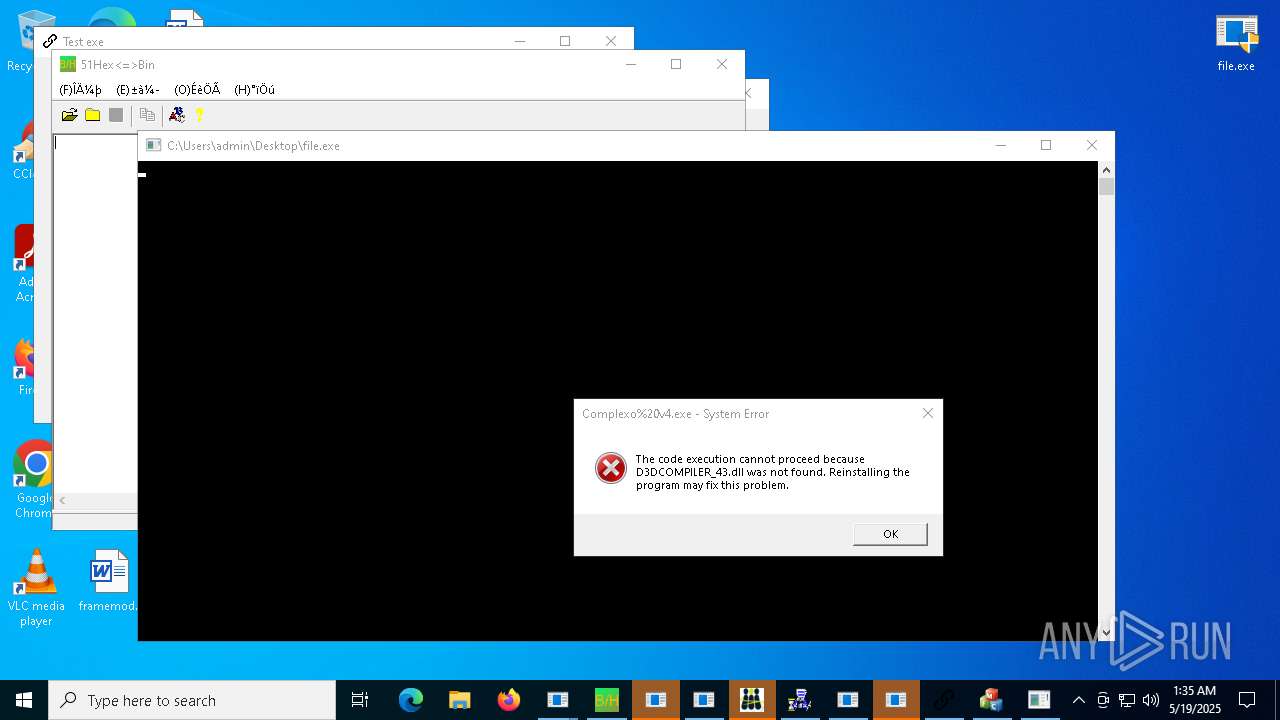
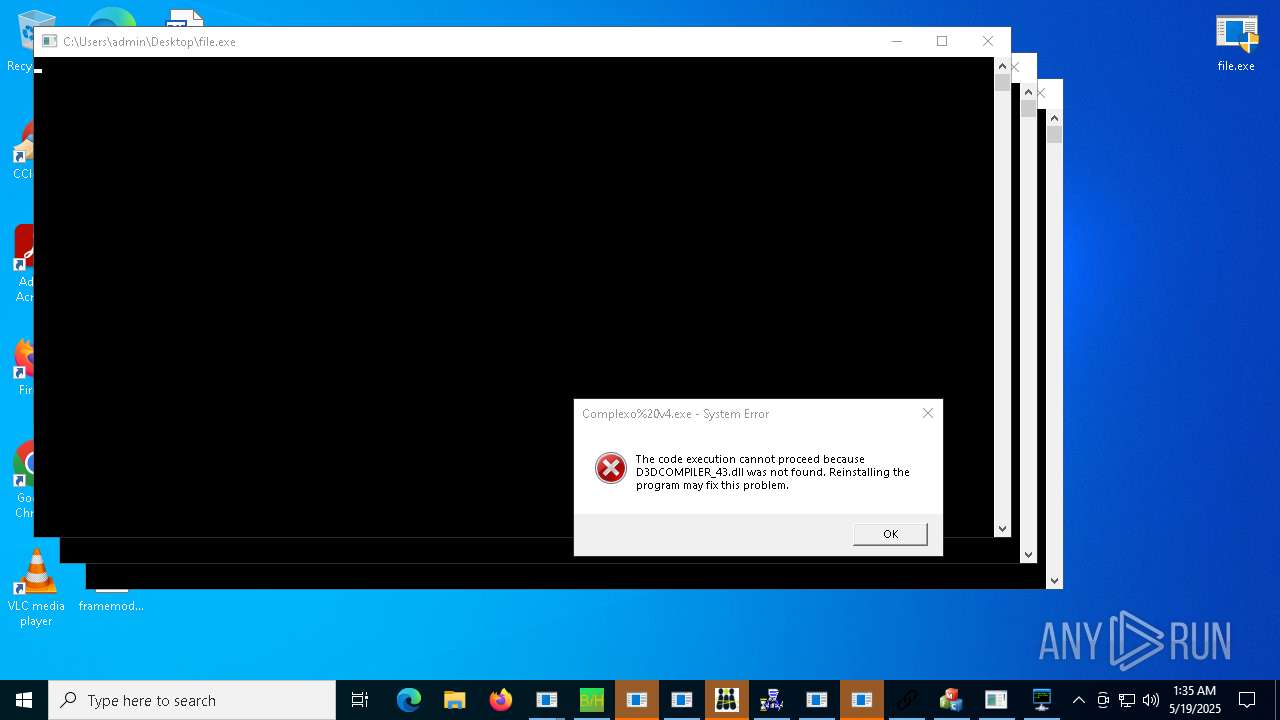
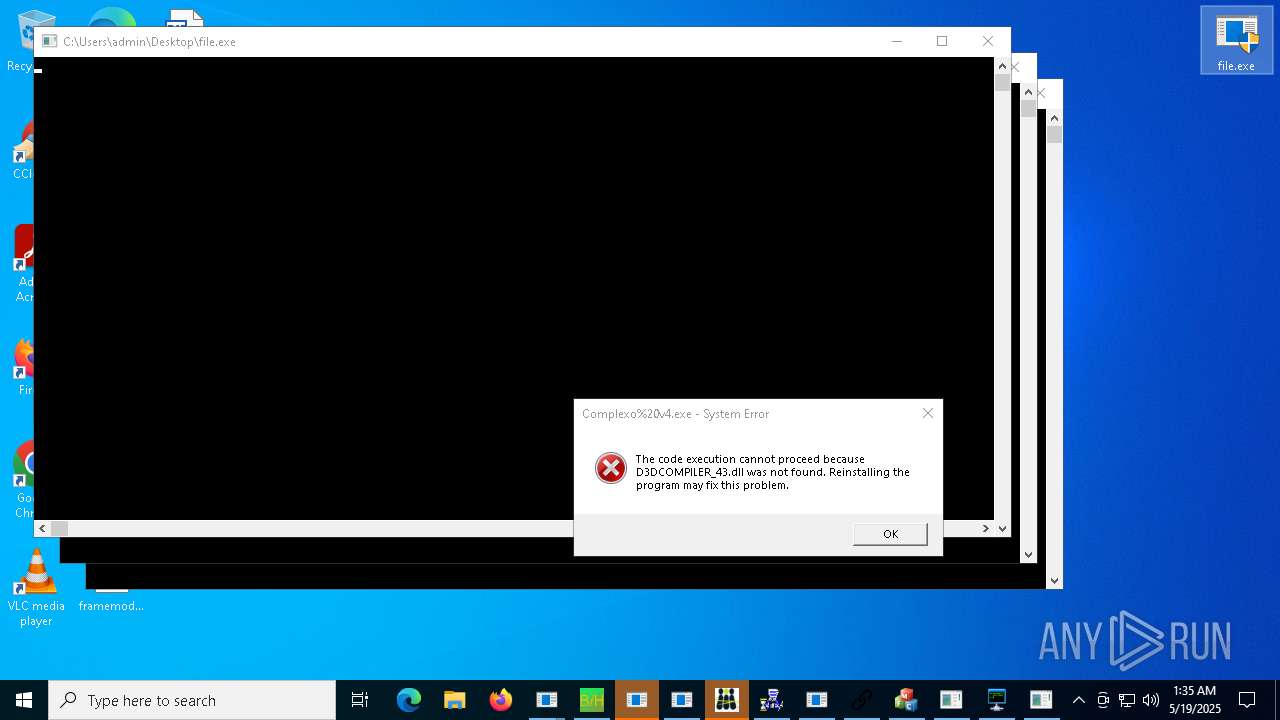
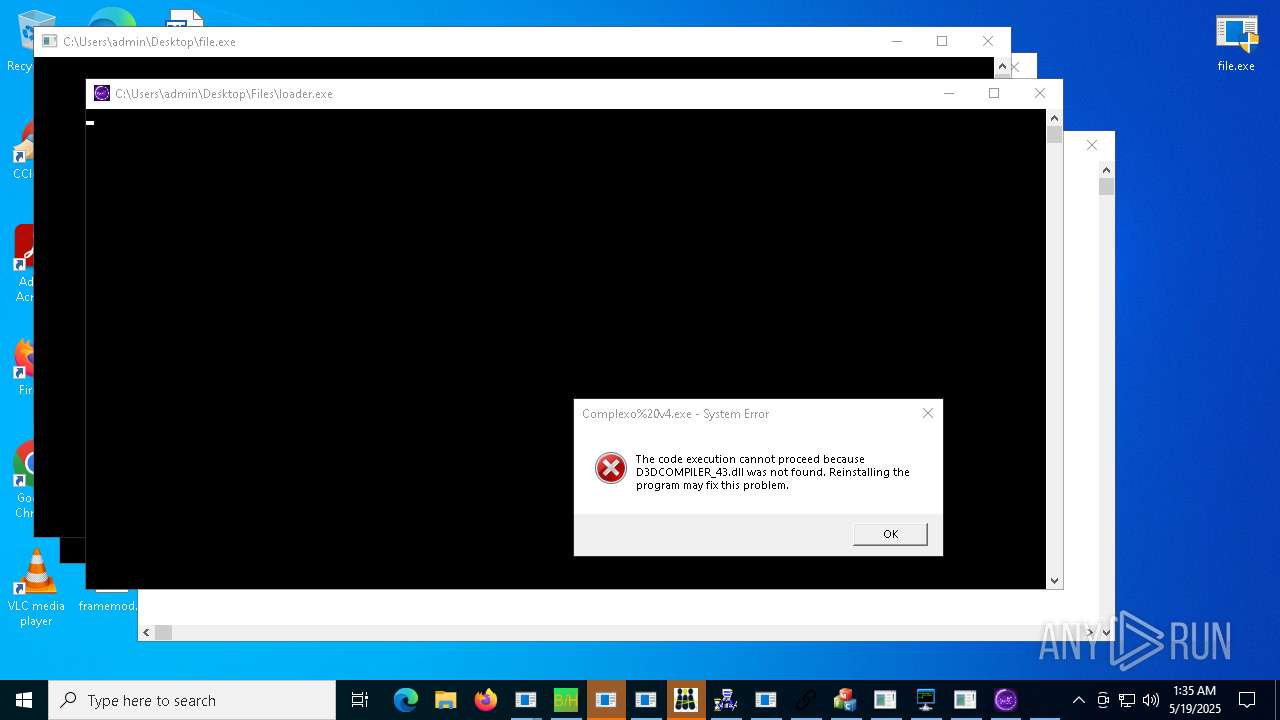
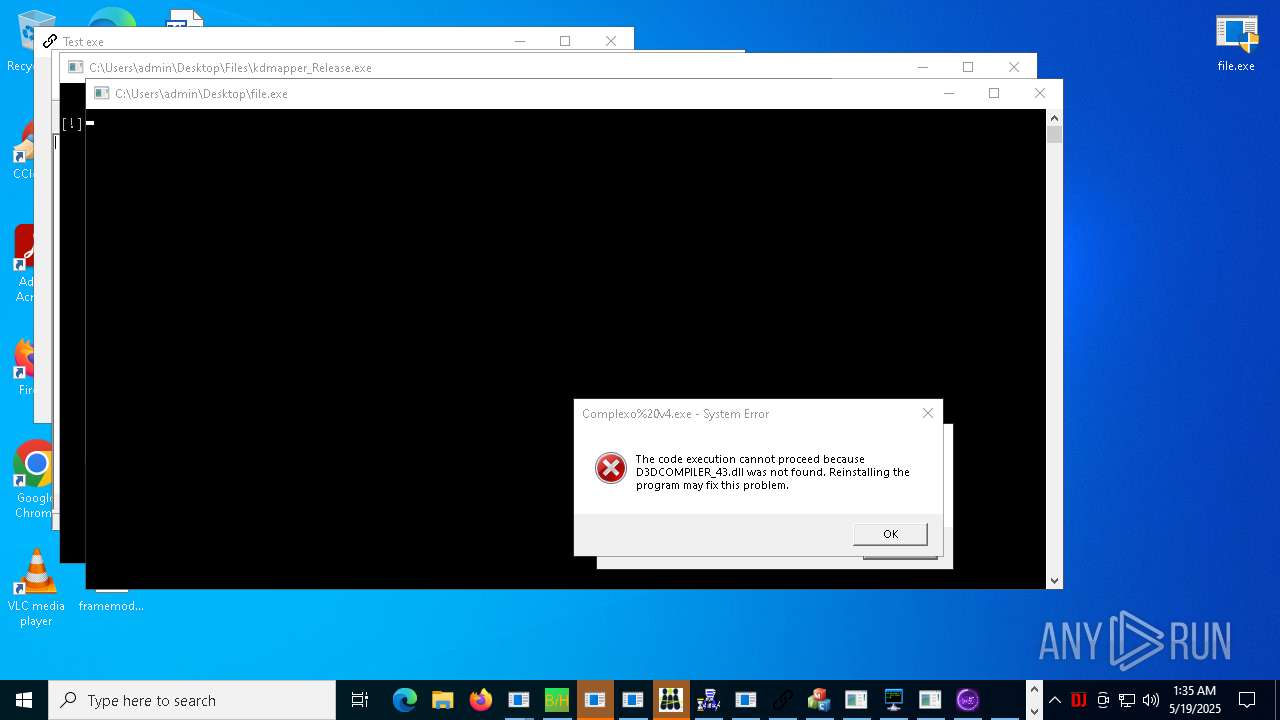
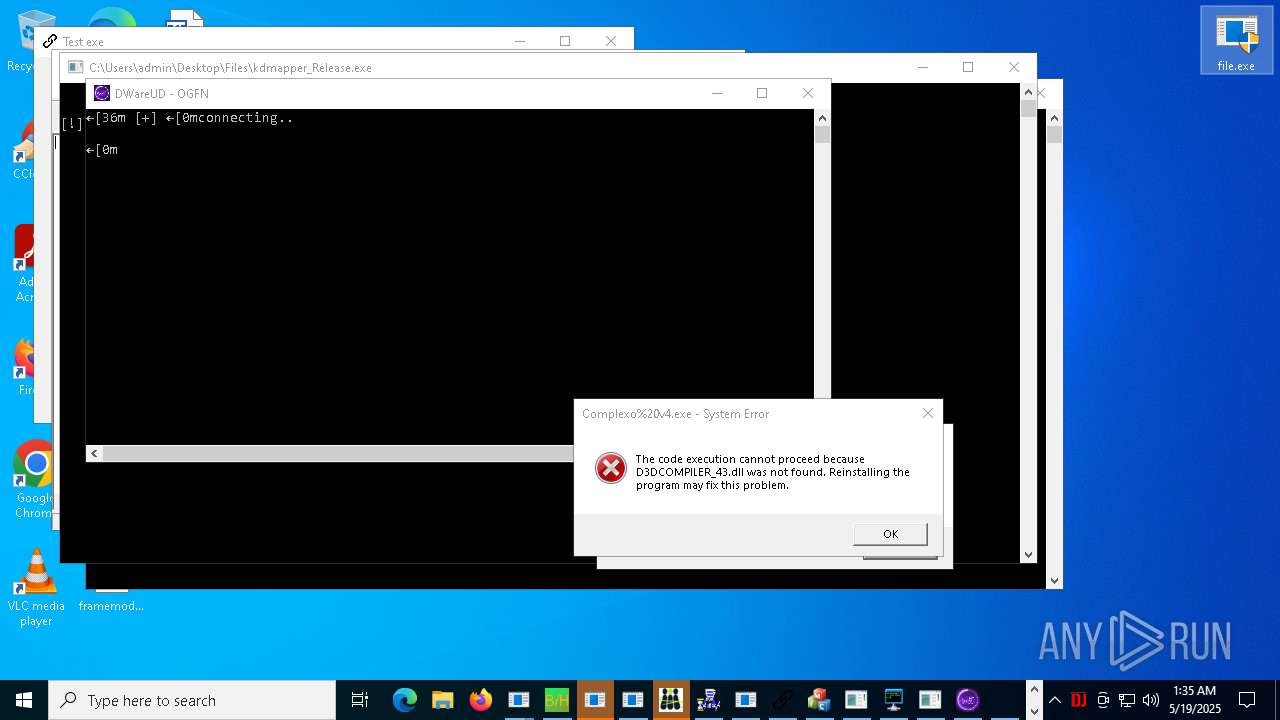
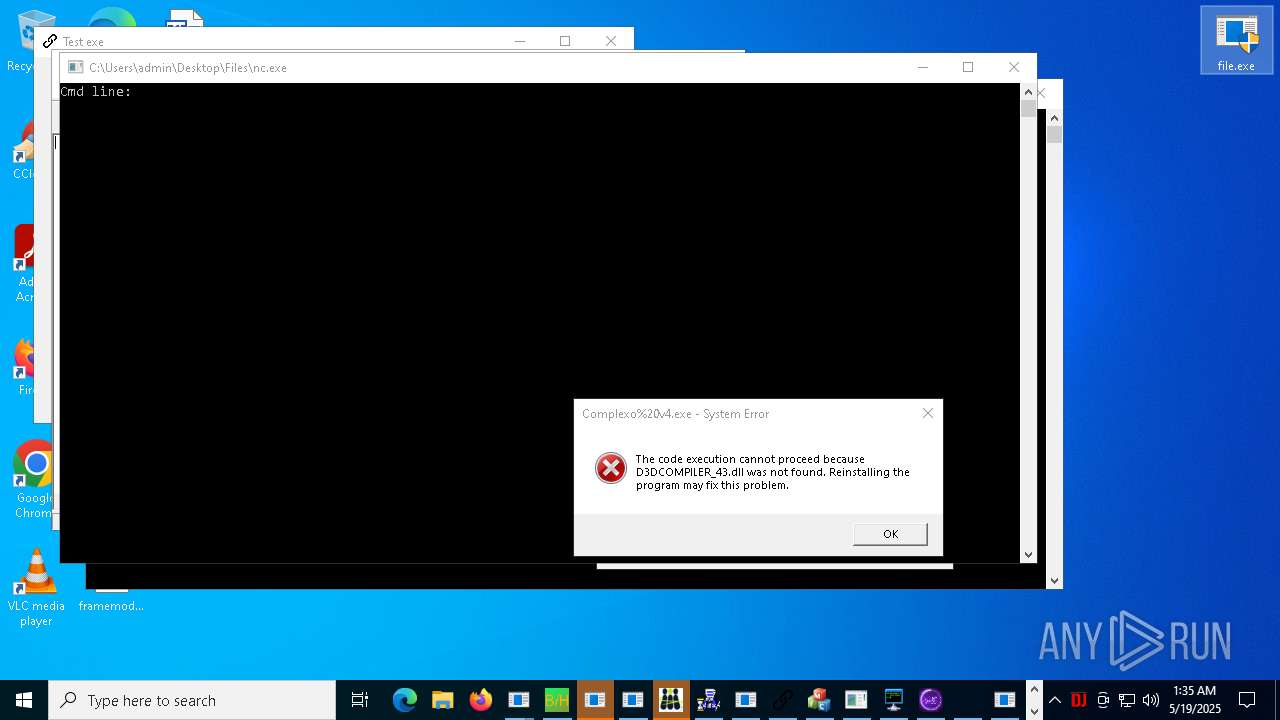
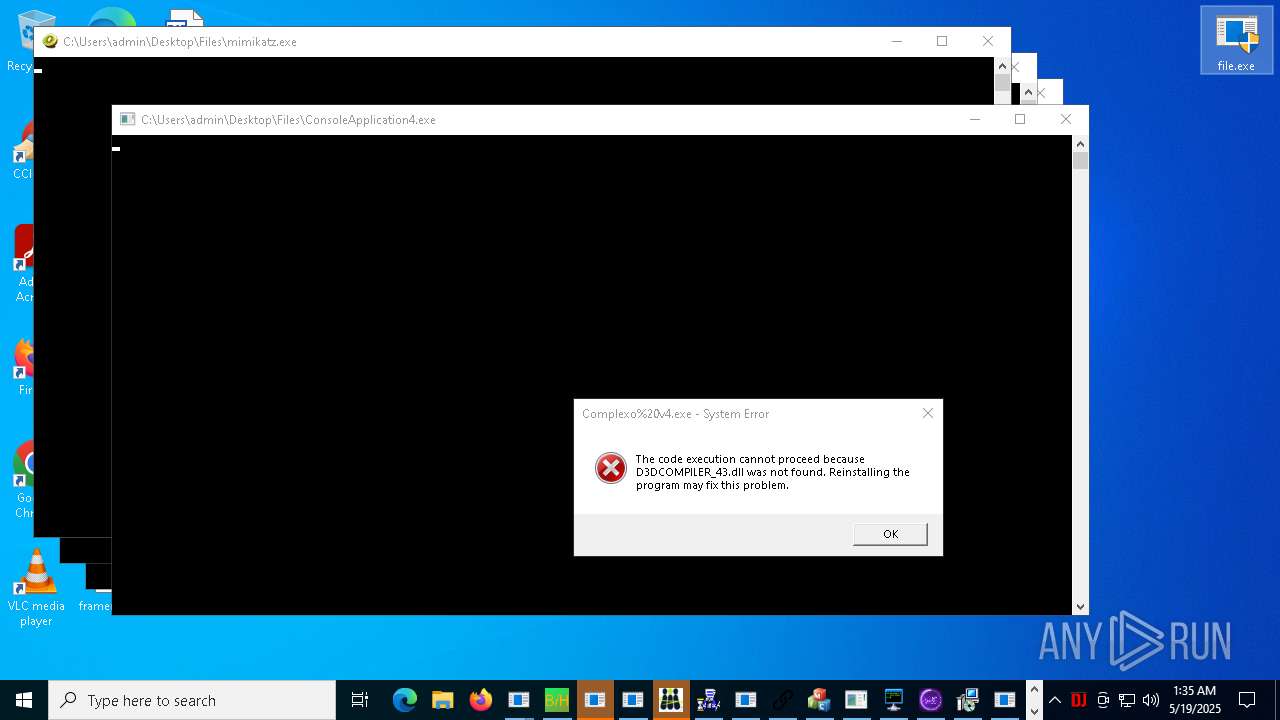
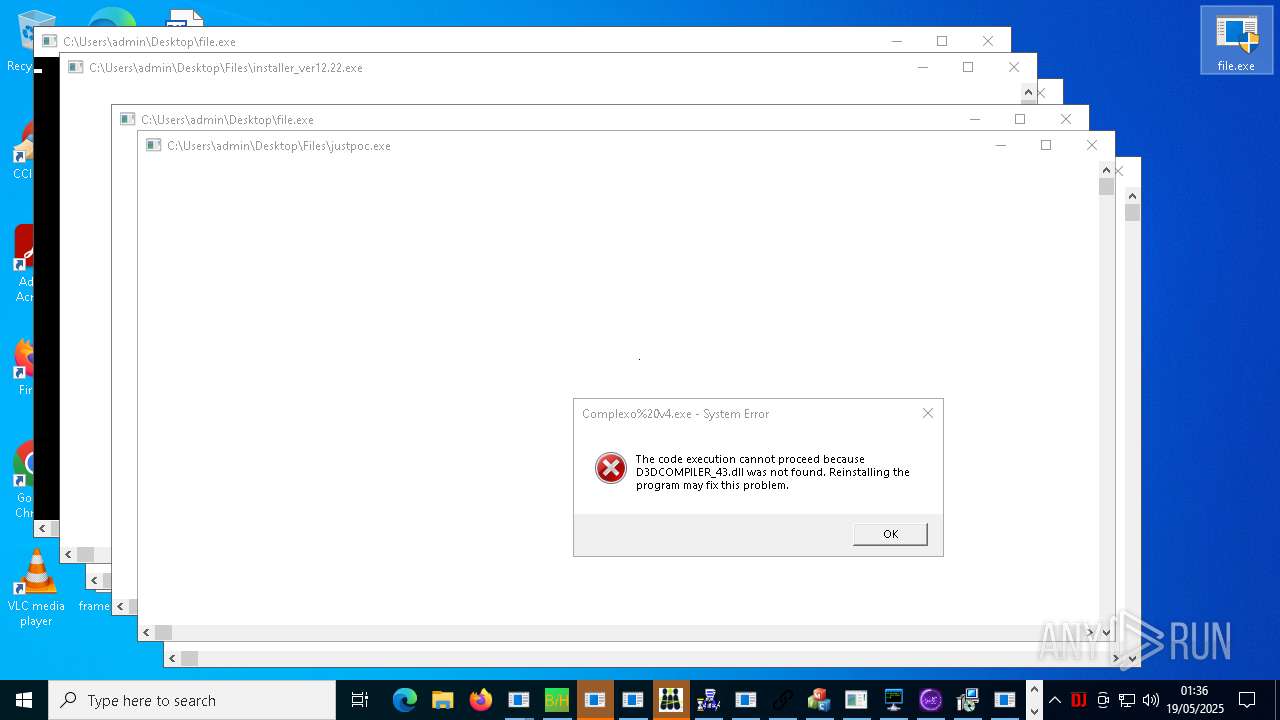
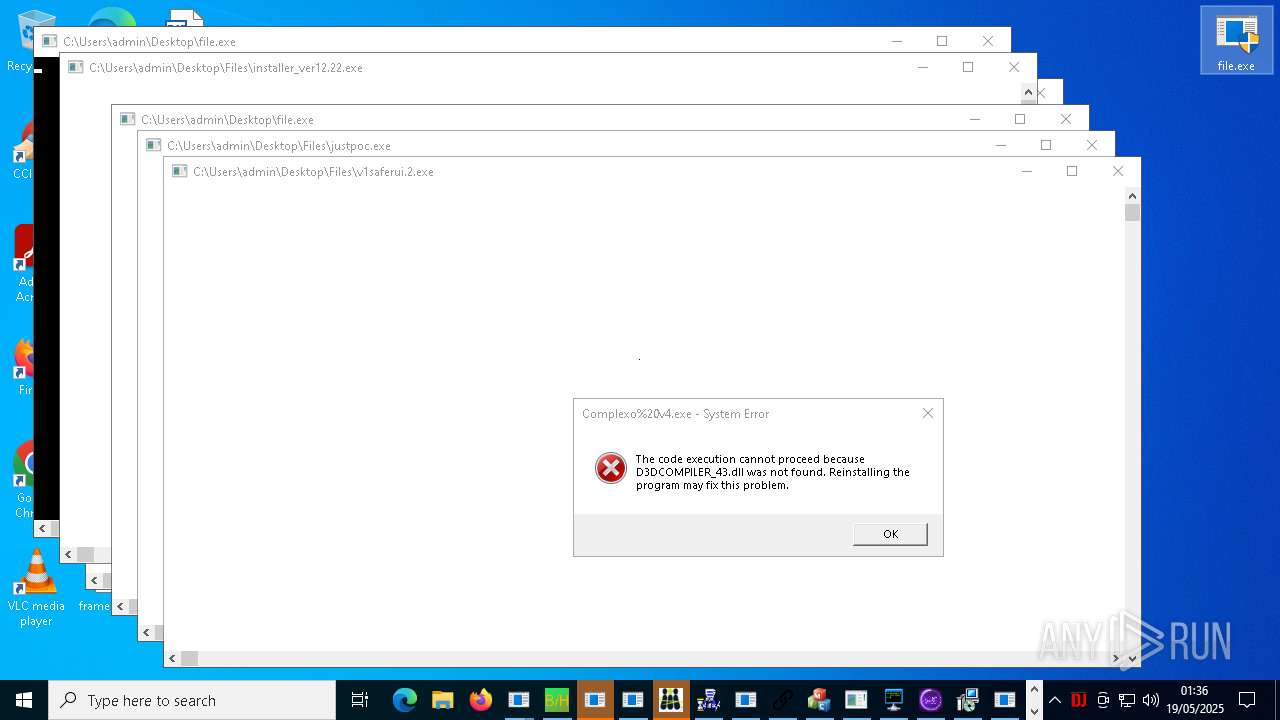
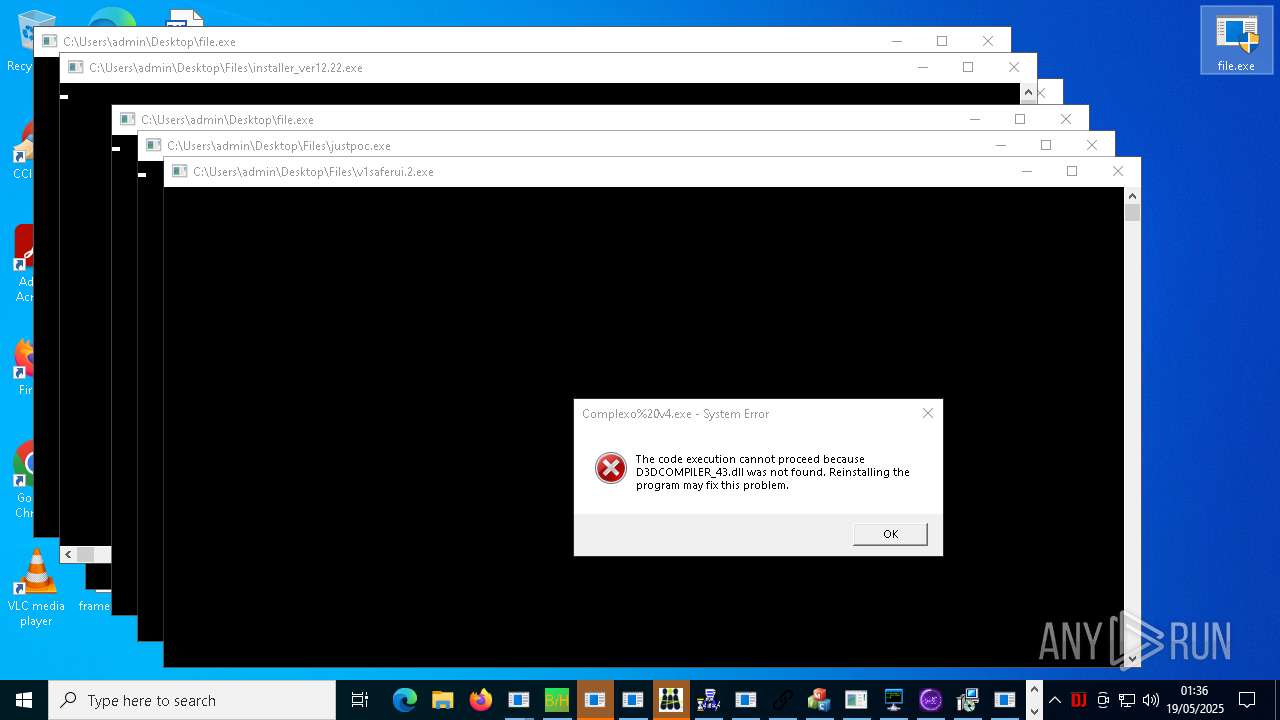
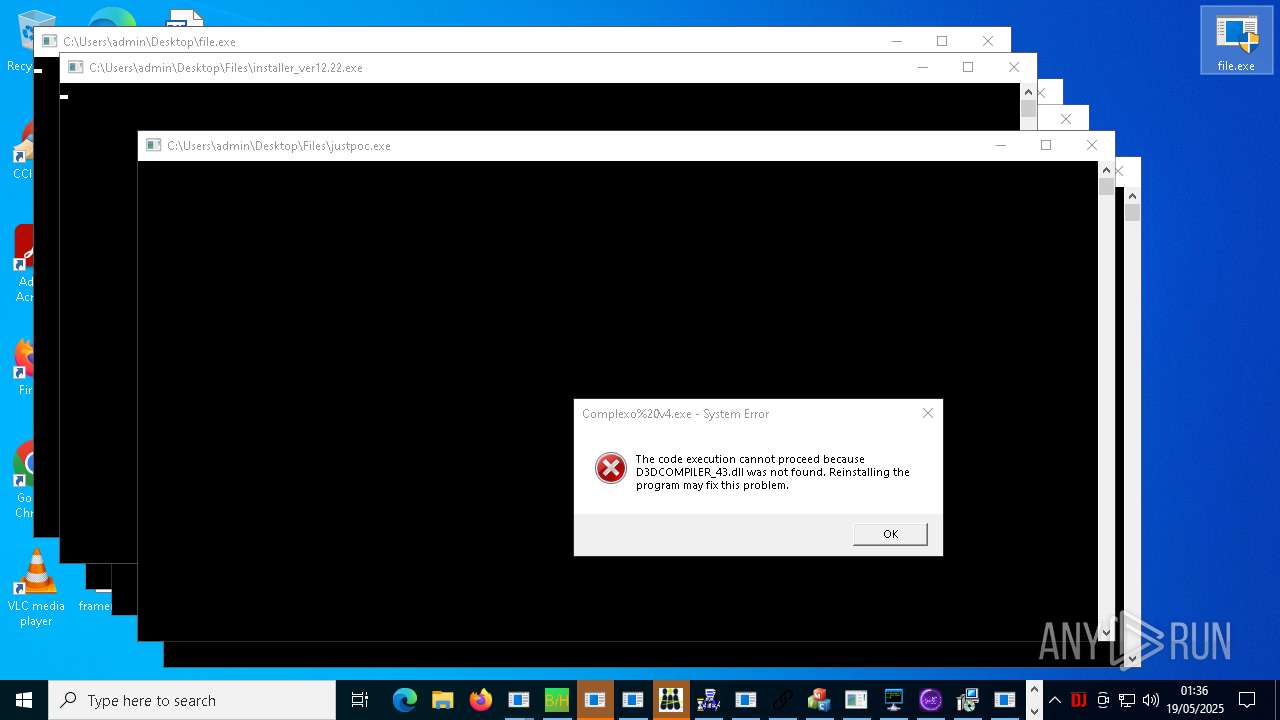
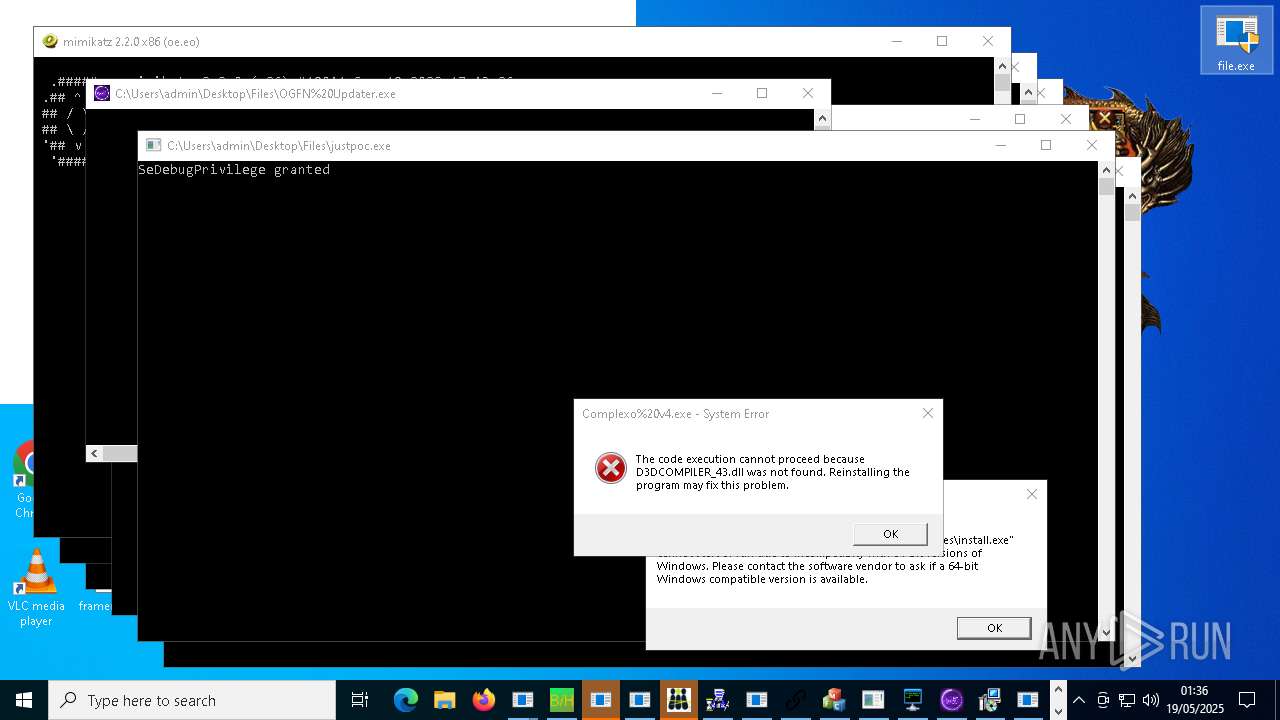
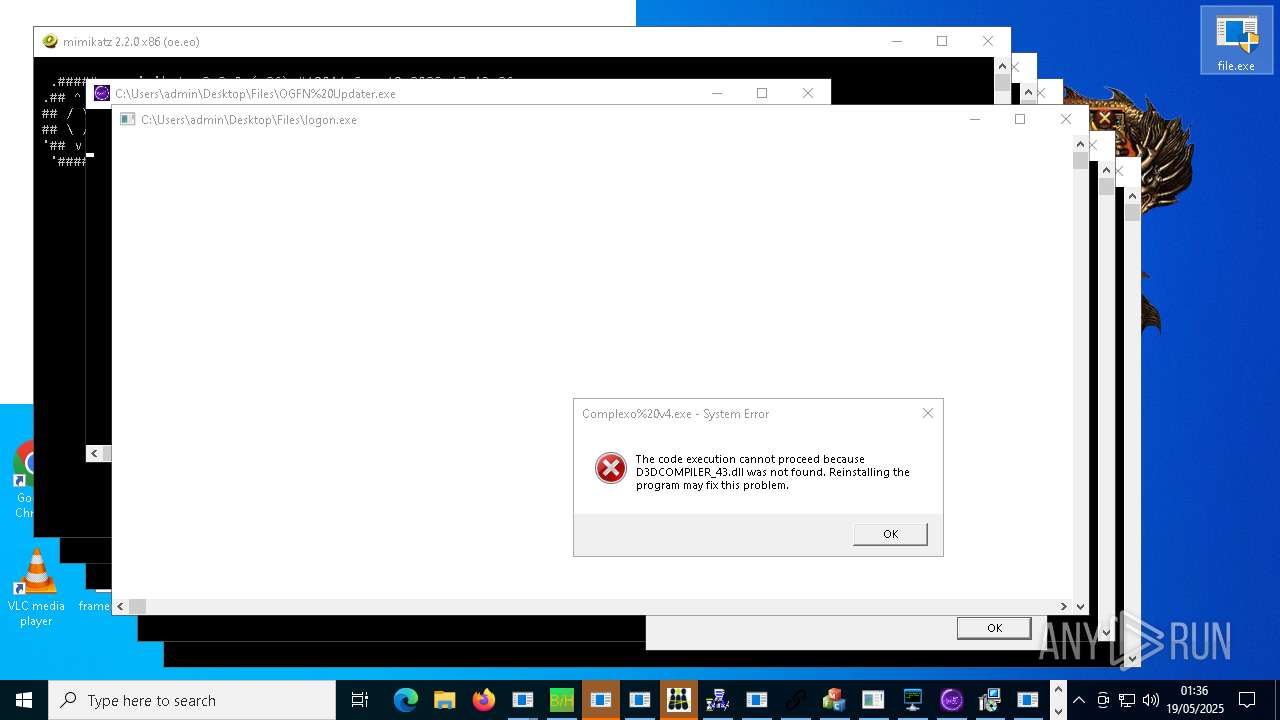
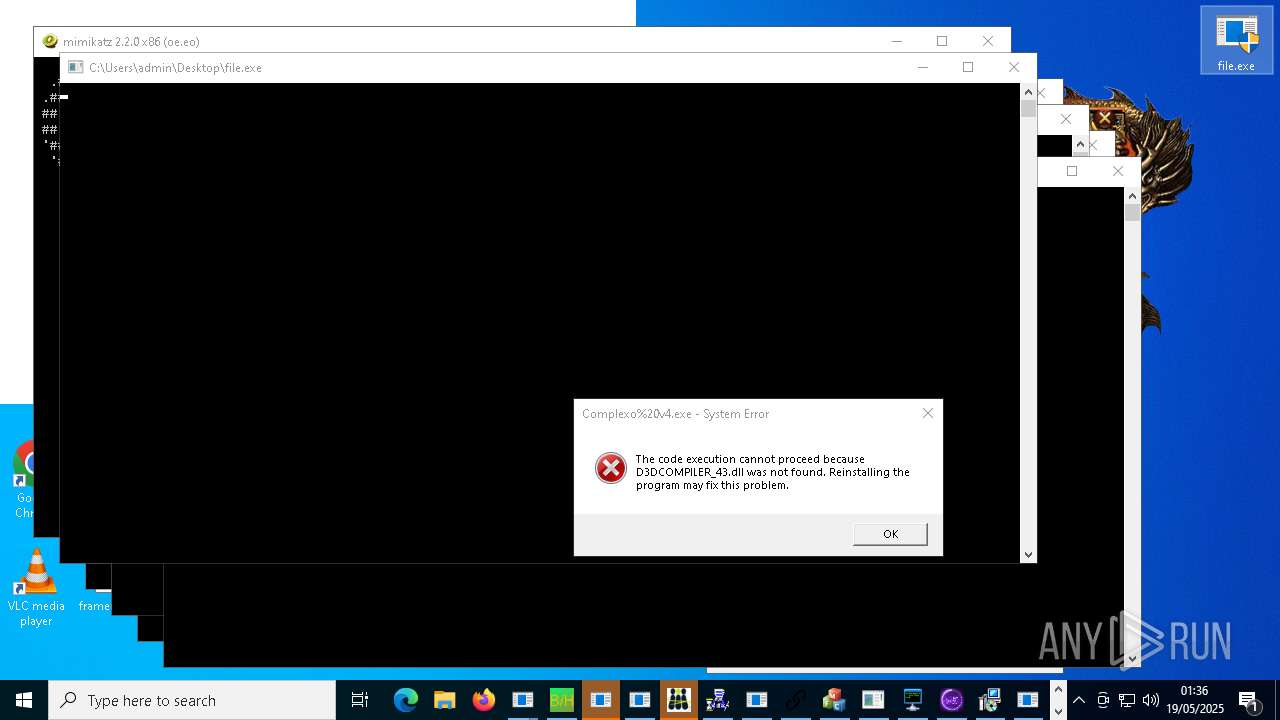
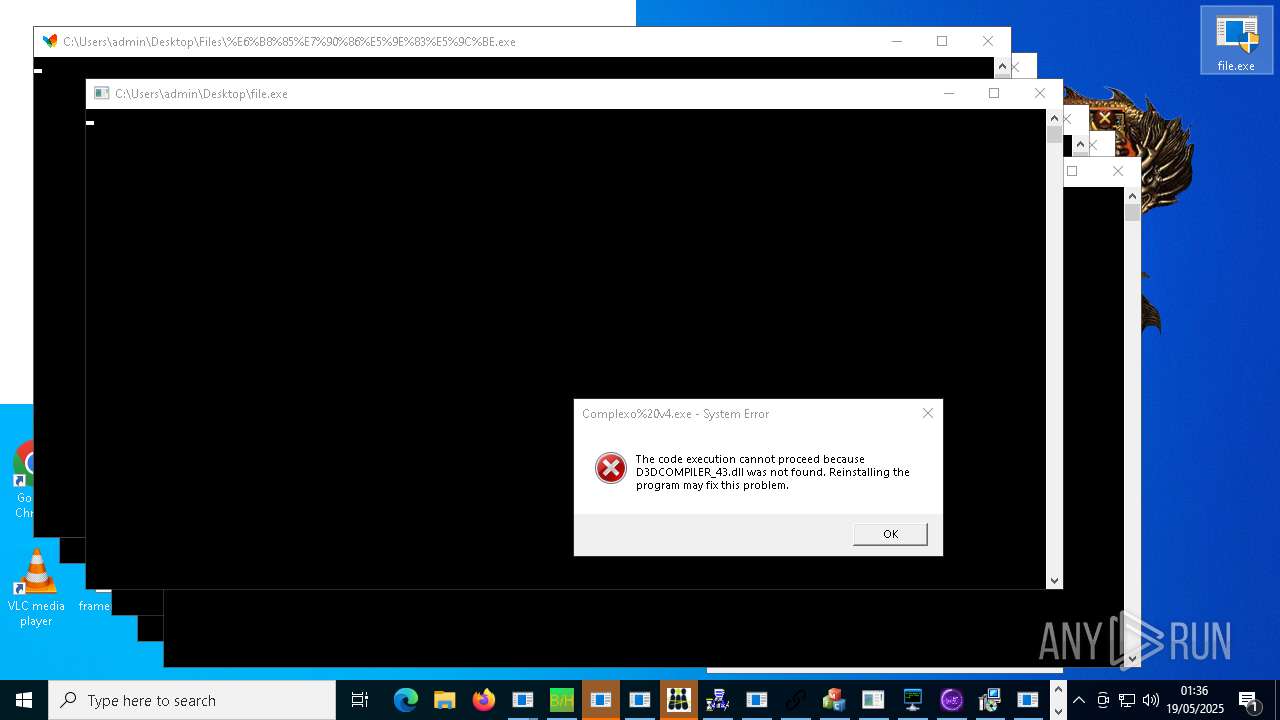
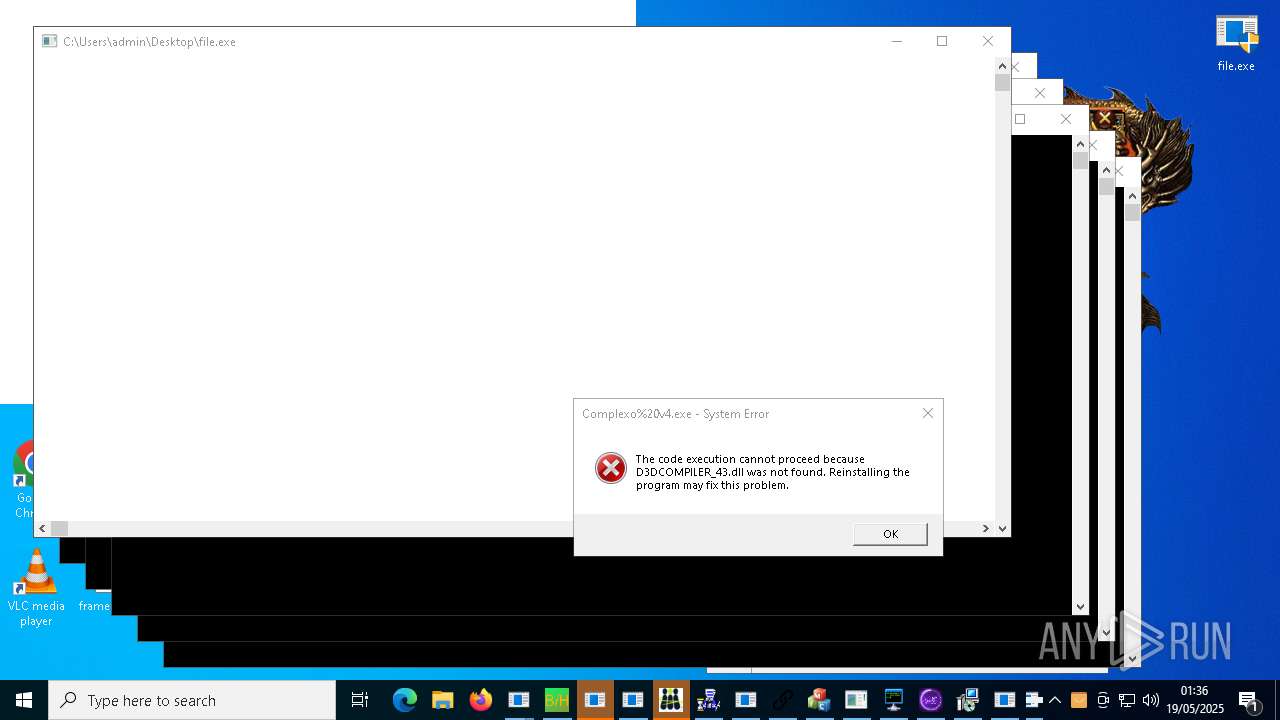
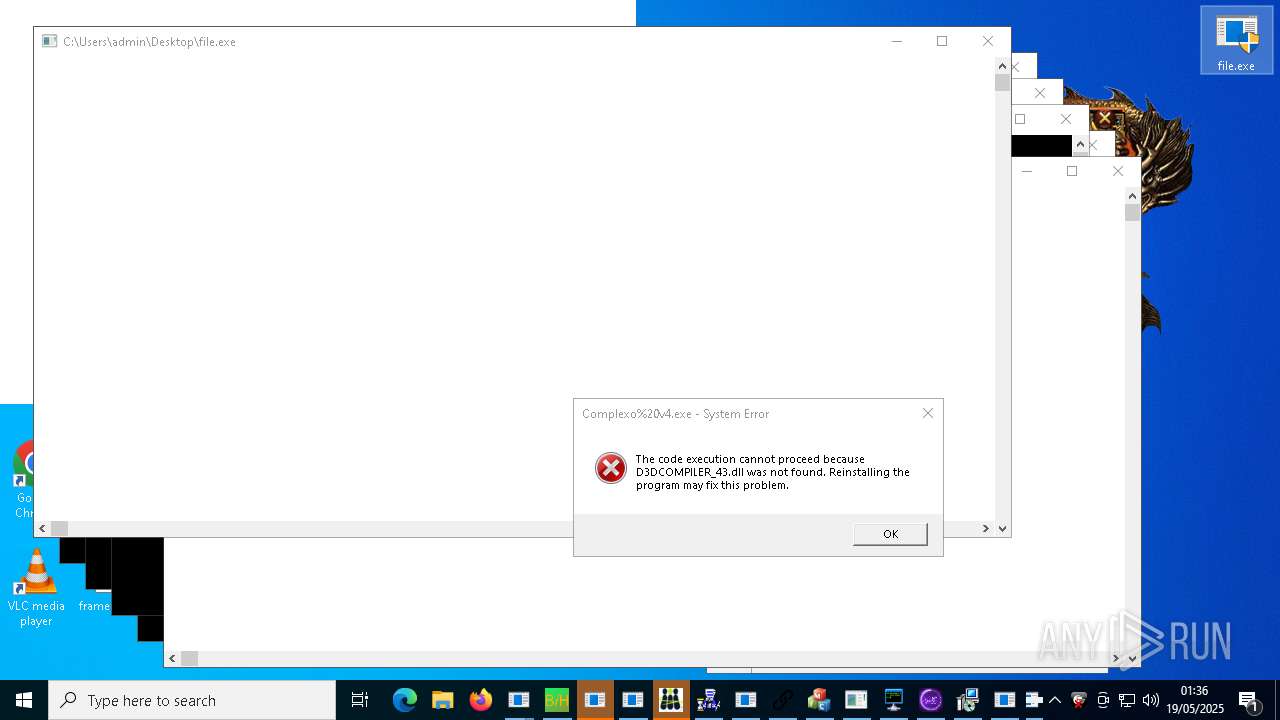
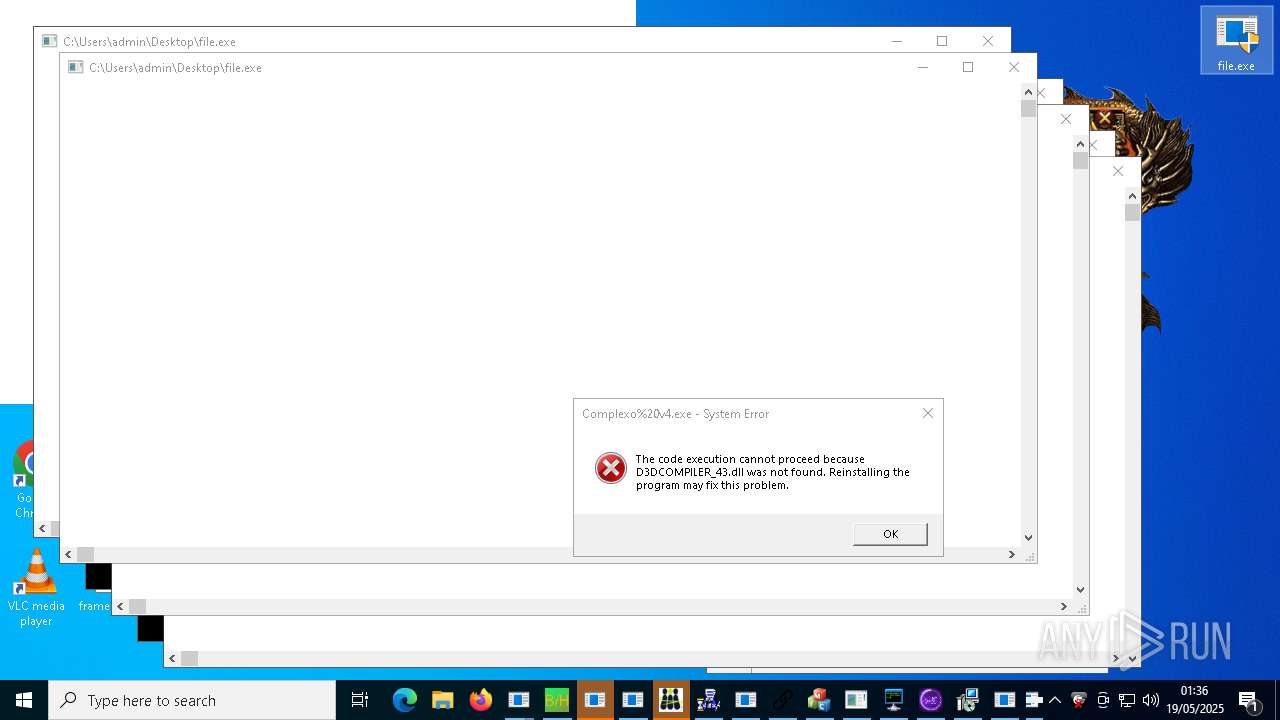
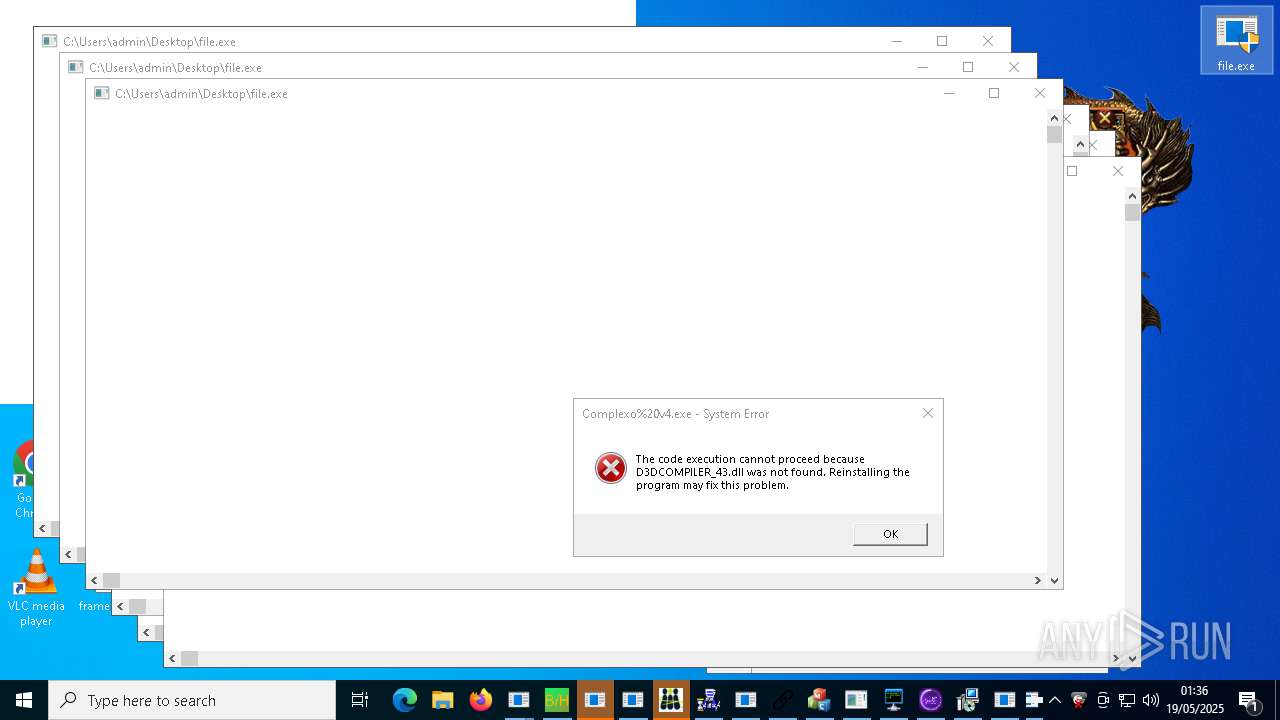
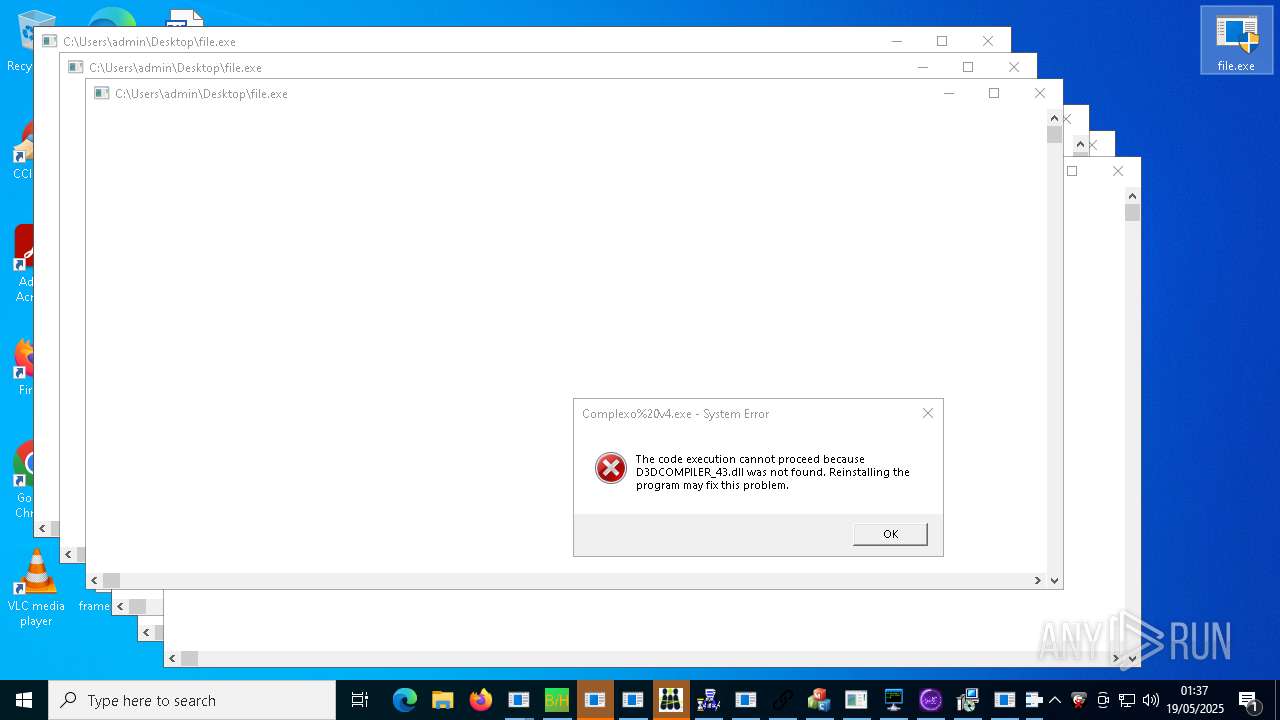
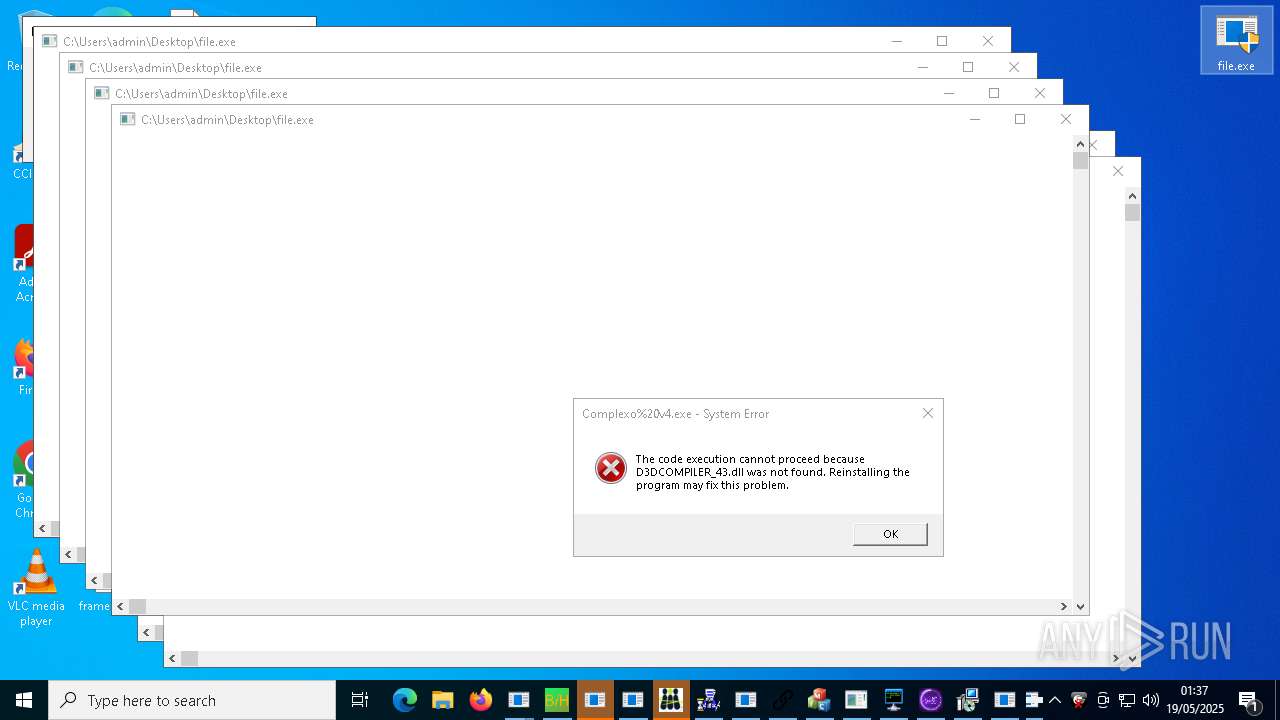
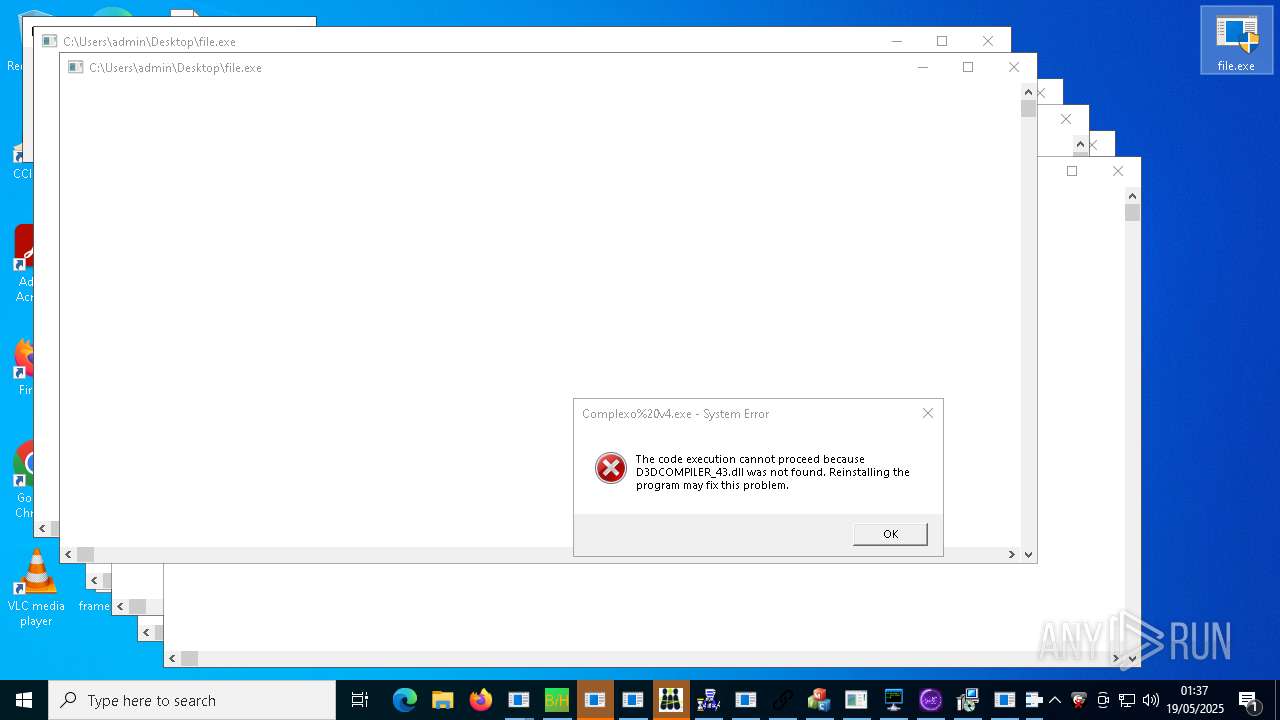
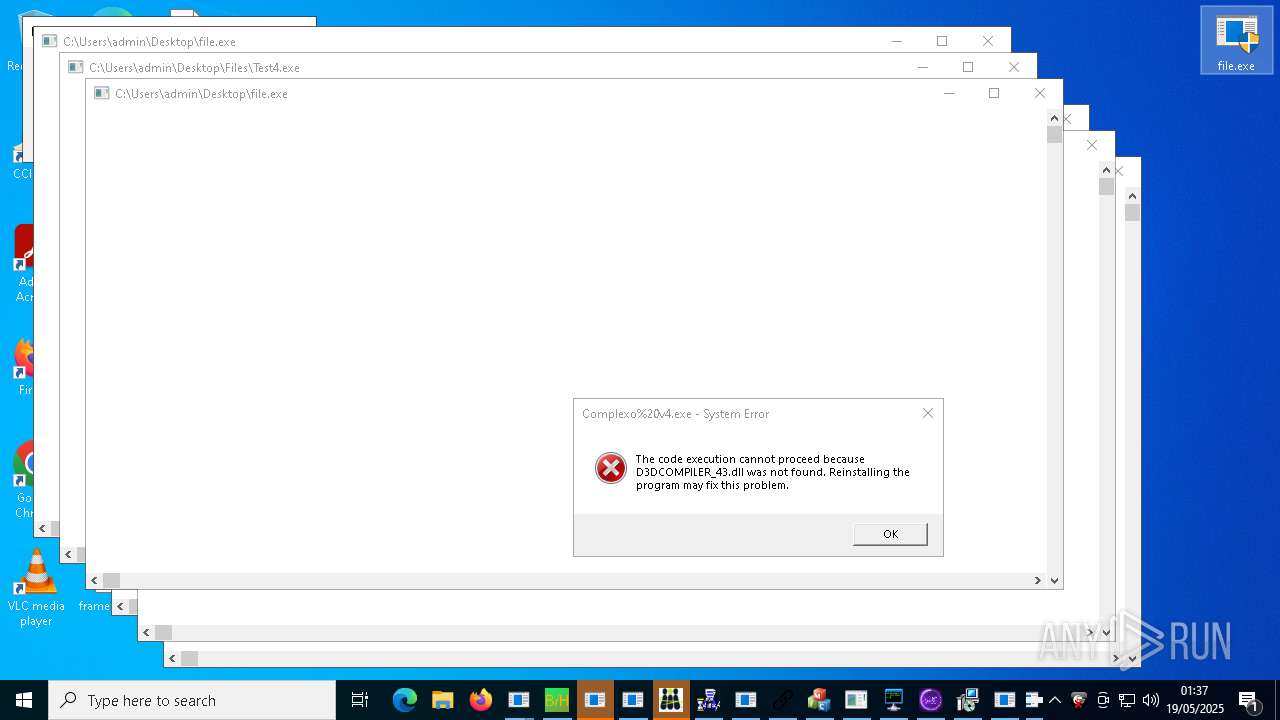
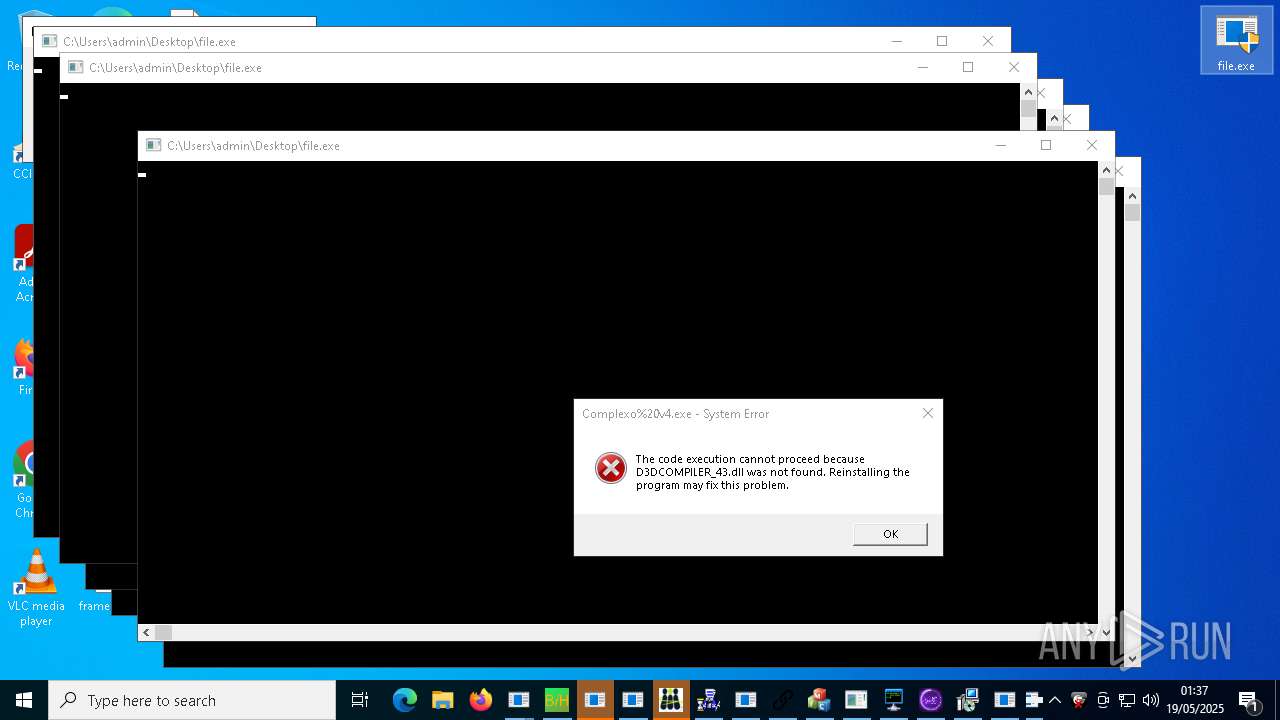
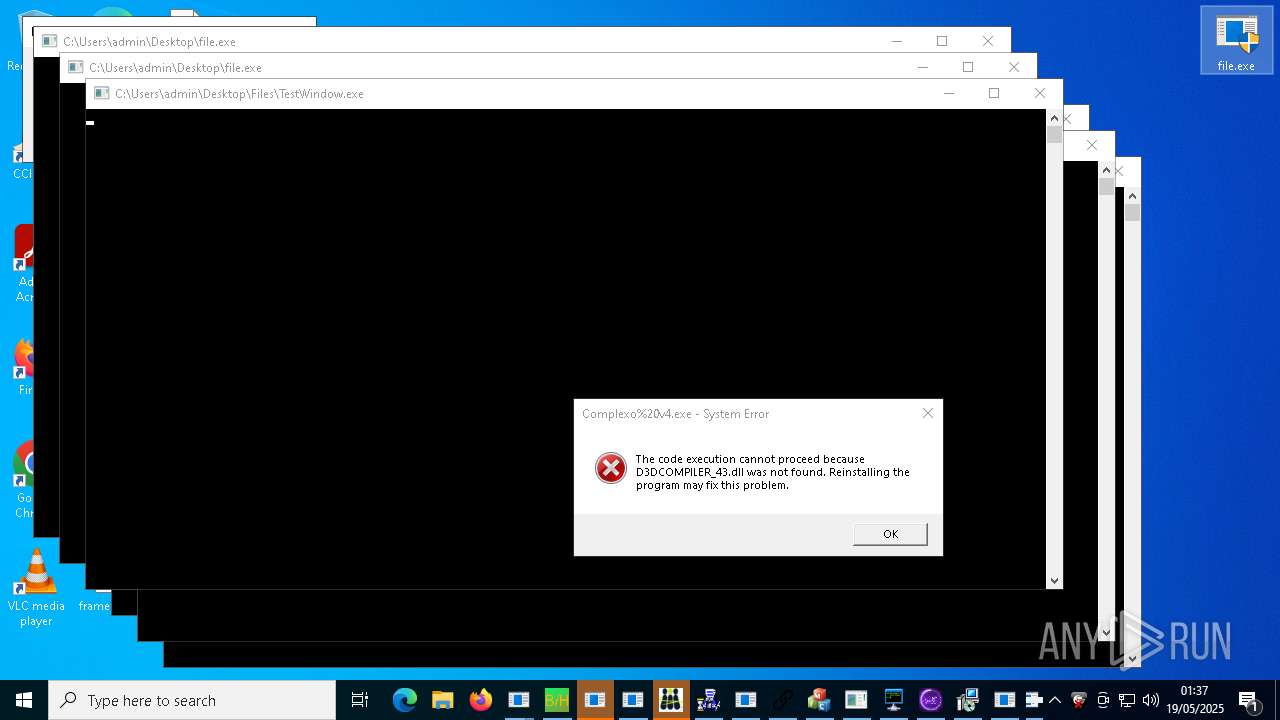
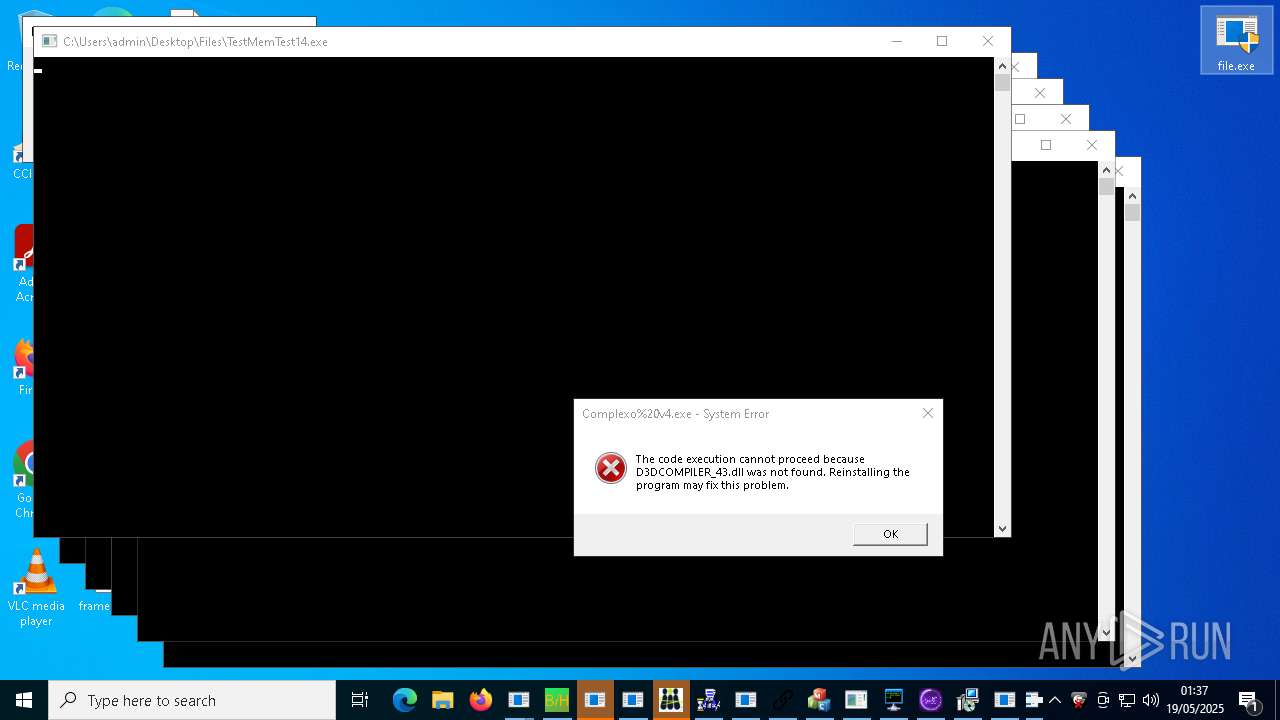
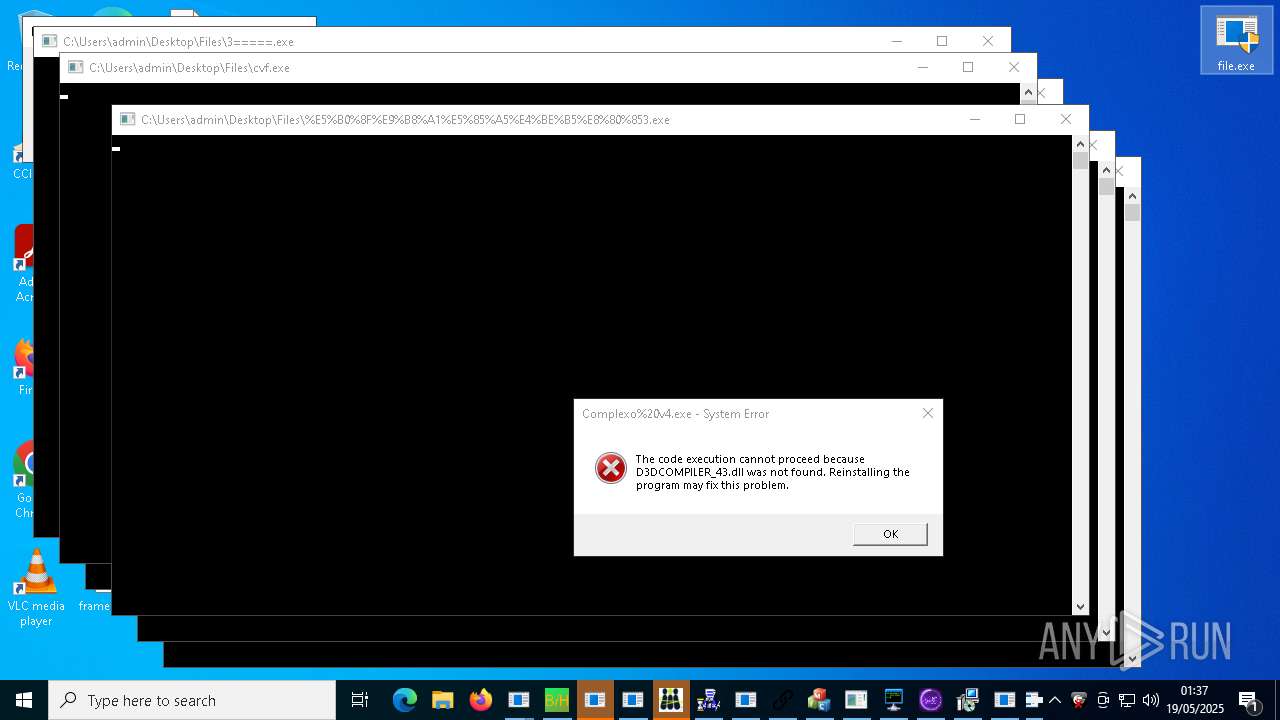
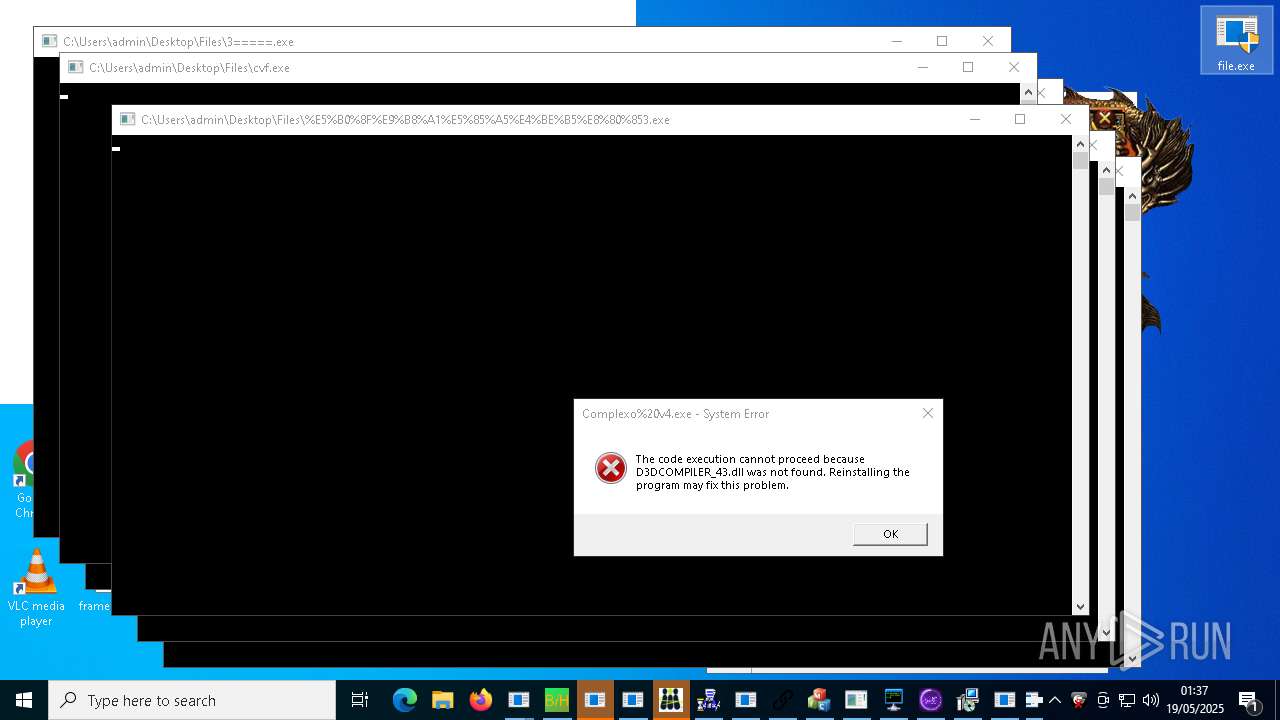
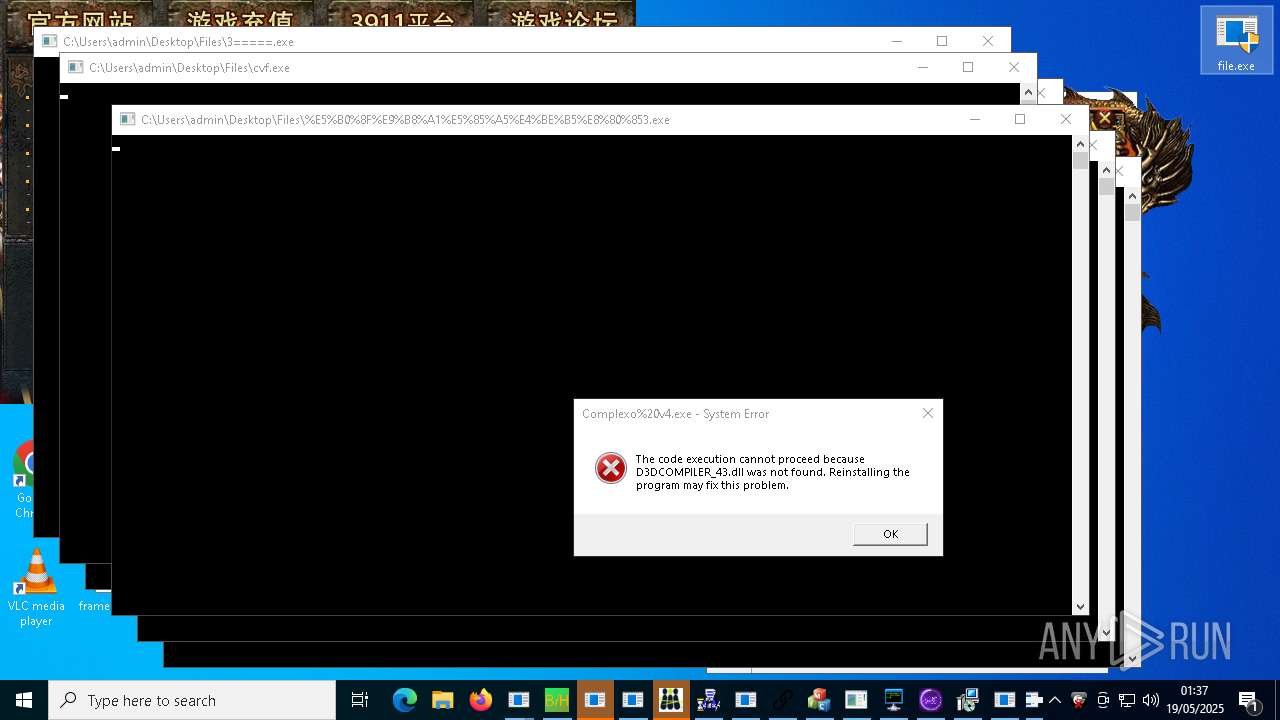
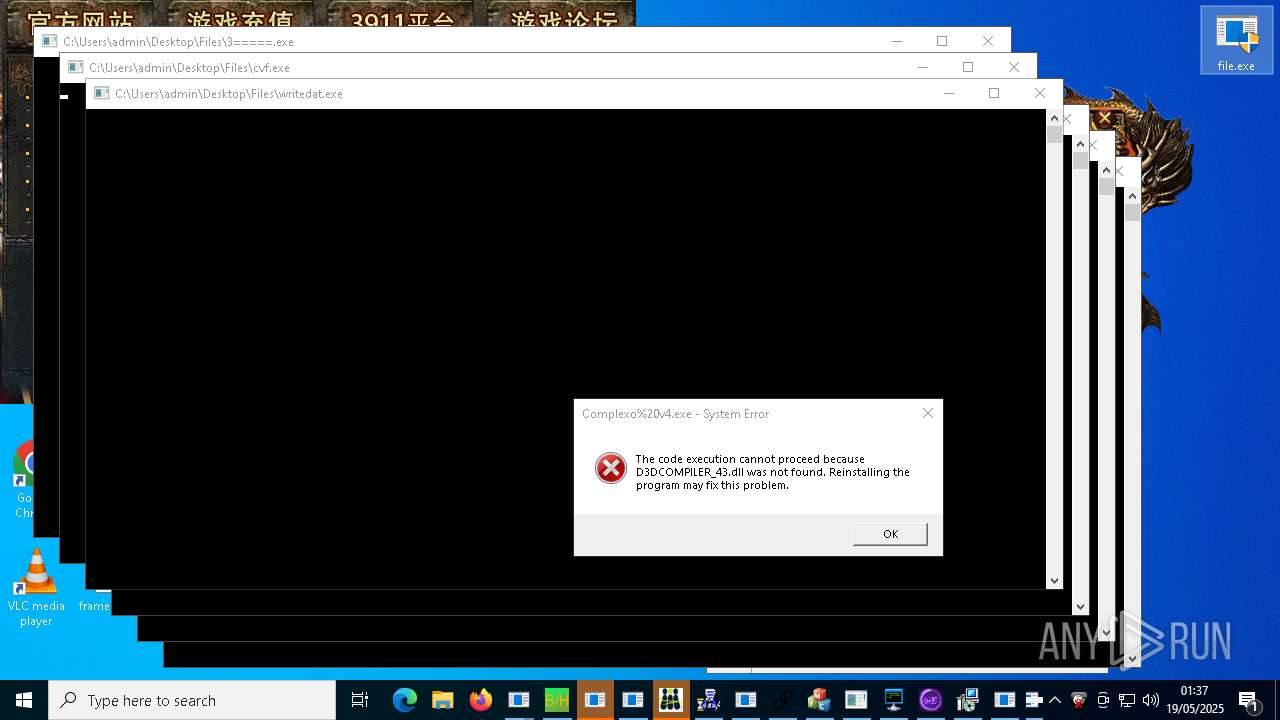
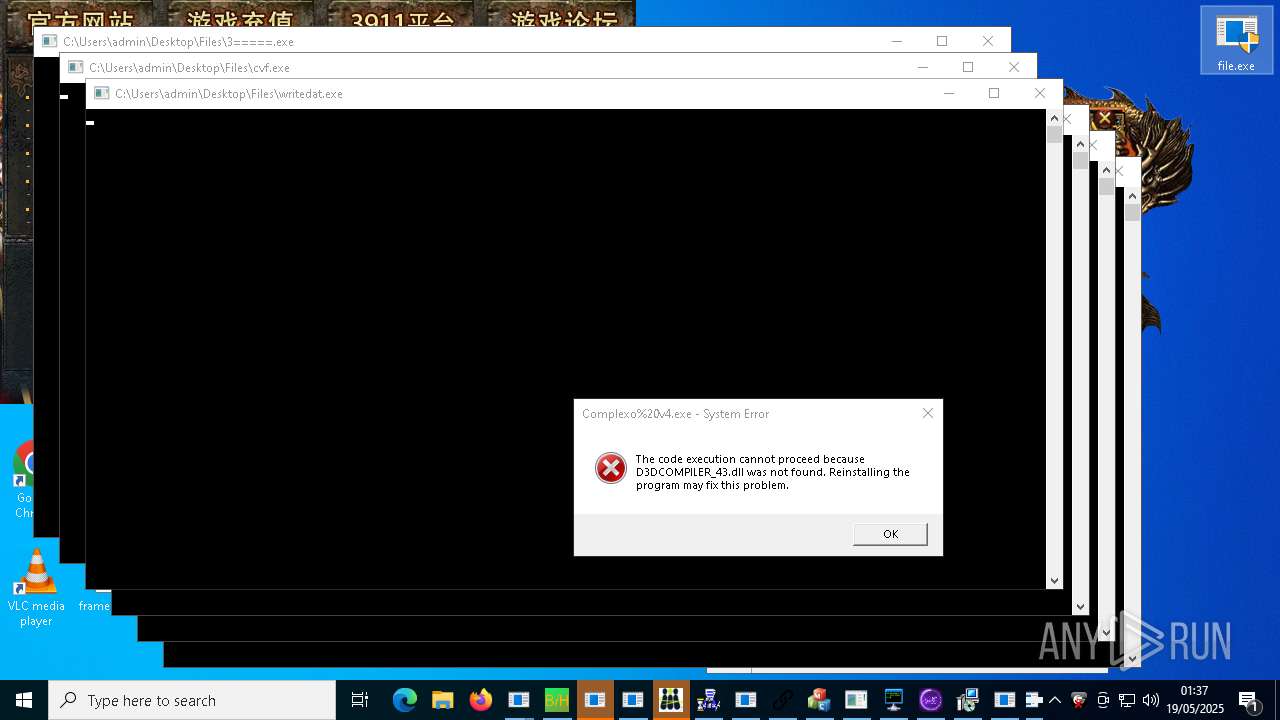
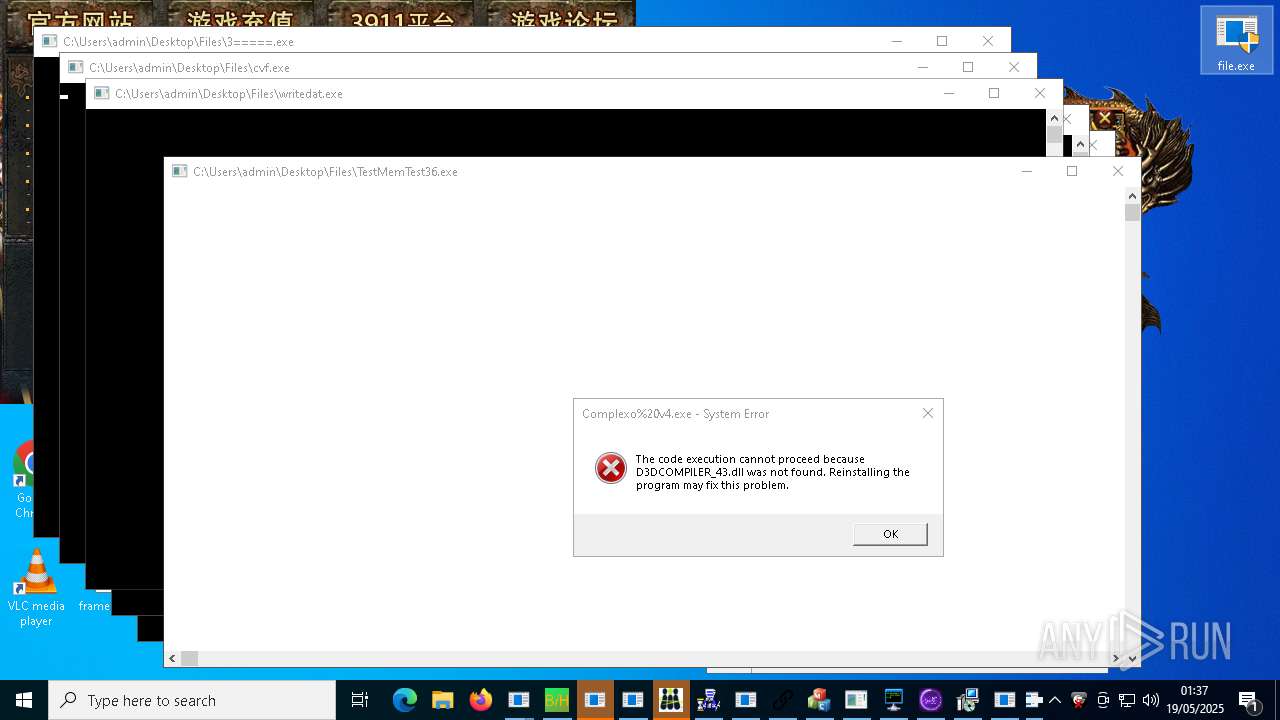
| URL: | https://s3.us-east-1.wasabisys.com/vxugmwdb/2fcad226b17131da4274e1b9f8f31359bdd325c9568665f08fd1f6c5d06a23ce |
| Full analysis: | https://app.any.run/tasks/7a9d36a2-3f05-4310-8a2b-35d2c935c85b |
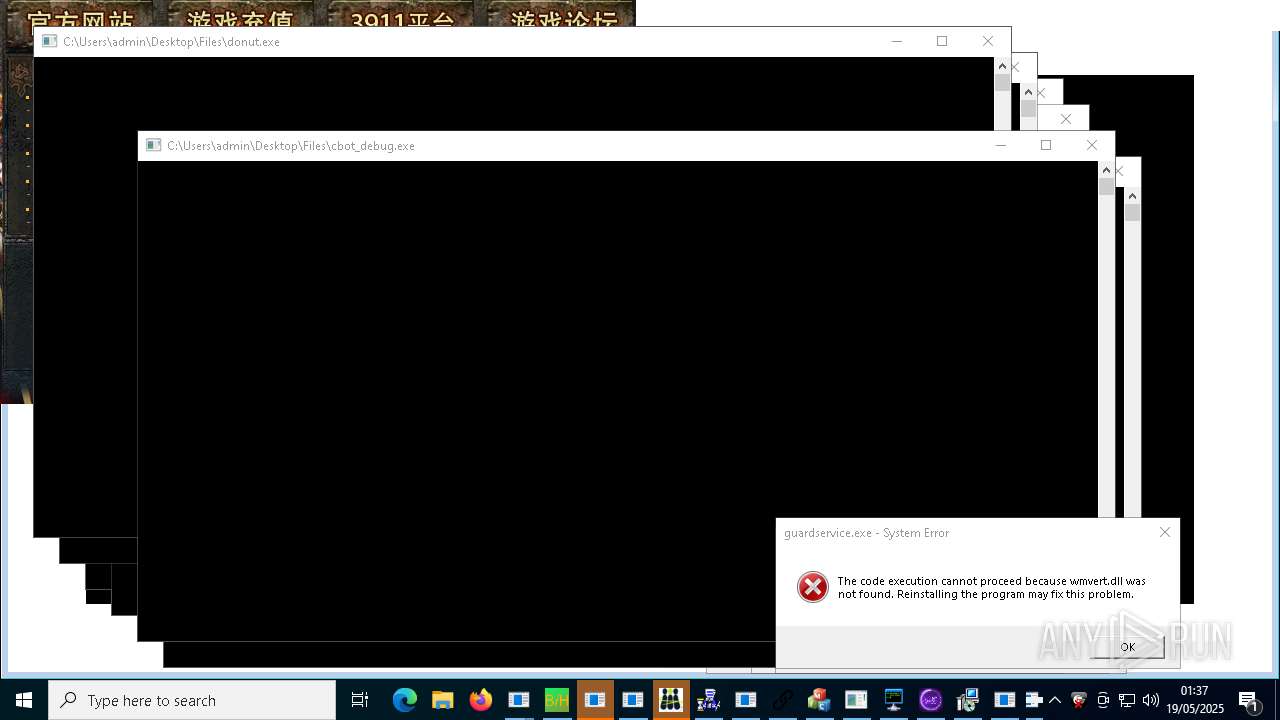
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | May 19, 2025, 01:34:06 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 5D8DE1793EFDF45C78867AC5CBE6D301 |
| SHA1: | 9845433643A2E841E96B96EF97A07D7024431FA7 |
| SHA256: | 6F7BC6F26FDC21FBB51A405D3D94583C008EA8358B8E7CBF70BF355B9B6B0EF6 |
| SSDEEP: | 3:N8chPSzHMy2KTShbUWCR4dKBH3FHdrMtX:2chPhXVhbUWCRQKBHVHdItX |
MALICIOUS
METERPRETER has been found (auto)
- file.exe (PID: 1280)
- file.exe (PID: 7692)
- file.exe (PID: 16244)
- file.exe (PID: 17012)
- file.exe (PID: 17376)
- file.exe (PID: 5260)
- file.exe (PID: 15340)
- file.exe (PID: 20296)
- file.exe (PID: 8492)
GENERIC has been found (auto)
- file.exe (PID: 6752)
- file.exe (PID: 13784)
- file.exe (PID: 15788)
- file.exe (PID: 17560)
- file.exe (PID: 17560)
- file.exe (PID: 15972)
- file.exe (PID: 17272)
- file.exe (PID: 15736)
- file.exe (PID: 12508)
- file.exe (PID: 10216)
- file.exe (PID: 19640)
- file.exe (PID: 7552)
- file.exe (PID: 22340)
- file.exe (PID: 10820)
- file.exe (PID: 10736)
- mixten.exe (PID: 22964)
- file.exe (PID: 7804)
- file.exe (PID: 8644)
- file.exe (PID: 5576)
- file.exe (PID: 8444)
- file.exe (PID: 9600)
- file.exe (PID: 12004)
- file.exe (PID: 17680)
- file.exe (PID: 15788)
- file.exe (PID: 9684)
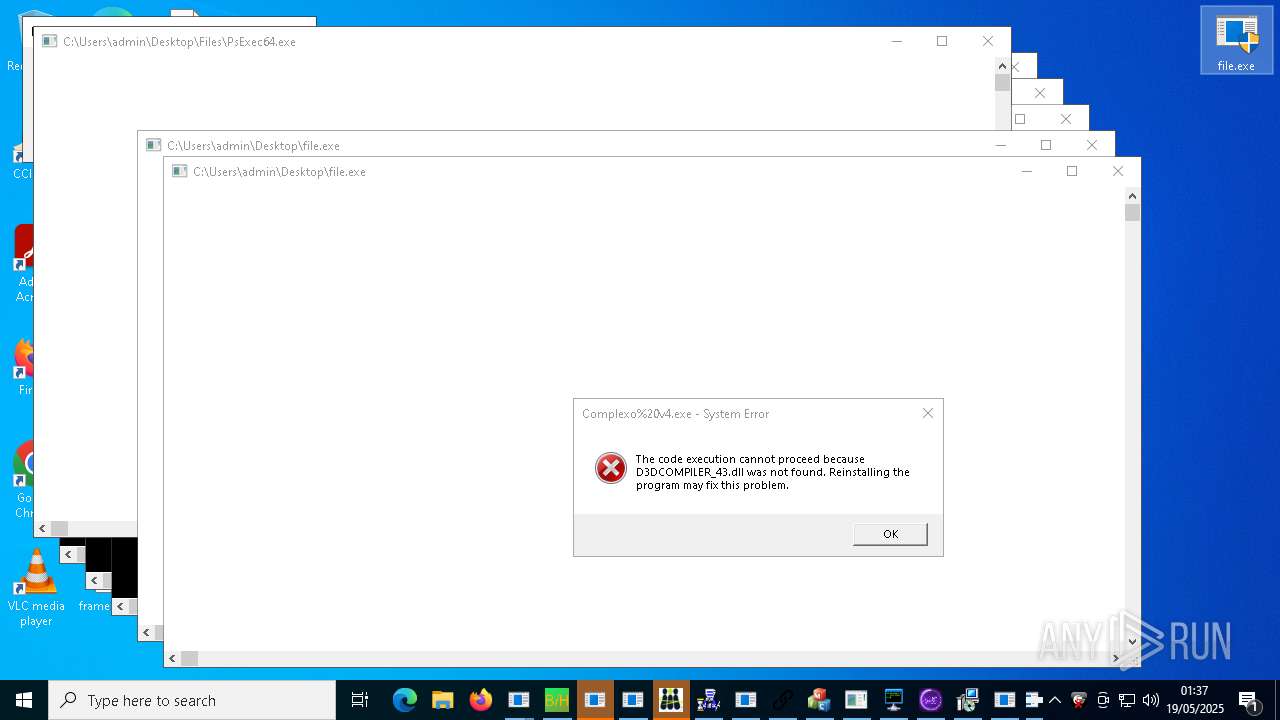
Executing a file with an untrusted certificate
- witheFile.exe (PID: 10864)
- LukeJazz.exe (PID: 15928)
- alex111111.exe (PID: 16412)
- alex111111.exe (PID: 11068)
- 123123213.exe (PID: 18864)
- PrivacyPolicy.exe (PID: 11820)
- ApertureLab.exe (PID: 20564)
- 1188%E7%83%88%E7%84%B0.exe (PID: 22568)
- inferno.exe (PID: 20804)
- 3911_wz.exe (PID: 12980)
- kzupdateagency-2.exe (PID: 25652)
- random.exe (PID: 26436)
- 32.exe (PID: 26152)
- dpinst_amd64.exe (PID: 26404)
- rsreport.exe (PID: 2096)
- goldik121212.exe (PID: 31012)
- begin.exe (PID: 31724)
- LatelyStated.2.exe (PID: 27160)
- goldik121212.exe (PID: 19696)
- goldik121212.exe (PID: 25972)
- client32.exe (PID: 33164)
- LatitudeVsnet.exe (PID: 28120)
- google.exe (PID: 34444)
- xdd.exe (PID: 34936)
- compiled.exe (PID: 34948)
- Built.exe (PID: 35316)
- brbotnet.exe (PID: 35544)
- Alli_AI_stable_latest_release_ver_801_Setup_win.exe (PID: 34996)
- FOi.exe (PID: 35700)
- PhilipPatrol.exe (PID: 22920)
- CompoundsTrim.exe (PID: 35716)
- TestLAB.exe (PID: 37156)
- n.exe (PID: 37852)
NJRAT has been found (auto)
- file.exe (PID: 2040)
- file.exe (PID: 6712)
- Server.exe (PID: 10732)
- file.exe (PID: 13168)
- Bloxflip%20Predictor.exe (PID: 11144)
- server.exe (PID: 14280)
- njrat.exe (PID: 11244)
- file.exe (PID: 15788)
- rundll32.exe (PID: 18672)
- Bloxflip Predictor.exe (PID: 15220)
- file.exe (PID: 18452)
- file.exe (PID: 5260)
- file.exe (PID: 9600)
- njSilent.exe (PID: 19956)
- file.exe (PID: 19488)
- file.exe (PID: 6752)
- svchost.exe (PID: 31792)
- file.exe (PID: 22932)
Connects to the CnC server
- file.exe (PID: 7804)
- file.exe (PID: 10692)
- svchost.exe (PID: 2196)
- file.exe (PID: 9648)
- file.exe (PID: 14820)
- file.exe (PID: 17164)
- file.exe (PID: 21628)
- file.exe (PID: 21048)
- file.exe (PID: 7732)
- file.exe (PID: 5576)
- syscrondvr.exe (PID: 24488)
ASYNCRAT has been found (auto)
- file.exe (PID: 9640)
- file.exe (PID: 10820)
- Krishna33.exe (PID: 11376)
- file.exe (PID: 13784)
- ddosziller.exe (PID: 13708)
- file.exe (PID: 9732)
- file.exe (PID: 17004)
- file.exe (PID: 14820)
- file.exe (PID: 7540)
- file.exe (PID: 14860)
- AsyncClient.exe (PID: 20748)
- file.exe (PID: 12160)
HAUSBOMBER has been detected (YARA)
- file.exe (PID: 8220)
- file.exe (PID: 5756)
- file.exe (PID: 5260)
- file.exe (PID: 6752)
- file.exe (PID: 2040)
REMCOS has been detected (SURICATA)
- Host.exe (PID: 12868)
Adds path to the Windows Defender exclusion list
- ometynadwa.exe (PID: 10320)
- cmd.exe (PID: 13432)
- cheese.exe (PID: 4880)
- v1saferui.2.exe (PID: 13172)
- svchost.exe (PID: 24152)
- VixenLoader.exe (PID: 12016)
AZORULT has been found (auto)
- file.exe (PID: 10820)
Uses Task Scheduler to autorun other applications
- MinerBTC.exe (PID: 13456)
- cmd.exe (PID: 11796)
- cmd.exe (PID: 17056)
- Client-built.exe (PID: 18332)
- RuntimeBroker.exe (PID: 18384)
- testingfile.exe (PID: 20280)
- JJSPLOIT.V2.exe (PID: 21716)
- diskutil.exe (PID: 11364)
- AdobePDFReader.exe (PID: 11972)
- CondoGenerator.exe (PID: 20528)
- LXGOhkH.exe (PID: 23176)
- CleanerV2.exe (PID: 25724)
- quasarat.exe (PID: 14464)
- cmd.exe (PID: 27168)
- cmd.exe (PID: 25716)
- XtuService.exe (PID: 27264)
- cmd.exe (PID: 28332)
- Quas_Brout_ncrypt.exe (PID: 29476)
- Java32.exe (PID: 31400)
- defender64.exe (PID: 32728)
- Client-built-Playit.exe (PID: 31596)
- Creal.exe (PID: 29584)
- WenzCord.exe (PID: 24300)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2196)
- MSBuild.exe (PID: 15188)
- alex111111.exe (PID: 11068)
- MSBuild.exe (PID: 17204)
- MSBuild.exe (PID: 17712)
- MSBuild.exe (PID: 18804)
- MSBuild.exe (PID: 6088)
- alex12312.exe (PID: 23576)
- MSBuild.exe (PID: 8164)
- MSBuild.exe (PID: 20236)
- MSBuild.exe (PID: 23844)
- MSBuild.exe (PID: 3008)
- MSBuild.exe (PID: 25796)
- MSBuild.exe (PID: 17532)
- MSBuild.exe (PID: 28988)
