| URL: | https://github.com/Da2dalus/The-MALWARE-Repo |
| Full analysis: | https://app.any.run/tasks/a0d5ed2a-8d07-4809-a859-d26493d84716 |
| Verdict: | Malicious activity |
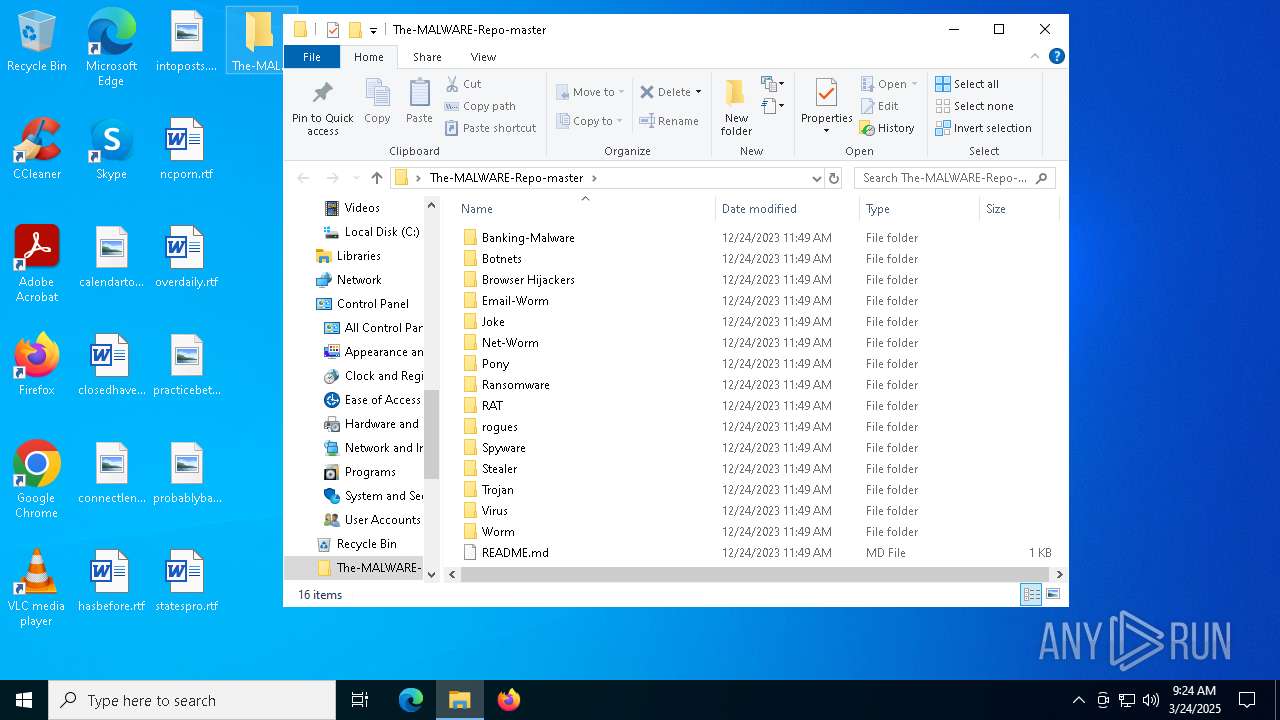
| Threats: | Danabot is an advanced banking Trojan malware that was designed to steal financial information from victims. Out of the Trojans in the wild, this is one of the most advanced thanks to the modular design and a complex delivery method. |
| Analysis date: | March 24, 2025, 09:22:54 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 95DE222D86979D6785AD30792191C545 |
| SHA1: | 0328EC532FE1B34F32B83E99013C67D2B17579A1 |
| SHA256: | 6A8070F67E43F623ABA9B346120783FD9371ADBC25D2852C02BB12D9BBC6C58A |
| SSDEEP: | 3:N8tEdJejSOpykOK:2ubYSOc0 |
MALICIOUS
DANABOT has been found (auto)
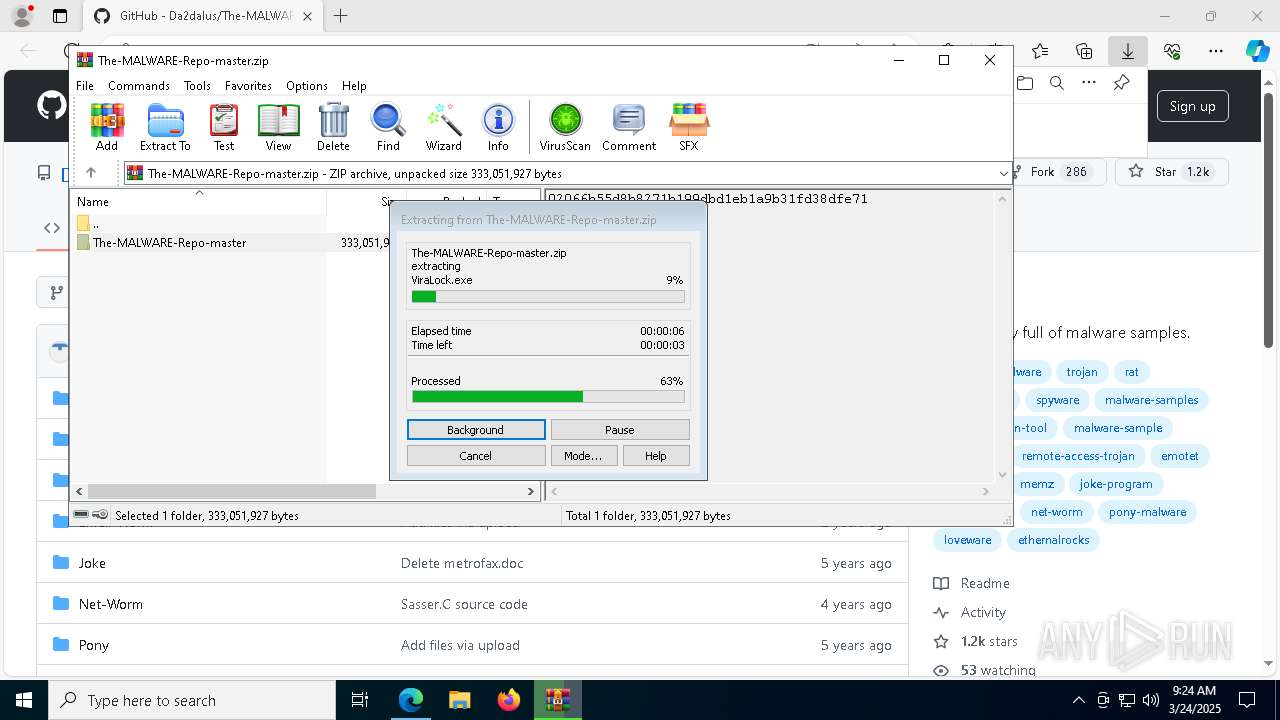
- WinRAR.exe (PID: 1228)
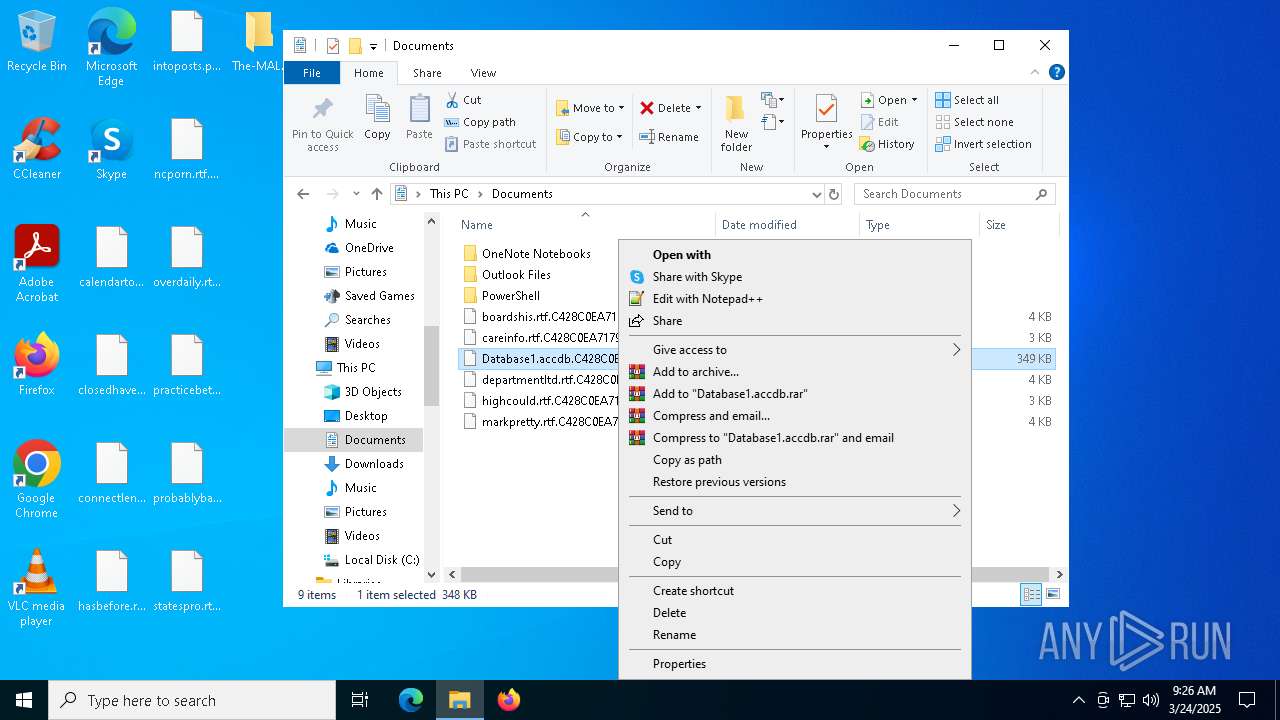
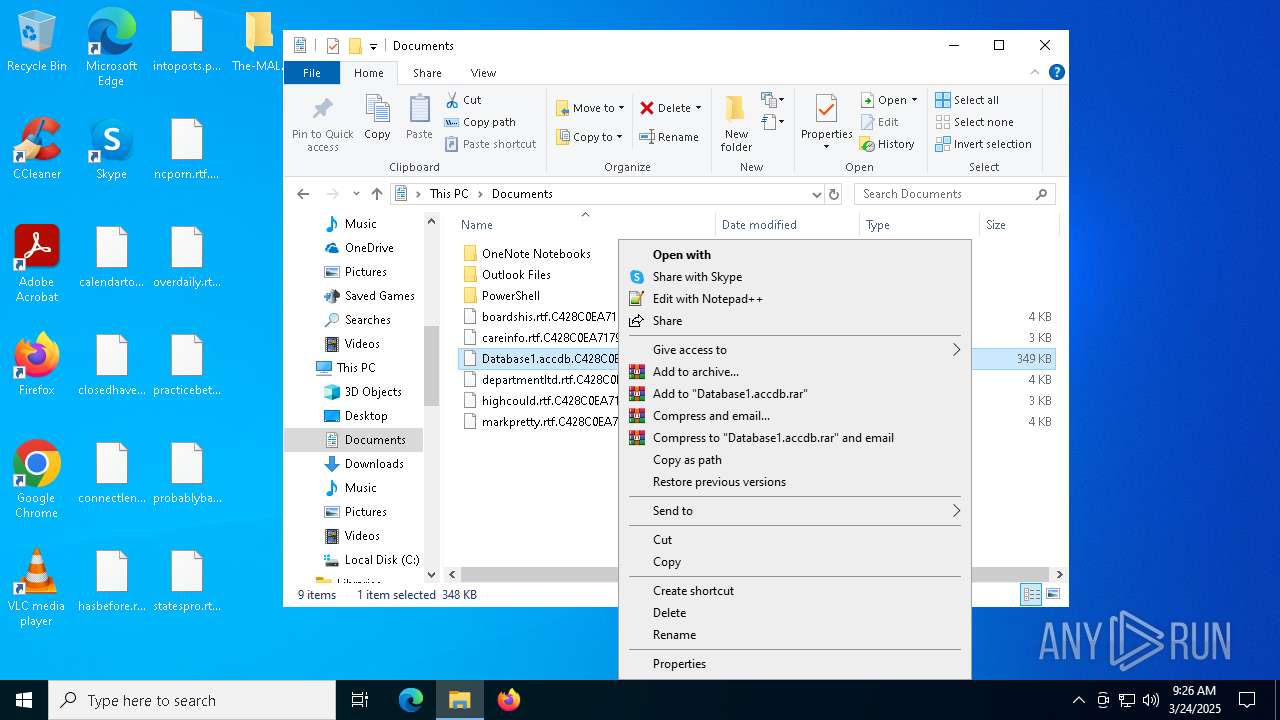
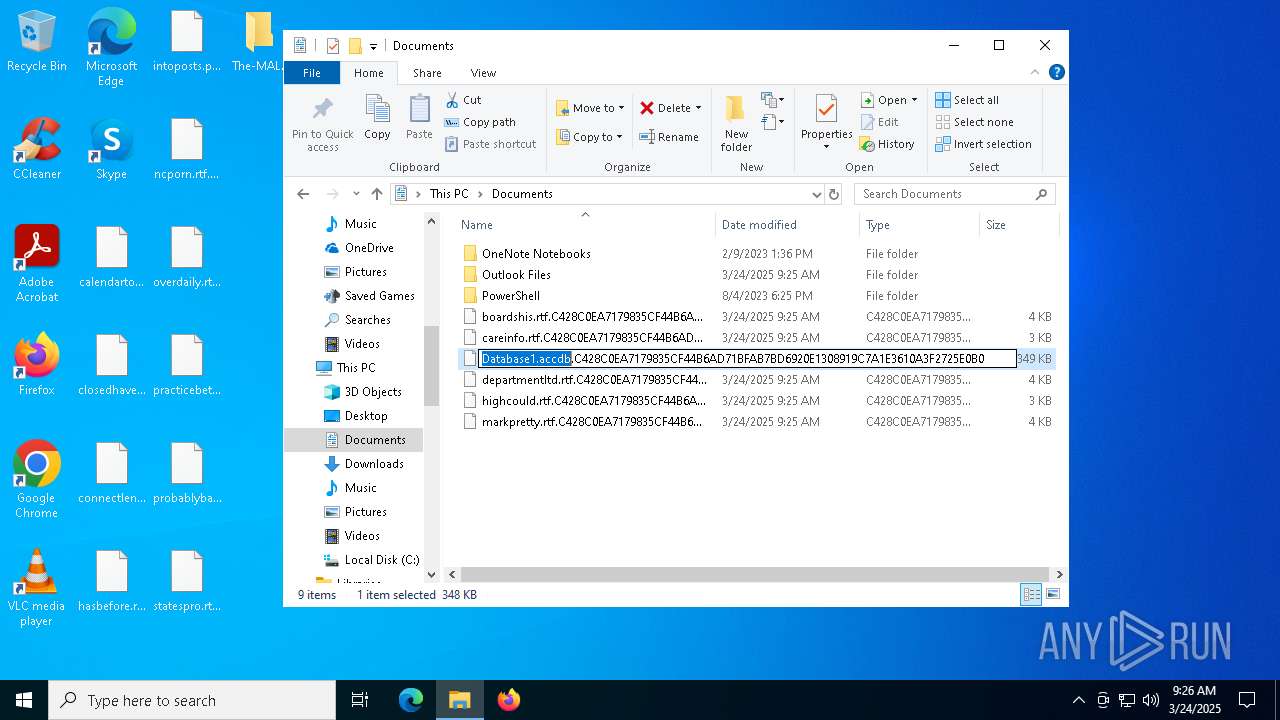
Drops known malicious document
- WinRAR.exe (PID: 1228)
- WinRAR.exe (PID: 1228)
Drops known malicious image
- WinRAR.exe (PID: 1228)
DESKTOPBOOM has been detected
- WinRAR.exe (PID: 1228)
DARKCOMET has been found (auto)
- WinRAR.exe (PID: 1228)
Actions looks like stealing of personal data
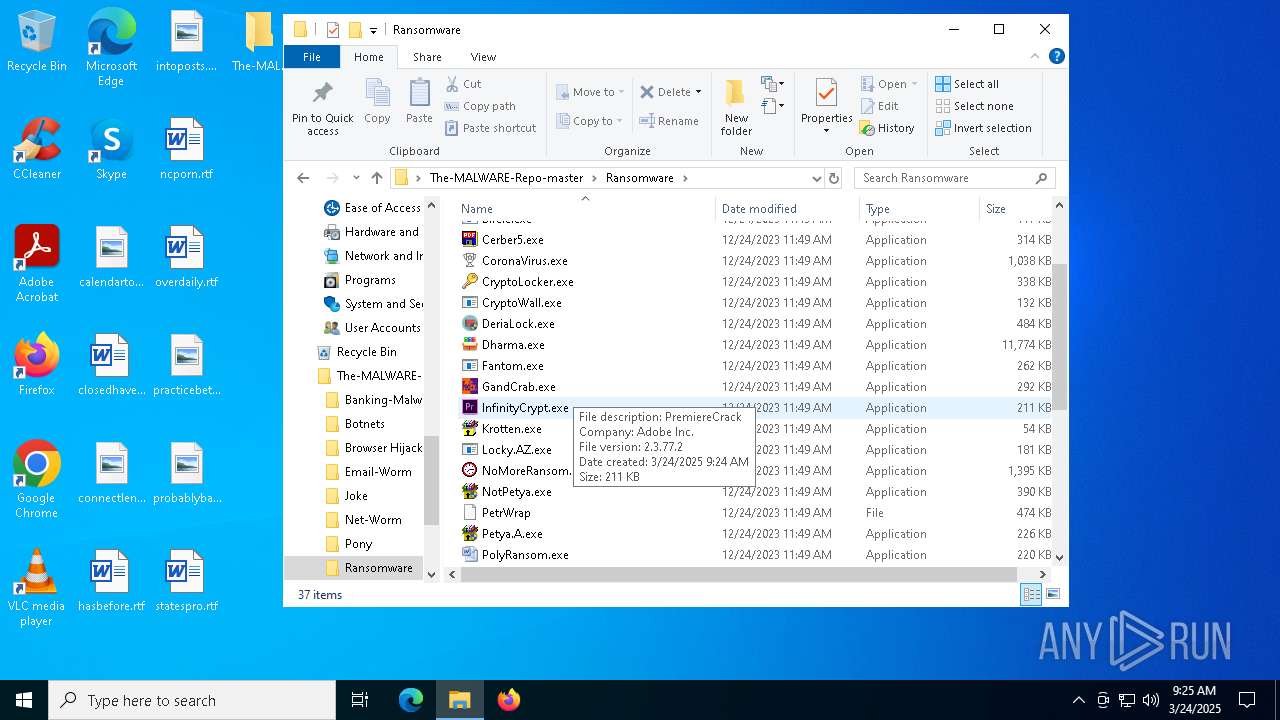
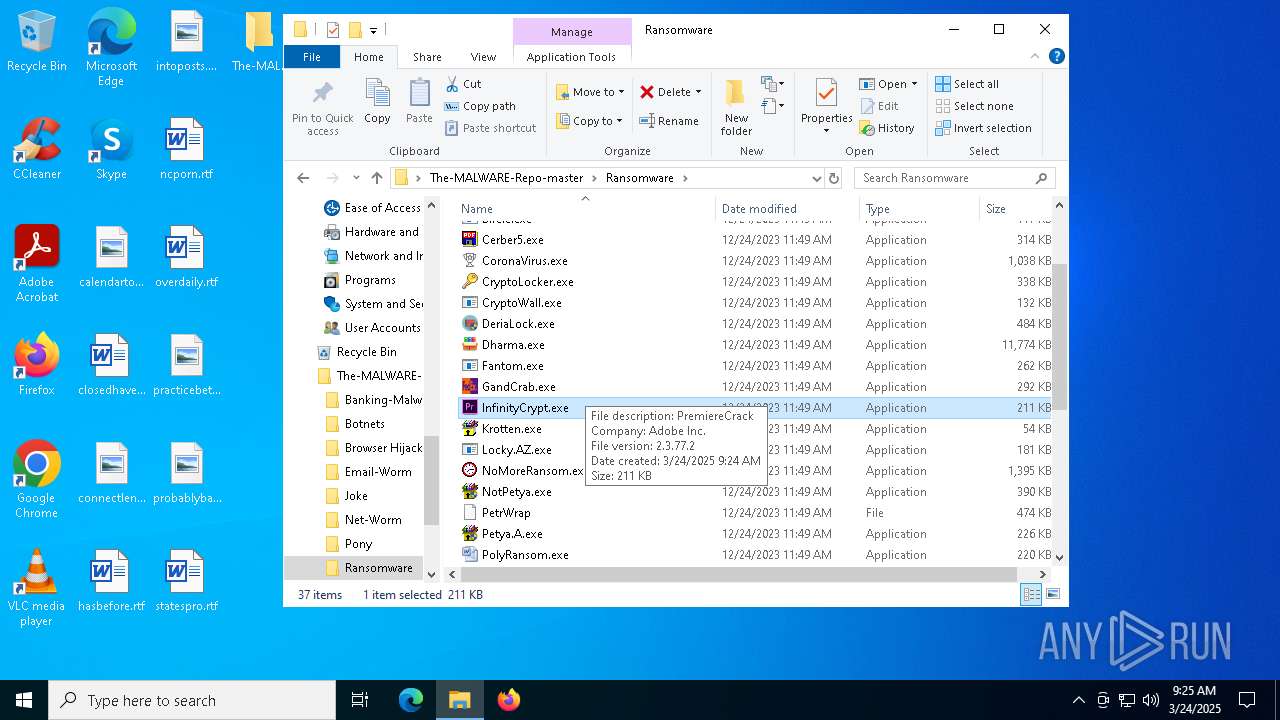
