| File name: | setup.exe |
| Full analysis: | https://app.any.run/tasks/88c972a3-a1fd-4e45-8c27-2feb553c395d |
| Verdict: | Malicious activity |
| Threats: | Remote access trojans (RATs) are a type of malware that enables attackers to establish complete to partial control over infected computers. Such malicious programs often have a modular design, offering a wide range of functionalities for conducting illicit activities on compromised systems. Some of the most common features of RATs include access to the users’ data, webcam, and keystrokes. This malware is often distributed through phishing emails and links. |
| Analysis date: | November 22, 2020, 17:07:48 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | 420CEED28A549675701F70A143695672 |
| SHA1: | 4D46DDFCEBB3C9B023E86639BD1232CFC5FC93A0 |
| SHA256: | 6F0C437B073DB6FE0676034200C4C1BCA04D8ED72C8041741174584E94A1AA8C |
| SSDEEP: | 196608:Gp9bIlNCgYBw8+ncIMGn8fvJrYJe3C47ce4nm8S33qihRxxfWnTQ2:GgNCgYanzMyQvlpC47N4mxlRxl4TQ2 |
MALICIOUS
Application was dropped or rewritten from another process
- rfusclient.exe (PID: 2764)
- rutserv.exe (PID: 3016)
- rutserv.exe (PID: 672)
- rutserv.exe (PID: 2000)
- rfusclient.exe (PID: 2632)
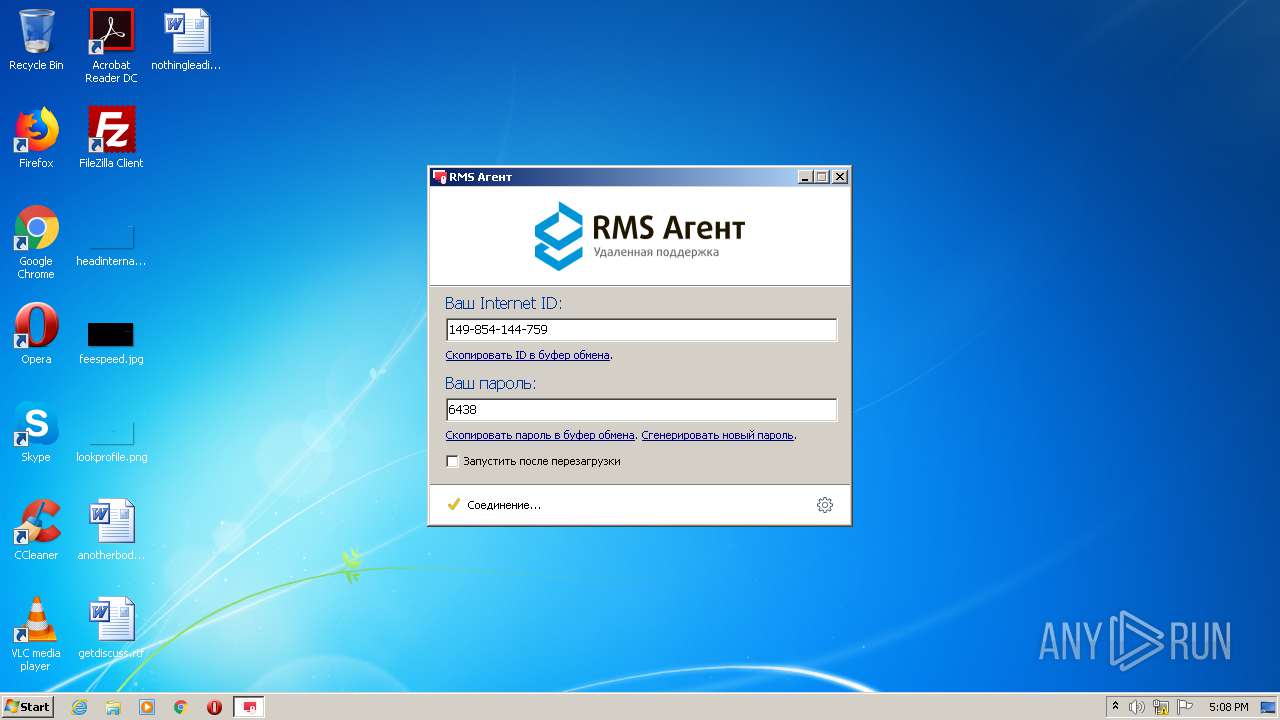
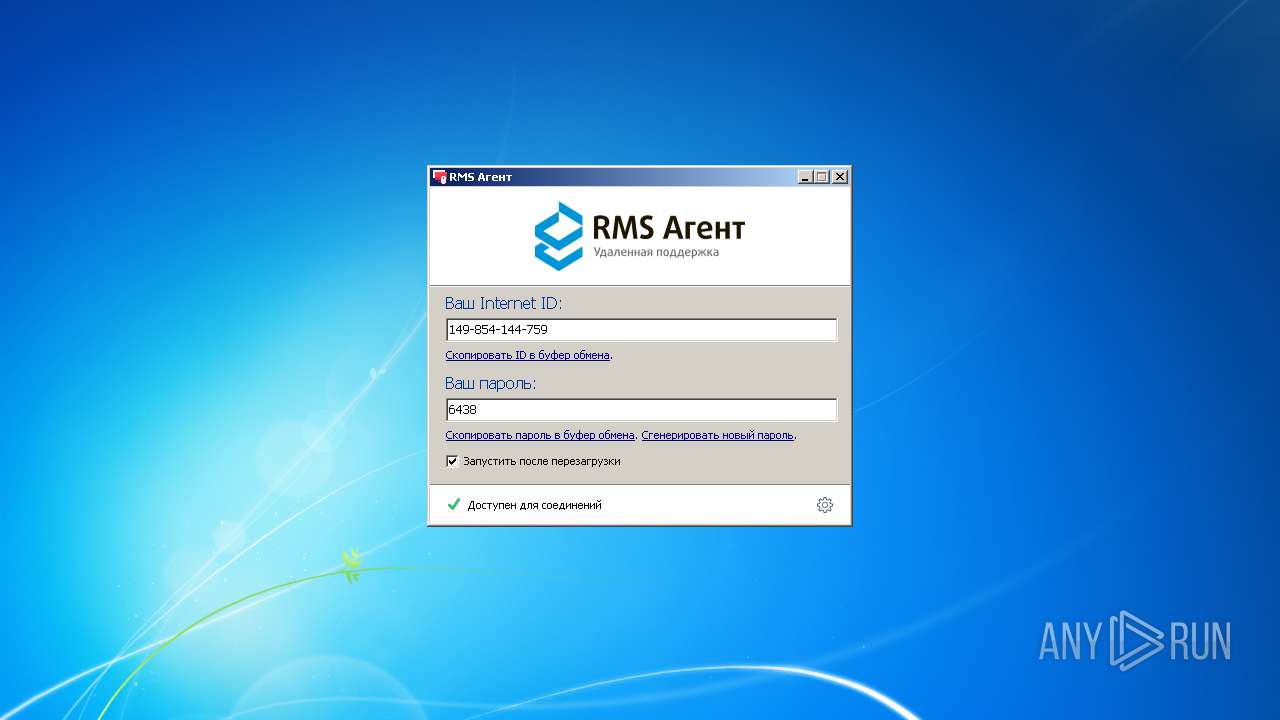
Drop RMS (RAT) executable file
- setup.exe (PID: 2936)
Loads dropped or rewritten executable
- rutserv.exe (PID: 672)
- rutserv.exe (PID: 2000)
Changes the autorun value in the registry
- rutserv.exe (PID: 2000)
RMS was detected
- rutserv.exe (PID: 2000)
SUSPICIOUS
Drops a file that was compiled in debug mode
- setup.exe (PID: 2936)
Reads Environment values
- rfusclient.exe (PID: 2764)
- rutserv.exe (PID: 672)
- rutserv.exe (PID: 2000)
- rfusclient.exe (PID: 2632)
Reads Windows Product ID
- rfusclient.exe (PID: 2764)
- rutserv.exe (PID: 672)
- rutserv.exe (PID: 2000)
- rfusclient.exe (PID: 2632)
Creates files in the user directory
- setup.exe (PID: 2936)
- rutserv.exe (PID: 2000)
Executable content was dropped or overwritten
- setup.exe (PID: 2936)
Removes files from Windows directory
- rutserv.exe (PID: 2000)
Application launched itself
- rutserv.exe (PID: 672)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (71.8) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (11.9) |
| .exe | | | Win16/32 Executable Delphi generic (5.5) |
| .exe | | | Generic Win/DOS Executable (5.3) |
| .exe | | | DOS Executable Generic (5.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:07:03 20:18:03+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 942080 |
| InitializedDataSize: | 10448896 |
| UninitializedDataSize: | 13340672 |
| EntryPoint: | 0xd9f080 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.10.10.0 |
| ProductVersionNumber: | 6.10.10.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | TektonIT |
| FileDescription: | RMS |
| FileVersion: | 6.10.10.0 |
| LegalCopyright: | Copyright © 2019 TektonIT. Ter-Osipov Alex. All rights reserved. |
| ProgramID: | com.remoteutilities.SfxExtractor |
| ProductName: | Remote Manipulator System |
| ProductVersion: | 6.10.10.0 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 03-Jul-2019 18:18:03 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 03-Jul-2019 18:18:03 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
UPX0 | 0x00001000 | 0x00CB9000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
