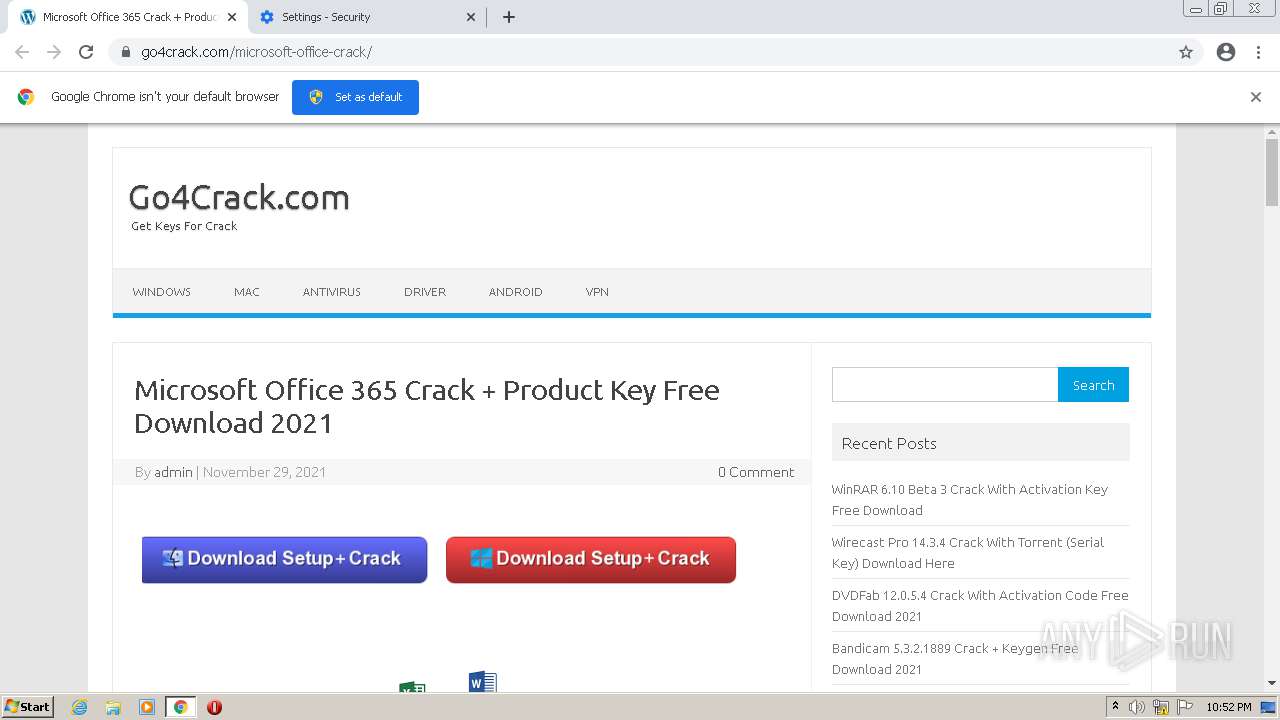
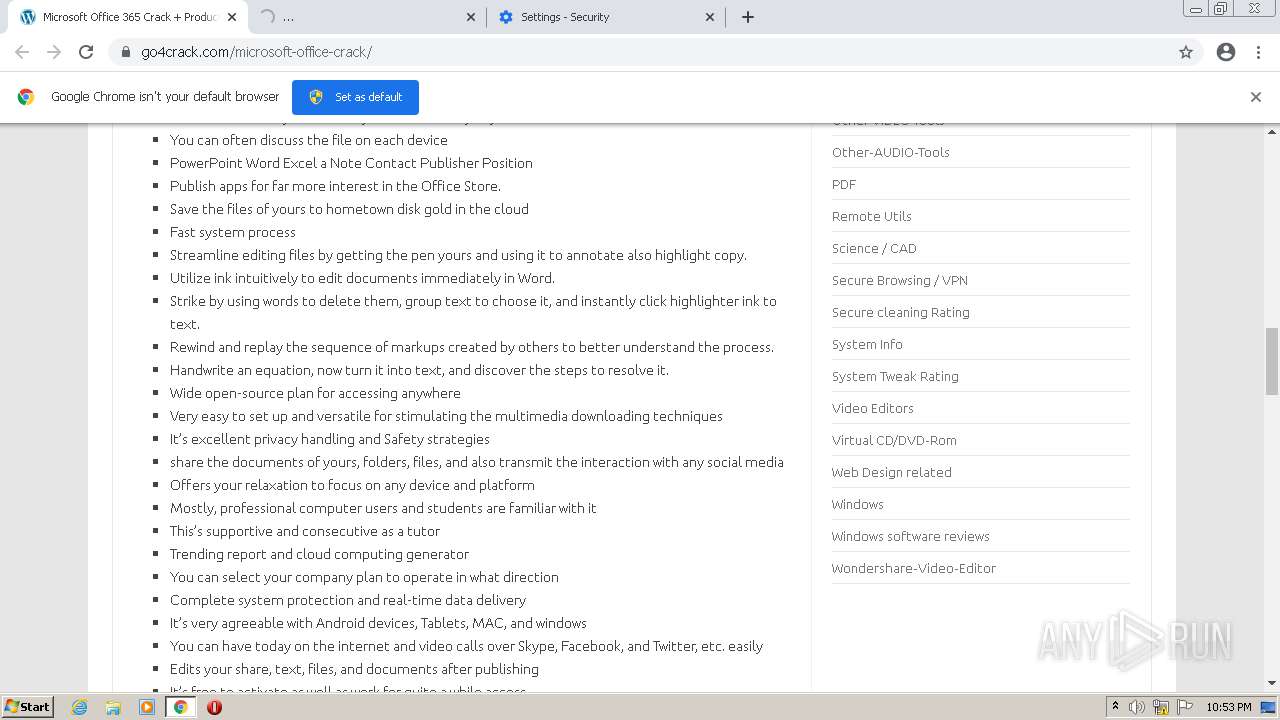
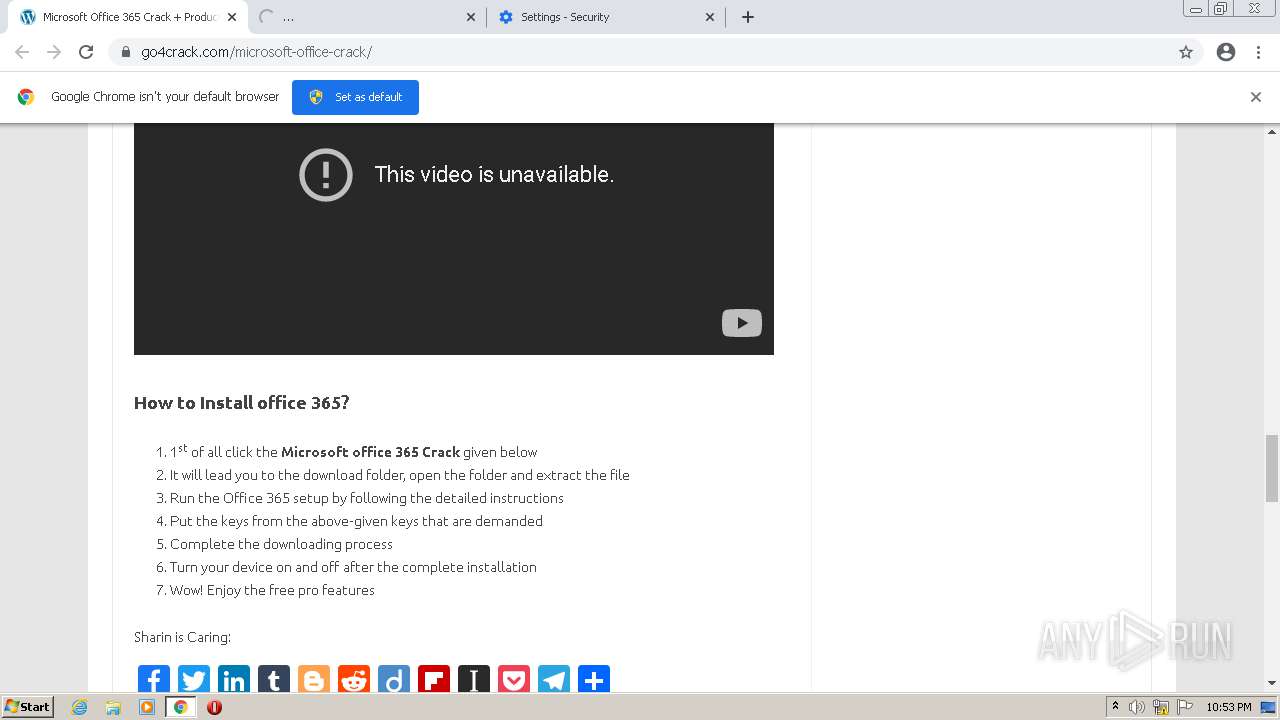
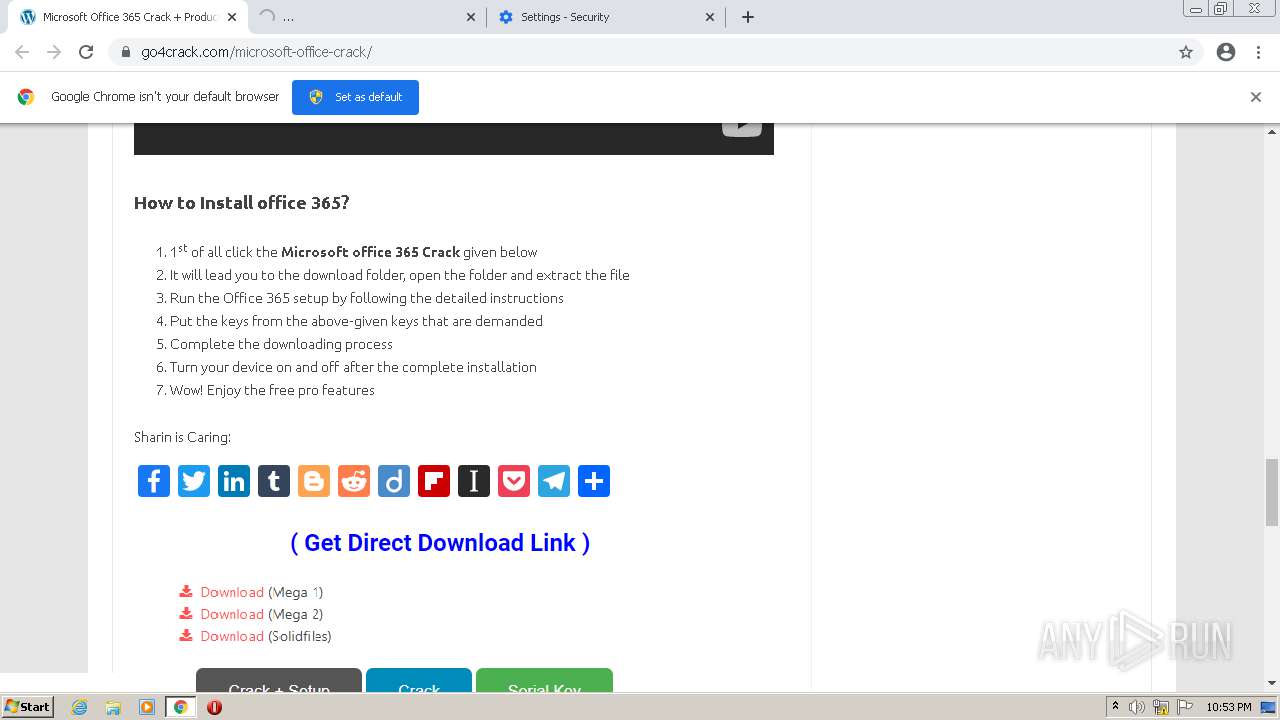
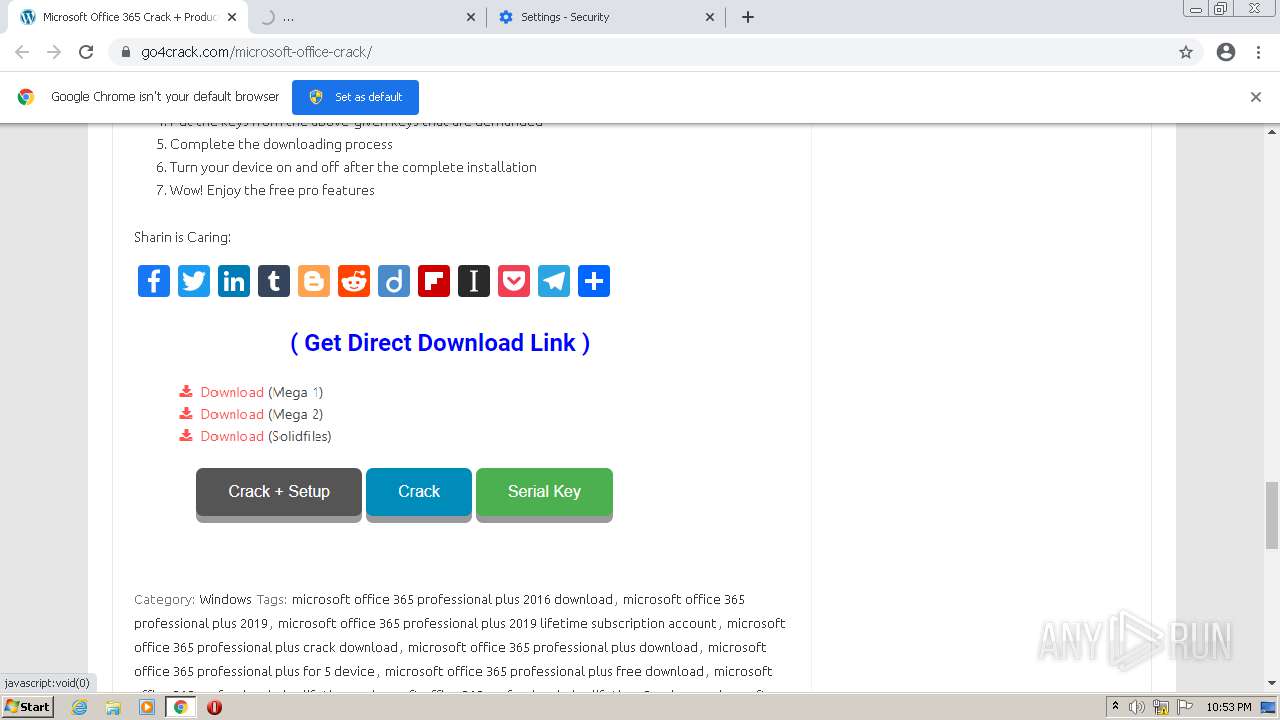
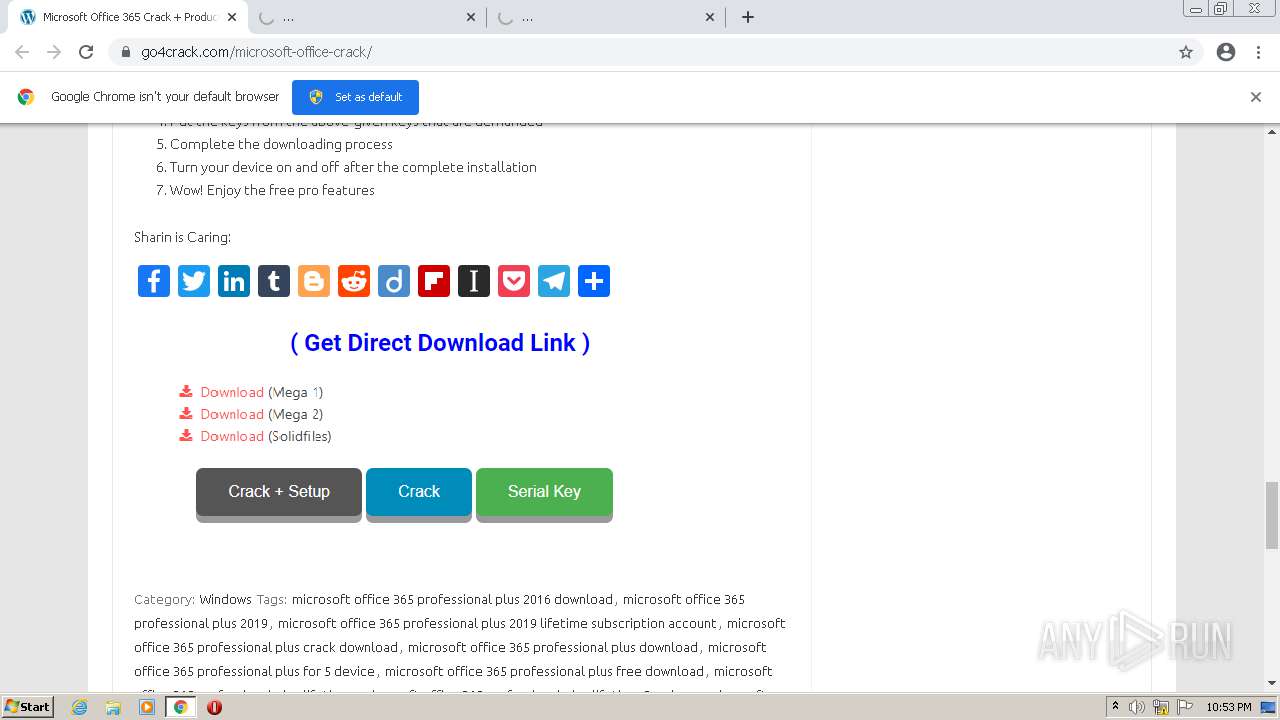
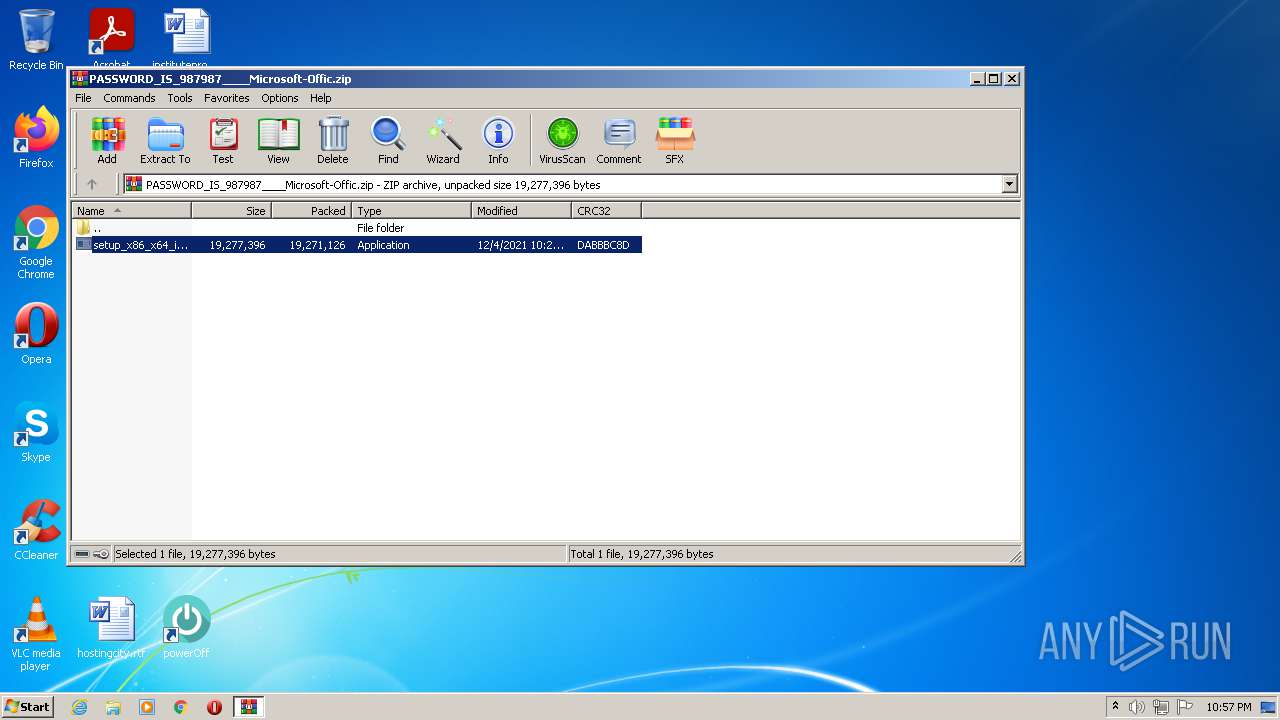
| URL: | https://go4crack.com/microsoft-office-crack/ |
| Full analysis: | https://app.any.run/tasks/515af017-6356-4d02-a13e-510a33f51e54 |
| Verdict: | Malicious activity |
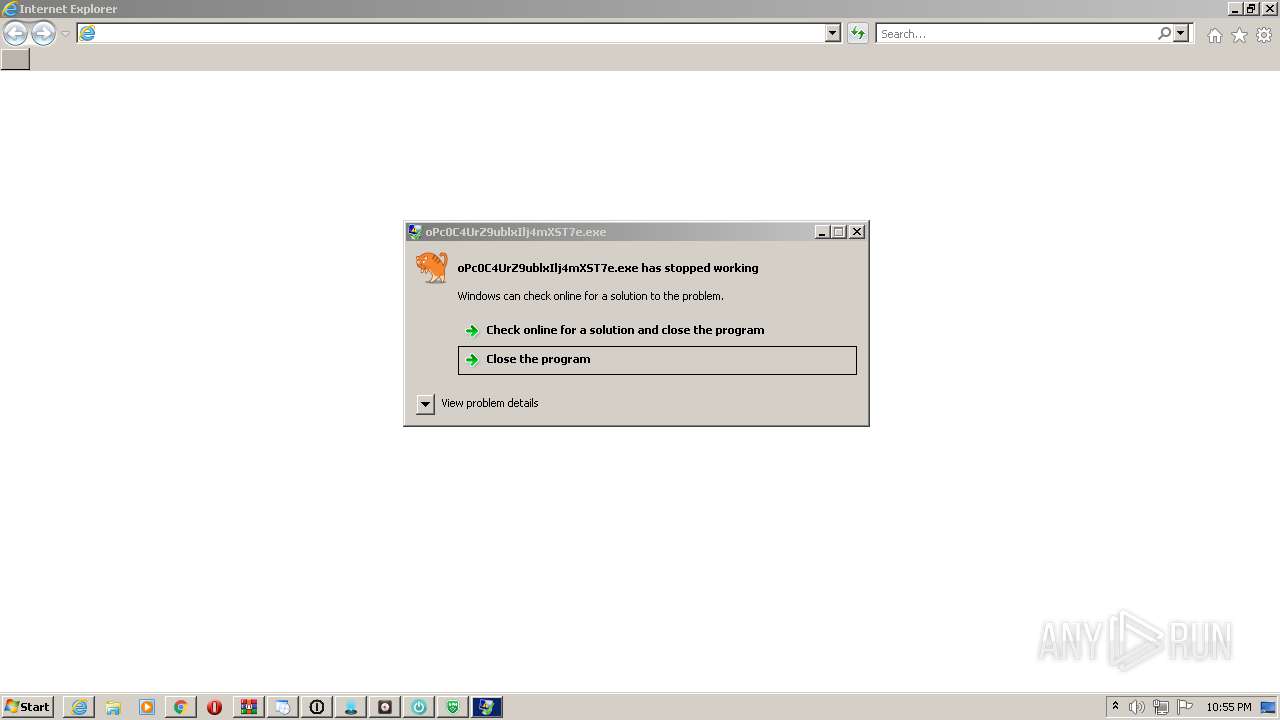
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | December 04, 2021, 22:52:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 069D92E93E77E904B4E69B3568ED1E62 |
| SHA1: | 8F16D62FE7603C3A344A0F4DBB0678F8C98DAB82 |
| SHA256: | 6DCAF38196BFF87B38EB219BE0F490C9E4143C31337C706B7563C9621FC38EF3 |
| SSDEEP: | 3:N8rSHTeWYuuH0XvOK:2GzeRuuH0XWK |
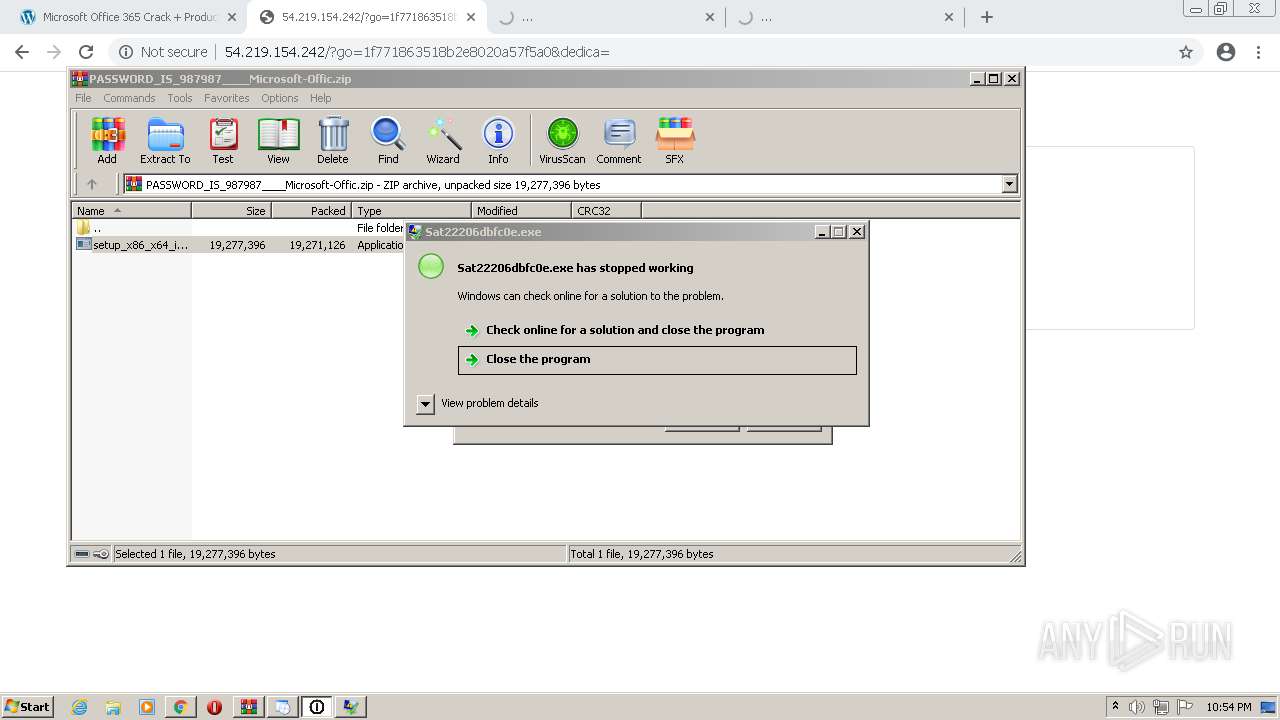
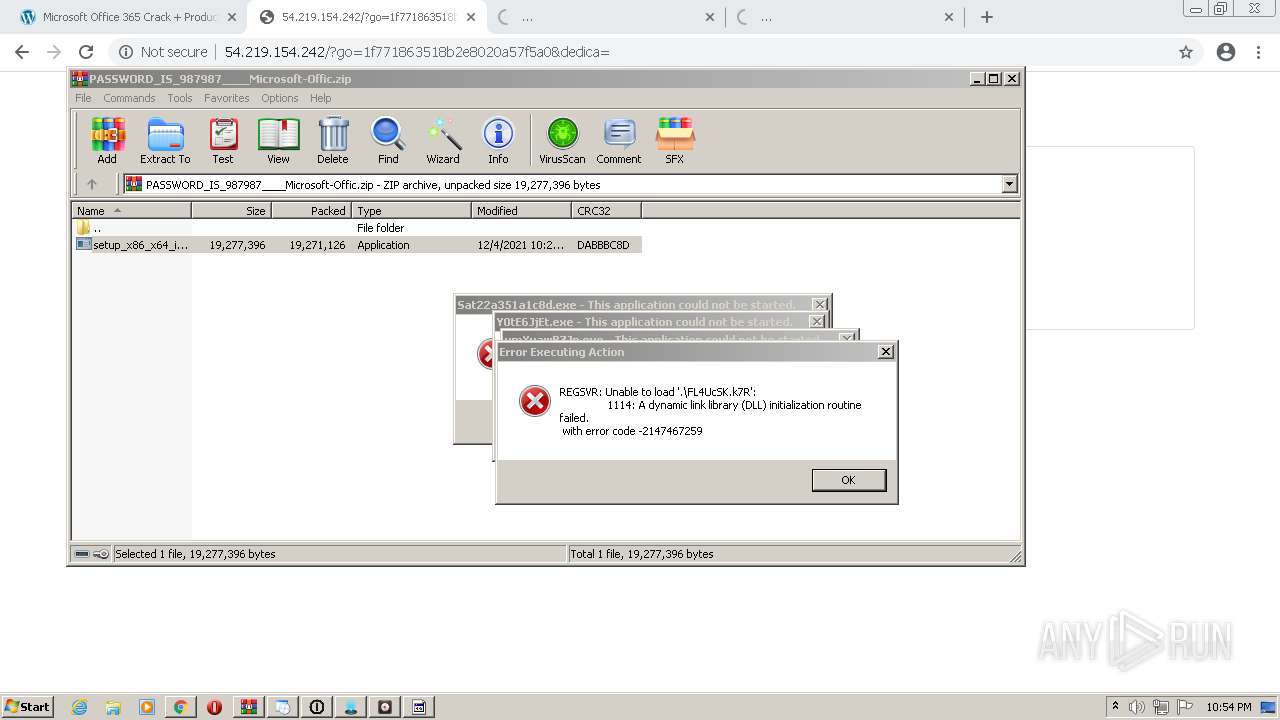
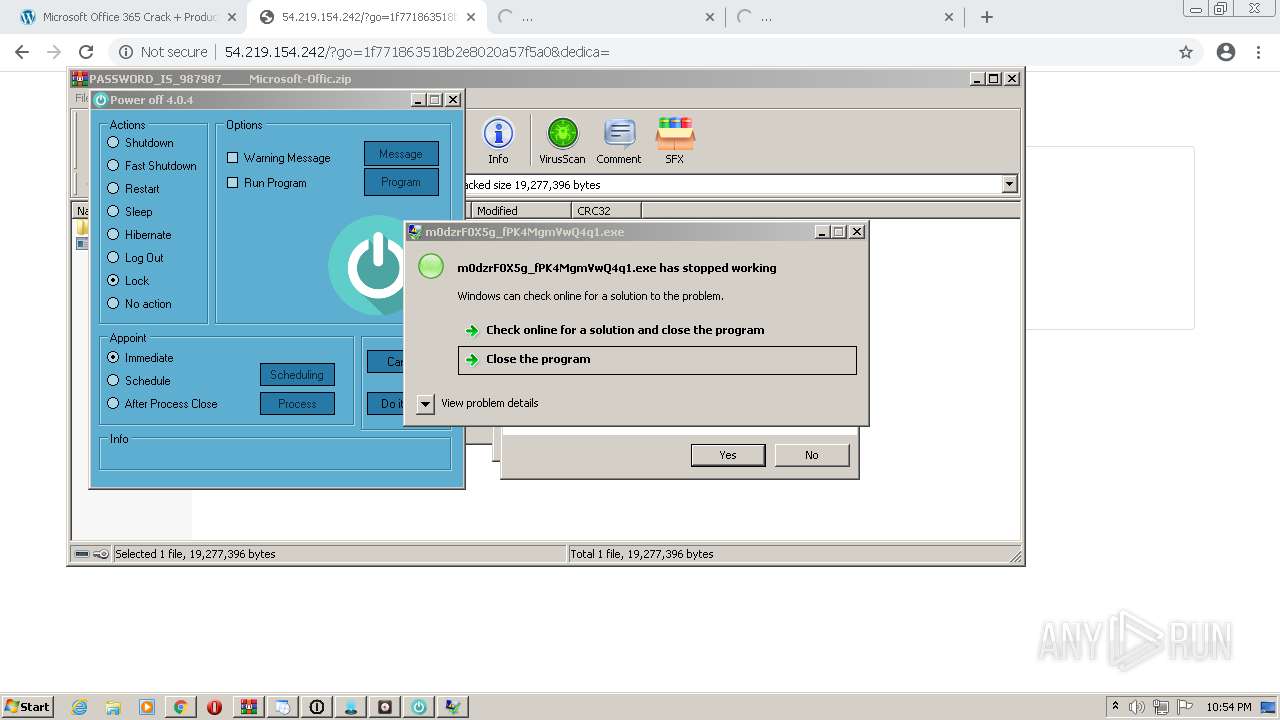
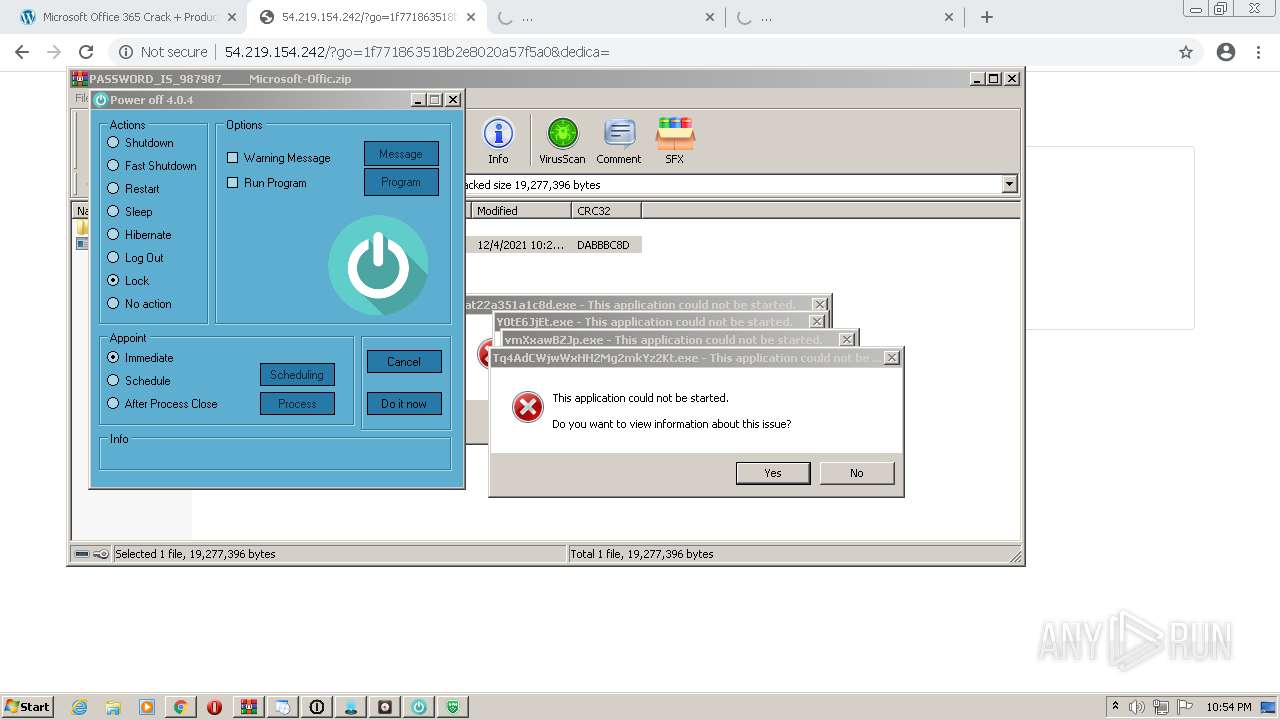
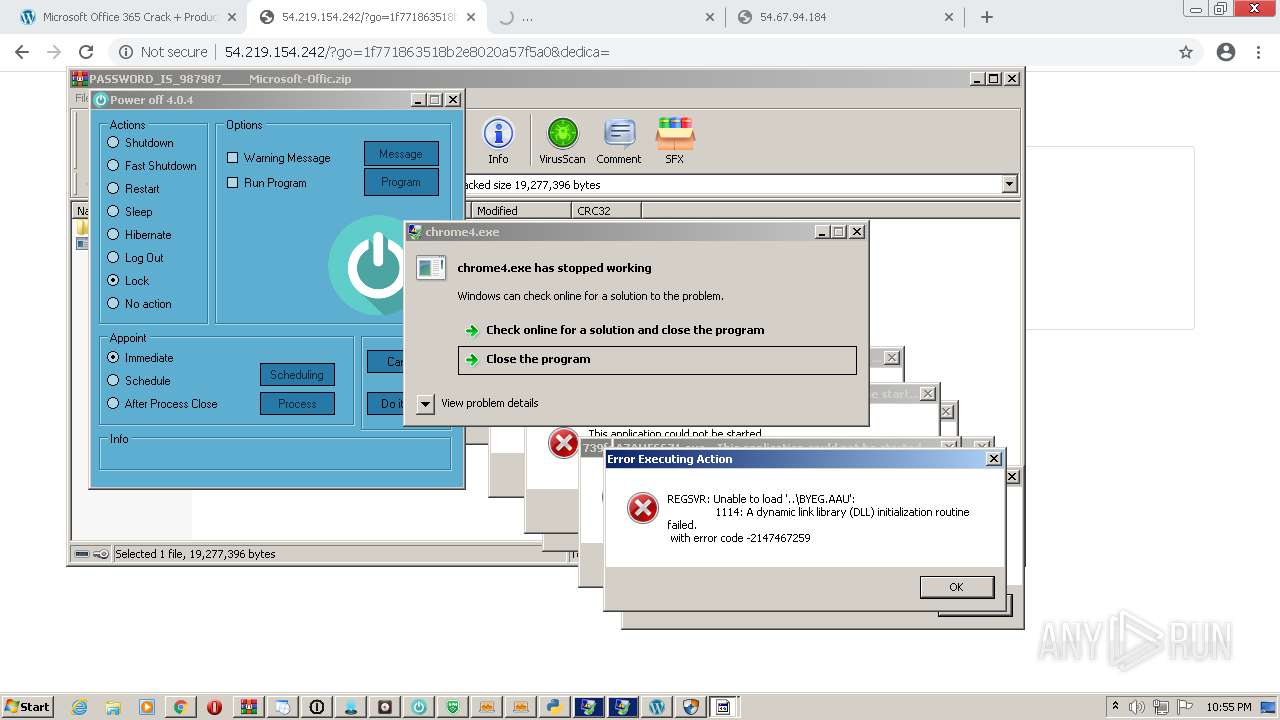
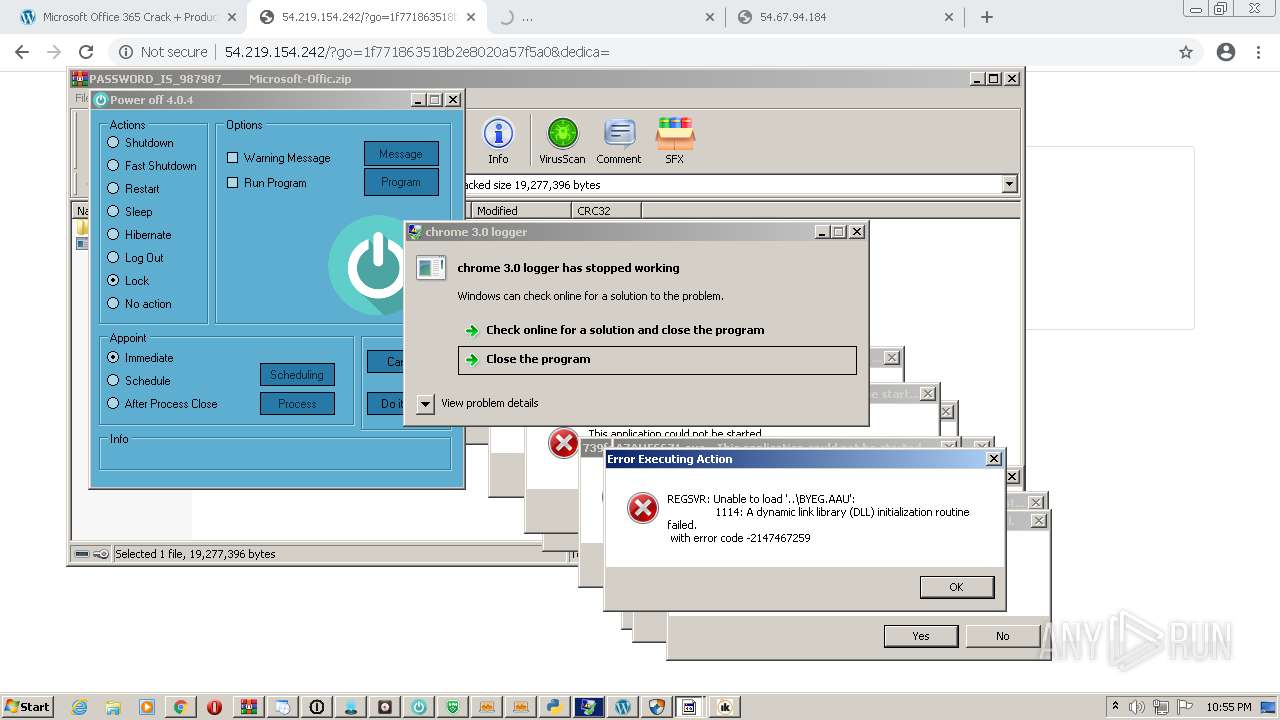
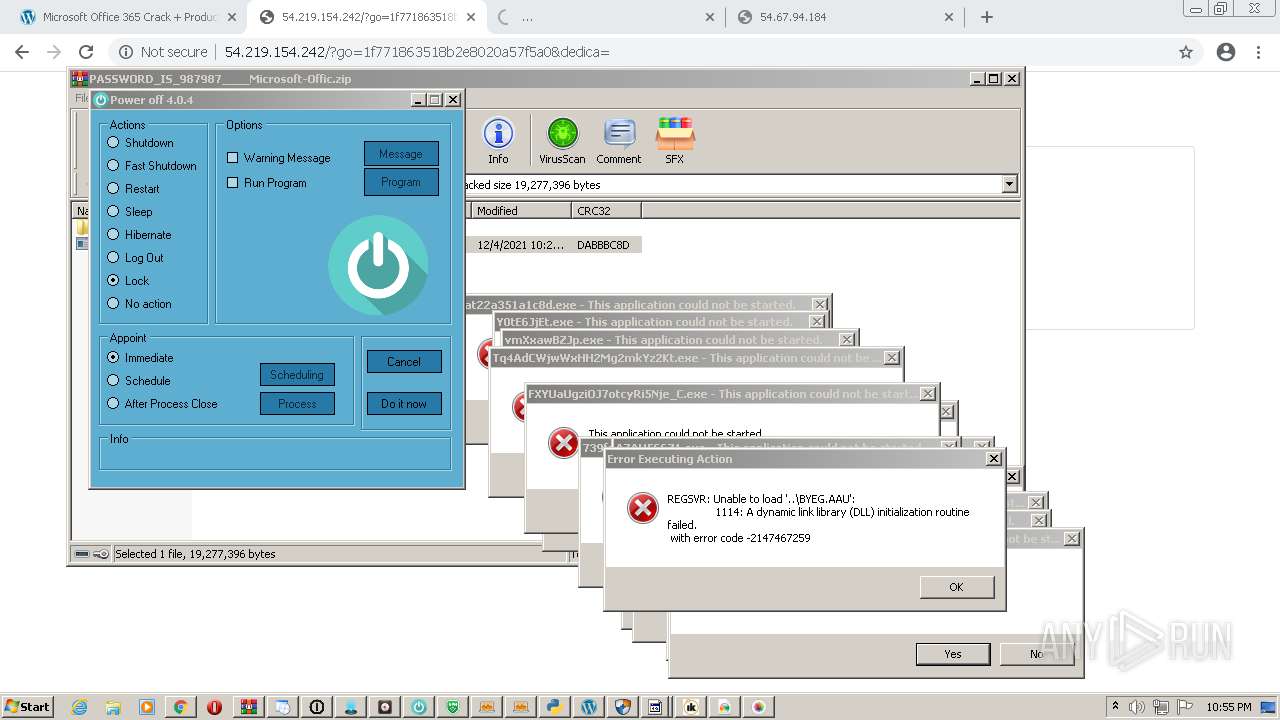
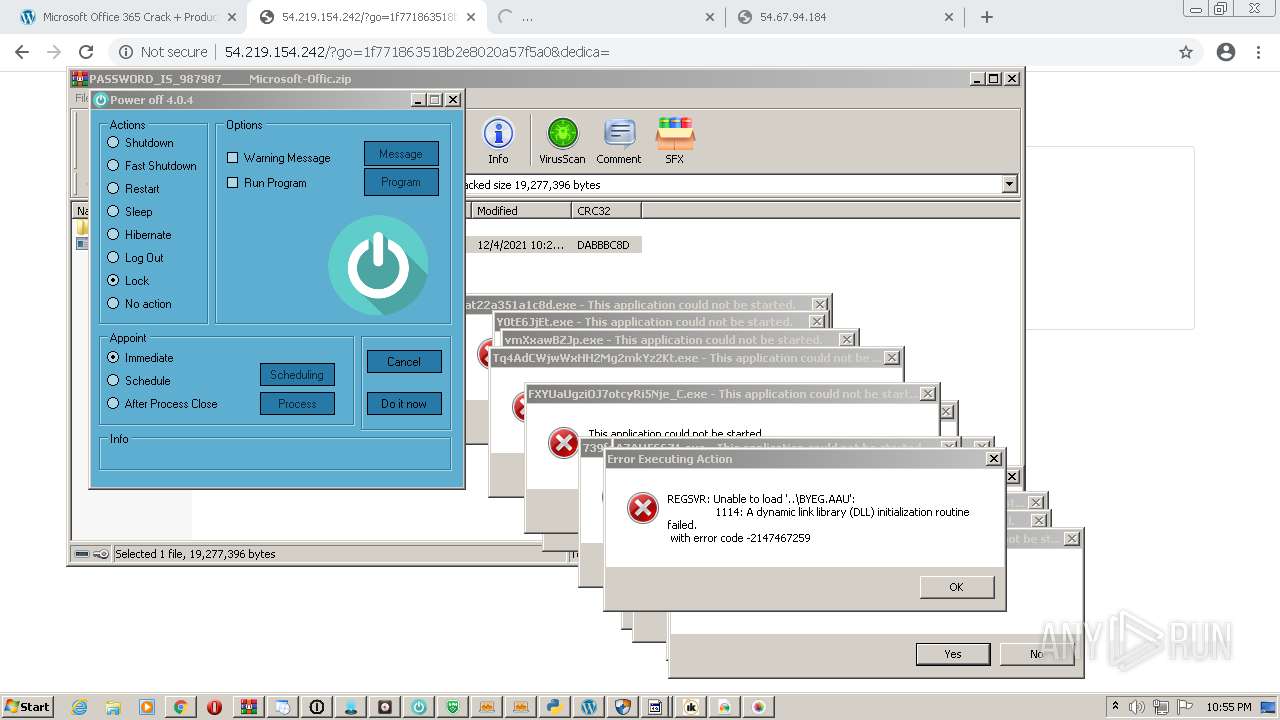
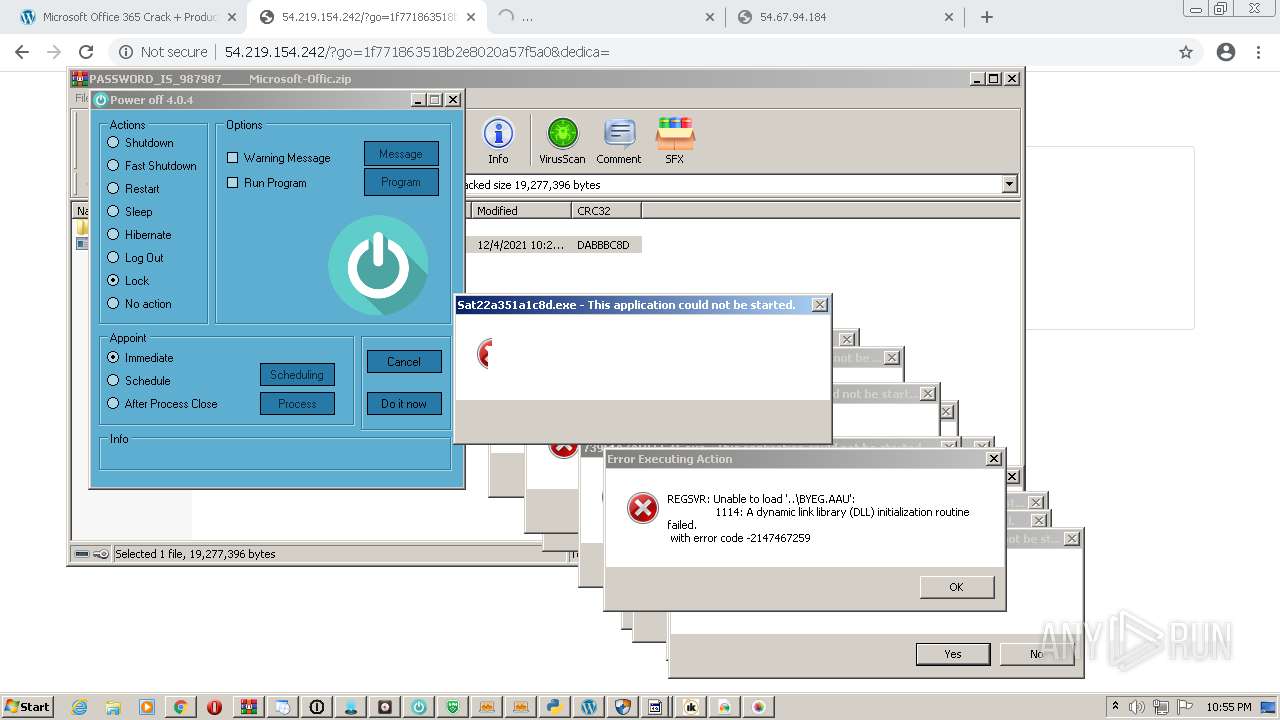
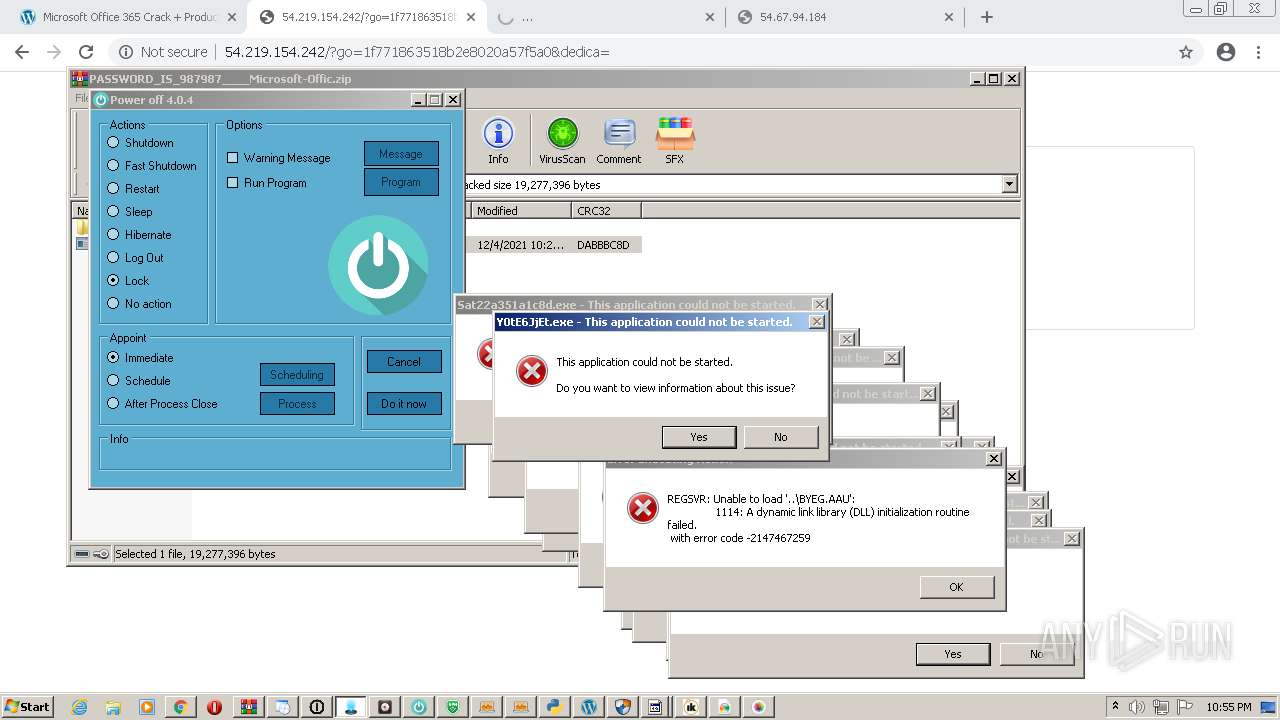
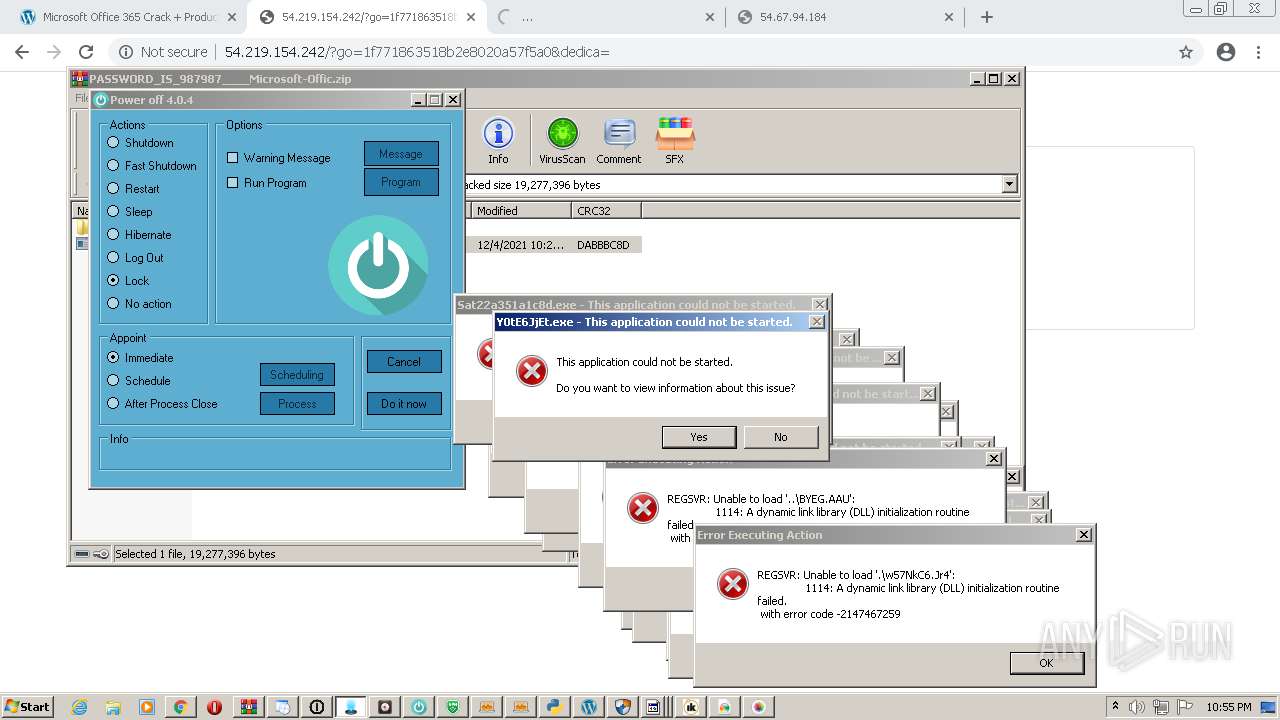
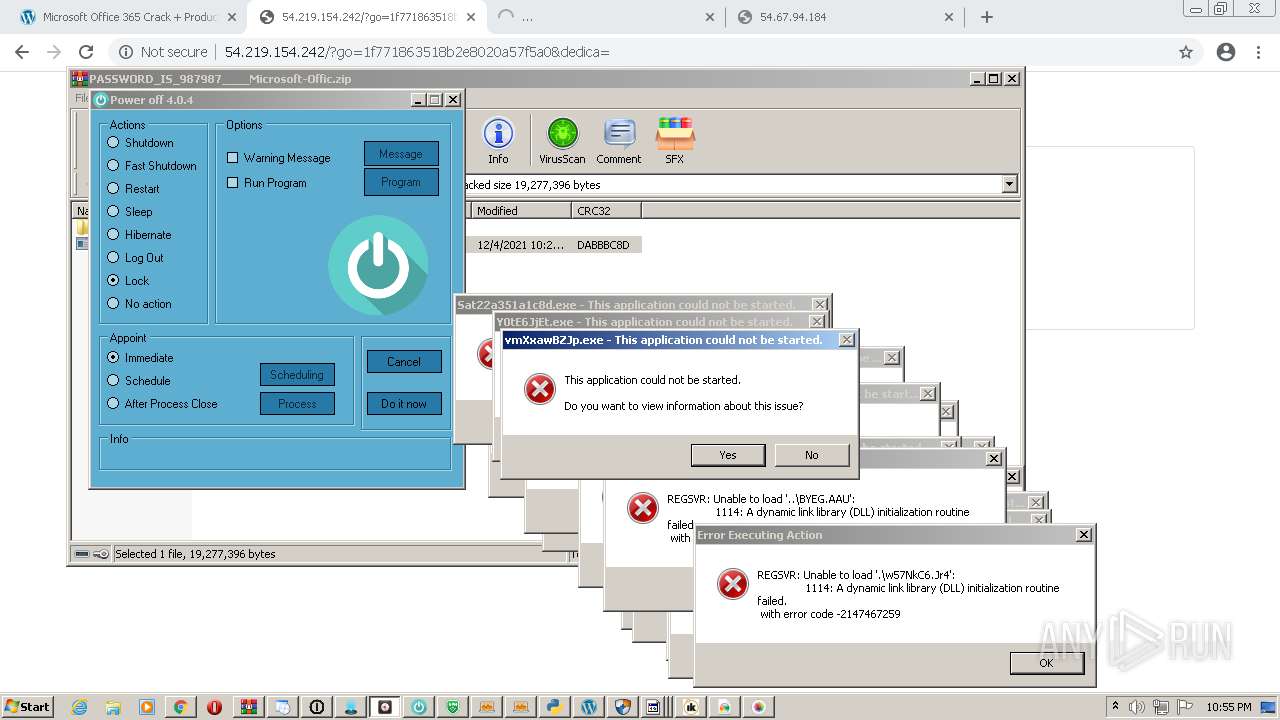
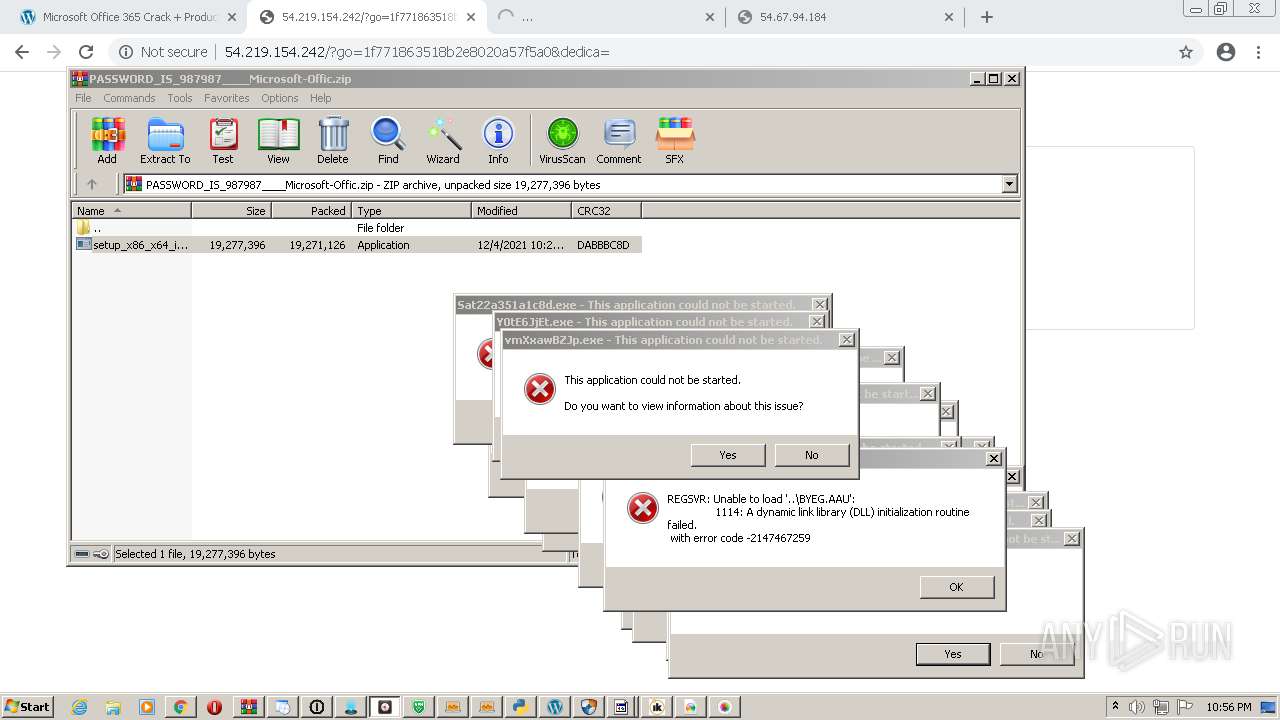
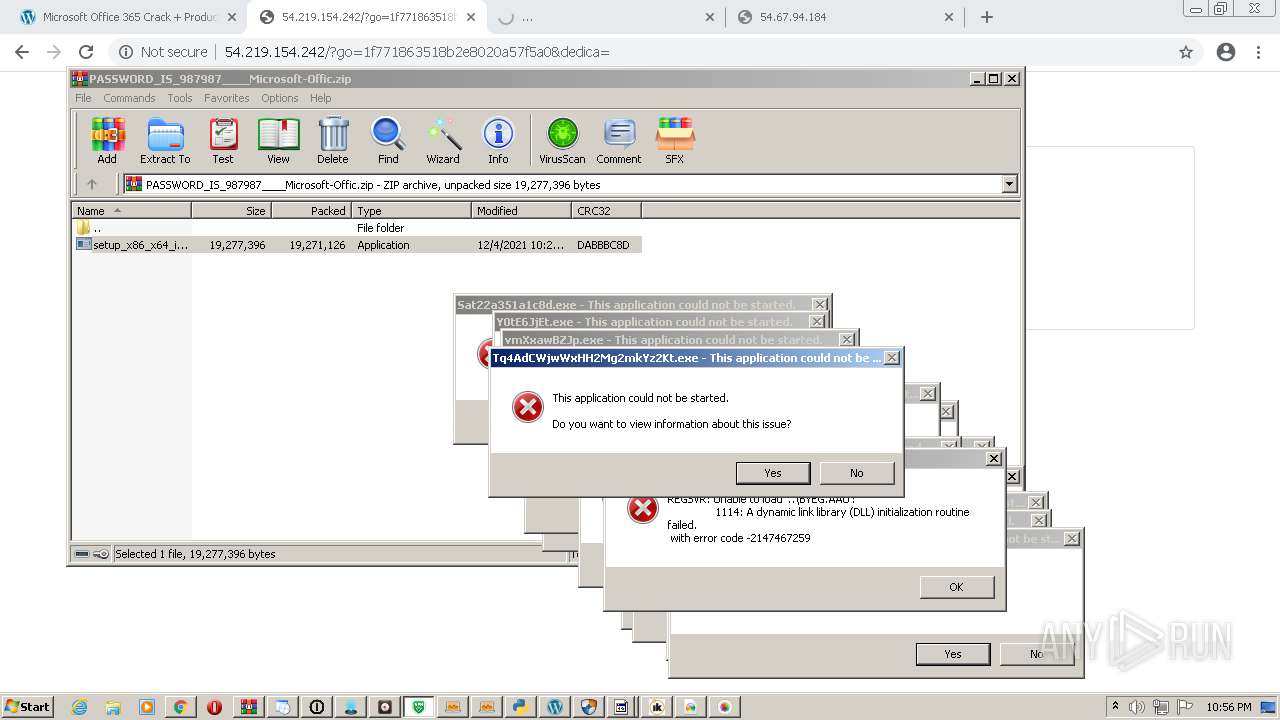
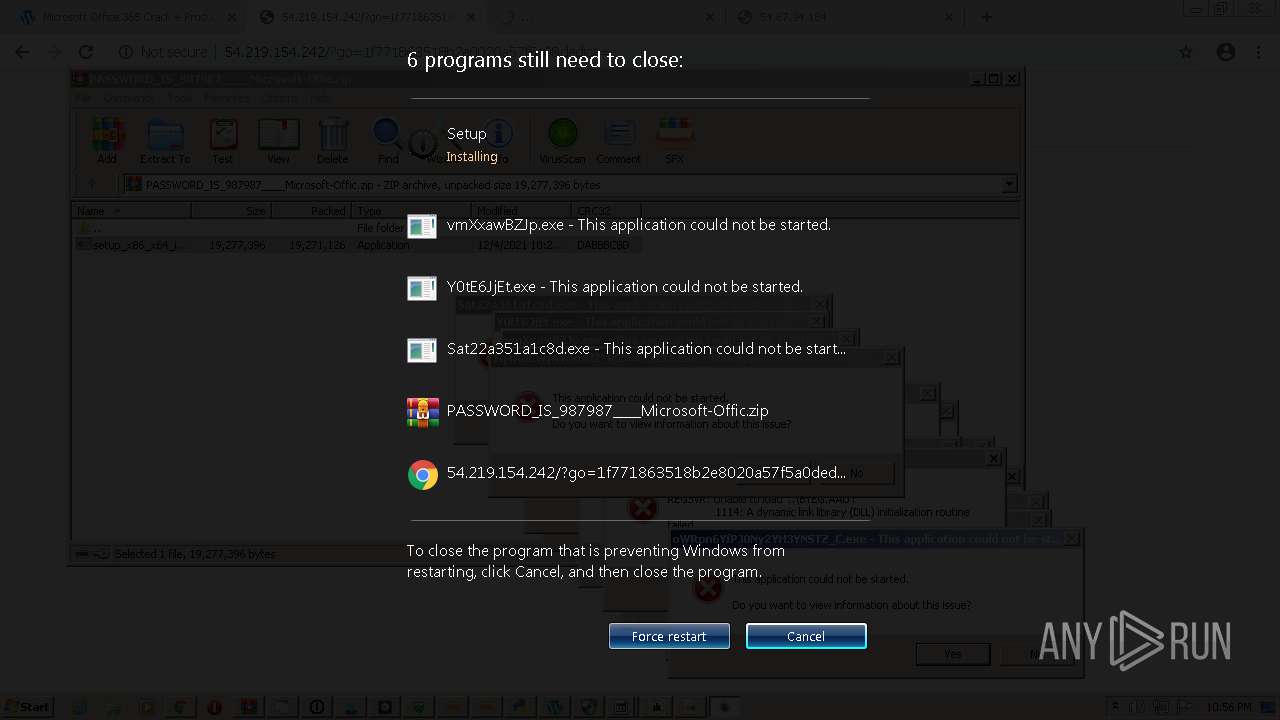
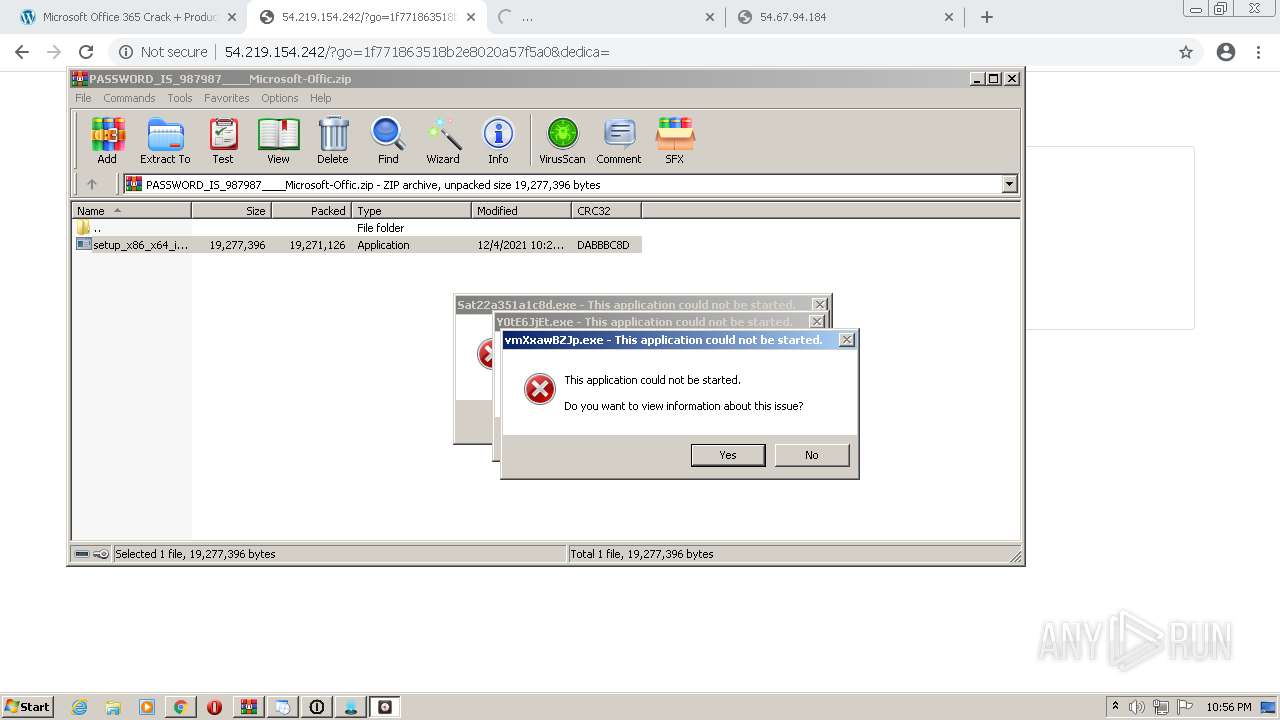
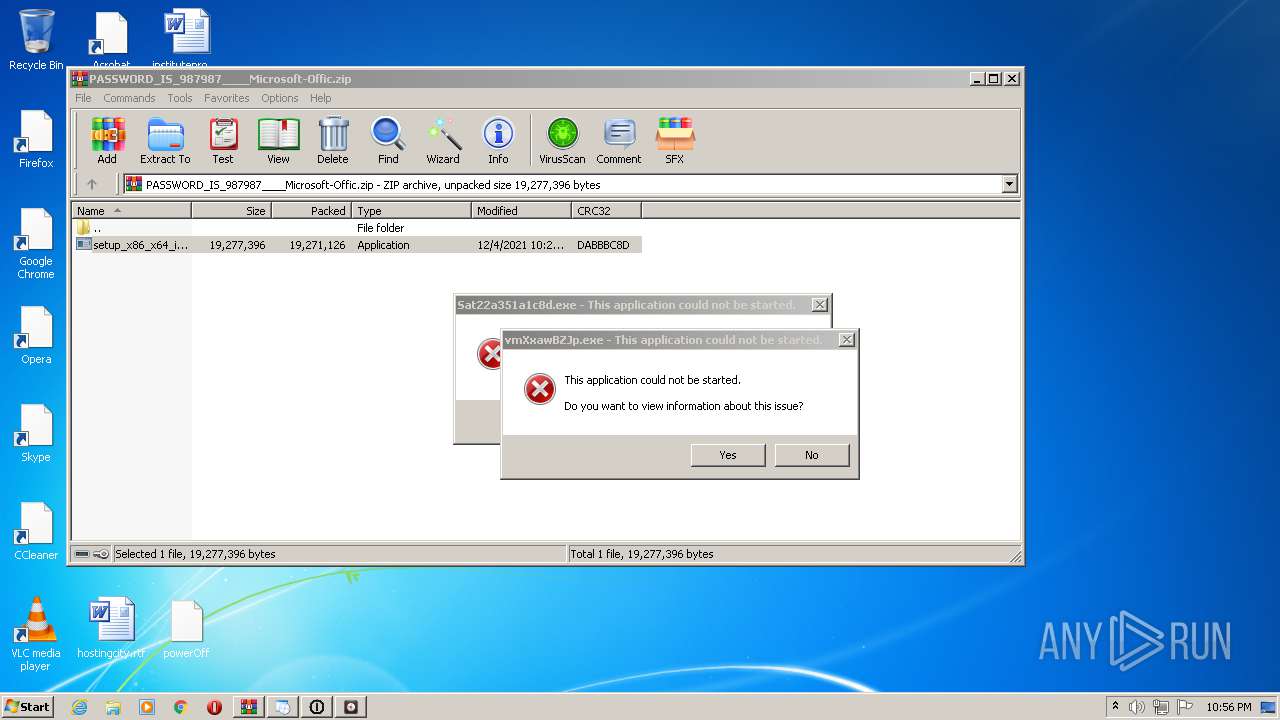
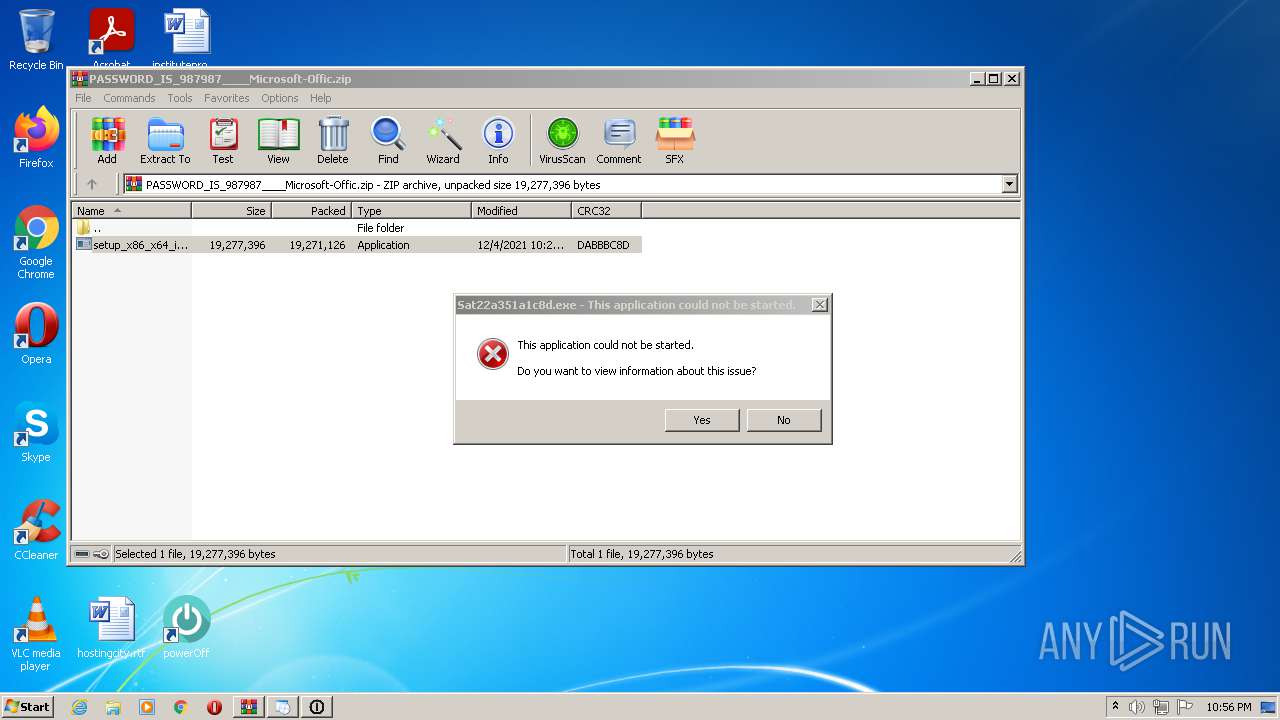
MALICIOUS
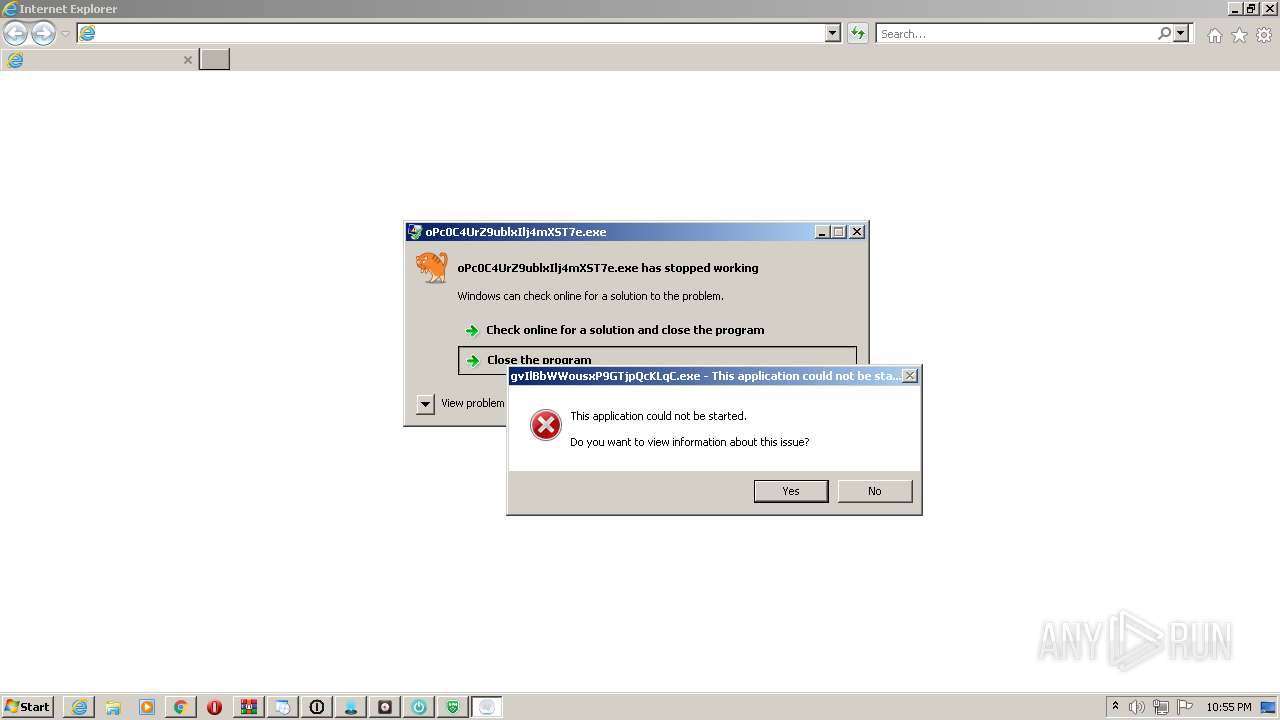
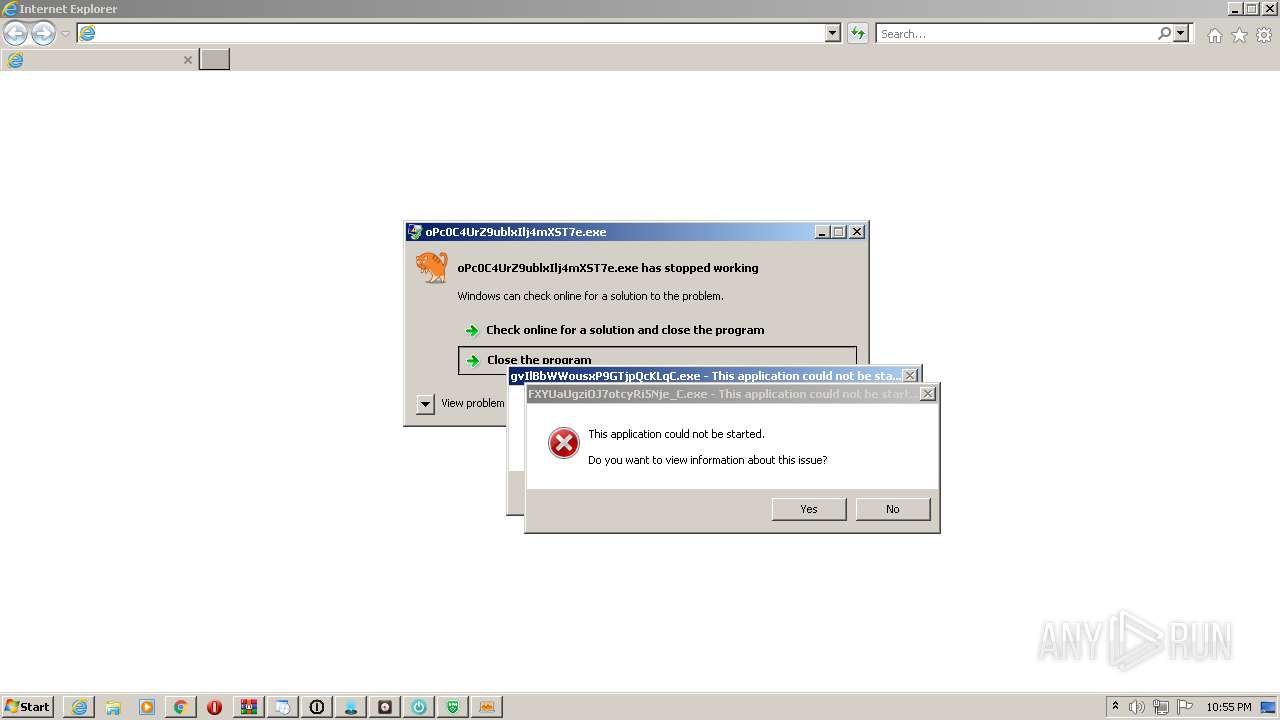
Application was dropped or rewritten from another process
- setup_x86_x64_install.exe (PID: 2620)
- setup_installer.exe (PID: 3620)
- setup_x86_x64_install.exe (PID: 4032)
- Sat2277dc8fdecf9955.exe (PID: 2980)
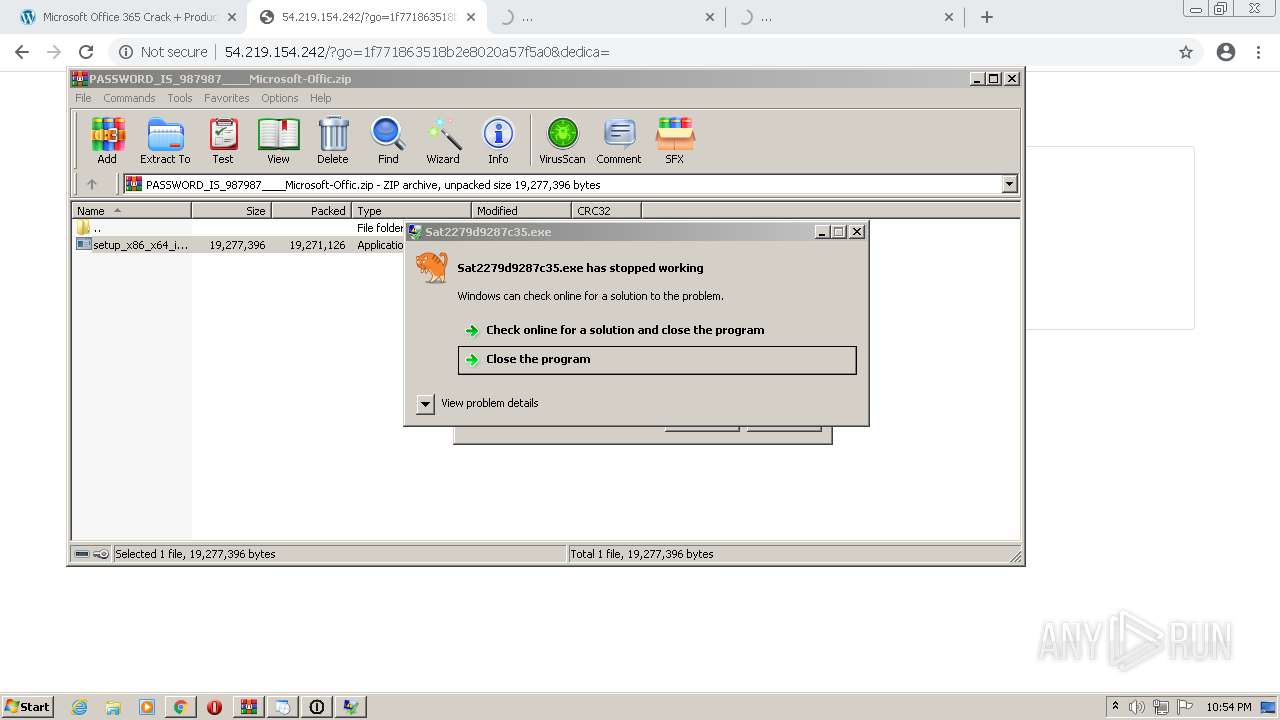
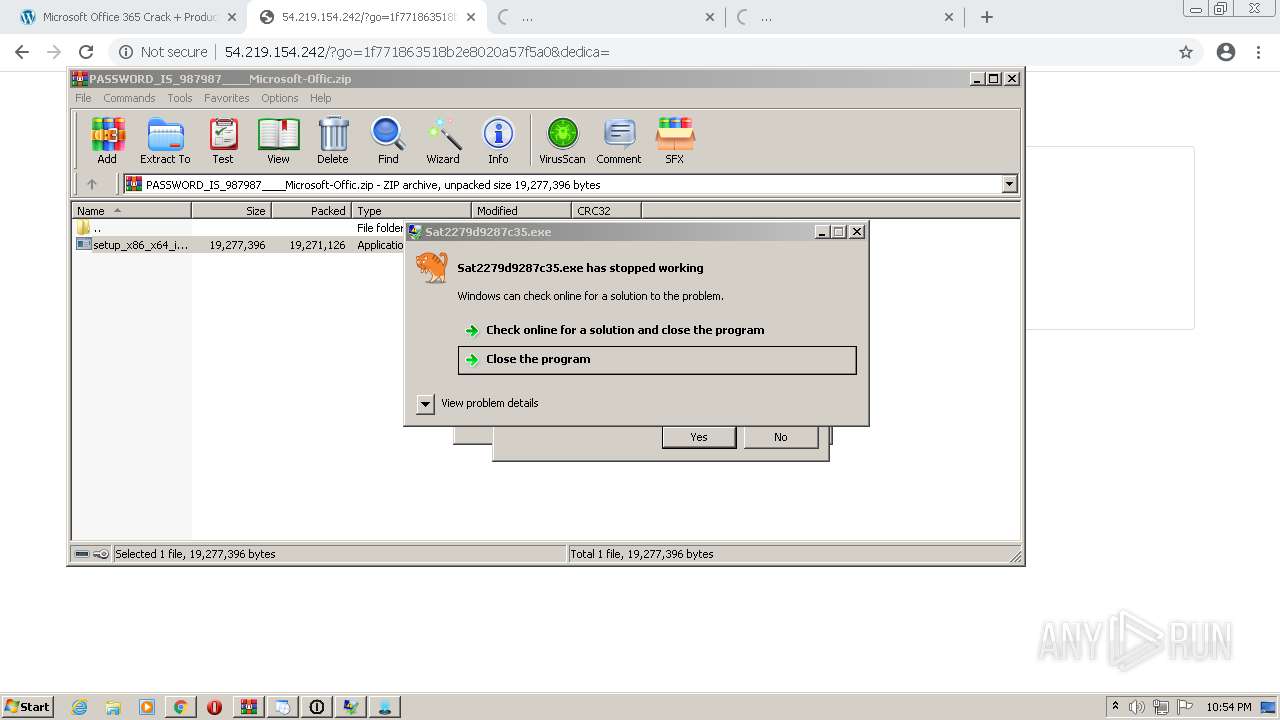
- Sat2279d9287c35.exe (PID: 1012)
- Sat2283597be5.exe (PID: 1468)
- Sat22a89dabd73a.exe (PID: 2204)
- Sat22e1de582fd2.exe (PID: 3380)
- setup_install.exe (PID: 320)
- Sat22c19354af50153fc.exe (PID: 1964)
