| File name: | AND64.exe |
| Full analysis: | https://app.any.run/tasks/ae11c8b8-cfb7-4e22-928b-2c5053b47ab7 |
| Verdict: | Malicious activity |
| Threats: | Amadey is a formidable Windows infostealer threat, characterized by its persistence mechanisms, modular design, and ability to execute various malicious tasks. |
| Analysis date: | January 06, 2024, 03:03:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 9A0B7EE713610B8395C8F0580A3B1E3D |
| SHA1: | E44A9E7EC6FE06AE6BA1B9518DB78E95AD451942 |
| SHA256: | 6B8E428CFF996C49AA52E017213C7016880A2BC1583D051240C74992BF83C357 |
| SSDEEP: | 6144:JO+8qkRrtd3yX13t39boWEtaXNUYViUMzkfjDyV4i78+4Bkq:+qkRrtVyX13DoJYViUMzknWI+O |
MALICIOUS
Changes the autorun value in the registry
- explorhe.exe (PID: 2072)
Uses Task Scheduler to run other applications
- explorhe.exe (PID: 2072)
- cmd.exe (PID: 2304)
Risepro uses scheduled tasks to run itself
- cmd.exe (PID: 2304)
- cmd.exe (PID: 2248)
Uses Task Scheduler to autorun other applications
- cmd.exe (PID: 2248)
Steals credentials from Web Browsers
- RegAsm.exe (PID: 984)
LUMMA has been detected (YARA)
- ev.exe (PID: 1592)
Actions looks like stealing of personal data
- RegAsm.exe (PID: 984)
SUSPICIOUS
Reads the Internet Settings
- explorhe.exe (PID: 2072)
- ev.exe (PID: 1592)
- AND64.exe (PID: 1356)
- ev.exe (PID: 2424)
- rise.exe (PID: 848)
Checks Windows Trust Settings
- explorhe.exe (PID: 2072)
Reads settings of System Certificates
- explorhe.exe (PID: 2072)
- ev.exe (PID: 1592)
- ev.exe (PID: 2424)
- rise.exe (PID: 848)
Reads security settings of Internet Explorer
- explorhe.exe (PID: 2072)
Adds/modifies Windows certificates
- ev.exe (PID: 1592)
- ev.exe (PID: 2424)
Starts CMD.EXE for commands execution
- rise.exe (PID: 848)
Searches for installed software
- RegAsm.exe (PID: 984)
Reads browser cookies
- RegAsm.exe (PID: 984)
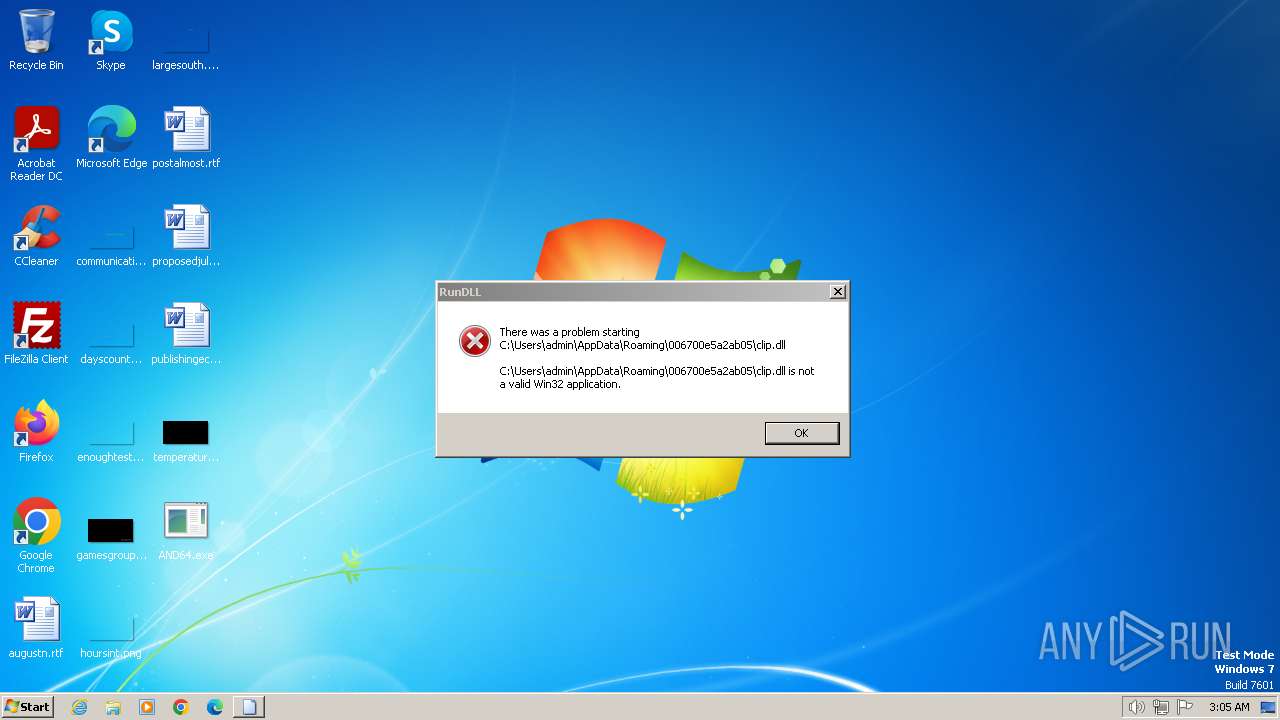
Uses RUNDLL32.EXE to load library
- explorhe.exe (PID: 2072)
INFO
Drops the executable file immediately after the start
- AND64.exe (PID: 1356)
- explorhe.exe (PID: 2072)
- rise.exe (PID: 848)
- bakhtiar.exe (PID: 664)
Create files in a temporary directory
- AND64.exe (PID: 1356)
- explorhe.exe (PID: 2072)
- rise.exe (PID: 848)
- ev.exe (PID: 1592)
- bakhtiar.exe (PID: 664)
Checks supported languages
- AND64.exe (PID: 1356)
- explorhe.exe (PID: 2072)
- ev.exe (PID: 1592)
- rise.exe (PID: 848)
- ev.exe (PID: 2424)
- bakhtiar.exe (PID: 664)
- golden.exe (PID: 552)
- RegAsm.exe (PID: 984)
- InstallUtil.exe (PID: 2488)
- AddInProcess32.exe (PID: 2888)
- explorhe.exe (PID: 3068)
- explorhe.exe (PID: 3028)
- explorhe.exe (PID: 3220)
- explorhe.exe (PID: 3016)
- explorhe.exe (PID: 908)
- AddInProcess32.exe (PID: 2960)
Starts itself from another location
- AND64.exe (PID: 1356)
Reads the machine GUID from the registry
- AND64.exe (PID: 1356)
- explorhe.exe (PID: 2072)
- ev.exe (PID: 1592)
- rise.exe (PID: 848)
- ev.exe (PID: 2424)
- RegAsm.exe (PID: 984)
- bakhtiar.exe (PID: 664)
Reads the computer name
- AND64.exe (PID: 1356)
- ev.exe (PID: 1592)
- explorhe.exe (PID: 2072)
- rise.exe (PID: 848)
- ev.exe (PID: 2424)
- bakhtiar.exe (PID: 664)
- golden.exe (PID: 552)
- RegAsm.exe (PID: 984)
Checks proxy server information
- explorhe.exe (PID: 2072)
Creates files or folders in the user directory
- explorhe.exe (PID: 2072)