UPX1 | 0x00CBA000 | 0x000E6000 | 0x000E5400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.91663 |
.rsrc | 0x00DA0000 | 0x009F7000 | 0x009F7000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.95495 |
Imports
KERNEL32.DLL |
SHFolder.dll |
advapi32.dll |
comctl32.dll |
gdi32.dll |
msvcrt.dll |
netapi32.dll |
ole32.dll |
oleaut32.dll |
shell32.dll |
Total processes
54
Monitored processes
6
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 672 | "C:\Users\admin\AppData\Roaming\RMS Agent\69110\99E7358134\rutserv.exe" | C:\Users\admin\AppData\Roaming\RMS Agent\69110\99E7358134\rutserv.exe | rfusclient.exe | ||||||||||||
User: admin Company: TektonIT Integrity Level: HIGH Description: RMS Exit code: 0 Version: 6.10.10.0 Modules
| |||||||||||||||
| 2000 | "C:\Users\admin\AppData\Roaming\RMS Agent\69110\99E7358134\rutserv.exe" -second | C:\Users\admin\AppData\Roaming\RMS Agent\69110\99E7358134\rutserv.exe | rutserv.exe | ||||||||||||
User: SYSTEM Company: TektonIT Integrity Level: SYSTEM Description: RMS Exit code: 0 Version: 6.10.10.0 Modules
| |||||||||||||||
| 2632 | "C:\Users\admin\AppData\Roaming\RMS Agent\69110\99E7358134\rfusclient.exe" /tray /user | C:\Users\admin\AppData\Roaming\RMS Agent\69110\99E7358134\rfusclient.exe | — | rutserv.exe | |||||||||||
User: admin Company: TektonIT Integrity Level: MEDIUM Description: RMS Exit code: 0 Version: 6.10.10.0 Modules
| |||||||||||||||
| 2764 | "C:\Users\admin\AppData\Roaming\RMS Agent\69110\99E7358134\rfusclient.exe" -run_agent | C:\Users\admin\AppData\Roaming\RMS Agent\69110\99E7358134\rfusclient.exe | — | setup.exe | |||||||||||
User: admin Company: TektonIT Integrity Level: MEDIUM Description: RMS Exit code: 0 Version: 6.10.10.0 Modules
| |||||||||||||||
| 2936 | "C:\Users\admin\AppData\Local\Temp\setup.exe" | C:\Users\admin\AppData\Local\Temp\setup.exe | explorer.exe | ||||||||||||
User: admin Company: TektonIT Integrity Level: MEDIUM Description: RMS Exit code: 0 Version: 6.10.10.0 Modules
| |||||||||||||||
| 3016 | "C:\Users\admin\AppData\Roaming\RMS Agent\69110\99E7358134\rutserv.exe" | C:\Users\admin\AppData\Roaming\RMS Agent\69110\99E7358134\rutserv.exe | — | rfusclient.exe | |||||||||||
User: admin Company: TektonIT Integrity Level: MEDIUM Description: RMS Exit code: 3221226540 Version: 6.10.10.0 Modules
| |||||||||||||||
Total events
1 059
Read events
1 016
Write events
43
Delete events
0
Modification events
| (PID) Process: | (2936) setup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2936) setup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2764) rfusclient.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2764) rfusclient.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2000) rutserv.exe | Key: | HKEY_USERS\S-1-5-21-1302019708-1500728564-335382590-1000\Software\TektonIT\Remote Manipulator System\Host\Parameters |
| Operation: | write | Name: | General |
