| URL: | https://data-cdn.mbamupdates.com/web/mb5-setup-consumer/MBSetup.exe |
| Full analysis: | https://app.any.run/tasks/45b9a29a-24e9-43e6-a5a7-1a3d744897e9 |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | June 19, 2025, 15:01:23 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 574BD4D3F4F6C006851ABC820EC05864 |
| SHA1: | 516FF240BDA07C21B7B9A0906801014B0D3E9E4A |
| SHA256: | 6BF79313B46C0AAD51789B3C0F9122D6D0E4C58116BEE0B4B66ABEC72F2E3CBE |
| SSDEEP: | 3:N8ciFiEnDMGFAAA2lMIZjaA:2cynnQGFlpXZjaA |
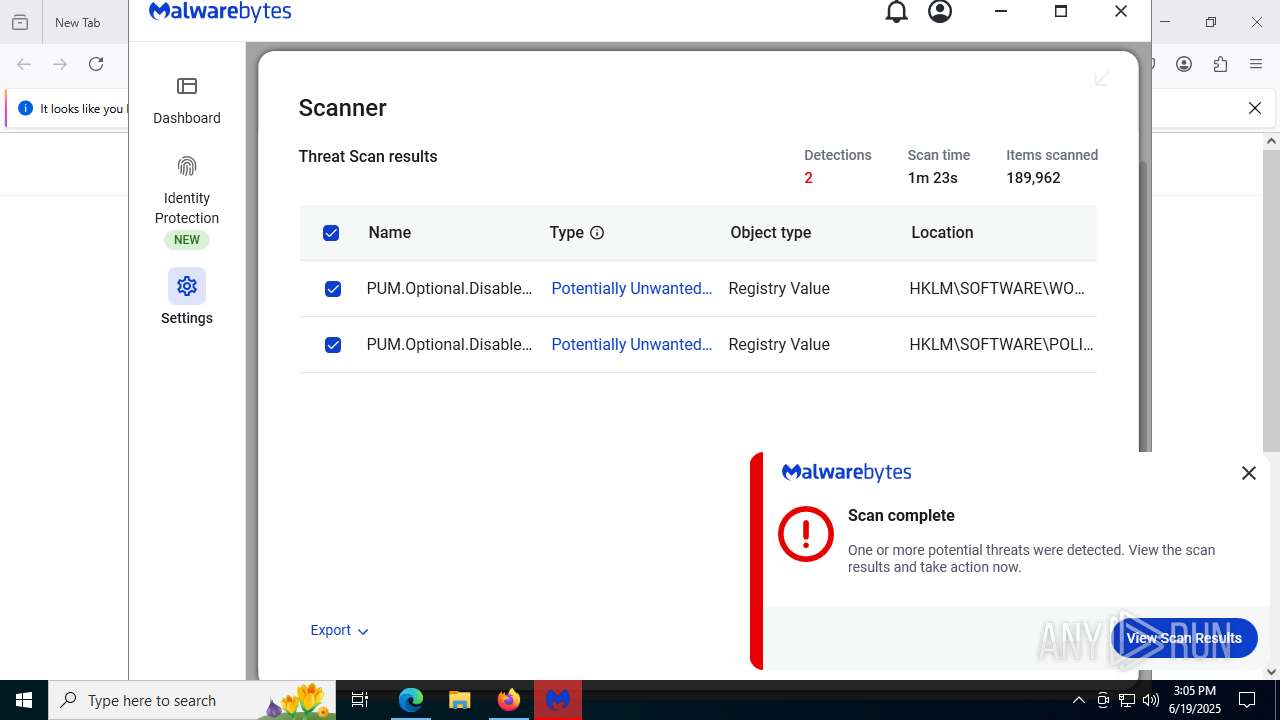
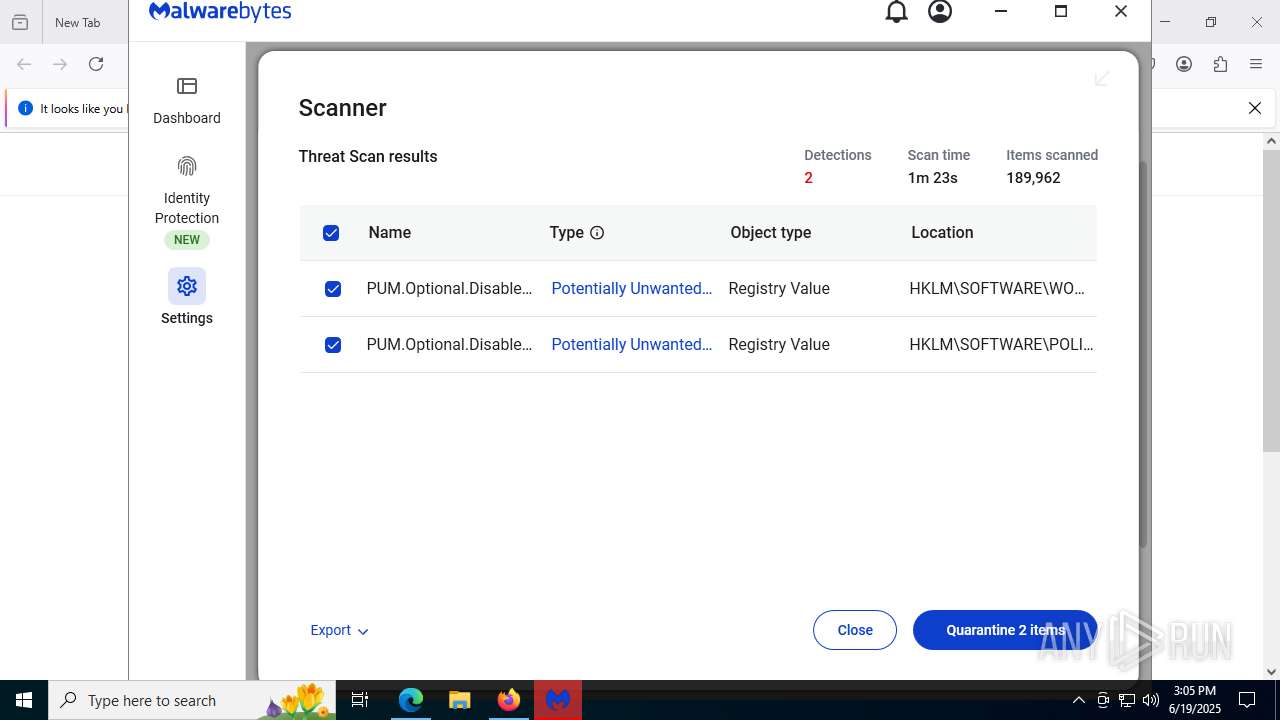
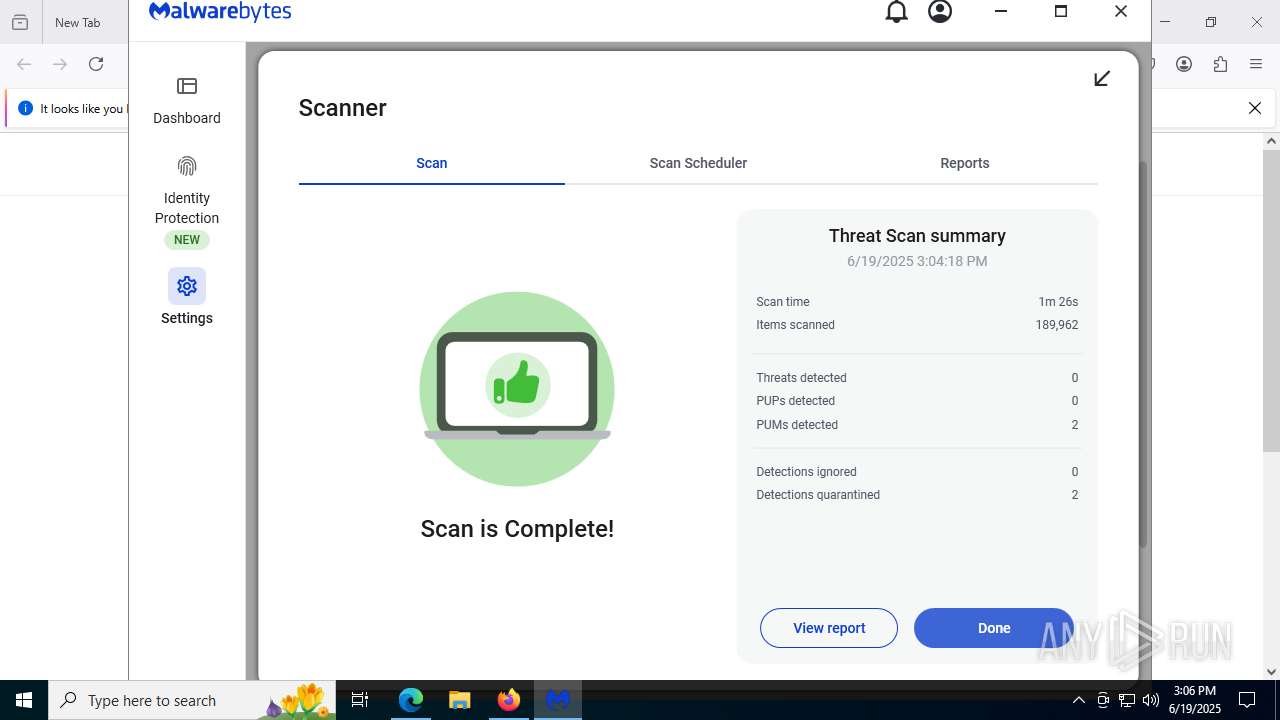
MALICIOUS
Actions looks like stealing of personal data
- MBAMInstallerService.exe (PID: 8012)
- MBAMService.exe (PID: 7480)
Steals credentials from Web Browsers
- MBAMService.exe (PID: 7480)
AGENTTESLA is detected
- MBAMService.exe (PID: 7480)
SUSPICIOUS
Reads the BIOS version
- MBSetup.exe (PID: 7860)
- MBAMService.exe (PID: 7480)
- mbupdatrV5.exe (PID: 9012)
Executable content was dropped or overwritten
- MBSetup.exe (PID: 7860)
- MBAMInstallerService.exe (PID: 8012)
- drvinst.exe (PID: 3576)
- MBVpnTunnelService.exe (PID: 7604)
- MBAMService.exe (PID: 7452)
- MBAMService.exe (PID: 7480)
The process verifies whether the antivirus software is installed
- MBSetup.exe (PID: 7860)
- MBAMInstallerService.exe (PID: 8012)
- drvinst.exe (PID: 3576)
- MBVpnTunnelService.exe (PID: 7604)
- MBAMService.exe (PID: 7452)
- MBAMService.exe (PID: 7480)
- MBAMWsc.exe (PID: 5904)
- Malwarebytes.exe (PID: 6536)
- firefox.exe (PID: 8072)
- firefox.exe (PID: 1720)
- MbamBgNativeMsg.exe (PID: 8644)
- Malwarebytes.exe (PID: 8812)
- firefox.exe (PID: 1080)
- Malwarebytes.exe (PID: 8744)
- MBAMWsc.exe (PID: 8940)
Executes as Windows Service
- MBAMInstallerService.exe (PID: 8012)
- MBAMService.exe (PID: 7480)
Searches for installed software
- MBSetup.exe (PID: 7860)
- MBSetup.exe (PID: 8124)
- MBSetup.exe (PID: 7336)
- MBAMInstallerService.exe (PID: 8012)
- MBAMService.exe (PID: 7480)
- Malwarebytes.exe (PID: 6536)
Creates files in the driver directory
- MBSetup.exe (PID: 7860)
- MBAMInstallerService.exe (PID: 8012)
- drvinst.exe (PID: 3576)
- MBVpnTunnelService.exe (PID: 7604)
- MBAMService.exe (PID: 7452)
- MBAMService.exe (PID: 7480)
Drops 7-zip archiver for unpacking
- MBAMInstallerService.exe (PID: 8012)
Drops a system driver (possible attempt to evade defenses)
- MBAMInstallerService.exe (PID: 8012)
- MBVpnTunnelService.exe (PID: 7604)
- drvinst.exe (PID: 3576)
- MBAMService.exe (PID: 7452)
