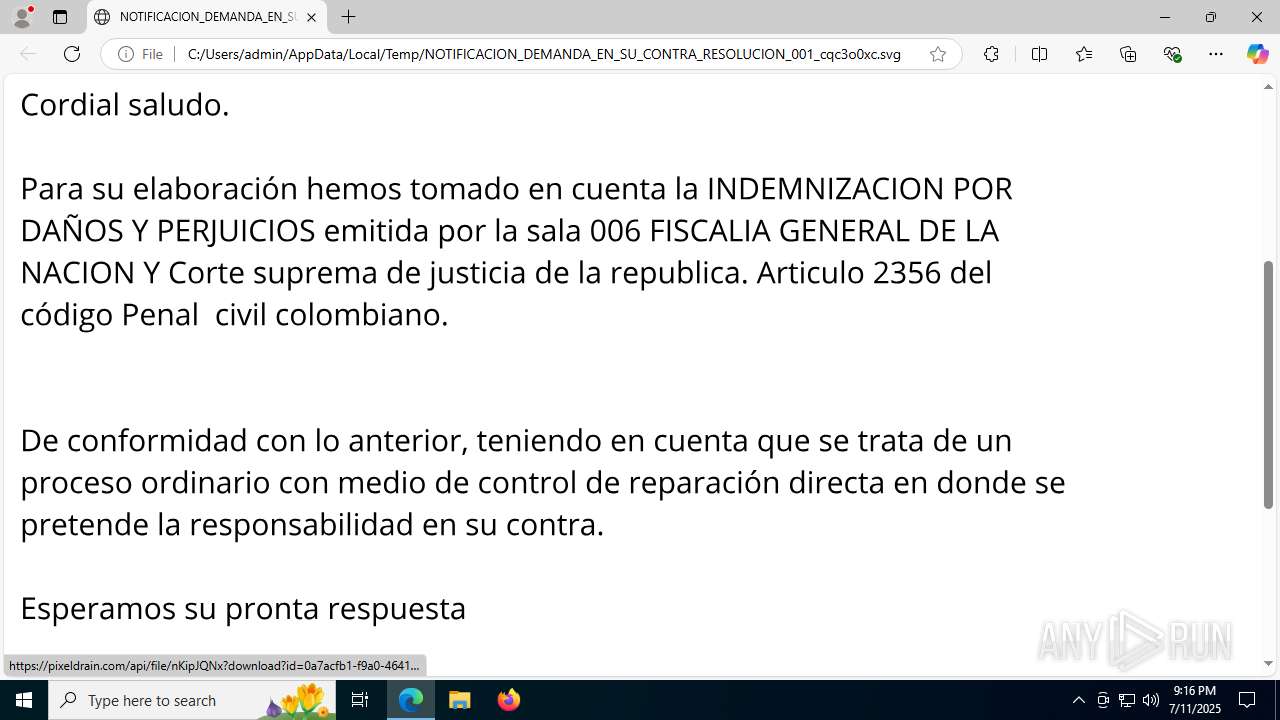
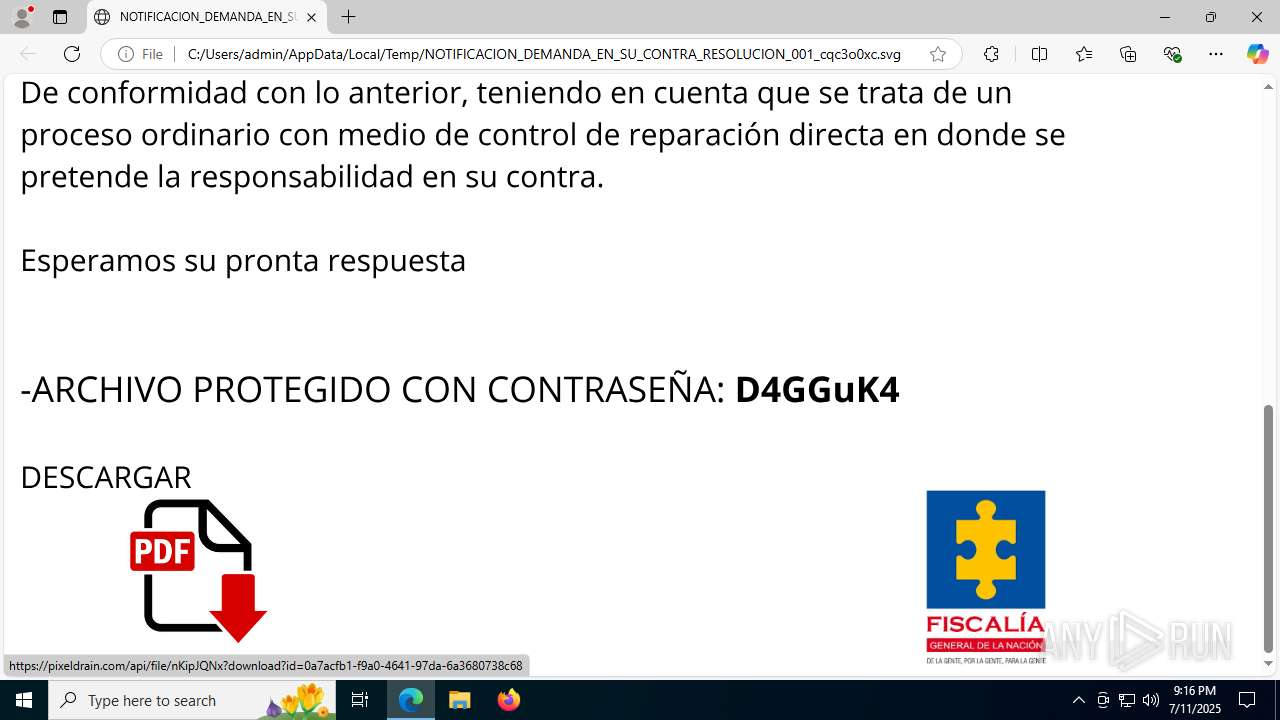
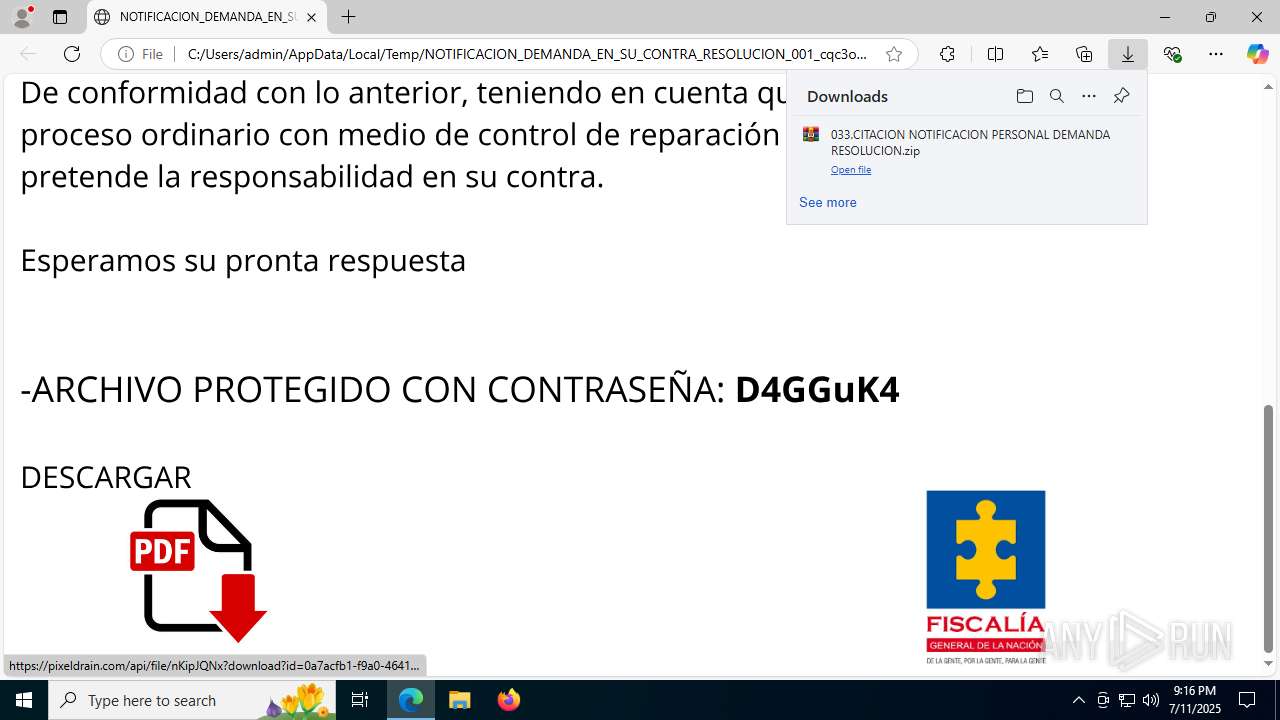
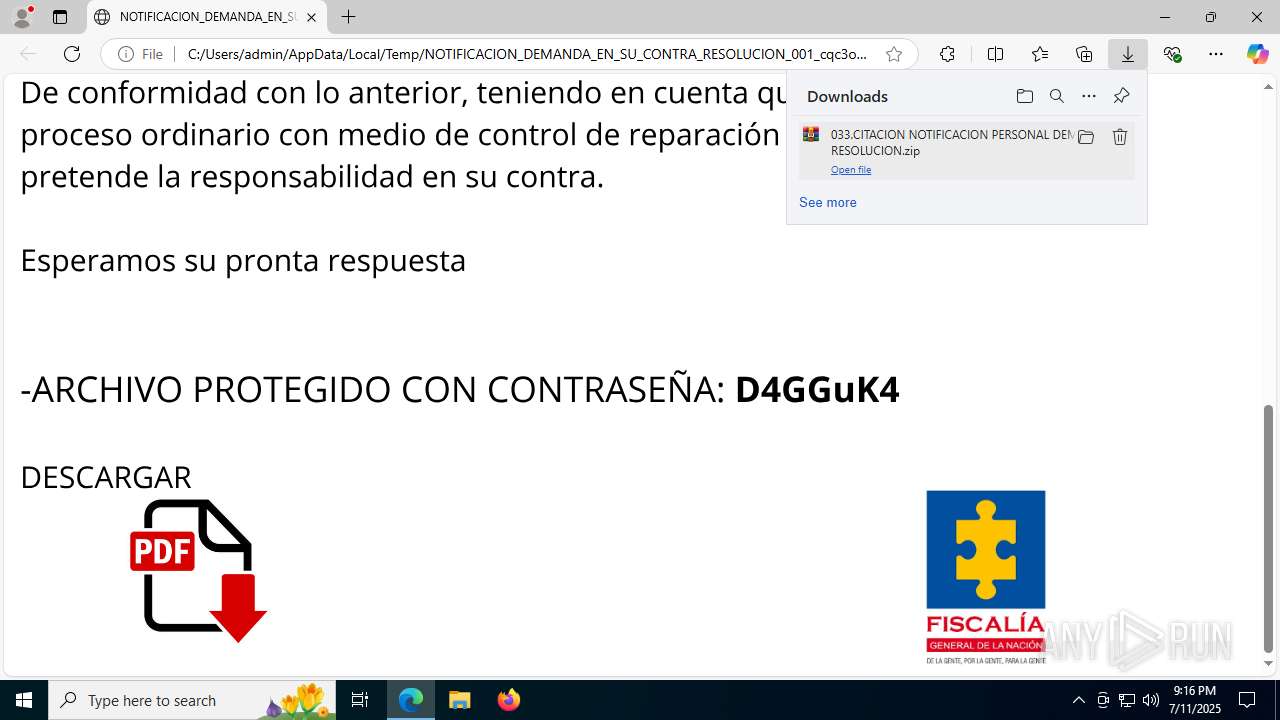
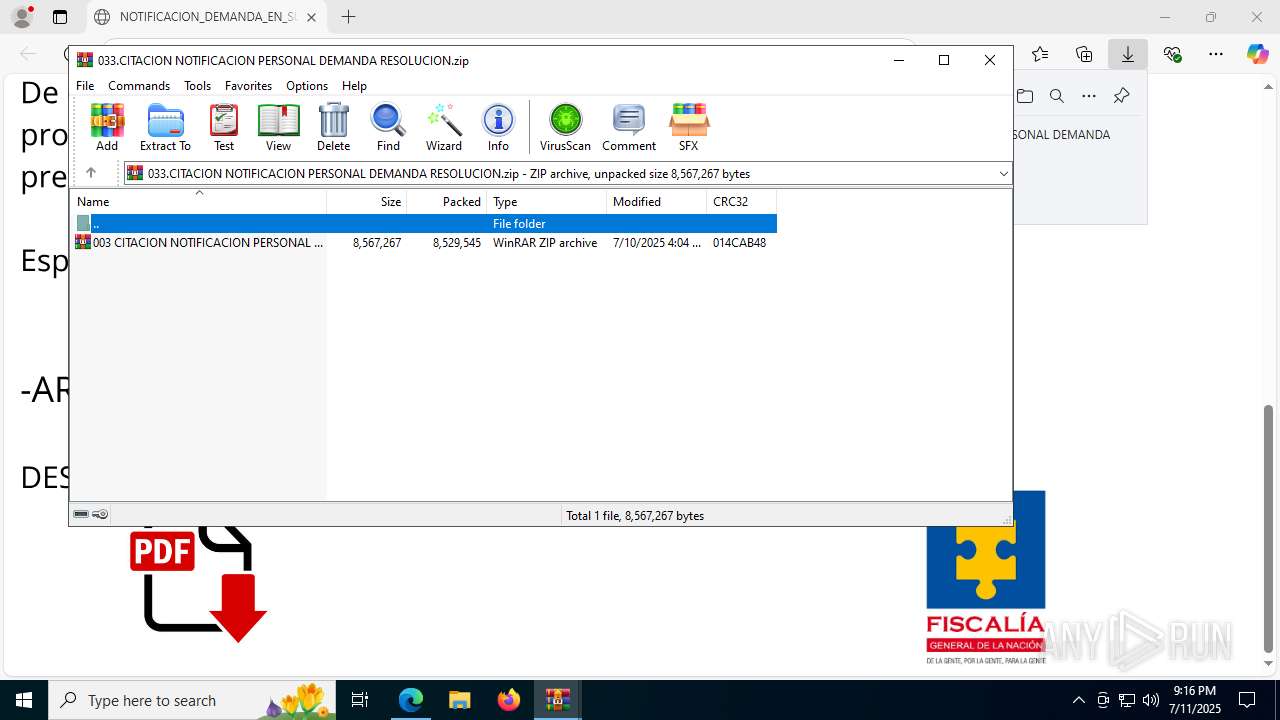
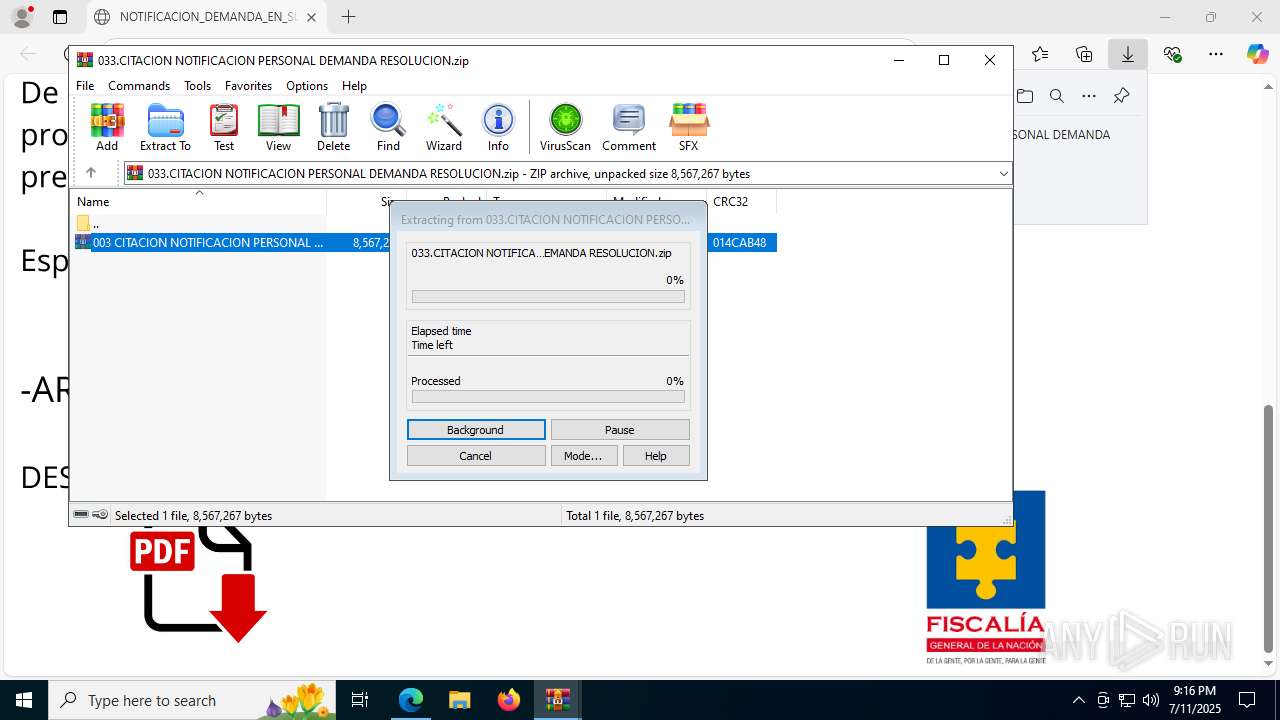
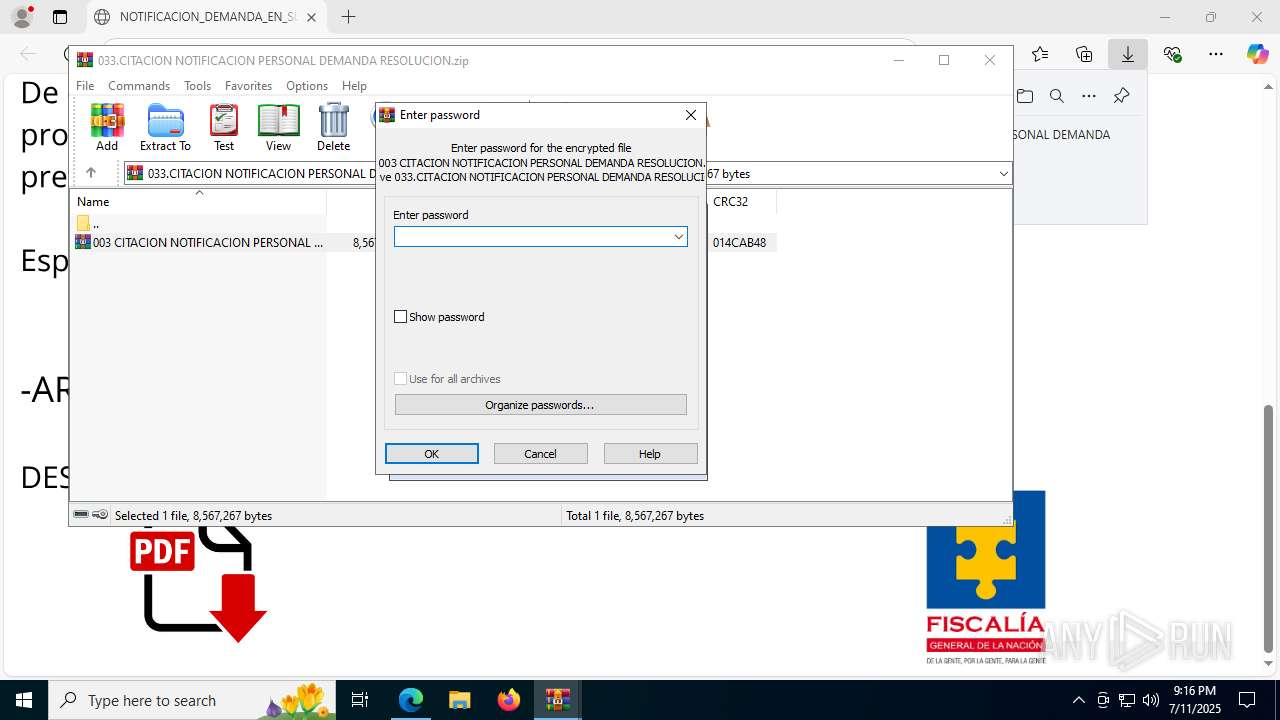
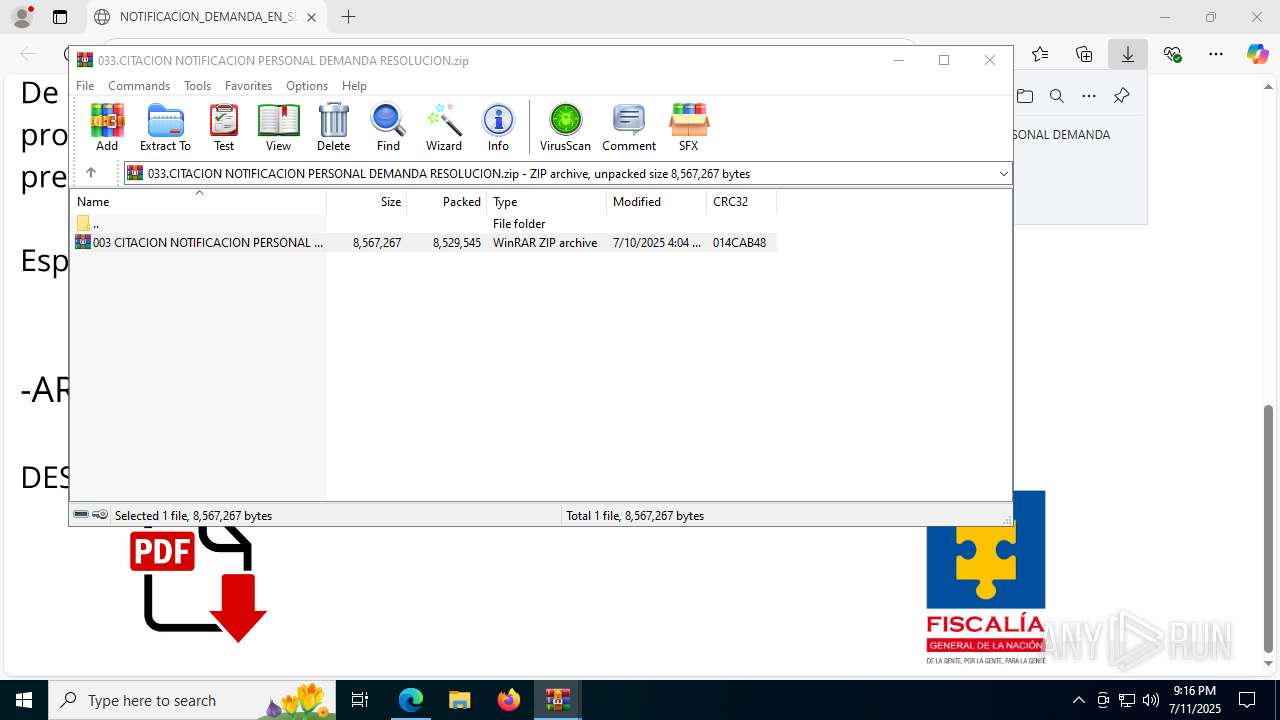
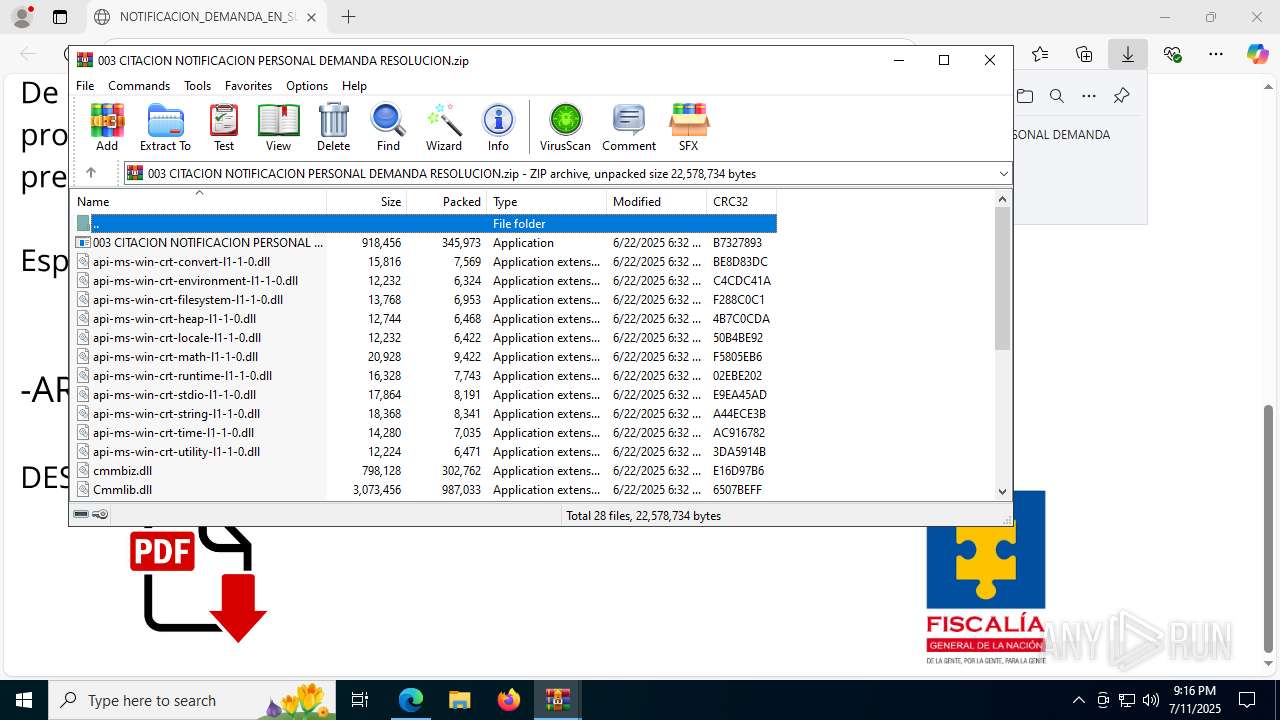
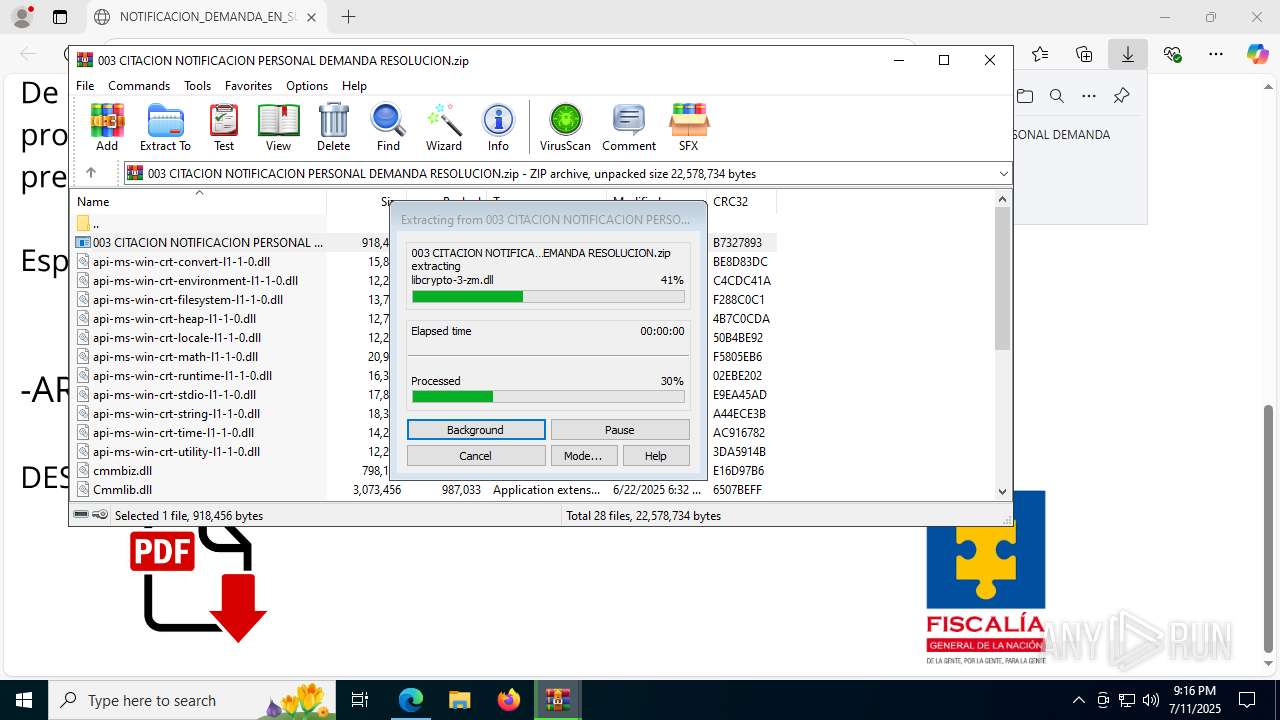
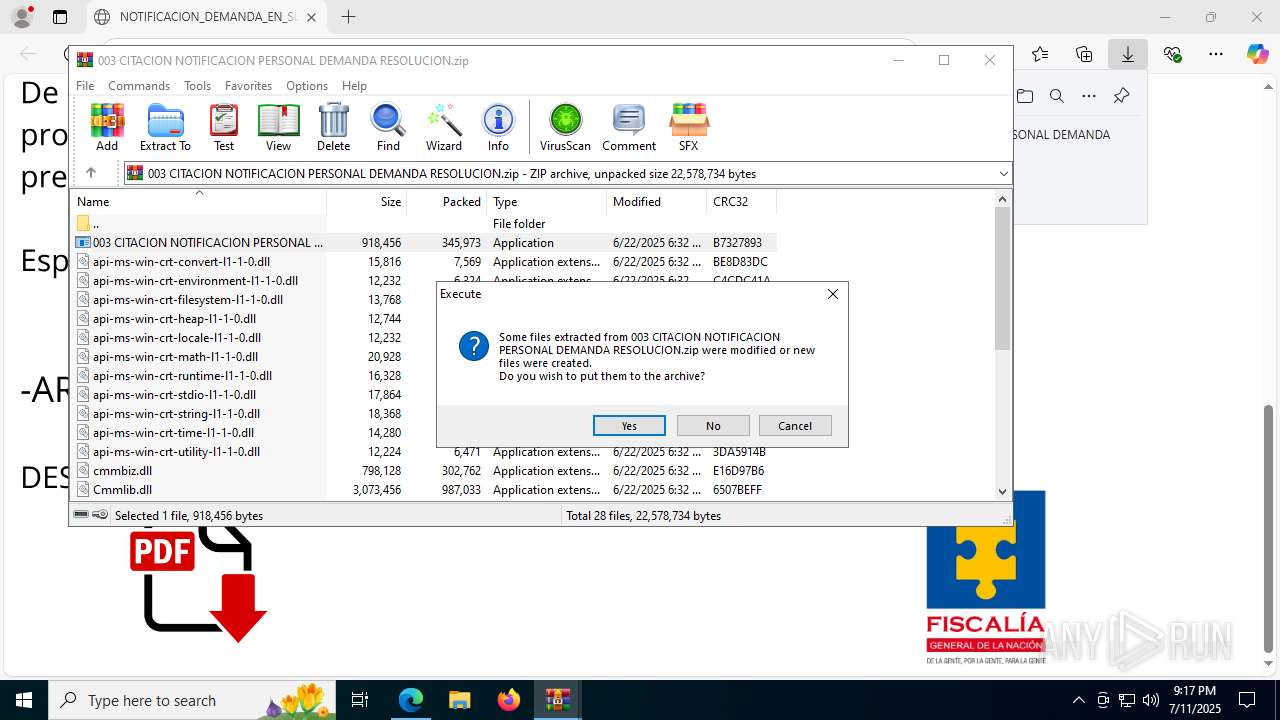
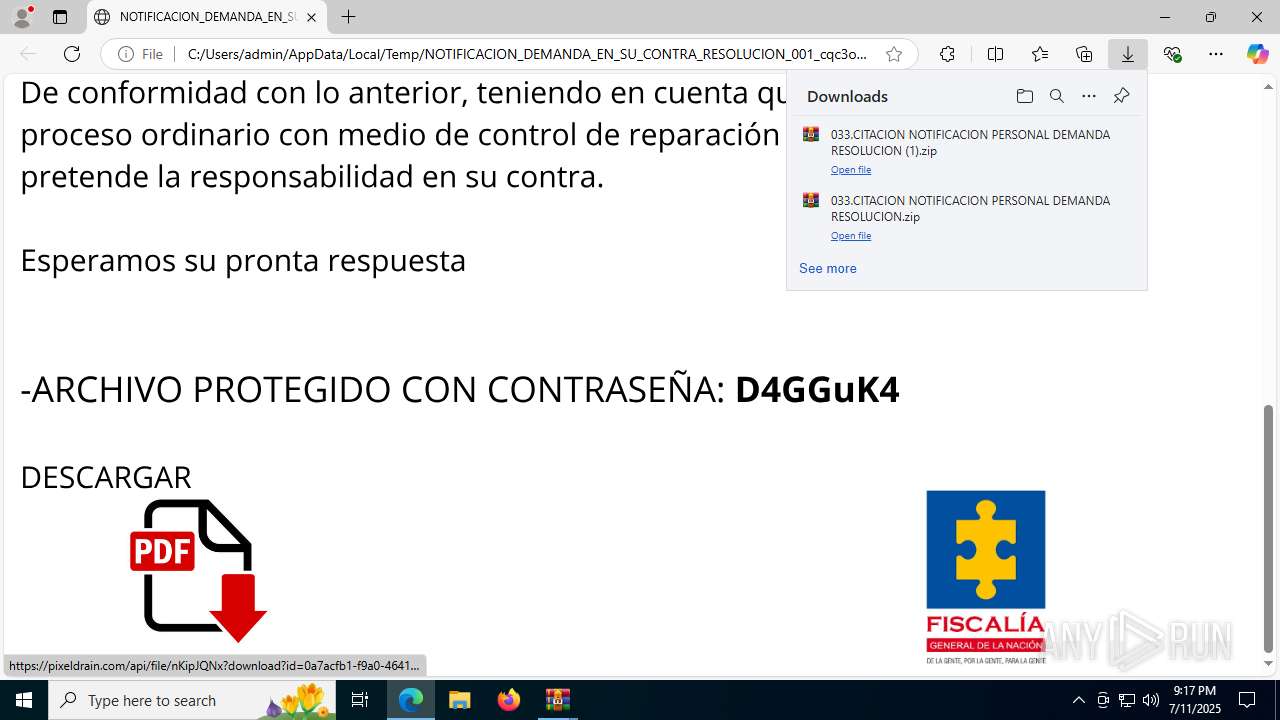
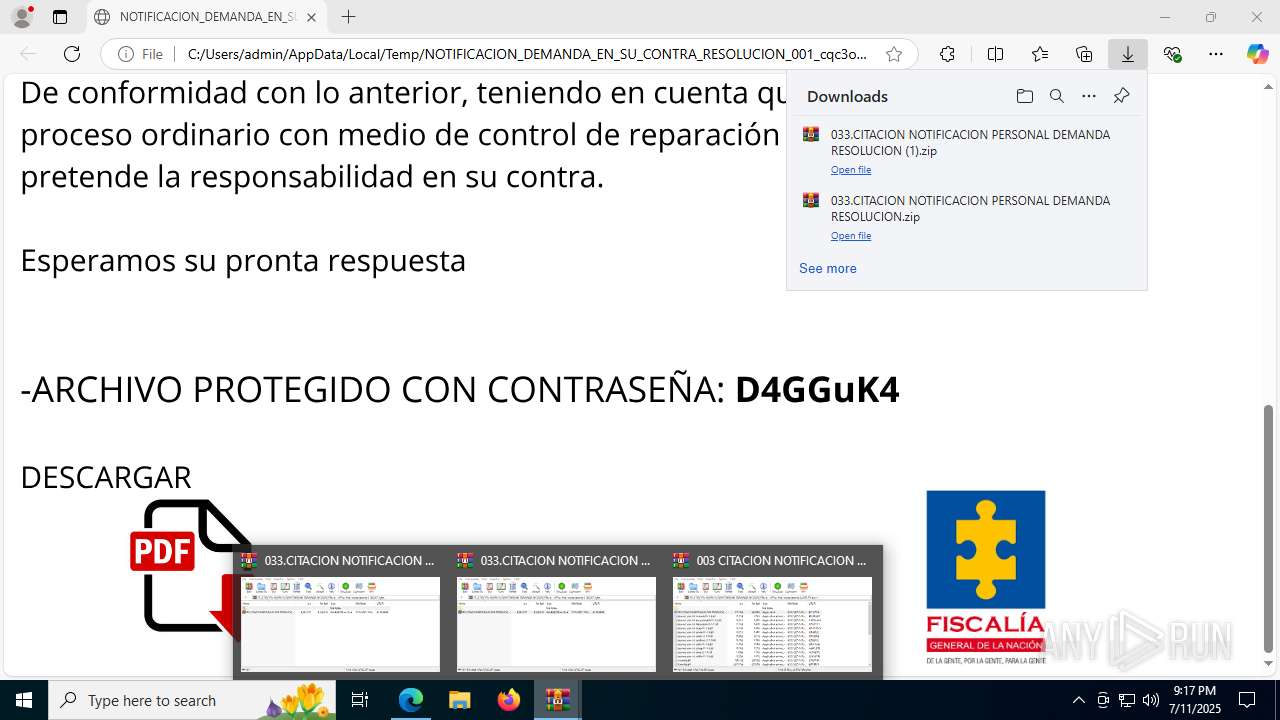
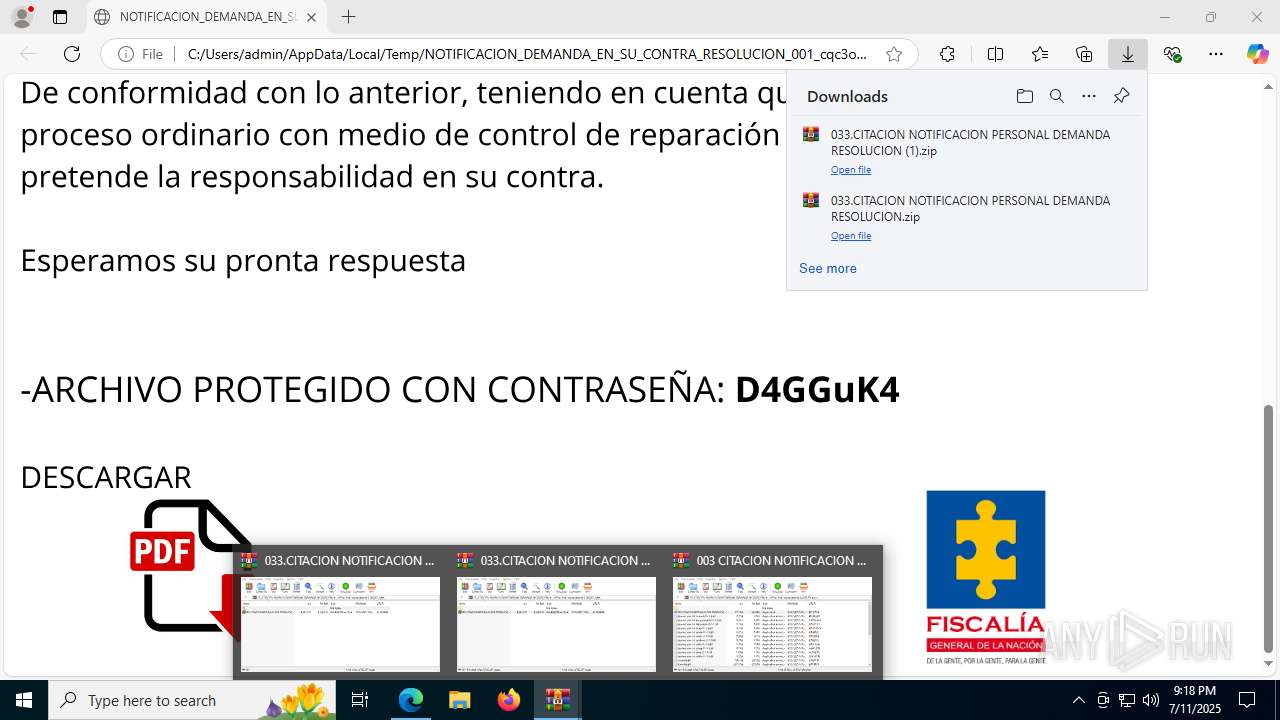
| File name: | NOTIFICACION_DEMANDA_EN_SU_CONTRA_RESOLUCION_001_cqc3o0xc.svg |
| Full analysis: | https://app.any.run/tasks/aa32c13a-cf61-414c-8fea-df1c467cd3ca |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | July 11, 2025, 21:16:12 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | image/svg+xml |
| File info: | SVG Scalable Vector Graphics image |
| MD5: | 3CBA52FD49F153EE2A02FAD7129BEAF8 |
| SHA1: | 46592D1DBE6E7C46CBA3F508A3BFE22C70CF9E9B |
| SHA256: | 6C0DF6766666EF853372A12B01C3306977379B7564B67227C3F6F73E5569EA19 |