Value: EFBBBF3C3F786D6C2076657273696F6E3D22312E302220656E636F64696E673D225554462D38223F3E0D0A3C67656E6572616C5F73657474696E67732076657273696F6E3D223639313130223E3C706F72743E353635303C2F706F72743E3C686964655F747261795F69636F6E5F706F7075705F6D656E753E66616C73653C2F686964655F747261795F69636F6E5F706F7075705F6D656E753E3C747261795F6D656E755F686964655F73746F703E66616C73653C2F747261795F6D656E755F686964655F73746F703E3C6C616E67756167653E5275737369616E3C2F6C616E67756167653E3C63616C6C6261636B5F6175746F5F636F6E6E6563743E747275653C2F63616C6C6261636B5F6175746F5F636F6E6E6563743E3C63616C6C6261636B5F636F6E6E6563745F696E74657276616C3E36303C2F63616C6C6261636B5F636F6E6E6563745F696E74657276616C3E3C70617373776F72645F646174613E364E324F6A7A7778394B553D3C2F70617373776F72645F646174613E3C70726F746563745F63616C6C6261636B5F73657474696E67733E66616C73653C2F70726F746563745F63616C6C6261636B5F73657474696E67733E3C70726F746563745F696E65745F69645F73657474696E67733E66616C73653C2F70726F746563745F696E65745F69645F73657474696E67733E3C7573655F6C65676163795F636170747572653E66616C73653C2F7573655F6C65676163795F636170747572653E3C646F5F6E6F745F636170747572655F7264703E66616C73653C2F646F5F6E6F745F636170747572655F7264703E3C7573655F69705F765F363E747275653C2F7573655F69705F765F363E3C6C6F675F7573653E747275653C2F6C6F675F7573653E3C636861745F636C69656E745F73657474696E67733E3C2F636861745F636C69656E745F73657474696E67733E3C617574685F6B65795F737472696E673E3C2F617574685F6B65795F737472696E673E3C7369645F69643E3C2F7369645F69643E3C6E6F746966795F73686F775F70616E656C3E66616C73653C2F6E6F746966795F73686F775F70616E656C3E3C6E6F746966795F6368616E67655F747261795F69636F6E3E747275653C2F6E6F746966795F6368616E67655F747261795F69636F6E3E3C6E6F746966795F62616C6C6F6E5F68696E743E66616C73653C2F6E6F746966795F62616C6C6F6E5F68696E743E3C6E6F746966795F706C61795F736F756E643E66616C73653C2F6E6F746966795F706C61795F736F756E643E3C6E6F746966795F70616E656C5F783E2D313C2F6E6F746966795F70616E656C5F783E3C6E6F746966795F70616E656C5F793E2D313C2F6E6F746966795F70616E656C5F793E3C70726F78795F73657474696E67733E3737752F5044393462577767646D567963326C76626A30694D5334774969426C626D4E765A476C755A7A3069565652474C546769507A344E436A7877636D39346556397A5A5852306157356E637942325A584A7A61573975505349324F5445784D43492B5048567A5A563977636D39346554356D5957787A5A54777664584E6C5833427962336835506A7877636D3934655639306558426C506A41384C33427962336835583352356347552B504768766333512B5043396F62334E30506A787762334A30506A67774F4441384C334276636E512B5047356C5A575266595856306144356D5957787A5A547776626D566C5A4639686458526F506A787564473173583246316447672B5A6D4673633255384C32353062577866595856306144343864584E6C636D35686257552B5043393163325679626D46745A5434386347467A63336476636D512B5043397759584E7A643239795A4434385A47397459576C75506A77765A47397459576C75506A777663484A7665486C666332563064476C755A334D2B44516F3D3C2F70726F78795F73657474696E67733E3C6164646974696F6E616C3E3C2F6164646974696F6E616C3E3C64697361626C655F696E7465726E65745F69643E66616C73653C2F64697361626C655F696E7465726E65745F69643E3C736166655F6D6F64655F7365743E66616C73653C2F736166655F6D6F64655F7365743E3C73686F775F69645F6E6F74696669636174696F6E3E66616C73653C2F73686F775F69645F6E6F74696669636174696F6E3E3C73686F775F69645F6E6F74696669636174696F6E5F726571756573743E66616C73653C2F73686F775F69645F6E6F74696669636174696F6E5F726571756573743E3C696E746567726174655F6669726577616C6C5F61745F737461727475703E747275653C2F696E746567726174655F6669726577616C6C5F61745F737461727475703E3C2F67656E6572616C5F73657474696E67733E0D0A | |||
| (PID) Process: | (2000) rutserv.exe | Key: | HKEY_USERS\S-1-5-21-1302019708-1500728564-335382590-1000\Software\TektonIT\Remote Manipulator System\Host\Parameters |
| Operation: | write | Name: | Security |
