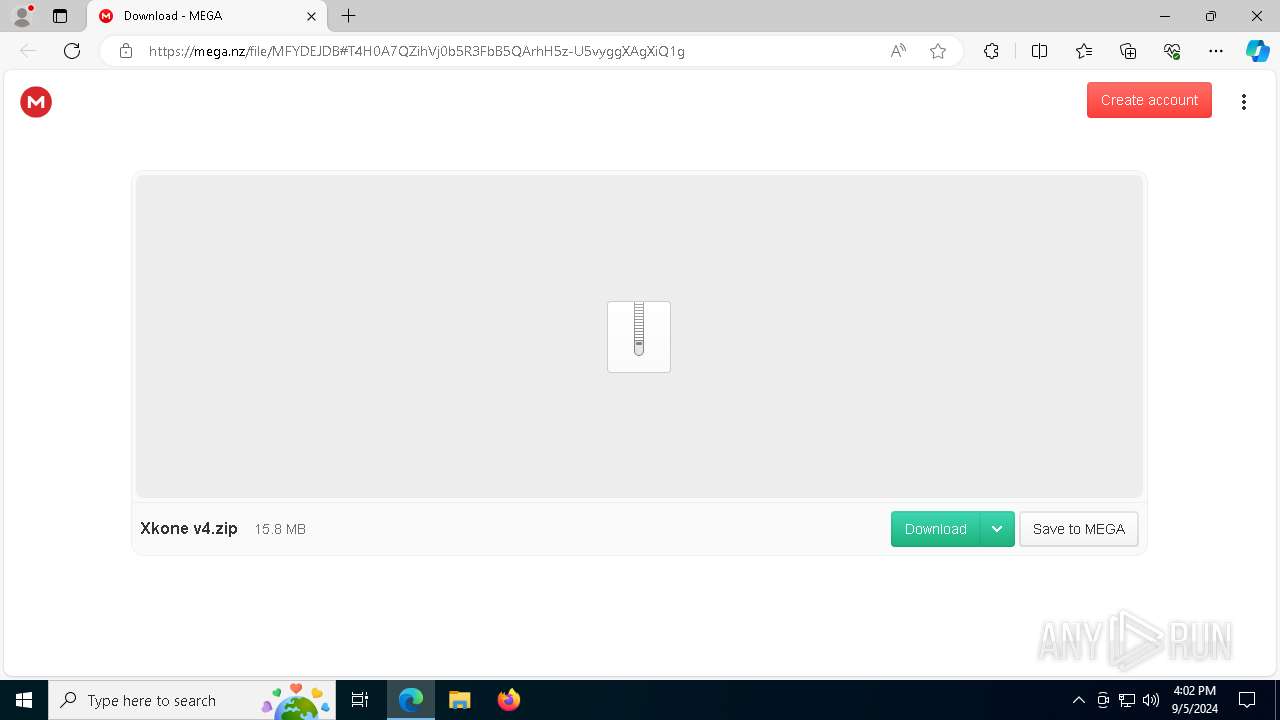
| URL: | https://bit.ly/4e5FTKk |
| Full analysis: | https://app.any.run/tasks/f107a8d7-d67c-482a-81ca-daed99720fed |
| Verdict: | Malicious activity |
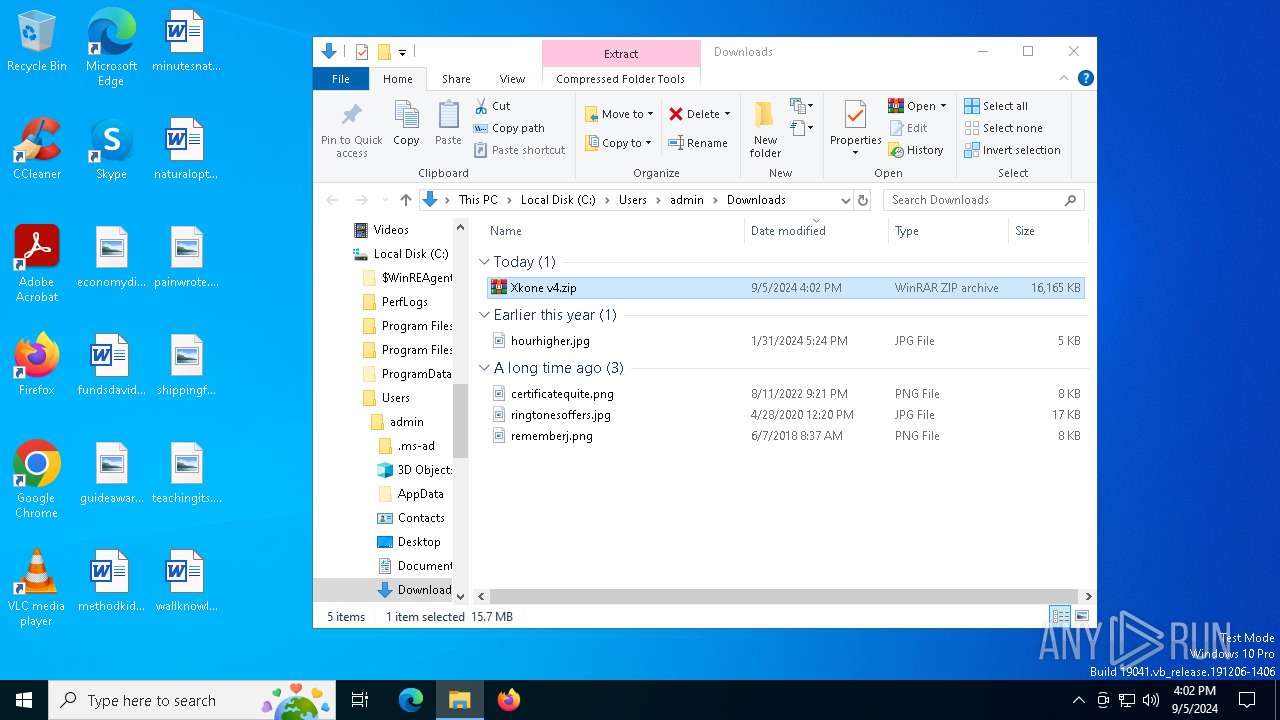
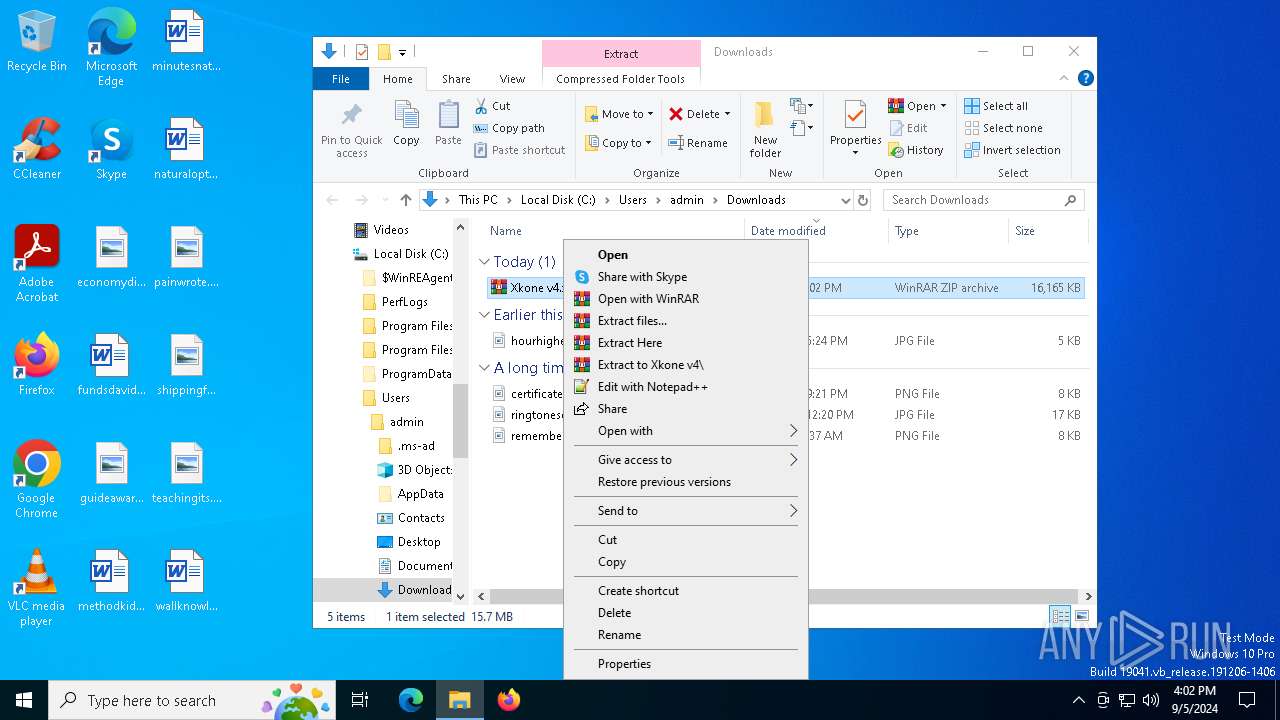
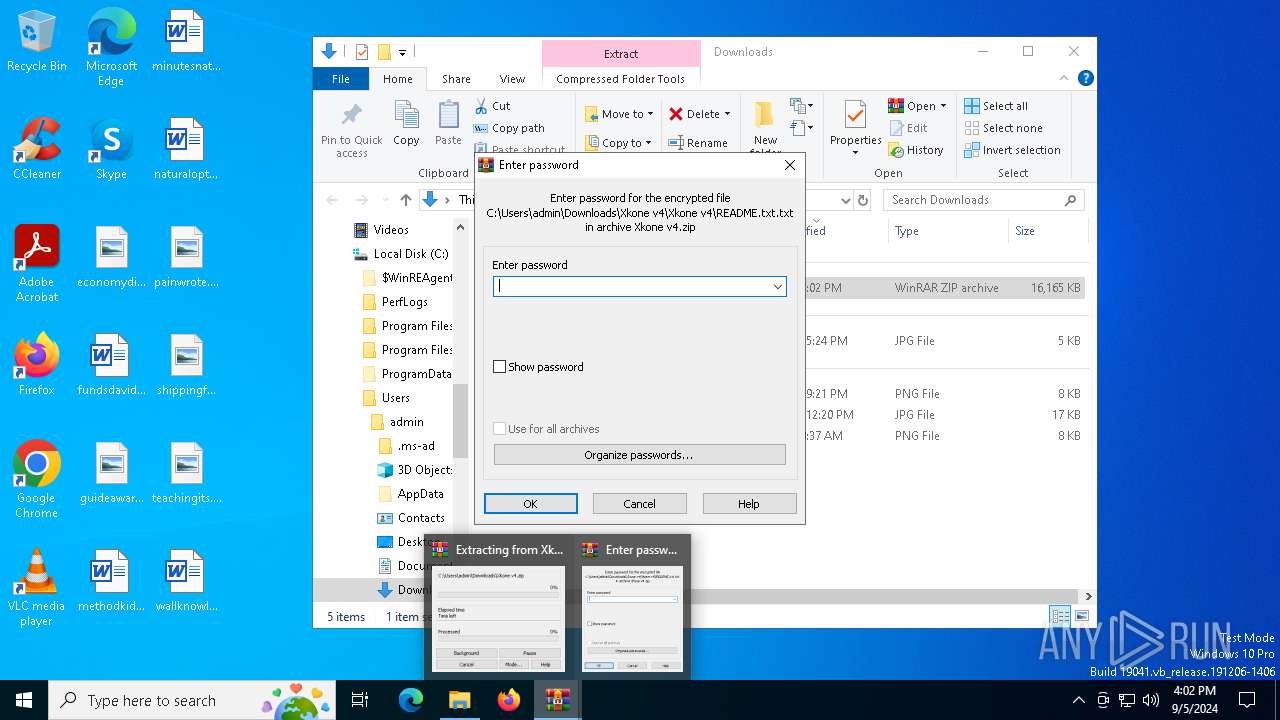
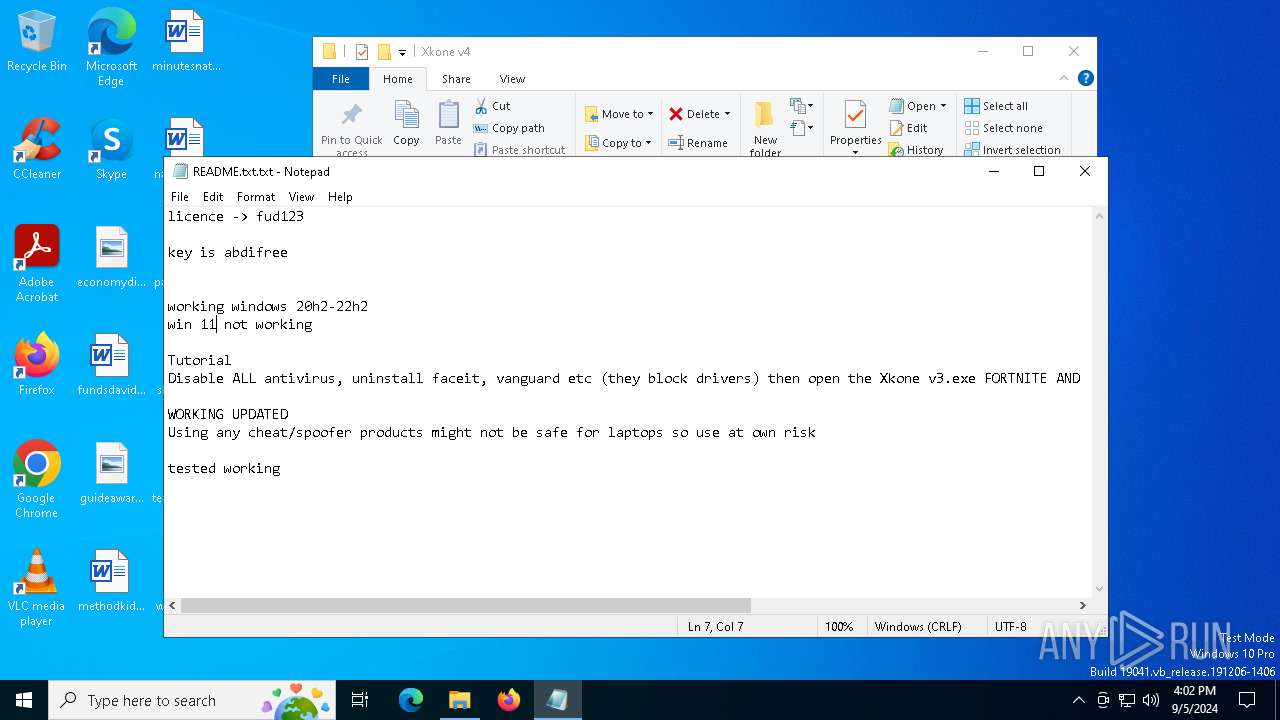
| Threats: | Blank Grabber is an infostealer written in Python. It is designed to steal a wide array of data, such as browser login credentials, crypto wallets, Telegram sessions, and Discord tokens. It is an open-source malware, with its code available on GitHub and regularly receiving updates. Blank Grabber builder’s simple interface lets threat actors even with basic skills to deploy it and conduct attacks. |
| Analysis date: | September 05, 2024, 16:01:59 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 22764EB5A4A0836A213C0C55F1B27C5C |
| SHA1: | D9191B94ED42F0C2D71F6040A3C1264EBDF1EAC3 |
| SHA256: | 6B3C92A7CC62B64C80453482C685855FEC4C9931958AD3CDCC746738681FFE38 |
| SSDEEP: | 3:N8kVGOn:2UZn |
MALICIOUS
Bypass User Account Control (Modify registry)
- reg.exe (PID: 5532)
Bypass User Account Control (ComputerDefaults)
- ComputerDefaults.exe (PID: 6836)
BlankGrabber has been detected
- Xkone v4.exe (PID: 5880)
- Xkone v4.exe (PID: 6928)
Antivirus name has been found in the command line (generic signature)
- cmd.exe (PID: 7140)
- MpCmdRun.exe (PID: 7924)
Adds path to the Windows Defender exclusion list
- Xkone v4.exe (PID: 7984)
- cmd.exe (PID: 6952)
- cmd.exe (PID: 7836)
Windows Defender preferences modified via 'Set-MpPreference'
- cmd.exe (PID: 7140)
Actions looks like stealing of personal data
- Xkone v4.exe (PID: 7984)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 6720)
Bypass execution policy to execute commands
- powershell.exe (PID: 2252)
DISCORDGRABBER has been detected (YARA)
- Xkone v4.exe (PID: 7984)
GROWTOPIA has been detected (YARA)
- Xkone v4.exe (PID: 7984)