- MSBuild.exe (PID: 30640)
- MSBuild.exe (PID: 30660)
- cronikxqqq.exe (PID: 24380)
- fuck122112.exe (PID: 33120)
DCRAT has been found (auto)
- file.exe (PID: 7540)
- file.exe (PID: 7416)
QUASARRAT has been found (auto)
- file.exe (PID: 6752)
- RuntimeBroker.exe (PID: 18384)
- System.exe (PID: 17000)
- file.exe (PID: 17448)
- testingfile.exe (PID: 20280)
- file.exe (PID: 13976)
- CleanerV2.exe (PID: 25724)
- file.exe (PID: 8632)
- file.exe (PID: 17272)
- Quas_Brout_ncrypt.exe (PID: 29476)
- file.exe (PID: 9628)
- Java32.exe (PID: 31400)
- file.exe (PID: 15756)
- Client-built-Playit.exe (PID: 31596)
- defender64.exe (PID: 32728)
- file.exe (PID: 10820)
- Creal.exe (PID: 29584)
- file.exe (PID: 15044)
- WenzCord.exe (PID: 24300)
- file.exe (PID: 17680)
LUMMA has been found (auto)
- file.exe (PID: 8492)
- file.exe (PID: 14860)
- file.exe (PID: 19488)
- file.exe (PID: 8632)
- file.exe (PID: 14888)
- file.exe (PID: 15264)
STEALER has been found (auto)
- file.exe (PID: 15264)
- file.exe (PID: 16388)
- file.exe (PID: 9440)
- file.exe (PID: 8632)
- file.exe (PID: 2040)
- file.exe (PID: 11320)
- file.exe (PID: 17004)
- file.exe (PID: 17004)
- file.exe (PID: 20296)
- file.exe (PID: 15340)
- file.exe (PID: 9556)
Changes Windows Defender settings
- cheese.exe (PID: 4880)
- svchost.exe (PID: 24152)
- VixenLoader.exe (PID: 12016)
- xdd.exe (PID: 34936)
REMCOS has been found (auto)
- file.exe (PID: 9632)
- file.exe (PID: 15736)
- FXServer.exe (PID: 24224)
- file.exe (PID: 7732)
- file.exe (PID: 10692)
Uses Task Scheduler to run other applications
- PowerShell.exe (PID: 14528)
- MSystem32.exe (PID: 23916)
- 1.exe (PID: 13860)
Stealers network behavior
- svchost.exe (PID: 2196)
STEALERIUM has been found (auto)
- file.exe (PID: 9952)
Signed with known abused certificate
- file.exe (PID: 12508)
RAT has been found (auto)
- file.exe (PID: 17012)
- file.exe (PID: 14888)
- file.exe (PID: 20092)
- SteamDetector.exe (PID: 23924)
- file.exe (PID: 12696)
- SteamDetector.exe (PID: 17620)
- file.exe (PID: 9600)
- file.exe (PID: 9684)
- file.exe (PID: 9684)
QUASAR has been found (auto)
- file.exe (PID: 12004)
- file.exe (PID: 12160)
- diskutil.exe (PID: 11364)
- AdobePDFReader.exe (PID: 11972)
- file.exe (PID: 8444)
- file.exe (PID: 20324)
- Test2.exe (PID: 26296)
RDP has been found (auto)
- file.exe (PID: 2040)
Adds process to the Windows Defender exclusion list
- LXGOhkH.exe (PID: 23176)
SYSTEMBC has been detected (SURICATA)
- VmManagedSetup.exe (PID: 23940)
COINMINER has been found (auto)
- file.exe (PID: 13976)
PHISHING has been detected (SURICATA)
- svchost.exe (PID: 2196)
JIGSAW has been detected
- Jigsaw.exe (PID: 21136)
Attempting to connect via SSH
- Client-built.exe (PID: 18332)
ADESSTEALER has been found (auto)
- file.exe (PID: 9632)
- file.exe (PID: 5756)
Starts CertUtil for downloading files
- cmd.exe (PID: 22464)
CLICKFIX has been detected (SURICATA)
- svchost.exe (PID: 2196)
- file.exe (PID: 10540)
NANOCORE has been found (auto)
- file.exe (PID: 15736)
- jij.exe (PID: 9100)
- file.exe (PID: 15848)
Bypass execution policy to execute commands
- powershell.exe (PID: 27840)
- powershell.exe (PID: 17600)
Changes powershell execution policy (Bypass)
- svchost.exe (PID: 24152)
- VixenLoader.exe (PID: 12016)
XMRig has been detected
- xmrig.exe (PID: 29700)
REDLINE has been found (auto)
- file.exe (PID: 18452)
- file.exe (PID: 12508)
QUASAR has been detected (SURICATA)
- quasarat.exe (PID: 14464)
- Creal.exe (PID: 29584)
SNAKEKEYLOGGER has been detected (SURICATA)
- RegSvcs.exe (PID: 28580)
VIDAR has been found (auto)
- file.exe (PID: 14860)
RHADAMANTHYS has been found (auto)
- file.exe (PID: 16388)
FORMBOOK has been found (auto)
- file.exe (PID: 10216)
The EICAR Standard Anti-Virus Test File is detected
- justpoc.exe (PID: 23724)
- CefSharp.BrowsersSubprocess.exe (PID: 25632)
SCREENCONNECT has been found (auto)
- file.exe (PID: 14028)
PURELOGS has been found (auto)
- file.exe (PID: 15340)
Starts REAGENTC.EXE to disable the Windows Recovery Environment
- ReAgentc.exe (PID: 31768)
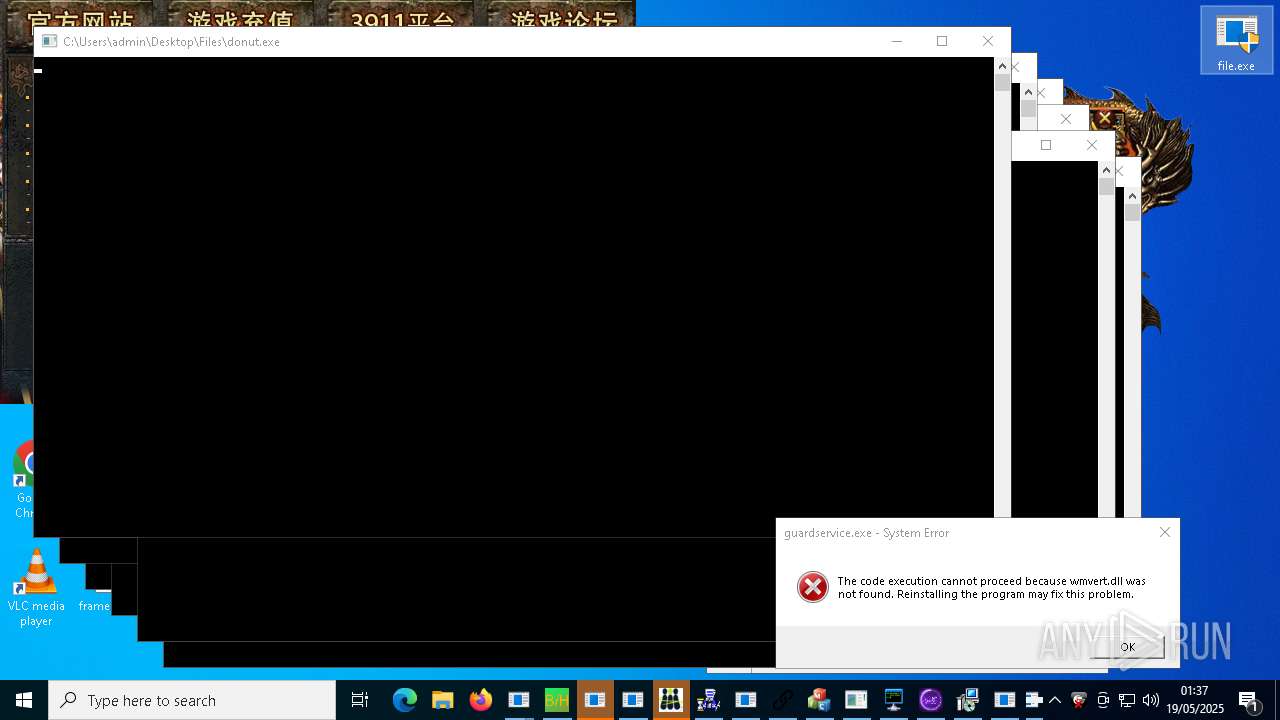
DONUTLOADER has been found (auto)
- file.exe (PID: 2320)
STEALC has been found (auto)
- file.exe (PID: 19488)
METASPLOIT has been detected (SURICATA)
- file.exe (PID: 17004)
METASPLOIT has been found (auto)
- file.exe (PID: 17004)
FORMBOOK has been detected (SURICATA)
- file.exe (PID: 5576)
COBALTSTRIKE has been found (auto)
- file.exe (PID: 9684)
Vulnerable driver has been detected
- sysmtdrav.exe (PID: 35184)
- sysmtdrav.exe (PID: 37220)
XRED has been found (auto)
- file.exe (PID: 15848)
Adds extension to the Windows Defender exclusion list
- xdd.exe (PID: 34936)
Execute application with conhost.exe as parent process
- sysmtdrav.exe (PID: 37220)
- sysmtdrav.exe (PID: 34016)
PHORPIEX has been detected (SURICATA)
- syscrondvr.exe (PID: 24488)
Attempting to scan the network
- Meredrop.exe (PID: 26668)
SMBSCAN has been detected (SURICATA)
- Meredrop.exe (PID: 26668)
SUSPICIOUS
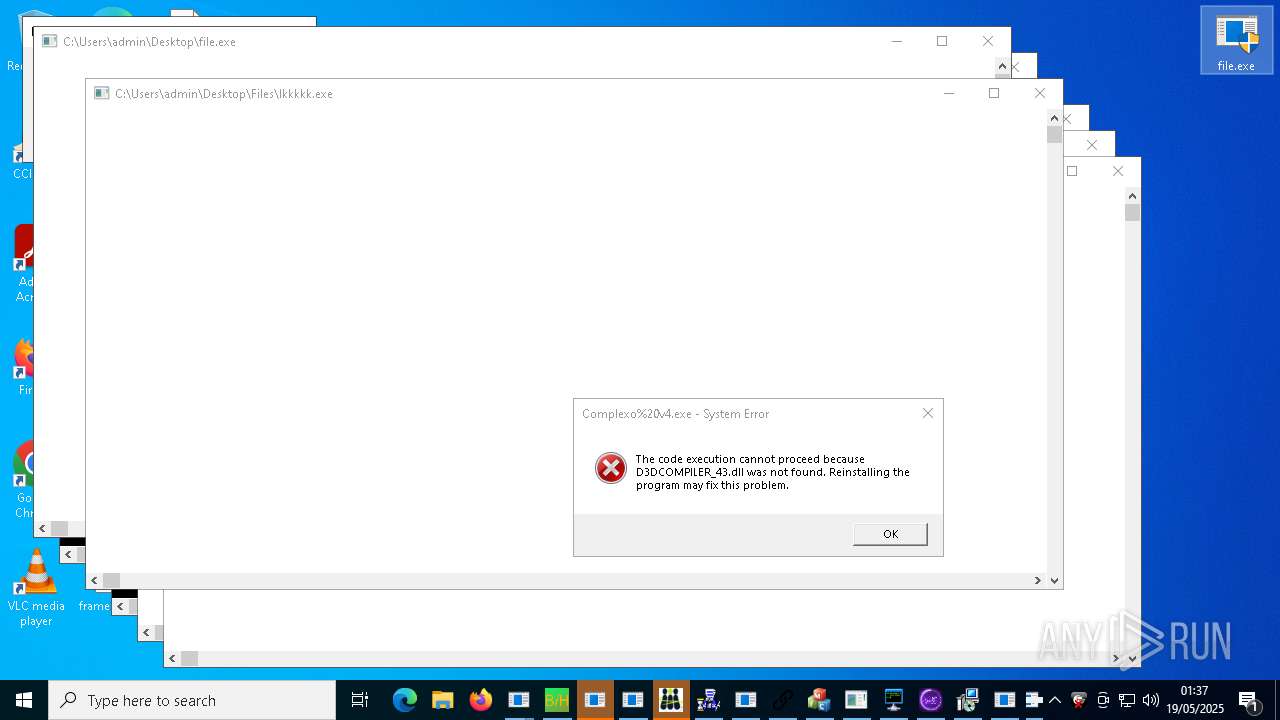
Executable content was dropped or overwritten
- file.exe (PID: 6752)
- file.exe (PID: 1280)
- file.exe (PID: 6712)
- file.exe (PID: 2040)
- file.exe (PID: 7540)
- file.exe (PID: 9648)
- file.exe (PID: 9468)
- file.exe (PID: 9640)
- Destover.exe (PID: 11920)
- file.exe (PID: 7552)
- file.exe (PID: 7416)
- file.exe (PID: 9692)
- file.exe (PID: 8492)
- file.exe (PID: 10820)
- Server.exe (PID: 10732)
- file.exe (PID: 7496)
- file.exe (PID: 11396)
- file.exe (PID: 7692)
- Bloxflip%20Predictor.exe (PID: 11144)
- file.exe (PID: 9684)
- file.exe (PID: 11996)
- file.exe (PID: 12508)
- file.exe (PID: 12332)
- file.exe (PID: 7732)
- PowerShell.exe (PID: 14528)
- file.exe (PID: 12680)
- file.exe (PID: 13168)
- Krishna33.exe (PID: 11376)
- file.exe (PID: 13812)
- file.exe (PID: 9632)
- file.exe (PID: 14028)
- file.exe (PID: 13784)
- file.exe (PID: 9952)
- server.exe (PID: 14280)
- c4284a2a6c1b60247944a03cbaf930c5.exe (PID: 17656)
- c4284a2a6c1b60247944a03cbaf930c5Srv.exe (PID: 18056)
- 444.exe (PID: 14924)
- file.exe (PID: 7720)
- ddosziller.exe (PID: 13708)
- file.exe (PID: 9732)
- file.exe (PID: 15616)
- njrat.exe (PID: 11244)
- Slasher.exe (PID: 8820)
- file.exe (PID: 15264)
- file.exe (PID: 15328)
- file.exe (PID: 15208)
- file.exe (PID: 13976)
- file.exe (PID: 15788)
- file.exe (PID: 15972)
- file.exe (PID: 17004)
- file.exe (PID: 15756)
- file.exe (PID: 17164)
- file.exe (PID: 17012)
- file.exe (PID: 15848)
- file.exe (PID: 16244)
- file.exe (PID: 14860)
- RuntimeBroker.exe (PID: 18384)
- rundll32.exe (PID: 18672)
- conhost.exe (PID: 19008)
- PrivacyPolicy.exe (PID: 11820)
- file.exe (PID: 17376)
- System.exe (PID: 17000)
- file.exe (PID: 17560)
- Bloxflip Predictor.exe (PID: 15220)