Value: EFBBBF3C3F786D6C2076657273696F6E3D22312E302220656E636F64696E673D225554462D38223F3E0D0A3C73656375726974795F73657474696E67732076657273696F6E3D223639313130223E3C77696E646F77735F73656375726974793E3C2F77696E646F77735F73656375726974793E3C73696E676C655F70617373776F72645F686173683E3C2F73696E676C655F70617373776F72645F686173683E3C6D795F757365725F6163636573735F6C6973743E3C757365725F6163636573735F6C6973742F3E3C2F6D795F757365725F6163636573735F6C6973743E3C69705F66696C7465725F747970653E323C2F69705F66696C7465725F747970653E3C69705F626C61636B5F6C6973743E3C2F69705F626C61636B5F6C6973743E3C69705F77686974655F6C6973743E3C2F69705F77686974655F6C6973743E3C617574685F6B696E643E303C2F617574685F6B696E643E3C6F74705F656E61626C653E66616C73653C2F6F74705F656E61626C653E3C6F74705F707269766174655F6B65793E3C2F6F74705F707269766174655F6B65793E3C6F74705F71725F7365637265743E3C2F6F74705F71725F7365637265743E3C757365725F7065726D697373696F6E735F61736B3E66616C73653C2F757365725F7065726D697373696F6E735F61736B3E3C757365725F7065726D697373696F6E735F696E74657276616C3E31303030303C2F757365725F7065726D697373696F6E735F696E74657276616C3E3C757365725F7065726D697373696F6E735F616C6C6F775F64656661756C743E66616C73653C2F757365725F7065726D697373696F6E735F616C6C6F775F64656661756C743E3C757365725F7065726D697373696F6E735F6F6E6C795F69665F757365725F6C6F676765645F6F6E3E66616C73653C2F757365725F7065726D697373696F6E735F6F6E6C795F69665F757365725F6C6F676765645F6F6E3E3C64697361626C655F72656D6F74655F636F6E74726F6C3E66616C73653C2F64697361626C655F72656D6F74655F636F6E74726F6C3E3C64697361626C655F72656D6F74655F73637265656E3E66616C73653C2F64697361626C655F72656D6F74655F73637265656E3E3C64697361626C655F66696C655F7472616E736665723E66616C73653C2F64697361626C655F66696C655F7472616E736665723E3C64697361626C655F72656469726563743E66616C73653C2F64697361626C655F72656469726563743E3C64697361626C655F74656C6E65743E66616C73653C2F64697361626C655F74656C6E65743E3C64697361626C655F72656D6F74655F657865637574653E66616C73653C2F64697361626C655F72656D6F74655F657865637574653E3C64697361626C655F7461736B5F6D616E616765723E66616C73653C2F64697361626C655F7461736B5F6D616E616765723E3C64697361626C655F73687574646F776E3E66616C73653C2F64697361626C655F73687574646F776E3E3C64697361626C655F72656D6F74655F757067726164653E66616C73653C2F64697361626C655F72656D6F74655F757067726164653E3C64697361626C655F707265766965775F636170747572653E66616C73653C2F64697361626C655F707265766965775F636170747572653E3C64697361626C655F6465766963655F6D616E616765723E66616C73653C2F64697361626C655F6465766963655F6D616E616765723E3C64697361626C655F636861743E66616C73653C2F64697361626C655F636861743E3C64697361626C655F73637265656E5F7265636F72643E66616C73653C2F64697361626C655F73637265656E5F7265636F72643E3C64697361626C655F61765F636170747572653E66616C73653C2F64697361626C655F61765F636170747572653E3C64697361626C655F73656E645F6D6573736167653E66616C73653C2F64697361626C655F73656E645F6D6573736167653E3C64697361626C655F72656769737472793E66616C73653C2F64697361626C655F72656769737472793E3C64697361626C655F61765F636861743E66616C73653C2F64697361626C655F61765F636861743E3C64697361626C655F72656D6F74655F73657474696E67733E66616C73653C2F64697361626C655F72656D6F74655F73657474696E67733E3C64697361626C655F72656D6F74655F7072696E74696E673E66616C73653C2F64697361626C655F72656D6F74655F7072696E74696E673E3C64697361626C655F7264703E66616C73653C2F64697361626C655F7264703E3C637573746F6D5F7365727