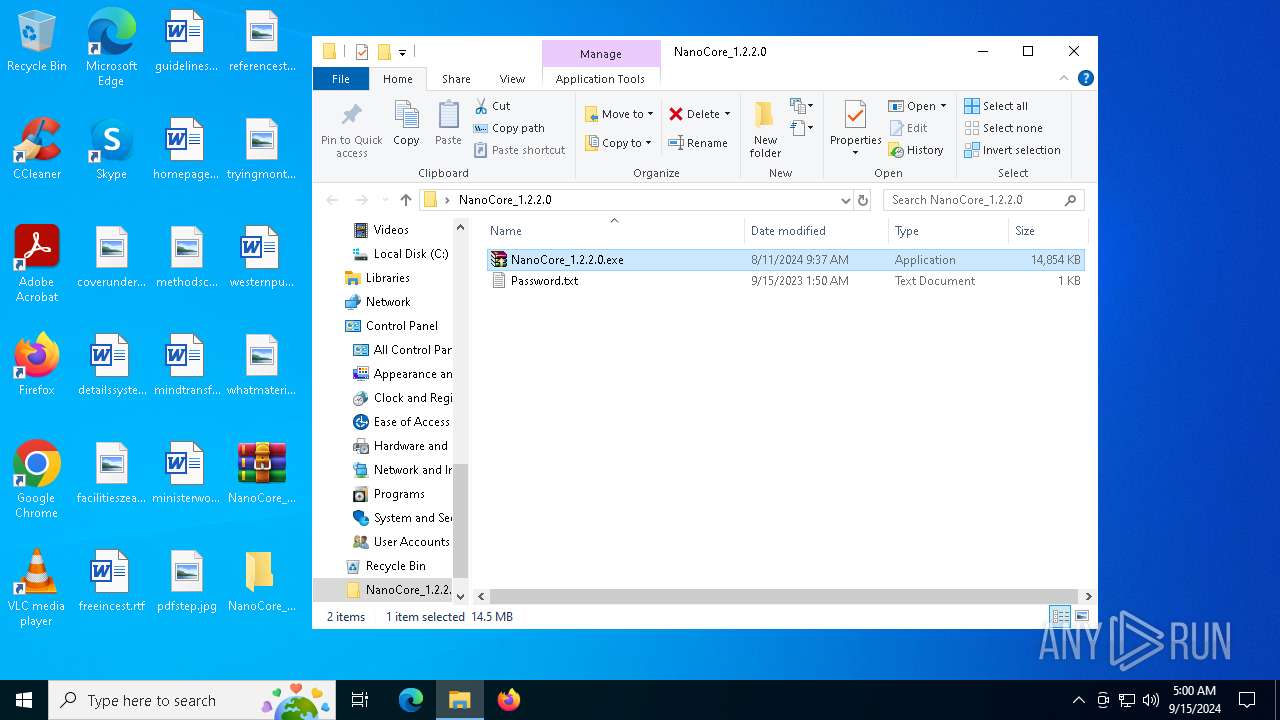
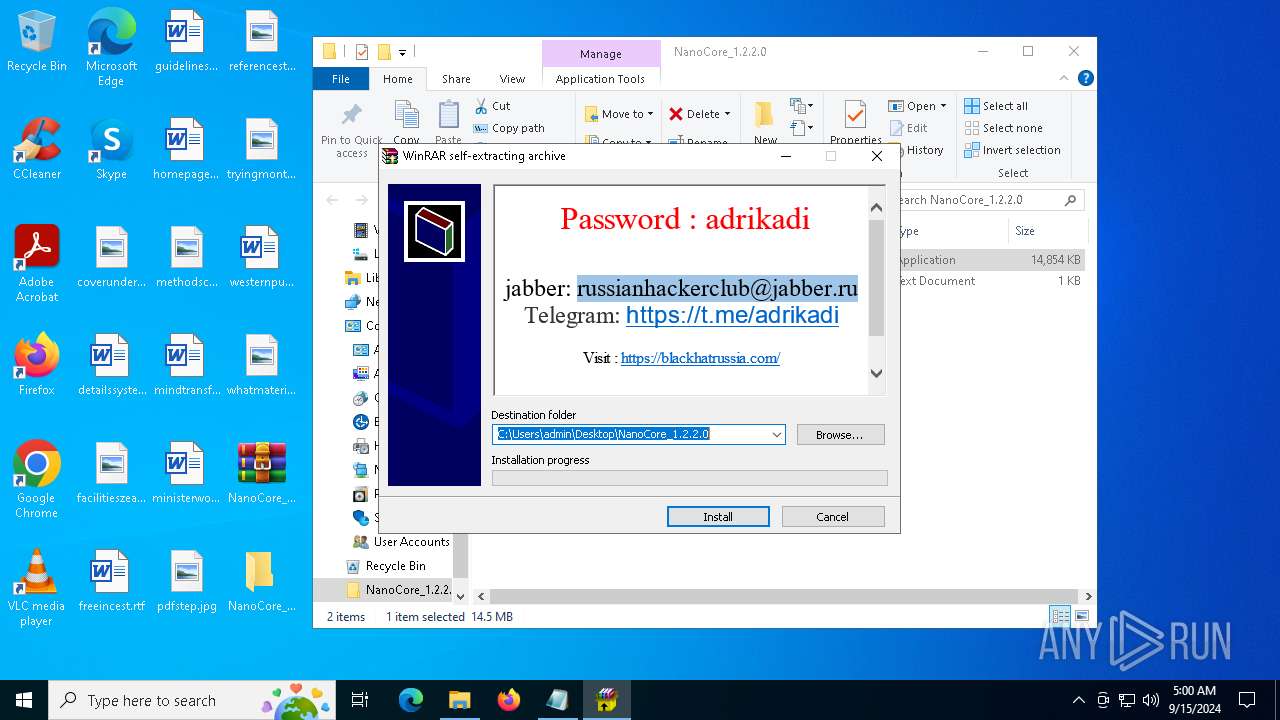
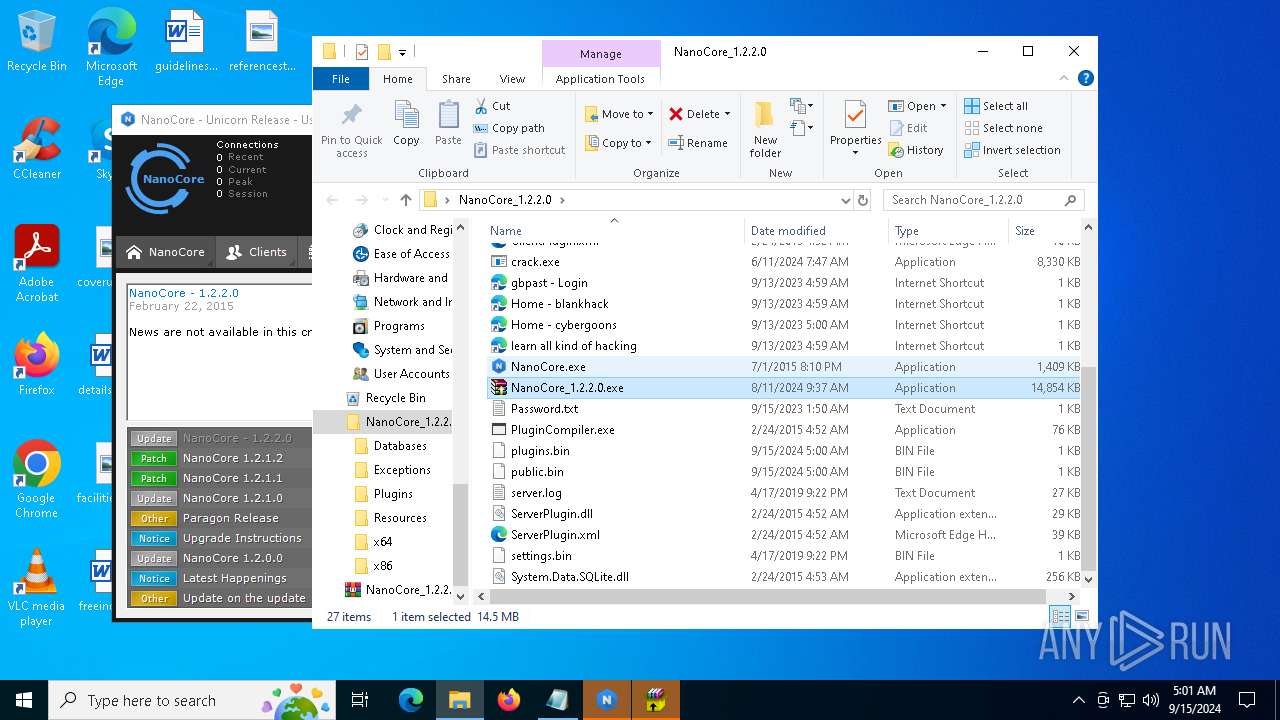
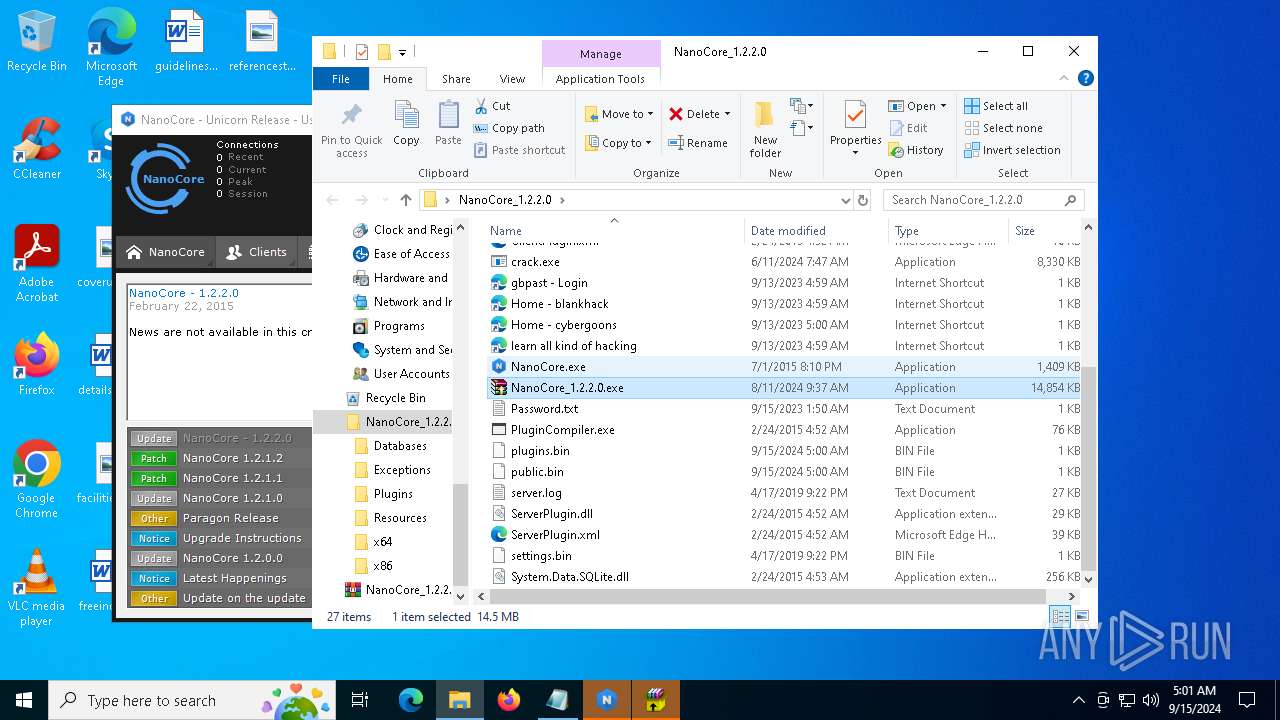
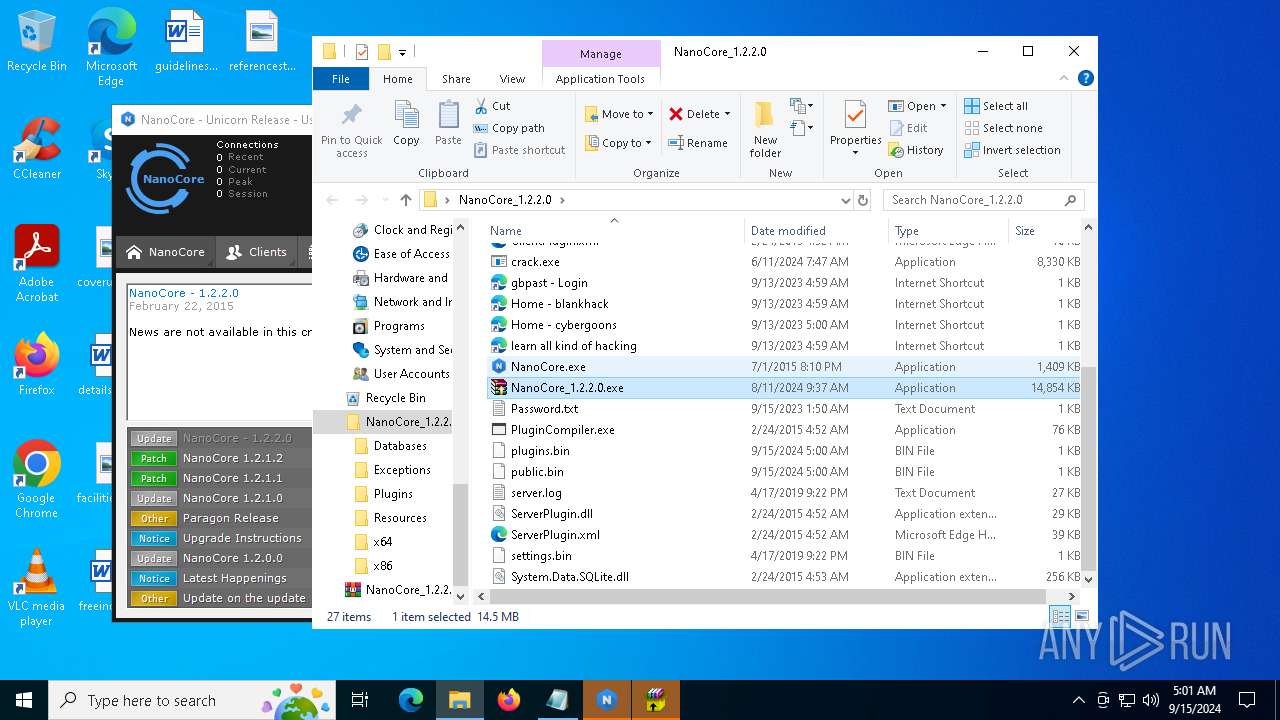
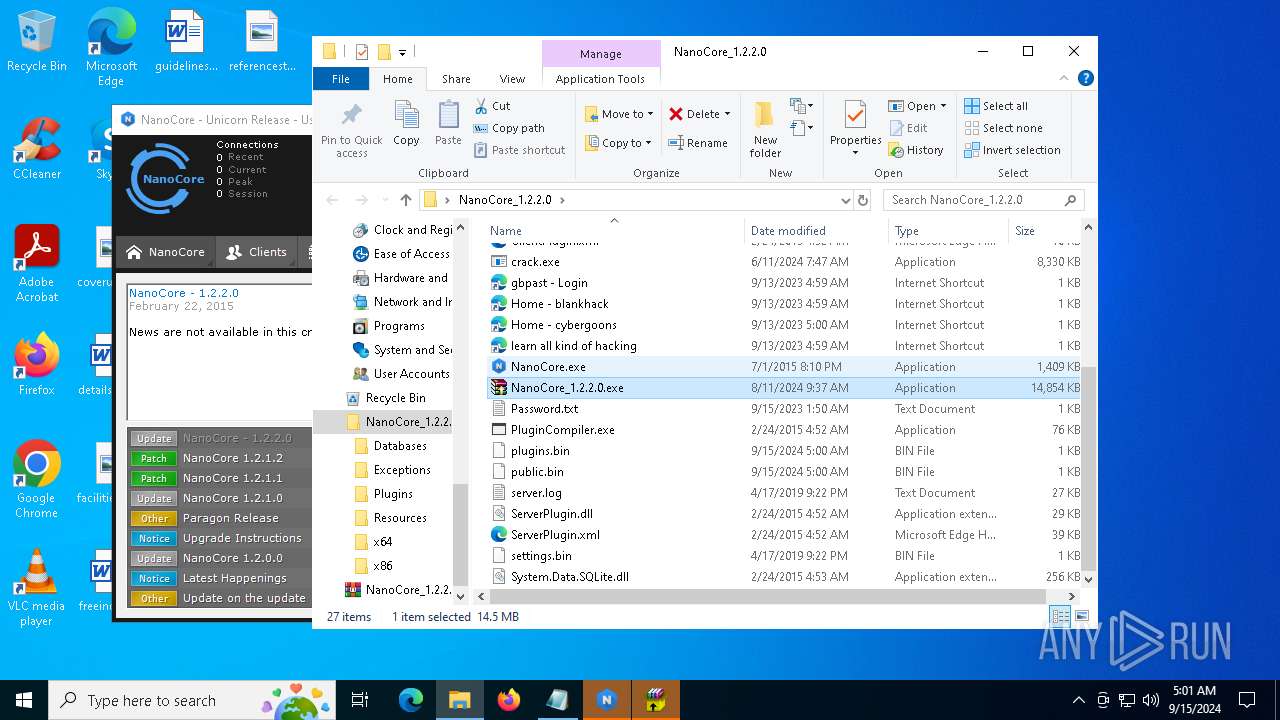
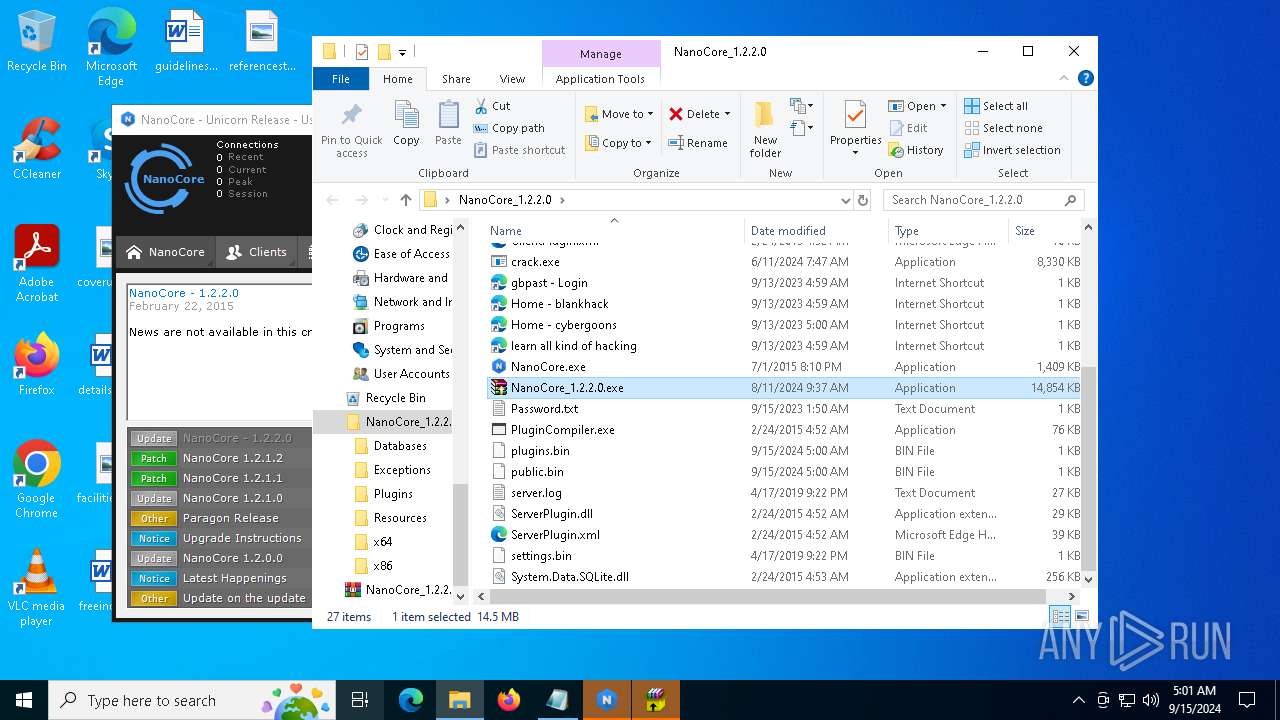
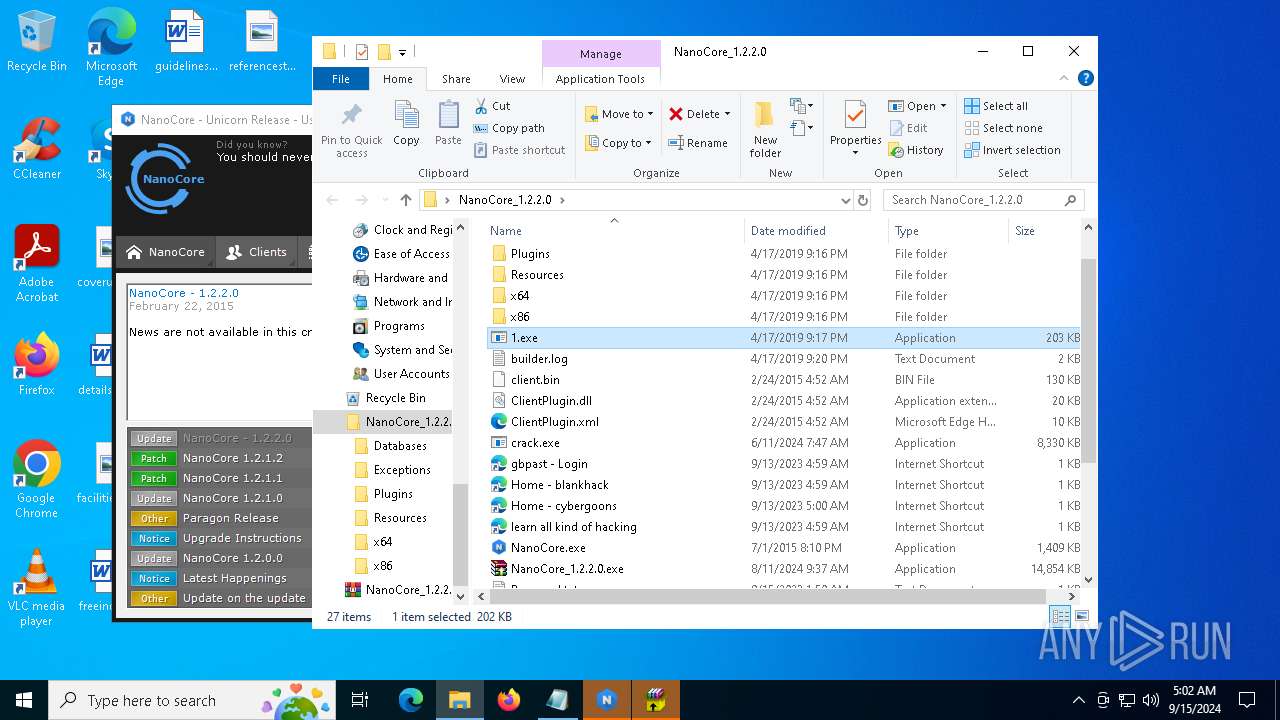
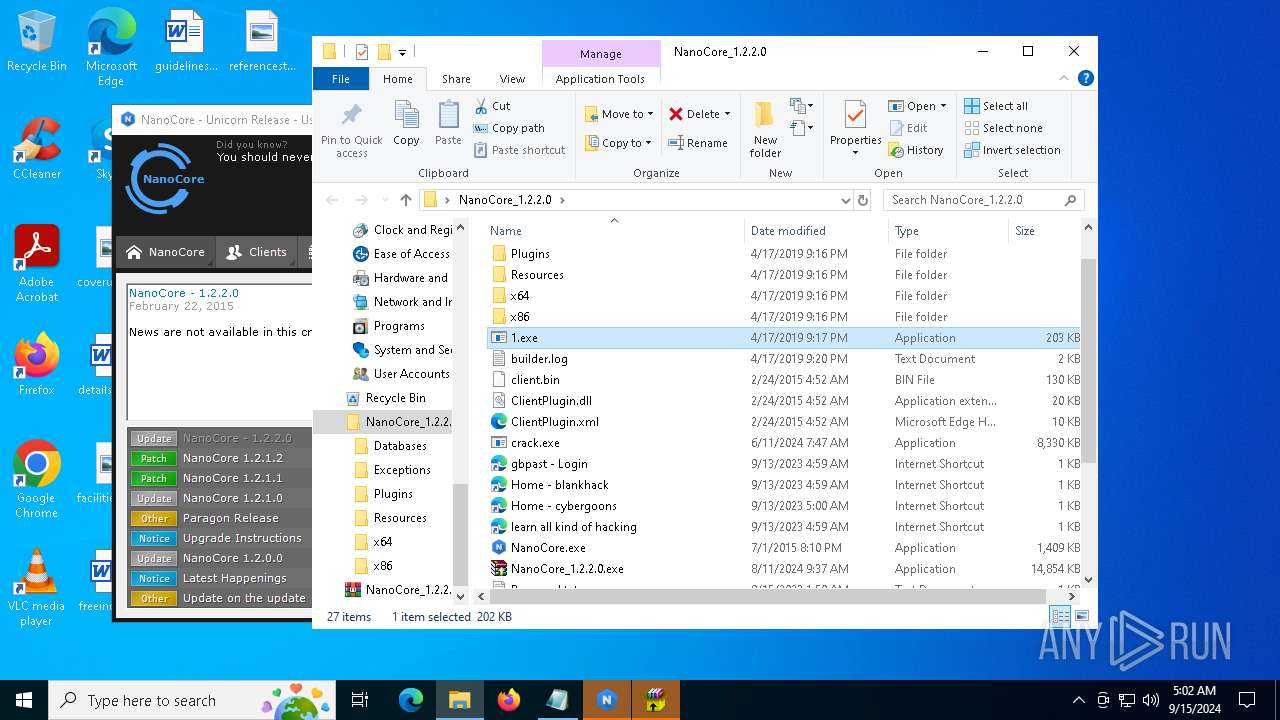
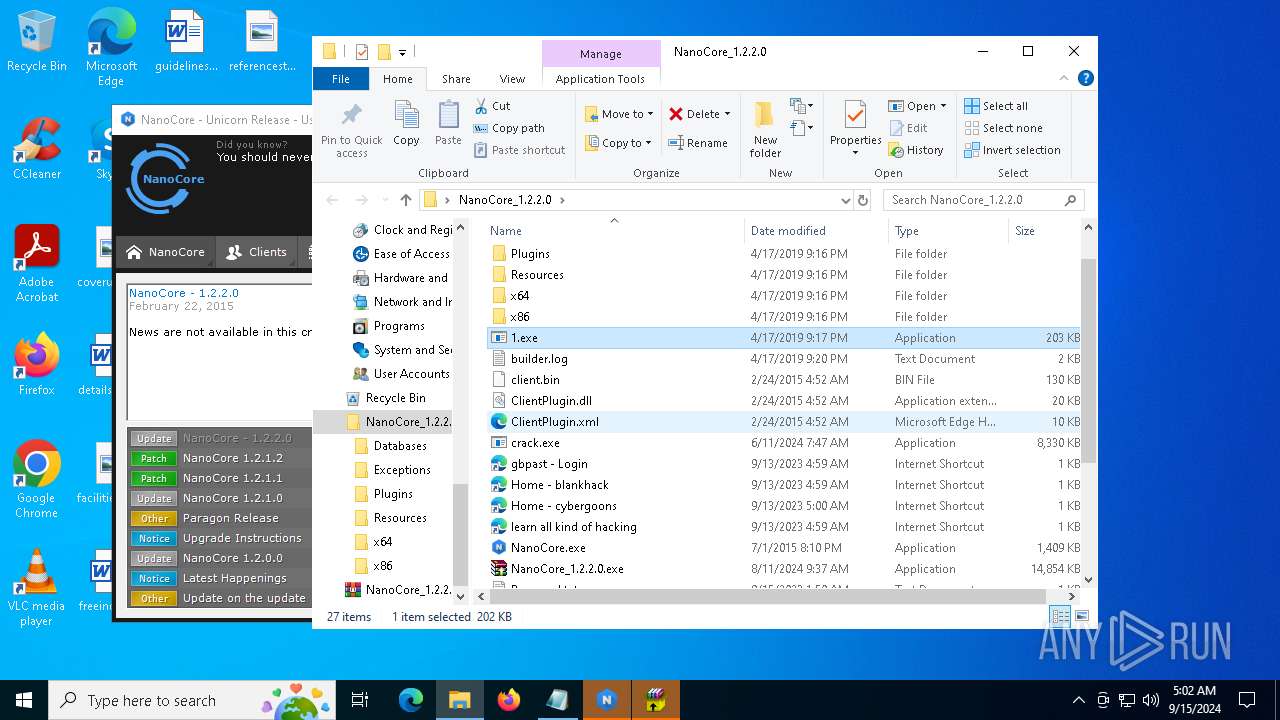
| File name: | NanoCore_1.2.2.0.zip |
| Full analysis: | https://app.any.run/tasks/718b6e19-8ee2-4cee-bb17-c00c5535012c |
| Verdict: | Malicious activity |
| Threats: | Blank Grabber is an infostealer written in Python. It is designed to steal a wide array of data, such as browser login credentials, crypto wallets, Telegram sessions, and Discord tokens. It is an open-source malware, with its code available on GitHub and regularly receiving updates. Blank Grabber builder’s simple interface lets threat actors even with basic skills to deploy it and conduct attacks. |
| Analysis date: | September 15, 2024, 04:58:31 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 8444E1DB6FF3EDC0FA2E4849F971EBBC |
| SHA1: | 9812681EE2E89C87F3314D4FA1C24B14806B14A8 |
| SHA256: | 6B52BD3A456800483DEEBACBF2E029D0A8599693E99758A2F2D0687AC405D21C |
| SSDEEP: | 98304:Lu2m3xWjlpUtVN5SsDwGiEUCCLZvHbDWeY0UAGhrgS0SNAHQLGt1dj0FzCpiCWPV:zeg10m5KqyPNQTfi63jkeZC0u |
MALICIOUS
BlankGrabber has been detected
- crack.exe (PID: 6628)
- crack.exe (PID: 1752)
- crack.exe (PID: 1780)
- crack.exe (PID: 5532)
- crack.exe (PID: 1280)
- crack.exe (PID: 5212)
Create files in the Startup directory
- Payload.exe (PID: 2132)
- crack.exe (PID: 6176)
Antivirus name has been found in the command line (generic signature)
- cmd.exe (PID: 5220)
- MpCmdRun.exe (PID: 2180)
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 4880)
- cmd.exe (PID: 2136)
- crack.exe (PID: 6176)
Windows Defender preferences modified via 'Set-MpPreference'
- cmd.exe (PID: 5220)
Actions looks like stealing of personal data
- crack.exe (PID: 6176)
Changes the autorun value in the registry
- 1.exe (PID: 2524)
Bypass execution policy to execute commands
- powershell.exe (PID: 2096)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 2724)
GROWTOPIA has been detected (YARA)
- crack.exe (PID: 6176)
BLANKGRABBER has been detected (SURICATA)
- crack.exe (PID: 6176)
Stealers network behavior
- crack.exe (PID: 6176)
