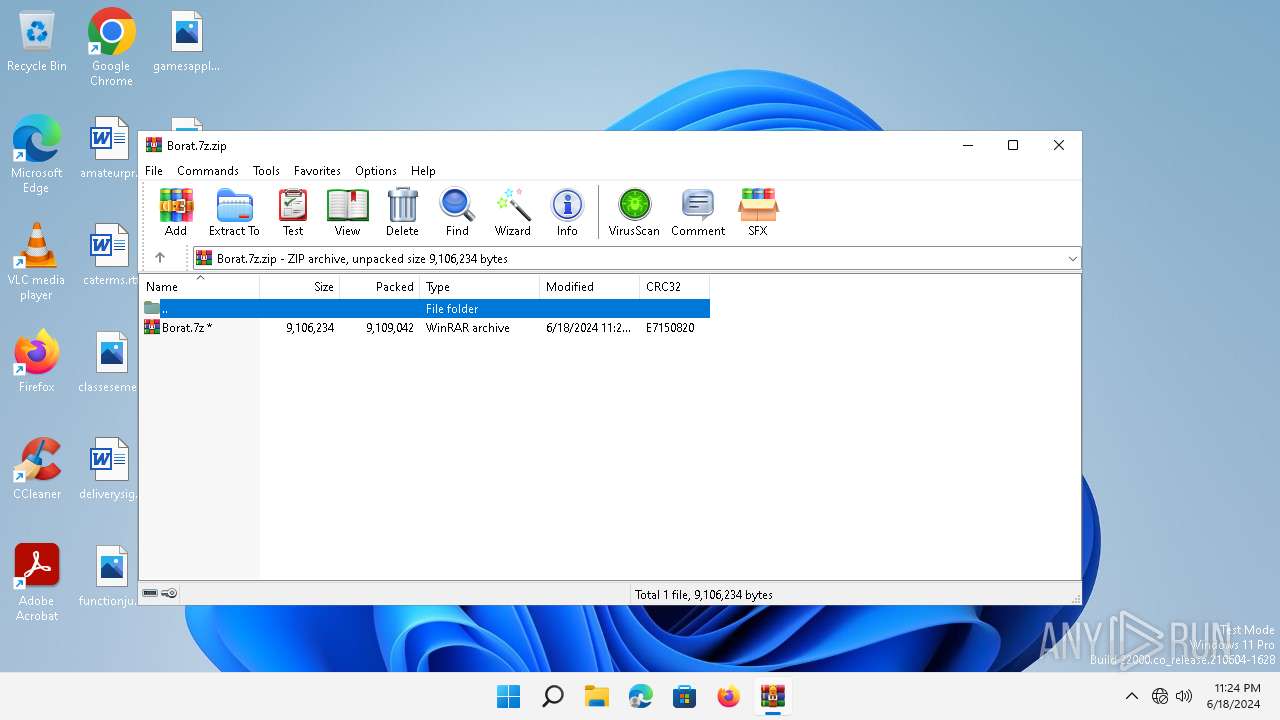
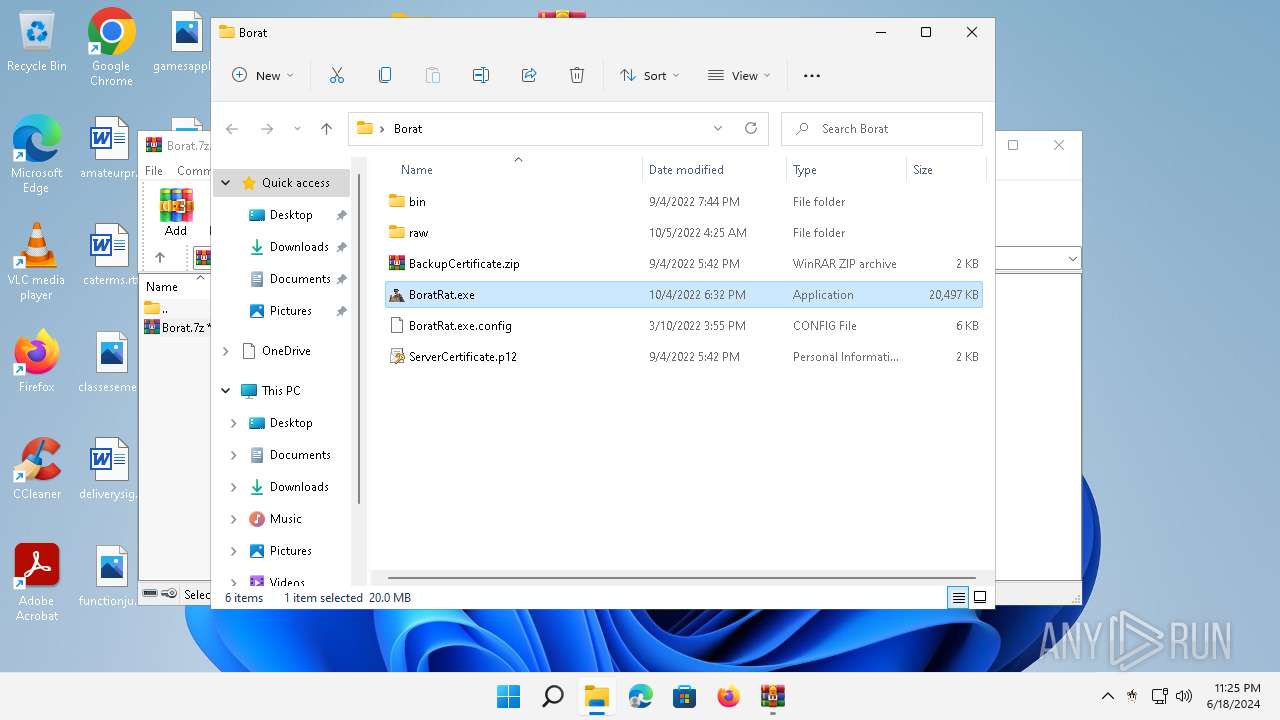
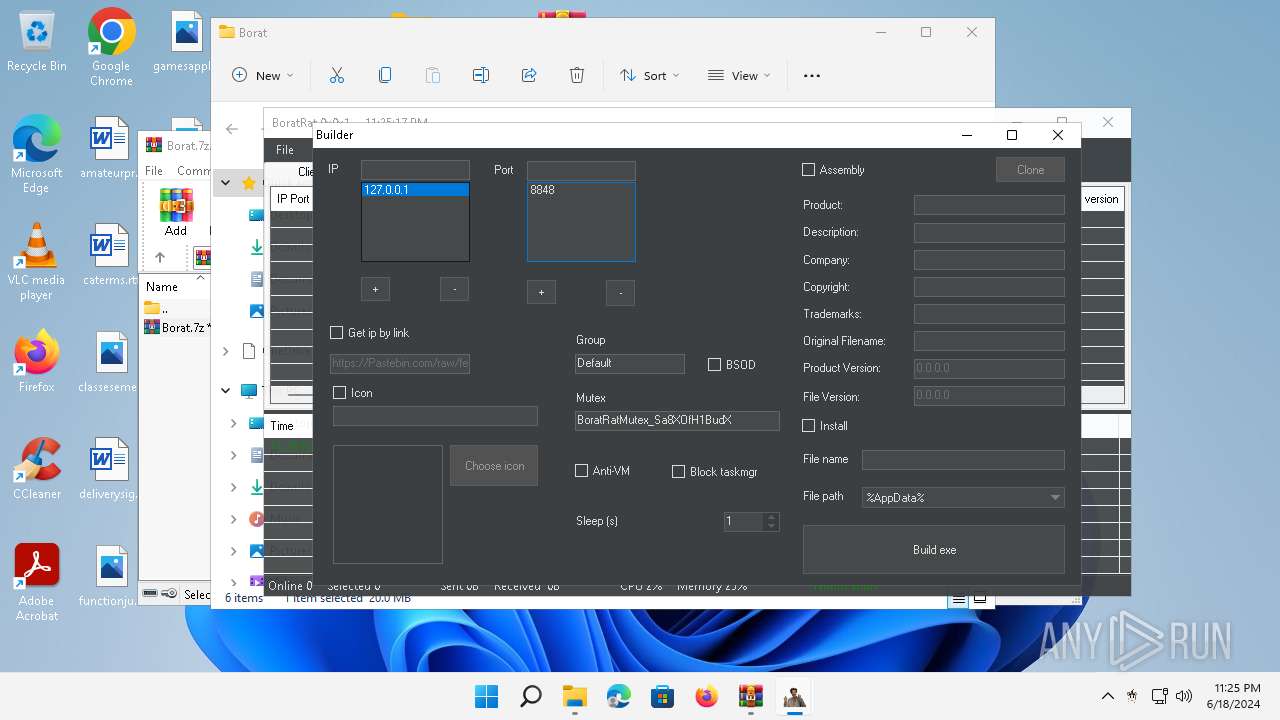
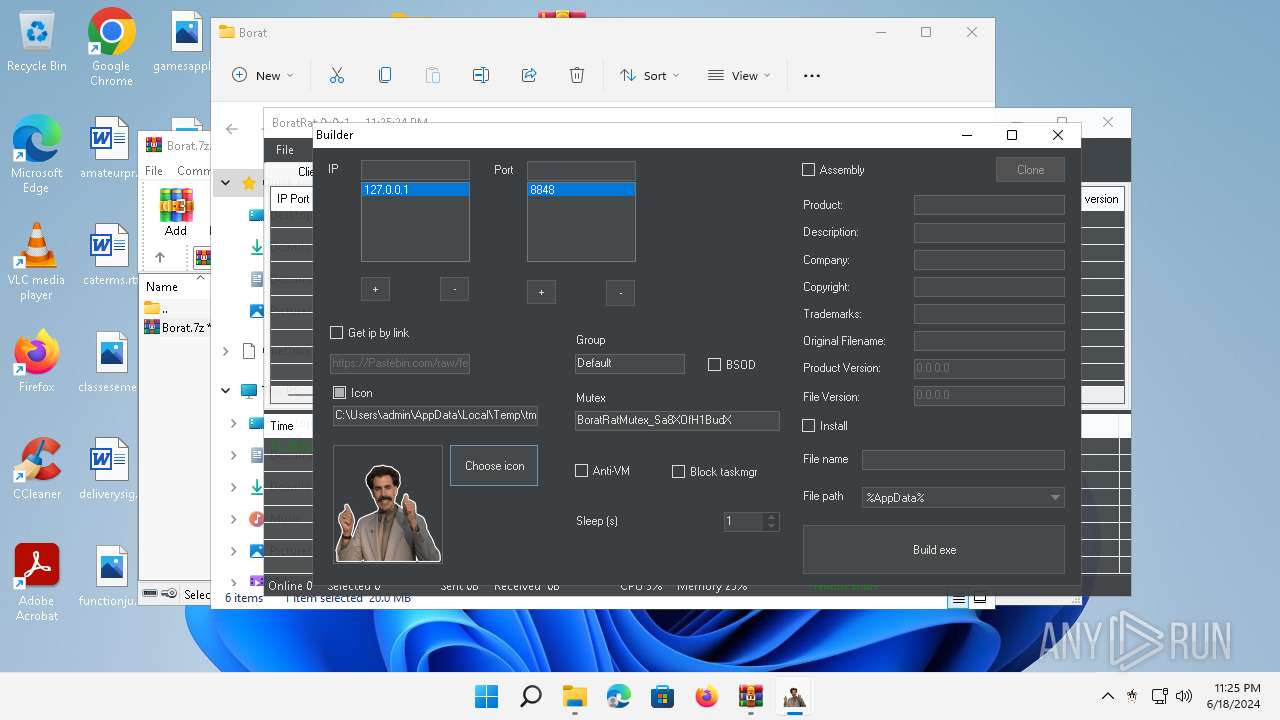
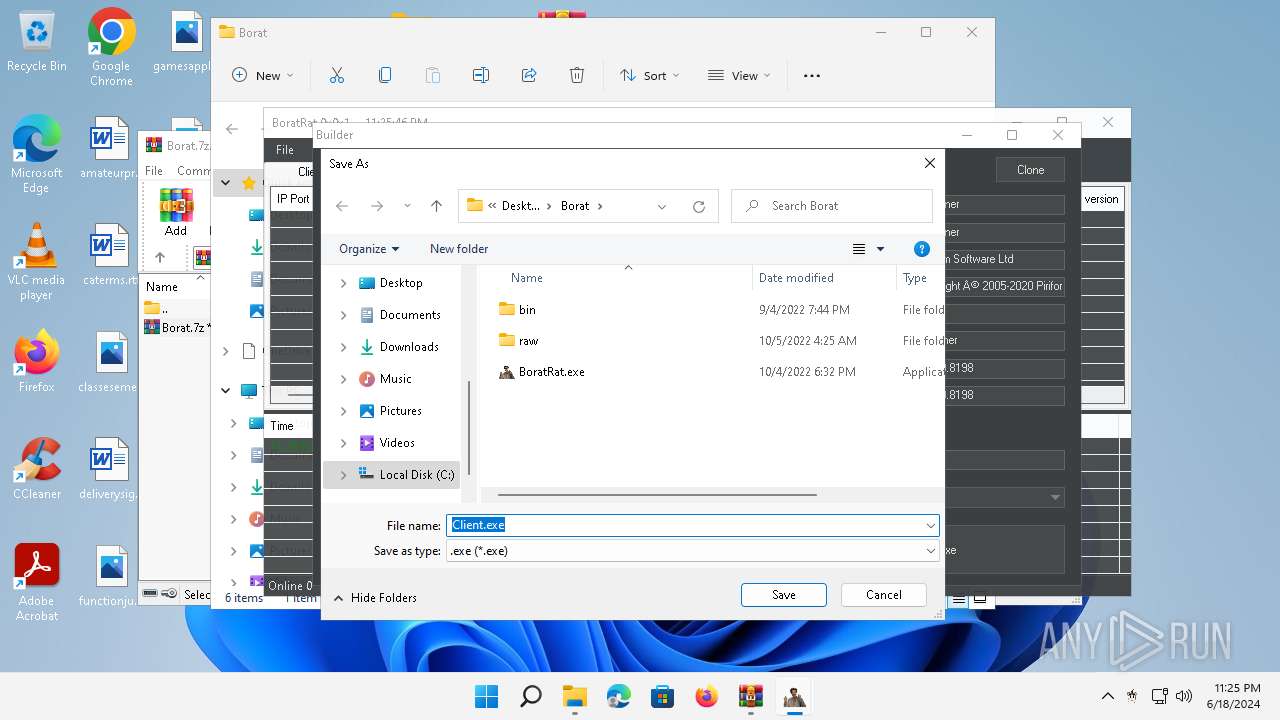
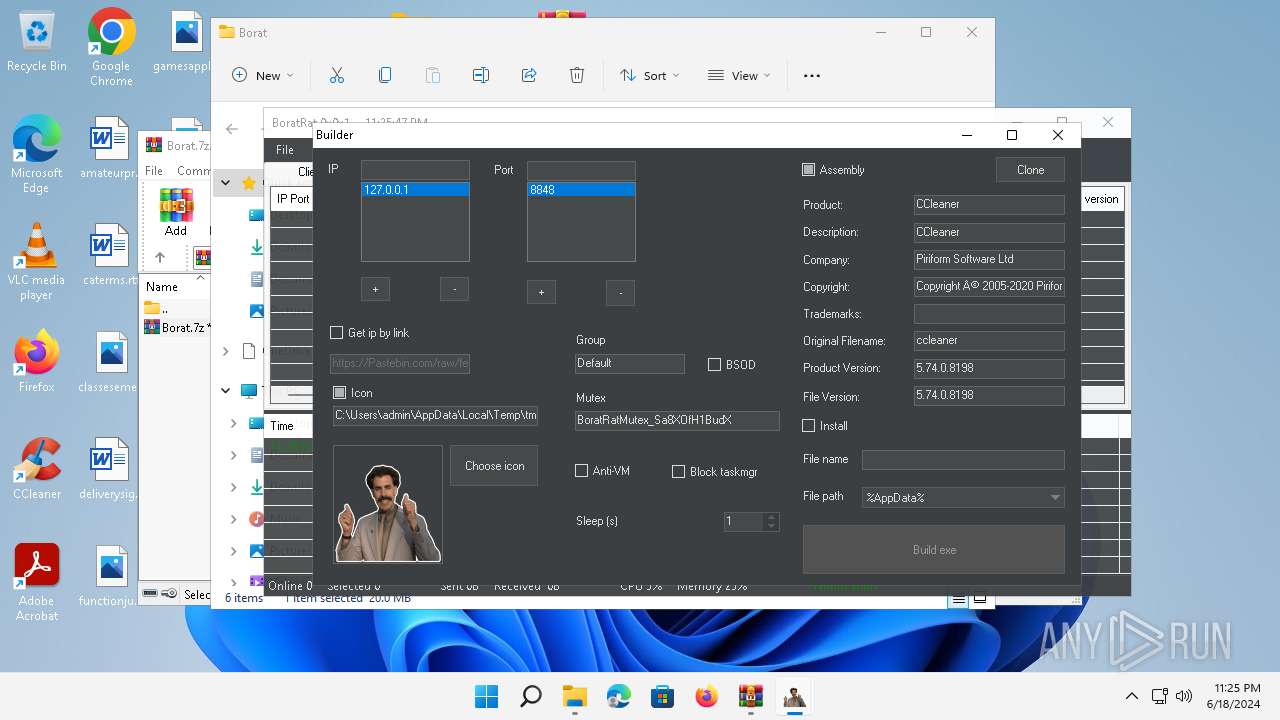
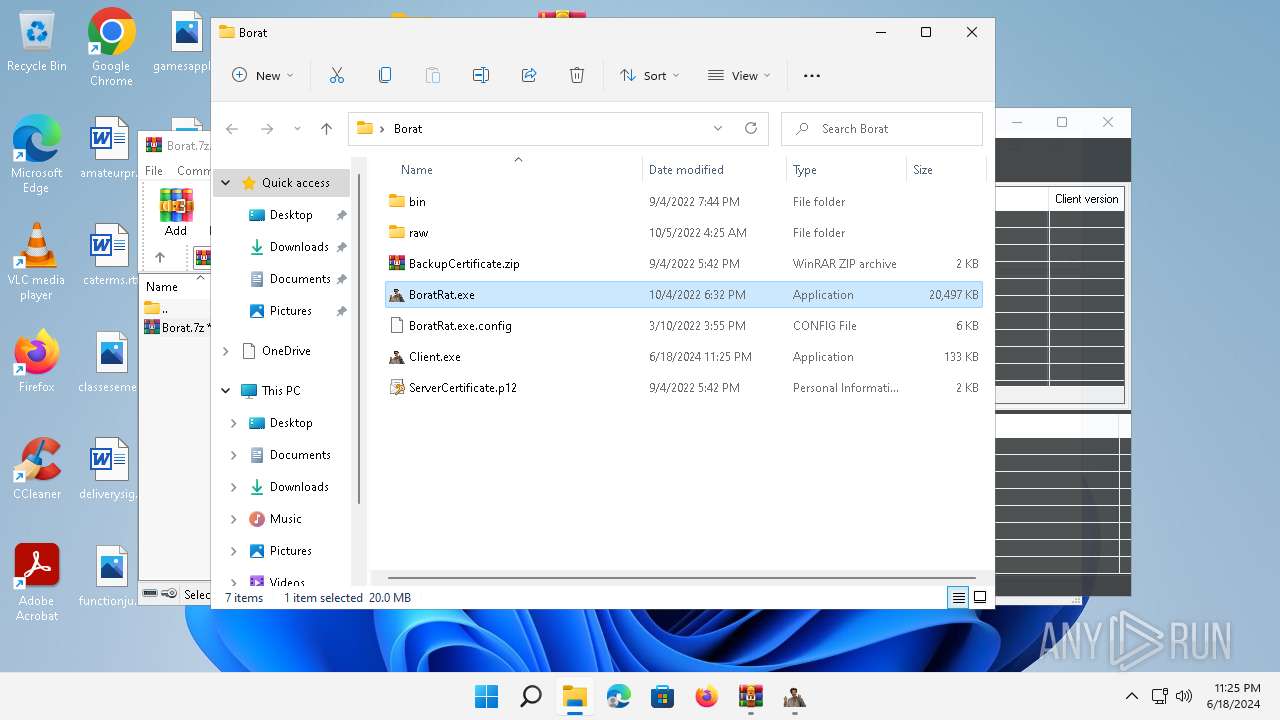
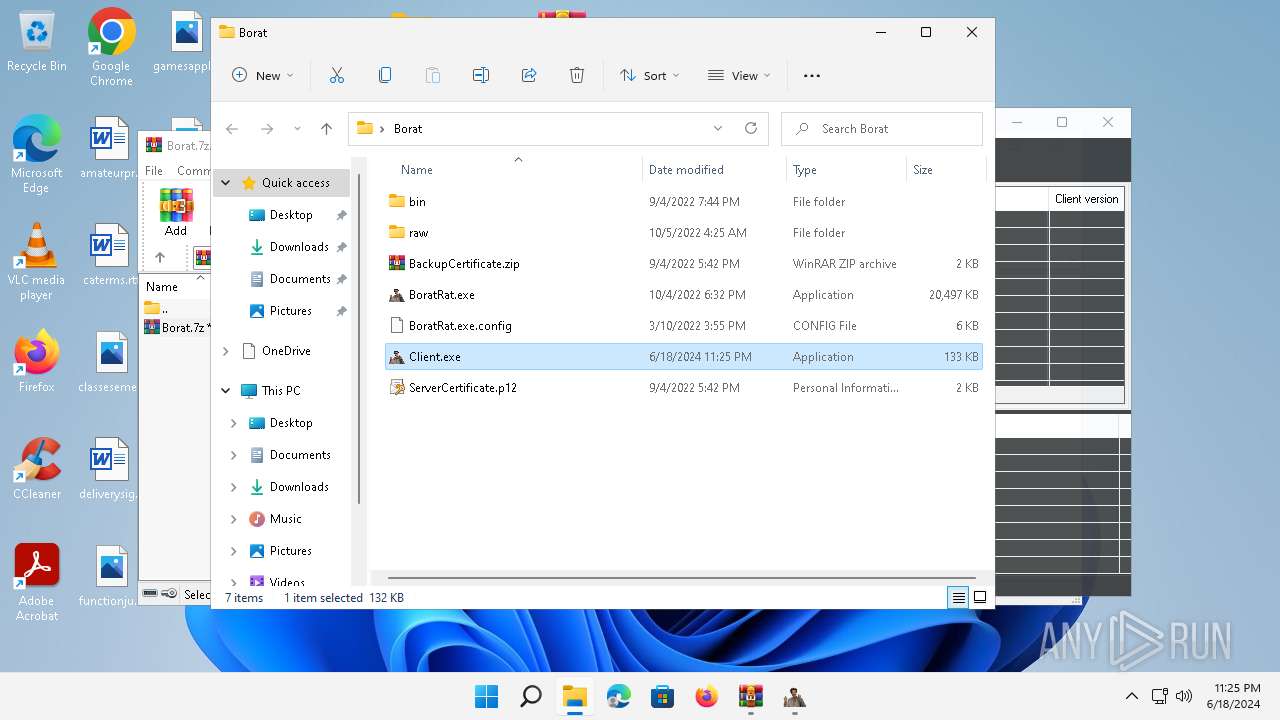
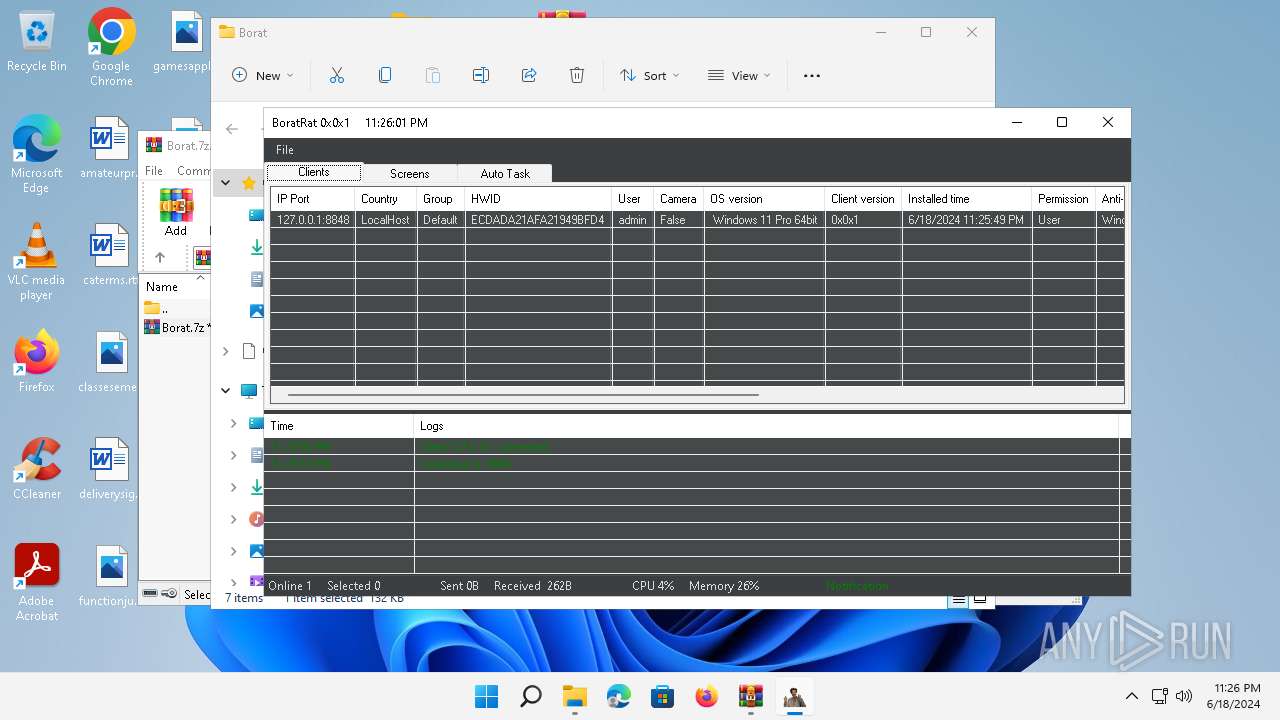
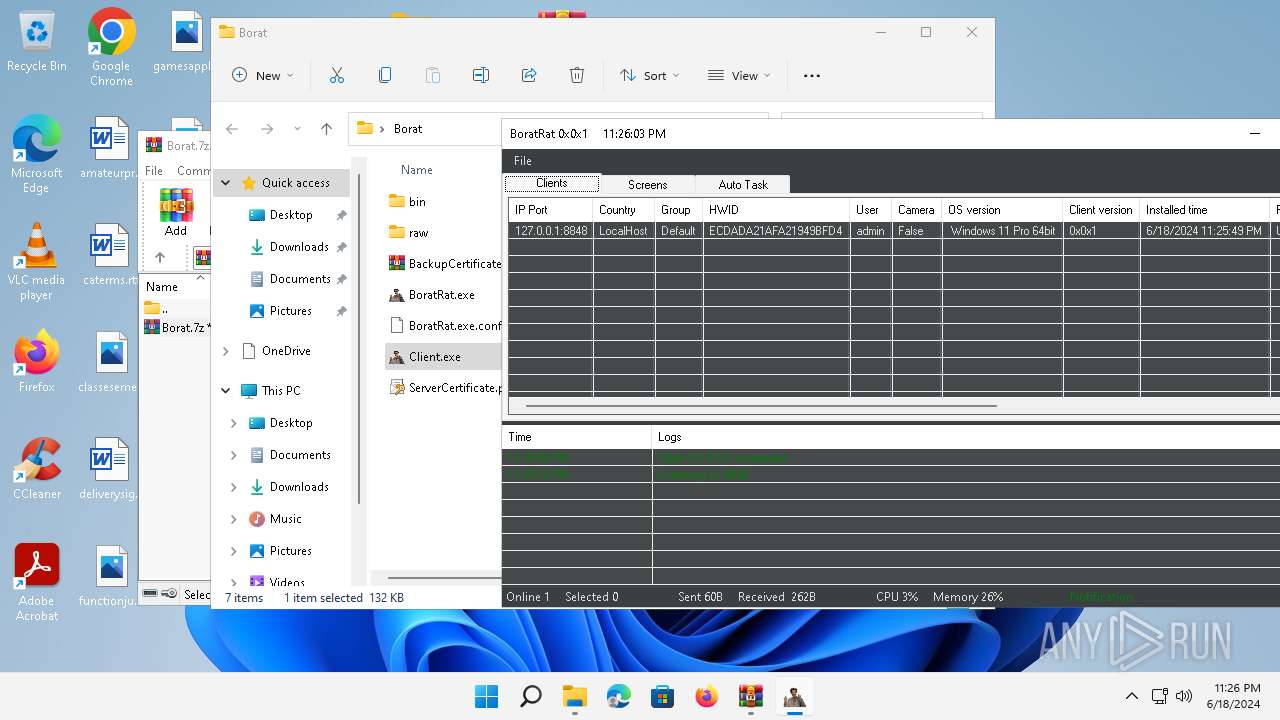
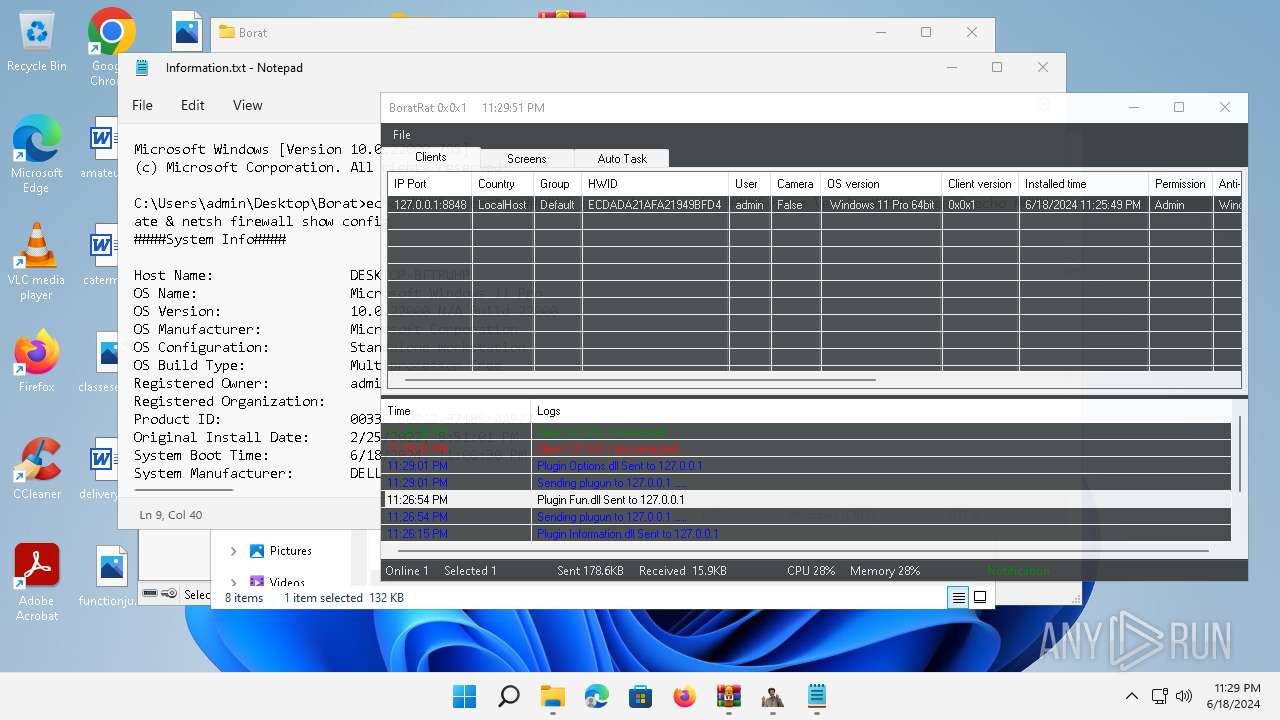
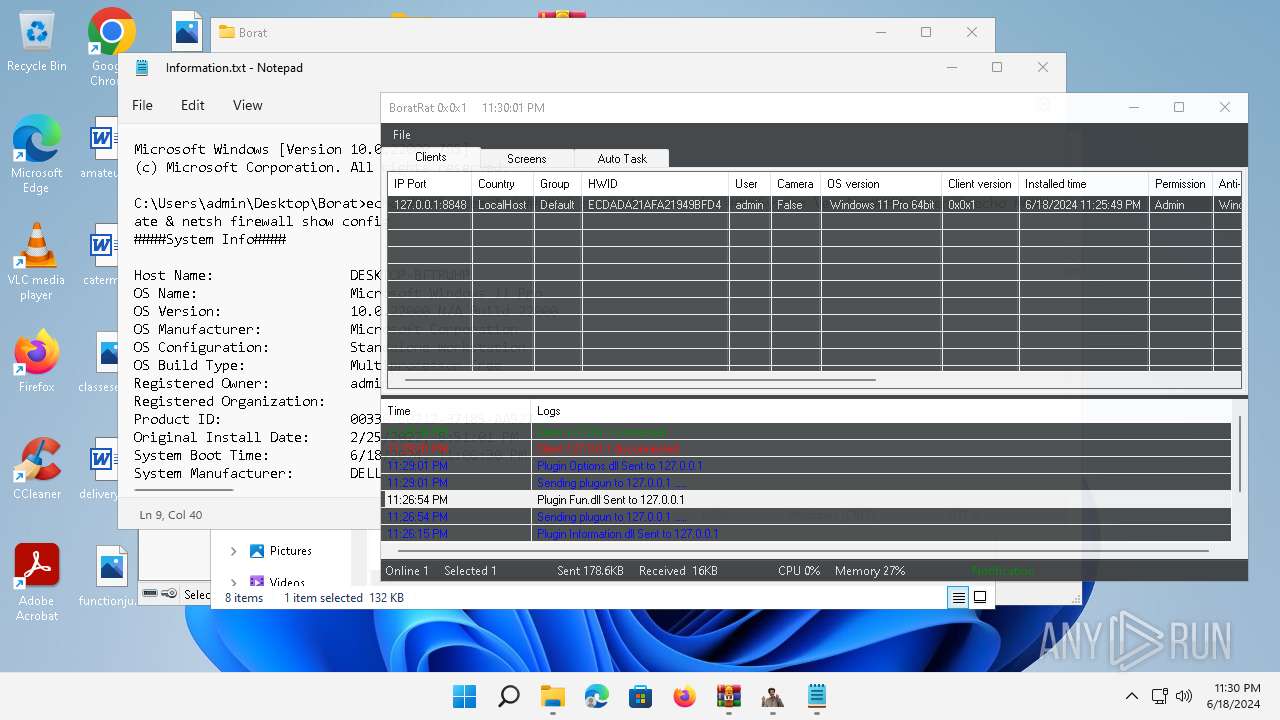
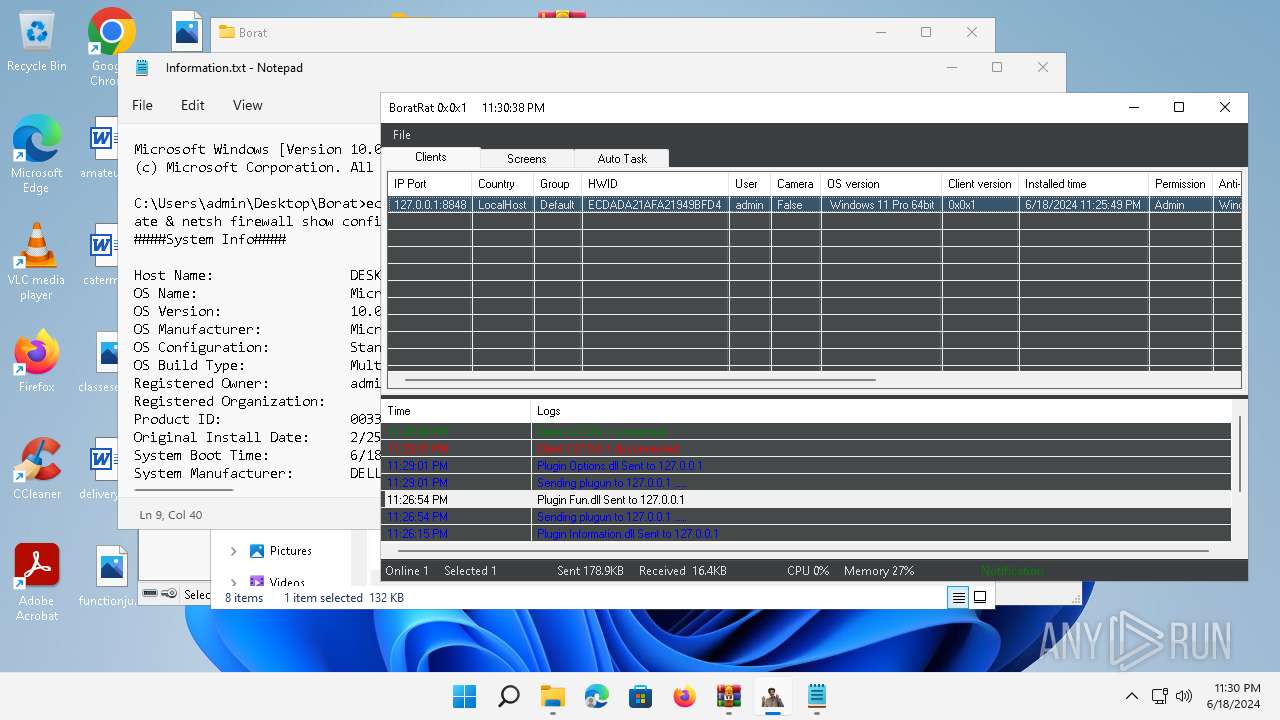
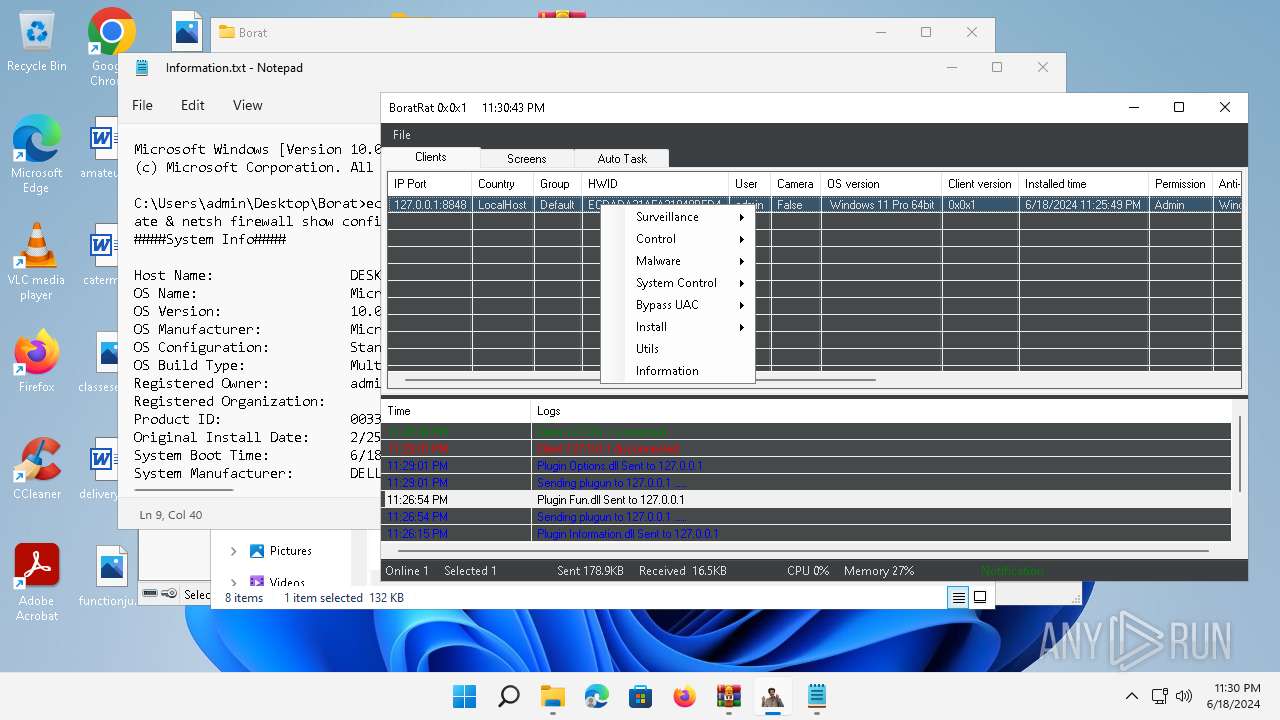
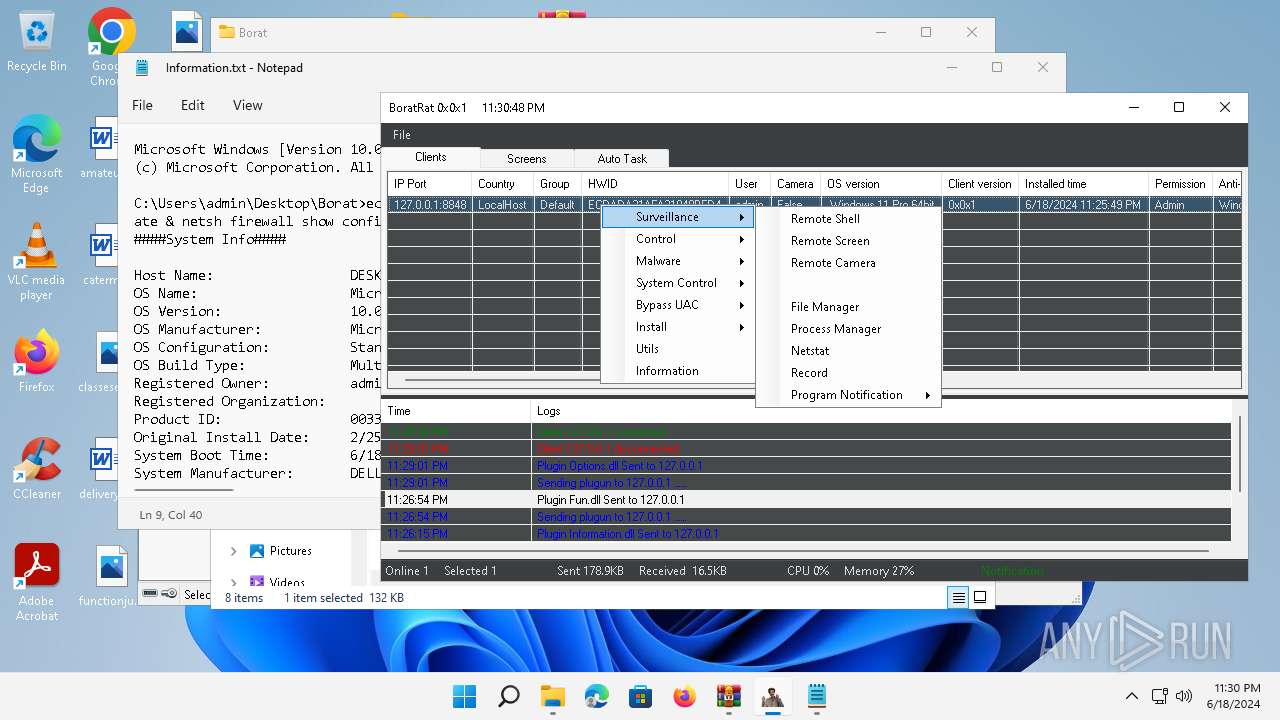
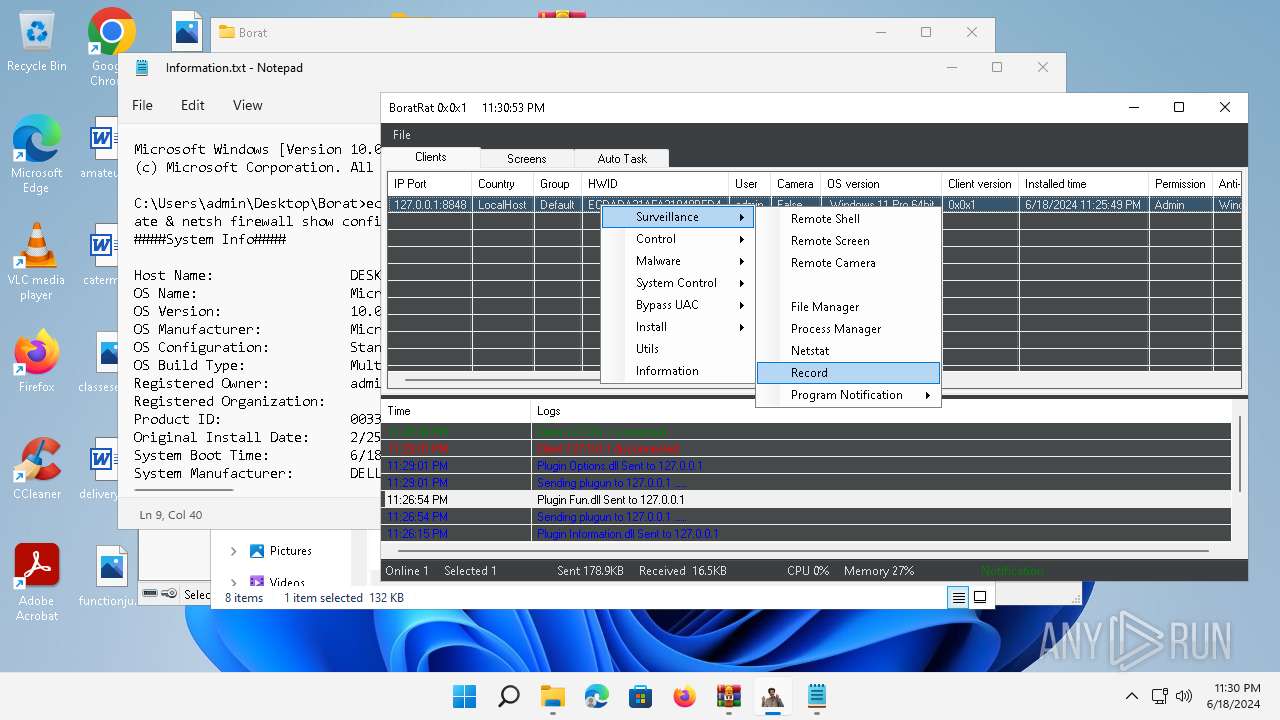
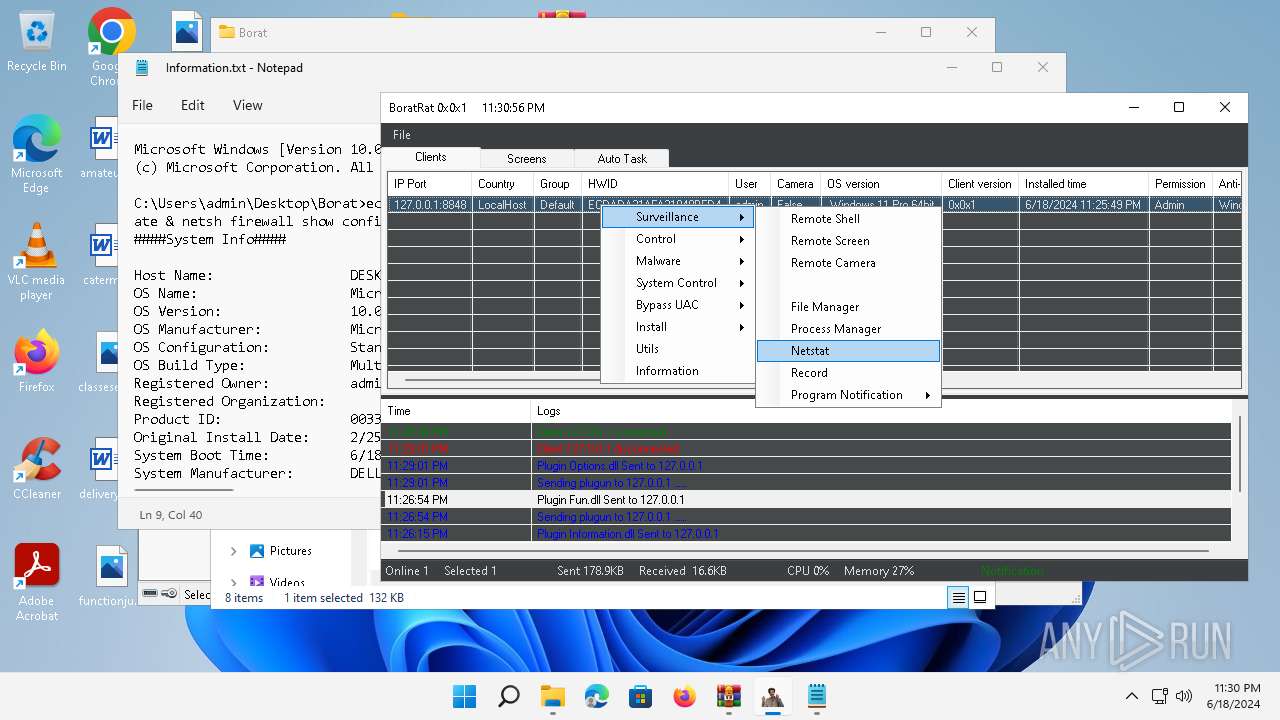
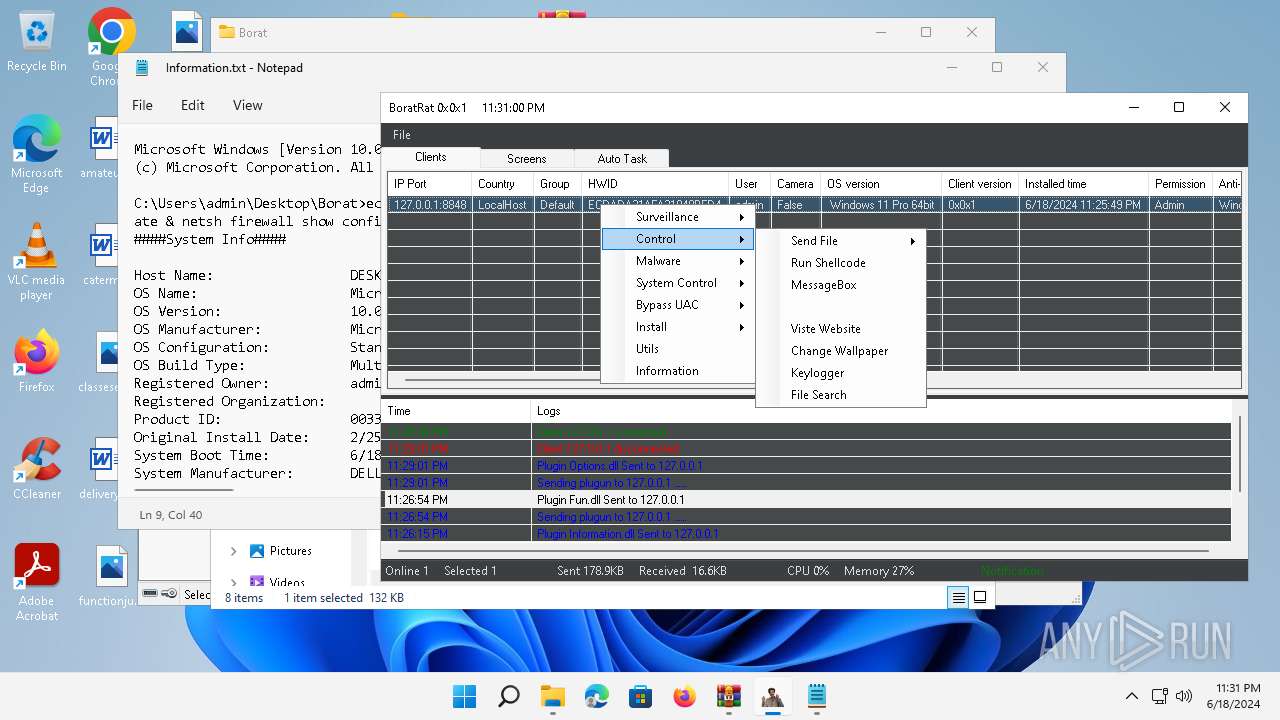
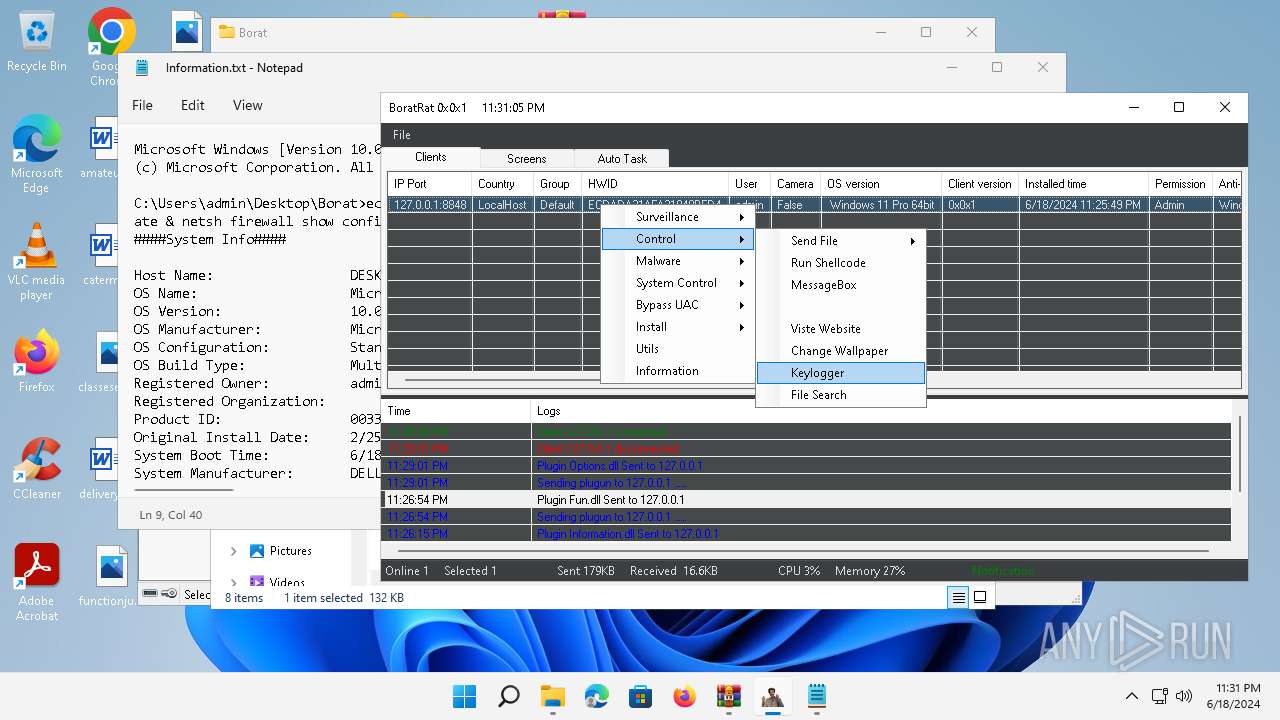
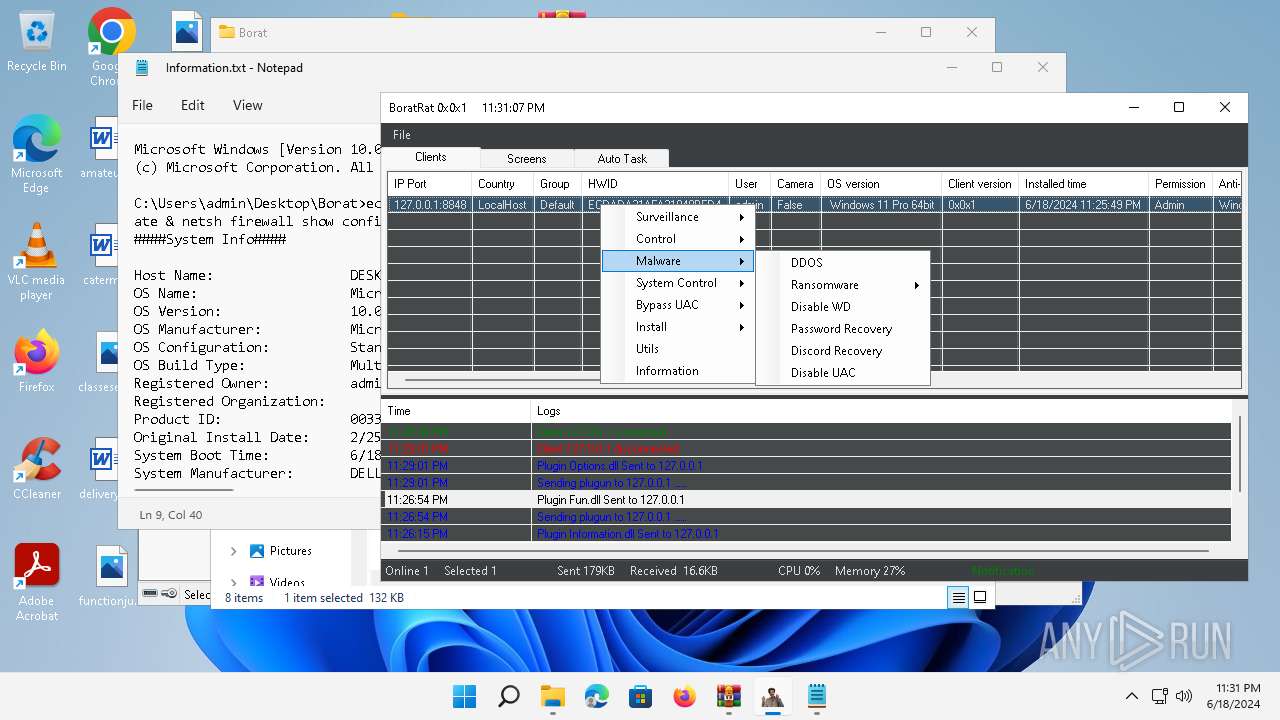
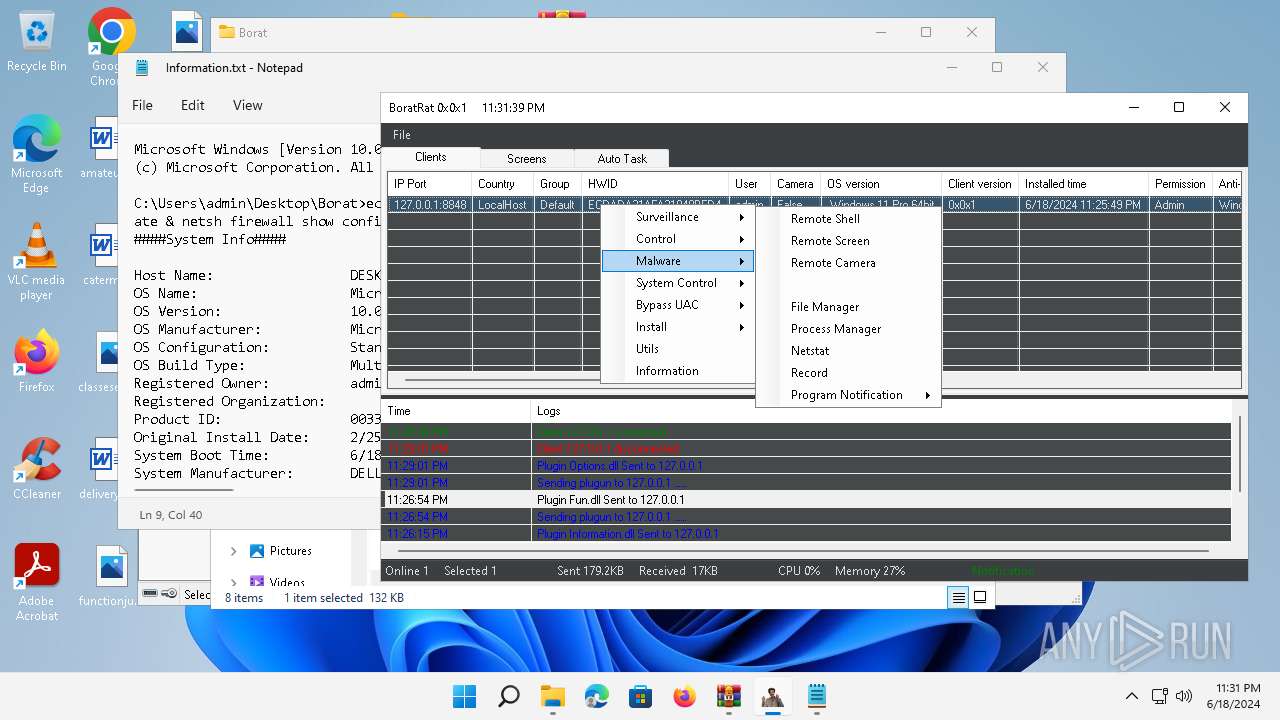
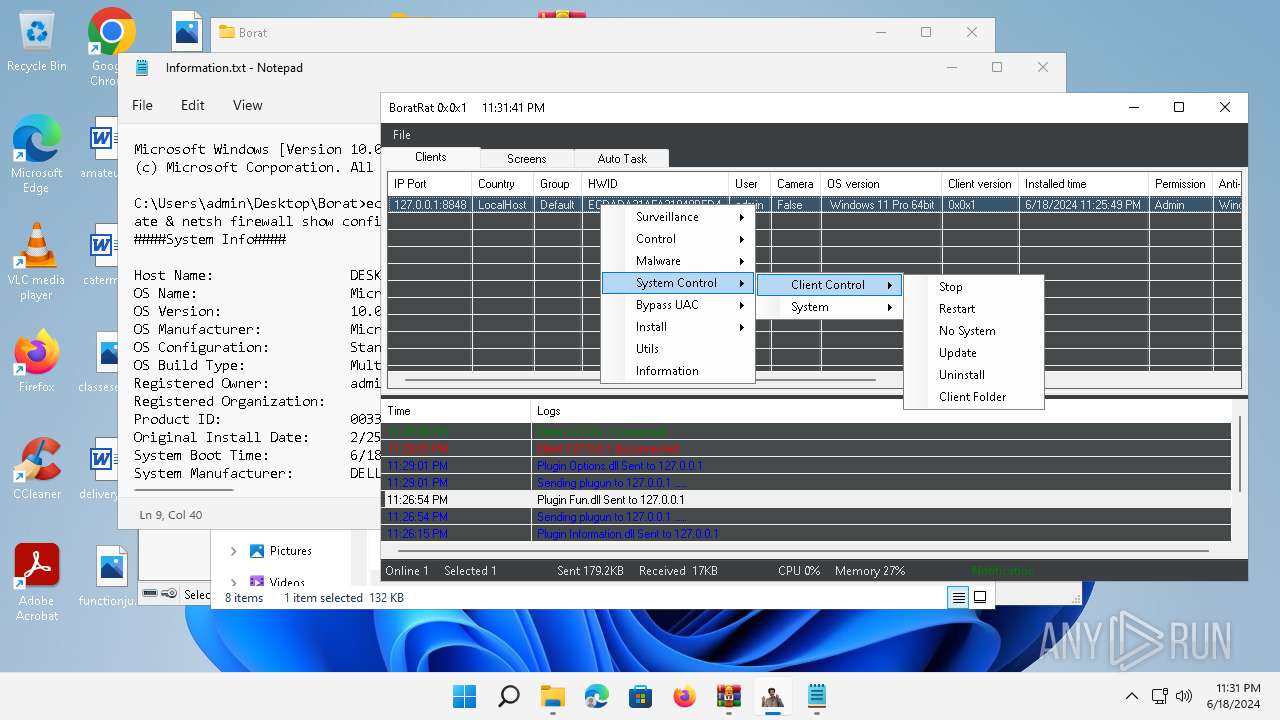
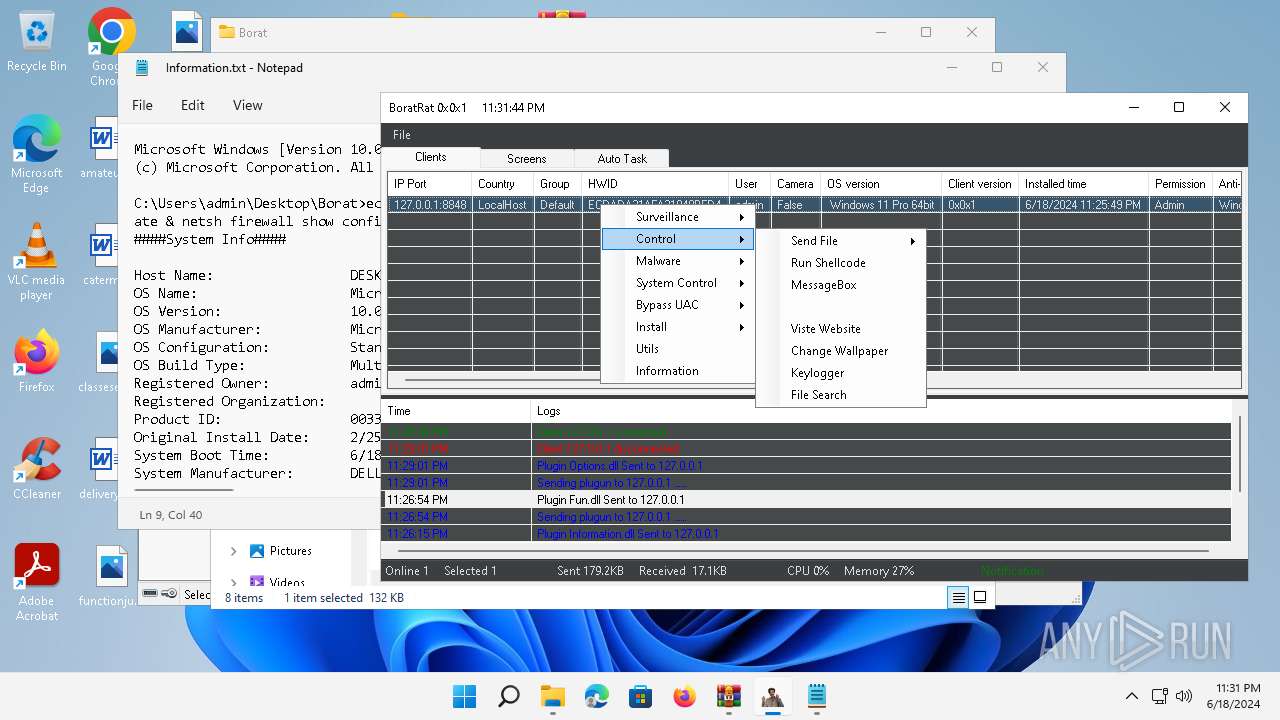
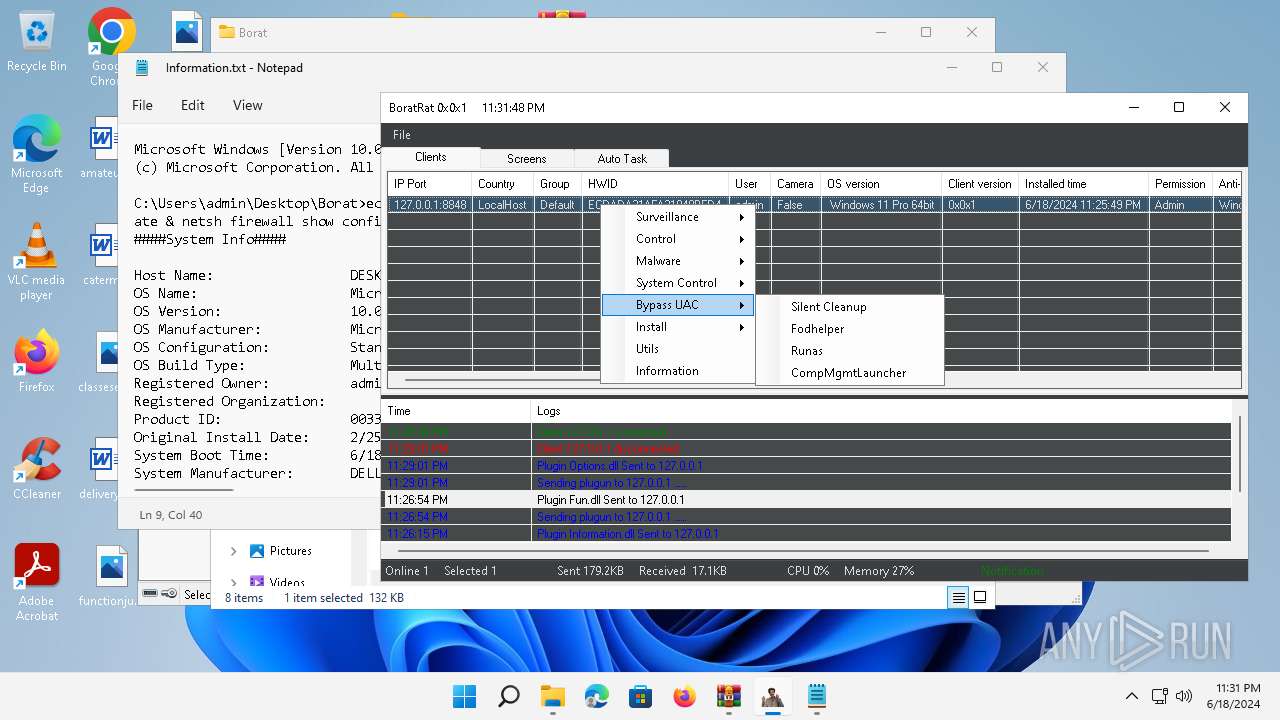
| File name: | Borat.7z.zip |
| Full analysis: | https://app.any.run/tasks/8e5cbea8-be5c-467c-bcc7-5fed51a00e1f |
| Verdict: | Malicious activity |
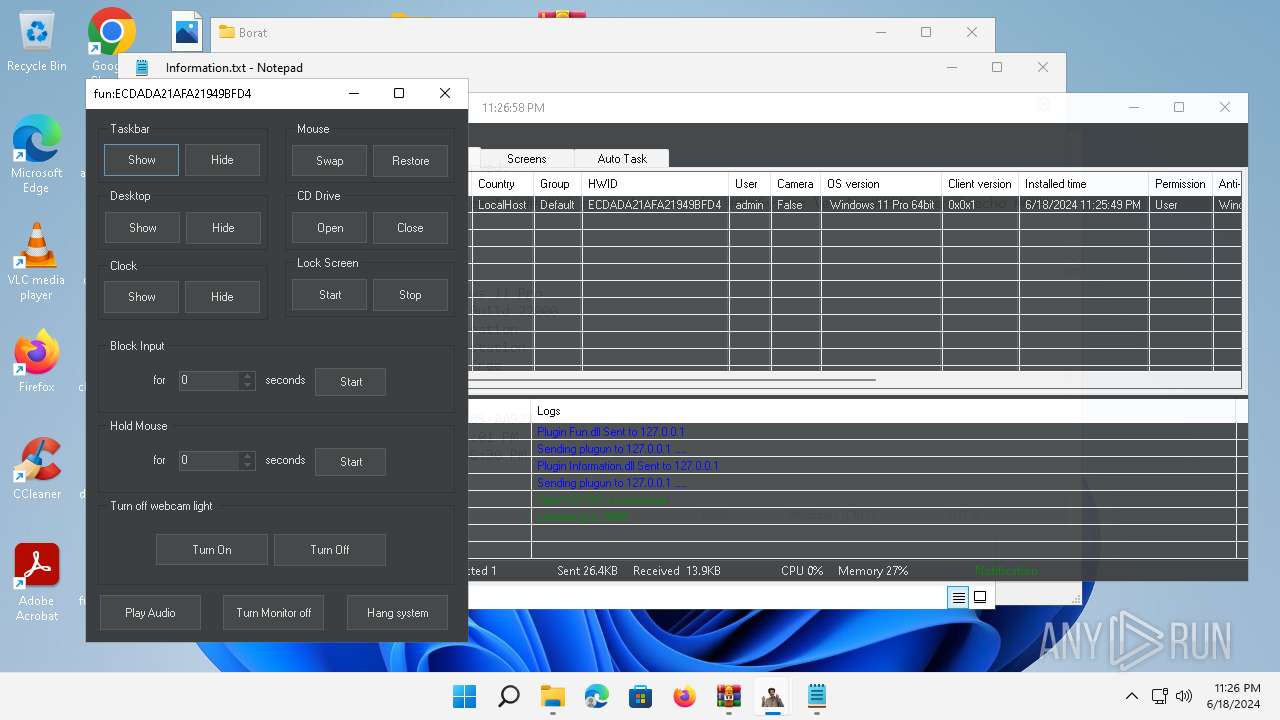
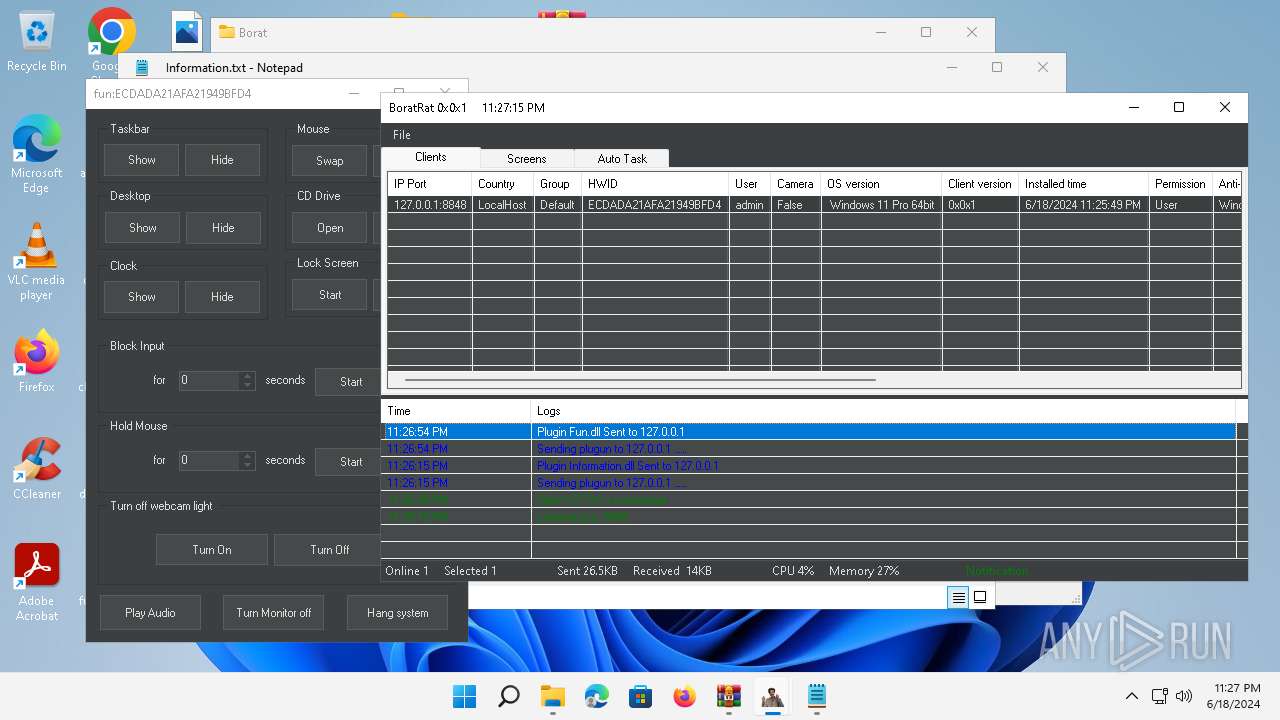
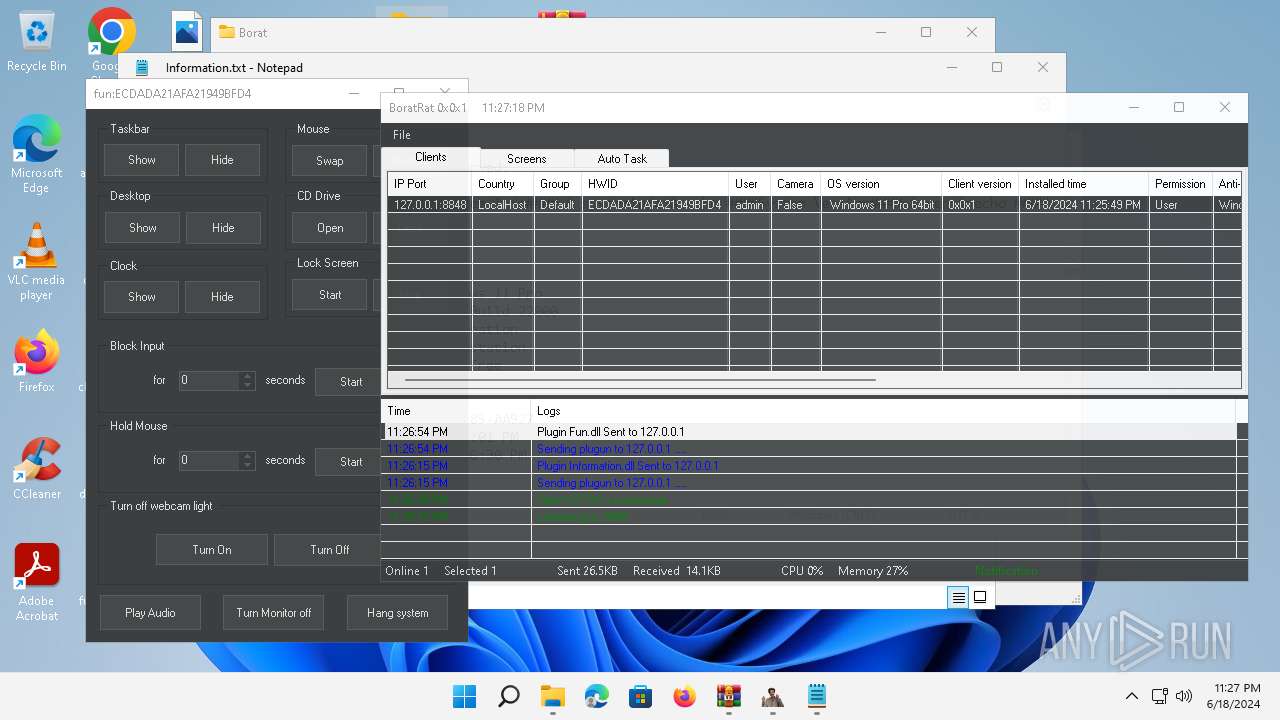
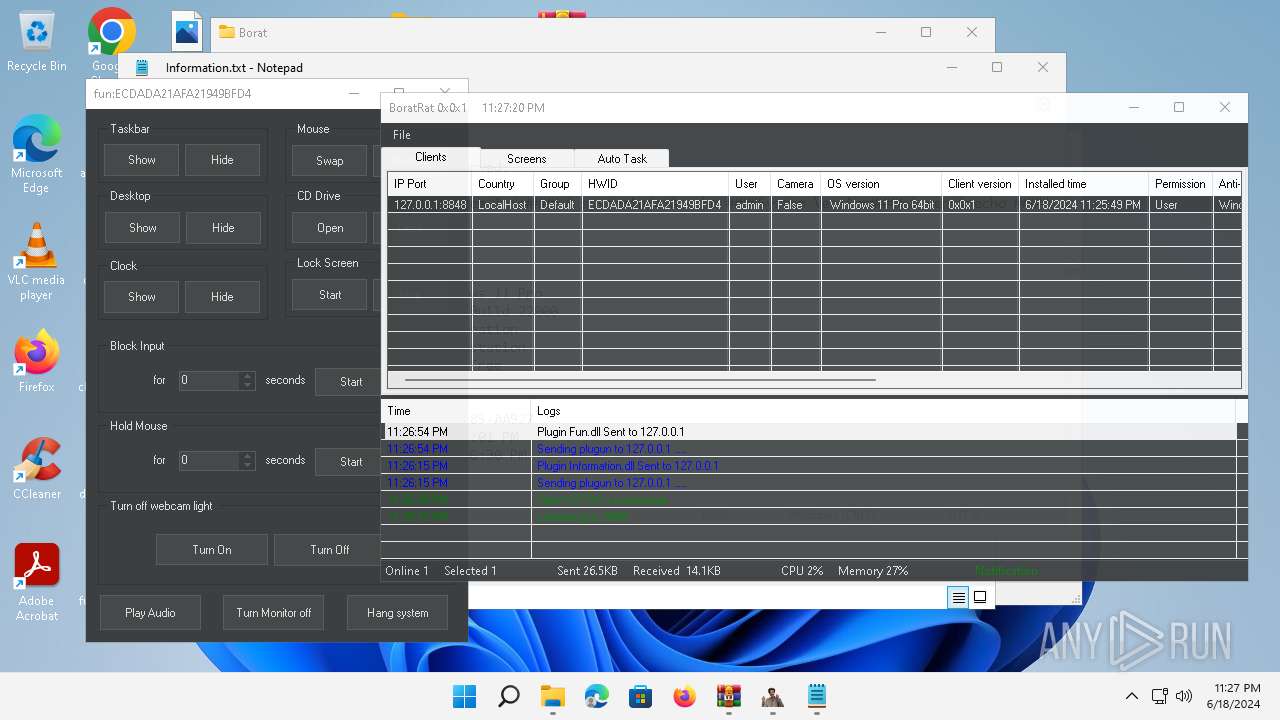
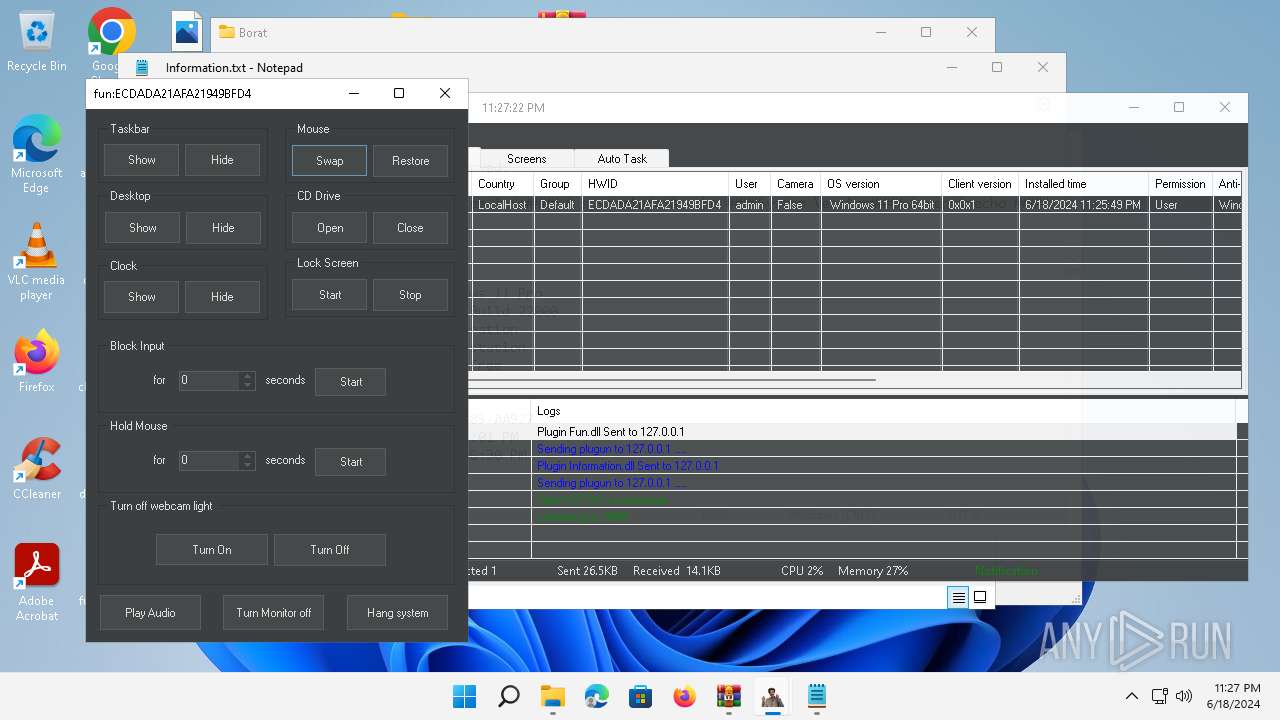
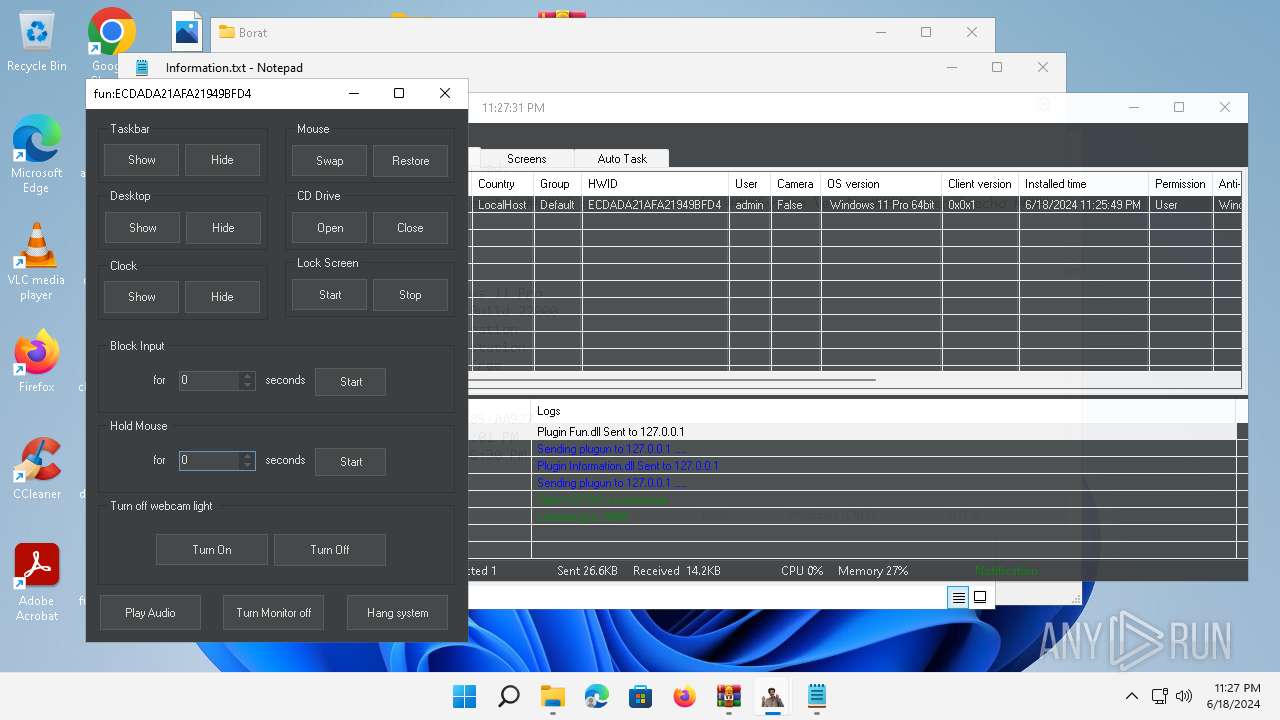
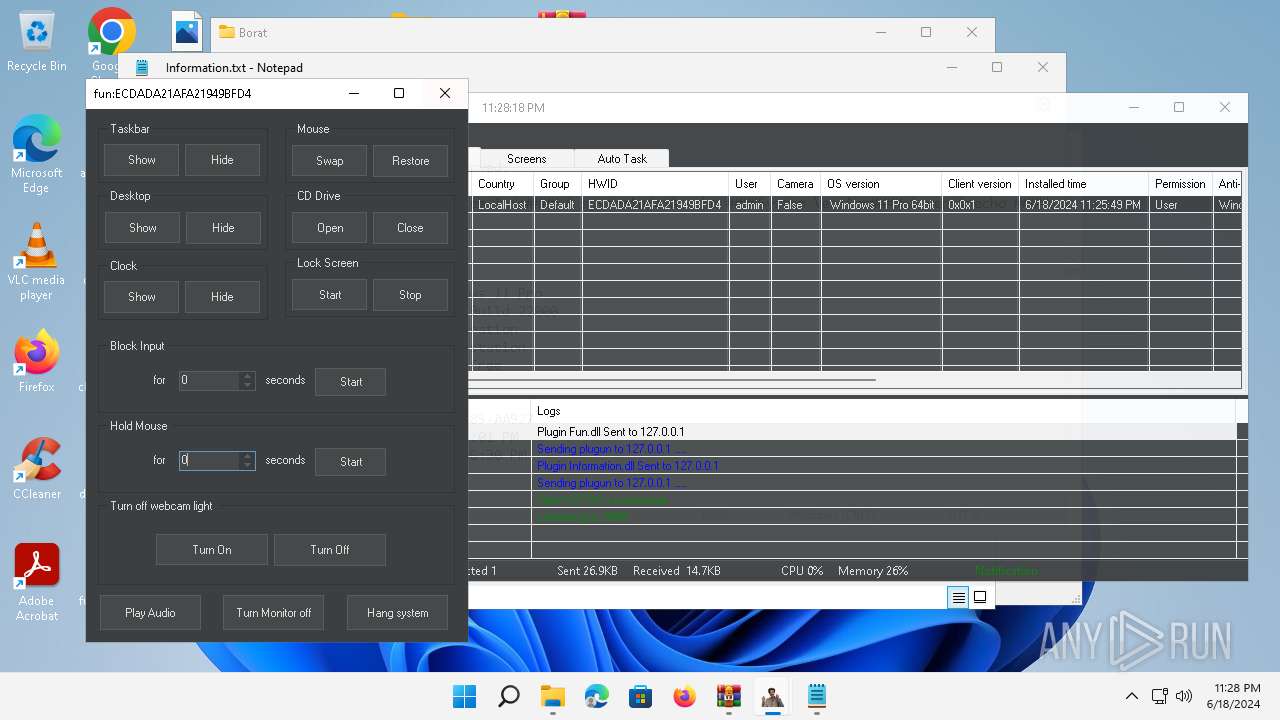
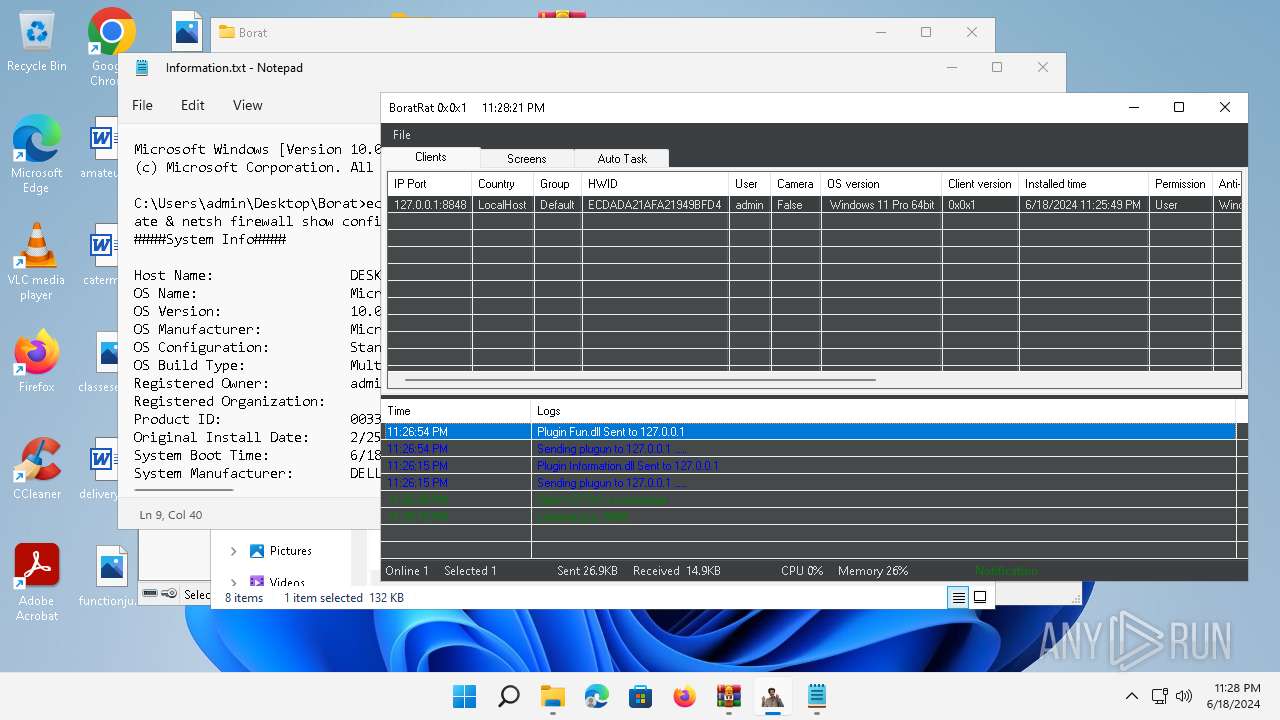
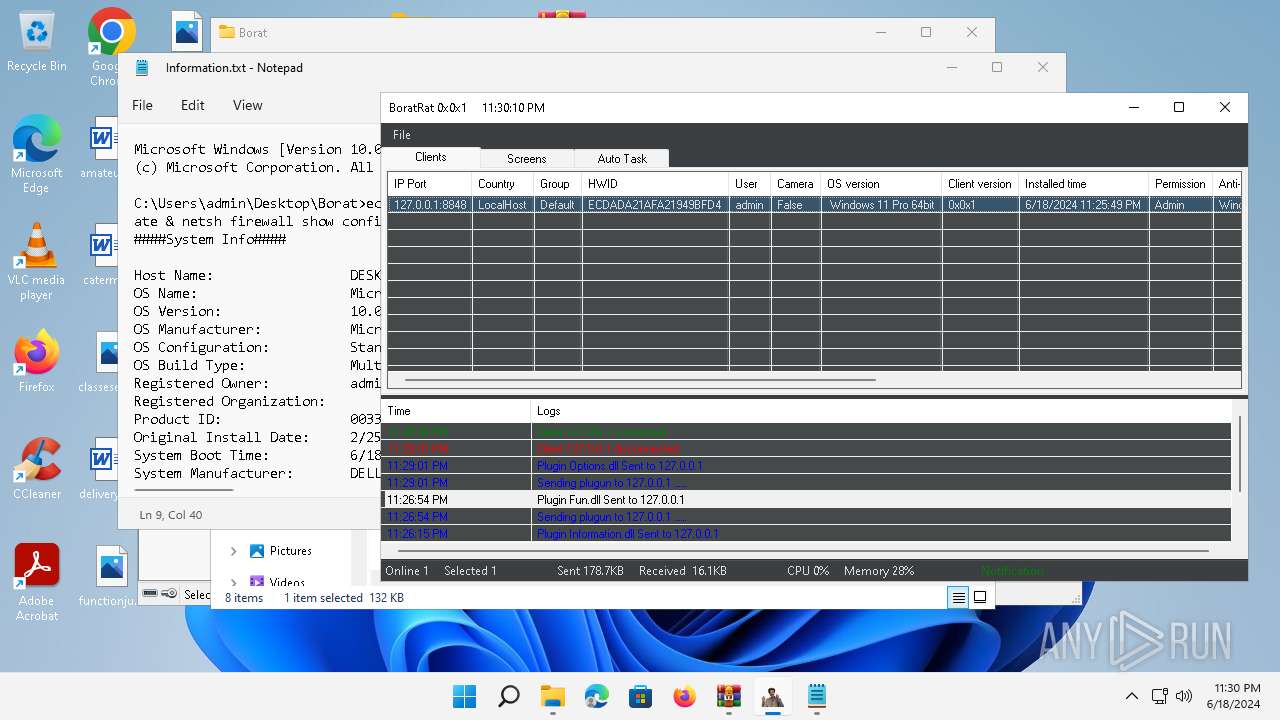
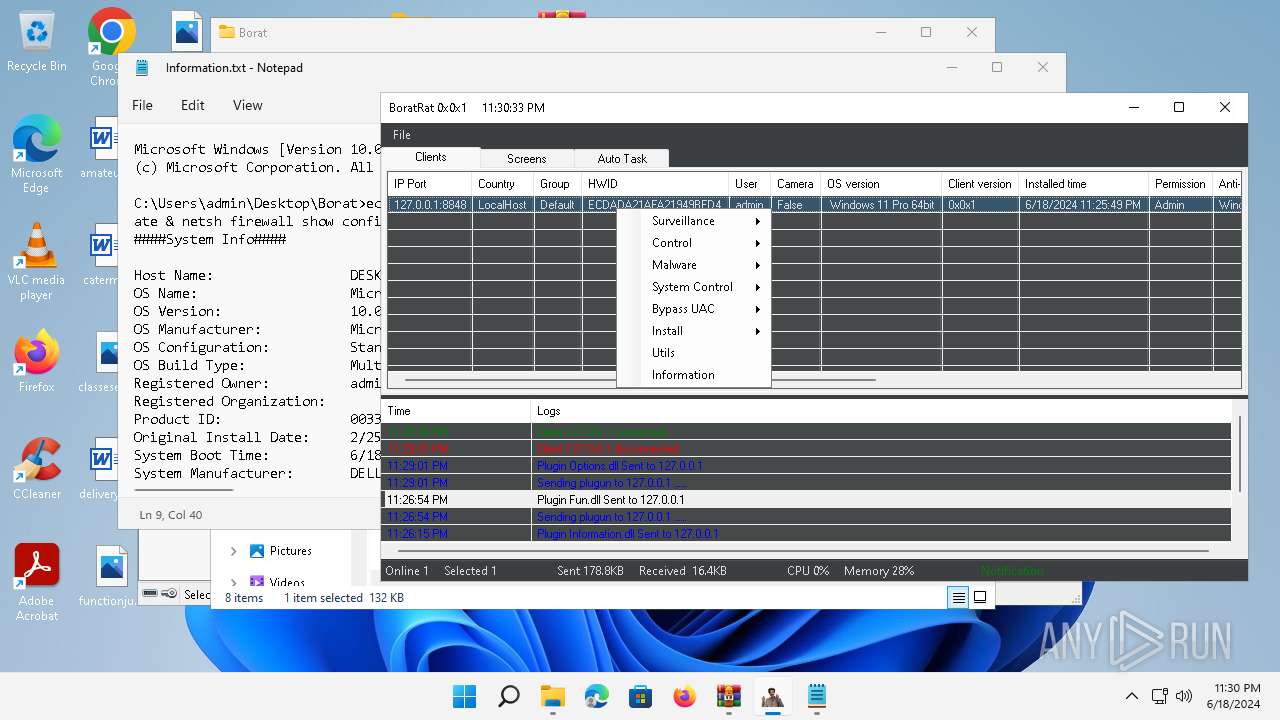
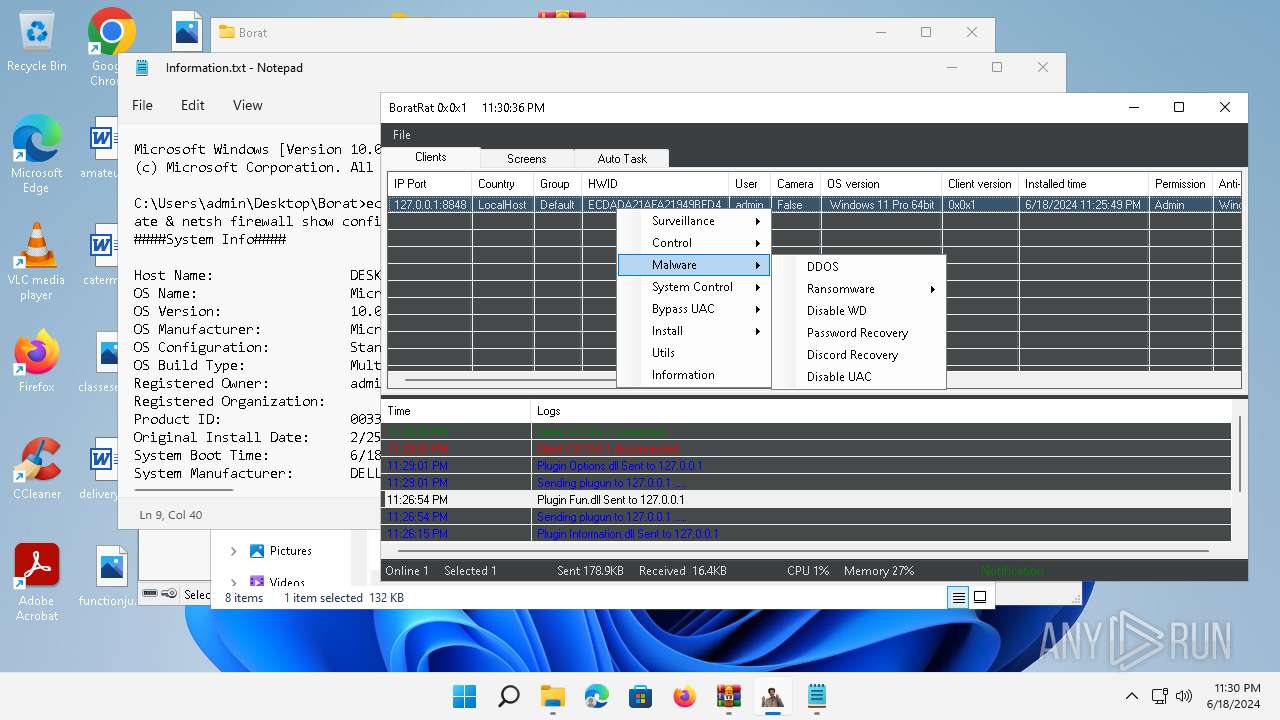
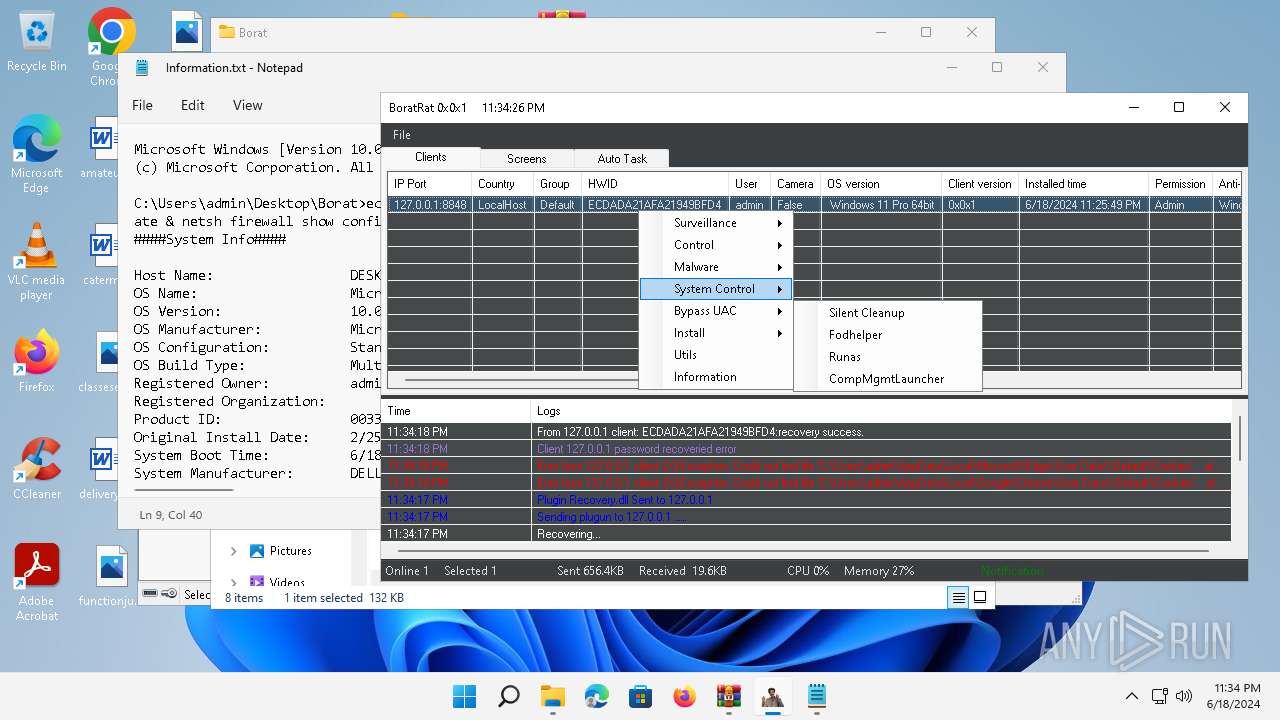
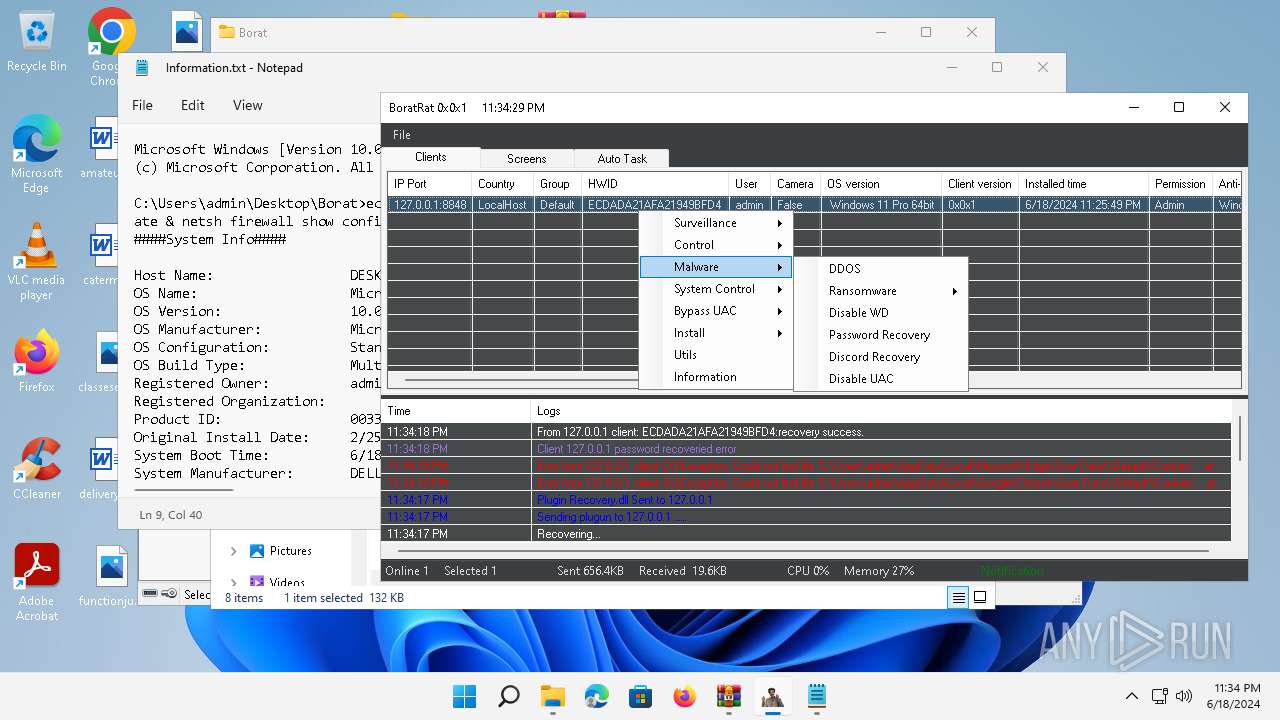
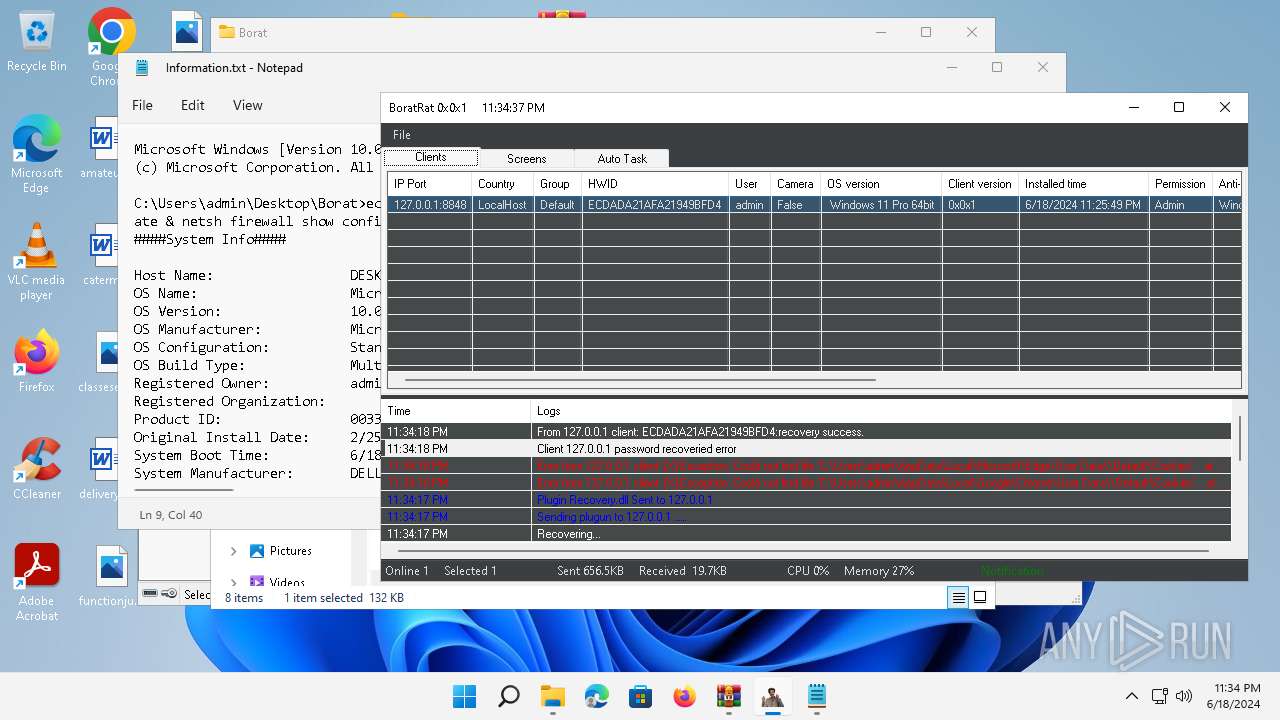
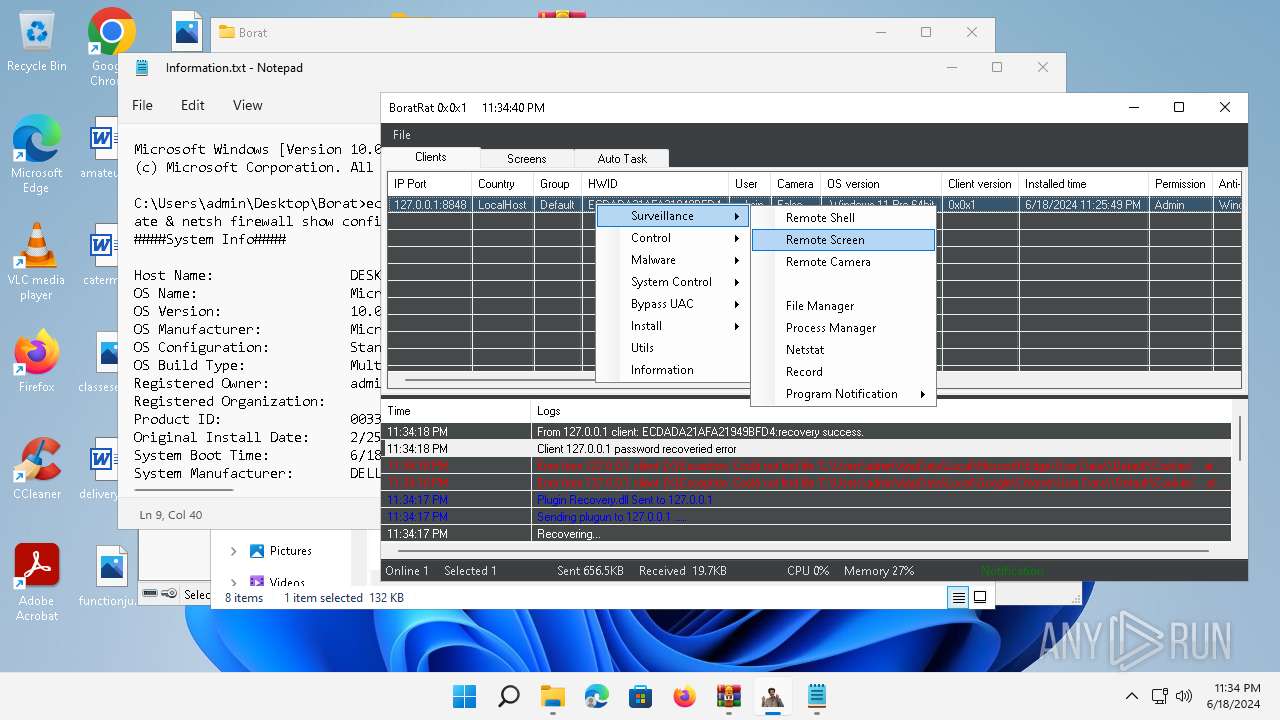
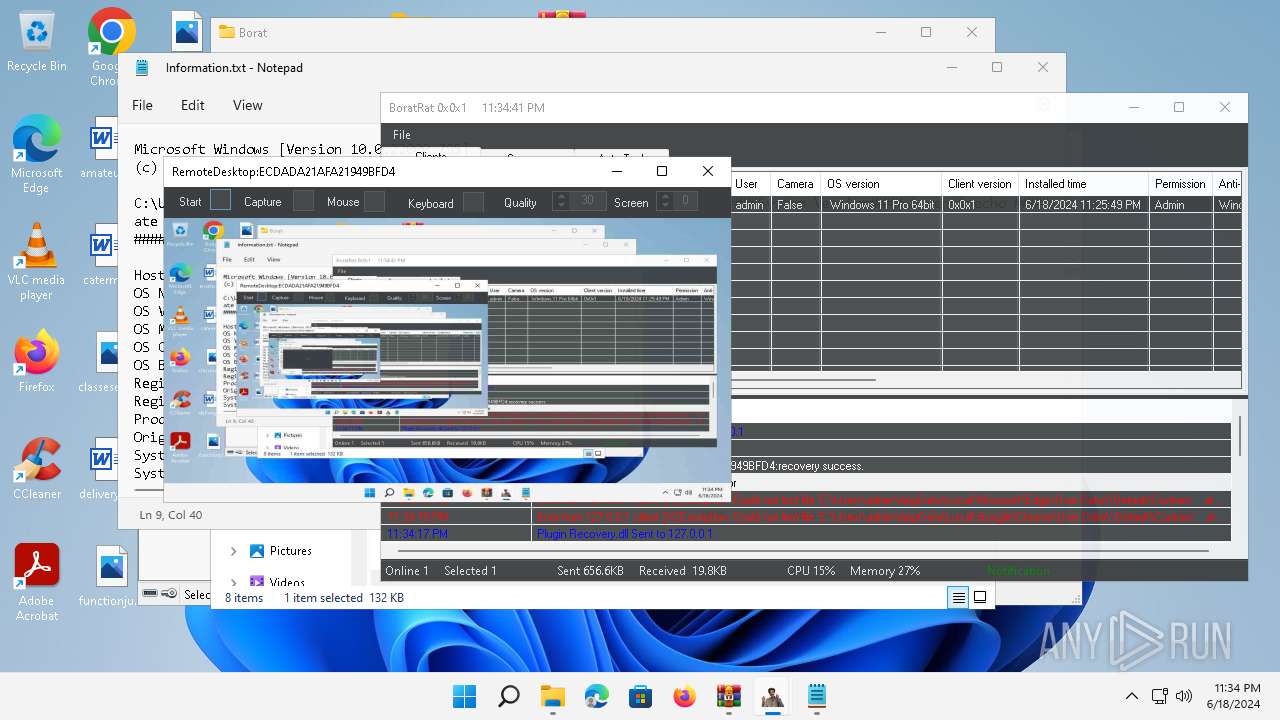
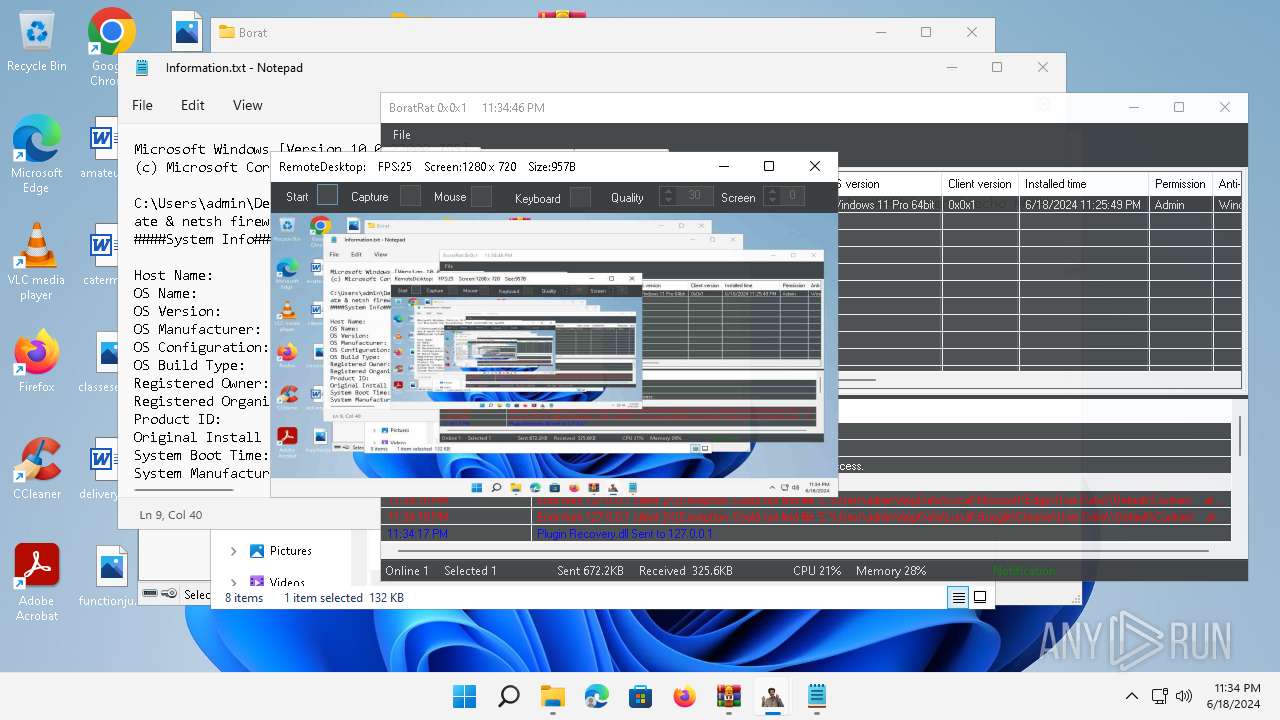
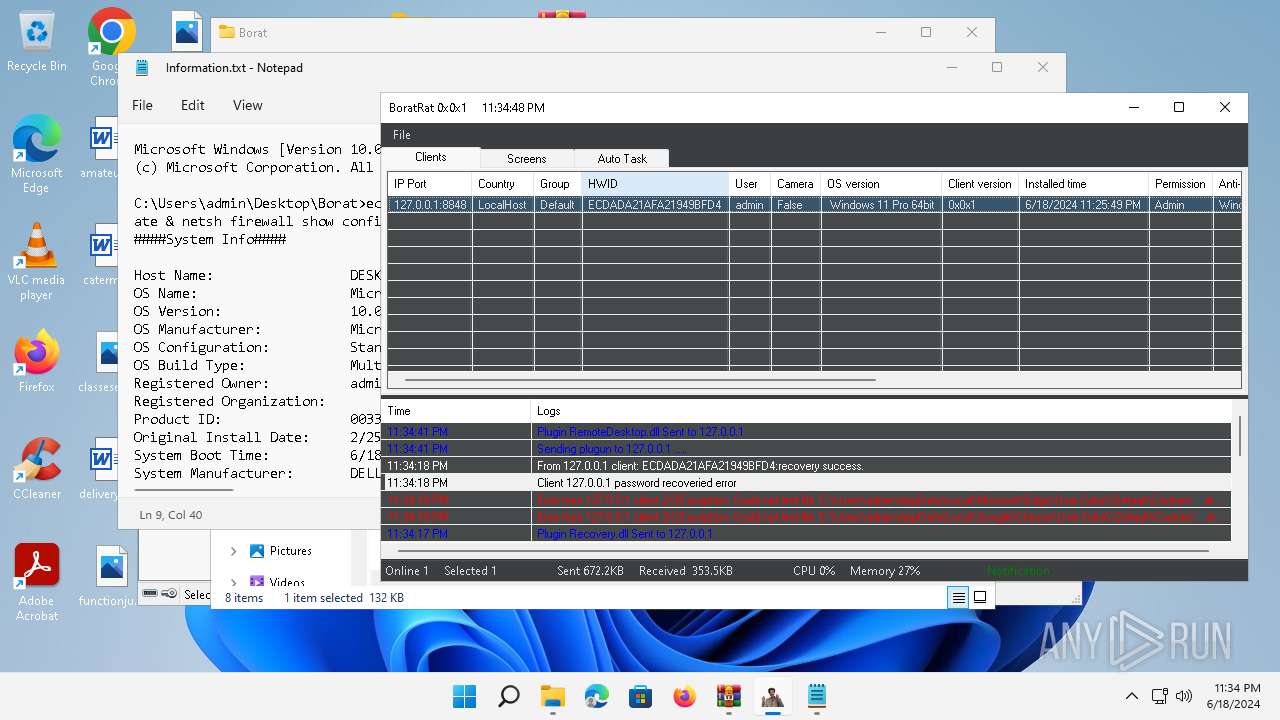
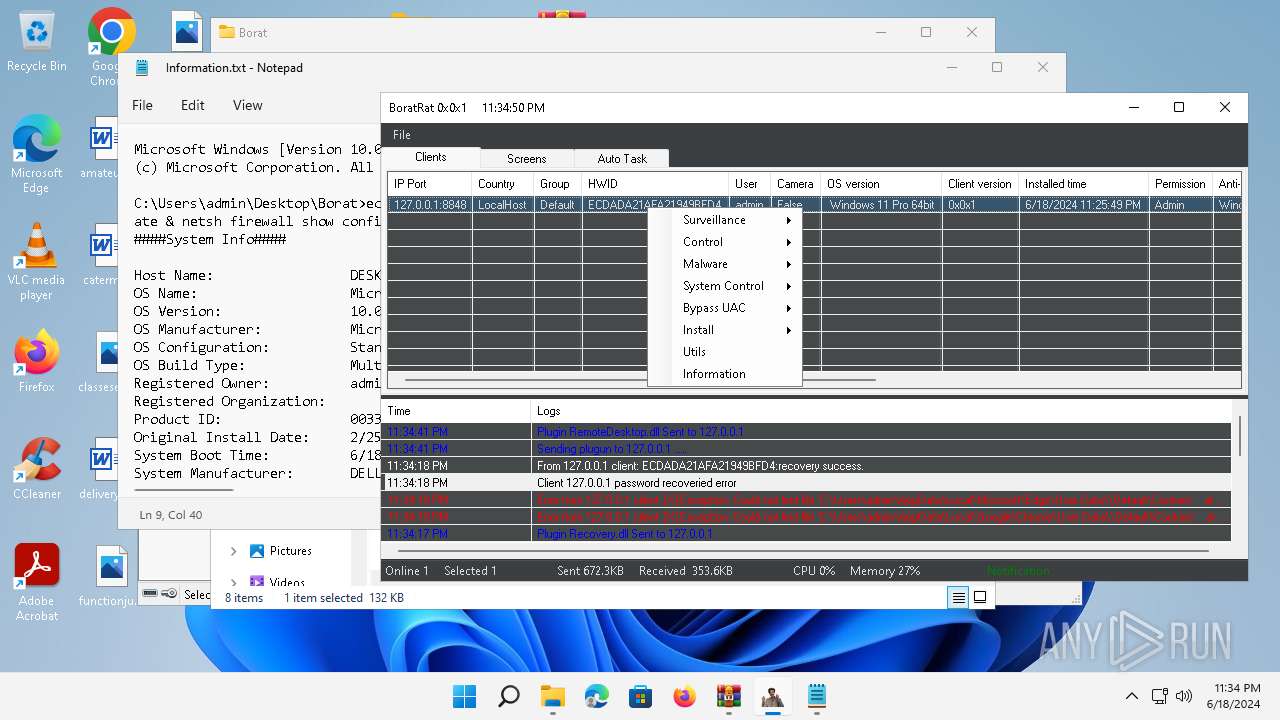
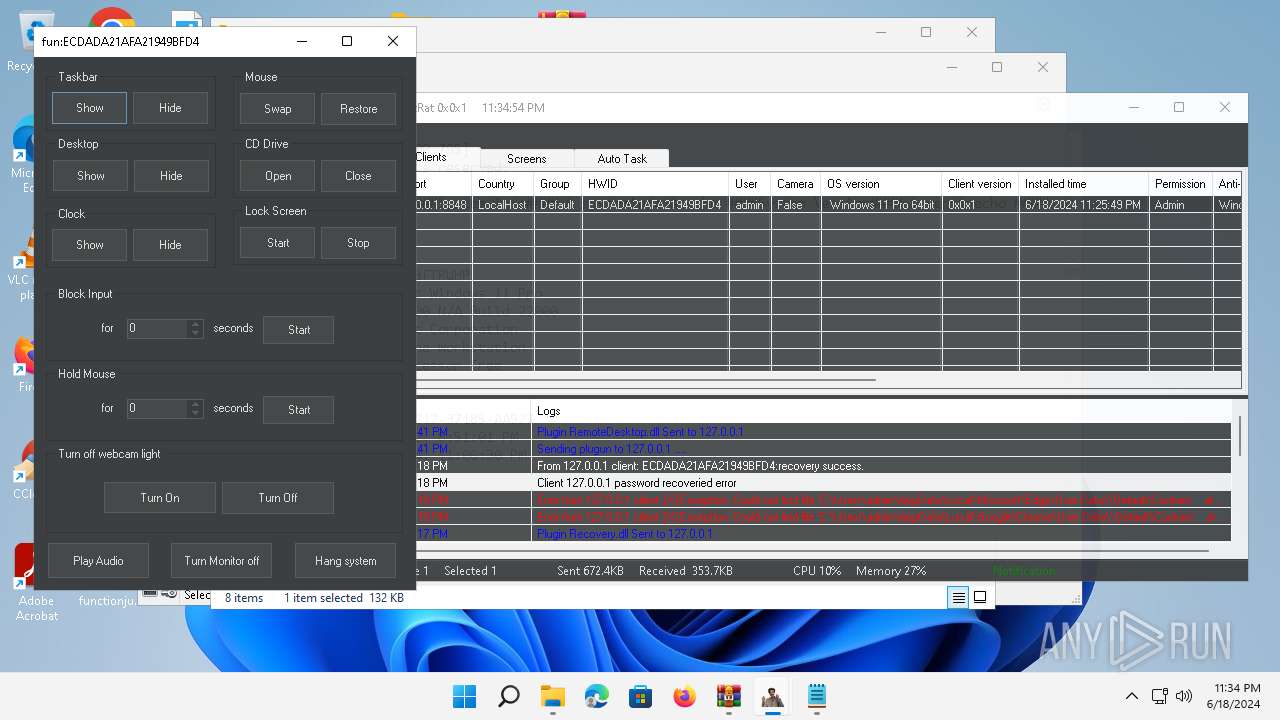
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | June 18, 2024, 23:24:22 |
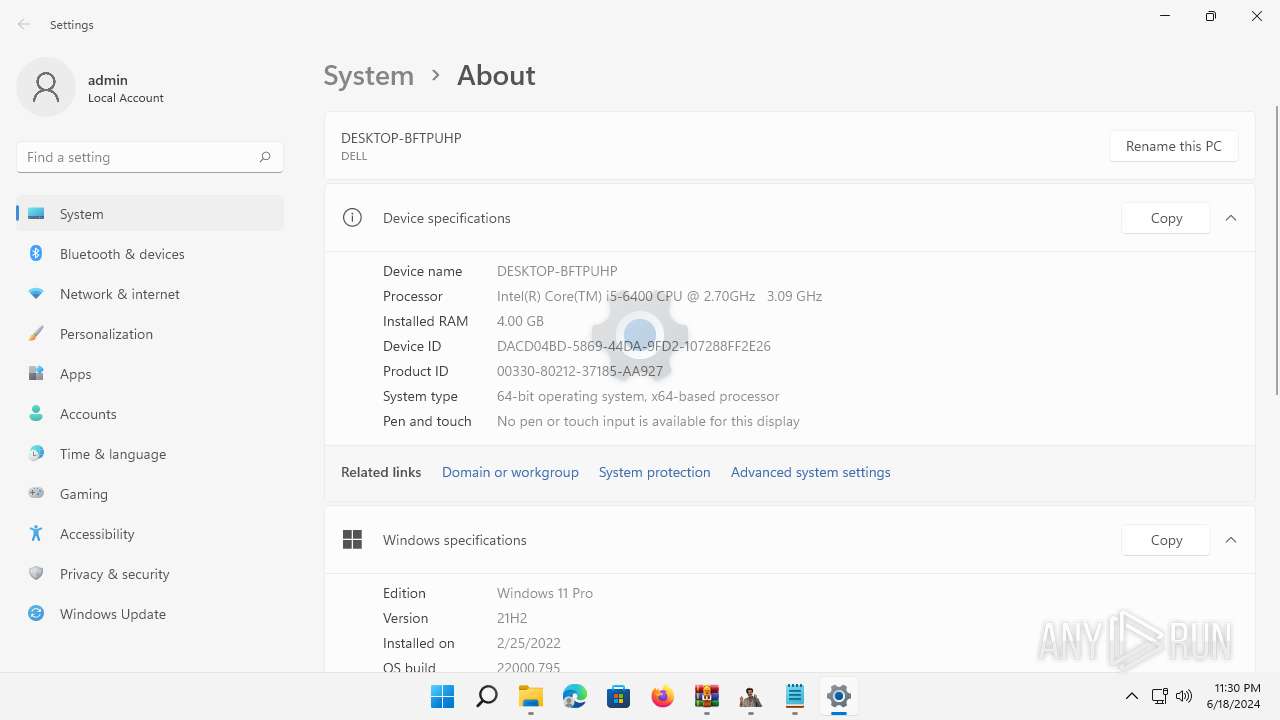
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
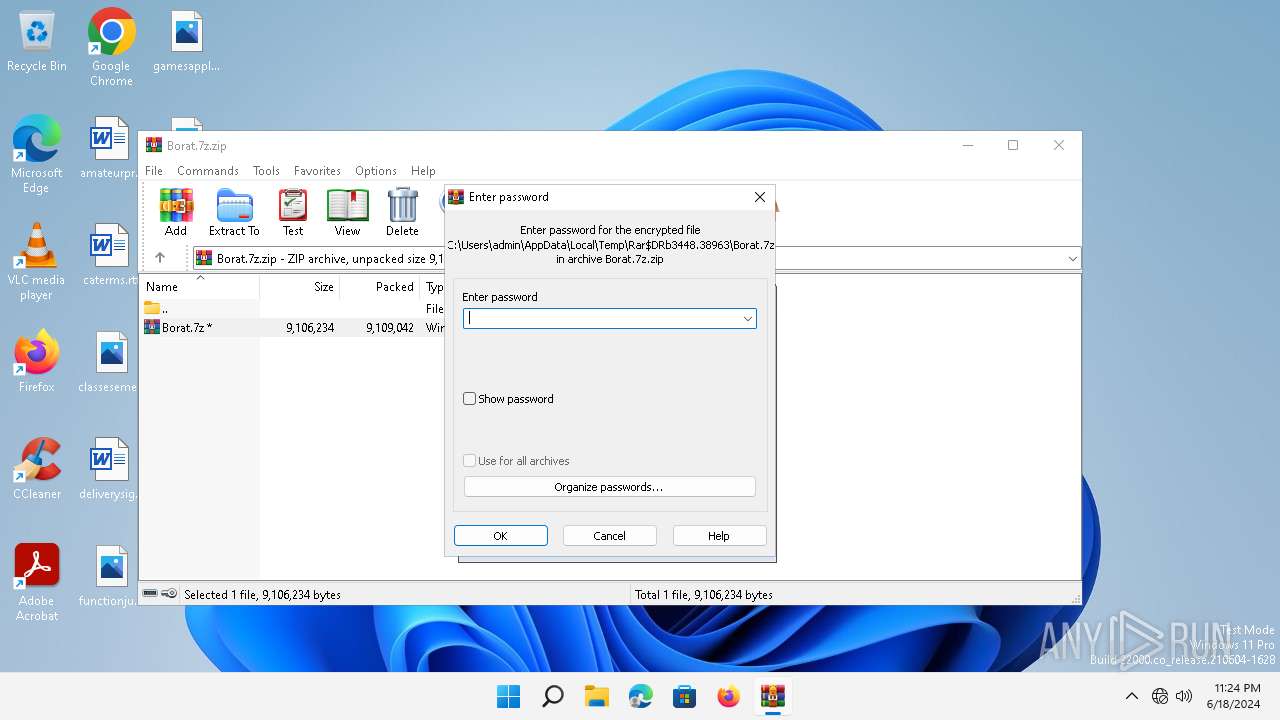
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 4ECD7D61FD44BA9B00F9FFFE56104AEA |
| SHA1: | 99B41343D4208B84737D2D14EA89DF52A0265CBD |
| SHA256: | 6DB561AB725644112034E859CEC376DB6A522ED25BE6D7C584A13010BE015845 |
| SSDEEP: | 98304:k91etKPlcheaO2oxQisWOIs7RVIFH4XT9MF1n3CWsYtif0tNovTskyH964CCRzPo:h6OIAGw4FOdNJ9XA78Gohf |
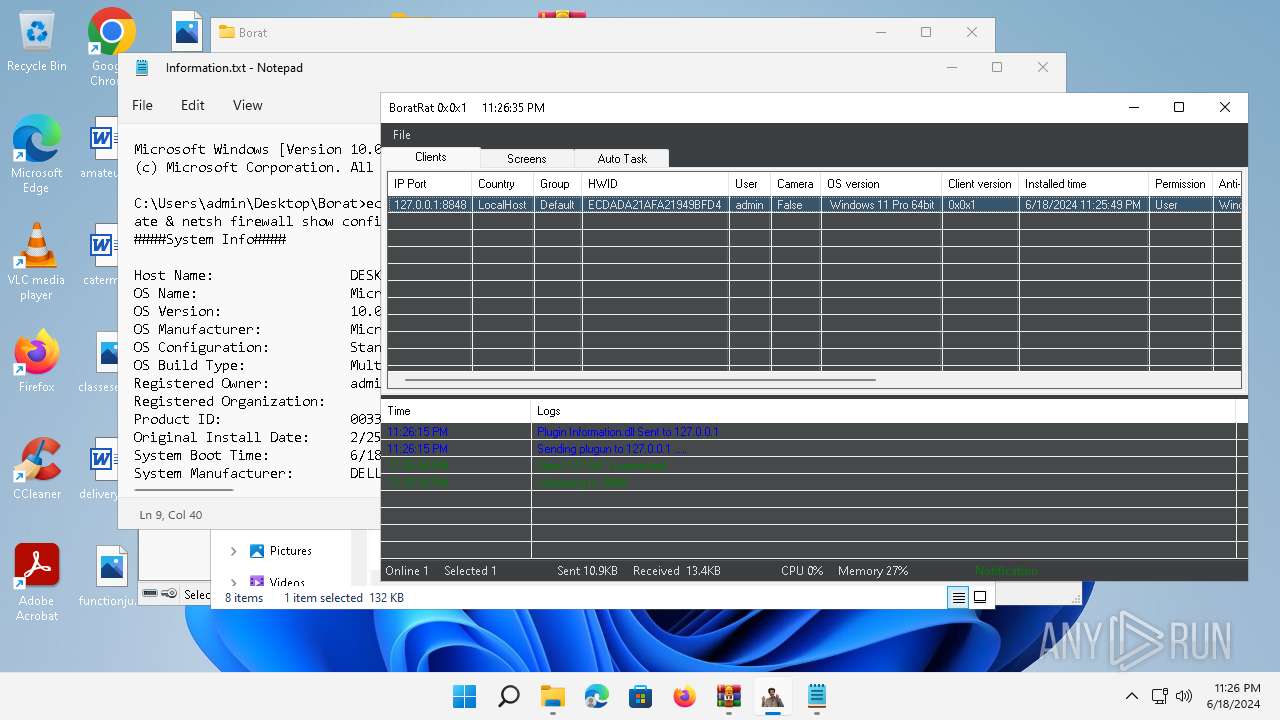
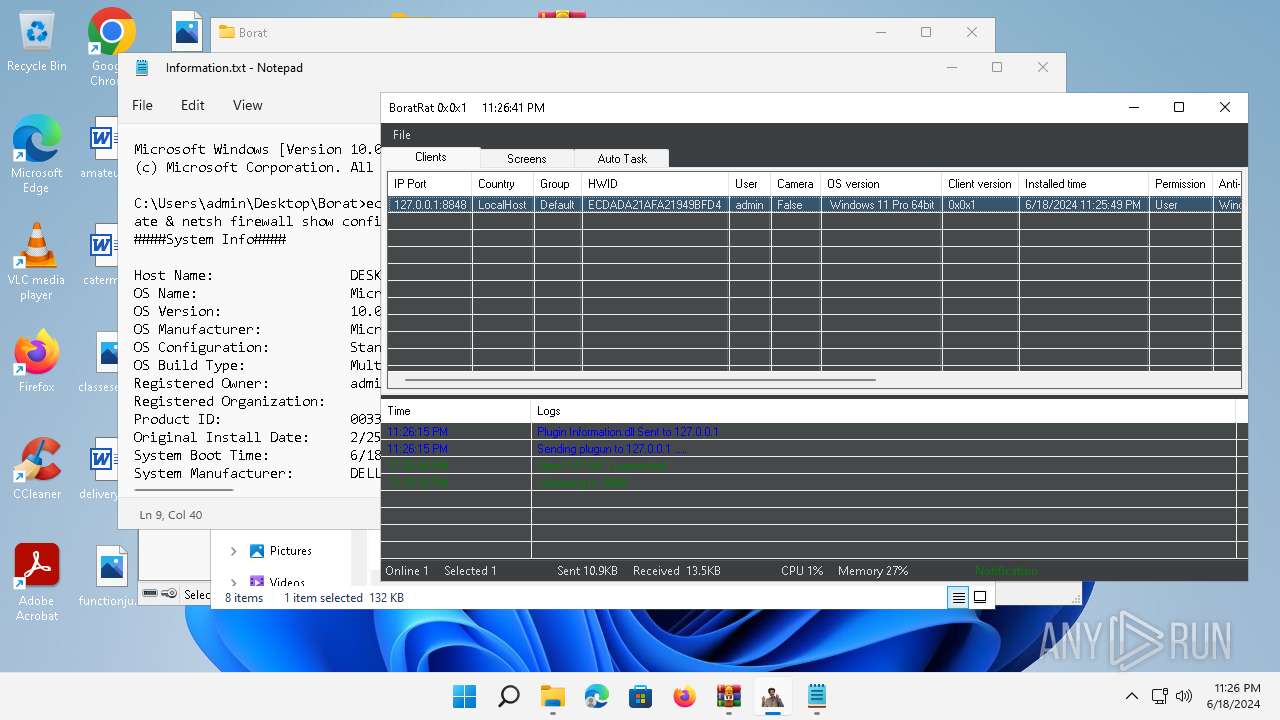
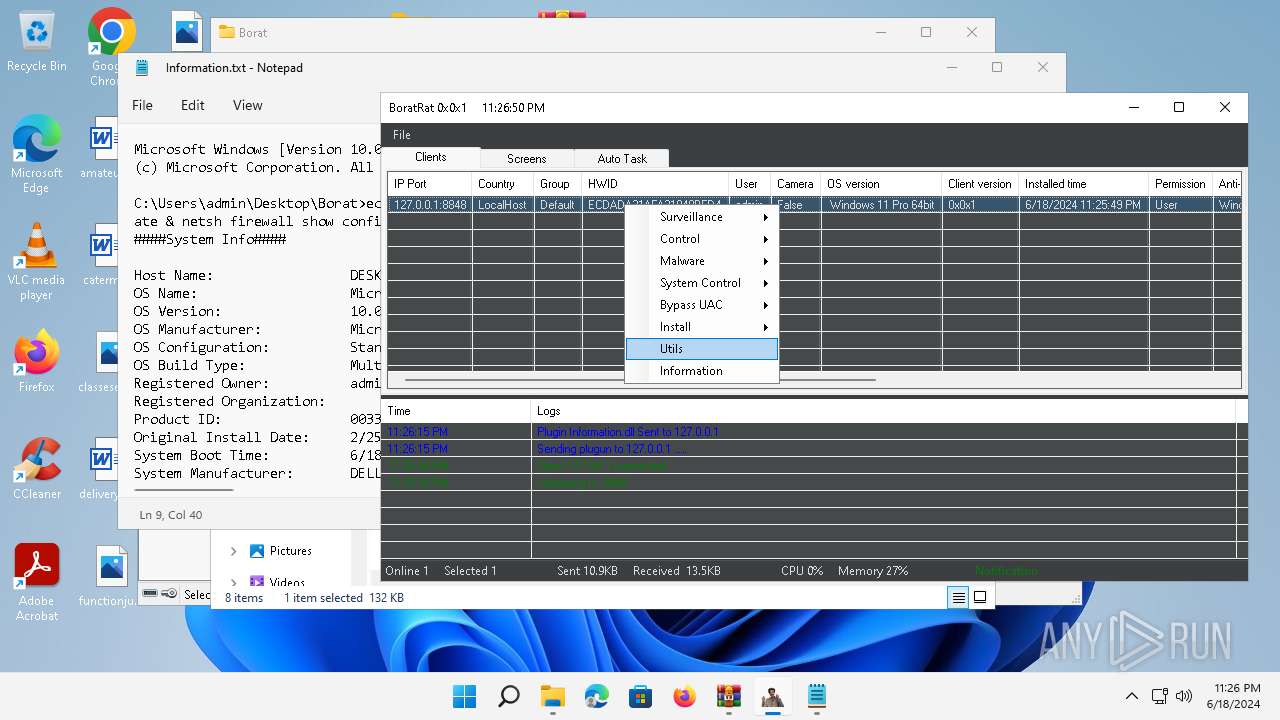
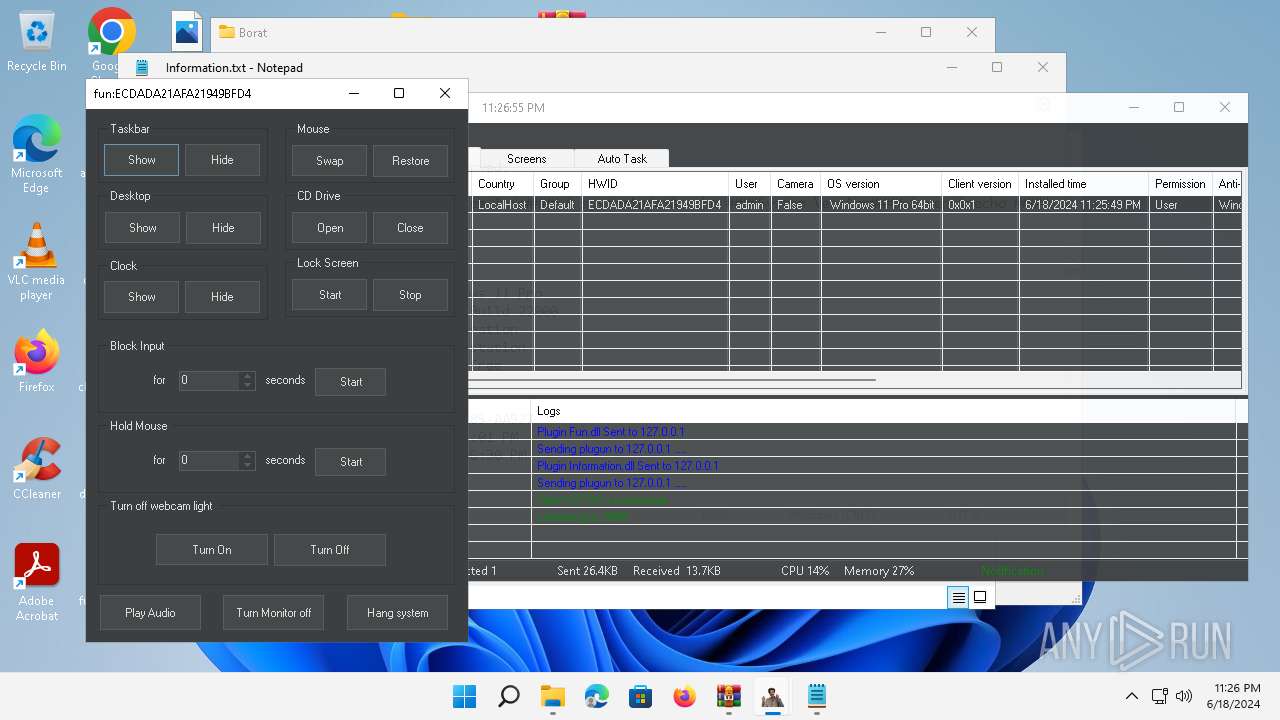
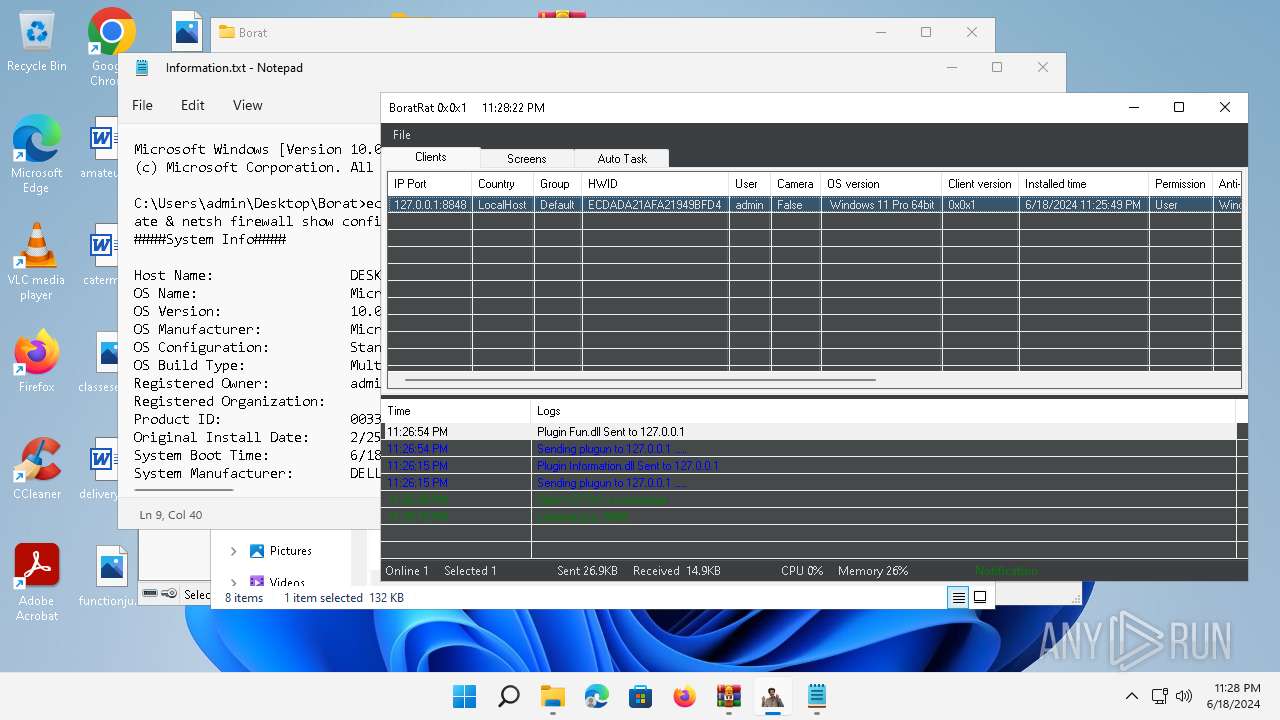
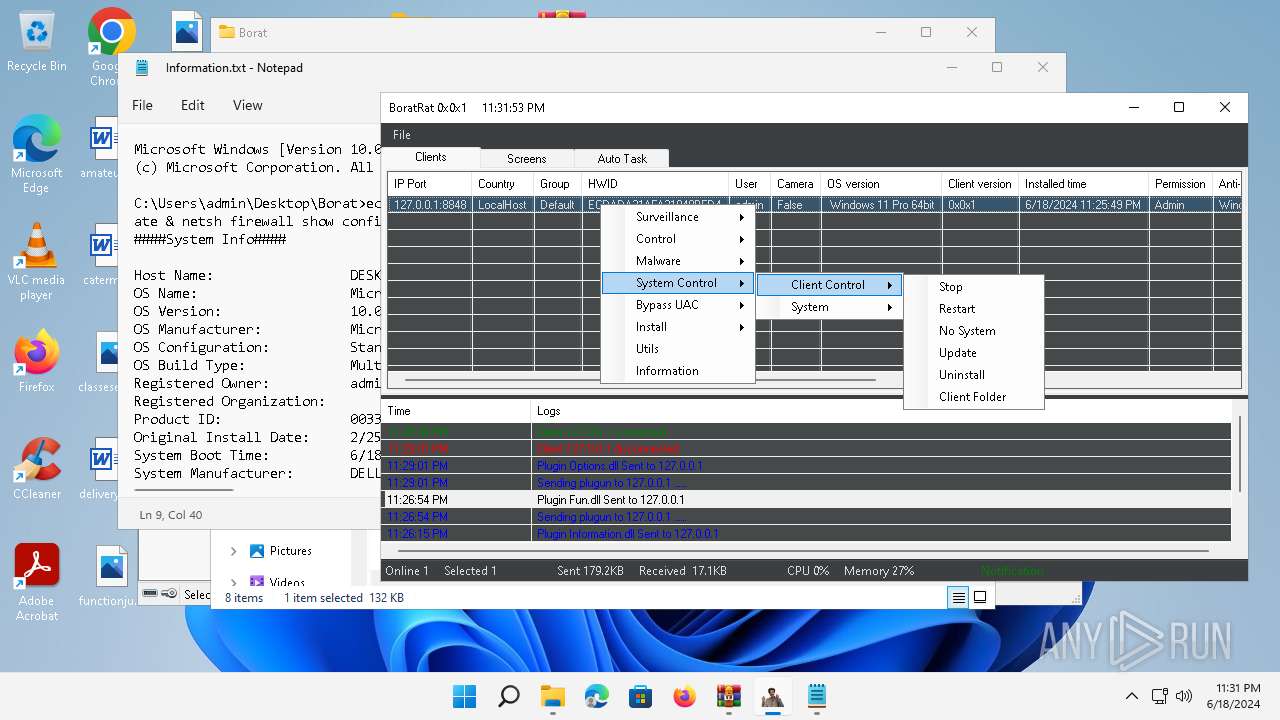
MALICIOUS
Actions looks like stealing of personal data
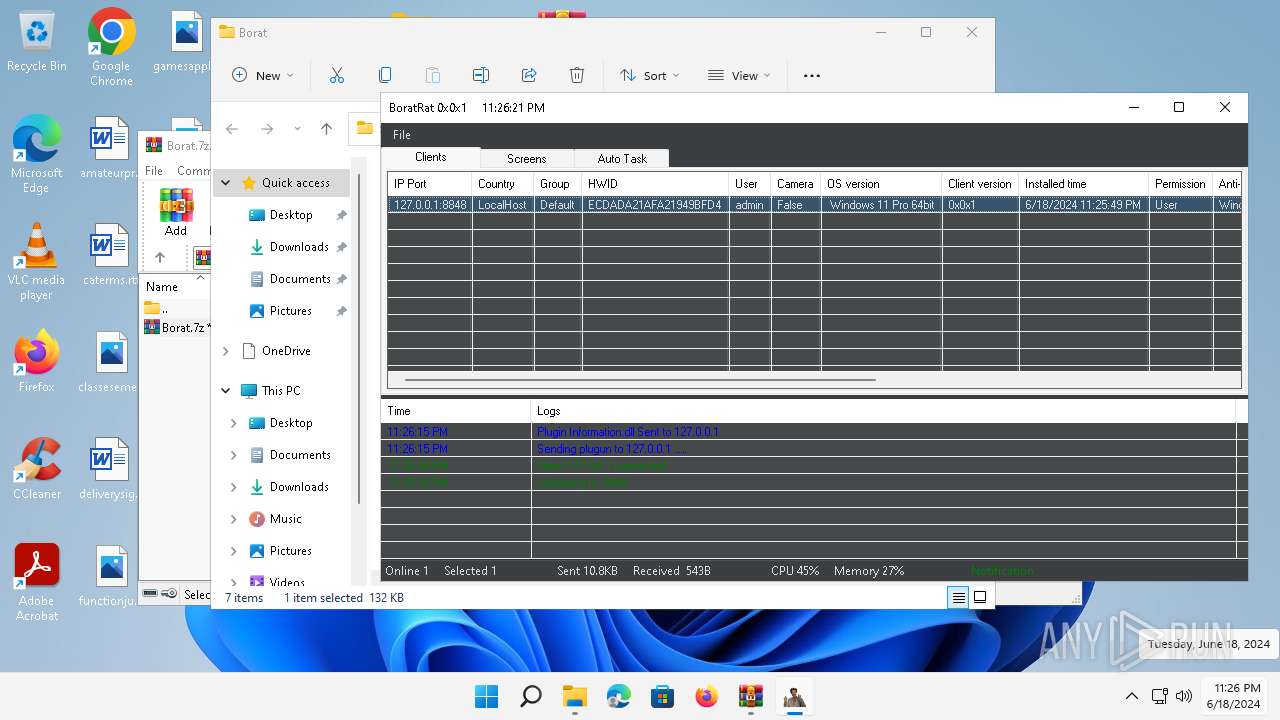
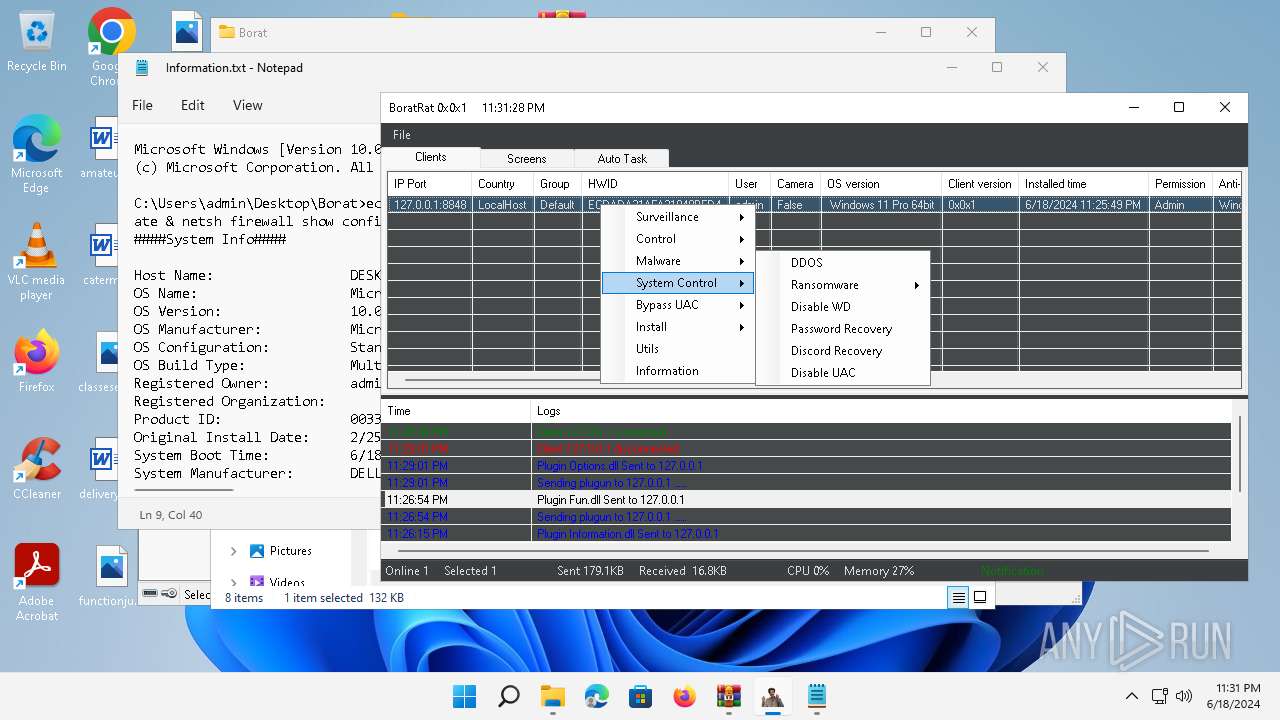
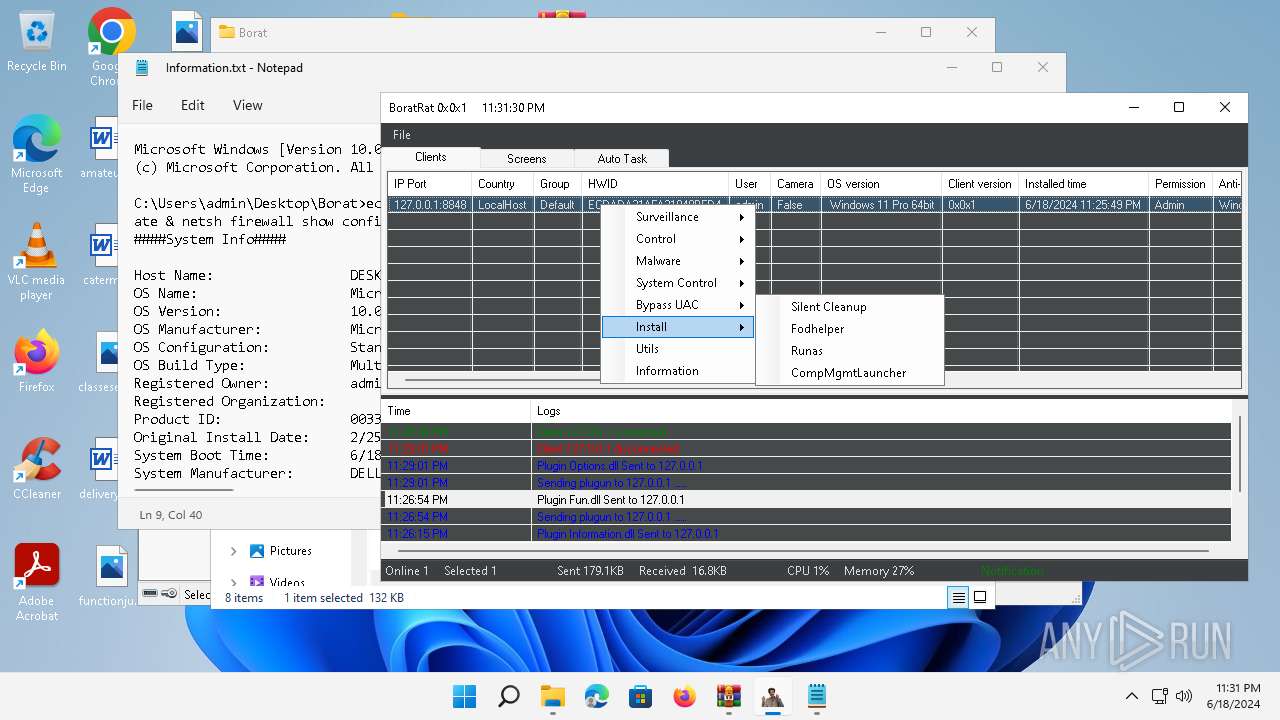
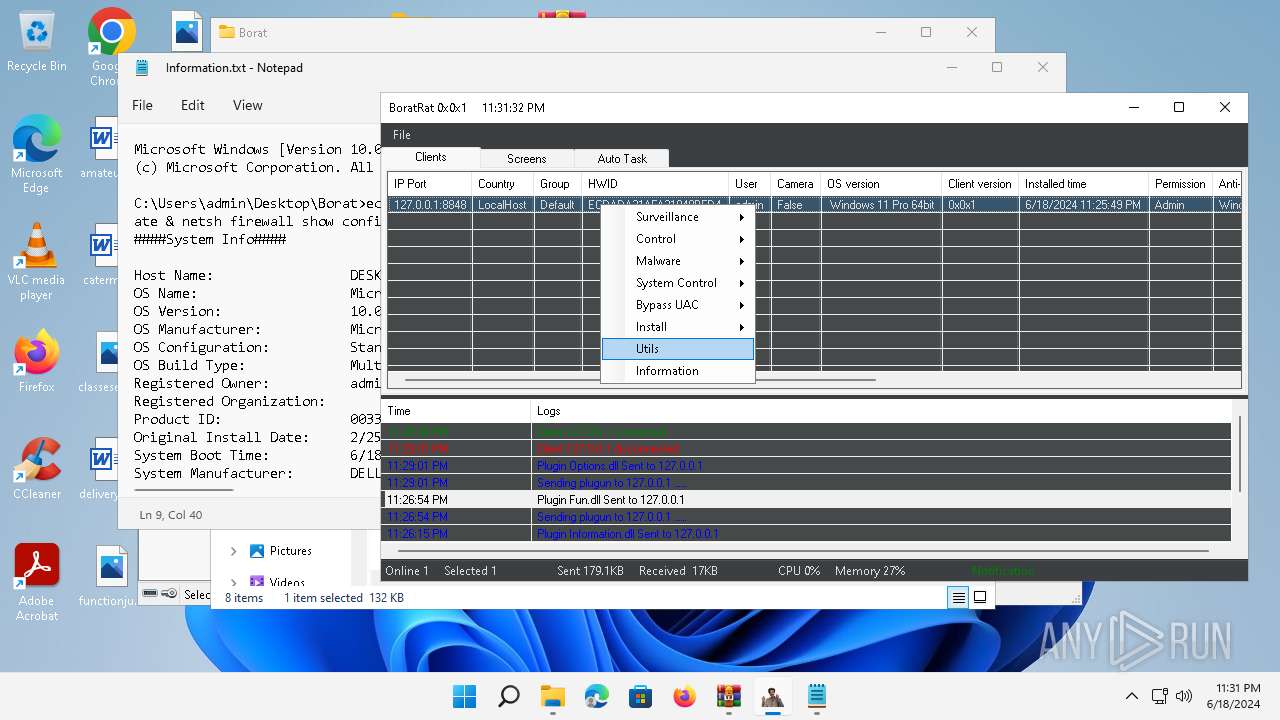
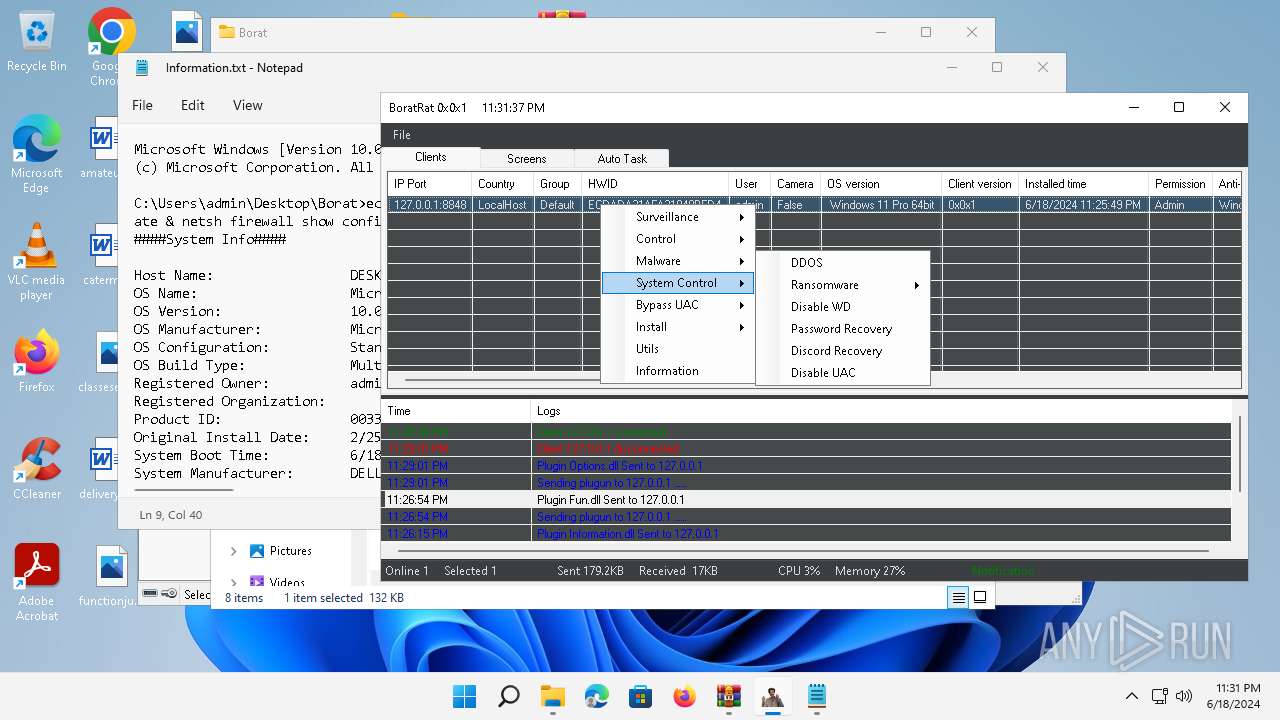
- WinRAR.exe (PID: 4388)
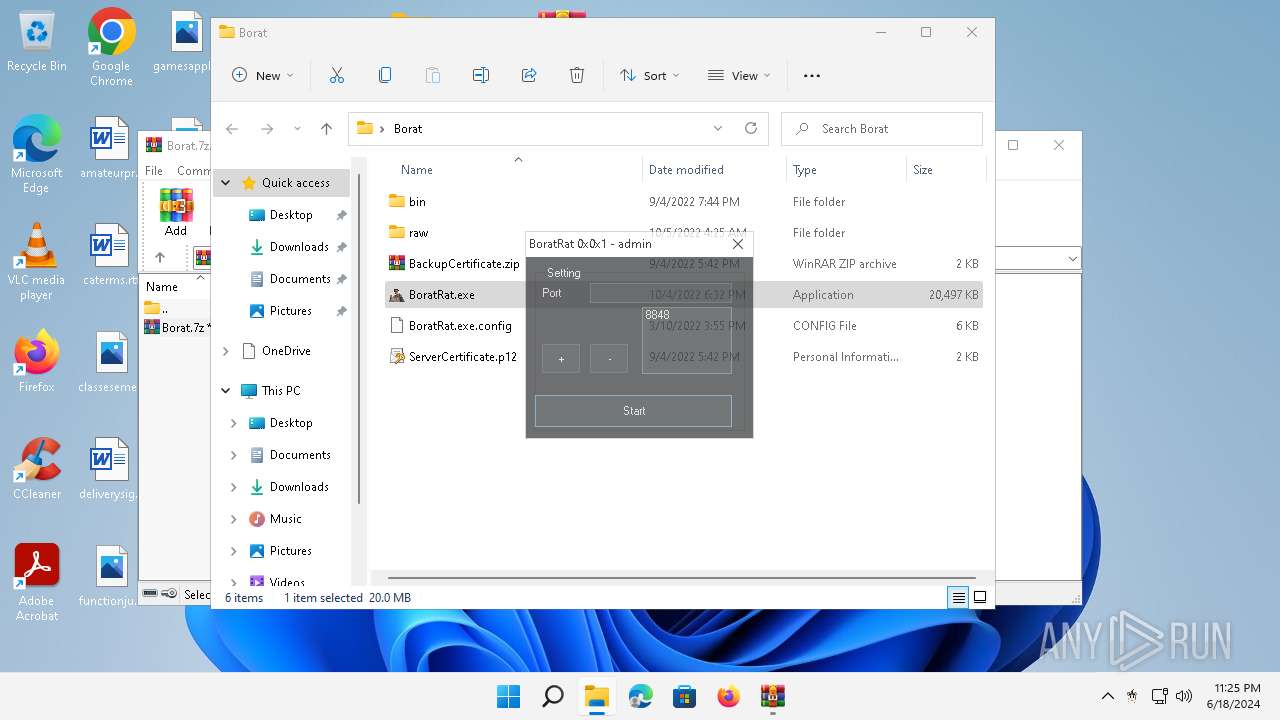
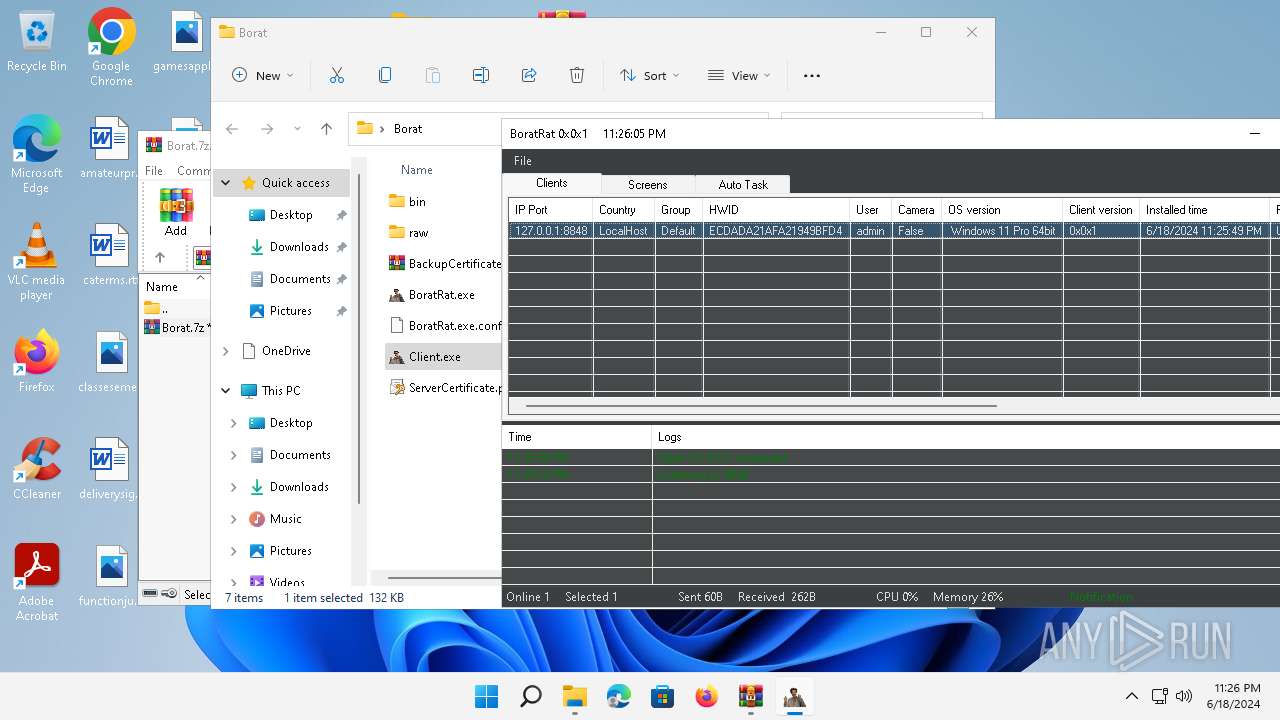
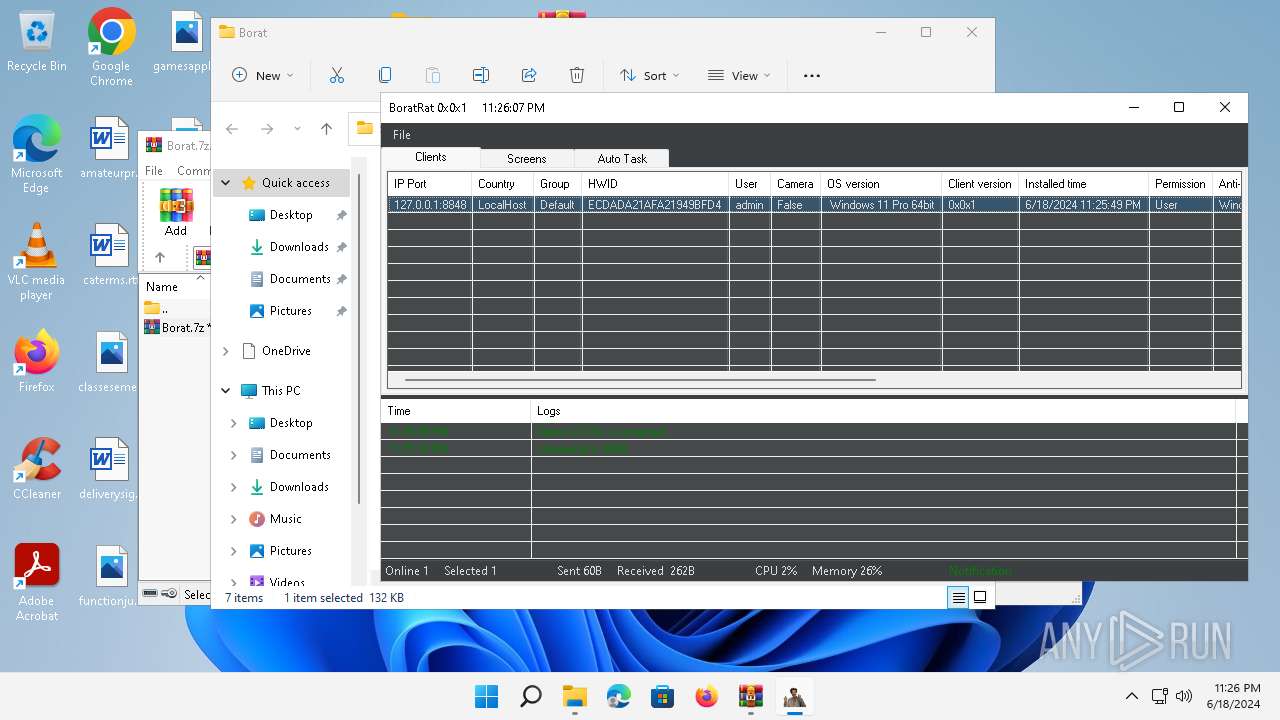
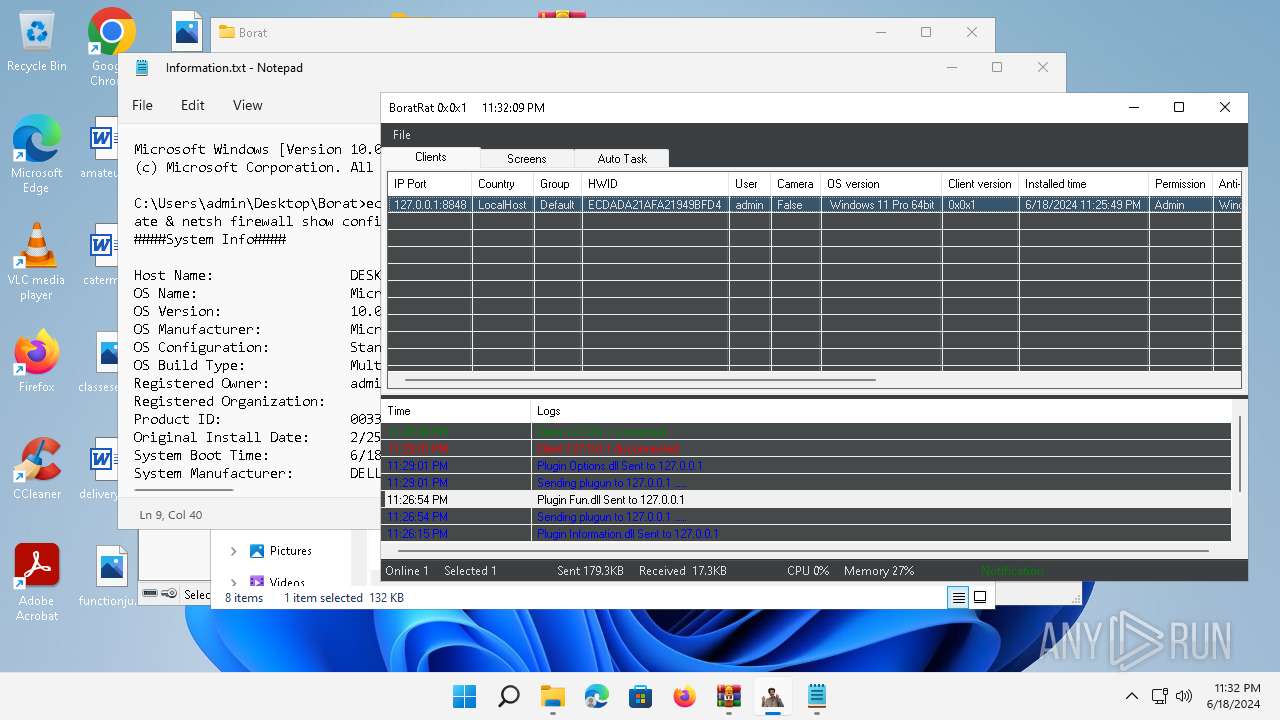
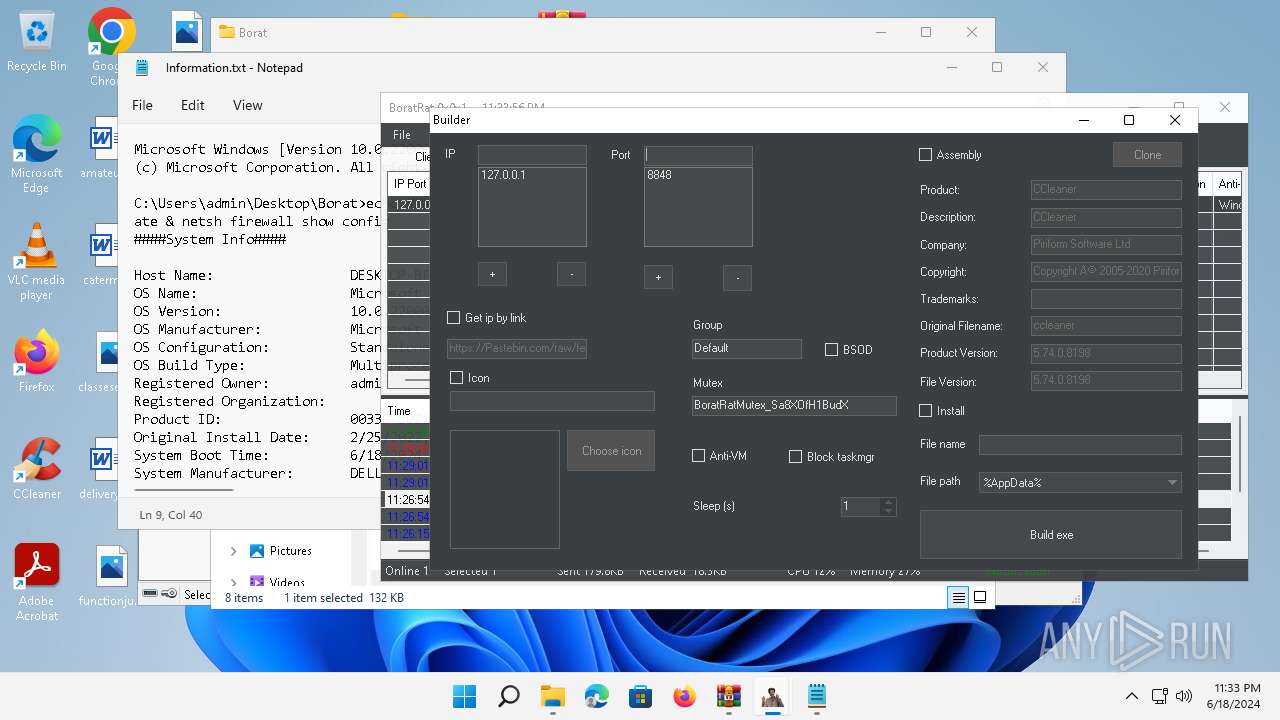
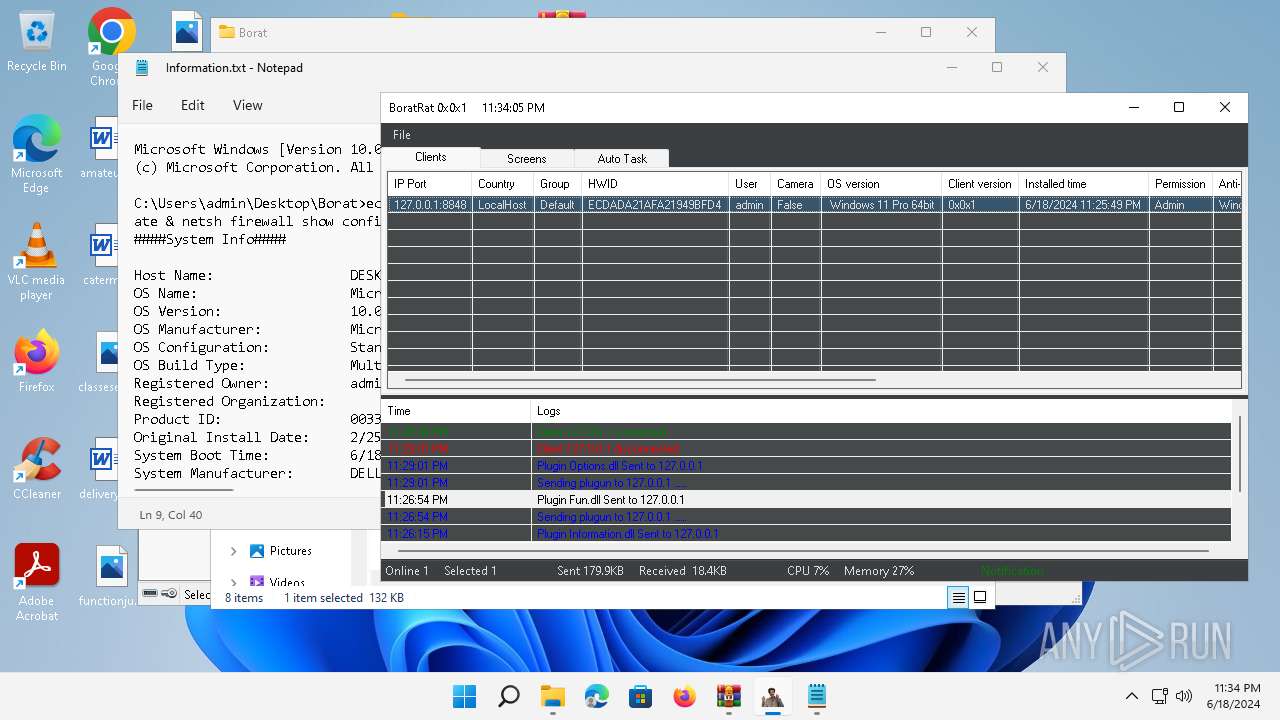
- BoratRat.exe (PID: 4456)
- Client.exe (PID: 3880)
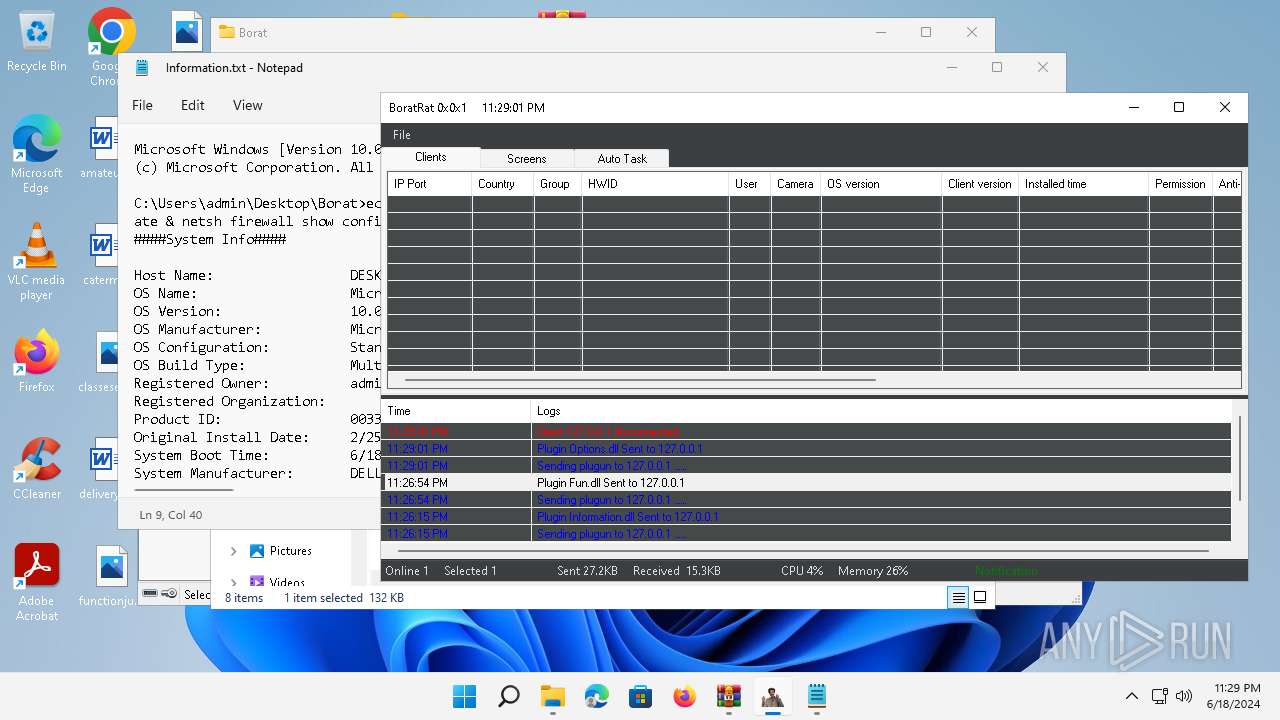
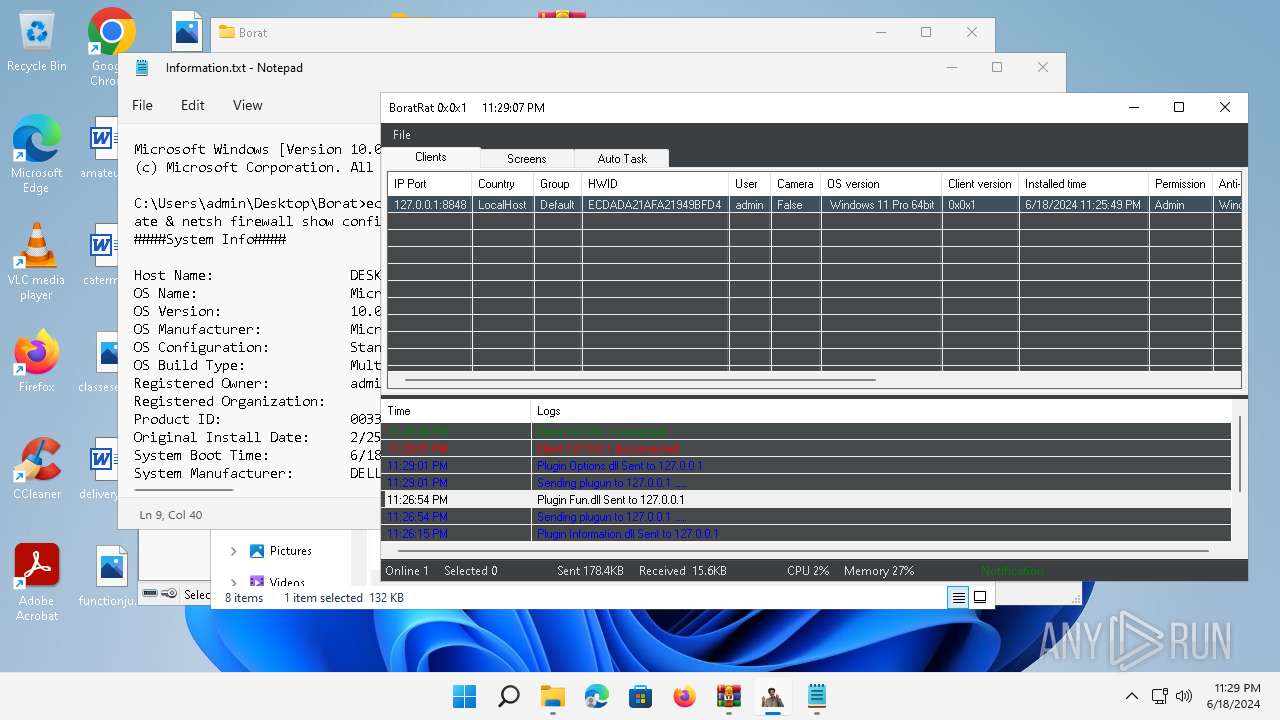
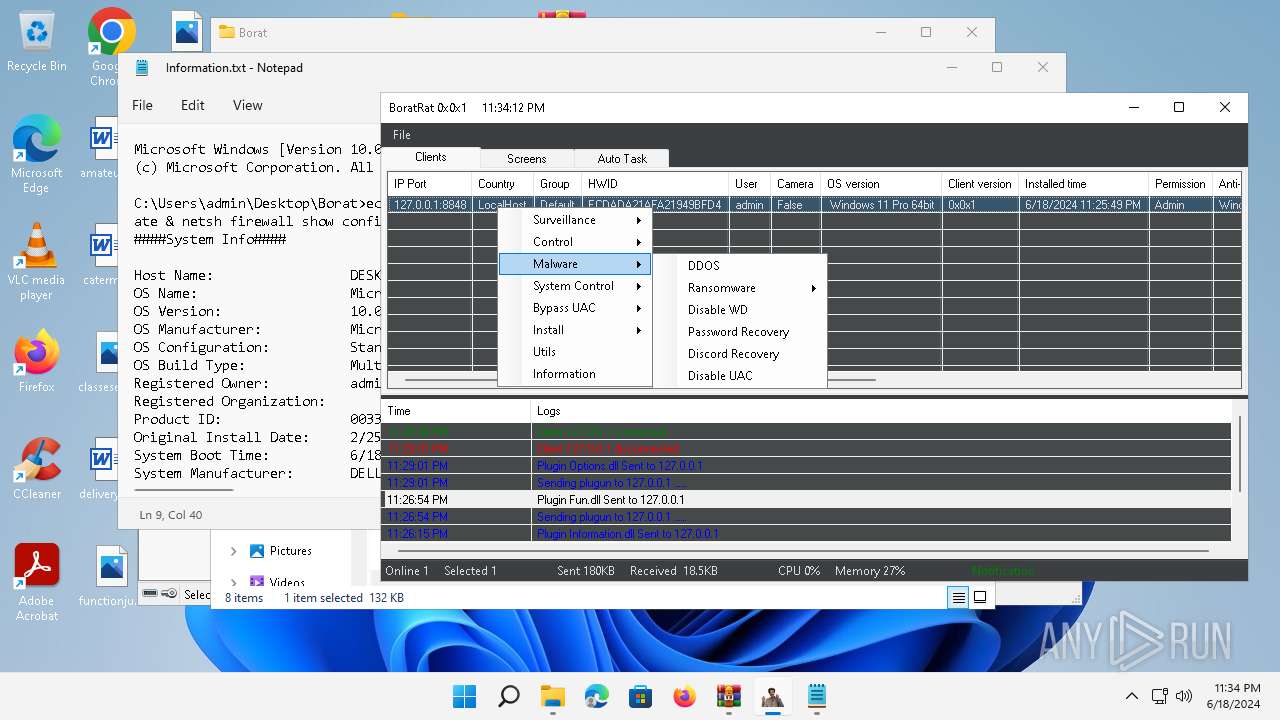
ASYNCRAT has been detected (YARA)
- BoratRat.exe (PID: 4456)
- Client.exe (PID: 2700)
Drops the executable file immediately after the start
- BoratRat.exe (PID: 4456)
Starts NET.EXE to view/add/change user profiles
- cmd.exe (PID: 1604)
- net.exe (PID: 1204)
- net.exe (PID: 5888)
- net.exe (PID: 5912)
Starts NET.EXE to view/change users localgroup
- net.exe (PID: 5160)
- net.exe (PID: 4864)
- cmd.exe (PID: 1604)
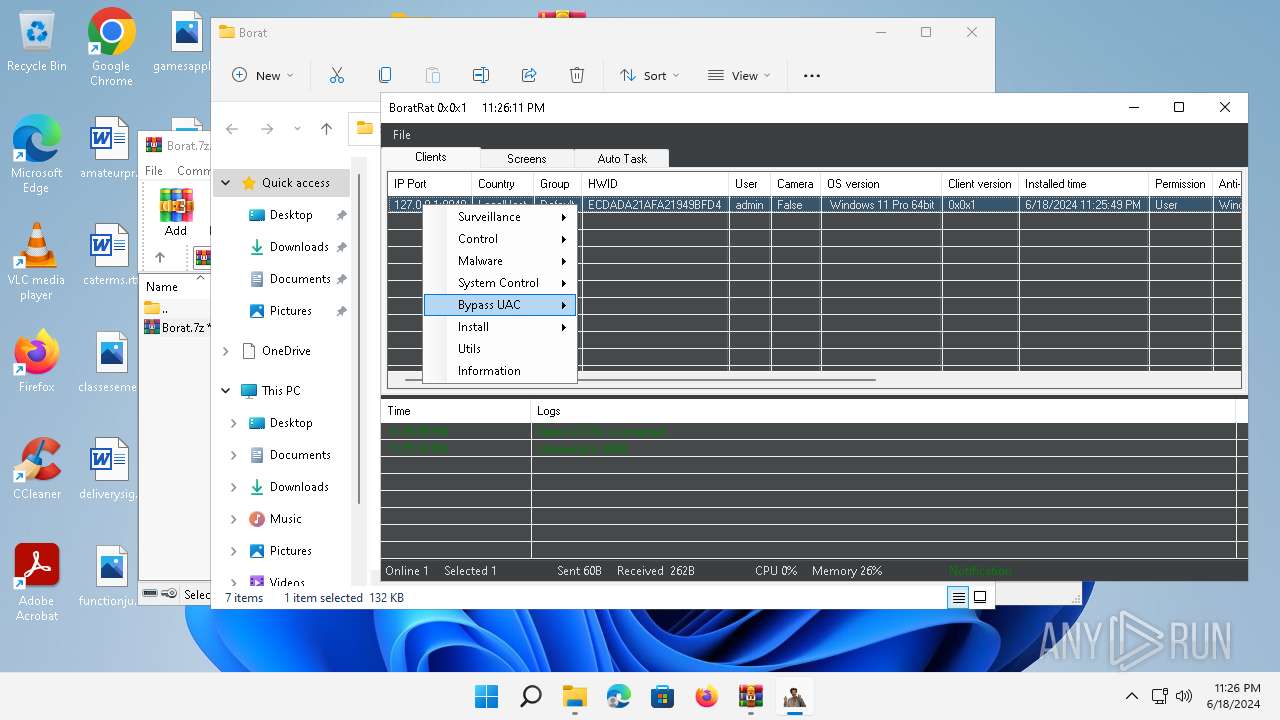
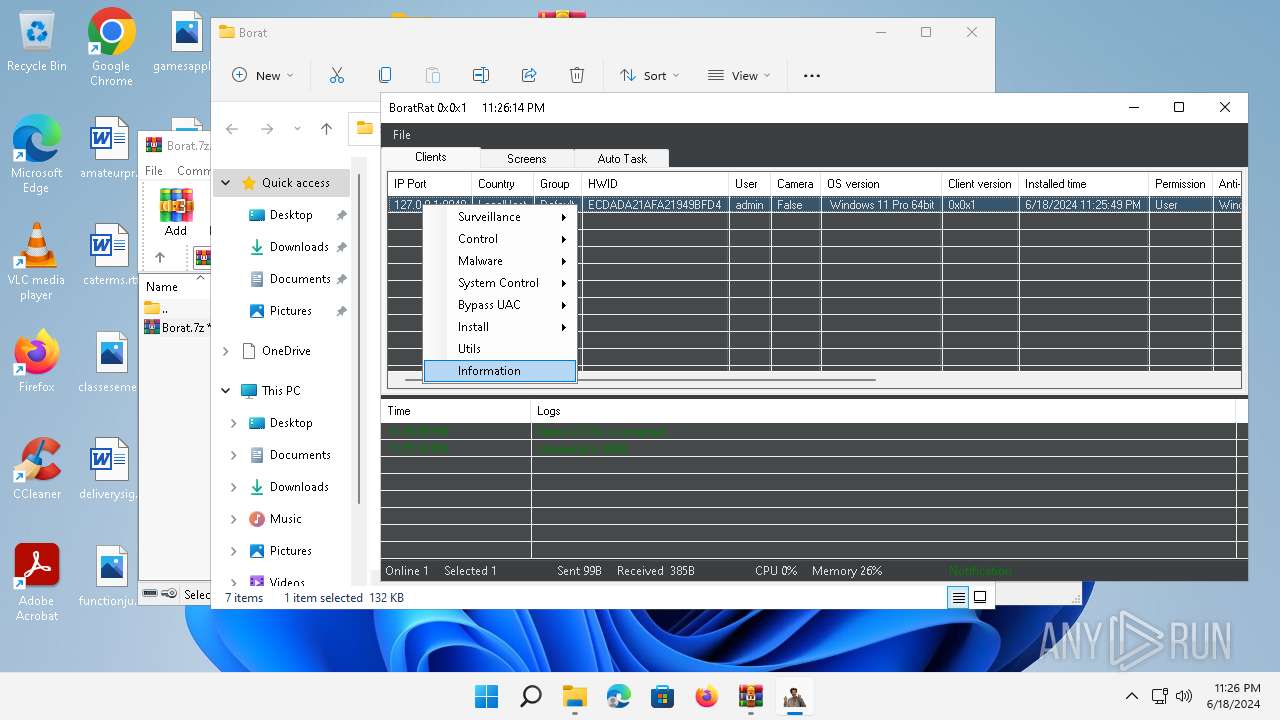
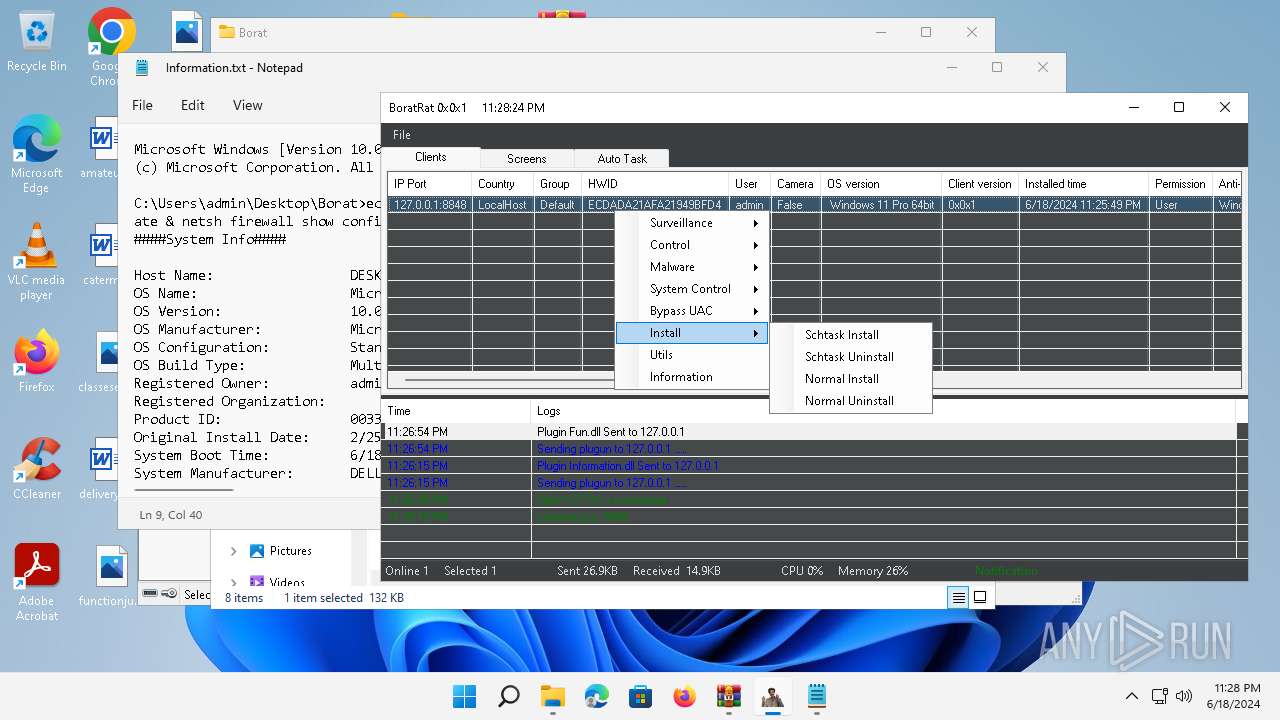
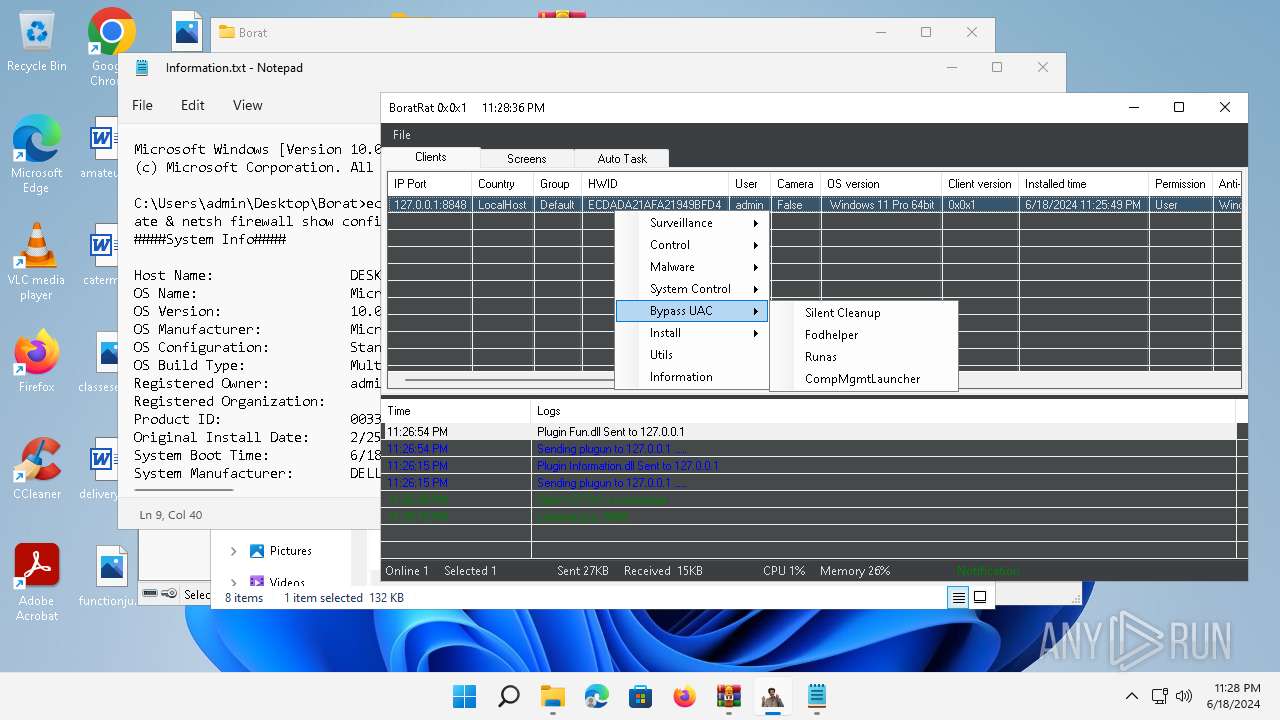
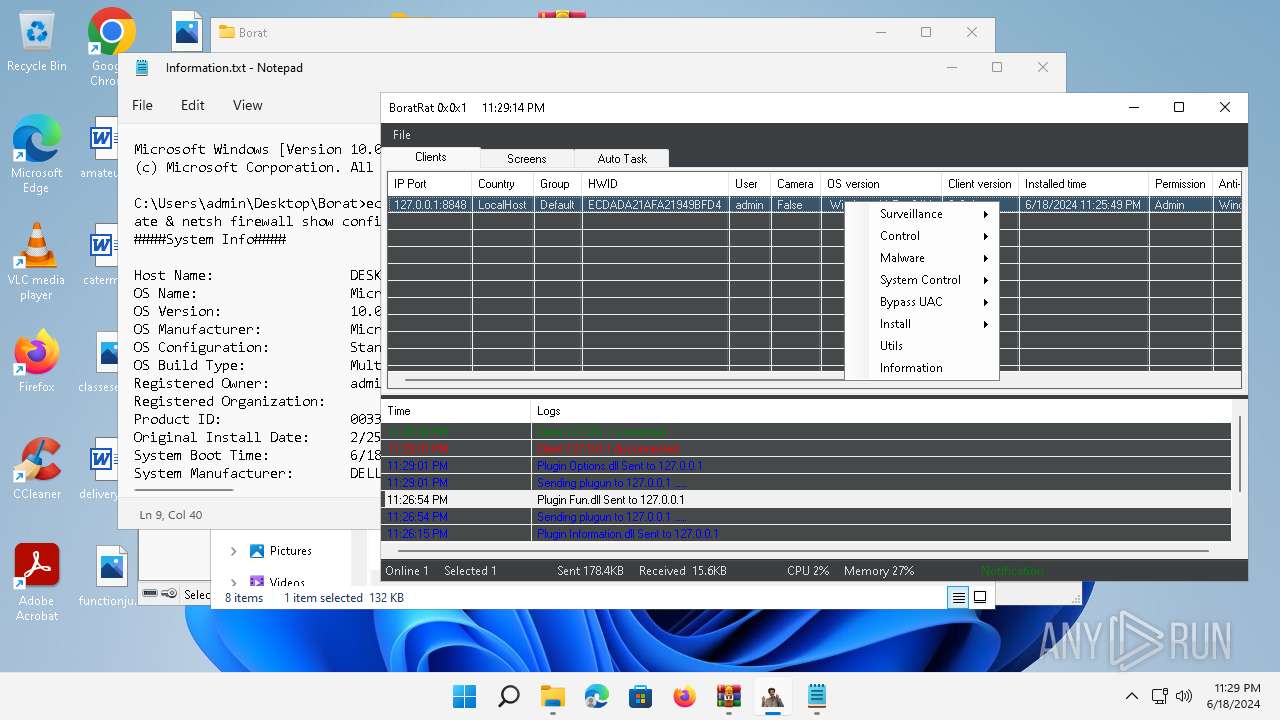
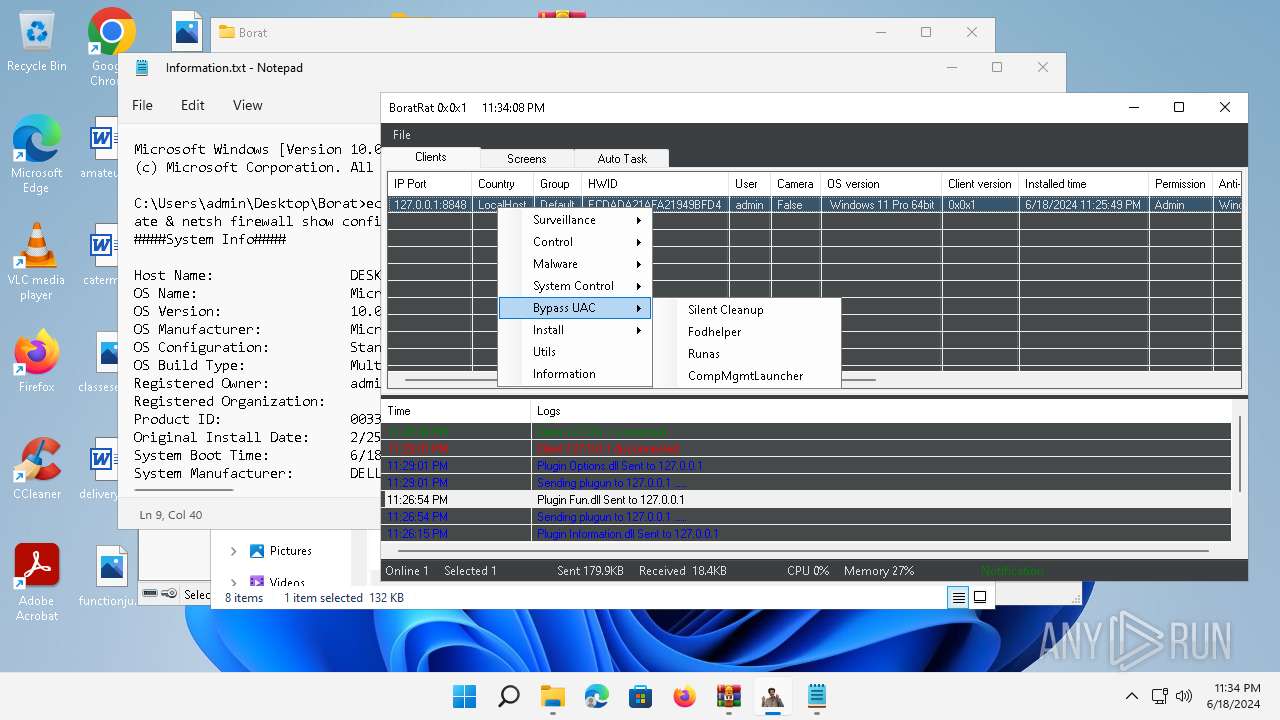
Bypass User Account Control (Modify registry)