665725F6C6973743E3737752F5044393462577767646D567963326C76626A30694D5334774969426C626D4E765A476C755A7A3069565652474C546769507A344E436A787A5A584A325A584A6659323975626D566A6446396A623235305A58683049485A6C636E4E7062323439496A59354D544577496A3438636D317A58334E6C636E5A6C636E4D76506A777663325679646D567958324E76626D356C5933526659323975644756346444344E43673D3D3C2F637573746F6D5F7365727665725F6C6973743E3C73656C65637465645F637573746F6D5F7365727665725F69643E3C2F73656C65637465645F637573746F6D5F7365727665725F69643E3C637573746F6D5F7365727665725F6163636573733E3737752F5044393462577767646D567963326C76626A30694D5334774969426C626D4E765A476C755A7A3069565652474C546769507A344E436A787962584E6659574E7349485A6C636E4E7062323439496A59354D544577496A3438636D317A5832466A5A584D76506A786C626D4669624756666157356F5A584A7064443530636E566C5043396C626D4669624756666157356F5A584A70644434384C334A74633139685932772B44516F3D3C2F637573746F6D5F7365727665725F6163636573733E3C2F73656375726974795F73657474696E67733E0D0A | |||
| (PID) Process: | (2000) rutserv.exe | Key: | HKEY_USERS\S-1-5-21-1302019708-1500728564-335382590-1000\Software\TektonIT\Remote Manipulator System\Host\Parameters |
| Operation: | write | Name: | notification |
Value: EFBBBF3C3F786D6C2076657273696F6E3D22312E302220656E636F64696E673D225554462D38223F3E0D0A3C726D735F696E65745F69645F6E6F74696669636174696F6E2076657273696F6E3D223639313130223E3C73657474696E67735F6170706C6965643E66616C73653C2F73657474696E67735F6170706C6965643E3C7573655F69645F73657474696E67733E747275653C2F7573655F69645F73657474696E67733E3C67656E65726174655F6E65775F69643E747275653C2F67656E65726174655F6E65775F69643E3C73656E645F746F5F656D61696C3E66616C73653C2F73656E645F746F5F656D61696C3E3C69643E7B39384232423533452D453643432D343937392D414339342D4245414235364538444234347D3C2F69643E3C67656E65726174655F6E65775F70617373776F72643E66616C73653C2F67656E65726174655F6E65775F70617373776F72643E3C61736B5F6964656E74696669636174696F6E3E66616C73653C2F61736B5F6964656E74696669636174696F6E3E3C73656E743E66616C73653C2F73656E743E3C76657273696F6E3E36393131303C2F76657273696F6E3E3C7075626C69635F6B65795F6D3E3C2F7075626C69635F6B65795F6D3E3C7075626C69635F6B65795F653E3C2F7075626C69635F6B65795F653E3C70617373776F72643E3C2F70617373776F72643E3C696E7465726E65745F69643E3C2F696E7465726E65745F69643E3C646973636C61696D65723E3C2F646973636C61696D65723E3C6F76657277726974655F69645F636F64653E66616C73653C2F6F76657277726974655F69645F636F64653E3C6F76657277726974655F69645F73657474696E67733E66616C73653C2F6F76657277726974655F69645F73657474696E67733E3C69645F637573746F6D5F7365727665725F7573653E66616C73653C2F69645F637573746F6D5F7365727665725F7573653E3C69645F637573746F6D5F7365727665725F616464726573733E3C2F69645F637573746F6D5F7365727665725F616464726573733E3C69645F637573746F6D5F7365727665725F706F72743E353635353C2F69645F637573746F6D5F7365727665725F706F72743E3C69645F637573746F6D5F7365727665725F697076363E66616C73653C2F69645F637573746F6D5F7365727665725F697076363E3C69645F637573746F6D5F7365727665725F7573655F70696E3E66616C73653C2F69645F637573746F6D5F7365727665725F7573655F70696E3E3C69645F637573746F6D5F7365727665725F70696E3E3C2F69645F637573746F6D5F7365727665725F70696E3E3C636F6D70757465725F6E616D653E3C2F636F6D70757465725F6E616D653E3C73656C665F6964656E74696669636174696F6E3E3C2F73656C665F6964656E74696669636174696F6E3E3C736D74705F73657474696E67733E3C686F73743E3C2F686F73743E3C706F72743E3538373C2F706F72743E3C757365726E616D653E3C2F757365726E616D653E3C70617373776F72643E3C2F70617373776F72643E3C66726F6D5F656D61696C3E3C2F66726F6D5F656D61696C3E3C7573655F746C733E747275653C2F7573655F746C733E3C656D61696C3E3C2F656D61696C3E3C7375626A6563743E3C2F7375626A6563743E3C746578743E3C2F746578743E3C2F736D74705F73657474696E67733E3C2F726D735F696E65745F69645F6E6F74696669636174696F6E3E0D0A | |||
