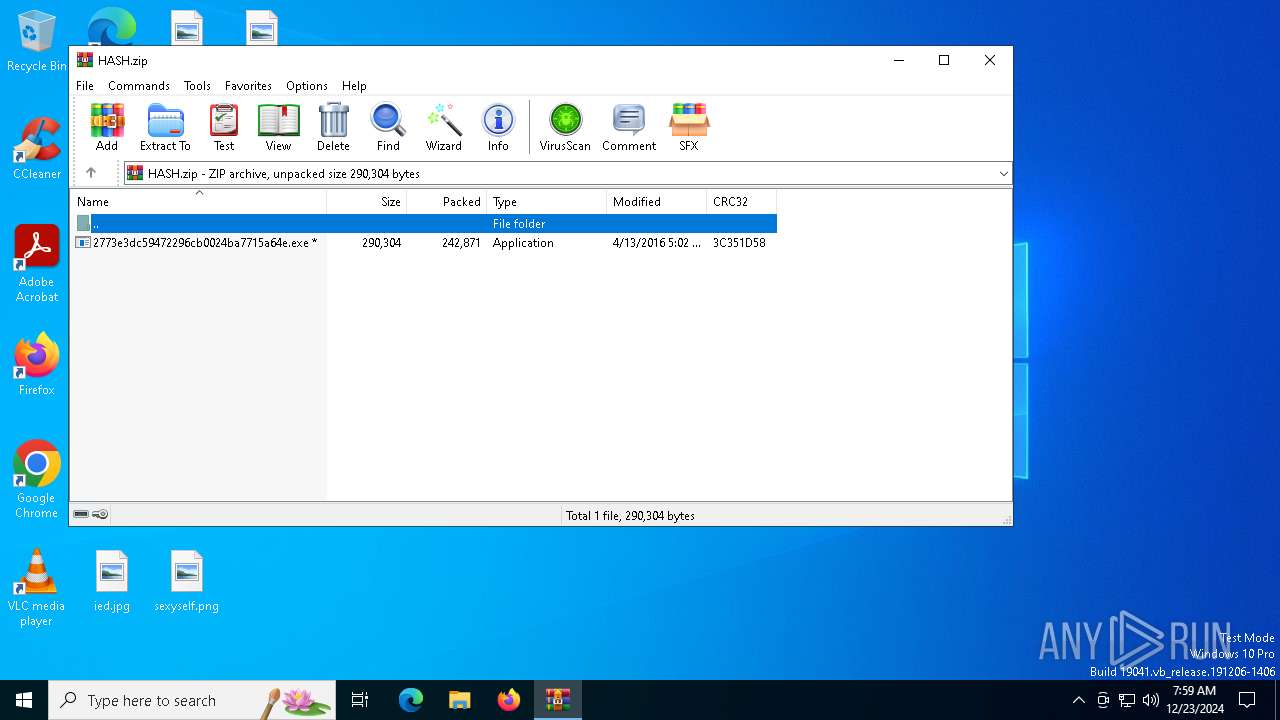
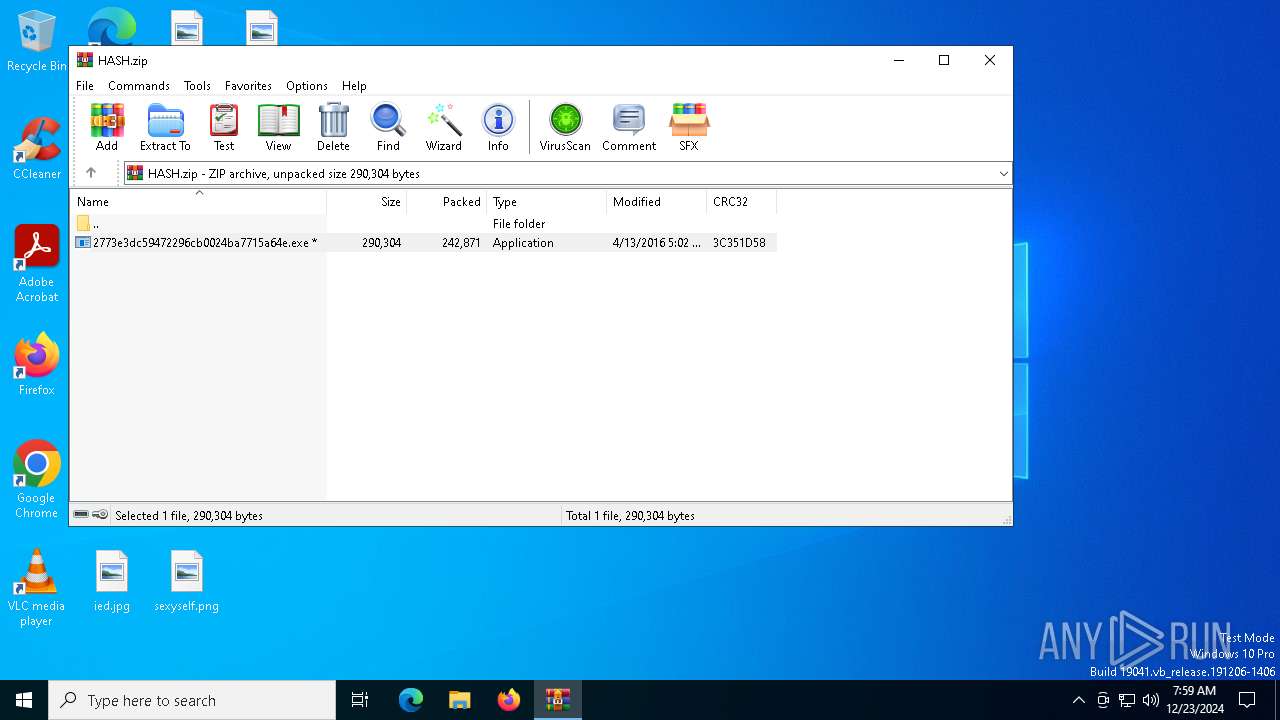
| File name: | HASH.zip |
| Full analysis: | https://app.any.run/tasks/a5cfae0c-c79d-44f5-9beb-6bfca77d232a |
| Verdict: | Malicious activity |
| Threats: | The Jigsaw ransomware, initially detected in 2016, encrypts files on compromised systems and requires a ransom payment in Bitcoin. If the ransom is not paid, the malware starts deleting files, increasing the pressure on victims to comply. Its source code is publicly accessible, allowing various threat actors to customize and repurpose the malware for different objectives. |
| Analysis date: | December 23, 2024, 07:59:21 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | B877491211BFCFF842912FD055588799 |
| SHA1: | D19E7A79B08BAE01B00AC447F6CFD236EF055474 |
| SHA256: | 6D230F1F3A10F78741545A9D6FBD43BBB0A6A55FEFCA245760D5DB92AC3CC1CD |
| SSDEEP: | 6144:zY4/Ezz+ML2q7kvNcezVavJdZP/B8ccT:z2XAGmNpdccT |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 4388)
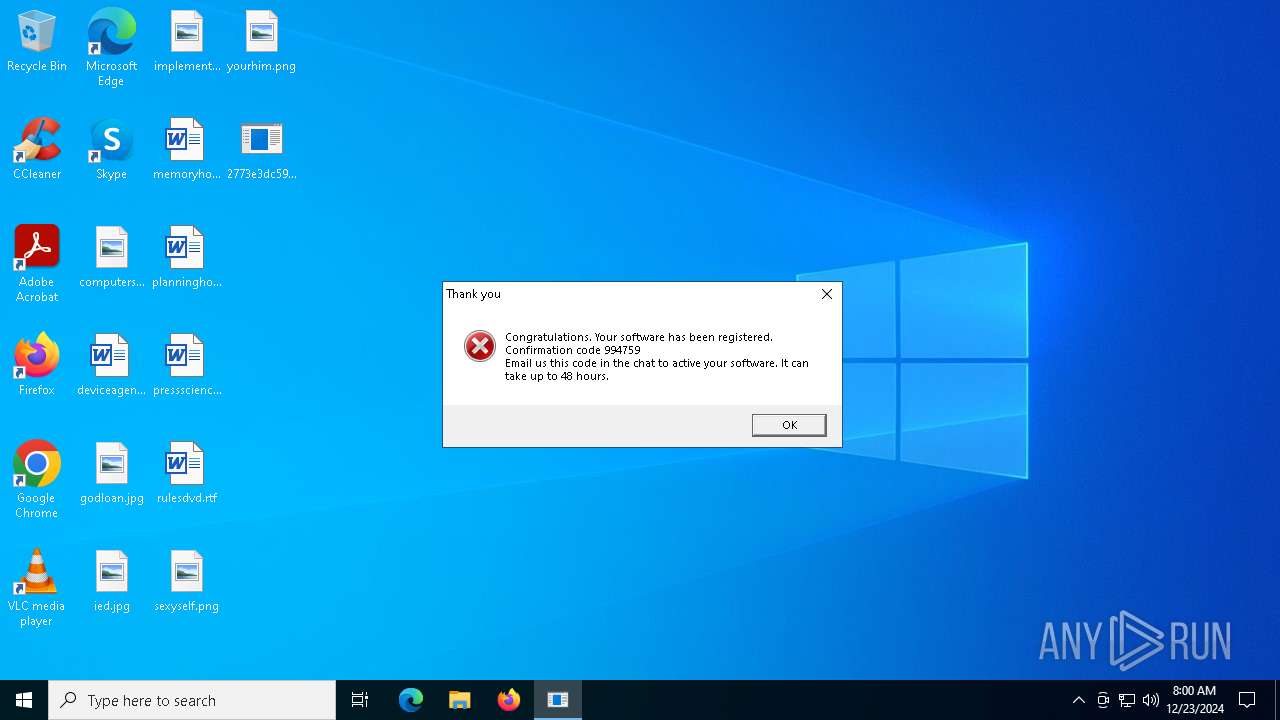
JIGSAW has been detected
- 2773e3dc59472296cb0024ba7715a64e.exe (PID: 4544)
RANSOMWARE has been detected
- drpbx.exe (PID: 624)
SUSPICIOUS
Executable content was dropped or overwritten
- 2773e3dc59472296cb0024ba7715a64e.exe (PID: 4544)
Creates file in the systems drive root
- drpbx.exe (PID: 624)
Starts itself from another location
- 2773e3dc59472296cb0024ba7715a64e.exe (PID: 4544)
INFO
Manual execution by a user
- 2773e3dc59472296cb0024ba7715a64e.exe (PID: 4544)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4388)
Creates files or folders in the user directory
- 2773e3dc59472296cb0024ba7715a64e.exe (PID: 4544)
The process uses the downloaded file
- WinRAR.exe (PID: 4388)
- 2773e3dc59472296cb0024ba7715a64e.exe (PID: 4544)
Checks supported languages
- drpbx.exe (PID: 624)
Creates files in the program directory
- drpbx.exe (PID: 624)
Reads the machine GUID from the registry
- drpbx.exe (PID: 624)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 788 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2016:04:13 18:02:34 |
| ZipCRC: | 0x3c351d58 |
| ZipCompressedSize: | 242871 |
| ZipUncompressedSize: | 290304 |
| ZipFileName: | 2773e3dc59472296cb0024ba7715a64e.exe |
Total processes
132
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 624 | "C:\Users\admin\AppData\Local\Drpbx\drpbx.exe" C:\Users\admin\Desktop\2773e3dc59472296cb0024ba7715a64e.exe | C:\Users\admin\AppData\Local\Drpbx\drpbx.exe | 2773e3dc59472296cb0024ba7715a64e.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Firefox Version: 37.0.2.5583 Modules
| |||||||||||||||
| 4388 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\HASH.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 4544 | "C:\Users\admin\Desktop\2773e3dc59472296cb0024ba7715a64e.exe" | C:\Users\admin\Desktop\2773e3dc59472296cb0024ba7715a64e.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Firefox Exit code: 0 Version: 37.0.2.5583 Modules
| |||||||||||||||
Total events
7 893
Read events
7 857
Write events
23
Delete events
13
Modification events