- MBAMService.exe (PID: 7480)
The process drops C-runtime libraries
- MBAMInstallerService.exe (PID: 8012)
- MBAMService.exe (PID: 7480)
The process creates files with name similar to system file names
- MBAMInstallerService.exe (PID: 8012)
Adds/modifies Windows certificates
- MBAMInstallerService.exe (PID: 8012)
- MBAMService.exe (PID: 7480)
Process drops legitimate windows executable
- MBAMInstallerService.exe (PID: 8012)
- MBAMService.exe (PID: 7480)
Changes Internet Explorer settings (feature browser emulation)
- MBAMInstallerService.exe (PID: 8012)
Creates or modifies Windows services
- MBAMService.exe (PID: 7452)
- MBAMService.exe (PID: 7480)
The process checks if it is being run in the virtual environment
- MBAMService.exe (PID: 7480)
- MBAMService.exe (PID: 7452)
Creates/Modifies COM task schedule object
- MBAMService.exe (PID: 7480)
Reads security settings of Internet Explorer
- MBAMService.exe (PID: 7480)
- Malwarebytes.exe (PID: 6536)
Creates a software uninstall entry
- MBAMInstallerService.exe (PID: 8012)
The process drops Mozilla's DLL files
- MBAMService.exe (PID: 7480)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2696)
Starts CMD.EXE for commands execution
- MBSetup.exe (PID: 7860)
There is functionality for taking screenshot (YARA)
- Malwarebytes.exe (PID: 6536)
Application launched itself
- Malwarebytes.exe (PID: 8744)
Read startup parameters
- MBAMService.exe (PID: 7480)
Starts application from unusual location
- MBAMService.exe (PID: 7480)
INFO
Executable content was dropped or overwritten
- msedge.exe (PID: 3864)
- msedge.exe (PID: 1508)
Reads the computer name
- identity_helper.exe (PID: 7528)
- MBSetup.exe (PID: 7860)
- MBAMInstallerService.exe (PID: 8012)
- MBVpnTunnelService.exe (PID: 7604)
- drvinst.exe (PID: 3576)
- MBAMService.exe (PID: 7452)
- MBAMService.exe (PID: 7480)
- ig.exe (PID: 6612)
- MBAMWsc.exe (PID: 5904)
- Malwarebytes.exe (PID: 6536)
- Malwarebytes.exe (PID: 8812)
- MbamBgNativeMsg.exe (PID: 8644)
- ig.exe (PID: 8324)
- MBAMWsc.exe (PID: 8940)
- mbupdatrV5.exe (PID: 9012)
The sample compiled with english language support
- msedge.exe (PID: 1508)
- msedge.exe (PID: 3864)
- MBSetup.exe (PID: 7860)
- MBAMInstallerService.exe (PID: 8012)
- MBVpnTunnelService.exe (PID: 7604)
- drvinst.exe (PID: 3576)
- MBAMService.exe (PID: 7452)
- MBAMService.exe (PID: 7480)
Application launched itself
- msedge.exe (PID: 3864)
- firefox.exe (PID: 7524)
- firefox.exe (PID: 8072)
Reads Environment values
- identity_helper.exe (PID: 7528)
- MBAMService.exe (PID: 7480)
Checks supported languages