- InfinityCrypt.exe (PID: 2504)
Connects to the CnC server
- InfinityCrypt.exe (PID: 2504)
Scans artifacts that could help determine the target
- MSACCESS.EXE (PID: 7600)
SUSPICIOUS
Suspicious files were dropped or overwritten
- WinRAR.exe (PID: 1228)
Process drops legitimate windows executable
- WinRAR.exe (PID: 1228)
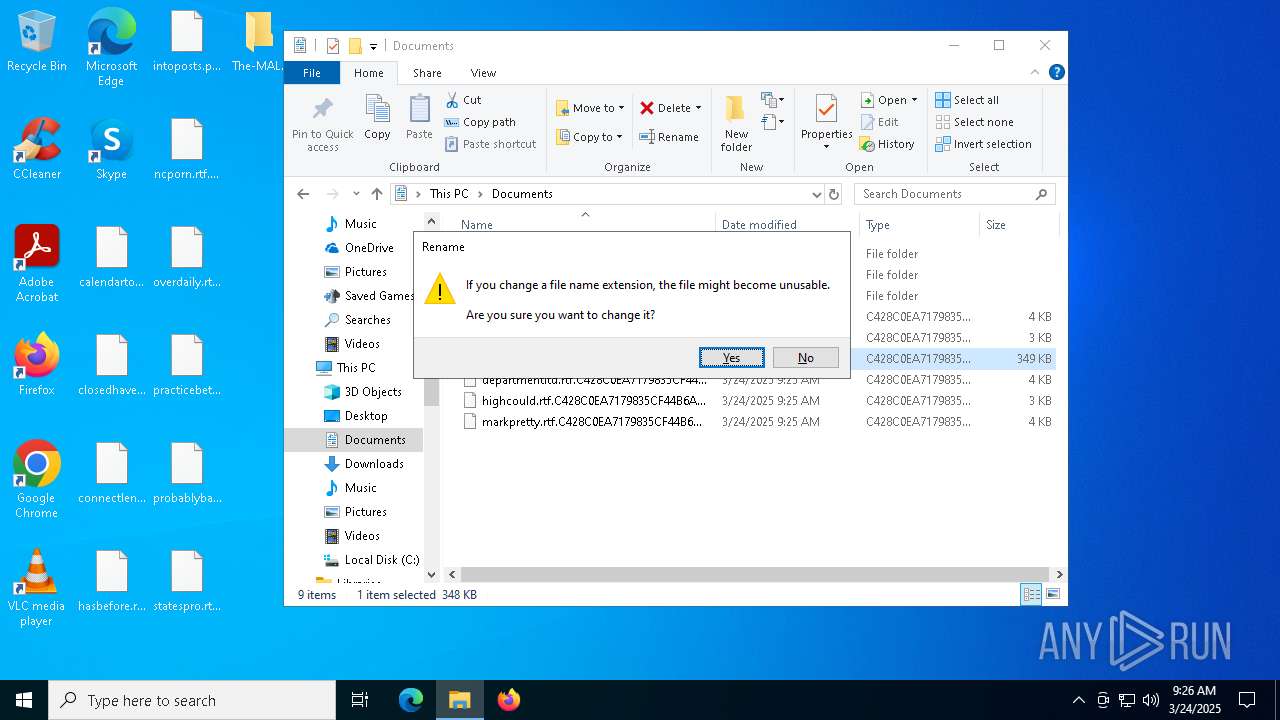
The process creates files with name similar to system file names
- WinRAR.exe (PID: 1228)
Contacting a server suspected of hosting an CnC
- InfinityCrypt.exe (PID: 2504)
Reads security settings of Internet Explorer
- MSACCESS.EXE (PID: 7600)
INFO
Checks supported languages
- identity_helper.exe (PID: 7260)
- ShellExperienceHost.exe (PID: 5588)
- identity_helper.exe (PID: 8252)
- InfinityCrypt.exe (PID: 2504)
- MSACCESS.EXE (PID: 7600)
- SecHealthUI.exe (PID: 7212)
Application launched itself
- msedge.exe (PID: 7360)
- msedge.exe (PID: 1388)
Reads the computer name
- identity_helper.exe (PID: 7260)
- ShellExperienceHost.exe (PID: 5588)
- InfinityCrypt.exe (PID: 2504)
- MSACCESS.EXE (PID: 7600)
- SecHealthUI.exe (PID: 7212)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 8408)
- BackgroundTransferHost.exe (PID: 660)
- BackgroundTransferHost.exe (PID: 8908)
- BackgroundTransferHost.exe (PID: 960)
- BackgroundTransferHost.exe (PID: 7212)
Reads Environment values