- Client.exe (PID: 2700)
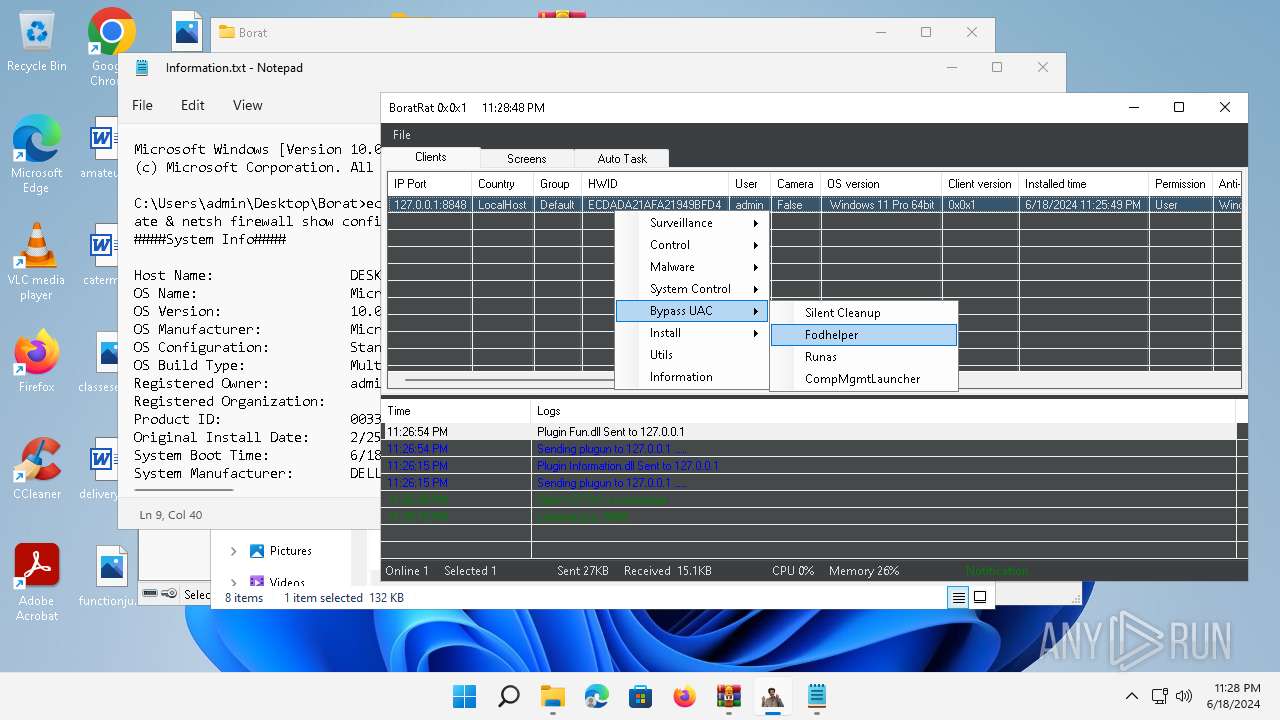
Bypass User Account Control (fodhelper)
- fodhelper.exe (PID: 1764)
SUSPICIOUS
The process creates files with name similar to system file names
- WinRAR.exe (PID: 4388)
Reads security settings of Internet Explorer
- BoratRat.exe (PID: 4456)
- Notepad.exe (PID: 252)
- Client.exe (PID: 3880)
Reads the Internet Settings
- BoratRat.exe (PID: 4456)
- WMIC.exe (PID: 788)
- WMIC.exe (PID: 1616)
- Notepad.exe (PID: 252)
- cmd.exe (PID: 2932)
- fodhelper.exe (PID: 1764)
- SystemSettings.exe (PID: 4036)
- Client.exe (PID: 3880)
- SystemSettings.exe (PID: 5480)
The process checks if it is being run in the virtual environment
- BoratRat.exe (PID: 4456)
Creates file in the systems drive root
- BoratRat.exe (PID: 4456)
Executable content was dropped or overwritten
- BoratRat.exe (PID: 4456)
Reads settings of System Certificates
- Client.exe (PID: 2700)
- Client.exe (PID: 3880)
Starts CMD.EXE for commands execution
- Client.exe (PID: 2700)
- Client.exe (PID: 3880)
Uses WMIC.EXE to obtain local storage devices information
- cmd.exe (PID: 1604)
Get information on the list of running processes
- cmd.exe (PID: 1604)
Uses WMIC.EXE to obtain commands that are run when users log in
- cmd.exe (PID: 1604)
Process uses ARP to discover network configuration
- cmd.exe (PID: 1604)
Uses ROUTE.EXE to obtain the routing table information
- cmd.exe (PID: 1604)
Process uses IPCONFIG to discover network configuration
- cmd.exe (PID: 1604)
Reads the date of Windows installation
- BoratRat.exe (PID: 4456)
- Client.exe (PID: 3880)
Starts SC.EXE for service management
- cmd.exe (PID: 1604)
Suspicious use of NETSH.EXE
- cmd.exe (PID: 1604)
Changes default file association
- Client.exe (PID: 2700)
INFO
Manual execution by a user
- WinRAR.exe (PID: 4388)
- BoratRat.exe (PID: 4456)
- Client.exe (PID: 2700)
Checks supported languages
- MiniSearchHost.exe (PID: 5132)
- BoratRat.exe (PID: 4456)
- Client.exe (PID: 2700)
- Notepad.exe (PID: 252)
- Client.exe (PID: 3880)
- SystemSettings.exe (PID: 4036)
- SystemSettings.exe (PID: 5480)
Reads the computer name
- MiniSearchHost.exe (PID: 5132)
- BoratRat.exe (PID: 4456)
- Client.exe (PID: 2700)
- Notepad.exe (PID: 252)
- Client.exe (PID: 3880)
- SystemSettings.exe (PID: 5480)
- SystemSettings.exe (PID: 4036)
Reads the machine GUID from the registry
- BoratRat.exe (PID: 4456)
- Client.exe (PID: 2700)
- Client.exe (PID: 3880)
- SystemSettings.exe (PID: 5480)
- SystemSettings.exe (PID: 4036)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4388)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 4388)
Creates files or folders in the user directory
- BoratRat.exe (PID: 4456)
- Client.exe (PID: 2700)
- SystemSettings.exe (PID: 5480)
Create files in a temporary directory
- BoratRat.exe (PID: 4456)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 788)
- WMIC.exe (PID: 1616)
- explorer.exe (PID: 5032)
- fodhelper.exe (PID: 1764)
Reads Environment values
- Client.exe (PID: 2700)
- BoratRat.exe (PID: 4456)
- Client.exe (PID: 3880)
Reads the software policy settings
- Client.exe (PID: 2700)
- Client.exe (PID: 3880)
- SystemSettings.exe (PID: 5480)
- SystemSettings.exe (PID: 4036)
Reads the time zone
- net1.exe (PID: 2808)
- net1.exe (PID: 2788)
Reads the Internet Settings
- explorer.exe (PID: 5032)
Reads Microsoft Office registry keys
- explorer.exe (PID: 5032)
- fodhelper.exe (PID: 1764)
Reads Windows Product ID
- SystemSettings.exe (PID: 4036)
Reads CPU info
- SystemSettings.exe (PID: 4036)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2024:06:18 23:23:48 |
| ZipCRC: | 0xe7150820 |
| ZipCompressedSize: | 9109042 |
| ZipUncompressedSize: | 9106234 |
| ZipFileName: | Borat.7z |
Total processes
598
Monitored processes
495
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
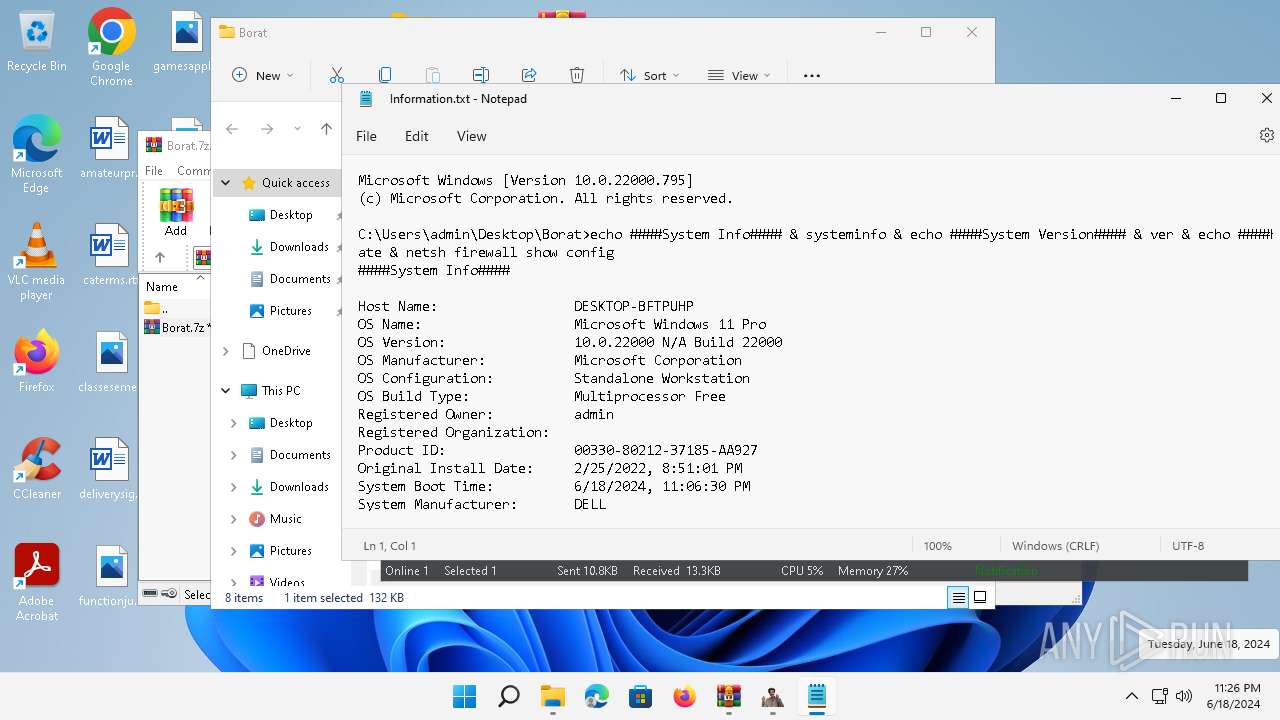
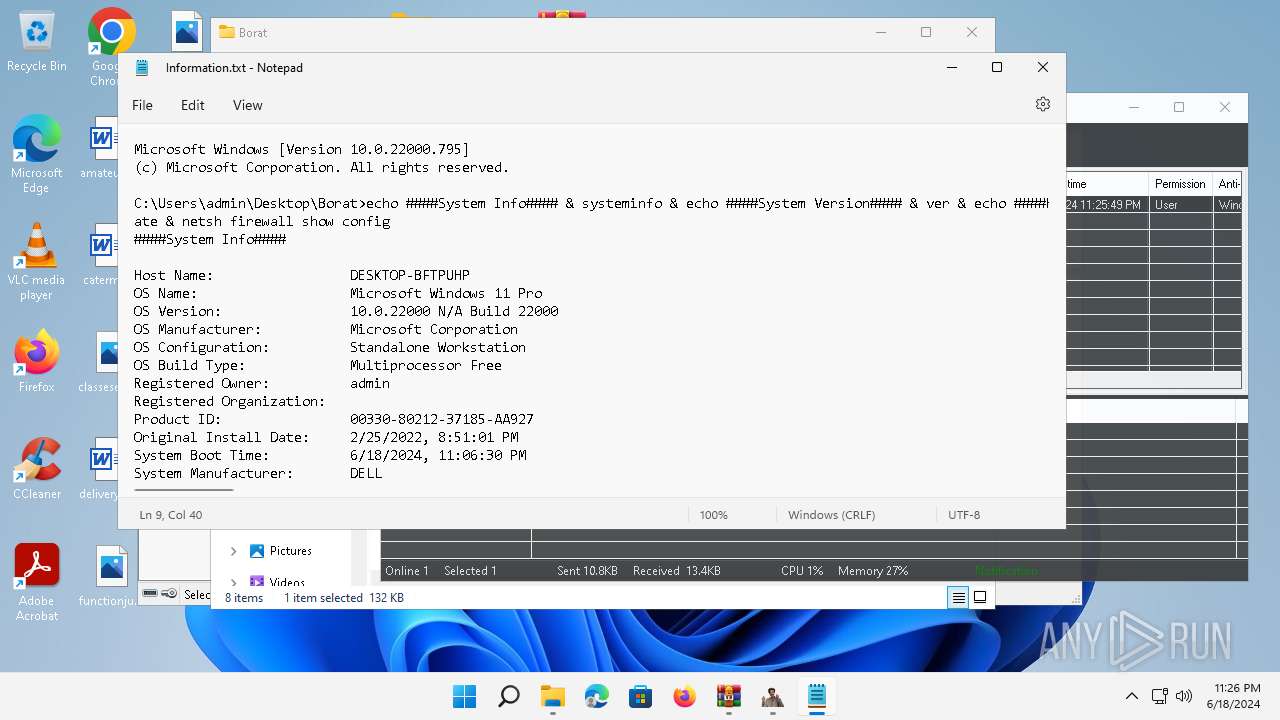