| (PID) Process: | (2000) rutserv.exe | Key: | HKEY_USERS\S-1-5-21-1302019708-1500728564-335382590-1000\Software\TektonIT\Remote Manipulator System\Host\Parameters |
| Operation: | write | Name: | FUSClientPath |
Value: C:\Users\admin\AppData\Roaming\RMS Agent\69110\99E7358134\rfusclient.exe | |||
| (PID) Process: | (2000) rutserv.exe | Key: | HKEY_USERS\S-1-5-21-1302019708-1500728564-335382590-1000\Software\TektonIT\Remote Manipulator System\Host\Parameters |
| Operation: | write | Name: | General |
Value: EFBBBF3C3F786D6C2076657273696F6E3D22312E302220656E636F64696E673D225554462D38223F3E0D0A3C67656E6572616C5F73657474696E67732076657273696F6E3D223639313130223E3C706F72743E353635303C2F706F72743E3C686964655F747261795F69636F6E5F706F7075705F6D656E753E66616C73653C2F686964655F747261795F69636F6E5F706F7075705F6D656E753E3C747261795F6D656E755F686964655F73746F703E66616C73653C2F747261795F6D656E755F686964655F73746F703E3C6C616E67756167653E5275737369616E3C2F6C616E67756167653E3C63616C6C6261636B5F6175746F5F636F6E6E6563743E747275653C2F63616C6C6261636B5F6175746F5F636F6E6E6563743E3C63616C6C6261636B5F636F6E6E6563745F696E74657276616C3E36303C2F63616C6C6261636B5F636F6E6E6563745F696E74657276616C3E3C70617373776F72645F646174613E364E324F6A7A7778394B553D3C2F70617373776F72645F646174613E3C70726F746563745F63616C6C6261636B5F73657474696E67733E66616C73653C2F70726F746563745F63616C6C6261636B5F73657474696E67733E3C70726F746563745F696E65745F69645F73657474696E67733E66616C73653C2F70726F746563745F696E65745F69645F73657474696E67733E3C7573655F6C65676163795F636170747572653E66616C73653C2F7573655F6C65676163795F636170747572653E3C646F5F6E6F745F636170747572655F7264703E66616C73653C2F646F5F6E6F745F636170747572655F7264703E3C7573655F69705F765F363E747275653C2F7573655F69705F765F363E3C6C6F675F7573653E747275653C2F6C6F675F7573653E3C636861745F636C69656E745F73657474696E67733E3C2F636861745F636C69656E745F73657474696E67733E3C617574685F6B65795F737472696E673E3C2F617574685F6B65795F737472696E673E3C7369645F69643E34343135372E373134303430353332343C2F7369645F69643E3C6E6F746966795F73686F775F70616E656C3E66616C73653C2F6E6F746966795F73686F775F70616E656C3E3C6E6F746966795F6368616E67655F747261795F69636F6E3E747275653C2F6E6F746966795F6368616E67655F747261795F69636F6E3E3C6E6F746966795F62616C6C6F6E5F68696E743E66616C73653C2F6E6F746966795F62616C6C6F6E5F68696E743E3C6E6F746966795F706C61795F736F756E643E66616C73653C2F6E6F746966795F706C61795F736F756E643E3C6E6F746966795F70616E656C5F783E2D313C2F6E6F746966795F70616E656C5F783E3C6E6F746966795F70616E656C5F793E2D313C2F6E6F746966795F70616E656C5F793E3C70726F78795F73657474696E67733E3737752F5044393462577767646D567963326C76626A30694D5334774969426C626D4E765A476C755A7A3069565652474C546769507A344E436A7877636D39346556397A5A5852306157356E637942325A584A7A61573975505349324F5445784D43492B5048567A5A563977636D39346554356D5957787A5A54777664584E6C5833427962336835506A7877636D3934655639306558426C506A41384C33427962336835583352356347