- identity_helper.exe (PID: 7260)
- MSACCESS.EXE (PID: 7600)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 660)
- InfinityCrypt.exe (PID: 2504)
- MSACCESS.EXE (PID: 7600)
Checks proxy server information
- BackgroundTransferHost.exe (PID: 660)
- MSACCESS.EXE (PID: 7600)
Reads the software policy settings
- BackgroundTransferHost.exe (PID: 660)
- slui.exe (PID: 8644)
- slui.exe (PID: 5556)
- MSACCESS.EXE (PID: 7600)
Autorun file from Downloads
- msedge.exe (PID: 2384)
Reads Microsoft Office registry keys
- msedge.exe (PID: 7360)
- OpenWith.exe (PID: 4620)
- MSACCESS.EXE (PID: 7600)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1228)
- msedge.exe (PID: 7300)
The sample compiled with chinese language support
- WinRAR.exe (PID: 1228)
The sample compiled with english language support
- WinRAR.exe (PID: 1228)
- msedge.exe (PID: 7300)
The sample compiled with german language support
- WinRAR.exe (PID: 1228)
Drops a (possible) Coronavirus decoy
- WinRAR.exe (PID: 1228)
- InfinityCrypt.exe (PID: 2504)
The sample compiled with french language support
- WinRAR.exe (PID: 1228)
The sample compiled with russian language support
- WinRAR.exe (PID: 1228)
Manual execution by a user
- InfinityCrypt.exe (PID: 2504)
- notepad++.exe (PID: 7852)
- MSACCESS.EXE (PID: 7600)
- msedge.exe (PID: 8392)
The sample compiled with spanish language support
