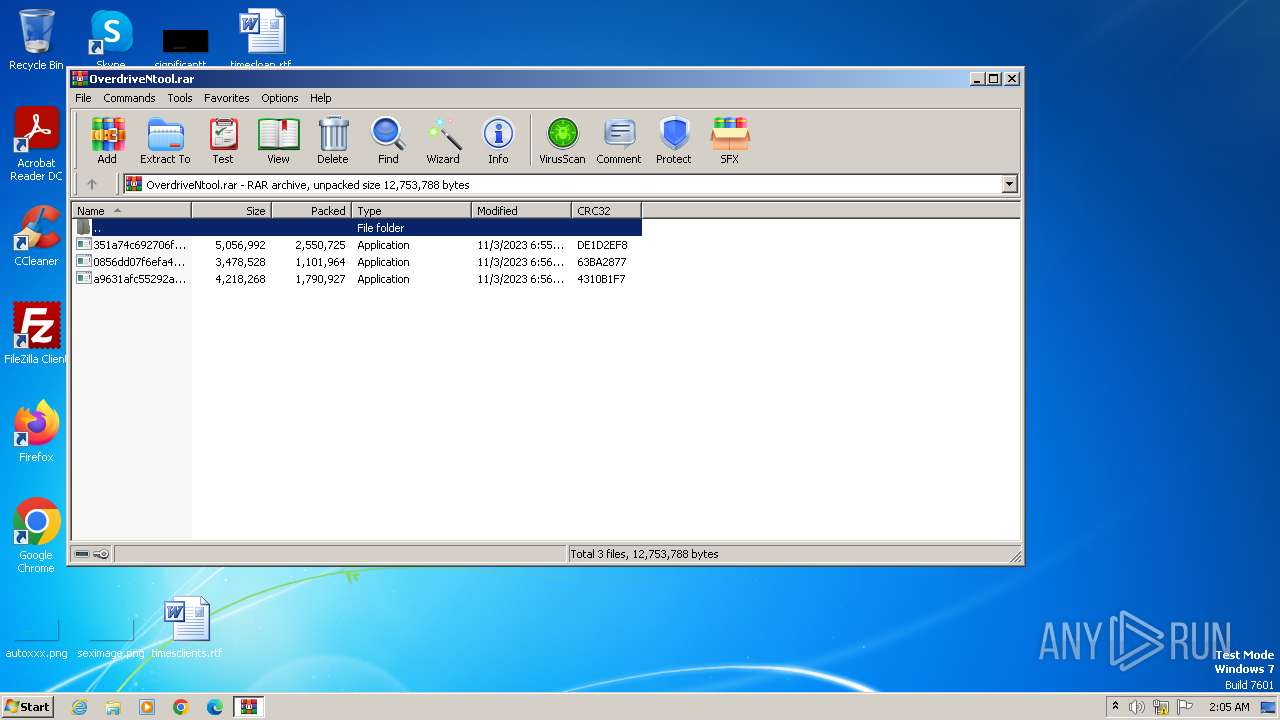
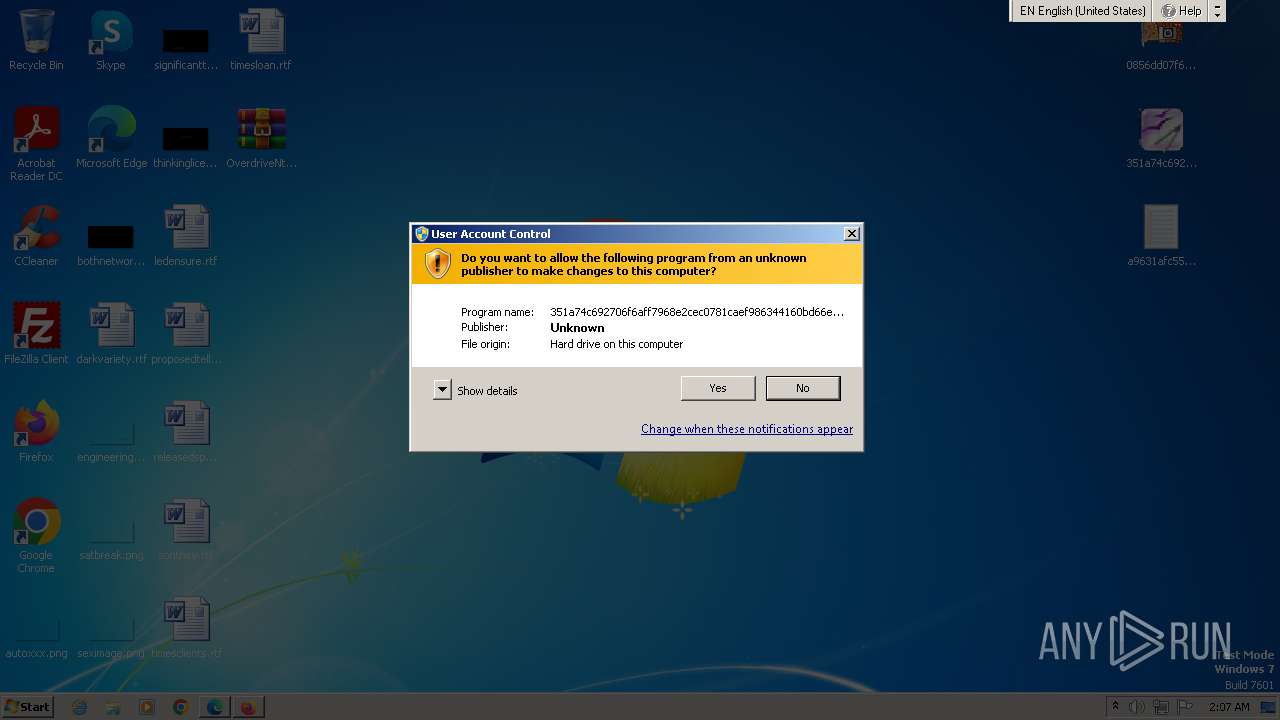
| File name: | OverdriveNtool.rar |
| Full analysis: | https://app.any.run/tasks/5ceb63e3-c984-47f8-b0e5-46b0ec526657 |
| Verdict: | Malicious activity |
| Threats: | Quasar is a very popular RAT in the world thanks to its code being available in open-source. This malware can be used to control the victim’s computer remotely. |
| Analysis date: | November 03, 2023, 02:05:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 79A849A75BD349C6BACBB5D8437D2B54 |
| SHA1: | 376DDF81B8A00F1B415F0F94D5934C1C8265E945 |
| SHA256: | 6ACDB63E2320DD3FE7E9254562157AD90D61FBF872707BDC84C66675C71FA7DE |
| SSDEEP: | 98304:EMmL9Ta3W9Zne+y1UpuW/jsFVVuRLlNHo7vLTnLCtBng0gRzkMTxIIToY1I+X619:uRKetfyyn5q8kW6lpCX |
MALICIOUS
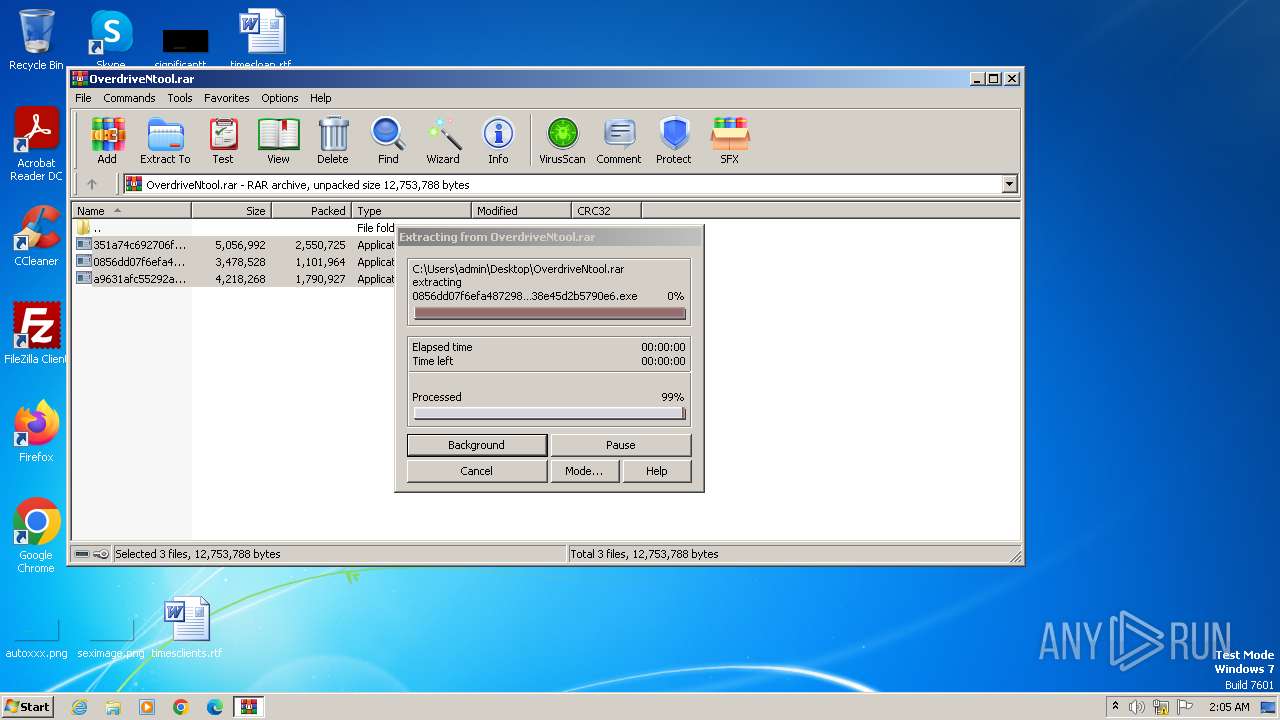
Drops the executable file immediately after the start
- cmd.exe (PID: 4148)
- a9631afc55292a5c013799dd1fdfa4eaaf1ef7faa97174cc3c3fdc85cf71f1e6.exe (PID: 4024)
- 351a74c692706f6aff7968e2cec0781caef986344160bd66e5d19852a2e908df.exe (PID: 4352)
- cmd.exe (PID: 4516)
- Beats.pif (PID: 4540)
- Full.pif (PID: 4172)
Create files in the Startup directory
- cmd.exe (PID: 4572)
REDLINE has been detected (SURICATA)
- jsc.exe (PID: 4864)
Connects to the CnC server
- jsc.exe (PID: 4864)
QUASAR has been detected (YARA)
- jsc.exe (PID: 4856)
Steals credentials from Web Browsers
- jsc.exe (PID: 4864)
Actions looks like stealing of personal data
- jsc.exe (PID: 4864)
SUSPICIOUS
Application launched itself
- cmd.exe (PID: 948)
- cmd.exe (PID: 968)
- cmd.exe (PID: 4396)
- cmd.exe (PID: 4428)
Drops the AutoIt3 executable file
- cmd.exe (PID: 4148)
- cmd.exe (PID: 4516)
- Beats.pif (PID: 4540)
Starts application with an unusual extension
- cmd.exe (PID: 948)
- cmd.exe (PID: 4428)
- cmd.exe (PID: 4984)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 948)
- cmd.exe (PID: 4428)
- cmd.exe (PID: 4984)
Starts CMD.EXE for commands execution
- a9631afc55292a5c013799dd1fdfa4eaaf1ef7faa97174cc3c3fdc85cf71f1e6.exe (PID: 4024)
- cmd.exe (PID: 968)
- cmd.exe (PID: 948)
- 351a74c692706f6aff7968e2cec0781caef986344160bd66e5d19852a2e908df.exe (PID: 4352)
- cmd.exe (PID: 4396)
- cmd.exe (PID: 4428)
- jsc.exe (PID: 4856)
Get information on the list of running processes
- cmd.exe (PID: 948)
