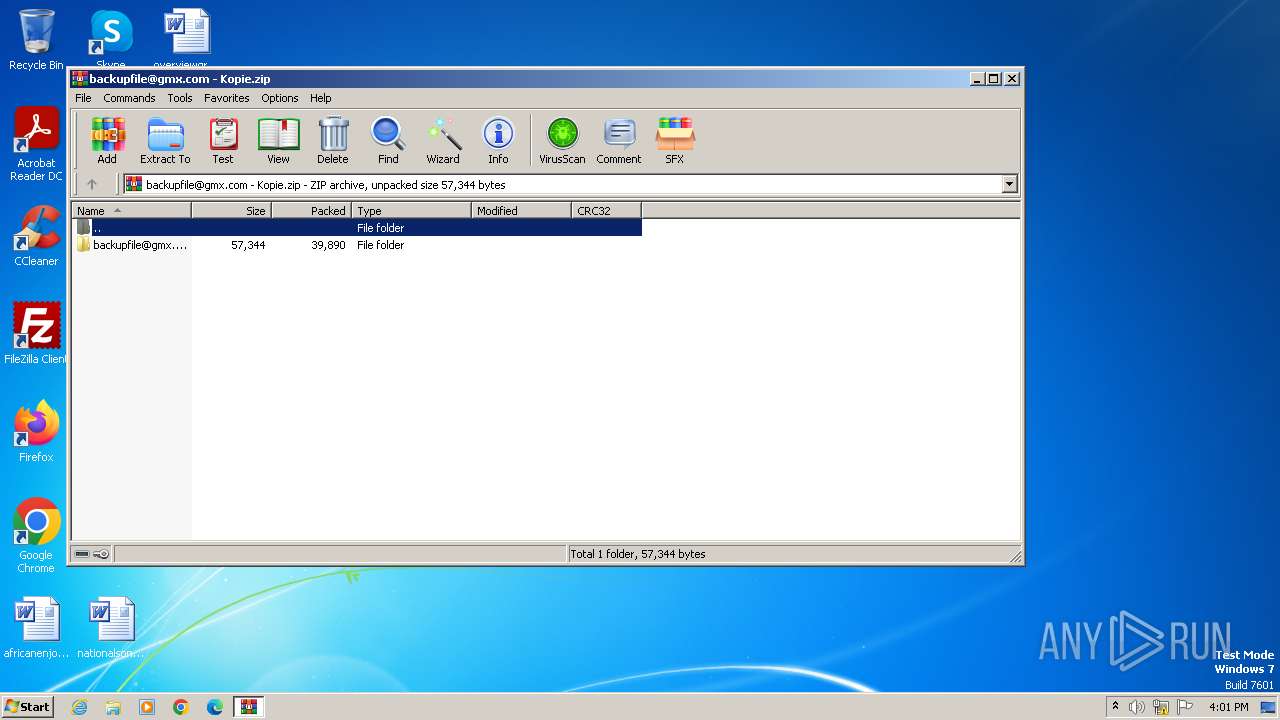
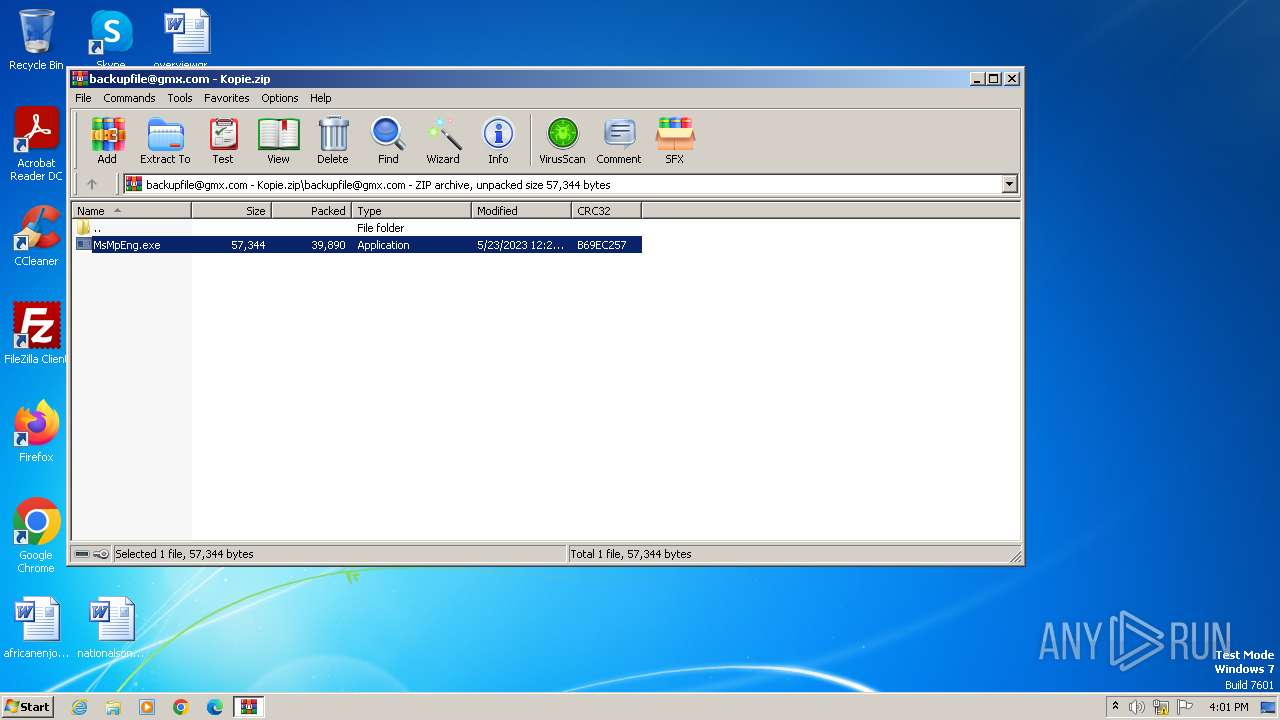
| File name: | backupfile@gmx.com - Kopie.zip |
| Full analysis: | https://app.any.run/tasks/b4fe9488-55c2-4147-a2a1-cfc7e2329b14 |
| Verdict: | Malicious activity |
| Threats: | Phobos is a ransomware that locks or encrypts files to demand a ransom. It uses AES encryption with different extensions, which leaves no chance to recover the infected files. |
| Analysis date: | June 05, 2024, 15:01:06 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | CD5C62E5946CB107B99FAB1A50A98ED2 |
| SHA1: | 4DFA3BC32393982CBB56FF9F02585844849476EA |
| SHA256: | 6EBA1FA4D9DD98407DF5084B0F5B0CD859F854B25948830EFA1CB8153FB4A511 |
| SSDEEP: | 768:Vj0zCt5B/7ETV319NXrAw5nCy313A/05hhme5e8FJnxT673s1lD4hqx5zBVNL7kz:VtzElqwD3ZAyz5e8da8LD4qNL7ODoy |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3972)
- MsMpEng.exe (PID: 752)
Antivirus name has been found in the command line (generic signature)
- MsMpEng.exe (PID: 4012)
- MsMpEng.exe (PID: 4020)
- MsMpEng.exe (PID: 752)
- MsMpEng.exe (PID: 2400)
Deletes shadow copies
- cmd.exe (PID: 112)
Create files in the Startup directory
- MsMpEng.exe (PID: 752)
Changes the autorun value in the registry
- MsMpEng.exe (PID: 752)
- MsMpEng.exe (PID: 4012)
PHOBOS has been detected
- MsMpEng.exe (PID: 752)
Using BCDEDIT.EXE to modify recovery options
- cmd.exe (PID: 112)
Renames files like ransomware
- MsMpEng.exe (PID: 752)
Actions looks like stealing of personal data
- MsMpEng.exe (PID: 752)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3972)
- MsMpEng.exe (PID: 4020)
Application launched itself
- MsMpEng.exe (PID: 4012)
- MsMpEng.exe (PID: 4020)
Reads the Internet Settings
- MsMpEng.exe (PID: 4020)
- WMIC.exe (PID: 2256)
Starts CMD.EXE for commands execution
- MsMpEng.exe (PID: 752)
Creates file in the systems drive root
- MsMpEng.exe (PID: 752)
Uses NETSH.EXE to change the status of the firewall
- cmd.exe (PID: 2032)
Reads browser cookies
- MsMpEng.exe (PID: 752)
Executes as Windows Service
- wbengine.exe (PID: 2452)
- vds.exe (PID: 2476)
- VSSVC.exe (PID: 312)
The process creates files with name similar to system file names
- MsMpEng.exe (PID: 752)
Executable content was dropped or overwritten
- MsMpEng.exe (PID: 752)
Process drops legitimate windows executable
- MsMpEng.exe (PID: 752)
Node.exe was dropped
- MsMpEng.exe (PID: 752)
INFO
Checks supported languages