- identity_helper.exe (PID: 7528)
- MBSetup.exe (PID: 7860)
- MBSetup.exe (PID: 8124)
- MBSetup.exe (PID: 7336)
- MBAMInstallerService.exe (PID: 8012)
- drvinst.exe (PID: 3576)
- MBAMService.exe (PID: 7452)
- MBVpnTunnelService.exe (PID: 7604)
- MBAMService.exe (PID: 7480)
- ig.exe (PID: 6612)
- MBAMWsc.exe (PID: 5904)
- MbamBgNativeMsg.exe (PID: 8644)
- Malwarebytes.exe (PID: 6536)
- mbupdatrV5.exe (PID: 9012)
Launching a file from the Downloads directory
- msedge.exe (PID: 3864)
Create files in a temporary directory
- MBSetup.exe (PID: 7860)
Reads the machine GUID from the registry
- MBSetup.exe (PID: 7860)
- drvinst.exe (PID: 3576)
- MBAMInstallerService.exe (PID: 8012)
- MBAMService.exe (PID: 7480)
- MbamBgNativeMsg.exe (PID: 8644)
- mbupdatrV5.exe (PID: 9012)
Manual execution by a user
- MBSetup.exe (PID: 7520)
- MBSetup.exe (PID: 7336)
- firefox.exe (PID: 7524)
- Malwarebytes.exe (PID: 8744)
Creates files in the program directory
- MBSetup.exe (PID: 7860)
- MBAMInstallerService.exe (PID: 8012)
- MBVpnTunnelService.exe (PID: 7604)
- MBAMService.exe (PID: 7480)
- Malwarebytes.exe (PID: 6536)
Reads the software policy settings
- MBSetup.exe (PID: 7860)
- slui.exe (PID: 1712)
- MBAMInstallerService.exe (PID: 8012)
- drvinst.exe (PID: 3576)
- MBAMService.exe (PID: 7480)
- Malwarebytes.exe (PID: 6536)
Checks proxy server information
- MBSetup.exe (PID: 7860)
- slui.exe (PID: 1712)
- Malwarebytes.exe (PID: 6536)
The sample compiled with spanish language support
- MBAMInstallerService.exe (PID: 8012)
Reads the time zone
- MBAMService.exe (PID: 7480)
Reads CPU info
- MBAMService.exe (PID: 7480)
CONNECTWISE has been detected
- MBAMService.exe (PID: 7480)
Creates files or folders in the user directory
- Malwarebytes.exe (PID: 6536)
Reads Microsoft Office registry keys
- firefox.exe (PID: 8072)
Process checks computer location settings
- Malwarebytes.exe (PID: 6536)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
242
Monitored processes
90
Malicious processes
15
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 316 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=6612,i,4515239330002767640,2769176721442263223,262144 --variations-seed-version --mojo-platform-channel-handle=4024 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 544 | ig.exe reseed | C:\Program Files\Malwarebytes\Anti-Malware\ig.exe | — | MBAMService.exe | |||||||||||
User: admin Company: MalwareBytes Integrity Level: LOW Description: Malware Scanner Exit code: 16646144 Version: 1.0.4.8 Modules
| |||||||||||||||
