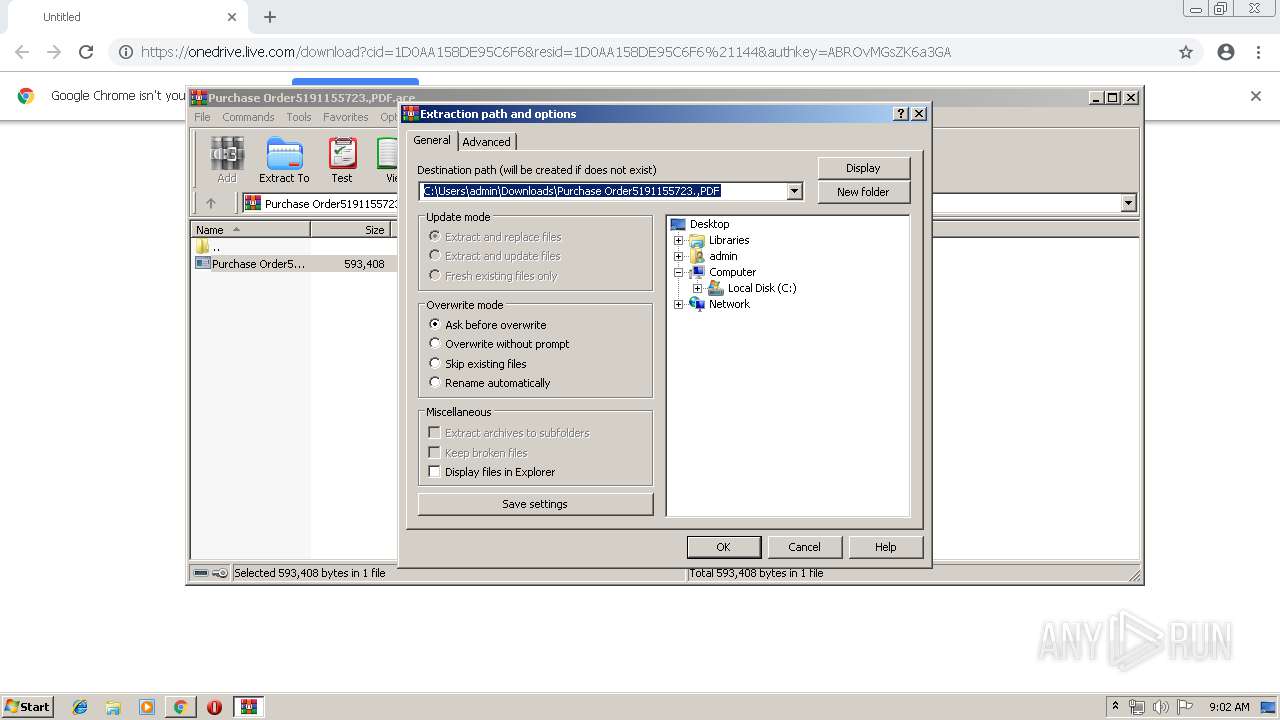
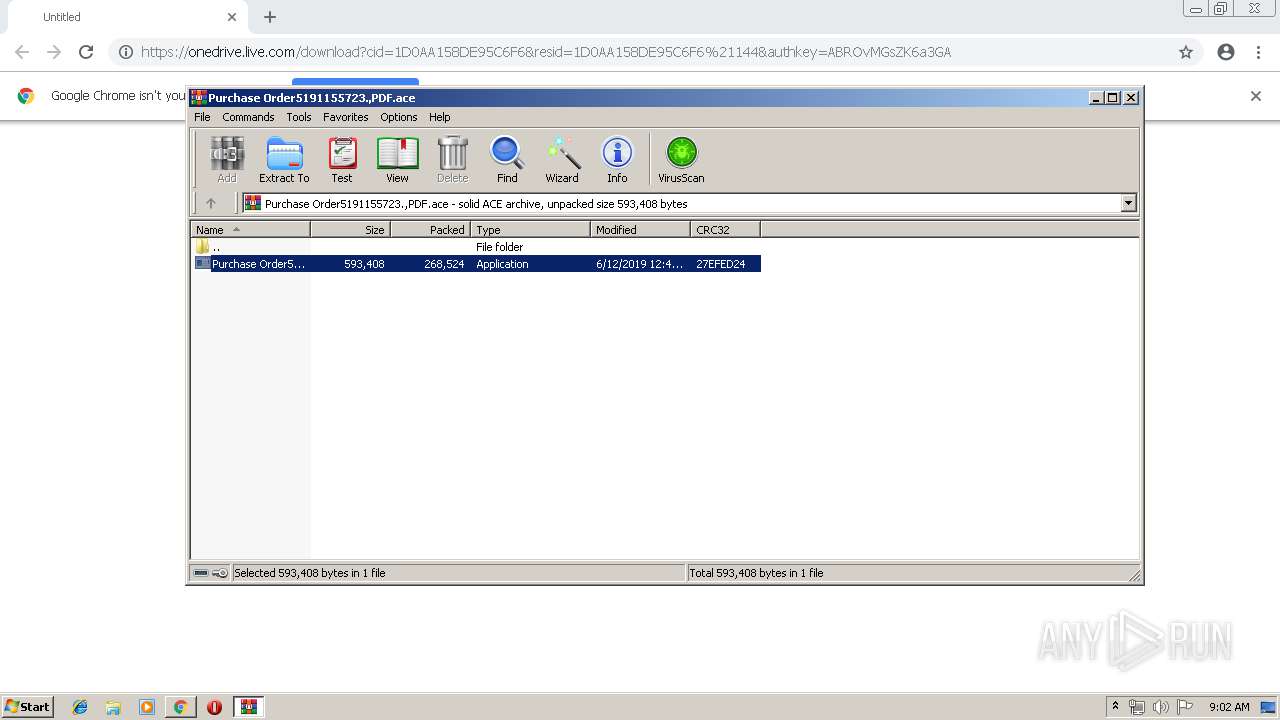
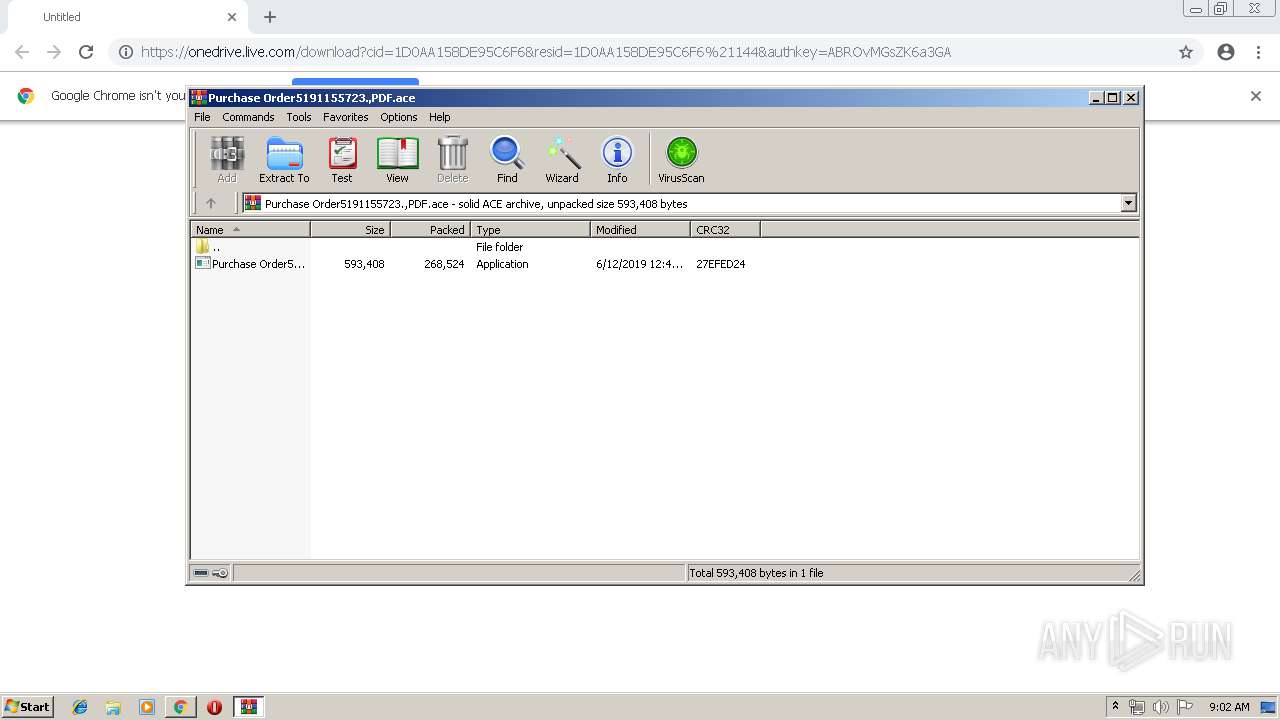
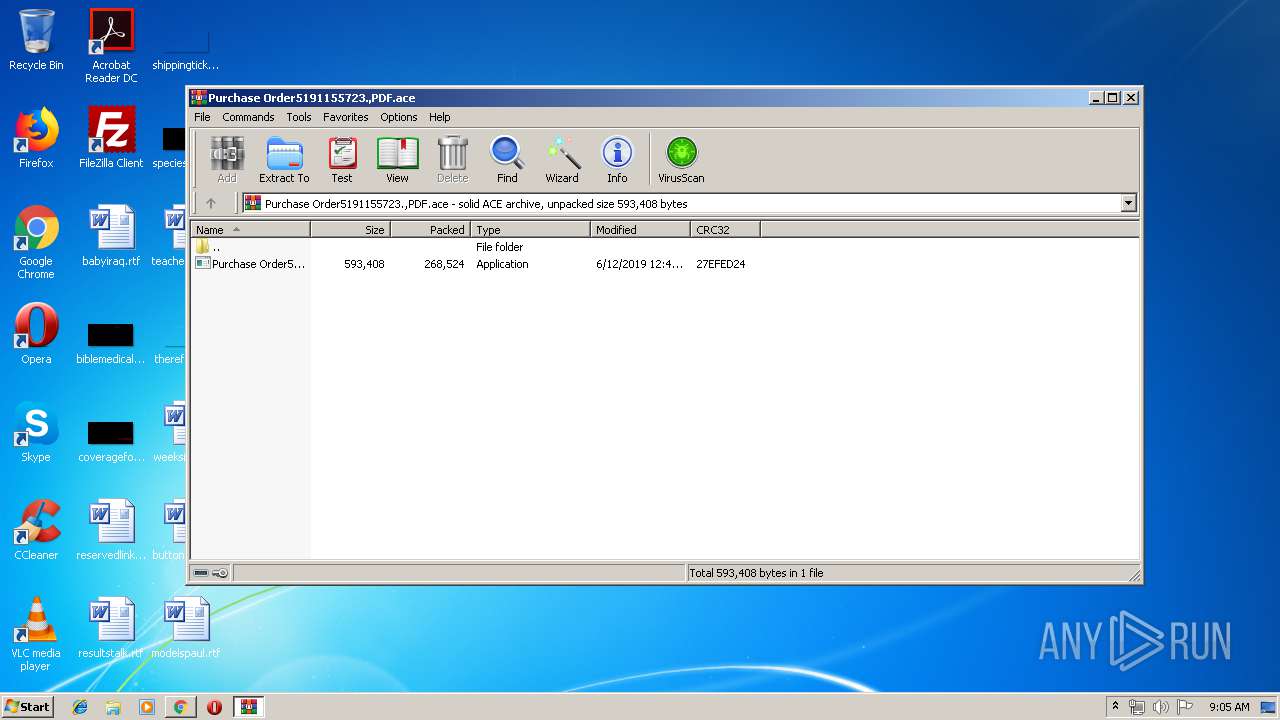
| URL: | https://onedrive.live.com/download?cid=1D0AA158DE95C6F6&resid=1D0AA158DE95C6F6%21144&authkey=ABROvMGsZK6a3GA |
| Full analysis: | https://app.any.run/tasks/d0cfd462-84bd-4bad-b0ad-6fea0609c33f |
| Verdict: | Malicious activity |
| Threats: | LokiBot was developed in 2015 to steal information from a variety of applications. Despite the age, this malware is still rather popular among cybercriminals. |
| Analysis date: | June 12, 2019, 08:01:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 39C7C38DB70023EF549043F97301E680 |
| SHA1: | 50BF16FB64F4A4BE7EC037D84ACCC73B97572DAF |
| SHA256: | 6F0077F4B579286AED30DED5A64A9A2631A001B64F23C6FAD917E3653F3681CD |
| SSDEEP: | 3:N8Ck3CTwKbldmQcw3QLb6Qcw0XUQrOApu3qT/4cfn:2CkST/ZYQcw3Q6QcwbQrvpuar4cf |
MALICIOUS
Application was dropped or rewritten from another process
- Purchase Order5191155723.,PDF.exe (PID: 3928)
- Purchase Order5191155723.,PDF.exe (PID: 3552)
Detected artifacts of LokiBot
- Purchase Order5191155723.,PDF.exe (PID: 3552)
Connects to CnC server
- Purchase Order5191155723.,PDF.exe (PID: 3552)
LOKIBOT was detected
- Purchase Order5191155723.,PDF.exe (PID: 3552)
Actions looks like stealing of personal data
- Purchase Order5191155723.,PDF.exe (PID: 3552)
SUSPICIOUS
Application launched itself
- Purchase Order5191155723.,PDF.exe (PID: 3928)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2148)
- Purchase Order5191155723.,PDF.exe (PID: 3552)
Loads DLL from Mozilla Firefox
- Purchase Order5191155723.,PDF.exe (PID: 3552)
Creates files in the user directory
- Purchase Order5191155723.,PDF.exe (PID: 3552)
Modifies files in Chrome extension folder