- PrivacyPolicy.tmp (PID: 21464)
- yhdl.exe (PID: 20540)
- file.exe (PID: 16388)
- file.exe (PID: 14820)
- testingfile.exe (PID: 20280)
- file.exe (PID: 9440)
- file.exe (PID: 15736)
- file.exe (PID: 12004)
- file.exe (PID: 12696)
- file.exe (PID: 12160)
- file.exe (PID: 18452)
- file.exe (PID: 2320)
- file.exe (PID: 15340)
- JJSPLOIT.V2.exe (PID: 21716)
- file.exe (PID: 14888)
- vncgroups.exe (PID: 21612)
- file.exe (PID: 5756)
- file.exe (PID: 19640)
- file.exe (PID: 8444)
- explorer.exe (PID: 8524)
- file.exe (PID: 15044)
- file.exe (PID: 8632)
- file.exe (PID: 17272)
- 1465810408079_502.exe (PID: 21732)
- file.exe (PID: 20092)
- FXServer.exe (PID: 24224)
- file.exe (PID: 5576)
- file.exe (PID: 17680)
- file.exe (PID: 5260)
- wj1bsetup.exe (PID: 24364)
- SteamDetector.exe (PID: 23924)
- Jigsaw.exe (PID: 21136)
- ApertureLab.exe (PID: 20564)
- file.exe (PID: 19488)
- tester.exe (PID: 14060)
- MSystem32.exe (PID: 23916)
- file.exe (PID: 9600)
- file.exe (PID: 8644)
- file.exe (PID: 17068)
- file.exe (PID: 10540)
- file.exe (PID: 20296)
- Sk7.6.exe (PID: 8464)
- wj1bsetup.tmp (PID: 3192)
- bridgesurrogatefontsvc.exe (PID: 23872)
- file.exe (PID: 10216)
- diskutil.exe (PID: 11364)
- AdobePDFReader.exe (PID: 11972)
- rah.exe (PID: 23148)
- installer.exe (PID: 15584)
- ChilledWindows.GUI.exe (PID: 25948)
- AsyncClient.exe (PID: 20748)
- rlol.exe (PID: 26132)
- file.exe (PID: 16640)
- ShtrayEasy.exe (PID: 19496)
- qwsrv3.3.exe (PID: 9892)
- file.exe (PID: 14704)
- discord.exe (PID: 20920)
- %E5%9B%9B%E6%96%B9%E5%B9%B3%E5%8F%B0-%E5%8D%A1%E5%95%86%E7%AB%AF.exe (PID: 24128)
- file.exe (PID: 10736)
- rlol.tmp (PID: 16852)
- IMG001.exe (PID: 24352)
- UHJKZD.exe (PID: 4000)
- qwsrv3.3.tmp (PID: 20764)
- file.exe (PID: 13788)
- LXGOhkH.exe (PID: 23176)
- file.exe (PID: 21048)
- SteamDetector.exe (PID: 17620)
- file.exe (PID: 20324)
- file.exe (PID: 9628)
- file.exe (PID: 7804)
- file.exe (PID: 22340)
- file.exe (PID: 17448)
- Solara_Protect.exe (PID: 18304)
- CleanerV2.exe (PID: 25724)
- mixten.exe (PID: 22964)
- powershell.exe (PID: 13804)
- jij.exe (PID: 9100)
- njSilent.exe (PID: 19956)
- file.exe (PID: 7728)
- jajajdva.exe (PID: 16084)
- pocketrar350sc.exe (PID: 18768)
- file.exe (PID: 22932)
- remcos_a.exe (PID: 29900)
- file.exe (PID: 11320)
- file.exe (PID: 21256)
- giftorder.exe (PID: 29544)
- XtuService.exe (PID: 27264)
- ChromeSetup.exe (PID: 29676)
- file.exe (PID: 12460)
- newtpp.exe (PID: 31000)
- v1saferui.2.exe (PID: 13172)
- file.exe (PID: 21604)
- file.exe (PID: 10692)
- Quodlibet.exe (PID: 31292)
- trojan.exe (PID: 14796)
- file.exe (PID: 23116)
- haozip_tiny.201805.exe (PID: 24040)
- file.exe (PID: 14776)
- file.exe (PID: 23308)
- Quas_Brout_ncrypt.exe (PID: 29476)
- Java32.exe (PID: 31400)
- Client-built-Playit.exe (PID: 31596)
- defender64.exe (PID: 32728)
- file.exe (PID: 10832)
- WindowsServices.exe (PID: 33208)
- black.exe (PID: 2392)
- x.exe (PID: 31068)
- eric.exe (PID: 31676)
- svchost.exe (PID: 31792)
- file.exe (PID: 11224)
- DiscordSpotifyBypass.exe (PID: 21788)
- Creal.exe (PID: 29584)
- 5vJ.exe (PID: 23704)
- fmt_01.exe (PID: 29760)
- file.exe (PID: 16856)
- file.exe (PID: 1312)
- sysmtdrav.exe (PID: 35184)
- file.exe (PID: 23076)
- file.exe (PID: 9556)
- CritScript.exe (PID: 33840)
- Built.exe (PID: 35316)
- wnbsqv3008.exe (PID: 33032)
- conhost.exe (PID: 36312)
- sysmtdrav.exe (PID: 37220)
- WenzCord.exe (PID: 24300)
- Test2.exe (PID: 26296)
- IcarusLite-v1.1.13-win.exe (PID: 31808)
- q-AMD64-Windows.exe (PID: 33864)
Potential Corporate Privacy Violation
- file.exe (PID: 6752)
- file.exe (PID: 7496)
- file.exe (PID: 7540)
- file.exe (PID: 5260)
- file.exe (PID: 8644)
- file.exe (PID: 7804)
- file.exe (PID: 7692)
- file.exe (PID: 9556)
- file.exe (PID: 5756)
- file.exe (PID: 7552)
- file.exe (PID: 8492)
- file.exe (PID: 9628)
- file.exe (PID: 9632)
- file.exe (PID: 9952)
- file.exe (PID: 10692)
- file.exe (PID: 9692)
- file.exe (PID: 10736)
- file.exe (PID: 10832)
- file.exe (PID: 9648)
- file.exe (PID: 11396)
- file.exe (PID: 1280)
- file.exe (PID: 12536)
- file.exe (PID: 11224)
- file.exe (PID: 12816)
- file.exe (PID: 12900)
- file.exe (PID: 13812)
- file.exe (PID: 11996)
- file.exe (PID: 9720)
- file.exe (PID: 7720)
- file.exe (PID: 13168)
- file.exe (PID: 15340)
- file.exe (PID: 15208)
- file.exe (PID: 15616)
- file.exe (PID: 15264)
- file.exe (PID: 15328)
- file.exe (PID: 15788)
- file.exe (PID: 9732)
- file.exe (PID: 17004)
- file.exe (PID: 17376)
- file.exe (PID: 17068)
- file.exe (PID: 15756)
- file.exe (PID: 12296)
- file.exe (PID: 17680)
- file.exe (PID: 16244)
- file.exe (PID: 17448)
- file.exe (PID: 12508)
- file.exe (PID: 17560)
- file.exe (PID: 16388)
- file.exe (PID: 17012)
- file.exe (PID: 15736)
- file.exe (PID: 14820)
- file.exe (PID: 14704)
- file.exe (PID: 12004)
- file.exe (PID: 20324)
- file.exe (PID: 15972)
- file.exe (PID: 8444)
- file.exe (PID: 2320)
- file.exe (PID: 9440)
- file.exe (PID: 12160)
- file.exe (PID: 12680)
- file.exe (PID: 18452)
- file.exe (PID: 14888)
- file.exe (PID: 17164)
- file.exe (PID: 14860)
- file.exe (PID: 12696)
- file.exe (PID: 8632)
- Client-built.exe (PID: 18332)
- file.exe (PID: 21048)
- file.exe (PID: 21300)
- file.exe (PID: 5576)
- file.exe (PID: 20296)
- file.exe (PID: 19640)
- file.exe (PID: 16640)
- file.exe (PID: 2040)
- file.exe (PID: 22340)
- file.exe (PID: 9600)
- file.exe (PID: 21628)
- file.exe (PID: 10820)
- file.exe (PID: 15848)
- file.exe (PID: 7732)
- file.exe (PID: 19488)
- file.exe (PID: 9684)
- file.exe (PID: 10216)
- file.exe (PID: 22932)
- file.exe (PID: 12460)
- file.exe (PID: 17272)
- file.exe (PID: 7416)
- file.exe (PID: 10540)
- file.exe (PID: 16856)
- Meredrop.exe (PID: 26668)
- file.exe (PID: 15044)
Contacting a server suspected of hosting an CnC
- file.exe (PID: 7804)
- file.exe (PID: 10692)
- Host.exe (PID: 12868)
- svchost.exe (PID: 2196)
- file.exe (PID: 9648)
- MSBuild.exe (PID: 15188)
- alex111111.exe (PID: 11068)
- MSBuild.exe (PID: 17204)
- MSBuild.exe (PID: 17712)
- MSBuild.exe (PID: 18804)
- file.exe (PID: 14820)
- MSBuild.exe (PID: 6088)
- alex12312.exe (PID: 23576)
- file.exe (PID: 17164)
- VmManagedSetup.exe (PID: 23940)
- MSBuild.exe (PID: 8164)
- MSBuild.exe (PID: 20236)
- MSBuild.exe (PID: 23844)
- MSBuild.exe (PID: 3008)
- MSBuild.exe (PID: 25796)
- file.exe (PID: 21628)
- quasarat.exe (PID: 14464)
- MSBuild.exe (PID: 17532)
- file.exe (PID: 21048)
- MSBuild.exe (PID: 28988)
- MSBuild.exe (PID: 30640)
- MSBuild.exe (PID: 30660)
- file.exe (PID: 7732)
- file.exe (PID: 5576)
- syscrondvr.exe (PID: 24488)
- cronikxqqq.exe (PID: 24380)
- fuck122112.exe (PID: 33120)
Process requests binary or script from the Internet
- file.exe (PID: 7540)