| 756 | ig.exe reseed | C:\Program Files\Malwarebytes\Anti-Malware\ig.exe | — | MBAMService.exe | |||||||||||
User: admin Company: MalwareBytes Integrity Level: LOW Description: Malware Scanner Exit code: 6946816 Version: 1.0.4.8 Modules
| |||||||||||||||
| 768 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=133.0.6943.142 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 --annotation=prod=Edge --annotation=ver=133.0.3065.92 --initial-client-data=0x304,0x308,0x30c,0x2fc,0x314,0x7ffc43cbf208,0x7ffc43cbf214,0x7ffc43cbf220 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1080 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 5612 -prefsLen 39580 -prefMapHandle 4840 -prefMapSize 272997 -jsInitHandle 5884 -jsInitLen 247456 -parentBuildID 20250227124745 -ipcHandle 4884 -initialChannelId {fa15ff81-9f12-4621-bb78-fcca037ad142} -parentPid 8072 -crashReporter "\\.\pipe\gecko-crash-server-pipe.8072" -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - 11 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 136.0 Modules
| |||||||||||||||
| 1100 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=5760,i,4515239330002767640,2769176721442263223,262144 --variations-seed-version --mojo-platform-channel-handle=5728 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1100 | ig.exe reseed | C:\Program Files\Malwarebytes\Anti-Malware\ig.exe | — | MBAMService.exe | |||||||||||
User: admin Company: MalwareBytes Integrity Level: LOW Description: Malware Scanner Exit code: 7536640 Version: 1.0.4.8 Modules
| |||||||||||||||
| 1268 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 5412 -prefsLen 39621 -prefMapHandle 5304 -prefMapSize 272997 -jsInitHandle 4084 -jsInitLen 247456 -parentBuildID 20250227124745 -ipcHandle 5340 -initialChannelId {5f357f23-ba1b-41e8-945d-fdb97c62a8b5} -parentPid 8072 -crashReporter "\\.\pipe\gecko-crash-server-pipe.8072" -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - 13 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 136.0 Modules
| |||||||||||||||
| 1296 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --string-annotations --gpu-preferences=UAAAAAAAAADoAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAABCAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --always-read-main-dll --field-trial-handle=1712,i,4515239330002767640,2769176721442263223,262144 --variations-seed-version --mojo-platform-channel-handle=2944 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1508 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=2220,i,4515239330002767640,2769176721442263223,262144 --variations-seed-version --mojo-platform-channel-handle=2536 /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