NANOCORE has been detected (YARA)
- NanoCore.exe (PID: 5164)
- 1.exe (PID: 2524)
UMBRALSTEALER has been detected (YARA)
- crack.exe (PID: 6176)
SUSPICIOUS
Reads security settings of Internet Explorer
- NanoCore_1.2.2.0.exe (PID: 4404)
- NanoCore_1.2.2.0.exe (PID: 7024)
- crack.exe (PID: 6484)
- crack.exe (PID: 5064)
- crack.exe (PID: 2608)
- crack.exe (PID: 4708)
- crack.exe (PID: 2680)
- crack.exe (PID: 6868)
- NanoCore_1.2.2.0.exe (PID: 6032)
- NanoCore.exe (PID: 5164)
Reads Microsoft Outlook installation path
- NanoCore_1.2.2.0.exe (PID: 4404)
- NanoCore_1.2.2.0.exe (PID: 7024)
- NanoCore_1.2.2.0.exe (PID: 6032)
Reads Internet Explorer settings
- NanoCore_1.2.2.0.exe (PID: 4404)
- NanoCore_1.2.2.0.exe (PID: 7024)
- NanoCore_1.2.2.0.exe (PID: 6032)
Executable content was dropped or overwritten
- NanoCore_1.2.2.0.exe (PID: 7024)
- crack.exe (PID: 6484)
- Payload.exe (PID: 2132)
- crack.exe (PID: 6628)
- crack.exe (PID: 1752)
- crack.exe (PID: 6176)
- 1.exe (PID: 2524)
- crack.exe (PID: 1780)
- csc.exe (PID: 2608)
- crack.exe (PID: 5532)
- crack.exe (PID: 1280)
- crack.exe (PID: 5212)
BASE64 encoded PowerShell command has been detected
- crack.exe (PID: 6484)
- cmd.exe (PID: 2724)
- crack.exe (PID: 2608)
- crack.exe (PID: 2680)
Base64-obfuscated command line is found
- crack.exe (PID: 6484)
- cmd.exe (PID: 2724)
- crack.exe (PID: 2608)
- crack.exe (PID: 2680)
Starts POWERSHELL.EXE for commands execution
- crack.exe (PID: 6484)
- cmd.exe (PID: 5220)
- cmd.exe (PID: 4880)
- cmd.exe (PID: 2136)
- cmd.exe (PID: 2724)
- cmd.exe (PID: 5212)
- crack.exe (PID: 2608)
- cmd.exe (PID: 6168)
- crack.exe (PID: 2680)
- cmd.exe (PID: 7056)
- cmd.exe (PID: 6580)
- cmd.exe (PID: 1828)
Starts a Microsoft application from unusual location
- crack.exe (PID: 6628)
- crack.exe (PID: 5064)
- crack.exe (PID: 1752)
- crack.exe (PID: 6176)
- crack.exe (PID: 1780)
- crack.exe (PID: 4708)
- crack.exe (PID: 5532)
- crack.exe (PID: 6212)
- crack.exe (PID: 1280)
- crack.exe (PID: 6868)
- crack.exe (PID: 1636)
- crack.exe (PID: 5212)
Loads Python modules
- crack.exe (PID: 5064)
- crack.exe (PID: 6176)
- crack.exe (PID: 4708)
- crack.exe (PID: 6212)
Application launched itself
- crack.exe (PID: 6628)
- crack.exe (PID: 5064)
- crack.exe (PID: 1752)
- crack.exe (PID: 1780)
- crack.exe (PID: 5532)
- crack.exe (PID: 4708)
- crack.exe (PID: 1280)
- crack.exe (PID: 5212)
- crack.exe (PID: 6868)