- file.exe (PID: 6712)
- file.exe (PID: 7552)
- file.exe (PID: 8492)
- file.exe (PID: 7496)
- file.exe (PID: 10820)
- file.exe (PID: 7692)
- file.exe (PID: 11996)
- file.exe (PID: 1280)
- file.exe (PID: 12508)
- file.exe (PID: 9648)
- file.exe (PID: 9692)
- file.exe (PID: 12680)
- file.exe (PID: 9632)
- file.exe (PID: 9952)
- file.exe (PID: 6752)
- file.exe (PID: 15264)
- file.exe (PID: 15736)
- file.exe (PID: 15972)
- file.exe (PID: 15788)
- file.exe (PID: 15208)
- file.exe (PID: 15328)
- file.exe (PID: 16856)
- file.exe (PID: 12296)
- file.exe (PID: 17012)
- file.exe (PID: 17448)
- file.exe (PID: 17376)
- file.exe (PID: 16244)
- file.exe (PID: 7720)
- file.exe (PID: 15756)
- file.exe (PID: 13168)
- file.exe (PID: 15340)
- file.exe (PID: 9732)
- file.exe (PID: 2320)
- file.exe (PID: 5756)
- file.exe (PID: 19640)
- file.exe (PID: 5260)
- file.exe (PID: 8444)
- file.exe (PID: 16388)
- file.exe (PID: 17680)
- file.exe (PID: 12004)
- file.exe (PID: 9556)
- file.exe (PID: 8644)
- file.exe (PID: 12696)
- file.exe (PID: 17068)
- file.exe (PID: 7732)
- file.exe (PID: 10736)
- file.exe (PID: 20296)
- file.exe (PID: 14860)
- file.exe (PID: 14704)
- file.exe (PID: 2040)
- file.exe (PID: 8632)
- file.exe (PID: 18452)
- file.exe (PID: 20324)
- file.exe (PID: 12160)
- file.exe (PID: 14888)
- kzupdateagency-2.exe (PID: 25652)
- file.exe (PID: 21048)
- file.exe (PID: 7804)
- file.exe (PID: 9628)
- file.exe (PID: 17560)
- file.exe (PID: 17004)
- %E5%9B%9B%E6%96%B9%E5%B9%B3%E5%8F%B0-%E5%8D%A1%E5%95%86%E7%AB%AF.exe (PID: 24128)
- file.exe (PID: 9600)
- 3911_wz.exe (PID: 12980)
- file.exe (PID: 22340)
- file.exe (PID: 10692)
- file.exe (PID: 15848)
- file.exe (PID: 5576)
- file.exe (PID: 19488)
- 1188%E7%83%88%E7%84%B0.exe (PID: 22568)
- file.exe (PID: 9684)
- file.exe (PID: 17164)
- file.exe (PID: 17272)
- file.exe (PID: 12900)
- file.exe (PID: 14820)
- file.exe (PID: 12536)
- file.exe (PID: 12460)
- file.exe (PID: 11224)
- file.exe (PID: 13812)
- file.exe (PID: 21628)
- file.exe (PID: 7416)
Connects to unusual port
- file.exe (PID: 8644)
- file.exe (PID: 7804)
- fern_wifi_recon%252.34.exe (PID: 10488)
- file.exe (PID: 6712)
- file.exe (PID: 5756)
- file.exe (PID: 9628)
- file.exe (PID: 10692)
- file.exe (PID: 10736)
- Host.exe (PID: 12868)
- file.exe (PID: 11396)
- file.exe (PID: 12680)
- MinerBTC.exe (PID: 13456)
- file.exe (PID: 9648)
- crack.exe (PID: 15720)
- file.exe (PID: 7720)
- file.exe (PID: 15340)
- XClient.exe (PID: 14048)
- PowerShell.exe (PID: 14528)
- file.exe (PID: 6752)
- file.exe (PID: 15328)
- file.exe (PID: 15788)
- conhost.exe (PID: 19008)
- rundll32.exe (PID: 18672)
- Client-built.exe (PID: 18332)
- prueba.exe (PID: 19904)
- file.exe (PID: 15972)
- file.exe (PID: 14820)
- file.exe (PID: 8444)
- CPDB.exe (PID: 21724)
- file.exe (PID: 18452)
- file.exe (PID: 17164)
- VmManagedSetup.exe (PID: 23940)
- System.exe (PID: 20672)
- idmans.exe (PID: 24076)
- 22.exe (PID: 24084)
- Bloxflip Predictor.exe (PID: 15220)
- EmmetPROD.exe (PID: 8740)
- CrSpoofer.exe (PID: 23292)
- Service.exe (PID: 8132)
- file.exe (PID: 9632)
- file.exe (PID: 12696)
- file.exe (PID: 19640)
- file.exe (PID: 15736)
- HTMSHE.exe (PID: 12096)
- file.exe (PID: 21628)
- systempreter.exe (PID: 8048)
- %E5%9B%9B%E6%96%B9%E5%B9%B3%E5%8F%B0-%E5%8D%A1%E5%95%86%E7%AB%AF.exe (PID: 24128)
- file.exe (PID: 15848)
- quasarat.exe (PID: 14464)
- MSystem32.exe (PID: 23916)
- System32.exe (PID: 9120)
- file.exe (PID: 21048)
- SubDir.exe (PID: 26324)
- file.exe (PID: 2320)
- file.exe (PID: 8632)
- toolwin.exe (PID: 17228)
- file.exe (PID: 7692)
- file.exe (PID: 9684)
- file.exe (PID: 14860)
- file.exe (PID: 7540)
- access.exe (PID: 13004)
- artifact.exe (PID: 31160)
- file.exe (PID: 14888)
- SearchUII.exe (PID: 18728)
- benpolatalemdar.exe (PID: 33216)
- svchost.exe (PID: 14568)
- Steanings.exe (PID: 31276)
- file.exe (PID: 17680)
- file.exe (PID: 7732)
- file.exe (PID: 17272)
- file.exe (PID: 2040)
- file.exe (PID: 12004)
- file.exe (PID: 8492)
- tmp.exe (PID: 32840)
- file.exe (PID: 16388)
- ckjg.exe (PID: 19708)
- svchost.exe (PID: 31792)
Process drops legitimate windows executable
- file.exe (PID: 9468)
- Destover.exe (PID: 11920)
- file.exe (PID: 7416)
- file.exe (PID: 9732)
- file.exe (PID: 12332)
- file.exe (PID: 17164)
- PrivacyPolicy.tmp (PID: 21464)
- file.exe (PID: 15972)
- file.exe (PID: 15328)
- file.exe (PID: 15044)
- 1465810408079_502.exe (PID: 21732)
- file.exe (PID: 2040)
- file.exe (PID: 9600)
- tester.exe (PID: 14060)
- file.exe (PID: 21048)
- diskutil.exe (PID: 11364)
- qwsrv3.3.tmp (PID: 20764)
- rlol.tmp (PID: 16852)
- file.exe (PID: 16388)
- ApertureLab.exe (PID: 20564)
- file.exe (PID: 13168)
- file.exe (PID: 18452)
- file.exe (PID: 21256)
- file.exe (PID: 14704)
- file.exe (PID: 10736)
- file.exe (PID: 5576)
- file.exe (PID: 14776)
- file.exe (PID: 7728)
- file.exe (PID: 7732)
- file.exe (PID: 19488)
- file.exe (PID: 12508)
- DiscordSpotifyBypass.exe (PID: 21788)
- Built.exe (PID: 35316)
- file.exe (PID: 10540)
- q-AMD64-Windows.exe (PID: 33864)
- IcarusLite-v1.1.13-win.exe (PID: 31808)
Starts a Microsoft application from unusual location
- Destover.exe (PID: 11920)
- ale22.exe (PID: 12292)
- 123123213.exe (PID: 18864)
- alex1221121212.exe (PID: 8740)
- alee12.exe (PID: 22900)
- crypted.2.exe (PID: 22808)
- inferno.exe (PID: 20804)
- diskutil.exe (PID: 11364)
- Windows%20Update.exe (PID: 6652)
- jajajdva.exe (PID: 16084)
- ChilledWindows.GUI.exe (PID: 25948)
- dpinst_amd64.exe (PID: 26404)
- alexx121212.exe (PID: 26752)
- cron2.exe (PID: 29100)
- cro2.exe (PID: 29652)
- BQ4m0sD.exe (PID: 22348)
- hell9o.exe (PID: 23892)
- Shy_lzt_crypted_LAB.exe (PID: 31192)
- voddddd.exe (PID: 25500)
- cron1.exe (PID: 26572)
- CrSpoof.exe (PID: 33200)
- cr1.exe (PID: 26588)
- Lead.Upload.Report.Feb.2025.exe (PID: 29020)
- addon.exe (PID: 34964)
- Built.exe (PID: 35316)
- cbot_debug.exe (PID: 21824)
- services.exe (PID: 35828)
- cleanup_tool.exe (PID: 30196)
- raw_cbot_debug.exe (PID: 5624)
Starts CMD.EXE for commands execution
- ometynadwa.exe (PID: 10320)
- Krishna33.exe (PID: 11376)
- ddosziller.exe (PID: 13708)
- LukeJazz.exe (PID: 15928)
- cheese.exe (PID: 4880)
- wscript.exe (PID: 12960)
- 1.exe (PID: 5172)
- downloader.exe (PID: 21172)
- loader.exe (PID: 20700)
- FXServer.exe (PID: 24224)
- OGFN%20Updater.exe (PID: 23708)
- IMG001.exe (PID: 24352)
- AsyncClient.exe (PID: 20748)
- discord.exe (PID: 20920)
- EmmetPROD.exe (PID: 8740)
- wscript.exe (PID: 8732)
- Solara_Protect.exe (PID: 18304)
- pornhub_downloader.exe (PID: 16784)
- %E6%B8%85%E7%90%86%E5%9E%83%E5%9C%BE.exe (PID: 18376)
- remcos_a.exe (PID: 29900)
- LXGOhkH.exe (PID: 23176)
- hell9o.exe (PID: 23892)
- bridgesurrogatefontsvc.exe (PID: 23872)
