| File name: | New_SoftwareFile_Full.zip |
| Full analysis: | https://app.any.run/tasks/d82a7993-defa-4ea8-aa80-723da41e8617 |
| Verdict: | Malicious activity |
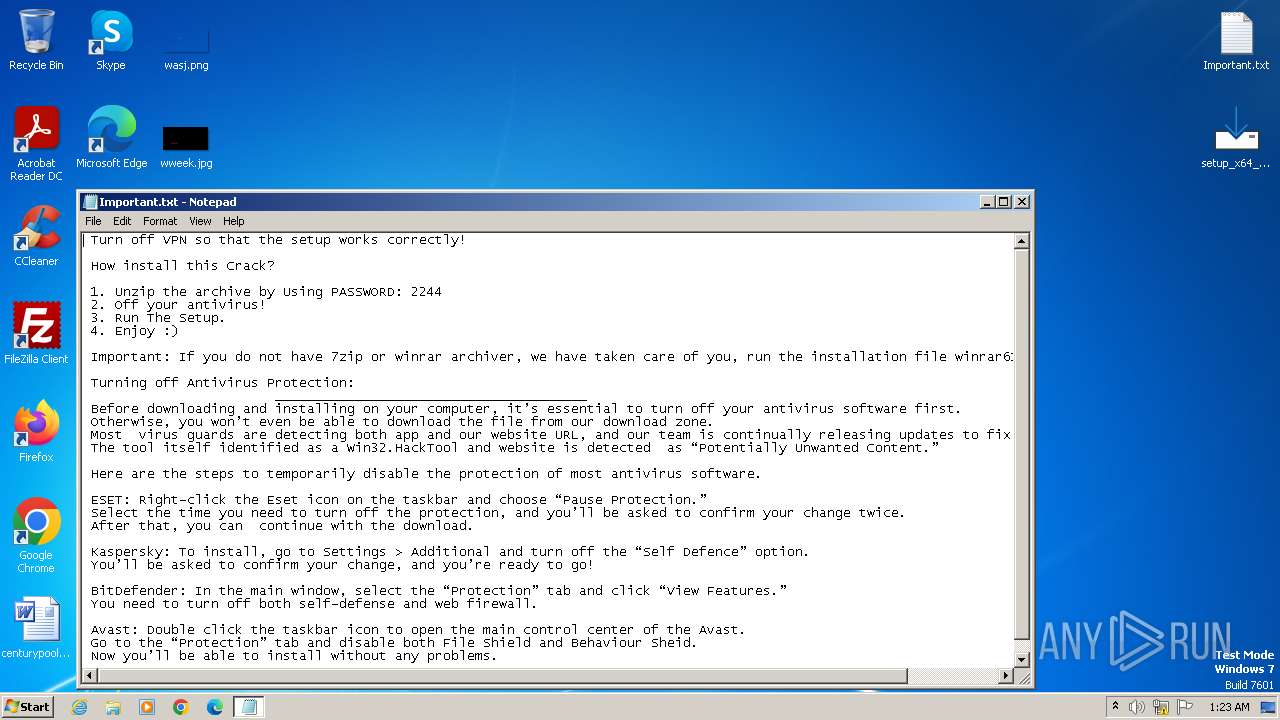
| Threats: | CryptBot is an advanced Windows-targeting infostealer delivered via pirate sites with "cracked" software. It has been first observed in the wild in 2019. |
| Analysis date: | December 07, 2023, 01:22:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | F92F35F252D872D40AB43542AF7582FD |
| SHA1: | 9198FD203A8083BFDFB1124F800CD546355D02BE |
| SHA256: | 6BA0CDB15EDF36C2E60E327609B8D032CEA37D7EC8F45539620F78A6C20AAAE1 |
| SSDEEP: | 98304:76p6xS+LnSlKLp/Nval4CDOv3r74A1c8Tl6/i5bedeVCmwr5gojbR0kmwZQzayT1:oQSvEkSQIgYSyce7wm/WiG0BH |
MALICIOUS
CRYPTBOT has been detected (SURICATA)
- setup_x64_86.exe (PID: 2548)
Connects to the CnC server
- setup_x64_86.exe (PID: 2548)
Drops the executable file immediately after the start
- setup_x64_86.exe (PID: 2548)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 2968)
Actions looks like stealing of personal data
- setup_x64_86.exe (PID: 2548)
SUSPICIOUS
Searches for installed software
- setup_x64_86.exe (PID: 2548)
Reads the Internet Settings
- setup_x64_86.exe (PID: 2548)
Drops the AutoIt3 executable file
- setup_x64_86.exe (PID: 2548)
Starts CMD.EXE for commands execution
- setup_x64_86.exe (PID: 2548)
The process executes via Task Scheduler
- Degomubas.exe (PID: 4004)
INFO
Checks supported languages
- setup_x64_86.exe (PID: 2548)
- wmpnscfg.exe (PID: 3492)
- Degomubas.exe (PID: 4004)
Reads the computer name
- setup_x64_86.exe (PID: 2548)
- wmpnscfg.exe (PID: 3492)
Manual execution by a user
- notepad.exe (PID: 2976)
- setup_x64_86.exe (PID: 2548)
- wmpnscfg.exe (PID: 3492)
Reads CPU info
- setup_x64_86.exe (PID: 2548)
Checks proxy server information
- setup_x64_86.exe (PID: 2548)
Reads the machine GUID from the registry
- setup_x64_86.exe (PID: 2548)
Creates files or folders in the user directory
- setup_x64_86.exe (PID: 2548)
Reads mouse settings
- Degomubas.exe (PID: 4004)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:12:06 12:04:14 |
| ZipCRC: | 0x2a5ebd6c |
| ZipCompressedSize: | 886 |
| ZipUncompressedSize: | 1752 |
| ZipFileName: | Important.txt |
Total processes
49
Monitored processes
7
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1864 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\New_SoftwareFile_Full.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2548 | "C:\Users\admin\Desktop\setup_x64_86.exe" | C:\Users\admin\Desktop\setup_x64_86.exe | explorer.exe | ||||||||||||
User: admin Company: Foyizo Integrity Level: HIGH Description: Foyizo Setup Exit code: 0 Version: 3.4.3.0 Modules
| |||||||||||||||