- rise.exe (PID: 848)
Creates files in the program directory
- rise.exe (PID: 848)
- bakhtiar.exe (PID: 664)
Reads Environment values
- ev.exe (PID: 1592)
- rise.exe (PID: 848)
- ev.exe (PID: 2424)
- RegAsm.exe (PID: 984)
RISEPRO has been detected (SURICATA)
- rise.exe (PID: 848)
AMADEY has been detected (SURICATA)
- explorhe.exe (PID: 2072)
KELIHOS has been detected (SURICATA)
- explorhe.exe (PID: 2072)
Checks for external IP
- rise.exe (PID: 848)
Connects to unusual port
- rise.exe (PID: 848)
- RegAsm.exe (PID: 984)
Process requests binary or script from the Internet
- explorhe.exe (PID: 2072)
Connects to the server without a host name
- explorhe.exe (PID: 2072)
Connects to the CnC server
- rise.exe (PID: 848)
- RegAsm.exe (PID: 984)
REDLINE has been detected (SURICATA)
- RegAsm.exe (PID: 984)
Reads product name
- RegAsm.exe (PID: 984)
The process executes via Task Scheduler
- explorhe.exe (PID: 908)
- explorhe.exe (PID: 3028)
- explorhe.exe (PID: 3220)
- explorhe.exe (PID: 3068)
- explorhe.exe (PID: 3016)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Lumma
(PID) Process(1592) ev.exe
C2 (7)netovrema.pw
opposesicknessopw.pw
carstirgapcheatdeposwte.pw
playerweighmailydailew.pw
politefrightenpowoa.pw
recessionconceptjetwe.pw
blastechohackopeower.pw
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:01:04 17:01:48+01:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.24 |
| CodeSize: | 330240 |
| InitializedDataSize: | 110592 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1f6a9 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
59
Monitored processes
22
Malicious processes
9
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 552 | "C:\Users\admin\AppData\Local\Temp\1000046001\golden.exe" | C:\Users\admin\AppData\Local\Temp\1000046001\golden.exe | — | explorhe.exe | |||||||||||
User: admin Company: Double CC Integrity Level: MEDIUM Description: Regular Compares Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 664 | "C:\Users\admin\AppData\Local\Temp\1000045001\bakhtiar.exe" | C:\Users\admin\AppData\Local\Temp\1000045001\bakhtiar.exe | — | explorhe.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: a_collection_of_necessary_programs_for_use Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 848 | "C:\Users\admin\AppData\Local\Temp\1000040001\rise.exe" | C:\Users\admin\AppData\Local\Temp\1000040001\rise.exe | explorhe.exe | ||||||||||||
User: admin Company: Polymod Inc. Integrity Level: MEDIUM Description: PolymodXT v1.3 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 908 | C:\Users\admin\AppData\Local\Temp\d887ceb89d\explorhe.exe | C:\Users\admin\AppData\Local\Temp\d887ceb89d\explorhe.exe | — | taskeng.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 984 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | golden.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 1356 | "C:\Users\admin\Desktop\AND64.exe" | C:\Users\admin\Desktop\AND64.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1560 | schtasks /create /f /RU "admin" /tr "C:\ProgramData\OfficeTrackerNMP131\OfficeTrackerNMP131.exe" /tn "OfficeTrackerNMP131 LG" /sc ONLOGON /rl HIGHEST | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1592 | "C:\Users\admin\AppData\Local\Temp\1000032001\ev.exe" | C:\Users\admin\AppData\Local\Temp\1000032001\ev.exe | explorhe.exe | ||||||||||||