- GoogleUpdate.exe (PID: 27780)
- CrSpoof.exe (PID: 33200)
- addon.exe (PID: 34964)
- pclient.exe (PID: 30508)
- Lead.Upload.Report.Feb.2025.exe (PID: 29020)
- NOTallowedtocrypt.exe (PID: 31284)
Starts POWERSHELL.EXE for commands execution
- file.exe (PID: 9684)
- client.exe (PID: 13392)
- cheese.exe (PID: 4880)
- svchost.exe (PID: 24152)
- VixenLoader.exe (PID: 12016)
- xdd.exe (PID: 34936)
Executes as Windows Service
- VSSVC.exe (PID: 13036)
- vds.exe (PID: 26708)
- g.exe (PID: 29056)
- vds.exe (PID: 26476)
- sysmtdrav.exe (PID: 35184)
Checks for external IP
- VClientssss.exe (PID: 11136)
- svchost.exe (PID: 2196)
- cssgo.exe (PID: 14596)
- NJRAT%20DANGEROUS.exe (PID: 17804)
- bypass.exe (PID: 20668)
- svchost.exe (PID: 14568)
- requirements.exe (PID: 9008)
- CefSharp.BrowsersSubprocess.exe (PID: 25632)
- s.exe (PID: 23272)
- quasarat.exe (PID: 14464)
- RegSvcs.exe (PID: 28580)
- tRp.exe (PID: 23908)
- Creal.exe (PID: 29584)
Base64-obfuscated command line is found
- client.exe (PID: 13392)
BASE64 encoded PowerShell command has been detected
- client.exe (PID: 13392)
Executes application which crashes
- VClientssss.exe (PID: 11136)
- alex111111.exe (PID: 16412)
- NJRAT%20DANGEROUS.exe (PID: 17804)
- alex12312.exe (PID: 22216)
- support.client.exe (PID: 12656)
- %EC%9D%B8%ED%84%B0%EB%84%B7_%EC%A2%85%EB%9F%89%EC%A0%9C_%ED%85%8C%EC%8A%A4%ED%8A%B8-cksal16.exe (PID: 29644)
- alphamm.exe (PID: 25660)
- cronikxqqq.exe (PID: 29400)
- goldik121212.exe (PID: 31012)
- fuck122112.exe (PID: 32692)
- installsbot.crypt.exe (PID: 7924)
- CefSharp.BrowsersSubprocess.exe (PID: 25632)
- Test4.exe (PID: 26928)
- TiWorker.exe (PID: 8312)
Starts itself from another location
- Server.exe (PID: 10732)
- Bloxflip%20Predictor.exe (PID: 11144)
- c4284a2a6c1b60247944a03cbaf930c5Srv.exe (PID: 18056)
- 444.exe (PID: 14924)
- njrat.exe (PID: 11244)
- System.exe (PID: 17000)
- vncgroups.exe (PID: 21612)
- rah.exe (PID: 23148)
- SteamDetector.exe (PID: 23924)
- Jigsaw.exe (PID: 21136)
- ShtrayEasy.exe (PID: 19496)
- UHJKZD.exe (PID: 4000)
- IMG001.exe (PID: 24352)
- njSilent.exe (PID: 19956)
- newtpp.exe (PID: 31000)
- Creal.exe (PID: 29584)
- Test2.exe (PID: 26296)
Uses ATTRIB.EXE to modify file attributes
- Bloxflip%20Predictor.exe (PID: 11144)
- Bloxflip Predictor.exe (PID: 15220)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- MSBuild.exe (PID: 13512)
- cssgo.exe (PID: 14596)
- MSBuild.exe (PID: 19412)
- MSBuild.exe (PID: 7100)
- MSBuild.exe (PID: 6088)
- MSBuild.exe (PID: 8164)
- MSBuild.exe (PID: 20236)
- MSBuild.exe (PID: 3008)
- MSBuild.exe (PID: 28988)
- MSBuild.exe (PID: 30660)
- RegSvcs.exe (PID: 28580)
- MSBuild.exe (PID: 20072)
Uses NETSH.EXE to obtain data on the network
- cssgo.exe (PID: 14596)
Uses NETSH.EXE to add a firewall rule or allowed programs
- server.exe (PID: 14280)
- conhost.exe (PID: 19008)
- rundll32.exe (PID: 18672)
- fusca%20game.exe (PID: 11896)
- SteamDetector.exe (PID: 17620)
- SearchUII.exe (PID: 18728)
- svchost.exe (PID: 31792)
Executing commands from a ".bat" file
- Krishna33.exe (PID: 11376)
- ddosziller.exe (PID: 13708)
- wscript.exe (PID: 12960)
- downloader.exe (PID: 21172)
- AsyncClient.exe (PID: 20748)
- discord.exe (PID: 20920)
- Solara_Protect.exe (PID: 18304)
- pornhub_downloader.exe (PID: 16784)
- %E6%B8%85%E7%90%86%E5%9E%83%E5%9C%BE.exe (PID: 18376)
- bridgesurrogatefontsvc.exe (PID: 23872)
- CrSpoof.exe (PID: 33200)
Suspicious use of NETSH.EXE
- cssgo.exe (PID: 14596)
Application launched itself
- alex111111.exe (PID: 16412)
- alex12312.exe (PID: 22216)
- installer_ver12.22.exe (PID: 10952)
- g.exe (PID: 29056)
- 1.exe (PID: 5172)
- goldik121212.exe (PID: 31012)
- cronikxqqq.exe (PID: 29400)
- fuck122112.exe (PID: 32692)
- installsbot.crypt.exe (PID: 7924)
- tester.exe (PID: 14060)
- lkkkkk.exe (PID: 4244)
- cvf.exe (PID: 33232)
Connects to FTP
- wblog.exe (PID: 12520)
- tftp.exe (PID: 23388)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 16404)
- cmd.exe (PID: 15380)
- cmd.exe (PID: 26956)
- cmd.exe (PID: 23928)
- cmd.exe (PID: 25308)
Executing commands from ".cmd" file
- LukeJazz.exe (PID: 15928)
- hell9o.exe (PID: 23892)
Script adds exclusion path to Windows Defender
- cheese.exe (PID: 4880)
- svchost.exe (PID: 24152)
- VixenLoader.exe (PID: 12016)
- xdd.exe (PID: 34936)
Execution of CURL command
- cheese.exe (PID: 4880)
- loader.exe (PID: 20700)
The executable file from the user directory is run by the CMD process
- chrome.exe (PID: 19772)
- tesst.exe (PID: 22072)
- epic.exe (PID: 29096)
- update.exe (PID: 21512)
- Windows.exe (PID: 18284)
Connects to the server without a host name
- file.exe (PID: 12296)
- file.exe (PID: 16244)
- file.exe (PID: 17448)
- file.exe (PID: 17376)
- file.exe (PID: 9952)
- file.exe (PID: 17012)
- file.exe (PID: 12508)
- file.exe (PID: 15736)
- file.exe (PID: 12680)
- file.exe (PID: 9556)
- file.exe (PID: 7732)
- file.exe (PID: 7552)
- file.exe (PID: 14860)
- file.exe (PID: 8632)
- file.exe (PID: 20324)
- file.exe (PID: 21048)
- file.exe (PID: 17004)
- file.exe (PID: 10736)
- file.exe (PID: 9600)
- file.exe (PID: 22340)
- file.exe (PID: 5576)
- file.exe (PID: 7692)
- file.exe (PID: 12900)
- file.exe (PID: 7804)
- file.exe (PID: 17680)
- file.exe (PID: 16388)
- file.exe (PID: 11224)
- file.exe (PID: 2040)
- file.exe (PID: 5756)
- file.exe (PID: 7416)
- syscrondvr.exe (PID: 24488)
- file.exe (PID: 6752)
Crypto Currency Mining Activity Detected
- file.exe (PID: 17004)
Hides command output
- cmd.exe (PID: 23136)
- cmd.exe (PID: 29776)
Probably fake Windows Update
- schtasks.exe (PID: 10188)
Probably fake Windows Update file has been dropped
- JJSPLOIT.V2.exe (PID: 21716)
The process executes via Task Scheduler
- PowerShell.exe (PID: 14472)
Drop NetSupport executable file
- ApertureLab.exe (PID: 20564)
The process drops C-runtime libraries
- tester.exe (PID: 14060)
- ApertureLab.exe (PID: 20564)
- DiscordSpotifyBypass.exe (PID: 21788)
- Built.exe (PID: 35316)
- IcarusLite-v1.1.13-win.exe (PID: 31808)
- q-AMD64-Windows.exe (PID: 33864)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 13184)
- cmd.exe (PID: 30432)
Process drops python dynamic module
- tester.exe (PID: 14060)
- DiscordSpotifyBypass.exe (PID: 21788)
- Built.exe (PID: 35316)
- IcarusLite-v1.1.13-win.exe (PID: 31808)
- q-AMD64-Windows.exe (PID: 33864)
The process executes VB scripts
- FXServer.exe (PID: 24224)
- jajajdva.exe (PID: 16084)
- remcos_a.exe (PID: 29900)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 22160)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 18808)
Contacting a server suspected of hosting an Exploit Kit
- file.exe (PID: 7804)
- file.exe (PID: 17680)
- file.exe (PID: 9684)
Starts SC.EXE for service management