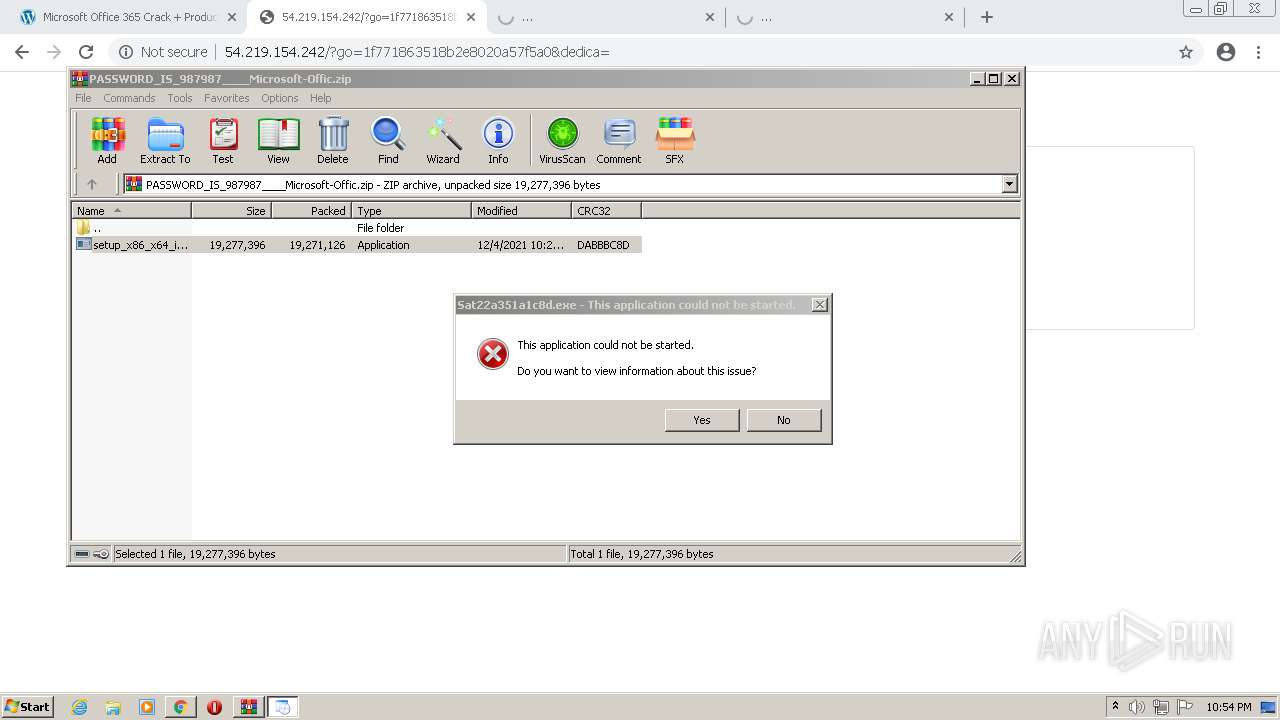
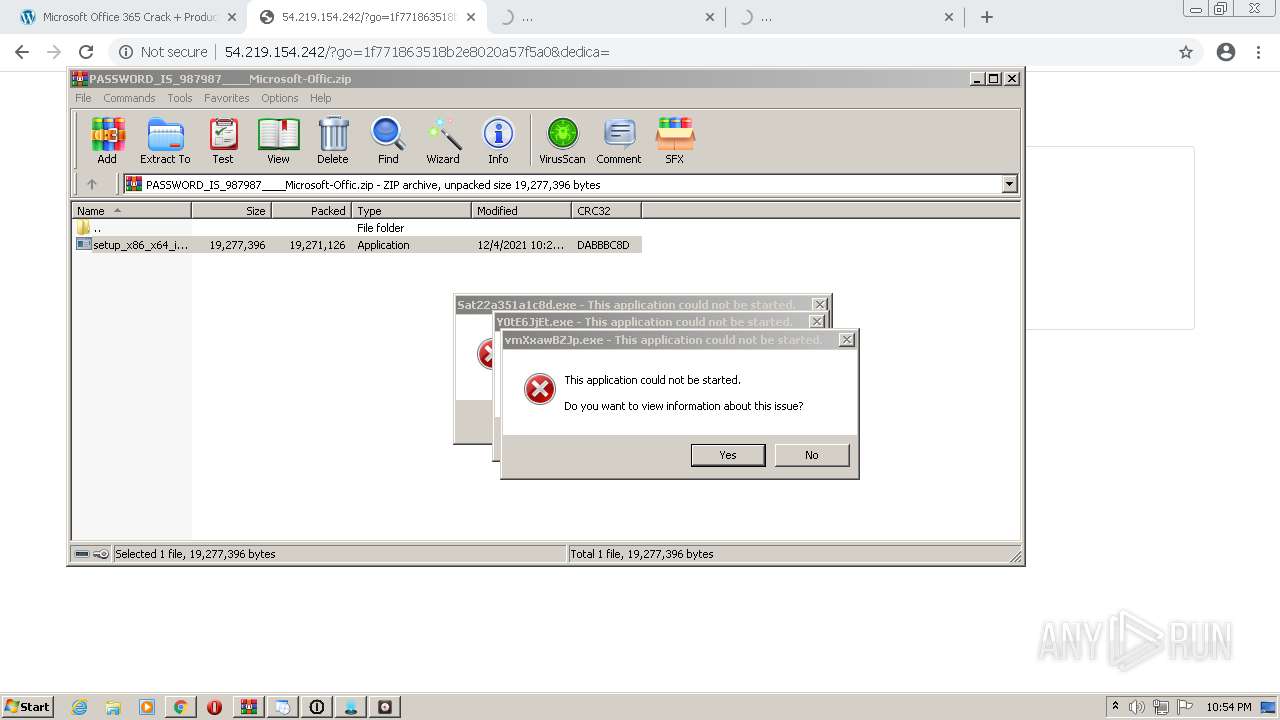
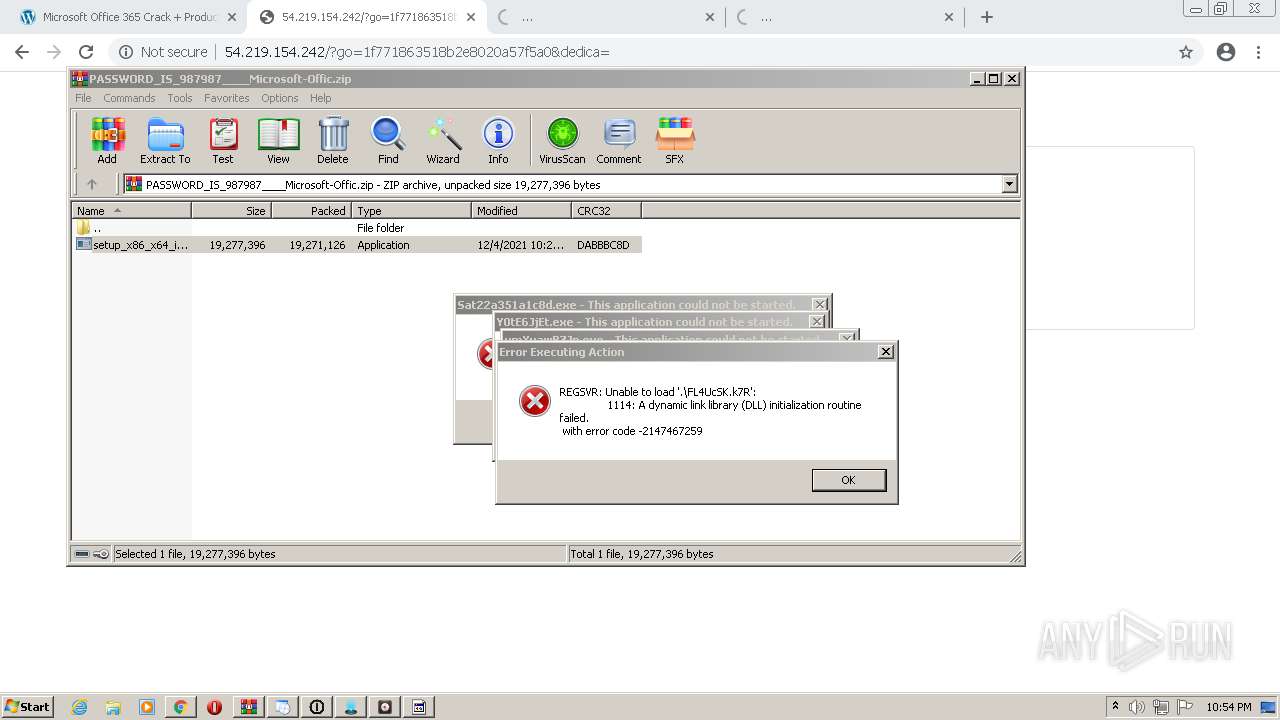
- Sat22a351a1c8d.exe (PID: 4056)
- Sat2222420371.exe (PID: 2444)
- Sat2289ad74b032.exe (PID: 1252)
- Sat22104da08f916892.exe (PID: 4492)
- Sat22982298fe96366.exe (PID: 4512)
- Sat22fef37ed548.exe (PID: 4612)
- Sat22b14fef46492a2.exe (PID: 2448)
- Sat22b96533ff4ab5.exe (PID: 2512)
- Sat22067ae64d39.exe (PID: 4324)
- Sat22b14fef46492a2.exe (PID: 3628)
- Sat22c16f4e6df1ac4f.exe (PID: 5140)
- Sat22ee5de845409.exe (PID: 5172)
- Sat22c19354af50153fc.exe (PID: 5508)
- Sat22206dbfc0e.exe (PID: 5944)
Loads dropped or rewritten executable
- setup_install.exe (PID: 320)
Executes PowerShell scripts
- cmd.exe (PID: 3992)
- cmd.exe (PID: 1576)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 2668)
- setup_x86_x64_install.exe (PID: 4032)
- setup_installer.exe (PID: 3620)
- setup_install.exe (PID: 320)
- cmd.exe (PID: 3992)
- cmd.exe (PID: 1576)
- powershell.exe (PID: 4036)
- powershell.exe (PID: 2128)
- cmd.exe (PID: 3176)
- cmd.exe (PID: 3092)
- cmd.exe (PID: 848)
- Sat22b14fef46492a2.exe (PID: 2448)
- Sat2279d9287c35.exe (PID: 1012)
- cmd.exe (PID: 2644)
- cmd.exe (PID: 3252)
- cmd.exe (PID: 2624)
- cmd.exe (PID: 3804)
- Sat22b14fef46492a2.exe (PID: 3628)
- cmd.exe (PID: 3480)
- cmd.exe (PID: 3200)
- Sat2277dc8fdecf9955.exe (PID: 2980)
- Sat22a89dabd73a.exe (PID: 2204)
- cmd.exe (PID: 3560)
- cmd.exe (PID: 2620)
- Sat2222420371.exe (PID: 2444)
- cmd.exe (PID: 3180)
- cmd.exe (PID: 2584)
- Sat22c19354af50153fc.exe (PID: 1964)
- Sat22a351a1c8d.exe (PID: 4056)
- Sat2289ad74b032.exe (PID: 1252)
- cmd.exe (PID: 2788)
- cmd.exe (PID: 4292)
- cmd.exe (PID: 3960)
- cmd.exe (PID: 2492)
- cmd.exe (PID: 4180)
- Sat22104da08f916892.exe (PID: 4492)
- Sat22e1de582fd2.exe (PID: 3380)
- cmd.exe (PID: 3124)
- Sat2283597be5.exe (PID: 1468)
- cmd.exe (PID: 272)
- Sat22982298fe96366.exe (PID: 4512)
- Sat22067ae64d39.exe (PID: 4324)
- Sat22b96533ff4ab5.exe (PID: 2512)
- Sat22fef37ed548.exe (PID: 4612)
- Sat22206dbfc0e.exe (PID: 5944)
- Sat22c16f4e6df1ac4f.exe (PID: 5140)
- Sat22c19354af50153fc.exe (PID: 5508)
Reads the computer name