| 252 | "C:\Program Files\WindowsApps\Microsoft.WindowsNotepad_11.2205.11.0_x64__8wekyb3d8bbwe\Notepad\Notepad.exe" "C:\Users\admin\Desktop\Borat\ClientsFolder\ECDADA21AFA21949BFD4\Information\Information.txt" | C:\Program Files\WindowsApps\Microsoft.WindowsNotepad_11.2205.11.0_x64__8wekyb3d8bbwe\Notepad\Notepad.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 592 | "C:\Windows\System32\cmd.exe" | C:\Windows\System32\cmd.exe | — | Client.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.22000.1 (WinBuild.160101.0800) | |||||||||||||||
| 616 | "C:\Windows\System32\cmd.exe" | C:\Windows\System32\cmd.exe | — | Client.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.22000.1 (WinBuild.160101.0800) | |||||||||||||||
| 748 | \??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 788 | wmic logicaldisk get caption,description,providername | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 788 | \??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 804 | \??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 816 | "C:\Windows\System32\cmd.exe" | C:\Windows\System32\cmd.exe | — | Client.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.22000.1 (WinBuild.160101.0800) | |||||||||||||||
| 948 | "C:\Windows\System32\cmd.exe" | C:\Windows\System32\cmd.exe | — | Client.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1036 | \??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.22000.1 (WinBuild.160101.0800) | |||||||||||||||
Total events
83 256
Read events
82 864
Write events
350
Delete events
42
Modification events
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | VerInfo |
Value: 005B0500A916BAAED6C1DA01 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Borat.7z.zip | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (4388) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
Executable files
28
Suspicious files
14
Text files
9
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3448.38963\Borat.7z | — | |
MD5:— | SHA256:— | |||
| 4388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4388.39971\Borat\bin\ip2region.db | — | |
MD5:— | SHA256:— | |||
| 4388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4388.39971\Borat\bin\Information.dll | executable | |
MD5:87651B12453131DAFD3E91F60D8AEF5A | SHA256:A15D72D990686D06D89D7E11DF2B16BCD5719A40298C19D046FA22C40D56AF44 | |||
| 4388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4388.39971\Borat\bin\Fun.dll | executable | |
MD5:499FC6AC30B3B342833C79523BE4A60C | SHA256:DCAC599B1BAB37E1A388AC469E6CC5DE1F35EB02BEAA6778F07A1C090CE3EA04 | |||
| 4388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4388.39971\Borat\BackupCertificate.zip | compressed | |
MD5:9322F71EDD95192E1F4D275BFD6D87F3 | SHA256:F13033134C386E85A1E9009E863A3E6380438F83E3336B76A33E701A88F64946 | |||
| 4388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4388.39971\Borat\bin\FileSearcher.dll | executable | |
MD5:0B7C33C5739903BA4F4B78C446773528 | SHA256:2D9625F41793F62BFE32C10B2D5E05668E321BCAF8B73414B3C31EF677B9BFF4 | |||
| 4388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4388.39971\Borat\bin\FileManager.dll | executable | |
MD5:4CCD3DFB14FFDDDFA598D1096F0190EA | SHA256:7F8A306826FCB0EE985A2B6D874C805F7F9B2062A1123EA4BB7F1EBA90FC1B81 | |||
| 4388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4388.39971\Borat\bin\Audio.dll | executable | |
MD5:9726D7FE49C8BA43845AD8E5E2802BB8 | SHA256:DF31A70CEB0C481646EEAF94189242200FAFD3DF92F8B3EC97C0D0670F0E2259 | |||
| 4388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4388.39971\Borat\bin\Logger.dll | executable | |
MD5:872145B37D107144894C9AA8729BAD42 | SHA256:2F258949FD95DA6CD912BEB7203A9FD5E99D050309A40341DE67537EDB75AADC | |||
| 4388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4388.39971\Borat\bin\MessagePackLib.dll | executable | |
MD5:590B00C87D5FF2FFE09079F0406EB2CD | SHA256:ADB00DEE751B4BA620D3B0E002F5B6D8B89CF63B062F74EC65BBA72294D553D1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
36
DNS requests
19
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1332 | svchost.exe | GET | 200 | 2.18.64.212:80 | http://www.msftconnecttest.com/connecttest.txt | unknown | — | — | unknown |
3984 | svchost.exe | GET | 304 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?951ec8ab5ba0455b | unknown | — | — | unknown |
1088 | svchost.exe | POST | 403 | 104.110.17.248:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
1088 | svchost.exe | POST | 403 | 104.110.17.248:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
1088 | svchost.exe | POST | 403 | 104.110.17.248:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
1088 | svchost.exe | POST | 403 | 104.110.17.248:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
2868 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | unknown |
1088 | svchost.exe | POST | 403 | 104.110.17.248:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
1088 | svchost.exe | POST | 403 | 104.110.17.248:80 | http://go.microsoft.com/fwlink/?LinkID=252669&clcid=0x409 | unknown | — | — | unknown |
3984 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4552 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1332 | svchost.exe | 2.18.64.200:80 | — | Administracion Nacional de Telecomunicaciones | UY | unknown |
1332 | svchost.exe | 2.18.64.212:80 | — | Administracion Nacional de Telecomunicaciones | UY | unknown |
3984 | svchost.exe | 20.190.159.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1088 | svchost.exe | 104.110.17.248:80 | go.microsoft.com | AKAMAI-AS | NO | unknown |
3984 | svchost.exe | 199.232.214.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
3984 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2844 | svchost.exe | 20.42.65.85:443 | v10.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2844 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
v10.events.data.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
v20.events.data.microsoft.com |
| whitelisted |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1332 | svchost.exe | Misc activity | ET INFO Microsoft Connection Test |
Process | Message |
|---|---|
TiWorker.exe | Populating UpdatePolicy AllowList |
TiWorker.exe | All policies are allowed
|
TiWorker.exe | |
TiWorker.exe | SKU MDM licensing allow list string from SLAPI:
|