Reads the date of Windows installation
- crack.exe (PID: 5064)
- crack.exe (PID: 4708)
- crack.exe (PID: 6868)
Process drops python dynamic module
- crack.exe (PID: 6628)
- crack.exe (PID: 1752)
- crack.exe (PID: 1780)
- crack.exe (PID: 5532)
- crack.exe (PID: 1280)
- crack.exe (PID: 5212)
Script disables Windows Defender's real-time protection
- cmd.exe (PID: 5220)
Script disables Windows Defender's IPS
- cmd.exe (PID: 5220)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 4880)
- cmd.exe (PID: 2136)
Starts CMD.EXE for commands execution
- crack.exe (PID: 6176)
Found strings related to reading or modifying Windows Defender settings
- crack.exe (PID: 6176)
The process creates files with name similar to system file names
- 1.exe (PID: 2524)
Get information on the list of running processes
- cmd.exe (PID: 6372)
- cmd.exe (PID: 1748)
- crack.exe (PID: 6176)
- cmd.exe (PID: 6192)
Uses SYSTEMINFO.EXE to read the environment
- cmd.exe (PID: 5172)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 6276)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 6572)
- cmd.exe (PID: 5508)
Accesses antivirus product name via WMI (SCRIPT)
- WMIC.exe (PID: 2868)
Starts application with an unusual extension
- cmd.exe (PID: 2028)
- cmd.exe (PID: 4072)
- cmd.exe (PID: 2028)
- cmd.exe (PID: 7072)
- cmd.exe (PID: 6840)
- cmd.exe (PID: 2028)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 2724)
Found regular expressions for crypto-addresses (YARA)
- Payload.exe (PID: 2132)
The executable file from the user directory is run by the CMD process
- rar.exe (PID: 7000)
Accesses operating system name via WMI (SCRIPT)
- WMIC.exe (PID: 5888)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 6452)
Accesses product unique identifier via WMI (SCRIPT)
- WMIC.exe (PID: 3896)
Accesses video controller name via WMI (SCRIPT)
- WMIC.exe (PID: 1344)
Uses WMIC.EXE to obtain a list of video controllers
- cmd.exe (PID: 6948)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 4920)
Checks for external IP
- svchost.exe (PID: 2256)
- crack.exe (PID: 6176)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- crack.exe (PID: 6176)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5796)
Checks supported languages
- NanoCore_1.2.2.0.exe (PID: 4404)
- NanoCore_1.2.2.0.exe (PID: 7024)
- crack.exe (PID: 6484)
- Payload.exe (PID: 2132)
- crack.exe (PID: 5064)
- crack.exe (PID: 6628)
- crack.exe (PID: 1752)