- chrome.exe (PID: 2152)
INFO
Application launched itself
- chrome.exe (PID: 2152)
Reads Internet Cache Settings
- chrome.exe (PID: 2152)
Manual execution by user
- Purchase Order5191155723.,PDF.exe (PID: 3928)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
55
Monitored processes
23
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 296 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=2160 --on-initialized-event-handle=308 --parent-handle=312 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 392 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=940,15087736579650055368,10115477344319233266,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=7189794884315377409 --mojo-platform-channel-handle=4488 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 480 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=940,15087736579650055368,10115477344319233266,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=6202926351707066793 --mojo-platform-channel-handle=3960 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 664 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=940,15087736579650055368,10115477344319233266,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=17607243141028480810 --mojo-platform-channel-handle=3212 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 684 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=940,15087736579650055368,10115477344319233266,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=7087917539289166090 --mojo-platform-channel-handle=4336 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 976 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=940,15087736579650055368,10115477344319233266,131072 --enable-features=PasswordImport --service-pipe-token=8159019702037697638 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=8159019702037697638 --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1988 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1476 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=940,15087736579650055368,10115477344319233266,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAACAAwAAAQAAAAAAAAAAAGAAAAAAAAEAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=17886513107392092211 --mojo-platform-channel-handle=964 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2136 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=940,15087736579650055368,10115477344319233266,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=12093861323897650286 --mojo-platform-channel-handle=1876 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2144 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=940,15087736579650055368,10115477344319233266,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=4113210894766238091 --mojo-platform-channel-handle=776 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
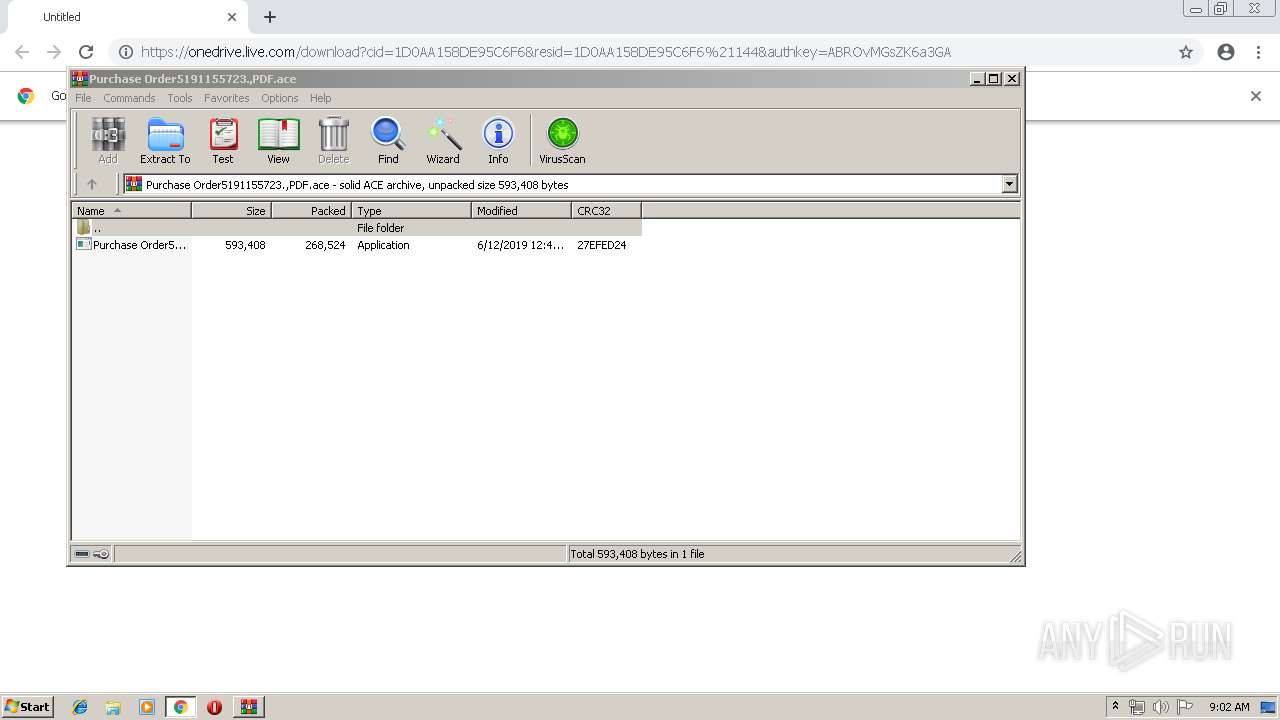
| 2148 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\Purchase Order5191155723.,PDF.ace" | C:\Program Files\WinRAR\WinRAR.exe | chrome.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
1 363
Read events
1 251
Write events
108
Delete events
4
Modification events
| (PID) Process: | (2152) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2152) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2152) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2152) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2152) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (296) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2152-13204800124791000 |
Value: 259 | |||