Total events
345 886
Read events
344 872
Write events
985
Delete events
29
Modification events
| (PID) Process: | (3864) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3864) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3864) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3864) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3864) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3864) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (3864) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 4B58D74D84962F00 | |||
| (PID) Process: | (3864) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | MicrosoftEdgeAutoLaunch_29EBC4579851B72EE312C449CF839B1A |
Value: "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --no-startup-window --win-session-start | |||
| (PID) Process: | (3864) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\Clients\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\Commands\on-logon-autolaunch |
| Operation: | write | Name: | Enabled |
Value: 0 | |||
| (PID) Process: | (3864) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\525152 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {702912FC-10E8-4349-A524-6E18D5B3F4F7} | |||
Executable files
1 319
Suspicious files
533
Text files
205
Unknown types
300
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3864 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old~RF176513.TMP | — | |
MD5:— | SHA256:— | |||
| 3864 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3864 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF176522.TMP | — | |
MD5:— | SHA256:— | |||
| 3864 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF176522.TMP | — | |
MD5:— | SHA256:— | |||
| 3864 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3864 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3864 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF176551.TMP | — | |
MD5:— | SHA256:— | |||
| 3864 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3864 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF176551.TMP | — | |
MD5:— | SHA256:— | |||
| 3864 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
87
TCP/UDP connections
169
DNS requests
273
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1508 | msedge.exe | GET | 200 | 150.171.28.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:7Wn5dj4-UNJNIgz7hDaAWYYE_WWqqSTErwwkkdeau7E&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