- x.exe (PID: 31068)
Windows service management via SC.EXE
- sc.exe (PID: 21356)
- sc.exe (PID: 30124)
Creates a new Windows service
- sc.exe (PID: 4220)
Deletes scheduled task without confirmation
- schtasks.exe (PID: 33256)
- schtasks.exe (PID: 34508)
Stops a currently running service
- sc.exe (PID: 30732)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 22160)
Malware-specific behavior (creating "System.dll" in Temp)
- haozip_tiny.201805.exe (PID: 24040)
Drops a system driver (possible attempt to evade defenses)
- sysmtdrav.exe (PID: 35184)
- sysmtdrav.exe (PID: 37220)
Uses WMIC.EXE to obtain Windows Installer data
- Trojan.Malpack.Themida%20(Anti%20VM).exe (PID: 20956)
Starts application with an unusual extension
- cmd.exe (PID: 31832)
Manipulates environment variables
- powershell.exe (PID: 37196)
Script adds exclusion extension to Windows Defender
- xdd.exe (PID: 34936)
INFO
Application launched itself
- msedge.exe (PID: 7264)
- msedge.exe (PID: 9032)
- msedge.exe (PID: 17224)
Reads the computer name
- identity_helper.exe (PID: 8488)
- identity_helper.exe (PID: 2600)
- file.exe (PID: 2040)
- file.exe (PID: 8220)
- file.exe (PID: 5756)
- file.exe (PID: 6752)
- file.exe (PID: 5260)
Executable content was dropped or overwritten
- msedge.exe (PID: 7264)
Reads Environment values
- identity_helper.exe (PID: 2600)
- identity_helper.exe (PID: 8488)
Checks supported languages
- identity_helper.exe (PID: 8488)
- identity_helper.exe (PID: 2600)
- file.exe (PID: 8220)
- file.exe (PID: 2040)
- file.exe (PID: 5260)
- file.exe (PID: 5756)
- file.exe (PID: 6752)
Manual execution by a user
- file.exe (PID: 8220)
- file.exe (PID: 8932)
- file.exe (PID: 8668)
- file.exe (PID: 2516)
- file.exe (PID: 1328)
- file.exe (PID: 4112)
- file.exe (PID: 5260)
- file.exe (PID: 5756)
- file.exe (PID: 2040)
- file.exe (PID: 6752)
- file.exe (PID: 7532)
- file.exe (PID: 7720)
- file.exe (PID: 7716)
- file.exe (PID: 7740)
- file.exe (PID: 7788)
- file.exe (PID: 7552)
- file.exe (PID: 7464)
- file.exe (PID: 7496)
- file.exe (PID: 7416)
- file.exe (PID: 7540)
- file.exe (PID: 7976)
- file.exe (PID: 8256)
- file.exe (PID: 7696)
- file.exe (PID: 7400)
- file.exe (PID: 5576)
- file.exe (PID: 6712)
- file.exe (PID: 7444)
- file.exe (PID: 1348)
- file.exe (PID: 1280)
- file.exe (PID: 1312)
- file.exe (PID: 6424)
- file.exe (PID: 6760)
- file.exe (PID: 6080)
- file.exe (PID: 7728)
- file.exe (PID: 6252)
- file.exe (PID: 7732)
- file.exe (PID: 7804)
- file.exe (PID: 8524)
- file.exe (PID: 7692)
- file.exe (PID: 7720)
- file.exe (PID: 7648)
- file.exe (PID: 2344)
- file.exe (PID: 8644)
- file.exe (PID: 8012)
- file.exe (PID: 9468)
- file.exe (PID: 7400)
- file.exe (PID: 7572)
- file.exe (PID: 9440)
- file.exe (PID: 9564)
- file.exe (PID: 9612)
- file.exe (PID: 9624)
- file.exe (PID: 9640)
- file.exe (PID: 9584)
- file.exe (PID: 9648)
- file.exe (PID: 9660)
- file.exe (PID: 9684)
- file.exe (PID: 9676)
- file.exe (PID: 8968)
- file.exe (PID: 9728)
- file.exe (PID: 8492)
- file.exe (PID: 9628)
- file.exe (PID: 9556)
- file.exe (PID: 9692)
- file.exe (PID: 9632)
- file.exe (PID: 9684)
- file.exe (PID: 9732)
- file.exe (PID: 9952)
- file.exe (PID: 9816)
- file.exe (PID: 9968)
- file.exe (PID: 1168)
- file.exe (PID: 10692)
- file.exe (PID: 10736)
- file.exe (PID: 10180)
- file.exe (PID: 10820)
- file.exe (PID: 10832)
- file.exe (PID: 7564)
- file.exe (PID: 11004)
- file.exe (PID: 11160)
- file.exe (PID: 11180)
- file.exe (PID: 11180)
- file.exe (PID: 11296)
- file.exe (PID: 11312)
- file.exe (PID: 11320)
- file.exe (PID: 11332)
- file.exe (PID: 11412)
- file.exe (PID: 11396)
- file.exe (PID: 11996)
- file.exe (PID: 11868)
- file.exe (PID: 12004)
- file.exe (PID: 12160)
- file.exe (PID: 12176)
- file.exe (PID: 8488)
- file.exe (PID: 8372)
- file.exe (PID: 12192)
- file.exe (PID: 9084)
- file.exe (PID: 12332)
- file.exe (PID: 12460)
- file.exe (PID: 12508)
- file.exe (PID: 12536)
- file.exe (PID: 12788)
- file.exe (PID: 12924)
- file.exe (PID: 12864)
- file.exe (PID: 12896)
- file.exe (PID: 12956)
- file.exe (PID: 11224)
- file.exe (PID: 9600)
- file.exe (PID: 12816)
- file.exe (PID: 12900)
- file.exe (PID: 13408)
- file.exe (PID: 13568)
- file.exe (PID: 13812)
- file.exe (PID: 13168)
- file.exe (PID: 13976)
- file.exe (PID: 14028)
- file.exe (PID: 14104)
- file.exe (PID: 14200)
- file.exe (PID: 13784)
- file.exe (PID: 8444)
- file.exe (PID: 9720)
- file.exe (PID: 13676)
- file.exe (PID: 14144)
- file.exe (PID: 13976)
- file.exe (PID: 14464)
- file.exe (PID: 14516)
- file.exe (PID: 12680)
- file.exe (PID: 14540)
- file.exe (PID: 14568)
- file.exe (PID: 14776)
- file.exe (PID: 15044)
- file.exe (PID: 15208)
- file.exe (PID: 15264)
- file.exe (PID: 15328)
- file.exe (PID: 15340)
- file.exe (PID: 14496)
- file.exe (PID: 14560)
- file.exe (PID: 14644)
- file.exe (PID: 14824)
- file.exe (PID: 6264)
- file.exe (PID: 14932)
- file.exe (PID: 14816)
- file.exe (PID: 14544)
- file.exe (PID: 15616)
- file.exe (PID: 15736)
- file.exe (PID: 15756)
- file.exe (PID: 15788)
- file.exe (PID: 15848)
- file.exe (PID: 15908)
- file.exe (PID: 15928)
- file.exe (PID: 15940)
- file.exe (PID: 15972)
- file.exe (PID: 16048)
- file.exe (PID: 16064)
- file.exe (PID: 16164)
- file.exe (PID: 16084)
- file.exe (PID: 16244)
- file.exe (PID: 16340)
- file.exe (PID: 14860)
- file.exe (PID: 16388)
- file.exe (PID: 16640)
- file.exe (PID: 14492)
- file.exe (PID: 16856)
- file.exe (PID: 16972)
- file.exe (PID: 16956)
- file.exe (PID: 16984)
- file.exe (PID: 17004)
- file.exe (PID: 17012)
- file.exe (PID: 17044)
- file.exe (PID: 17032)
- file.exe (PID: 17052)
- file.exe (PID: 17164)
- file.exe (PID: 17068)
- file.exe (PID: 14820)
- file.exe (PID: 12296)
- file.exe (PID: 17272)
- file.exe (PID: 17376)
- file.exe (PID: 12696)
- file.exe (PID: 17448)
- file.exe (PID: 17560)
- file.exe (PID: 17680)
- file.exe (PID: 17876)
- file.exe (PID: 17868)
- file.exe (PID: 17896)
- file.exe (PID: 18184)
- file.exe (PID: 18216)
- file.exe (PID: 17500)
- file.exe (PID: 2320)
- file.exe (PID: 8632)
- file.exe (PID: 14704)
- file.exe (PID: 13788)
- file.exe (PID: 18452)
- file.exe (PID: 18716)
- file.exe (PID: 18936)
- file.exe (PID: 18784)
- file.exe (PID: 18804)
- file.exe (PID: 18824)
- file.exe (PID: 18852)
- file.exe (PID: 18896)
- file.exe (PID: 14888)
- file.exe (PID: 17252)
- file.exe (PID: 19488)
- file.exe (PID: 19640)
- file.exe (PID: 20092)
- file.exe (PID: 20012)
- file.exe (PID: 20296)
- file.exe (PID: 20080)
- file.exe (PID: 20260)
- file.exe (PID: 20264)
- file.exe (PID: 20324)
- file.exe (PID: 21048)
- file.exe (PID: 21256)
- file.exe (PID: 21300)
- file.exe (PID: 10540)
- file.exe (PID: 12952)
- file.exe (PID: 16712)
- file.exe (PID: 21264)
