| File name: | kiddionsmodmenu.exe |
| Full analysis: | https://app.any.run/tasks/f1df1743-00d7-45ee-a085-9d08c396b289 |
| Verdict: | Malicious activity |
| Threats: | Ransomware is a type of malicious software that locks users out of their system or data using different methods to force them to pay a ransom. Most often, such programs encrypt files on an infected machine and demand a fee to be paid in exchange for the decryption key. Additionally, such programs can be used to steal sensitive information from the compromised computer and even conduct DDoS attacks against affected organizations to pressure them into paying. |
| Analysis date: | May 14, 2024, 11:00:05 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 88E737816CC5F3E3809152C5F9DAD5BE |
| SHA1: | 56DEDF42285C74795F714DBAC7782A5D0E695A97 |
| SHA256: | 6D09D43C755D5081924748104AC487AFADAF68ADD75D85FEB2A256DE032A5E2C |
| SSDEEP: | 6144:FiMwXBYxymBX9Gt8pbSslwq3zTOXY9C+w6jhglvTo7xVoZhEVjDJt/r0dYhHCgBC:FinmxyENGiZzTO76j62xuZQr0fgBzh8x |
MALICIOUS
Drops the executable file immediately after the start
- kiddionsmodmenu.exe (PID: 7100)
- powershell.exe (PID: 4360)
Run PowerShell with an invisible window
- powershell.exe (PID: 3976)
- powershell.exe (PID: 4360)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 3976)
- powershell.exe (PID: 4360)
Gets or sets the symmetric key that is used for encryption and decryption (POWERSHELL)
- powershell.exe (PID: 3976)
- powershell.exe (PID: 4360)
Gets or sets the initialization vector for the symmetric algorithm (POWERSHELL)
- powershell.exe (PID: 3976)
- powershell.exe (PID: 4360)
XWORM has been detected (YARA)
- powershell.exe (PID: 4360)
SUSPICIOUS
Reads the date of Windows installation
- kiddionsmodmenu.exe (PID: 7100)
Starts CMD.EXE for commands execution
- kiddionsmodmenu.exe (PID: 7100)
- cmd.exe (PID: 7140)
- wscript.exe (PID: 5716)
- cmd.exe (PID: 4108)
Reads security settings of Internet Explorer
- kiddionsmodmenu.exe (PID: 7100)
Cryptography encrypted command line is found
- cmd.exe (PID: 5420)
- cmd.exe (PID: 4284)
Executing commands from a ".bat" file
- kiddionsmodmenu.exe (PID: 7100)
- cmd.exe (PID: 4108)
- cmd.exe (PID: 7140)
- wscript.exe (PID: 5716)
Application launched itself
- cmd.exe (PID: 7140)
- cmd.exe (PID: 4108)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7140)
- cmd.exe (PID: 4108)
Connects to unusual port
- powershell.exe (PID: 4360)
Unusual connection from system programs
- powershell.exe (PID: 4360)
The Powershell connects to the Internet
- powershell.exe (PID: 4360)
The process executes VB scripts
- powershell.exe (PID: 3976)
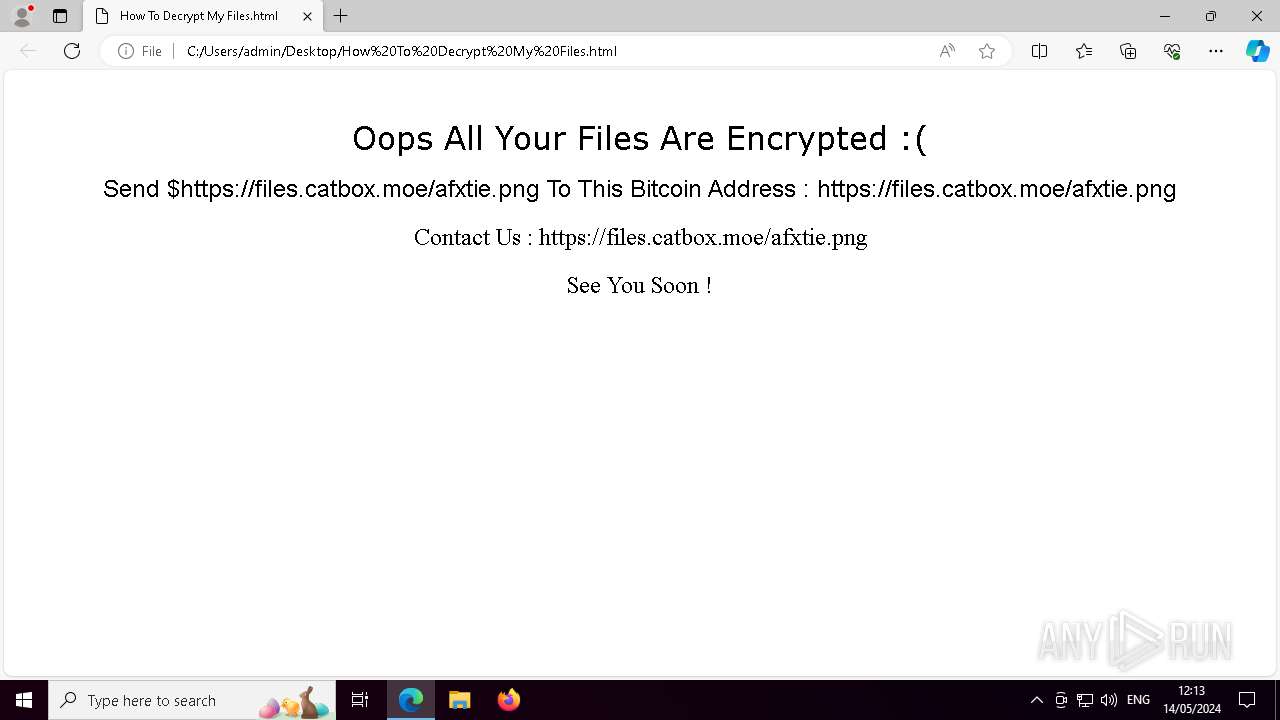
Creates files like ransomware instruction
- powershell.exe (PID: 4360)
Runs shell command (SCRIPT)
- wscript.exe (PID: 5716)
INFO
Reads the computer name
- kiddionsmodmenu.exe (PID: 7100)
- identity_helper.exe (PID: 4724)
Checks current location (POWERSHELL)
- powershell.exe (PID: 3976)
- powershell.exe (PID: 4360)
Gets data length (POWERSHELL)
- powershell.exe (PID: 3976)
- powershell.exe (PID: 4360)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 3976)
- powershell.exe (PID: 4360)
Checks supported languages
- kiddionsmodmenu.exe (PID: 7100)
- identity_helper.exe (PID: 4724)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 3976)
- powershell.exe (PID: 4360)
Application launched itself
- msedge.exe (PID: 3808)
Reads Microsoft Office registry keys
- msedge.exe (PID: 3808)
Create files in a temporary directory
- kiddionsmodmenu.exe (PID: 7100)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
XWorm
(PID) Process(4360) powershell.exe
C294.156.8.167:2020
Keys
AEScasttteristhebest123
Options
Splitter<Xwormmm>
Sleep time3
USB drop nameXWorm V5.2
Mutex8sPZSP21r8KwS1LM
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2010:11:18 16:27:32+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 82944 |