- MsMpEng.exe (PID: 4012)
- MsMpEng.exe (PID: 4020)
- MsMpEng.exe (PID: 752)
- MsMpEng.exe (PID: 2400)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3972)
Reads the computer name
- MsMpEng.exe (PID: 4020)
- MsMpEng.exe (PID: 752)
- MsMpEng.exe (PID: 4012)
Creates files or folders in the user directory
- MsMpEng.exe (PID: 752)
Creates files in the program directory
- MsMpEng.exe (PID: 752)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:05:23 12:26:46 |
| ZipCRC: | 0xb69ec257 |
| ZipCompressedSize: | 39890 |
| ZipUncompressedSize: | 57344 |
| ZipFileName: | backupfile@gmx.com/MsMpEng.exe |
Total processes
57
Monitored processes
18
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 112 | "C:\Windows\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | MsMpEng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 188 | bcdedit /set {default} bootstatuspolicy ignoreallfailures | C:\Windows\System32\bcdedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Configuration Data Editor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 312 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 752 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3972.48974\backupfile@gmx.com\MsMpEng.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3972.48974\backupfile@gmx.com\MsMpEng.exe | MsMpEng.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 1332 | C:\Windows\System32\vdsldr.exe -Embedding | C:\Windows\System32\vdsldr.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Virtual Disk Service Loader Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1588 | netsh firewall set opmode mode=disable | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1764 | vssadmin delete shadows /all /quiet | C:\Windows\System32\vssadmin.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Command Line Interface for Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2032 | "C:\Windows\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | MsMpEng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2256 | wmic shadowcopy delete | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2316 | netsh advfirewall set currentprofile state off | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
8 312
Read events
8 171
Write events
141
Delete events
0
Modification events
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\backupfile@gmx.com - Kopie.zip | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