- WinRAR.exe (PID: 1228)
Reads CPU info
- InfinityCrypt.exe (PID: 2504)
Reads the machine GUID from the registry
- InfinityCrypt.exe (PID: 2504)
Create files in a temporary directory
- MSACCESS.EXE (PID: 7600)
Reads product name
- MSACCESS.EXE (PID: 7600)
The sample compiled with korean language support
- WinRAR.exe (PID: 1228)
Process checks computer location settings
- MSACCESS.EXE (PID: 7600)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
255
Monitored processes
99
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 660 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 960 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 968 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=122.0.2365.59 --initial-client-data=0x1e0,0x294,0x298,0x1e8,0x2a0,0x7ffc88165fd8,0x7ffc88165fe4,0x7ffc88165ff0 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1096 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=3816 --field-trial-handle=2340,i,16302215403251573258,13096748413484882203,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
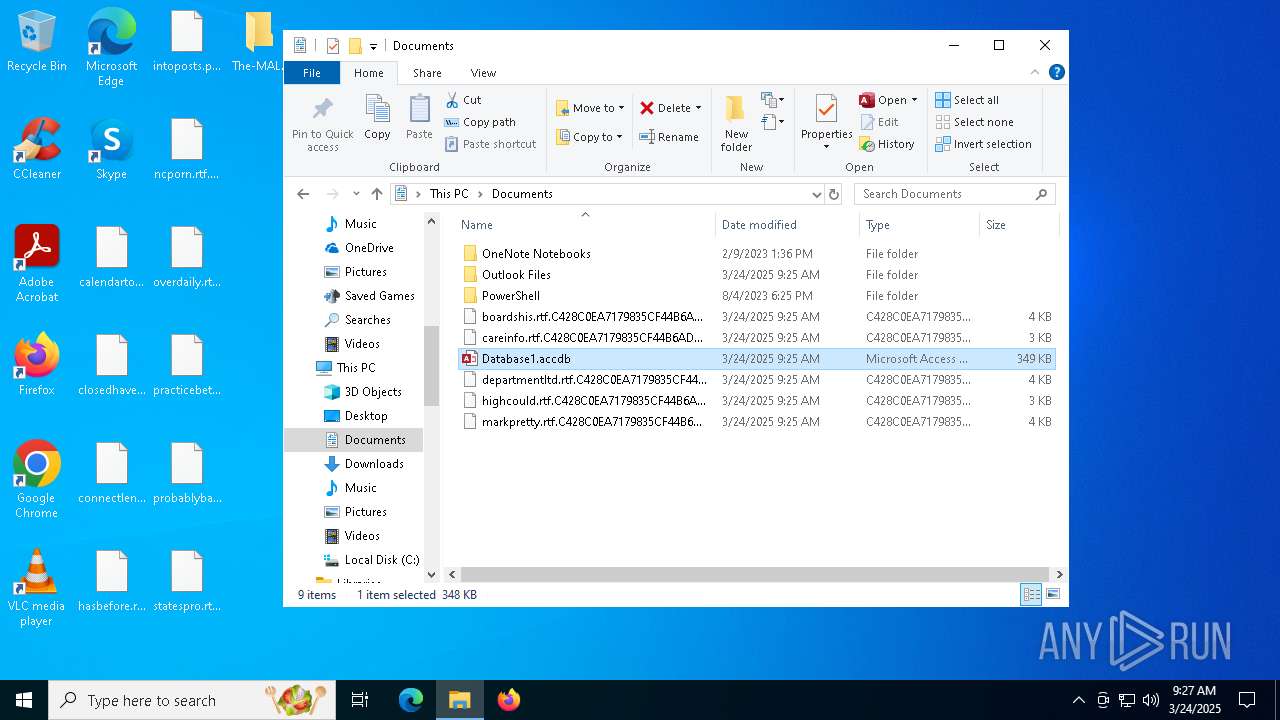
| 1228 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\The-MALWARE-Repo-master.zip" | C:\Program Files\WinRAR\WinRAR.exe | msedge.