2764 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3924 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3924 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7752 | svchost.exe | HEAD | 200 | 23.50.131.72:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1750781230&P2=404&P3=2&P4=PI2JSc82S6d3DsHANe2Uvp44nLd5TyuASNtFGoc4lwXqKYQC4d8LRmrTEfnfXFDT9eeaOs1O5giSAJqOqNOJYg%3d%3d | unknown | — | — | whitelisted |
7752 | svchost.exe | GET | 206 | 23.50.131.72:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1750781230&P2=404&P3=2&P4=PI2JSc82S6d3DsHANe2Uvp44nLd5TyuASNtFGoc4lwXqKYQC4d8LRmrTEfnfXFDT9eeaOs1O5giSAJqOqNOJYg%3d%3d | unknown | — | — | whitelisted |
7752 | svchost.exe | GET | 206 | 23.50.131.72:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1750781230&P2=404&P3=2&P4=PI2JSc82S6d3DsHANe2Uvp44nLd5TyuASNtFGoc4lwXqKYQC4d8LRmrTEfnfXFDT9eeaOs1O5giSAJqOqNOJYg%3d%3d | unknown | — | — | whitelisted |
7752 | svchost.exe | HEAD | 200 | 23.50.131.72:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/4c4fdee0-d69c-42b7-bf5c-3ec046e9dfc9?P1=1750781231&P2=404&P3=2&P4=RpQn7QUFnZnrVa4hqQ42UjJwmigphtFbFKJAw6p82fyQkshbfe73rLdDirVq1KX5KBWfaLQwYoHceG2Cpg1pLA%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4960 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1508 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1508 | msedge.exe | 150.171.28.11:80 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1508 | msedge.exe | 150.171.28.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1508 | msedge.exe | 65.9.66.107:443 | data-cdn.mbamupdates.com | AMAZON-02 | US | unknown |
1508 | msedge.exe | 2.16.241.220:443 | copilot.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
data-cdn.mbamupdates.com |
| whitelisted |
copilot.microsoft.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
www.bing.com |
| whitelisted |
edgeassetservice.azureedge.net |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Malwarebytes.exe | Profiler was prevented from loading notification profiler due to app settings.
Process ID (decimal): 6536. Message ID: [0x2509].
|
MBAMService.exe | Retry XPE file open
|
MBAMService.exe | Retry XPE file open
|
MBAMService.exe | Retry XPE file open
|
Malwarebytes.exe | Profiler was prevented from loading notification profiler due to app settings.
Process ID (decimal): 8744. Message ID: [0x2509].
|
Malwarebytes.exe | Profiler was prevented from loading notification profiler due to app settings.
Process ID (decimal): 8812. Message ID: [0x2509].
|
MBAMService.exe | Retry XPE file open
|