| SSDEEP: | 6144:UzGWfeZwIsM7gxie6uDQczGWfeZwIsM7gxie6uDQn:mfhzM8xiUDQufhzM8xiUDQn |
MALICIOUS
ASYNCRAT has been detected (MUTEX)
- AddInProcess32.exe (PID: 6796)
Actions looks like stealing of personal data
- AddInProcess32.exe (PID: 6796)
Steals credentials from Web Browsers
- AddInProcess32.exe (PID: 6796)
ASYNCRAT has been detected (YARA)
- AddInProcess32.exe (PID: 6796)
ASYNCRAT has been detected (SURICATA)
- AddInProcess32.exe (PID: 6796)
Bypass User Account Control (Modify registry)
- reg.exe (PID: 8116)
UAC/LUA settings modification
- LowerUAC_2732921611.exe (PID: 3948)
Changes Windows Defender settings
- cmd.exe (PID: 7440)
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 7440)
Adds process to the Windows Defender exclusion list
- cmd.exe (PID: 7440)
NESHTA mutex has been found
- enggww.exe (PID: 7816)
Changes the autorun value in the registry
- enggww.exe (PID: 7344)
- AMARRADO.exe (PID: 4884)
REMCOS mutex has been found
- enggww.exe (PID: 7344)
- AMARRADO.exe (PID: 4884)
REMCOS has been detected
- AMARRADO.exe (PID: 4884)
REMCOS has been detected (YARA)
- AMARRADO.exe (PID: 4884)
Executing a file with an untrusted certificate