- crack.exe (PID: 6176)
- 1.exe (PID: 2524)
- tree.com (PID: 5160)
- 1.exe (PID: 6512)
- tree.com (PID: 6840)
- tree.com (PID: 3864)
- crack.exe (PID: 2608)
- Payload.exe (PID: 2036)
- tree.com (PID: 1440)
- tree.com (PID: 2584)
- csc.exe (PID: 2608)
- crack.exe (PID: 1780)
- tree.com (PID: 6964)
- crack.exe (PID: 4708)
- cvtres.exe (PID: 6988)
- MpCmdRun.exe (PID: 2180)
- crack.exe (PID: 5532)
- crack.exe (PID: 6212)
- crack.exe (PID: 2680)
- Payload.exe (PID: 4920)
- crack.exe (PID: 6868)
- crack.exe (PID: 1280)
- crack.exe (PID: 5212)
- NanoCore.exe (PID: 5164)
- crack.exe (PID: 1636)
- rar.exe (PID: 7000)
- NanoCore_1.2.2.0.exe (PID: 6032)
- 1.exe (PID: 6680)
- 1.exe (PID: 6744)
The process uses the downloaded file
- WinRAR.exe (PID: 5796)
- NanoCore_1.2.2.0.exe (PID: 7024)
- crack.exe (PID: 6484)
- crack.exe (PID: 5064)
- powershell.exe (PID: 6336)
- 1.exe (PID: 2524)
- crack.exe (PID: 2608)
- crack.exe (PID: 4708)
- powershell.exe (PID: 6012)
- crack.exe (PID: 2680)
- powershell.exe (PID: 2508)
- crack.exe (PID: 6868)
Manual execution by a user
- NanoCore_1.2.2.0.exe (PID: 4404)
- WinRAR.exe (PID: 5796)
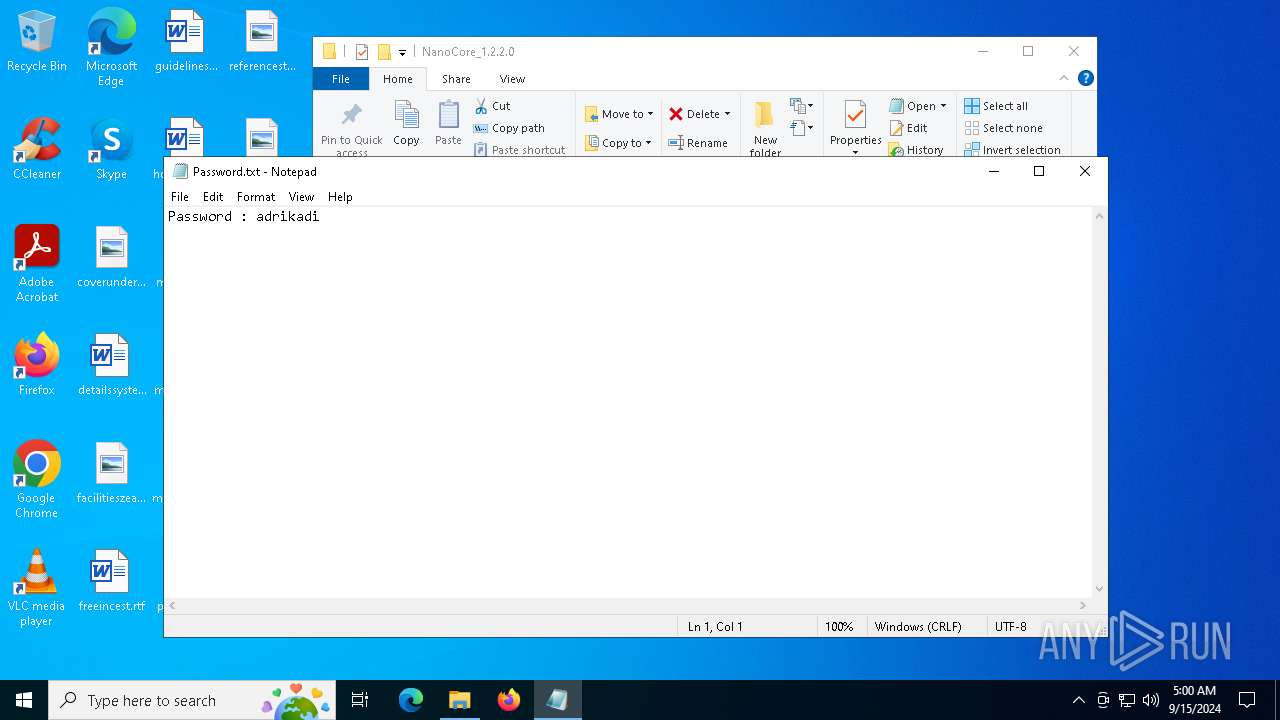
- notepad.exe (PID: 5852)
- NanoCore_1.2.2.0.exe (PID: 7024)
- 1.exe (PID: 2524)
- 1.exe (PID: 6512)
- crack.exe (PID: 2608)
- crack.exe (PID: 2680)
- NanoCore.exe (PID: 5164)
- NanoCore_1.2.2.0.exe (PID: 6032)
- 1.exe (PID: 6744)
- 1.exe (PID: 6680)
Reads the computer name
- NanoCore_1.2.2.0.exe (PID: 4404)
- NanoCore_1.2.2.0.exe (PID: 7024)
- crack.exe (PID: 6484)
- Payload.exe (PID: 2132)
- crack.exe (PID: 5064)
- crack.exe (PID: 6628)
- crack.exe (PID: 1752)
- crack.exe (PID: 6176)
- 1.exe (PID: 2524)
- crack.exe (PID: 2608)
- 1.exe (PID: 6512)
- Payload.exe (PID: 2036)
- crack.exe (PID: 1780)
- crack.exe (PID: 4708)
- MpCmdRun.exe (PID: 2180)
- crack.exe (PID: 5532)
- crack.exe (PID: 2680)
- Payload.exe (PID: 4920)
- crack.exe (PID: 6868)
- crack.exe (PID: 1280)
- crack.exe (PID: 5212)
- NanoCore.exe (PID: 5164)
- NanoCore_1.2.2.0.exe (PID: 6032)
- 1.exe (PID: 6744)
Checks proxy server information
- NanoCore_1.2.2.0.exe (PID: 4404)
- NanoCore_1.2.2.0.exe (PID: 7024)
- NanoCore_1.2.2.0.exe (PID: 6032)
- NanoCore.exe (PID: 5164)
Reads security settings of Internet Explorer
- notepad.exe (PID: 5852)
- WMIC.exe (PID: 2868)
- WMIC.exe (PID: 5888)
- WMIC.exe (PID: 7128)
- WMIC.exe (PID: 3896)