- WinRAR.exe (PID: 2668)
- setup_x86_x64_install.exe (PID: 4032)
- setup_installer.exe (PID: 3620)
- powershell.exe (PID: 2128)
- powershell.exe (PID: 4036)
- Sat2279d9287c35.exe (PID: 1012)
- Sat22a89dabd73a.exe (PID: 2204)
- Sat22a351a1c8d.exe (PID: 4056)
- Sat22b14fef46492a2.exe (PID: 3628)
- Sat2283597be5.exe (PID: 1468)
- Sat2289ad74b032.exe (PID: 1252)
- Sat2277dc8fdecf9955.exe (PID: 2980)
- Sat22c19354af50153fc.exe (PID: 1964)
- Sat22e1de582fd2.exe (PID: 3380)
- Sat22982298fe96366.exe (PID: 4512)
- Sat22fef37ed548.exe (PID: 4612)
- Sat22c19354af50153fc.exe (PID: 5508)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2668)
- setup_x86_x64_install.exe (PID: 4032)
- setup_installer.exe (PID: 3620)
- Sat2277dc8fdecf9955.exe (PID: 2980)
Drops a file with too old compile date
- setup_installer.exe (PID: 3620)
Drops a file with a compile date too recent
- setup_installer.exe (PID: 3620)
Drops a file that was compiled in debug mode
- setup_installer.exe (PID: 3620)
Starts CMD.EXE for commands execution
- setup_install.exe (PID: 320)
Application launched itself
- Sat22b14fef46492a2.exe (PID: 2448)
- Sat22c19354af50153fc.exe (PID: 1964)
Reads Environment values
- Sat22fef37ed548.exe (PID: 4612)
Starts MSHTA.EXE for opening HTA or HTMLS files
- Sat2289ad74b032.exe (PID: 1252)
INFO
Checks supported languages
- chrome.exe (PID: 3652)
- chrome.exe (PID: 4024)
- chrome.exe (PID: 2216)
- chrome.exe (PID: 3792)
- chrome.exe (PID: 2688)
- chrome.exe (PID: 2452)
- chrome.exe (PID: 3068)
- chrome.exe (PID: 2488)
- chrome.exe (PID: 3240)
- chrome.exe (PID: 3632)
- chrome.exe (PID: 3596)
- chrome.exe (PID: 3188)
- chrome.exe (PID: 2736)
- chrome.exe (PID: 3708)
- chrome.exe (PID: 2472)
- chrome.exe (PID: 1176)
- chrome.exe (PID: 3408)
- chrome.exe (PID: 1976)
- chrome.exe (PID: 3256)
- chrome.exe (PID: 2032)
- chrome.exe (PID: 2556)
- chrome.exe (PID: 3964)
- chrome.exe (PID: 2708)
- chrome.exe (PID: 2832)
- chrome.exe (PID: 2960)
- chrome.exe (PID: 1204)
- chrome.exe (PID: 2856)
- chrome.exe (PID: 2780)
- chrome.exe (PID: 1792)
- chrome.exe (PID: 3248)
Application launched itself
- chrome.exe (PID: 3652)
Reads the computer name
- chrome.exe (PID: 3652)