UMBRALSTEALER has been detected (YARA)
- Xkone v4.exe (PID: 7984)
Stealers network behavior
- Xkone v4.exe (PID: 7984)
BLANKGRABBER has been detected (SURICATA)
- Xkone v4.exe (PID: 7984)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 7636)
- Xkone v4.exe (PID: 5880)
- Xkone v4.exe (PID: 6928)
The process drops C-runtime libraries
- Xkone v4.exe (PID: 6928)
- Xkone v4.exe (PID: 5880)
Application launched itself
- Xkone v4.exe (PID: 6928)
- Xkone v4.exe (PID: 5880)
Process drops python dynamic module
- Xkone v4.exe (PID: 6928)
- Xkone v4.exe (PID: 5880)
Executable content was dropped or overwritten
- Xkone v4.exe (PID: 6928)
- Xkone v4.exe (PID: 5880)
- csc.exe (PID: 6492)
- Xkone v4.exe (PID: 7984)
Starts CMD.EXE for commands execution
- Xkone v4.exe (PID: 7100)
- Xkone v4.exe (PID: 7984)
Changes default file association
- reg.exe (PID: 5532)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 1148)
- cmd.exe (PID: 2148)
- cmd.exe (PID: 5096)
Found strings related to reading or modifying Windows Defender settings
- Xkone v4.exe (PID: 7100)
- Xkone v4.exe (PID: 7984)
Uses WEVTUTIL.EXE to query events from a log or log file
- cmd.exe (PID: 6472)
- cmd.exe (PID: 4444)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7140)
- cmd.exe (PID: 6952)
- cmd.exe (PID: 7160)
- cmd.exe (PID: 7836)
- cmd.exe (PID: 6720)
- cmd.exe (PID: 6452)
- cmd.exe (PID: 6764)
- cmd.exe (PID: 4404)
- cmd.exe (PID: 6776)
Script disables Windows Defender's real-time protection
- cmd.exe (PID: 7140)
Script disables Windows Defender's IPS
- cmd.exe (PID: 7140)
Detected use of alternative data streams (AltDS)
- powershell.exe (PID: 7752)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 7836)
- cmd.exe (PID: 6952)
Get information on the list of running processes
- cmd.exe (PID: 6956)
- Xkone v4.exe (PID: 7984)
- cmd.exe (PID: 7008)
- cmd.exe (PID: 2228)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 6192)
- cmd.exe (PID: 6312)
The executable file from the user directory is run by the CMD process
- bound.exe (PID: 7440)
- rar.exe (PID: 1140)
Base64-obfuscated command line is found
- cmd.exe (PID: 6720)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 6720)
BASE64 encoded PowerShell command has been detected
- cmd.exe (PID: 6720)
Accesses antivirus product name via WMI (SCRIPT)
- WMIC.exe (PID: 7484)
Uses SYSTEMINFO.EXE to read the environment
- cmd.exe (PID: 3268)
Starts application with an unusual extension
- cmd.exe (PID: 304)
- cmd.exe (PID: 4824)
- cmd.exe (PID: 6764)
- cmd.exe (PID: 8132)
- cmd.exe (PID: 7004)
- cmd.exe (PID: 2368)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 4316)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 7116)
- cmd.exe (PID: 608)
- cmd.exe (PID: 7068)
- cmd.exe (PID: 7836)
- cmd.exe (PID: 7856)
- cmd.exe (PID: 6304)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 7140)
Accesses operating system name via WMI (SCRIPT)
- WMIC.exe (PID: 7976)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 2648)
Uses WMIC.EXE to obtain a list of video controllers
- cmd.exe (PID: 3708)
Accesses product unique identifier via WMI (SCRIPT)
- WMIC.exe (PID: 7348)
Checks for external IP
- svchost.exe (PID: 2256)
- Xkone v4.exe (PID: 7984)
Accesses video controller name via WMI (SCRIPT)
- WMIC.exe (PID: 936)
INFO
Reads the computer name
- identity_helper.exe (PID: 6980)
- identity_helper.exe (PID: 1780)
- Xkone v4.exe (PID: 6928)
- Xkone v4.exe (PID: 5880)
- Xkone v4.exe (PID: 7984)
- MpCmdRun.exe (PID: 7924)
Application launched itself
- msedge.exe (PID: 7136)
- msedge.exe (PID: 7964)
Reads Environment values
- identity_helper.exe (PID: 6980)
- identity_helper.exe (PID: 1780)
Checks supported languages
- identity_helper.exe (PID: 6980)
- identity_helper.exe (PID: 1780)
- Xkone v4.exe (PID: 6928)
- Xkone v4.exe (PID: 7100)
- Xkone v4.exe (PID: 5880)
- Xkone v4.exe (PID: 7984)
- tree.com (PID: 7192)
- tree.com (PID: 6932)
- tree.com (PID: 6928)
- tree.com (PID: 7980)
- tree.com (PID: 4688)
- tree.com (PID: 1608)
- csc.exe (PID: 6492)
- MpCmdRun.exe (PID: 7924)
- rar.exe (PID: 1140)
- cvtres.exe (PID: 5000)
The process uses the downloaded file
- msedge.exe (PID: 7524)
- WinRAR.exe (PID: 7636)
- cmd.exe (PID: 232)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7636)
Manual execution by a user
- WinRAR.exe (PID: 7636)
- notepad.exe (PID: 6108)
- Xkone v4.exe (PID: 6928)
Reads security settings of Internet Explorer
- notepad.exe (PID: 6108)
- ComputerDefaults.exe (PID: 6836)
- WMIC.exe (PID: 7484)
- WMIC.exe (PID: 7976)
- WMIC.exe (PID: 8136)
- WMIC.exe (PID: 7348)
- WMIC.exe (PID: 936)
Create files in a temporary directory
- Xkone v4.exe (PID: 6928)
- Xkone v4.exe (PID: 7100)
- Xkone v4.exe (PID: 5880)
- Xkone v4.exe (PID: 7984)
- csc.exe (PID: 6492)
- MpCmdRun.exe (PID: 7924)
- cvtres.exe (PID: 5000)
- rar.exe (PID: 1140)
The Powershell gets current clipboard
- powershell.exe (PID: 6548)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7748)
- powershell.exe (PID: 7840)
- powershell.exe (PID: 7752)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7748)
- powershell.exe (PID: 7840)
- powershell.exe (PID: 7752)
- powershell.exe (PID: 7880)
- powershell.exe (PID: 3036)
Reads the machine GUID from the registry
- csc.exe (PID: 6492)
- rar.exe (PID: 1140)
Displays MAC addresses of computer network adapters
- getmac.exe (PID: 6428)
PyInstaller has been detected (YARA)
- Xkone v4.exe (PID: 5880)
- Xkone v4.exe (PID: 7984)
Found Base64 encoded reflection usage via PowerShell (YARA)
- Xkone v4.exe (PID: 7984)
UPX packer has been detected
- Xkone v4.exe (PID: 7984)
Attempting to use instant messaging service
- svchost.exe (PID: 2256)
- Xkone v4.exe (PID: 7984)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
323
Monitored processes
189
Malicious processes
7
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 232 | C:\WINDOWS\system32\cmd.exe /c "computerdefaults --nouacbypass" | C:\Windows\System32\cmd.exe | — | Xkone v4.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 304 | C:\WINDOWS\system32\cmd.exe /c "tree /A /F" | C:\Windows\System32\cmd.exe | — | Xkone v4.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 508 | wevtutil qe "Microsoft-Windows-Windows Defender/Operational" /f:text | C:\Windows\System32\wevtutil.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Eventing Command Line Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 568 | tasklist /FO LIST | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 608 | C:\WINDOWS\system32\cmd.exe /c "taskkill /F /PID 8188" | C:\Windows\System32\cmd.exe | — | Xkone v4.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 936 | wmic path win32_VideoController get name | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1076 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5868 --field-trial-handle=2304,i,12871211788356512534,664916412254013952,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1128 | taskkill /F /PID 6576 | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1140 | C:\Users\admin\AppData\Local\Temp\_MEI58802\rar.exe a -r -hp"123" "C:\Users\admin\AppData\Local\Temp\lmkOF.zip" * | C:\Users\admin\AppData\Local\Temp\_MEI58802\rar.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1148 | C:\WINDOWS\system32\cmd.exe /c "reg add hkcu\Software\Classes\ms-settings\shell\open\command /d "C:\Users\admin\Downloads\Xkone v4\Xkone v4\Xkone v4.exe" /f" | C:\Windows\System32\cmd.exe | — | Xkone v4.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
67 892
Read events
67 808
Write events
80
Delete events
4
Modification events
| (PID) Process: | (7136) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (7136) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (7136) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (7136) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (7136) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: BCCCF5B1F77F2F00 | |||
| (PID) Process: | (7136) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 5D2500B2F77F2F00 | |||
| (PID) Process: | (7136) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\459388 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {154018A3-AF06-4F0A-84D1-B4A2E767D617} | |||
| (PID) Process: | (7136) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\459388 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {C3CC2B91-FEA2-41CA-8761-B4000412AFED} | |||
| (PID) Process: | (7136) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\459388 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {7783725C-2EE3-4799-BDF2-C313E1D6E013} | |||
| (PID) Process: | (7136) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: A1FE35B2F77F2F00 | |||
Executable files
118
Suspicious files
128
Text files
181
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7136 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF129f74.TMP | — | |
MD5:— | SHA256:— | |||
| 7136 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7136 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF129f55.TMP | — | |
MD5:— | SHA256:— | |||
| 7136 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7136 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF129fa3.TMP | — | |
MD5:— | SHA256:— | |||
| 7136 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7136 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF129fa3.TMP | — | |
MD5:— | SHA256:— | |||
| 7136 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF129fc2.TMP | — | |
MD5:— | SHA256:— | |||
| 7136 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7136 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
83
DNS requests
66
Threats
24
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7700 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7984 | Xkone v4.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json/?fields=225545 | unknown | — | — | shared |
7700 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6056 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3296 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6056 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1828 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5712 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7136 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5712 | msedge.exe | 67.199.248.10:443 | bit.ly | GOOGLE-CLOUD-PLATFORM | US | shared |
5712 | msedge.exe | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5712 | msedge.exe | 13.107.6.158:443 | business.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5712 | msedge.exe | 13.107.246.60:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
bit.ly |
| shared |
edge.microsoft.com |
| whitelisted |
api.edgeoffer.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
mega.nz |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5712 | msedge.exe | Misc activity | ET INFO File Sharing Domain Observed in TLS SNI (mega .nz) |
5712 | msedge.exe | Misc activity | ET INFO File Sharing Related Domain in DNS Lookup (mega .nz) |
5712 | msedge.exe | Misc activity | ET INFO File Sharing Related Domain in DNS Lookup (mega .nz) |
5712 | msedge.exe | Misc activity | ET INFO Observed DNS Query to Filesharing Service (mega .co .nz) |
5712 | msedge.exe | Misc activity | ET INFO Observed DNS Query to Filesharing Service (mega .co .nz) |
5712 | msedge.exe | Misc activity | ET INFO File Sharing Domain Observed in TLS SNI (mega .nz) |
5712 | msedge.exe | Misc activity | ET INFO File Sharing Related Domain in DNS Lookup (mega .nz) |
5712 | msedge.exe | Misc activity | ET INFO File Sharing Related Domain in DNS Lookup (mega .nz) |
5712 | msedge.exe | Misc activity | ET INFO File Sharing Domain Observed in TLS SNI (mega .nz) |
5712 | msedge.exe | Misc activity | ET INFO File Sharing Domain Observed in TLS SNI (mega .nz) |