| File name: | 6cad0a9c721959e6f3c47a33dc6a3e34db3c07e4e5f2f563e4db30fe64838cd7.apk |
| Full analysis: | https://app.any.run/tasks/cb044b48-f0cd-49d3-baa5-acbe6af77e68 |
| Verdict: | Malicious activity |
| Threats: | SpyNote, also known as SpyMax and CypherRat, is a powerful Android malware family designed primarily for surveillance and data theft, often categorized as a Remote Access Trojan (RAT). Originally emerged in 2016, SpyNote has evolved significantly, with new variants continuing to appear as recently as 2023–2025. |
| Analysis date: | March 24, 2025, 18:22:35 |
| OS: | Android 14 |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.android.package-archive |
| File info: | Android package (APK), with AndroidManifest.xml, with APK Signing Block |
| MD5: | 1C53DDD5D8720F7A59572BDDDB603597 |
| SHA1: | 1B86E6610D292FB46E87BB135ED7457A4FB3AEEB |
| SHA256: | 6CAD0A9C721959E6F3C47A33DC6A3E34DB3C07E4E5F2F563E4DB30FE64838CD7 |
| SSDEEP: | 98304:IpfeZrnF+cvMX1faYdS8TFLHF5ejW6814SpTNCiF0YCXXzyb0aSAWieur9/dLDko:TjIYJy |
MALICIOUS
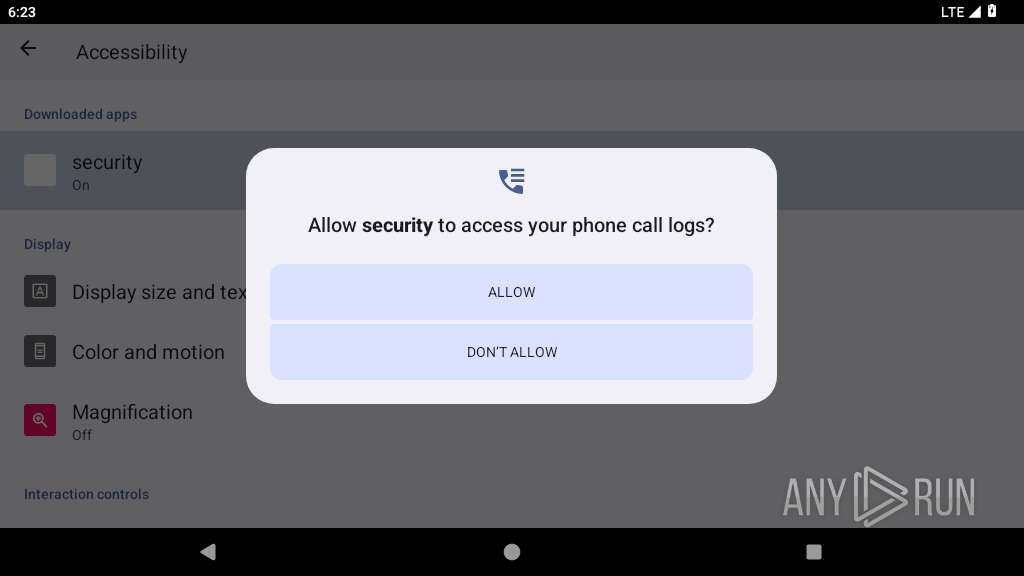
Uses APIs to record audio and video from various sources
- app_process64 (PID: 2273)
SUSPICIOUS
Starts a service
- app_process64 (PID: 2273)
Abuses foreground service for persistence
- app_process64 (PID: 2273)
Launches a new activity
- app_process64 (PID: 2273)
Detects when screen powers off
- app_process64 (PID: 2273)
Accesses external device storage files
- app_process64 (PID: 2273)
Retrieves a list of running services
- app_process64 (PID: 2273)
Triggers notification to user
- app_process64 (PID: 2273)
Acquires a wake lock to keep the device awake
- app_process64 (PID: 2273)
Checks if the device's lock screen is showing
- app_process64 (PID: 2273)
Creates a WakeLock to manage power state
- app_process64 (PID: 2273)
Updates the value of a system setting
- app_process64 (PID: 2273)
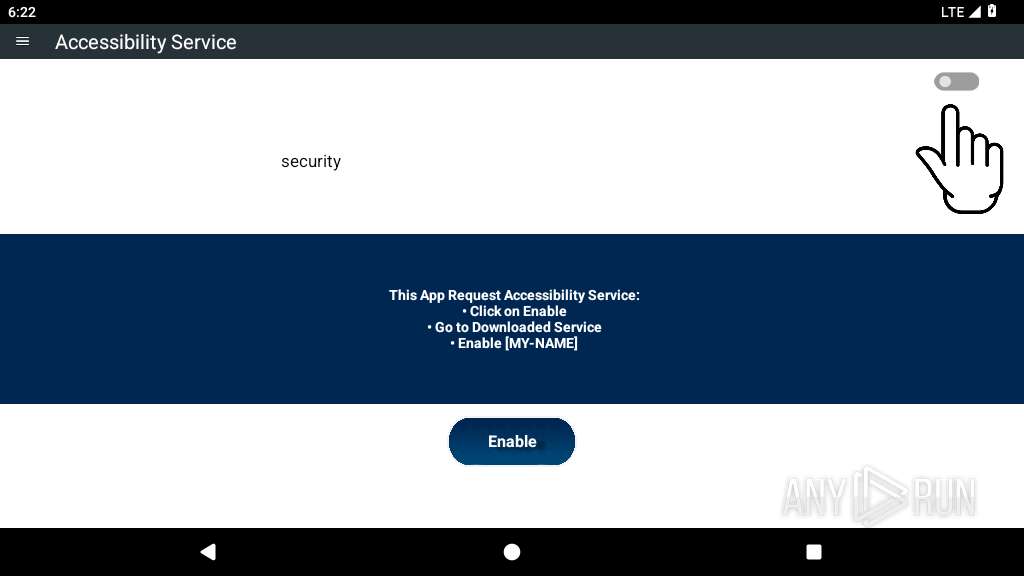
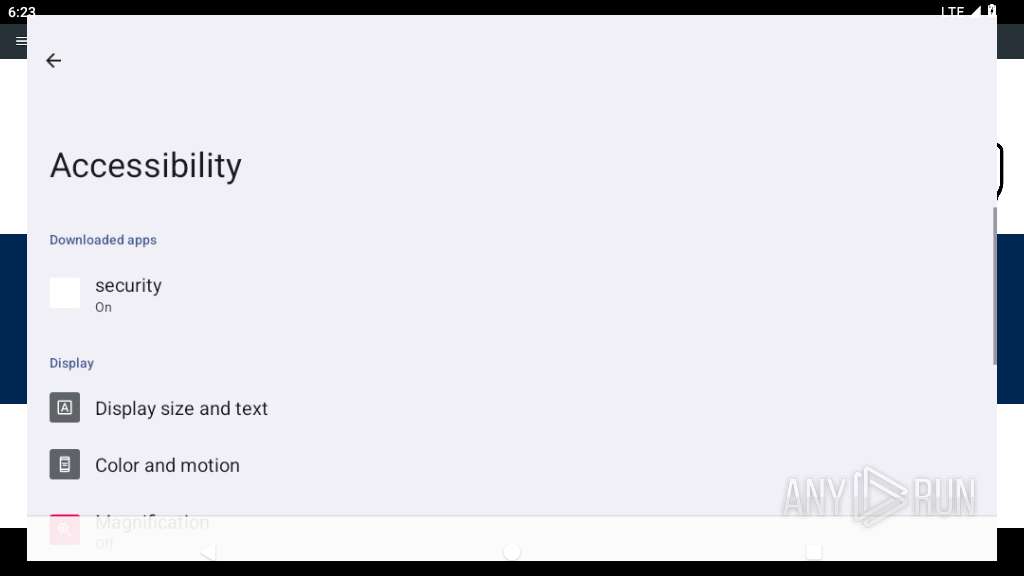
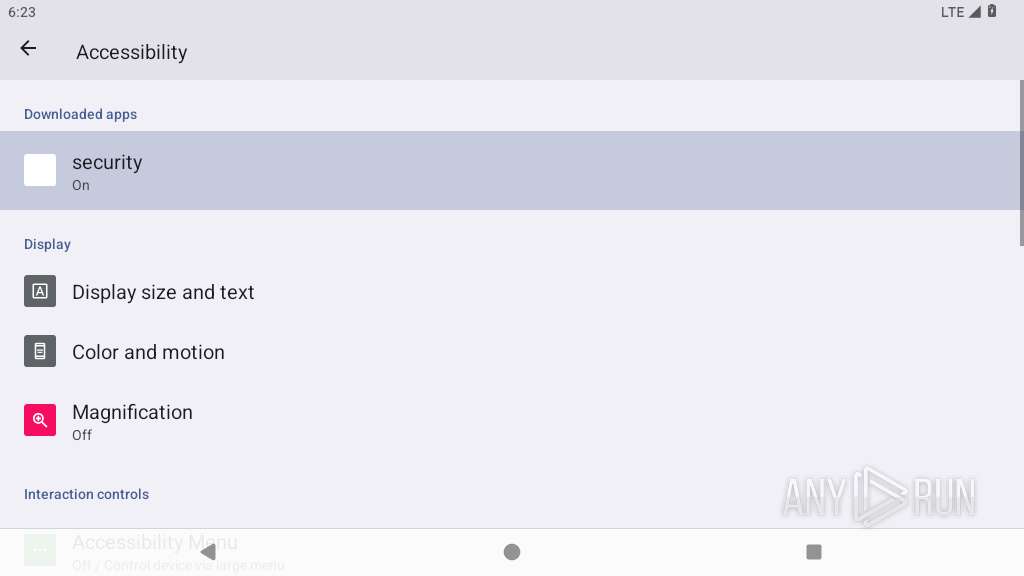
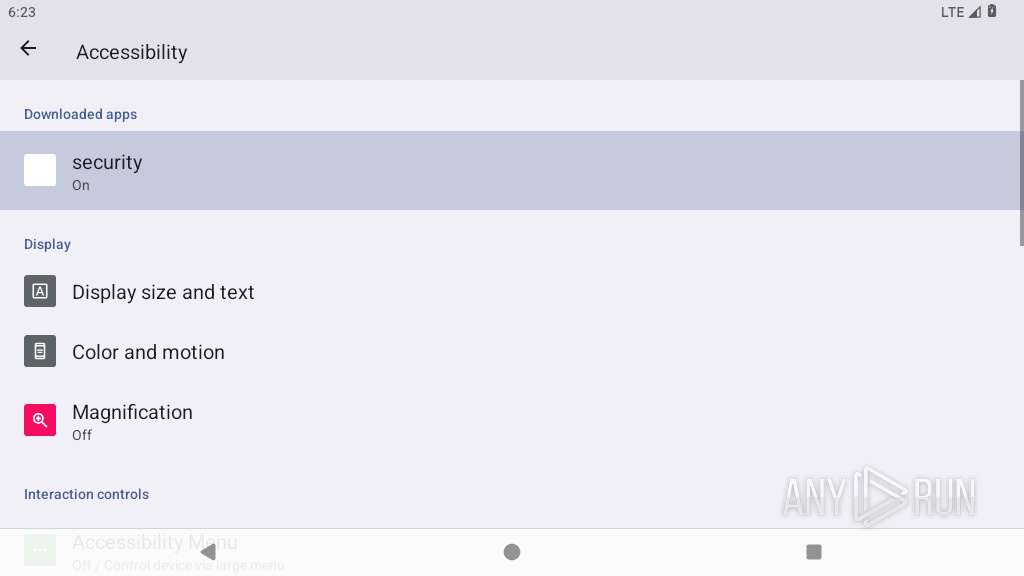
Requests access to accessibility settings
- app_process64 (PID: 2273)
Overlays content on other applications
- app_process64 (PID: 2273)
Updates data in the storage of application settings (SharedPreferences)
- app_process64 (PID: 2273)
Intercepts events for accessibility services
- app_process64 (PID: 2273)
Performs UI accessibility actions without user input
- app_process64 (PID: 2273)
Leverages accessibility to control apps
- app_process64 (PID: 2273)
Checks exemption from battery optimization
- app_process64 (PID: 2273)
Connects to unusual port
- app_process64 (PID: 2273)
Prevents its uninstallation by user
- app_process64 (PID: 2273)
INFO
Dynamically registers broadcast event listeners
- app_process64 (PID: 2273)
Retrieves the value of a secure system setting
- app_process64 (PID: 2273)
Retrieves data from storage of application settings (SharedPreferences)
- app_process64 (PID: 2273)
Creates and writes local files
- app_process64 (PID: 2273)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .apk | | | Android Package (62.1) |
|---|---|---|
| .jar | | | Java Archive (17.1) |
| .zan | | | BlueEyes Animation (15.9) |
| .zip | | | ZIP compressed archive (4.7) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0808 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:02:26 00:42:48 |
| ZipCRC: | 0xd1e338df |
| ZipCompressedSize: | 8152 |
| ZipUncompressedSize: | 44464 |
| ZipFileName: | AndroidManifest.xml |
Total processes
127