- chrome.exe (PID: 2216)
- chrome.exe (PID: 3792)
- chrome.exe (PID: 2488)
- chrome.exe (PID: 3188)
- chrome.exe (PID: 1976)
- chrome.exe (PID: 3964)
- chrome.exe (PID: 3408)
- chrome.exe (PID: 2780)
- chrome.exe (PID: 1792)
- chrome.exe (PID: 2856)
Reads the hosts file
- chrome.exe (PID: 3652)
- chrome.exe (PID: 3792)
Reads settings of System Certificates
- chrome.exe (PID: 3792)
- Sat2279d9287c35.exe (PID: 1012)
- Sat22c19354af50153fc.exe (PID: 5508)
Reads the date of Windows installation
- chrome.exe (PID: 1976)
Checks Windows Trust Settings
- powershell.exe (PID: 2128)
- powershell.exe (PID: 4036)
- Sat2279d9287c35.exe (PID: 1012)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
125
Monitored processes
82
Malicious processes
5
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 272 | C:\Windows\system32\cmd.exe /c Sat2206366bfaba.exe | C:\Windows\system32\cmd.exe | — | setup_install.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) | |||||||||||||||
| 320 | "C:\Users\admin\AppData\Local\Temp\7zS42E289C2\setup_install.exe" | C:\Users\admin\AppData\Local\Temp\7zS42E289C2\setup_install.exe | — | setup_installer.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 848 | C:\Windows\system32\cmd.exe /c Sat2277dc8fdecf9955.exe | C:\Windows\system32\cmd.exe | — | setup_install.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1012 | Sat2279d9287c35.exe | C:\Users\admin\AppData\Local\Temp\7zS42E289C2\Sat2279d9287c35.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 1176 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1036,7434490469501562208,16193926447410187082,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --disable-client-side-phishing-detection --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=15 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3612 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1204 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1036,7434490469501562208,16193926447410187082,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --disable-client-side-phishing-detection --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=25 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=844 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1252 | Sat2289ad74b032.exe | C:\Users\admin\AppData\Local\Temp\7zS42E289C2\Sat2289ad74b032.exe | — | cmd.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: HIGH Description: WinRAR archiver Exit code: 0 Version: 5.90.0 Modules
| |||||||||||||||
| 1468 | Sat2283597be5.exe | C:\Users\admin\AppData\Local\Temp\7zS42E289C2\Sat2283597be5.exe | — | cmd.exe | |||||||||||
User: admin Company: jhsdejufgsige Integrity Level: HIGH Description: jhsdejufgsige Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1576 | C:\Windows\system32\cmd.exe /c powershell -inputformat none -outputformat none -NonInteractive -Command Add-MpPreference -ExclusionPath "C:\Users\admin\AppData\Local\Temp" | C:\Windows\system32\cmd.exe | — | setup_install.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1792 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1036,7434490469501562208,16193926447410187082,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1736 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
18 421
Read events
18 205
Write events
211
Delete events
5
Modification events
| (PID) Process: | (3652) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3652) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3652) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3652) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3652) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3652) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3652) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3652) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3652) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
| (PID) Process: | (3652) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_installdate |
Value: 0 | |||
Executable files
29
Suspicious files
37
Text files
88
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3652 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-61ABF13A-E44.pma | — | |
MD5:— | SHA256:— | |||
| 3652 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\a35780d3-8064-4e33-8b2f-68ba37b9b052.tmp | text | |
MD5:— | SHA256:— | |||
| 4024 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\CrashpadMetrics.pma | binary | |
MD5:03C4F648043A88675A920425D824E1B3 | SHA256:F91DBB7C64B4582F529C968C480D2DCE1C8727390482F31E4355A27BB3D9B450 | |||
| 3652 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old~RF115745.TMP | text | |
MD5:81F483F77EE490F35306A4F94DB2286B | SHA256:82434CE3C9D13F509EBEEBE3A7A1A1DE9AB4557629D9FC855761E0CFA45E8BCE | |||
| 3652 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:5BD3C311F2136A7A88D3E197E55CF902 | SHA256:FA331915E1797E59979A3E4BCC2BD0D3DEAA039B94D4DB992BE251FD02A224B9 | |||
| 3652 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Preferences | text | |
MD5:— | SHA256:— | |||
| 3652 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:8FF312A95D60ED89857FEB720D80D4E1 | SHA256:946A57FAFDD28C3164D5AB8AB4971B21BD5EC5BFFF7554DBF832CB58CC37700B | |||
| 3652 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:00046F773EFDD3C8F8F6D0F87A2B93DC | SHA256:593EDE11D17AF7F016828068BCA2E93CF240417563FB06DC8A579110AEF81731 | |||
| 3652 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old | text | |
MD5:7721CDA9F5B73CE8A135471EB53B4E0E | SHA256:DD730C576766A46FFC84E682123248ECE1FF1887EC0ACAB22A5CE93A450F4500 | |||
| 3652 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF115725.TMP | text | |
MD5:936EB7280DA791E6DD28EF3A9B46D39C | SHA256:CBAF2AFD831B32F6D1C12337EE5D2F090D6AE1F4DCB40B08BEF49BF52AD9721F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
184
TCP/UDP connections
379
DNS requests
141
Threats
434
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3792 | chrome.exe | GET | — | 54.67.94.184:80 | http://54.67.94.184/?61abf16d522d5=00e4d8152198ab51e11479b8369b3be5f921fa92Array&m=41&q=Microsoft-Office-365-Crack---Product-Key-Free-Download-2021&dedica=&tron=61abf16d522dc.asp | US | — | — | unknown |
3792 | chrome.exe | GET | 301 | 104.21.69.103:80 | http://jloyrorai.xyz/?s=41&q=Microsoft-Office-365-Crack---Product-Key-Free-Download-2021&g=2b189a8302c4995e2c4f58b7636fc789&mode=&hmac=WyI2ZjA4MzhlZWJmYTAzMzAxNzczZGVlZDhjNGQxNmY1NDIyNTk1ODg2IiwiMzU2MDc3MTA5YmFhODJjOGNmOWM3OGEzZjQ3MTQ0OTQ0ZjRmYjk4MSIsImI5OWZmZjM1N2RlMmZiNGMwNTY4YTdmZDIzMjU4NDY5OTJmYmIwYjMiXQ== | US | — | — | malicious |