254
Suspicious files
6 517
Text files
9
Unknown types
21
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 752 | MsMpEng.exe | C:\MSOCache\All Users\{90140000-0015-0407-0000-0000000FF1CE}-C\AccLR.cab.id[C4BA3647-3429].[backupfile@gmx.com].faust | — | |
MD5:— | SHA256:— | |||
| 752 | MsMpEng.exe | C:\MSOCache\All Users\{90140000-0015-040C-0000-0000000FF1CE}-C\AccLR.cab.id[C4BA3647-3429].[backupfile@gmx.com].faust | — | |
MD5:— | SHA256:— | |||
| 752 | MsMpEng.exe | C:\MSOCache\All Users\{90140000-0015-0410-0000-0000000FF1CE}-C\AccLR.cab.id[C4BA3647-3429].[backupfile@gmx.com].faust | — | |
MD5:— | SHA256:— | |||
| 752 | MsMpEng.exe | C:\programdata\microsoft\windows\start menu\programs\startup\MsMpEng.exe | executable | |
MD5:47E35509151B6F873E0D2850F80FB6C5 | SHA256:BDC0B4ED743F44CEE4F75E97E413EC9ECEC851DD5E62F756AACA46AB77D5D05D | |||
| 752 | MsMpEng.exe | C:\MSOCache\All Users\{90140000-0015-0407-0000-0000000FF1CE}-C\AccessMUI.msi.id[C4BA3647-3429].[backupfile@gmx.com].faust | executable | |
MD5:B68BD80A5A3B703BABC7FB19BAF104AB | SHA256:1CB1E08D560E9E6C62A7E48680A218D022F0D331EB52F3CE66504A167FAD652F | |||
| 752 | MsMpEng.exe | C:\users\admin\appdata\roaming\microsoft\windows\start menu\programs\startup\MsMpEng.exe | executable | |
MD5:47E35509151B6F873E0D2850F80FB6C5 | SHA256:BDC0B4ED743F44CEE4F75E97E413EC9ECEC851DD5E62F756AACA46AB77D5D05D | |||
| 752 | MsMpEng.exe | C:\MSOCache\All Users\{90140000-0015-0411-0000-0000000FF1CE}-C\AccLR.cab.id[C4BA3647-3429].[backupfile@gmx.com].faust | — | |
MD5:— | SHA256:— | |||
| 3972 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3972.48974\backupfile@gmx.com\MsMpEng.exe | executable | |
MD5:47E35509151B6F873E0D2850F80FB6C5 | SHA256:BDC0B4ED743F44CEE4F75E97E413EC9ECEC851DD5E62F756AACA46AB77D5D05D | |||
| 752 | MsMpEng.exe | C:\MSOCache\All Users\{90140000-0015-040C-0000-0000000FF1CE}-C\AccessMUI.msi.id[C4BA3647-3429].[backupfile@gmx.com].faust | executable | |
MD5:859AB199A959FB1487CB2B59885E4DA6 | SHA256:41817D9973027BA79057E641930B28A6C62408CB61599F5212A5690350681101 | |||
| 752 | MsMpEng.exe | C:\MSOCache\All Users\{90140000-0015-0407-0000-0000000FF1CE}-C\AccessMUI.xml.id[C4BA3647-3429].[backupfile@gmx.com].faust | binary | |
MD5:D637A45C30DDF156C66DB846621CBFBB | SHA256:2FD8CC263F8E79DD218170BDF00FBBAE4FB4A4F7BA013F43EA614E42F65F856B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |