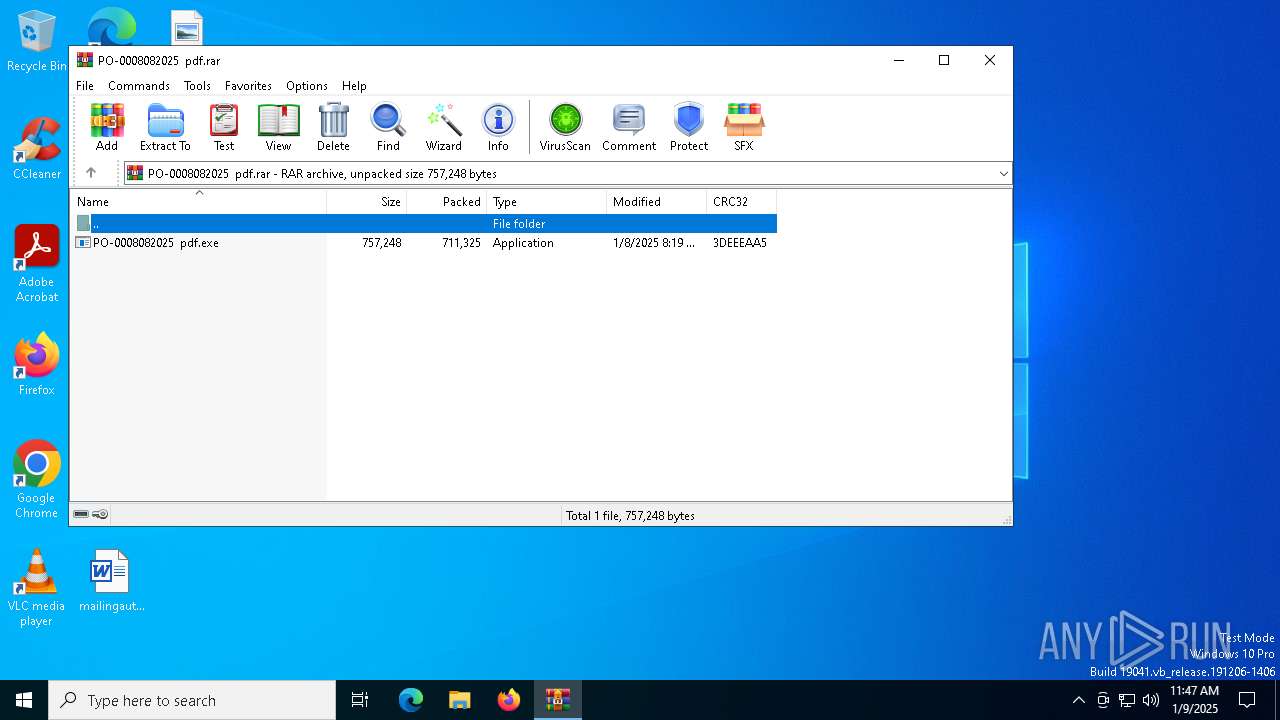
| File name: | PO-0008082025 pdf.rar |
| Full analysis: | https://app.any.run/tasks/7d5a873e-323f-441c-9220-344e54f1fc4b |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | January 09, 2025, 11:47:33 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | AA59FE1912ADB5FE4630A324AC51787E |
| SHA1: | 65900379CA9218595B0B5E8BAE347D3FCD6C42C4 |
| SHA256: | 6DDA666D011A18B9123D2872183D11F793CB31ECC3A5C38D636BB5D6BF2A89C0 |
| SSDEEP: | 24576:z48FUiSGQ2fMdpqeERIQrHeClU1zbDYTo8bEhzSA0xL7nt7THVG3PlqgfViHHk:z48FRSGQ2fMdpqeERIQrHeClU1zbDYTW |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6248)
FORMBOOK has been detected (YARA)
- cttune.exe (PID: 2456)
Connects to the CnC server
- WinRAR.exe (PID: 6248)
Actions looks like stealing of personal data
- cttune.exe (PID: 2456)
FORMBOOK has been detected (SURICATA)
- WinRAR.exe (PID: 6248)
SUSPICIOUS
Starts a Microsoft application from unusual location
- PO-0008082025 pdf.exe (PID: 6440)
- PO-0008082025 pdf.exe (PID: 6848)
- PO-0008082025 pdf.exe (PID: 6856)
- PO-0008082025 pdf.exe (PID: 6868)
Reads security settings of Internet Explorer
- PO-0008082025 pdf.exe (PID: 6440)
Application launched itself
- PO-0008082025 pdf.exe (PID: 6440)
Process drops legitimate windows executable
- WinRAR.exe (PID: 6248)
INFO
Reads the machine GUID from the registry
- PO-0008082025 pdf.exe (PID: 6440)
Reads the computer name
- PO-0008082025 pdf.exe (PID: 6440)
Checks supported languages
- PO-0008082025 pdf.exe (PID: 6440)
- PO-0008082025 pdf.exe (PID: 6868)
Manual execution by a user
- PO-0008082025 pdf.exe (PID: 6440)
The process uses the downloaded file
- PO-0008082025 pdf.exe (PID: 6440)
Reads security settings of Internet Explorer
- cttune.exe (PID: 2456)
Create files in a temporary directory
- cttune.exe (PID: 2456)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 711325 |
| UncompressedSize: | 757248 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | PO-0008082025 pdf.exe |
Total processes
132
Monitored processes
8
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2456 | "C:\Windows\SysWOW64\cttune.exe" | C:\Windows\SysWOW64\cttune.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: ClearType Tuner Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3436 | "C:\Program Files\Mozilla Firefox\Firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | cttune.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 6248 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\PO-0008082025 pdf.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6440 | "C:\Users\admin\Desktop\PO-0008082025 pdf.exe" | C:\Users\admin\Desktop\PO-0008082025 pdf.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: RDP Session Agent Exit code: 0 Version: 1.0.1.0 Modules
| |||||||||||||||
| 6848 | "C:\Users\admin\Desktop\PO-0008082025 pdf.exe" | C:\Users\admin\Desktop\PO-0008082025 pdf.exe | — | PO-0008082025 pdf.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: RDP Session Agent Exit code: 4294967295 Version: 1.0.1.0 Modules
| |||||||||||||||
| 6856 | "C:\Users\admin\Desktop\PO-0008082025 pdf.exe" | C:\Users\admin\Desktop\PO-0008082025 pdf.exe | — | PO-0008082025 pdf.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: RDP Session Agent Exit code: 4294967295 Version: 1.0.1.0 Modules
| |||||||||||||||
| 6868 | "C:\Users\admin\Desktop\PO-0008082025 pdf.exe" | C:\Users\admin\Desktop\PO-0008082025 pdf.exe | — | PO-0008082025 pdf.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: RDP Session Agent Exit code: 0 Version: 1.0.1.0 Modules
| |||||||||||||||
Total events
6 249
Read events
6 231
Write events
18
Delete events
0
Modification events
| (PID) Process: | (6248) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6248) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6248) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6248) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\PO-0008082025 pdf.rar | |||
| (PID) Process: | (6248) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6248) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6248) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6248) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2456) cttune.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2456) cttune.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
Executable files
0
Suspicious files
2
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2456 | cttune.exe | C:\Users\admin\AppData\Local\Temp\--cG1-69- | binary | |
MD5:A45465CDCDC6CB30C8906F3DA4EC114C | SHA256:4412319EF944EBCCA9581CBACB1D4E1DC614C348D1DFC5D2FAAAAD863D300209 | |||
| 6248 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\rebuilt.PO-0008082025 pdf.rar | compressed | |
MD5:46BEC3547F865E54AAFA69A6C6158112 | SHA256:D3DB000FAD247AAD7FD022851F193A91D426450C54FF56938E016EDFC840DDEA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
39
DNS requests
24
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7000 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.147:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7000 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6248 | WinRAR.exe | GET | 404 | 85.159.66.93:80 | http://www.tabyscooterrentals.xyz/4wxo/?7CI=fqDKo1rWIlLUmv&uAjR=AuCk/wTI7zW3ld/vn1qiB/S7AJshg/F9prPfFK+Yc5xTqeXBXJi84rnX4QtnNLSqr4pLPSODfOM24Q7oPb8nqMZX+jkeihJfrBa+8WaX/07QX/ShnQe0XYYOLilfT5ySZTdLvHk= | unknown | — | — | unknown |
4504 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6248 | WinRAR.exe | POST | 200 | 194.9.94.86:80 | http://www.milp.store/2j93/ | unknown | — | — | malicious |
6248 | WinRAR.exe | POST | 200 | 194.9.94.86:80 | http://www.milp.store/2j93/ | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3220 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.147:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 40.126.32.72:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5064 | SearchApp.exe | 104.126.37.139:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6248 | WinRAR.exe | A Network Trojan was detected | STEALER [ANY.RUN] Formbook HTTP Header |
1 ETPRO signatures available at the full report