- WMIC.exe (PID: 1344)
Create files in a temporary directory
- crack.exe (PID: 6484)
- crack.exe (PID: 5064)
- crack.exe (PID: 6628)
- crack.exe (PID: 1752)
- crack.exe (PID: 6176)
- crack.exe (PID: 1780)
- csc.exe (PID: 2608)
- cvtres.exe (PID: 6988)
- crack.exe (PID: 4708)
- MpCmdRun.exe (PID: 2180)
- crack.exe (PID: 5532)
- crack.exe (PID: 6212)
- crack.exe (PID: 6868)
- crack.exe (PID: 1280)
- crack.exe (PID: 5212)
- crack.exe (PID: 1636)
- rar.exe (PID: 7000)
Process checks computer location settings
- NanoCore_1.2.2.0.exe (PID: 7024)
- crack.exe (PID: 6484)
- crack.exe (PID: 5064)
- crack.exe (PID: 2608)
- crack.exe (PID: 4708)
- crack.exe (PID: 2680)
- crack.exe (PID: 6868)
Reads the machine GUID from the registry
- Payload.exe (PID: 2132)
- 1.exe (PID: 2524)
- 1.exe (PID: 6512)
- csc.exe (PID: 2608)
- NanoCore.exe (PID: 5164)
- rar.exe (PID: 7000)
- 1.exe (PID: 6744)
- 1.exe (PID: 6680)
Creates files or folders in the user directory
- Payload.exe (PID: 2132)
- 1.exe (PID: 2524)
- NanoCore.exe (PID: 5164)
Creates files in the program directory
- crack.exe (PID: 6176)
Process checks whether UAC notifications are on
- 1.exe (PID: 2524)
The Powershell gets current clipboard
- powershell.exe (PID: 488)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6336)
- powershell.exe (PID: 5040)
- powershell.exe (PID: 4132)
- powershell.exe (PID: 6740)
- powershell.exe (PID: 6012)
- powershell.exe (PID: 2508)
Found Base64 encoded access to Windows Defender via PowerShell (YARA)
- powershell.exe (PID: 6336)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6336)
- powershell.exe (PID: 5040)
- powershell.exe (PID: 4132)
- powershell.exe (PID: 6740)
- powershell.exe (PID: 5524)
- powershell.exe (PID: 6012)
- powershell.exe (PID: 2508)
- powershell.exe (PID: 6200)
Sends debugging messages
- crack.exe (PID: 2608)
- crack.exe (PID: 2680)
- NanoCore.exe (PID: 5164)
Displays MAC addresses of computer network adapters
- getmac.exe (PID: 6380)
Disables trace logs
- NanoCore.exe (PID: 5164)
PyInstaller has been detected (YARA)
- crack.exe (PID: 1752)
Found Base64 encoded reflection usage via PowerShell (YARA)
- crack.exe (PID: 6176)
Attempting to use instant messaging service
- crack.exe (PID: 6176)
- svchost.exe (PID: 2256)
.NET Reactor protector has been detected
- NanoCore.exe (PID: 5164)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Nanocore
(PID) Process(2524) 1.exe