- cmd.exe (PID: 4428)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 948)
- cmd.exe (PID: 4428)
Process drops legitimate windows executable
- Beats.pif (PID: 4540)
- Full.pif (PID: 4172)
Reads the Internet Settings
- jsc.exe (PID: 4856)
- jsc.exe (PID: 5224)
Connects to unusual port
- jsc.exe (PID: 4864)
- jsc.exe (PID: 4856)
Executing commands from a ".bat" file
- jsc.exe (PID: 4856)
Checks for external IP
- jsc.exe (PID: 4856)
Searches for installed software
- jsc.exe (PID: 4864)
Reads browser cookies
- jsc.exe (PID: 4864)
INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3448)
- firefox.exe (PID: 3080)
Checks supported languages
- wmpnscfg.exe (PID: 600)
- Full.pif (PID: 4172)
- a9631afc55292a5c013799dd1fdfa4eaaf1ef7faa97174cc3c3fdc85cf71f1e6.exe (PID: 4024)
- 0856dd07f6efa48729888ba519e2a3fd4eaa37de3463eb7bc838e45d2b5790e6.exe (PID: 4224)
- 351a74c692706f6aff7968e2cec0781caef986344160bd66e5d19852a2e908df.exe (PID: 4352)
- Beats.pif (PID: 4540)
- jsc.exe (PID: 4864)
- chcp.com (PID: 5008)
- jsc.exe (PID: 4856)
- jsc.exe (PID: 5224)
Reads the computer name
- wmpnscfg.exe (PID: 600)
- 0856dd07f6efa48729888ba519e2a3fd4eaa37de3463eb7bc838e45d2b5790e6.exe (PID: 4224)
- Full.pif (PID: 4172)
- Beats.pif (PID: 4540)
- jsc.exe (PID: 4864)
- jsc.exe (PID: 4856)
- jsc.exe (PID: 5224)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 600)
- jsc.exe (PID: 4856)
- jsc.exe (PID: 4864)
- jsc.exe (PID: 5224)
Manual execution by a user
- msedge.exe (PID: 3576)
- wmpnscfg.exe (PID: 600)
- firefox.exe (PID: 3184)
- a9631afc55292a5c013799dd1fdfa4eaaf1ef7faa97174cc3c3fdc85cf71f1e6.exe (PID: 4024)
- 351a74c692706f6aff7968e2cec0781caef986344160bd66e5d19852a2e908df.exe (PID: 4352)
- 0856dd07f6efa48729888ba519e2a3fd4eaa37de3463eb7bc838e45d2b5790e6.exe (PID: 4224)
- cmd.exe (PID: 4572)
- jsc.exe (PID: 4856)
- jsc.exe (PID: 4864)
Application launched itself
- firefox.exe (PID: 3184)
- msedge.exe (PID: 3576)
- firefox.exe (PID: 3080)
The executable file from the user directory is run by the CMD process
- Full.pif (PID: 4172)
- Beats.pif (PID: 4540)
- jsc.exe (PID: 5224)
Reads mouse settings
- Full.pif (PID: 4172)
- Beats.pif (PID: 4540)
Create files in a temporary directory
- a9631afc55292a5c013799dd1fdfa4eaaf1ef7faa97174cc3c3fdc85cf71f1e6.exe (PID: 4024)
- 351a74c692706f6aff7968e2cec0781caef986344160bd66e5d19852a2e908df.exe (PID: 4352)
- Beats.pif (PID: 4540)
- Full.pif (PID: 4172)
- jsc.exe (PID: 4856)
Creates files or folders in the user directory
- Beats.pif (PID: 4540)
Reads Environment values
- jsc.exe (PID: 4856)
- jsc.exe (PID: 4864)
Reads product name
- jsc.exe (PID: 4864)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Quasar
(PID) Process(4856) jsc.exe
Version1.4.0.0
C2 (2)135.181.11.41:2424
Sub_DirSubDir
Install_Namecsrss.exe
MutexQpjXdwKWwAWi8fR2WYfnvnfjnvjbgh
StartupNET framework
TagOffice
LogDirLogs
Signature
Certificate
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
121
Monitored processes
69
Malicious processes
9
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 276 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=4940 --field-trial-handle=1380,i,16149519403048093654,4725570579187075524,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 536 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=1128 --field-trial-handle=1380,i,16149519403048093654,4725570579187075524,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 600 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 948 | cmd | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 968 | cmd /k cmd < Frequent & exit | C:\Windows\System32\cmd.exe | — | a9631afc55292a5c013799dd1fdfa4eaaf1ef7faa97174cc3c3fdc85cf71f1e6.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1348 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=9 --mojo-platform-channel-handle=4012 --field-trial-handle=1380,i,16149519403048093654,4725570579187075524,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1432 | findstr /I "avastui.exe avgui.exe nswscsvc.exe sophoshealth.exe" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1452 | tasklist | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1560 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=2460 --field-trial-handle=1380,i,16149519403048093654,4725570579187075524,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1584 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3080.6.1810596506\719489244" -childID 5 -isForBrowser -prefsHandle 3996 -prefMapHandle 3988 -prefsLen 29209 -prefMapSize 244195 -jsInitHandle 876 -jsInitLen 240908 -parentBuildID 20230710165010 -appDir "C:\Program Files\Mozilla Firefox\browser" - {b713b1ed-41d1-43b5-8fee-264e25e21b55} 3080 "\\.\pipe\gecko-crash-server-pipe.3080" 4008 17908560 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
Total events
24 312
Read events
24 214
Write events
92
Delete events
6
Modification events
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
78
Suspicious files
1 575
Text files
118
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3576 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF1699d3.TMP | — | |
MD5:— | SHA256:— | |||
| 3576 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3576 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF1699f3.TMP | — | |
MD5:— | SHA256:— | |||
| 3576 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3576 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF169a02.TMP | — | |
MD5:— | SHA256:— | |||
| 3576 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF169a41.TMP | — | |
MD5:— | SHA256:— | |||
| 3576 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3448.12991\a9631afc55292a5c013799dd1fdfa4eaaf1ef7faa97174cc3c3fdc85cf71f1e6.exe | executable | |
MD5:08194A6558D79AC3A4CAD8D84B68EA3B | SHA256:A9631AFC55292A5C013799DD1FDFA4EAAF1EF7FAA97174CC3C3FDC85CF71F1E6 | |||
| 3576 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\8e6d9274-4365-4ff2-afea-f57a0f7747e1.tmp | binary | |
MD5:5058F1AF8388633F609CADB75A75DC9D | SHA256:— | |||
| 3576 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Last Version | text | |
MD5:61FE7896F9494DCDF53480A325F4FB85 | SHA256:ACFD3CD36E0DFCF1DCB67C7F31F2A5B9BA0815528A0C604D4330DFAA9E683E51 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
35
TCP/UDP connections
135
DNS requests
266
Threats
28
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3928 | msedge.exe | GET | 301 | 142.250.185.229:80 | http://gmail.com/ | unknown | html | 230 b | unknown |
3080 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | text | 90 b | unknown |
3080 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | text | 8 b | unknown |
3080 | firefox.exe | POST | 200 | 184.24.77.54:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
3080 | firefox.exe | POST | 200 | 142.250.186.67:80 | http://ocsp.pki.goog/gts1c3 | unknown | binary | 472 b | unknown |
3080 | firefox.exe | POST | 200 | 184.24.77.54:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
3080 | firefox.exe | POST | 200 | 184.24.77.54:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
3080 | firefox.exe | POST | 200 | 142.250.186.67:80 | http://ocsp.pki.goog/gts1c3 | unknown | binary | 472 b | unknown |
3080 | firefox.exe | POST | 200 | 184.24.77.54:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
3080 | firefox.exe | POST | 200 | 184.24.77.54:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3928 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3576 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3928 | msedge.exe | 204.79.197.203:443 | ntp.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3928 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3928 | msedge.exe | 23.53.42.121:443 | assets.msn.com | Akamai International B.V. | DE | unknown |
3928 | msedge.exe | 2.21.20.136:443 | img-s-msn-com.akamaized.net | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.edge.skype.com |
| whitelisted |
ntp.msn.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
assets.msn.com |
| whitelisted |
img-s-msn-com.akamaized.net |
| whitelisted |
sb.scorecardresearch.com |
| shared |
th.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
c.msn.com |
| whitelisted |
c.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4864 | jsc.exe | Potentially Bad Traffic | ET INFO Microsoft net.tcp Connection Initialization Activity |
4864 | jsc.exe | A Network Trojan was detected | ET MALWARE Redline Stealer TCP CnC Activity |
4864 | jsc.exe | A Network Trojan was detected | ET MALWARE [ANY.RUN] RedLine Stealer Related (MC-NMF Authorization) |
4864 | jsc.exe | A Network Trojan was detected | ET MALWARE Redline Stealer TCP CnC - Id1Response |
4856 | jsc.exe | A Network Trojan was detected | ET MALWARE Common RAT Connectivity Check Observed |
4856 | jsc.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup ip-api.com |
4856 | jsc.exe | Potential Corporate Privacy Violation | AV POLICY Internal Host Retrieving External IP Address (ip-api. com) |
4864 | jsc.exe | A Network Trojan was detected | ET MALWARE Redline Stealer TCP CnC Activity |
4864 | jsc.exe | A Network Trojan was detected | ET MALWARE Redline Stealer TCP CnC Activity |
4864 | jsc.exe | A Network Trojan was detected | ET MALWARE Redline Stealer Activity (Response) |