- FileCoAuth.exe (PID: 1760)
REMCOS has been detected (SURICATA)
- AMARRADO.exe (PID: 4884)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 8008)
- WinRAR.exe (PID: 1480)
- FileCoAuth.exe (PID: 7744)
Application launched itself
- WinRAR.exe (PID: 8008)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 8008)
- WinRAR.exe (PID: 1480)
- AddInProcess32.exe (PID: 6796)
- enggww.exe (PID: 7816)
- enggww.exe (PID: 7344)
- AMARRADO.exe (PID: 4884)
- FileCoAuth.exe (PID: 7744)
Connects to unusual port
- AddInProcess32.exe (PID: 6796)
- AMARRADO.exe (PID: 4884)
Contacting a server suspected of hosting an CnC
- AddInProcess32.exe (PID: 6796)
- AMARRADO.exe (PID: 4884)
Starts CMD.EXE for commands execution
- AddInProcess32.exe (PID: 6796)
- cscript.exe (PID: 3400)
- cscript.exe (PID: 7404)
The process executes VB scripts
- cmd.exe (PID: 7520)
- cmd.exe (PID: 7856)
Executing commands from a ".bat" file
- AddInProcess32.exe (PID: 6796)
- cscript.exe (PID: 3400)
- cscript.exe (PID: 7404)
Runs shell command (SCRIPT)
- cscript.exe (PID: 3400)
- cscript.exe (PID: 7404)
Executable content was dropped or overwritten
- csc.exe (PID: 4476)