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 2273 | bottom.vote.himself | /system/bin/app_process64 | app_process64 | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2349 | com.android.systemui.accessibility.accessibilitymenu | /system/bin/app_process64 | — | app_process64 |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
0
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2273 | app_process64 | /data/user/0/bottom.vote.himself/shared_prefs/bottom.vote.himself.xml | xml | |
MD5:— | SHA256:— | |||
| 2273 | app_process64 | /data/user/0/bottom.vote.himself/cache/oat_primary/arm64/base.2273.tmp | — | |
MD5:— | SHA256:— | |||
| 2273 | app_process64 | /storage/emulated/0/Config/sys/apps/log/log-2025-03-24.txt | — | |
MD5:— | SHA256:— | |||
| 2273 | app_process64 | /data/user/0/bottom.vote.himself/shared_prefs/bottom.vote.himself_preferences.xml | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
10
DNS requests
5
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 204 | 142.250.74.3:80 | http://connectivitycheck.gstatic.com/generate_204 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
447 | mdnsd | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 8.8.8.8:853 | — | GOOGLE | US | malicious |
— | — | 216.239.35.12:123 | time.android.com | — | — | whitelisted |
— | — | 8.8.8.8:443 | — | — | — | malicious |
— | — | 216.58.207.196:443 | www.google.com | GOOGLE | US | whitelisted |
— | — | 142.250.74.3:80 | connectivitycheck.gstatic.com | GOOGLE | US | whitelisted |
— | — | 173.194.69.81:443 | — | GOOGLE | US | unknown |
2273 | app_process64 | 196.251.66.190:4455 | — | — | ZA | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.google.com |
| whitelisted |
time.android.com |
| whitelisted |
google.com |
| whitelisted |
connectivitycheck.gstatic.com |
| whitelisted |
EbQA6d-dnsotls-ds.metric.gstatic.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Android Device Connectivity Check |