BuildTime2019-04-17 18:17:16.895688
Version1.2.2.0
Mutexf5968560-41da-44be-bf8f-6c3fa860d635
DefaultGroupDefault
PrimaryConnectionHost
BackupConnectionHost127.0.0.1
ConnectionPort54984
RunOnStartupTrue
RequestElevationFalse
BypassUserAccountControlFalse
ClearZoneIdentifierTrue
ClearAccessControlFalse
SetCriticalProcessFalse
PreventSystemSleepTrue
ActivateAwayModeFalse
EnableDebugModeFalse
RunDelay0
ConnectDelay4000
RestartDelay5000
TimeoutInterval5000
KeepAliveTimeout30000
MutexTimeout5000
LanTimeout2500
WanTimeout8000
BufferSize65535
MaxPacketSize10485760
GCThreshold10485760
UseCustomDnsServerTrue
PrimaryDnsServer8.8.8.8
BackupDnsServer8.8.4.4
(PID) Process(5164) NanoCore.exe
ERROR
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:08:11 09:37:24 |
| ZipCRC: | 0xfae0ba02 |
| ZipCompressedSize: | 15075741 |
| ZipUncompressedSize: | 15209580 |
| ZipFileName: | NanoCore_1.2.2.0/NanoCore_1.2.2.0.exe |
Total processes
250
Monitored processes
122
Malicious processes
19
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 488 | powershell Get-Clipboard | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1084 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1224 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\NanoCore_1.2.2.0.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1280 | "C:\Users\admin\AppData\Local\Temp\crack.exe" | C:\Users\admin\AppData\Local\Temp\crack.exe | crack.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MDMAgent Exit code: 0 Version: 10.0.22621.2506 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1344 | wmic path win32_VideoController get name | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1436 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1440 | tree /A /F | C:\Windows\System32\tree.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Tree Walk Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1636 | "C:\Users\admin\AppData\Local\Temp\crack.exe" C:\Users\admin\AppData\Local\Temp\crack.exe | C:\Users\admin\AppData\Local\Temp\crack.exe | — | crack.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: MDMAgent Exit code: 0 Version: 10.0.22621.2506 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1748 | C:\WINDOWS\system32\cmd.exe /c "tasklist /FO LIST" | C:\Windows\System32\cmd.exe | — | crack.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
83 674
Read events
83 623
Write events
47