552B504768766333512B5043396F62334E30506A787762334A30506A67774F4441384C334276636E512B5047356C5A575266595856306144356D5957787A5A547776626D566C5A4639686458526F506A787564473173583246316447672B5A6D4673633255384C32353062577866595856306144343864584E6C636D35686257552B5043393163325679626D46745A5434386347467A63336476636D512B5043397759584E7A643239795A4434385A47397459576C75506A77765A47397459576C75506A777663484A7665486C666332563064476C755A334D2B44516F3D3C2F70726F78795F73657474696E67733E3C6164646974696F6E616C3E3C2F6164646974696F6E616C3E3C64697361626C655F696E7465726E65745F69643E66616C73653C2F64697361626C655F696E7465726E65745F69643E3C736166655F6D6F64655F7365743E66616C73653C2F736166655F6D6F64655F7365743E3C73686F775F69645F6E6F74696669636174696F6E3E66616C73653C2F73686F775F69645F6E6F74696669636174696F6E3E3C73686F775F69645F6E6F74696669636174696F6E5F726571756573743E66616C73653C2F73686F775F69645F6E6F74696669636174696F6E5F726571756573743E3C696E746567726174655F6669726577616C6C5F61745F737461727475703E747275653C2F696E746567726174655F6669726577616C6C5F61745F737461727475703E3C2F67656E6572616C5F73657474696E67733E0D0A | |||
| (PID) Process: | (2000) rutserv.exe | Key: | HKEY_USERS\S-1-5-21-1302019708-1500728564-335382590-1000\Software\TektonIT\Remote Manipulator System\Host\Parameters |
| Operation: | write | Name: | InternetId |
Value: EFBBBF3C3F786D6C2076657273696F6E3D22312E302220656E636F64696E673D225554462D38223F3E0D0A3C726D735F696E7465726E65745F69645F73657474696E67732076657273696F6E3D223639313130223E3C696E7465726E65745F69643E3C2F696E7465726E65745F69643E3C7573655F696E65745F636F6E6E656374696F6E3E66616C73653C2F7573655F696E65745F636F6E6E656374696F6E3E3C696E65745F7365727665723E3C2F696E65745F7365727665723E3C7573655F637573746F6D5F696E65745F7365727665723E66616C73653C2F7573655F637573746F6D5F696E65745F7365727665723E3C696E65745F69645F706F72743E353635353C2F696E65745F69645F706F72743E3C7573655F696E65745F69645F697076363E66616C73653C2F7573655F696E65745F69645F697076363E3C696E65745F69645F7573655F70696E3E66616C73653C2F696E65745F69645F7573655F70696E3E3C696E65745F69645F70696E3E3C2F696E65745F69645F70696E3E3C2F726D735F696E7465726E65745F69645F73657474696E67733E0D0A | |||
Executable files
9
Suspicious files
0
Text files
14
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2000 | rutserv.exe | C:\Users\admin\AppData\Roaming\RMS Agent\Logs\rms_log_2020-11.html | html | |
MD5:— | SHA256:— | |||
| 2936 | setup.exe | C:\Users\admin\AppData\Roaming\RMS Agent\69110\99E7358134\settings.dat | text | |
MD5:853D8B59C04648FD3CEF1C5506C30228 | SHA256:9A0939001CCC14B9B0BBADCA5763AA51888A1EA9B04D78BD56852DEFC4C0B597 | |||
| 2936 | setup.exe | C:\Users\admin\AppData\Roaming\RMS Agent\69110\99E7358134\vp8encoder.dll | executable | |
MD5:89770647609AC26C1BBD9CF6ED50954E | SHA256:7B4FC8E104914CDD6A7BF3F05C0D7197CFCD30A741CC0856155F2C74E62005A4 | |||
| 2936 | setup.exe | C:\Users\admin\AppData\Roaming\RMS Agent\69110\99E7358134\rutserv.exe | executable | |
MD5:55D66BD554511F803BEBEAD2BD1BFDE0 | SHA256:DECFE9F582F6EED39ADE6C5770E4146D4BA9B488B146753D7F652815D25379BD | |||
| 2936 | setup.exe | C:\Users\admin\AppData\Roaming\RMS Agent\69110\99E7358134\rfusclient.exe | executable | |
MD5:CD97F125A6462574065FD1E3854F9D7F | SHA256:B46F3AE494D9EFFB0B3CFB4AB6D364ECFF8D65F94090344F6526094D067B5DF2 | |||
| 2936 | setup.exe | C:\Users\admin\AppData\Roaming\RMS Agent\69110\99E7358134\webmvorbisencoder.dll | executable | |
MD5:5308B9945E348FBE3A480BE06885434C | SHA256:9DC30FB2118AAD48F6A5E0A82504F365FE40ABB3134F6CCEEB65859F61AD939A | |||
| 2936 | setup.exe | C:\Users\admin\AppData\Roaming\RMS Agent\69110\99E7358134\Russian.lg | text | |
MD5:55A0B95A1D1B7E309F2C22AF82A07CC0 | SHA256:704A1A83D11C21717C17E6A7EB264D94A98D45A7C1ABA8EBB82FAFC65F4F199D | |||
| 2936 | setup.exe | C:\Users\admin\AppData\Roaming\RMS Agent\69110\99E7358134\webmvorbisdecoder.dll | executable | |
MD5:7A9EEAC3CEAF7F95F44EB5C57B4DB2E3 | SHA256:B497D07ED995B16D1146209158D3B90D85C47A643FBF25A5158B26D75C478C88 | |||
| 2936 | setup.exe | C:\Users\admin\AppData\Roaming\RMS Agent\69110\99E7358134\libeay32.dll | executable | |
MD5:4CB2E1B9294DDAE1BF7DCAAF42B365D1 | SHA256:A8124500CAE0ABA3411428C2C6DF2762EA11CC11C312ABED415D3F3667EB6884 | |||
| 2936 | setup.exe | C:\Users\admin\AppData\Roaming\RMS Agent\69110\99E7358134\vp8decoder.dll | executable | |
MD5:1EA62293AC757A0C2B64E632F30DB636 | SHA256:970CB3E00FA68DAEC266CD0AA6149D3604CB696853772F20AD67555A2114D5DF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
44
DNS requests
1
Threats
33
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2000 | rutserv.exe | 185.175.44.167:5655 | rms-server.tektonit.ru | Storm Systems LLC | RU | malicious |
2000 | rutserv.exe | 185.175.47.32:5655 | — | — | RU | suspicious |
2000 | rutserv.exe | 31.184.215.135:5655 | — | Petersburg Internet Network ltd. | RU | unknown |
— | — | 31.184.215.135:5655 | — | Petersburg Internet Network ltd. | RU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
rms-server.tektonit.ru |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2000 | rutserv.exe | Potential Corporate Privacy Violation | REMOTE [PTsecurity] RMS.Remote Utilities Access Tool |
2000 | rutserv.exe | Potential Corporate Privacy Violation | REMOTE [PTsecurity] RMS.Remote Utilities Access Tool |
2000 | rutserv.exe | Misc activity | REMOTE [PTsecurity] RMS Remote Access Tool (1c-connect) |
2000 | rutserv.exe | Potential Corporate Privacy Violation | REMOTE [PTsecurity] RMS.Remote Utilities Access Tool |
2000 | rutserv.exe | Misc activity | REMOTE [PTsecurity] RMS Remote Access Tool (1c-connect) |
2000 | rutserv.exe | Misc activity | REMOTE [PTsecurity] RMS Remote Access Tool (1c-connect) |
2000 | rutserv.exe | Misc activity | REMOTE [PTsecurity] RMS Remote Access Tool (1c-connect) |
2000 | rutserv.exe | Misc activity | REMOTE [PTsecurity] RMS Remote Access Tool (1c-connect) |
2000 | rutserv.exe | Misc activity | REMOTE [PTsecurity] RMS Remote Access Tool (1c-connect) |
2000 | rutserv.exe | Misc activity | REMOTE [PTsecurity] RMS Remote Access Tool (1c-connect) |
1 ETPRO signatures available at the full report
Process | Message |
|---|---|
rutserv.exe | 22-11-2020_17:08:46:805#T:MSG_KEEP_ALIVE |
rutserv.exe | MSG_KEEP_ALIVE |
rutserv.exe | error:00000000:lib(0):func(0):reason(0) |
rutserv.exe | error:00000000:lib(0):func(0):reason(0) |
rutserv.exe | error:00000000:lib(0):func(0):reason(0) |
rutserv.exe | error:00000000:lib(0):func(0):reason(0) |
rutserv.exe | error:00000000:lib(0):func(0):reason(0) |
rutserv.exe | error:00000000:lib(0):func(0):reason(0) |
rutserv.exe | error:00000000:lib(0):func(0):reason(0) |
rutserv.exe | error:00000000:lib(0):func(0):reason(0) |