User: admin Company: ArtVibes Innovations Integrity Level: MEDIUM Description: InkCraft Master Exit code: 0 Version: 1.0.3 Modules
Lumma(PID) Process(1592) ev.exe C2 (7)netovrema.pw opposesicknessopw.pw carstirgapcheatdeposwte.pw playerweighmailydailew.pw politefrightenpowoa.pw recessionconceptjetwe.pw blastechohackopeower.pw | |||||||||||||||
| 2072 | "C:\Users\admin\AppData\Local\Temp\d887ceb89d\explorhe.exe" | C:\Users\admin\AppData\Local\Temp\d887ceb89d\explorhe.exe | AND64.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2248 | "cmd.exe" /c schtasks /create /f /RU "admin" /tr "C:\ProgramData\OfficeTrackerNMP131\OfficeTrackerNMP131.exe" /tn "OfficeTrackerNMP131 LG" /sc ONLOGON /rl HIGHEST | C:\Windows\System32\cmd.exe | rise.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
17 739
Read events
17 614
Write events
102
Delete events
23
Modification events
| (PID) Process: | (1356) AND64.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1356) AND64.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1356) AND64.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1356) AND64.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2072) explorhe.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders |
| Operation: | write | Name: | Startup |
Value: %USERPROFILE%\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup | |||
| (PID) Process: | (2072) explorhe.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2072) explorhe.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2072) explorhe.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2072) explorhe.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2072) explorhe.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
Executable files
19
Suspicious files
9
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2072 | explorhe.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:3D2A2AAB8F3DA96E7BF80B00AB156721 | SHA256:54026822CBAD99B5B974B3E04367614226731DC899522945FF75F12909810F90 | |||
| 1356 | AND64.exe | C:\Users\admin\AppData\Local\Temp\d887ceb89d\explorhe.exe | executable | |
MD5:9A0B7EE713610B8395C8F0580A3B1E3D | SHA256:6B8E428CFF996C49AA52E017213C7016880A2BC1583D051240C74992BF83C357 | |||
| 2072 | explorhe.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\rise[1].exe | executable | |
MD5:E33B43AC05FDDF2791D1312F67E921A5 | SHA256:B6BC62948875B3B8F74A1726BCBCE53E74F1C918B0676D20E6BBF76F9F069AE2 | |||
| 848 | rise.exe | C:\Users\admin\AppData\Local\Temp\FANBooster131\FANBooster131.exe | executable | |
MD5:E33B43AC05FDDF2791D1312F67E921A5 | SHA256:B6BC62948875B3B8F74A1726BCBCE53E74F1C918B0676D20E6BBF76F9F069AE2 | |||
| 2072 | explorhe.exe | C:\Users\admin\AppData\Local\Temp\1000040001\rise.exe | executable | |
MD5:E33B43AC05FDDF2791D1312F67E921A5 | SHA256:B6BC62948875B3B8F74A1726BCBCE53E74F1C918B0676D20E6BBF76F9F069AE2 | |||
| 848 | rise.exe | C:\Users\admin\AppData\Local\MaxLoonaFest131\MaxLoonaFest131.exe | executable | |
MD5:E33B43AC05FDDF2791D1312F67E921A5 | SHA256:B6BC62948875B3B8F74A1726BCBCE53E74F1C918B0676D20E6BBF76F9F069AE2 | |||
| 848 | rise.exe | C:\Users\admin\AppData\Local\Temp\d887ceb89d\FANBooster131.lnk | binary | |
MD5:EE254AFF1DD270D13497CD23D9FF2143 | SHA256:BF3F5768E1D6443F818355DB0E553A023EFC9724627FFC982C5E60AA020666DC | |||