Delete events
4
Modification events
| (PID) Process: | (1224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (1224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\NanoCore_1.2.2.0.zip | |||
| (PID) Process: | (1224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000200000003000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (1224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (1224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | psize |
Value: 80 | |||
Executable files
359
Suspicious files
52
Text files
419
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7024 | NanoCore_1.2.2.0.exe | C:\Users\admin\Desktop\NanoCore_1.2.2.0\Resources\Themes\Classic.xml | xml | |
MD5:769E96DFDE51FF03A4A1B6F1B7A6F0D9 | SHA256:F35CCB8A314F11EE46668D08528F6F21F02BC7E8D5716C838623C9F0ECC557E9 | |||
| 7024 | NanoCore_1.2.2.0.exe | C:\Users\admin\Desktop\NanoCore_1.2.2.0\Resources\Themes\Terminus.xml | xml | |
MD5:0E74131700FDA404D96EAF7ECEB279F4 | SHA256:32F80F9434A1D137CFEB2ED9850C4A900165ABBFED2269533C0FC8CE5481D7CA | |||
| 7024 | NanoCore_1.2.2.0.exe | C:\Users\admin\Desktop\NanoCore_1.2.2.0\server.log | text | |
MD5:94B077234490A33228A743A400EDDBB7 | SHA256:61B45AFD63D8ADF0A44751B3BAC3C63F6810E2DAD903108C79D59060480FC328 | |||
| 7024 | NanoCore_1.2.2.0.exe | C:\Users\admin\Desktop\NanoCore_1.2.2.0\x86\SQLite.Interop.dll | executable | |
MD5:9B19DCEE960DC215E64B1D82348707A9 | SHA256:3515F704B0012C01FC8BE5B717905C0587B29255FC9EB7AD3F2B66A130691D38 | |||
| 7024 | NanoCore_1.2.2.0.exe | C:\Users\admin\Desktop\NanoCore_1.2.2.0\1.exe | executable | |
MD5:7262CD751358CFECB8D31FF81575AC29 | SHA256:4667CA924AA5CBFD0A793DA30825F5CB7EA98B2DDF83377C7B6ED91D73C3420C | |||
| 7024 | NanoCore_1.2.2.0.exe | C:\Users\admin\Desktop\NanoCore_1.2.2.0\PluginCompiler.exe | executable | |
MD5:E2D1C5DF11F9573F6C5D0A7AD1A79FBF | SHA256:0B41B2FCD0F1A4E913D3EFE293F713849D59EFEBB27BAC060AB31BED51AC2F6B | |||
| 7024 | NanoCore_1.2.2.0.exe | C:\Users\admin\Desktop\NanoCore_1.2.2.0\Exceptions\Server\1.2.2.0\f739a9d34beac42d55c5ae90e14e54f8.log | text | |
MD5:F739A9D34BEAC42D55C5AE90E14E54F8 | SHA256:EADFAAD62CA5015686CCE060C9B015F4BD3A4A662D5F7151D91C672C3DCECFAE | |||
| 7024 | NanoCore_1.2.2.0.exe | C:\Users\admin\Desktop\NanoCore_1.2.2.0\ServerPlugin.xml | xml | |
MD5:8245E02B3A884C86E66791879FB79A28 | SHA256:3CF9CC86656B3719555E76B9F86D1765BC700C6A9A8228539F0521AF96E81CDA | |||