| (PID) Process: | (2152) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2152) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2152) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3488-13197474229333984 |
Value: 0 | |||
| (PID) Process: | (2152) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 2152-13204800124791000 |
Value: 259 | |||
Executable files
2
Suspicious files
25
Text files
178
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2152 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\index | — | |
MD5:— | SHA256:— | |||
| 2152 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_0 | — | |
MD5:— | SHA256:— | |||
| 2152 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_1 | — | |
MD5:— | SHA256:— | |||
| 2152 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_2 | — | |
MD5:— | SHA256:— | |||
| 2152 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_3 | — | |
MD5:— | SHA256:— | |||
| 2152 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2152 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000018.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2152 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\2b4f5552-61c8-44b5-98be-fbb9bf3f097e.tmp | — | |
MD5:— | SHA256:— | |||
| 2152 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\GPUCache\index | — | |
MD5:— | SHA256:— | |||
| 2152 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\GPUCache\data_0 | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
19
DNS requests
15
Threats
18
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3552 | Purchase Order5191155723.,PDF.exe | POST | — | 216.194.166.32:80 | http://tackleworldmerimbula.com.au/glorious/Panel/five/fre.php | US | — | — | malicious |
3552 | Purchase Order5191155723.,PDF.exe | POST | — | 216.194.166.32:80 | http://tackleworldmerimbula.com.au/glorious/Panel/five/fre.php | US | — | — | malicious |
2152 | chrome.exe | GET | 200 | 173.194.183.200:80 | http://r3---sn-aigl6nl7.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvMjJlQUFXRC12Ny1ldUFnMXF3SDlXZDlFZw/7319.128.0.1_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx?cms_redirect=yes&mip=130.185.144.231&mm=28&mn=sn-aigl6nl7&ms=nvh&mt=1560325482&mv=u&pl=22&shardbypass=yes | US | crx | 842 Kb | whitelisted |
2152 | chrome.exe | GET | 302 | 172.217.16.206:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvMjJlQUFXRC12Ny1ldUFnMXF3SDlXZDlFZw/7319.128.0.1_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 506 b | whitelisted |
3552 | Purchase Order5191155723.,PDF.exe | POST | — | 216.194.166.32:80 | http://tackleworldmerimbula.com.au/glorious/Panel/five/fre.php | US | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2152 | chrome.exe | 172.217.23.141:443 | accounts.google.com | Google Inc. | US | whitelisted |
2152 | chrome.exe | 172.217.23.163:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2152 | chrome.exe | 13.107.42.13:443 | onedrive.live.com | Microsoft Corporation | US | malicious |
2152 | chrome.exe | 13.107.42.12:443 | c8nyzw.bn.files.1drv.com | Microsoft Corporation | US | suspicious |
2152 | chrome.exe | 172.217.21.206:443 | sb-ssl.google.com | Google Inc. | US | whitelisted |
2152 | chrome.exe | 172.217.23.132:443 | www.google.com | Google Inc. | US | whitelisted |
2152 | chrome.exe | 172.217.18.3:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
2152 | chrome.exe | 172.217.22.35:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3552 | Purchase Order5191155723.,PDF.exe | 216.194.166.32:80 | tackleworldmerimbula.com.au | InMotion Hosting, Inc. | US | malicious |
2152 | chrome.exe | 216.58.208.42:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
onedrive.live.com |
| shared |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
c8nyzw.bn.files.1drv.com |
| whitelisted |
sb-ssl.google.com |
| whitelisted |
www.google.com |
| malicious |
ssl.gstatic.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
tackleworldmerimbula.com.au |
| malicious |
safebrowsing.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3552 | Purchase Order5191155723.,PDF.exe | A Network Trojan was detected | ET TROJAN LokiBot User-Agent (Charon/Inferno) |
3552 | Purchase Order5191155723.,PDF.exe | A Network Trojan was detected | ET TROJAN LokiBot Checkin |
3552 | Purchase Order5191155723.,PDF.exe | A Network Trojan was detected | ET TROJAN LokiBot Application/Credential Data Exfiltration Detected M1 |
3552 | Purchase Order5191155723.,PDF.exe | A Network Trojan was detected | ET TROJAN LokiBot Application/Credential Data Exfiltration Detected M2 |
3552 | Purchase Order5191155723.,PDF.exe | A Network Trojan was detected | MALWARE [PTsecurity] Loki Bot Check-in M2 |
3552 | Purchase Order5191155723.,PDF.exe | A Network Trojan was detected | ET TROJAN LokiBot User-Agent (Charon/Inferno) |
3552 | Purchase Order5191155723.,PDF.exe | A Network Trojan was detected | ET TROJAN LokiBot Checkin |
3552 | Purchase Order5191155723.,PDF.exe | A Network Trojan was detected | ET TROJAN LokiBot Application/Credential Data Exfiltration Detected M1 |
3552 | Purchase Order5191155723.,PDF.exe | A Network Trojan was detected | ET TROJAN LokiBot Application/Credential Data Exfiltration Detected M2 |
3552 | Purchase Order5191155723.,PDF.exe | A Network Trojan was detected | MALWARE [PTsecurity] Loki Bot Check-in M2 |
3 ETPRO signatures available at the full report