- enggww.exe (PID: 7816)
- AddInProcess32.exe (PID: 6796)
- enggww.exe (PID: 7344)
- FileCoAuth.exe (PID: 7744)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7760)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 7760)
Changes default file association
- reg.exe (PID: 8116)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7760)
- cmd.exe (PID: 7440)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 7440)
Script adds exclusion process to Windows Defender
- cmd.exe (PID: 7440)
Mutex name with non-standard characters
- enggww.exe (PID: 7816)
Starts itself from another location
- enggww.exe (PID: 7344)
Starts a Microsoft application from unusual location
- FileCoAuth.exe (PID: 1760)
There is functionality for taking screenshot (YARA)
- enggww.exe (PID: 7816)
- AMARRADO.exe (PID: 4884)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 8008)
- WinRAR.exe (PID: 1480)
- FileCoAuth.exe (PID: 7744)
The sample compiled with chinese language support
- WinRAR.exe (PID: 8008)
- WinRAR.exe (PID: 1480)
Checks supported languages
- 003 CITACION NOTIFICACION PERSONAL DEMANDA RESOLUCION.exe (PID: 3740)
- identity_helper.exe (PID: 7420)
- AddInProcess32.exe (PID: 6796)
- csc.exe (PID: 4476)
- cvtres.exe (PID: 8176)
- LowerUAC_2732921611.exe (PID: 3948)
- enggww.exe (PID: 7816)
- enggww.exe (PID: 7344)
- AMARRADO.exe (PID: 4884)
- FileCoAuth.exe (PID: 1760)
Reads the computer name
- 003 CITACION NOTIFICACION PERSONAL DEMANDA RESOLUCION.exe (PID: 3740)
- identity_helper.exe (PID: 7420)
- AddInProcess32.exe (PID: 6796)
- LowerUAC_2732921611.exe (PID: 3948)
- enggww.exe (PID: 7816)
- enggww.exe (PID: 7344)
- AMARRADO.exe (PID: 4884)
- FileCoAuth.exe (PID: 1760)
Application launched itself
- msedge.exe (PID: 3640)
Reads Microsoft Office registry keys
- msedge.exe (PID: 3640)
Reads Environment values
- identity_helper.exe (PID: 7420)
Reads the machine GUID from the registry
- AddInProcess32.exe (PID: 6796)
- csc.exe (PID: 4476)
- AMARRADO.exe (PID: 4884)
- FileCoAuth.exe (PID: 1760)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1480)
Reads the software policy settings
- AddInProcess32.exe (PID: 6796)
- slui.exe (PID: 7280)
Process checks computer location settings
- AddInProcess32.exe (PID: 6796)
- enggww.exe (PID: 7816)
- enggww.exe (PID: 7344)