| 5796 | WinRAR.exe | C:\Users\admin\Desktop\NanoCore_1.2.2.0\NanoCore_1.2.2.0.exe | executable | |
MD5:9F0245A3C5E691126F42EE5BB1BC1A40 | SHA256:F53F62A9093F8AF6FD63F1284E2E264343E9E54080DD7345B8F0247FCA8C80B4 | |||
| 7024 | NanoCore_1.2.2.0.exe | C:\Users\admin\Desktop\NanoCore_1.2.2.0\ClientPlugin.xml | xml | |
MD5:5D0381A56563B1CA8928E3CF087F1625 | SHA256:0497B92461C2A9CE3101D9397FB3079F60979164336A16653D282273D3085BCC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
31
DNS requests
17
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1776 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3332 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3332 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6176 | crack.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/?fields=225545 | unknown | — | — | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6440 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6280 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1776 | svchost.exe | 40.126.32.134:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1776 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
gstatic.com |
| whitelisted |
lazyshare.net |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
2256 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
2256 | svchost.exe | Misc activity | SUSPICIOUS [ANY.RUN] Possible sending an external IP address to Telegram |
6176 | crack.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
2256 | svchost.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
6176 | crack.exe | A Network Trojan was detected | STEALER [ANY.RUN] BlankGrabber (SkochGrabber) Generic External IP Check |
6176 | crack.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
Process | Message |
|---|---|
crack.exe | Invalid parameter passed to C runtime function.
|
crack.exe | Invalid parameter passed to C runtime function.
|
crack.exe | Invalid parameter passed to C runtime function.
|
crack.exe | Invalid parameter passed to C runtime function.
|
crack.exe | Invalid parameter passed to C runtime function.
|
crack.exe | Invalid parameter passed to C runtime function.
|
crack.exe | Invalid parameter passed to C runtime function.
|
crack.exe | Invalid parameter passed to C runtime function.
|
NanoCore.exe | Trying to load native SQLite library "C:\Users\admin\Desktop\NanoCore_1.2.2.0\x86\SQLite.Interop.dll"...
|