| 2968 | "C:\Windows\system32\cmd.exe" /c schtasks /create /tn \Service\Data /tr """"C:\Users\admin\AppData\Roaming\ServiceData\Degomubas.exe""" """C:\Users\admin\AppData\Roaming\ServiceData\Degomubas.jpg"""" /st 00:01 /du 9800:39 /sc once /ri 1 /f | C:\Windows\System32\cmd.exe | — | setup_x64_86.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2976 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Important.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3492 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 4004 | C:\Users\admin\AppData\Roaming\ServiceData\Degomubas.exe "C:\Users\admin\AppData\Roaming\ServiceData\Degomubas.jpg" | C:\Users\admin\AppData\Roaming\ServiceData\Degomubas.exe | — | taskeng.exe | |||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script Exit code: 0 Version: 3, 3, 16, 1 Modules
| |||||||||||||||
| 4040 | schtasks /create /tn \Service\Data /tr """"C:\Users\admin\AppData\Roaming\ServiceData\Degomubas.exe""" """C:\Users\admin\AppData\Roaming\ServiceData\Degomubas.jpg"""" /st 00:01 /du 9800:39 /sc once /ri 1 /f | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 569
Read events
1 537
Write events
32
Delete events
0
Modification events
| (PID) Process: | (1864) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (1864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (1864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
1
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1864.18466\setup_x64_86.exe | — | |
MD5:— | SHA256:— | |||
| 2548 | setup_x64_86.exe | C:\Users\admin\AppData\Roaming\ServiceData\Degomubas.jpg | text | |
MD5:6EEADC283D518568B97DBCF9005ACC14 | SHA256:64DC4868D1B7AC07390C3AD35D720C379C3ACBE3E9586064F4479F22697AD92A | |||
| 1864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1864.18466\Important.txt | text | |
MD5:103C526250943E076DBCB04D90D1DD04 | SHA256:F265558AB44976E3864888787111003950AE0381F851103719CE1D4D616310A2 | |||
| 2548 | setup_x64_86.exe | C:\Users\admin\AppData\Roaming\ServiceData\Degomubas.exe | executable | |
MD5:0ADB9B817F1DF7807576C2D7068DD931 | SHA256:98E4F904F7DE1644E519D09371B8AFCBBF40FF3BD56D76CE4DF48479A4AB884B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
5
DNS requests
1
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2548 | setup_x64_86.exe | POST | 200 | 130.193.43.88:80 | http://qaone1ht.top/zip.php | unknown | text | 2 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2548 | setup_x64_86.exe | 130.193.43.88:80 | qaone1ht.top | Yandex.Cloud LLC | RU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
qaone1ht.top |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2548 | setup_x64_86.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
2548 | setup_x64_86.exe | A Network Trojan was detected | ET MALWARE Win32/Cryptbot CnC Activity (POST) |
2548 | setup_x64_86.exe | A Network Trojan was detected | ET HUNTING Observed Malicious Filename in Outbound POST Request (Information.txt) |
2 ETPRO signatures available at the full report