- FileCoAuth.exe (PID: 7744)
Create files in a temporary directory
- AddInProcess32.exe (PID: 6796)
- csc.exe (PID: 4476)
- cvtres.exe (PID: 8176)
- enggww.exe (PID: 7816)
- FileCoAuth.exe (PID: 1760)
Reads security settings of Internet Explorer
- cscript.exe (PID: 3400)
- ComputerDefaults.exe (PID: 7460)
- cscript.exe (PID: 7404)
Process checks whether UAC notifications are on
- LowerUAC_2732921611.exe (PID: 3948)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7288)
- powershell.exe (PID: 7584)
- powershell.exe (PID: 7296)
- powershell.exe (PID: 1728)
- powershell.exe (PID: 7364)
- powershell.exe (PID: 4664)
- powershell.exe (PID: 7908)
- powershell.exe (PID: 6896)
- powershell.exe (PID: 5080)
- powershell.exe (PID: 1984)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7584)
- powershell.exe (PID: 7288)
- powershell.exe (PID: 7296)
- powershell.exe (PID: 1728)
- powershell.exe (PID: 7364)
- powershell.exe (PID: 7908)
- powershell.exe (PID: 4664)
- powershell.exe (PID: 6896)
- powershell.exe (PID: 5080)
- powershell.exe (PID: 1984)
Checks proxy server information
- slui.exe (PID: 7280)
- AMARRADO.exe (PID: 4884)
Launching a file from a Registry key
- enggww.exe (PID: 7344)
- AMARRADO.exe (PID: 4884)
Creates files in the program directory
- enggww.exe (PID: 7344)
- AMARRADO.exe (PID: 4884)
Creates files or folders in the user directory
- AMARRADO.exe (PID: 4884)
- FileCoAuth.exe (PID: 1760)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(6796) AddInProcess32.exe
C2 (1)luisdiaz.kozow.com
Ports (1)1458
Version| CRACKED BY https://t.me/xworm_v2
Options
AutoRunfalse
MutexAsyncMutex_6SI8OkPnk
InstallFolder%AppData%
Certificates
Cert1MIIE8jCCAtqgAwIBAgIQAOQb7nA/hP/L1XXxqdDJNzANBgkqhkiG9w0BAQ0FADAaMRgwFgYDVQQDDA9Bc3luY1JBVCBTZXJ2ZXIwIBcNMjMwNTI1MDUyMTIyWhgPOTk5OTEyMzEyMzU5NTlaMBoxGDAWBgNVBAMMD0FzeW5jUkFUIFNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAIykAVxs0s6rZ/dwP6ujJtpnj6RSsCsZN6Cfj1InZxSIswX+zNiKJys8xyLlyexoya3ebLp5gOSz...
Server_SignatureAwzIrzsdotDBZgoxP8j8aXzTTR6Co/7koCsccEkHruoqsFVxgBhoyVZvRx/b7fxpvzdRt8vvpY1JF+4HyhiqZhHc2L1m5R3XAr+WA7jP4T+874a8KgTbmhMxECa8e5/kEYlzdAt2Fj+0jkc7sgLWLe2bzTvECKohvMYyak3YOD90H0mCvgYQ+5HKlIdgEHKdfM+NxmAAATqIN0eFKInEbIM/4mp6tSw/Ont6MnSB5aY82KaMxW4iRCX+L0VX4haaCKDo3Bdo9LQ7F0iMcSB6BR1/npD40VpILryLZZvBnHyb...
Keys
AES5d773578ce9575077dd3f61c61ed2ebb470403cfc6c30a2a84ab56d4d411fd82
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
Remcos
(PID) Process(4884) AMARRADO.exe
C2 (1)amarradosnuevo2025.kozow.com:6606
BotnetAMARRADO
Options
Connect_interval1
Install_flagTrue
Install_HKCU\RunTrue
Install_HKLM\RunTrue
Install_HKLM\Explorer\Run1
Install_HKLM\Winlogon\Shell100000
Setup_path%LOCALAPPDATA%
Copy_fileAMARRADO.exe
Startup_valueFalse
Hide_fileFalse
Mutex_nameAMARRADO-8CFO22
Keylog_flag1
Keylog_path%LOCALAPPDATA%
Keylog_filelogs.dat
Keylog_cryptFalse
Hide_keylogFalse
Screenshot_flagFalse
Screenshot_time5
Take_ScreenshotFalse
Screenshot_path%APPDATA%
Screenshot_fileScreenshots
Screenshot_cryptFalse
Mouse_optionFalse
Delete_fileFalse
Audio_record_time5
Audio_path1
Audio_dirMicRecords
Connect_delay0
Copy_dirAMARRADO
Keylog_dirAMARRADO
TRiD
| .svg | | | Scalable Vector Graphics (var.3) (74.3) |
|---|---|---|
| .xml | | | Generic XML (ASCII) (25.6) |
EXIF
SVG
| Xmlns: | http://www.w3.org/2000/svg |
|---|---|
| ImageWidth: | 1080 |
| ZoomAndPan: | magnify |
| ViewBox: | 0 0 810 1012.49997 |
| ImageHeight: | 1350 |
| PreserveAspectRatio: | xMidYMid meet |
| SVGVersion: | 1.2 |
| Data-unique-id: | d7e9c60b-1c0f-4d02-8cbe-1e60b013df44 |
Composite
| ImageSize: | 1080x1350 |
|---|---|
| Megapixels: | 1.5 |
Total processes
228
Monitored processes
78
Malicious processes
15
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 728 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --string-annotations --gpu-preferences=UAAAAAAAAADgAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --always-read-main-dll --field-trial-handle=2456,i,8926588220974337432,7610002329870878255,262144 --variations-seed-version --mojo-platform-channel-handle=2452 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1480 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIb8008.40458\003 CITACION NOTIFICACION PERSONAL DEMANDA RESOLUCION.zip" | C:\Program Files\WinRAR\WinRAR.exe | WinRAR.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 1728 | powershell -Command "Add-MpPreference -ExclusionProcess 'aspnet_compiler.exe'" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1740 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --message-loop-type-ui --string-annotations --always-read-main-dll --field-trial-handle=5008,i,8926588220974337432,7610002329870878255,262144 --variations-seed-version --mojo-platform-channel-handle=7116 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1760 | "C:\Users\admin\AppData\Local\Temp\3582-490\FileCoAuth.exe" -Embedding | C:\Users\admin\AppData\Local\Temp\3582-490\FileCoAuth.exe | — | FileCoAuth.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft OneDriveFile Co-Authoring Executable Exit code: 0 Version: 19.043.0304.0013 Modules
| |||||||||||||||
| 1984 | powershell -Command "Add-MpPreference -ExclusionProcess 'escrito.exe'" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2064 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=6836,i,8926588220974337432,7610002329870878255,262144 --variations-seed-version --mojo-platform-channel-handle=4048 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2076 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --message-loop-type-ui --string-annotations --always-read-main-dll --field-trial-handle=5948,i,8926588220974337432,7610002329870878255,262144 --variations-seed-version --mojo-platform-channel-handle=1652 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2848 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --always-read-main-dll --field-trial-handle=3616,i,8926588220974337432,7610002329870878255,262144 --variations-seed-version --mojo-platform-channel-handle=2776 /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
Total events
79 040
Read events
78 960
Write events
79
Delete events
1
Modification events
| (PID) Process: | (4216) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (4216) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4216) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (4216) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (4216) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (4216) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | DisableFirstRunCustomize |
Value: 1 | |||
| (PID) Process: | (3640) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3640) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3640) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3640) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
Executable files
39
Suspicious files
114
Text files
115
Unknown types
35
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3640 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF176699.TMP | — | |
MD5:— | SHA256:— | |||
| 3640 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3640 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF1766a9.TMP | — | |
MD5:— | SHA256:— | |||
| 3640 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3640 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old~RF1766c8.TMP | — | |
MD5:— | SHA256:— | |||
| 3640 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3640 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF1766e7.TMP | — | |
MD5:— | SHA256:— | |||
| 3640 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3640 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF1766e7.TMP | — | |
MD5:— | SHA256:— | |||
| 3640 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
24
TCP/UDP connections
70
DNS requests
69
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5244 | msedge.exe | GET | 200 | 150.171.27.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:XO6igzEFZSgk7koXbyvhONUCxn8JQwVbMSCMqh6P1WM&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
3100 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7588 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7588 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8180 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1752363601&P2=404&P3=2&P4=fYUMQGT7%2bCDwkJV2RwoZLvcwuPl120eAbvfSqkgkLdO3FO2zOxE4u%2fl65KsQucMSWZ%2bY8VTXgyHHsIC0RiG9JA%3d%3d | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
8180 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1752363601&P2=404&P3=2&P4=fYUMQGT7%2bCDwkJV2RwoZLvcwuPl120eAbvfSqkgkLdO3FO2zOxE4u%2fl65KsQucMSWZ%2bY8VTXgyHHsIC0RiG9JA%3d%3d | unknown | — | — | whitelisted |
8180 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/4c4fdee0-d69c-42b7-bf5c-3ec046e9dfc9?P1=1752363602&P2=404&P3=2&P4=PSXDfL6yzPCTkszjn7Go6SHcQZBMJ8yKK9kzM5T7fx87q54pM2AuPwqQCLu9TH51%2bOua1NZJc124U1cNQpR%2bhQ%3d%3d | unknown | — | — | whitelisted |
4884 | AMARRADO.exe | GET | 200 | 178.237.33.50:80 | http://geoplugin.net/json.gp | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5600 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5244 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5244 | msedge.exe | 150.171.27.11:80 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5244 | msedge.exe | 150.171.27.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5244 | msedge.exe | 2.23.227.199:443 | copilot.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
3640 | msedge.exe | 224.0.0.251:5353 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
copilot.microsoft.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
www.bing.com |
| whitelisted |
edgeassetservice.azureedge.net |
| whitelisted |
www.googleapis.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5244 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (pixeldrain .com) |
5244 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (pixeldrain .com) |
5244 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (pixeldrain .com) |
5244 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (pixeldrain .com) |
2200 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.kozow .com Domain |
6796 | AddInProcess32.exe | Domain Observed Used for C2 Detected | REMOTE [ANY.RUN] AsyncRAT SSL certificate |
6796 | AddInProcess32.exe | Domain Observed Used for C2 Detected | ET MALWARE Generic AsyncRAT/zgRAT Style SSL Cert |
6796 | AddInProcess32.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Malicious SSL Cert (AsyncRAT Server) |
6796 | AddInProcess32.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] AsyncRAT Successful Connection |
2200 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.kozow .com Domain |