| InitializedDataSize: | 205312 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1373c |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.0.0.0 |
| ProductVersionNumber: | 2.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Islam Adel |
| FileDescription: | Created by BAT2EXE.net |
| FileVersion: | 2 |
| InternalName: | bat2exe.exe |
| LegalCopyright: | Islam Adel |
| OriginalFileName: | bat2exe.exe |
| ProductName: | BAT2EXE |
| ProductVersion: | 2 |
Total processes
163
Monitored processes
38
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 32 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5840 --field-trial-handle=2332,i,17276981022033472063,9733129555016421831,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 256 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6048 --field-trial-handle=2332,i,17276981022033472063,9733129555016421831,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2124 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5448 --field-trial-handle=2332,i,17276981022033472063,9733129555016421831,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2424 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5548 --field-trial-handle=2332,i,17276981022033472063,9733129555016421831,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3232 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_search_indexer.mojom.SearchIndexerInterfaceBroker --lang=en-US --service-sandbox-type=search_indexer --message-loop-type-ui --no-appcompat-clear --mojo-platform-channel-handle=5904 --field-trial-handle=2332,i,17276981022033472063,9733129555016421831,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3396 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5756 --field-trial-handle=2332,i,17276981022033472063,9733129555016421831,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3808 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --single-argument C:\Users\admin\Desktop\How To Decrypt My Files.html | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3896 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=122.0.2365.59 --initial-client-data=0x2ec,0x2f0,0x2f4,0x2e8,0x2fc,0x7ffcf45f5fd8,0x7ffcf45f5fe4,0x7ffcf45f5ff0 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3912 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5640 --field-trial-handle=2332,i,17276981022033472063,9733129555016421831,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3976 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -w hidden | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 4294967295 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
30 464
Read events
30 345
Write events
116
Delete events
3
Modification events
| (PID) Process: | (7100) kiddionsmodmenu.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (7100) kiddionsmodmenu.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (7100) kiddionsmodmenu.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (7100) kiddionsmodmenu.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3976) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3976) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3976) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3976) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3976) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Windows_Log_277_str |
Value: wscript.exe "C:\Users\admin\AppData\Roaming\Windows_Log_277.vbs" | |||
| (PID) Process: | (3976) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbs\OpenWithProgids |
| Operation: | write | Name: | VBSFile |
Value: | |||
Executable files
1
Suspicious files
147
Text files
53
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4360 | powershell.exe | C:\Users\admin\NTUSER.DAT.ENC | — | |
MD5:— | SHA256:— | |||
| 4360 | powershell.exe | C:\Users\admin\NTUSER.DAT{53b39e88-18c4-11ea-a811-000d3aa4692b}.TMContainer00000000000000000002.regtrans-ms.ENC | — | |