TiWorker.exe | AboveLock|Accounts|ActiveXControls|ADMXIngest|AllowMessageSync|AppHVSI|ApplicationDefaults|AllowAllTrustedApps|AllowAppStoreAutoUpdate|AllowAutomaticAppArchiving|AllowDeveloperUnlock|AllowGameDVR|AllowSharedUserAppData|ApplicationRestrictions|Audit|ConfigureChatIcon|LaunchAppAfterLogOn|MSIAllowUserControlOverInstall|MSIAlwaysInstallWithElevatedPrivileges|RestrictAppDataToSystemVolume|RestrictAppToSystemVolume|AppRuntime|AttachmentManager|Authentication|Autoplay|BitLocker|BITS|Bluetooth|Browser|Camera|Cellular|Connectivity|ControlPolicyConflict|CredentialProviders|CredentialsDelegation|CredentialsUI|Cryptography|DataProtection|DataUsage|Defender|DeliveryOptimization|Desktop|ConfigureSystemGuardLaunch|EnableVirtualizationBasedSecurity|DeviceHealthMonitoring|DeviceInstallation|DeviceLock|Display|DmaGuard|ErrorReporting|Eap|Education|EnterpriseCloudPrint|EventLogService|AllowClipboardHistory|AllowCopyPaste|AllowCortana|AllowDeviceDiscovery|AllowManualMDMUnenrollment|AllowSaveAsOfOfficeFiles|AllowScreenCapture|AllowSharingOfOfficeFiles|AllowSIMErrorDialogPromptWhenNoSIM|AllowSyncMySettings|AllowTailoredExperiencesWithDiagnosticData|AllowTaskSwitcher|AllowThirdPartySuggestionsInWindowsSpotlight|AllowVoiceRecording|DoNotShowFeedbackNotifications|DoNotSyncBrowserSettings|AllowFindMyDevice|ExploitGuard|Feeds|FileExplorer|Games|Handwriting|HumanPresence|InternetExplorer|Kerberos|KioskBrowser|Knobs|LanmanWorkstation|Licensing|LocalPoliciesSecurityOptions|LocalUsersAndGroups|Lockdown|Maps|MemoryDump|MSSecurityGuide|MSSLegacy|Multitasking|NetworkIsolation|NetworkListManager|NewsAndInterests|Notifications|OneDrive|Power|Printers|Privacy|RemoteAssistance|RemoteDesktopServices|RemoteDesktop|RemoteManagement|RemoteProcedureCall|RemoteShell|RestrictedGroups|Search|Security|Settings|SmartScreen|Speech|Start|Storage|System|SystemServices|TaskManager|TaskScheduler|TenantRestrictions|TextInput|TimeLanguageSettings|Troubleshooting|Update|UserRights|VirtualizationBasedTechnology|WiFi|WindowsLogon|WirelessDisplay|Location|WindowsAutopilot|WindowsConnectionManager|WindowsDefenderSecurityCenter|WindowsInkWorkspace|WindowsPowerShell|WindowsSandbox|WiredNetwork|ADMX_ |