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1280 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_collections.mojom.CollectionsDataManager --lang=en-US --service-sandbox-type=collections --no-appcompat-clear --mojo-platform-channel-handle=4892 --field-trial-handle=2308,i,1130232894402091931,4245448821688000554,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1328 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=1524 --field-trial-handle=2308,i,1130232894402091931,4245448821688000554,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1388 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --no-startup-window | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1676 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4924 --field-trial-handle=2340,i,16302215403251573258,13096748413484882203,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2108 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=5336 --field-trial-handle=2340,i,16302215403251573258,13096748413484882203,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
24 790
Read events
24 289
Write events
454
Delete events
47
Modification events
| (PID) Process: | (7360) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (7360) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (7360) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (7360) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (7360) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 1EFE1A6FA98F2F00 | |||
| (PID) Process: | (7360) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 64652D6FA98F2F00 | |||
| (PID) Process: | (7360) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328284 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {F2B5159D-329A-40FD-A886-98C49985ADD2} | |||
| (PID) Process: | (7360) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328284 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {EB346977-9678-4AB9-B854-2C393C35D6C1} | |||
| (PID) Process: | (7360) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328284 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {C20F1509-3D49-4804-87AB-50465C9B7A6C} | |||
| (PID) Process: | (7360) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328284 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {E1C84D89-F413-4005-A6A0-A49239FA5C73} | |||
Executable files
220
Suspicious files
1 222
Text files
218
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7360 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF10c1ea.TMP | — | |
MD5:— | SHA256:— | |||
| 7360 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF10c1ea.TMP | — | |
MD5:— | SHA256:— | |||
| 7360 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7360 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF10c1fa.TMP | — | |
MD5:— | SHA256:— | |||
| 7360 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7360 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7360 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF10c248.TMP | — | |
MD5:— | SHA256:— | |||
| 7360 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7360 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF10c248.TMP | — | |
MD5:— | SHA256:— | |||
| 7360 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
56
TCP/UDP connections
148
DNS requests
146
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
660 | BackgroundTransferHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
8184 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
1568 | svchost.exe | HEAD | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a575cead-e662-4f4d-b0c3-81f1438d0388?P1=1742973082&P2=404&P3=2&P4=GVT3Ye6AYUYSnR1fU0jcjIg%2fe%2fIua10OFkXYo1qSjrVXp549oU8Pqm785ta9kTZe8n4vNoasGAkmyDnPg1fBSw%3d%3d | unknown | — | — | whitelisted |
9140 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
9140 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1568 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a575cead-e662-4f4d-b0c3-81f1438d0388?P1=1742973082&P2=404&P3=2&P4=GVT3Ye6AYUYSnR1fU0jcjIg%2fe%2fIua10OFkXYo1qSjrVXp549oU8Pqm785ta9kTZe8n4vNoasGAkmyDnPg1fBSw%3d%3d | unknown | — | — | whitelisted |
1568 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a575cead-e662-4f4d-b0c3-81f1438d0388?P1=1742973082&P2=404&P3=2&P4=GVT3Ye6AYUYSnR1fU0jcjIg%2fe%2fIua10OFkXYo1qSjrVXp549oU8Pqm785ta9kTZe8n4vNoasGAkmyDnPg1fBSw%3d%3d | unknown | — | — | whitelisted |
1568 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/a575cead-e662-4f4d-b0c3-81f1438d0388?P1=1742973082&P2=404&P3=2&P4=GVT3Ye6AYUYSnR1fU0jcjIg%2fe%2fIua10OFkXYo1qSjrVXp549oU8Pqm785ta9kTZe8n4vNoasGAkmyDnPg1fBSw%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7360 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7664 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7664 | msedge.exe | 150.171.28.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7664 | msedge.exe | 140.82.121.3:443 | github.com | GITHUB | US | whitelisted |
3216 | svchost.exe | 20.197.71.89:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
7664 | msedge.exe | 13.107.6.158:443 | business.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
github.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
www.bing.com |
| whitelisted |
github.githubassets.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2504 | InfinityCrypt.exe | Malware Command and Control Activity Detected | RANSOMWARE [ANY.RUN] InfinityLock Ransomware CnC Communication |
2504 | InfinityCrypt.exe | Misc activity | ET HUNTING [TW] Likely Javascript-Obfuscator Usage Observed M1 |