- file.exe (PID: 20616)
- file.exe (PID: 21524)
- file.exe (PID: 5956)
- file.exe (PID: 22060)
- file.exe (PID: 21616)
- file.exe (PID: 22932)
- file.exe (PID: 23076)
- file.exe (PID: 21604)
- file.exe (PID: 21628)
- file.exe (PID: 23308)
- file.exe (PID: 10216)
- file.exe (PID: 18224)
- file.exe (PID: 22340)
- file.exe (PID: 24320)
- file.exe (PID: 24328)
- file.exe (PID: 24384)
- file.exe (PID: 24400)
- file.exe (PID: 24436)
- file.exe (PID: 24408)
- file.exe (PID: 24424)
- file.exe (PID: 24432)
- file.exe (PID: 24456)
- file.exe (PID: 24448)
- file.exe (PID: 24472)
- file.exe (PID: 24488)
- file.exe (PID: 24464)
- file.exe (PID: 24480)
- file.exe (PID: 24392)
- file.exe (PID: 24416)
- file.exe (PID: 24504)
- file.exe (PID: 24520)
- file.exe (PID: 24512)
- file.exe (PID: 24496)
- file.exe (PID: 24528)
- file.exe (PID: 24536)
- file.exe (PID: 24552)
- file.exe (PID: 24564)
- file.exe (PID: 24684)
- file.exe (PID: 20928)
- file.exe (PID: 17120)
- file.exe (PID: 25608)
- file.exe (PID: 25616)
- file.exe (PID: 23116)
- file.exe (PID: 19684)
- file.exe (PID: 11840)
- file.exe (PID: 19852)
- file.exe (PID: 27092)
- file.exe (PID: 26812)
- file.exe (PID: 24600)
- file.exe (PID: 26564)
- file.exe (PID: 27036)
- file.exe (PID: 19876)
- file.exe (PID: 27272)
- file.exe (PID: 27496)
- file.exe (PID: 27528)
- file.exe (PID: 27200)
- file.exe (PID: 27208)
- file.exe (PID: 24412)
- file.exe (PID: 13996)
- file.exe (PID: 27628)
- file.exe (PID: 18596)
- file.exe (PID: 25292)
- file.exe (PID: 26764)
- file.exe (PID: 26248)
- file.exe (PID: 4988)
- file.exe (PID: 10496)
- file.exe (PID: 26148)
- file.exe (PID: 25700)
- file.exe (PID: 26188)
- file.exe (PID: 25216)
- file.exe (PID: 15516)
- file.exe (PID: 27828)
- file.exe (PID: 15252)
- file.exe (PID: 27252)
- file.exe (PID: 27668)
- file.exe (PID: 27080)
- file.exe (PID: 14104)
- file.exe (PID: 27712)
- file.exe (PID: 27764)
- file.exe (PID: 28192)
- file.exe (PID: 28096)
- file.exe (PID: 28088)
- file.exe (PID: 28160)
- file.exe (PID: 28256)
- file.exe (PID: 28292)
- file.exe (PID: 28024)
- file.exe (PID: 28228)
- file.exe (PID: 36028)
- file.exe (PID: 4352)
- file.exe (PID: 23288)
The sample compiled with english language support
- file.exe (PID: 1280)
- file.exe (PID: 6752)
- file.exe (PID: 9556)
- file.exe (PID: 9468)
- Destover.exe (PID: 11920)
- file.exe (PID: 7416)
- file.exe (PID: 12536)
- file.exe (PID: 7692)
- c4284a2a6c1b60247944a03cbaf930c5.exe (PID: 17656)
- c4284a2a6c1b60247944a03cbaf930c5Srv.exe (PID: 18056)
- file.exe (PID: 9732)
- file.exe (PID: 12332)
- file.exe (PID: 16244)
- file.exe (PID: 17068)
- file.exe (PID: 17164)
- PrivacyPolicy.tmp (PID: 21464)
- file.exe (PID: 17560)
- file.exe (PID: 17012)
- file.exe (PID: 12508)
- file.exe (PID: 15756)
- file.exe (PID: 15972)
- file.exe (PID: 17376)
- file.exe (PID: 15328)
- file.exe (PID: 15736)
- file.exe (PID: 7552)
- file.exe (PID: 20324)
- file.exe (PID: 18452)
- file.exe (PID: 5260)
- ApertureLab.exe (PID: 20564)
- file.exe (PID: 9600)
- file.exe (PID: 5576)
- file.exe (PID: 21048)
- tester.exe (PID: 14060)
- file.exe (PID: 12680)
- file.exe (PID: 19640)
- file.exe (PID: 2040)
- qwsrv3.3.tmp (PID: 20764)
- rlol.tmp (PID: 16852)
- file.exe (PID: 13788)
- file.exe (PID: 16388)
- file.exe (PID: 13168)
- mixten.exe (PID: 22964)
- file.exe (PID: 11320)
- file.exe (PID: 15788)
- file.exe (PID: 21256)
- giftorder.exe (PID: 29544)
- file.exe (PID: 14704)
- file.exe (PID: 10216)
- ChromeSetup.exe (PID: 29676)
- file.exe (PID: 10736)
- file.exe (PID: 8444)
- Quodlibet.exe (PID: 31292)
- file.exe (PID: 14776)
- file.exe (PID: 15340)
- file.exe (PID: 7728)
- file.exe (PID: 10692)
- file.exe (PID: 5756)
- file.exe (PID: 12004)
- file.exe (PID: 20296)
- file.exe (PID: 7732)
- DiscordSpotifyBypass.exe (PID: 21788)
- file.exe (PID: 17004)
- file.exe (PID: 10540)
- Built.exe (PID: 35316)
- file.exe (PID: 15848)
- q-AMD64-Windows.exe (PID: 33864)
- IcarusLite-v1.1.13-win.exe (PID: 31808)
The sample compiled with chinese language support
- file.exe (PID: 8644)
- file.exe (PID: 9628)
- file.exe (PID: 10736)
- file.exe (PID: 7692)
- file.exe (PID: 9952)
- file.exe (PID: 12680)
- file.exe (PID: 9632)
- file.exe (PID: 11996)
- file.exe (PID: 13168)
- file.exe (PID: 7720)
- file.exe (PID: 15756)
- file.exe (PID: 15264)
- file.exe (PID: 17680)
- file.exe (PID: 16388)
- file.exe (PID: 6752)
- file.exe (PID: 14704)
- file.exe (PID: 2320)
- file.exe (PID: 14888)
- file.exe (PID: 8444)
- rlol.exe (PID: 26132)
- qwsrv3.3.exe (PID: 9892)
- file.exe (PID: 15736)
- file.exe (PID: 10820)
- file.exe (PID: 17448)
- ChromeSetup.exe (PID: 29676)
- file.exe (PID: 5260)
- file.exe (PID: 19488)
Attempting to use instant messaging service
- MSBuild.exe (PID: 13512)
- cssgo.exe (PID: 14596)
- svchost.exe (PID: 2196)
- MSBuild.exe (PID: 19412)
- MSBuild.exe (PID: 7100)
- MSBuild.exe (PID: 6088)
- MSBuild.exe (PID: 8164)
- MSBuild.exe (PID: 20236)
- Bloxflip Predictor.exe (PID: 15220)
- MSBuild.exe (PID: 28988)
- MSBuild.exe (PID: 30660)
- RegSvcs.exe (PID: 28580)
- MSBuild.exe (PID: 20072)
The sample compiled with polish language support
- file.exe (PID: 15788)
- ChromeSetup.exe (PID: 29676)
Execution of CURL command
- cmd.exe (PID: 19552)
- cmd.exe (PID: 23136)
- cmd.exe (PID: 29776)
The sample compiled with arabic language support
- 1465810408079_502.exe (PID: 21732)
- ChromeSetup.exe (PID: 29676)
Compiled with Borland Delphi (YARA)
- conhost.exe (PID: 6576)
- file.exe (PID: 2040)
- conhost.exe (PID: 7296)
The sample compiled with russian language support
- qwsrv3.3.tmp (PID: 20764)
- ChromeSetup.exe (PID: 29676)
- file.exe (PID: 17004)
- file.exe (PID: 9684)
The sample compiled with korean language support
- file.exe (PID: 22340)
- ChromeSetup.exe (PID: 29676)
The sample compiled with turkish language support
- file.exe (PID: 7804)
- file.exe (PID: 17680)
- ChromeSetup.exe (PID: 29676)
The sample compiled with bulgarian language support
- ChromeSetup.exe (PID: 29676)
The sample compiled with czech language support
- ChromeSetup.exe (PID: 29676)
The sample compiled with german language support
- ChromeSetup.exe (PID: 29676)
The sample compiled with spanish language support
- ChromeSetup.exe (PID: 29676)
The sample compiled with french language support
- ChromeSetup.exe (PID: 29676)
The sample compiled with Indonesian language support
- ChromeSetup.exe (PID: 29676)
The sample compiled with Italian language support
- ChromeSetup.exe (PID: 29676)
The sample compiled with japanese language support
- ChromeSetup.exe (PID: 29676)
- sysmtdrav.exe (PID: 35184)
- sysmtdrav.exe (PID: 37220)
The sample compiled with slovak language support
- ChromeSetup.exe (PID: 29676)
The sample compiled with swedish language support