MD5:— | SHA256:— | |||
| 3976 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_zhhcbnmo.f0v.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4360 | powershell.exe | C:\Users\admin\ntuser.dat.LOG2.ENC | binary | |
MD5:EF5AAE18E4593A8DC38878CF347A22B4 | SHA256:D5AC89F67B05560D5187FCA02A1CF4F616B9C4343A7923FD2BBC4CD0FE559788 | |||
| 4360 | powershell.exe | C:\Users\admin\Contacts\desktop.ini.ENC | binary | |
MD5:23553EBB3D7F157587611FFB4228A4C2 | SHA256:03DC22EFF87CE205D923A0FC13E96FBDB3B330A4BF9C371E4E45C20E7778BDB8 | |||
| 4360 | powershell.exe | C:\Users\admin\ntuser.ini.ENC | binary | |
MD5:8208AC543788E88E13BE1061DD91A3F3 | SHA256:5F5D0C0E7B468EE8A2E41A76F7563ECA03C97992717840ED68D24AD501E55EA7 | |||
| 4664 | FileCoAuth.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\logs\Common\FileCoAuth-2024-05-14.1111.4664.1.aodl | binary | |
MD5:28DCA2FF4B34B5A52A2E59DF202A6ED3 | SHA256:33BACCB7296F1ED1F995FC77A23049F261CF391AC0388F9E8DD161F8C17B7F94 | |||
| 4360 | powershell.exe | C:\Users\admin\ntuser.dat.LOG1.ENC | binary | |
MD5:EF5AAE18E4593A8DC38878CF347A22B4 | SHA256:D5AC89F67B05560D5187FCA02A1CF4F616B9C4343A7923FD2BBC4CD0FE559788 | |||
| 4360 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\ModuleAnalysisCache | binary | |
MD5:8B8A832FCE2174C8FEE26B70F2483FBB | SHA256:0FBA3A37EF443507F533A7C3F31C0B5826EA416B95FDE43479E02D4E0C29400B | |||
| 6724 | FileCoAuth.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\logs\Common\FileCoAuth-2024-05-14.1101.6724.1.odl | binary | |
MD5:42624EC9851EE400D6A1B084C34C5FF5 | SHA256:BB0AD8E85F4F215C62BF7985F19B16E4F7D4342FC131A1ABF092589EB221BA5B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
64
TCP/UDP connections
58
DNS requests
48
Threats
181
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4716 | SIHClient.exe | GET | 200 | 20.12.23.50:443 | https://slscr.update.microsoft.com/SLS/%7BE7A50285-D08D-499D-9FF8-180FDC2332BC%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
4716 | SIHClient.exe | GET | 304 | 20.12.23.50:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
4716 | SIHClient.exe | GET | 200 | 20.12.23.50:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
4716 | SIHClient.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | unknown |
4716 | SIHClient.exe | GET | 200 | 20.3.187.198:443 | https://fe3cr.delivery.mp.microsoft.com/clientwebservice/ping | unknown | — | — | unknown |
4716 | SIHClient.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | unknown |
4716 | SIHClient.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
4716 | SIHClient.exe | GET | 200 | 2.19.217.218:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | — | — | unknown |
4716 | SIHClient.exe | GET | 200 | 20.12.23.50:443 | https://slscr.update.microsoft.com/sls/ping | unknown | — | — | unknown |
— | — | POST | 204 | 95.100.146.19:443 | https://www.bing.com/threshold/xls.aspx | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4364 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5140 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5456 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4360 | powershell.exe | 94.156.8.167:2020 | — | Vivacom | BG | unknown |
2908 | OfficeClickToRun.exe | 20.42.72.131:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4716 | SIHClient.exe | 20.114.59.183:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4716 | SIHClient.exe | 2.19.217.218:80 | www.microsoft.com | Akamai International B.V. | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| unknown |
business.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] Xworm |
4360 | powershell.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 15 |
— | — | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] Xworm |
178 ETPRO signatures available at the full report