876 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | — | — | whitelisted |
3792 | chrome.exe | GET | — | 54.67.94.184:80 | http://54.67.94.184/?61abf14e43de6=2c531f7c896fc49fd9b0e3d4319161c1ce686170Array&m=41&q=Microsoft-Office-365-Crack---Product-Key-Free-Download-2021&dedica=&tron=61abf14e43df1.asp | US | — | — | unknown |
3792 | chrome.exe | GET | 301 | 172.67.192.130:80 | http://kahinpyr.xyz/?s=41&q=Microsoft-Office-365-Crack---Product-Key-Free-Download-2021&g=6f2a80f1fc4c075da93f33f9c19735ee&mode=&hmac=WyI2ZjA4MzhlZWJmYTAzMzAxNzczZGVlZDhjNGQxNmY1NDIyNTk1ODg2IiwiMzU2MDc3MTA5YmFhODJjOGNmOWM3OGEzZjQ3MTQ0OTQ0ZjRmYjk4MSIsImI5OWZmZjM1N2RlMmZiNGMwNTY4YTdmZDIzMjU4NDY5OTJmYmIwYjMiXQ== | US | — | — | malicious |
3792 | chrome.exe | GET | 301 | 104.21.21.241:80 | http://uengener.xyz/?s=41&q=Microsoft-Office-365-Crack---Product-Key-Free-Download-2021&g=c767f21c3420c88a96bc041533984557&mode=&hmac=WyI2ZjA4MzhlZWJmYTAzMzAxNzczZGVlZDhjNGQxNmY1NDIyNTk1ODg2IiwiMzU2MDc3MTA5YmFhODJjOGNmOWM3OGEzZjQ3MTQ0OTQ0ZjRmYjk4MSIsImI5OWZmZjM1N2RlMmZiNGMwNTY4YTdmZDIzMjU4NDY5OTJmYmIwYjMiXQ== | US | — | — | malicious |
3792 | chrome.exe | GET | 302 | 54.219.154.242:80 | http://54.219.154.242/?61abf17ce8e13=b37d6a7e97be9c634d531966a34b26d6d442fddcArray&m=41&q=Microsoft-Office-365-Crack---Product-Key-Free-Download-2021&dedica=&tron=61abf17ce8e1a.asp | US | html | 19.0 Kb | unknown |
3792 | chrome.exe | POST | 200 | 54.219.154.242:80 | http://54.219.154.242/?go=1f771863518b2e8020a57f5a0&dedica= | US | html | 707 b | unknown |
876 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adys6mm2sd23z36ns7e4hcs4hrqq_1.3.36.111/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.111_win_ac5lwr5427en7czu7myxmee6c7xq.crx3 | US | binary | 5.63 Kb | whitelisted |
3792 | chrome.exe | POST | 200 | 54.219.154.242:80 | http://54.219.154.242/?verify-id=41&verify-hash=761f22b2c1593d0bb87e0b606f990ba4974706de&verify-msch=TWljcm9zb2Z0LU9mZmljZS0zNjUtQ3JhY2stLS1Qcm9kdWN0LUtleS1GcmVlLURvd25sb2FkLTIwMjE=&download=1&xtrans=MTM4 | US | compressed | 18.3 Mb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3792 | chrome.exe | 142.250.186.110:443 | clients2.google.com | Google Inc. | US | whitelisted |
3792 | chrome.exe | 172.67.209.95:443 | go4crack.com | — | US | unknown |
3792 | chrome.exe | 142.250.186.170:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3792 | chrome.exe | 172.67.39.148:443 | static.addtoany.com | — | US | unknown |
3792 | chrome.exe | 142.250.186.173:443 | accounts.google.com | Google Inc. | US | suspicious |
3792 | chrome.exe | 142.250.184.206:443 | www.youtube.com | Google Inc. | US | whitelisted |
3792 | chrome.exe | 172.67.138.239:443 | crackshops.com | — | US | unknown |
3792 | chrome.exe | 142.250.186.174:443 | encrypted-tbn0.gstatic.com | Google Inc. | US | whitelisted |
3792 | chrome.exe | 142.250.185.162:443 | googleads.g.doubleclick.net | Google Inc. | US | whitelisted |
3792 | chrome.exe | 142.250.185.131:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clients2.google.com |
| whitelisted |
accounts.google.com |
| shared |
go4crack.com |
| suspicious |
fonts.googleapis.com |
| whitelisted |
s.w.org |
| whitelisted |
static.addtoany.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
www.youtube.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
crackshops.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3792 | chrome.exe | A Network Trojan was detected | ET TROJAN Fake Software Download Redirect Leading to Malware M3 |
3792 | chrome.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
3792 | chrome.exe | A Network Trojan was detected | ET TROJAN Fake Software Download Redirect Leading to Malware M3 |
3792 | chrome.exe | Potentially Bad Traffic | AV INFO HTTP Request to a *.xyz domain |
— | — | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
2512 | Sat22b96533ff4ab5.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
2512 | Sat22b96533ff4ab5.exe | A Network Trojan was detected | ET MALWARE User-Agent (???) |
2512 | Sat22b96533ff4ab5.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
2512 | Sat22b96533ff4ab5.exe | A Network Trojan was detected | ET MALWARE User-Agent (???) |
— | — | Generic Protocol Command Decode | SURICATA Applayer Mismatch protocol both directions |
224 ETPRO signatures available at the full report