| 2072 | explorhe.exe | C:\Users\admin\AppData\Local\Temp\1000043001\ev.exe | executable | |
MD5:5D7EA462FC3F943663C9A2C4B3AF3EDC | SHA256:BD7A5EC85EB43127E57033AD64FC8527481F4139A343F86C48BB3EA2C4537052 | |||
| 848 | rise.exe | C:\Users\admin\AppData\Local\Temp\rise131M9Asphalt.tmp | text | |
MD5:9821B784A2EF1D60B1006405395BFEF3 | SHA256:533E208A0355E224FB6A02151BCCACE93E73FF748E431D5DD92420CCA15230BE | |||
| 2072 | explorhe.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
19
DNS requests
6
Threats
74
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2072 | explorhe.exe | POST | 200 | 185.215.113.68:80 | http://185.215.113.68/theme/index.php | unknown | text | 2 b | unknown |
2072 | explorhe.exe | GET | 200 | 77.91.68.21:80 | http://77.91.68.21/lend/bakhtiar.exe | unknown | executable | 4.53 Mb | unknown |
2072 | explorhe.exe | GET | 200 | 77.91.68.21:80 | http://77.91.68.21/lend/YT.exe | unknown | executable | 2.21 Mb | unknown |
2072 | explorhe.exe | POST | 200 | 185.215.113.68:80 | http://185.215.113.68/theme/index.php | unknown | text | 4 b | unknown |
2072 | explorhe.exe | GET | 404 | 185.215.113.68:80 | http://185.215.113.68/theme/Plugins/cred.dll | unknown | html | 162 b | unknown |
2072 | explorhe.exe | GET | 200 | 77.91.68.21:80 | http://77.91.68.21/lend/golden.exe | unknown | executable | 365 Kb | unknown |
2072 | explorhe.exe | POST | 200 | 185.215.113.68:80 | http://185.215.113.68/theme/index.php | unknown | text | 4 b | unknown |
2072 | explorhe.exe | POST | 200 | 185.215.113.68:80 | http://185.215.113.68/theme/index.php | unknown | text | 4 b | unknown |
2072 | explorhe.exe | POST | 200 | 185.215.113.68:80 | http://185.215.113.68/theme/index.php | unknown | text | 697 b | unknown |
2072 | explorhe.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?8744af06b0e0ce08 | unknown | compressed | 4.66 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2072 | explorhe.exe | 185.215.113.68:80 | — | 1337team Limited | SC | malicious |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2072 | explorhe.exe | 162.159.129.233:443 | cdn.discordapp.com | CLOUDFLARENET | — | shared |
2072 | explorhe.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
2072 | explorhe.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1592 | ev.exe | 162.19.58.156:443 | i.ibb.co | OVH SAS | FR | unknown |
1592 | ev.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cdn.discordapp.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
i.ibb.co |
| shared |
ipinfo.io |
| shared |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2072 | explorhe.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 22 |
2072 | explorhe.exe | Malware Command and Control Activity Detected | BOTNET [ANY.RUN] Amadey |
1080 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
2072 | explorhe.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
1592 | ev.exe | Not Suspicious Traffic | INFO [ANY.RUN] Image hosting service ImgBB |
2072 | explorhe.exe | A Network Trojan was detected | ET MALWARE Win32/Amadey Host Fingerprint Exfil (POST) M2 |
2072 | explorhe.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
2072 | explorhe.exe | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
2072 | explorhe.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2072 | explorhe.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |