| download: | PO_3100191302_pdf%20%20%20IGST.com.gz |
| Full analysis: | https://app.any.run/tasks/2d4d2a1f-23e8-4c07-a5ca-ddf55662ff75 |
| Verdict: | Malicious activity |
| Threats: | Hawkeye often gets installed in a bundle with other malware. This is a Trojan and keylogger that is used to retrieve private information such as passwords and login credentials. This is an advanced malware that features strong anti-evasion functions. |
| Analysis date: | July 18, 2019, 13:15:31 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
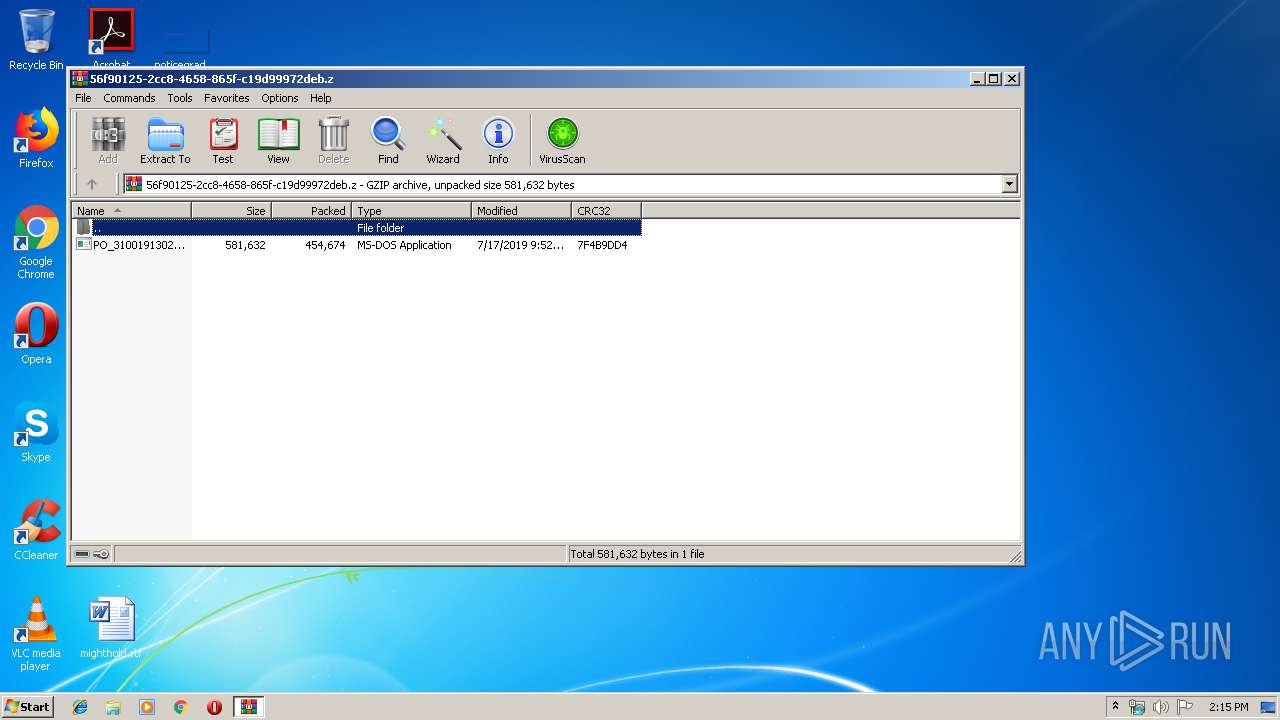
| MIME: | application/gzip |
| File info: | gzip compressed data, was "PO_3100191302_pdf IGST.com", last modified: Wed Jul 17 20:52:16 2019, from Unix |
| MD5: | F315262E9AE5FC9C8B5FAEC160D14905 |
| SHA1: | C68439076BA57B07DEC9053BF5800F4934855212 |
| SHA256: | 6B3E31106968E2134F689EF95ECEEDFEA96ADEE21438944809974D626EA521F8 |
| SSDEEP: | 12288:4D42ZY7pLLQ6+3+x7M9vZ3PIDhEQBXd5mekj3S:4D42ZY9Q6+A7MhZohtd5mLj3S |
MALICIOUS
Application was dropped or rewritten from another process
- PO_3100191302_pdf IGST.com (PID: 2856)
- msconfig1.exe (PID: 3420)
Actions looks like stealing of personal data
- vbc.exe (PID: 2104)
Changes the autorun value in the registry
- msconfig1.exe (PID: 3420)
Changes settings of System certificates
- msconfig1.exe (PID: 3420)
Detected Hawkeye Keylogger
- msconfig1.exe (PID: 3420)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2880)
- msconfig1.exe (PID: 3420)
- PO_3100191302_pdf IGST.com (PID: 2856)
Starts itself from another location
- PO_3100191302_pdf IGST.com (PID: 2856)
Executes scripts
- msconfig1.exe (PID: 3420)
Loads DLL from Mozilla Firefox
- vbc.exe (PID: 2496)
Checks for external IP
- msconfig1.exe (PID: 3420)
Adds / modifies Windows certificates
- msconfig1.exe (PID: 3420)
Creates files in the user directory
- PO_3100191302_pdf IGST.com (PID: 2856)
- msconfig1.exe (PID: 3420)
INFO
Manual execution by user
- PO_3100191302_pdf IGST.com (PID: 2856)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .z/gz/gzip | | | GZipped data (100) |
|---|
EXIF
ZIP
| Compression: | Deflated |
|---|---|
| Flags: | FileName |
| ModifyDate: | 2019:07:17 22:52:16+02:00 |
| ExtraFlags: | (none) |
| OperatingSystem: | Unix |
| ArchivedFileName: | PO_3100191302_pdf IGST.com |
Total processes
42
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2104 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe /stext "C:\Users\admin\AppData\Local\Temp\holdermail.txt" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe | msconfig1.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Basic Command Line Compiler Exit code: 0 Version: 8.0.50727.5420 Modules
| |||||||||||||||
| 2496 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe /stext "C:\Users\admin\AppData\Local\Temp\holderwb.txt" | C:\Windows\Microsoft.NET\Framework\v2.0.50727\vbc.exe | — | msconfig1.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Basic Command Line Compiler Exit code: 0 Version: 8.0.50727.5420 Modules
| |||||||||||||||
| 2856 | "C:\Users\admin\Desktop\PO_3100191302_pdf IGST.com" | C:\Users\admin\Desktop\PO_3100191302_pdf IGST.com | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 2880 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\56f90125-2cc8-4658-865f-c19d99972deb.z" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3420 | "C:\Users\admin\AppData\Roaming\msconfig1.exe" | C:\Users\admin\AppData\Roaming\msconfig1.exe | PO_3100191302_pdf IGST.com | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
Total events
952
Read events
909
Write events
42
Delete events
1
Modification events
| (PID) Process: | (2880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2880) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\56f90125-2cc8-4658-865f-c19d99972deb.z | |||
| (PID) Process: | (2880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2880) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
| (PID) Process: | (2856) PO_3100191302_pdf IGST.com | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
4
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2104 | vbc.exe | C:\Users\admin\AppData\Local\Temp\holdermail.txt | — | |
MD5:— | SHA256:— | |||
| 2496 | vbc.exe | C:\Users\admin\AppData\Local\Temp\holderwb.txt | — | |
MD5:— | SHA256:— | |||
| 2880 | WinRAR.exe | C:\Users\admin\Desktop\PO_3100191302_pdf IGST.com | executable | |
MD5:— | SHA256:— | |||
| 2856 | PO_3100191302_pdf IGST.com | C:\Users\admin\AppData\Roaming\msconfig1.exe | executable | |
MD5:— | SHA256:— | |||
| 3420 | msconfig1.exe | C:\Users\admin\AppData\RoamingMicrosoft\System\Services\18.exe | executable | |
MD5:— | SHA256:— | |||
| 3420 | msconfig1.exe | C:\Users\admin\AppData\Roaming\pidloc.txt | text | |
MD5:— | SHA256:— | |||
| 3420 | msconfig1.exe | C:\Users\admin\AppData\Roaming\WindowsUpdate.exe | executable | |
MD5:— | SHA256:— | |||
| 3420 | msconfig1.exe | C:\Users\admin\AppData\Roaming\pid.txt | text | |
MD5:643DE7CF7BA769C7466CCBC4ADFD7FAC | SHA256:7C6CB0B8E3DCE46864D50F483D628391F1F6F5398A8404003CE8D12150F563B2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
3
DNS requests
2
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3420 | msconfig1.exe | GET | 301 | 104.16.154.36:80 | http://whatismyipaddress.com/ | US | — | — | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3420 | msconfig1.exe | 104.16.154.36:80 | whatismyipaddress.com | Cloudflare Inc | US | shared |
3420 | msconfig1.exe | 104.16.154.36:443 | whatismyipaddress.com | Cloudflare Inc | US | shared |
3420 | msconfig1.exe | 192.185.105.194:587 | mail.freeautocadtutor4.com | CyrusOne LLC | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
whatismyipaddress.com |
| shared |
mail.freeautocadtutor4.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3420 | msconfig1.exe | Potential Corporate Privacy Violation | ET POLICY Known External IP Lookup Service Domain in SNI |
3420 | msconfig1.exe | A Network Trojan was detected | MALWARE [PTsecurity] Spyware.HawkEyeKeyLogger (IP Chck) |
3420 | msconfig1.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |
2 ETPRO signatures available at the full report