| (PID) Process: | (4388) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4388) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4388) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4388) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\HASH.zip | |||
| (PID) Process: | (4388) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4388) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4388) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4388) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4388) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (4388) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
3
Suspicious files
255
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 624 | drpbx.exe | C:\Program Files\Microsoft Office\AppXManifest.xml.fun | — | |
MD5:— | SHA256:— | |||
| 624 | drpbx.exe | C:\$WinREAgent\Backup\location.txt.fun | binary | |
MD5:2FDB7D8636728CE93ACAE2DE41F538F8 | SHA256:D686366FD52A64CB12967BC2695C36232BF8F62CA3932D62D57C5EADEF41AE43 | |||
| 624 | drpbx.exe | C:\$WinREAgent\Backup\ReAgent.xml.fun | binary | |
MD5:00F415906318124BC0B37ACD5DCE6223 | SHA256:C80FD782ECAD256B113A14772BD9AC86361BD779EA552BA489E441ACEED88381 | |||
| 4544 | 2773e3dc59472296cb0024ba7715a64e.exe | C:\Users\admin\AppData\Local\Drpbx\drpbx.exe | executable | |
MD5:2773E3DC59472296CB0024BA7715A64E | SHA256:3AE96F73D805E1D3995253DB4D910300D8442EA603737A1428B613061E7F61E7 | |||
| 624 | drpbx.exe | C:\Program Files\CUAssistant\CUAssistantRebootTask.xml.fun | binary | |
MD5:3DECCBF36AC50C9FE969A71327D43B94 | SHA256:2FF0AD3907E88AB1BFF199F323E6F08DD5945634E9648A6EAF86201826C35DFC | |||