- ChromeSetup.exe (PID: 29676)
NirSoft software is detected
- nircmd.exe (PID: 36732)
Changes the display of characters in the console
- cmd.exe (PID: 31832)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
1 668
Monitored processes
1 369
Malicious processes
195
Suspicious processes
54
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 448 | dwm.exe | C:\Windows\System32\dwm.exe | — | sysmtdrav.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Desktop Window Manager Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | "C:\Users\admin\Desktop\Files\PowerRat.exe" | C:\Users\admin\Desktop\Files\PowerRat.exe | — | file.exe | |||||||||||
User: admin Integrity Level: HIGH Version: 1.0.0.0 Modules
| |||||||||||||||
| 660 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=entity_extraction_service.mojom.Extractor --lang=en-US --service-sandbox-type=entity_extraction --onnx-enabled-for-ee --no-appcompat-clear --mojo-platform-channel-handle=5368 --field-trial-handle=2336,i,4445419202811472793,1872631290632447787,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 812 | powershell.exe -NoProfile -WindowStyle Hidden -Command "Add-MpPreference -ExclusionPath 'C:\Program Files (x86)\00000029.exe'" | C:\Users\admin\Desktop\Files\PowerShell.exe | — | v1saferui.2.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 856 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | file.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 920 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | file.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 968 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | file.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1052 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | file.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1152 | cmstp.exe "C:\Users\admin\AppData\Roaming\Realtek HD Audio Manager\crazy.bin" | C:\Windows\System32\cmstp.exe | — | ConsoleApplication4.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Connection Manager Profile Installer Version: 7.2.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1168 | "C:\Users\admin\Desktop\file.exe" | C:\Users\admin\Desktop\file.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 3221226540 Version: 0.0.0.0 Modules
| |||||||||||||||
Total events
322 380
Read events
319 580
Write events
2 694
Delete events
106
Modification events
| (PID) Process: | (7264) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (7264) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (7264) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (7264) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (7264) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: BDCE7C6909942F00 | |||
| (PID) Process: | (7264) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: DEED896909942F00 | |||
| (PID) Process: | (7264) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\197228 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {3069A266-B135-45E1-A19A-8C7844F618ED} | |||
| (PID) Process: | (7264) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 006ECD6909942F00 | |||
| (PID) Process: | (7264) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\197228 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {F4626954-ECCD-4B8F-9061-AC7D613E6E41} | |||
| (PID) Process: | (7264) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\197228 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {B135ABD3-3F85-45FD-A187-84414C6461A5} | |||
Executable files
823
Suspicious files
302
Text files
228
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7264 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF10bf79.TMP | — | |
MD5:— | SHA256:— | |||
| 7264 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7264 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF10bf89.TMP | — | |
MD5:— | SHA256:— | |||
| 7264 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7264 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF10bfa8.TMP | — | |
MD5:— | SHA256:— | |||
| 7264 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7264 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF10bfd7.TMP | — | |
MD5:— | SHA256:— | |||
| 7264 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7264 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF10bfd7.TMP | — | |
MD5:— | SHA256:— | |||
| 7264 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
381
TCP/UDP connections
2 985
DNS requests
705
Threats
1 513
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
8576 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8576 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7496 | file.exe | GET | 200 | 62.109.140.53:80 | http://stud.clanweb.eu/gym.exe | unknown | — | — | unknown |
6712 | file.exe | GET | 301 | 140.82.121.4:80 | http://github.com/venisz/Roblox-Coding-Tutorial/raw/refs/heads/gang/VClientssss.exe | unknown | — | — | whitelisted |
6752 | file.exe | GET | 200 | 45.192.216.81:80 | http://45.192.216.81/witheFile.exe | unknown | — | — | unknown |
7540 | file.exe | GET | 200 | 163.171.146.42:80 | http://file.elecfans.com/web1/M00/8F/36/o4YBAFy-2m2AARFZAAhkAIik5pI122.exe | unknown | — | — | whitelisted |
5260 | file.exe | GET | 200 | 120.79.26.14:80 | http://dl.dzqzd.com/wj1bsetup.exe | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7264 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7560 | msedge.exe | 38.27.106.109:443 | s3.us-east-1.wasabisys.com | BLUEARCHIVE-ZONE-1 | US | whitelisted |
7560 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7560 | msedge.exe | 150.171.27.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7560 | msedge.exe | 13.107.246.45:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
s3.us-east-1.wasabisys.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
update.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7560 | msedge.exe | Misc activity | ET FILE_SHARING Commonly Abused File Sharing Domain (wasabisys .com) in DNS Lookup |
7560 | msedge.exe | Misc activity | ET FILE_SHARING Commonly Abused File Sharing Domain (wasabisys .com) in DNS Lookup |
7560 | msedge.exe | Misc activity | ET FILE_SHARING Commonly Abused File Sharing Domain (wasabisys .com) in TLS SNI |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
7496 | file.exe | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
6752 | file.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
6752 | file.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
6752 | file.exe | Misc activity | ET INFO EXE IsDebuggerPresent (Used in Malware Anti-Debugging) |
6752 | file.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
6752 | file.exe | Misc activity | ET INFO Packed Executable Download |