| 624 | drpbx.exe | C:\$WinREAgent\Rollback.xml.fun | binary | |
MD5:FC47B2CE41A7FDE5B9FE09400D7FD699 | SHA256:57445F5BB379E9BFFF553F6A85331C4A066081A5CB33AEC7C5AEB78248105899 | |||
| 624 | drpbx.exe | C:\Program Files\CUAssistant\Snooze_80.png.fun | binary | |
MD5:3136F68140CAACF7B5001C3B0437F906 | SHA256:BE922969B1D02545BBACB3153B1963AF6946323082DA40EAFECF5B2A816AF760 | |||
| 624 | drpbx.exe | C:\found.000\dir0001.chk\WmiApRpl.h.fun | binary | |
MD5:49797E3DB38FF59262F6307F2C548D28 | SHA256:C422A7002739FE999632BFC9A904C5081EF8FC5411593DCD744E08FDF84D47A1 | |||
| 624 | drpbx.exe | C:\Program Files\CUAssistant\RestartNowPower_80.png.fun | binary | |
MD5:85CD50E7EAE1C698189FA3E9C113C66A | SHA256:BC990CE3B5A0FAE8AC38CA182648FAA76DEA908DA6D03F0AD75C21F88EF4DDA1 | |||
| 624 | drpbx.exe | C:\bootTel.dat.fun | binary | |
MD5:B91A2A4E7E88D20EFEA15DE4BA074262 | SHA256:968F0E759D606DB20724DF46B8756AD3EFFBA3C090113ED4705F73F9841FFF2E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
34
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6328 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7156 | SIHClient.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7156 | SIHClient.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3700 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.19.217.218:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5064 | SearchApp.exe | 23.212.110.178:443 | www.bing.com | Akamai International B.V. | CZ | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 40.126.32.134:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |