| File name: | BIN.exe |
| Full analysis: | https://app.any.run/tasks/a028492c-7c0c-4b89-afff-f129ce6ebc61 |
| Verdict: | Malicious activity |
| Threats: | Remote access trojans (RATs) are a type of malware that enables attackers to establish complete to partial control over infected computers. Such malicious programs often have a modular design, offering a wide range of functionalities for conducting illicit activities on compromised systems. Some of the most common features of RATs include access to the users’ data, webcam, and keystrokes. This malware is often distributed through phishing emails and links. |
| Analysis date: | October 24, 2020, 17:03:06 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 68B0FF10343F5E356F4682DFA79F9424 |
| SHA1: | 99754504507E53F7197A086C6CE61B1111275815 |
| SHA256: | 6A0BA704A65336684450FEF2FCDB9954E263AEE7A38EEB2140D79EF43183734B |
| SSDEEP: | 98304:+x9cHoVw7srhNupA9+qlpZGB8ZW82jIV0Blzm:iCHoVukoXqlSBsW82MSBQ |
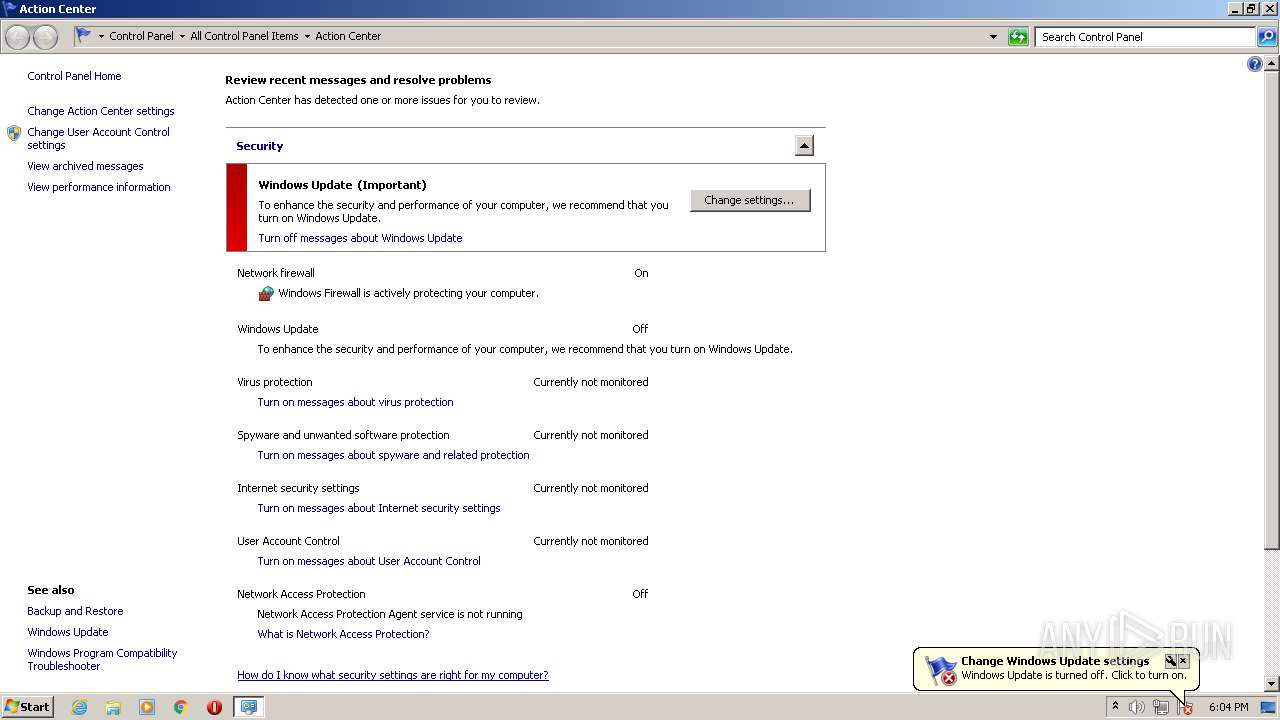
MALICIOUS
Loads dropped or rewritten executable
- test.exe (PID: 1948)
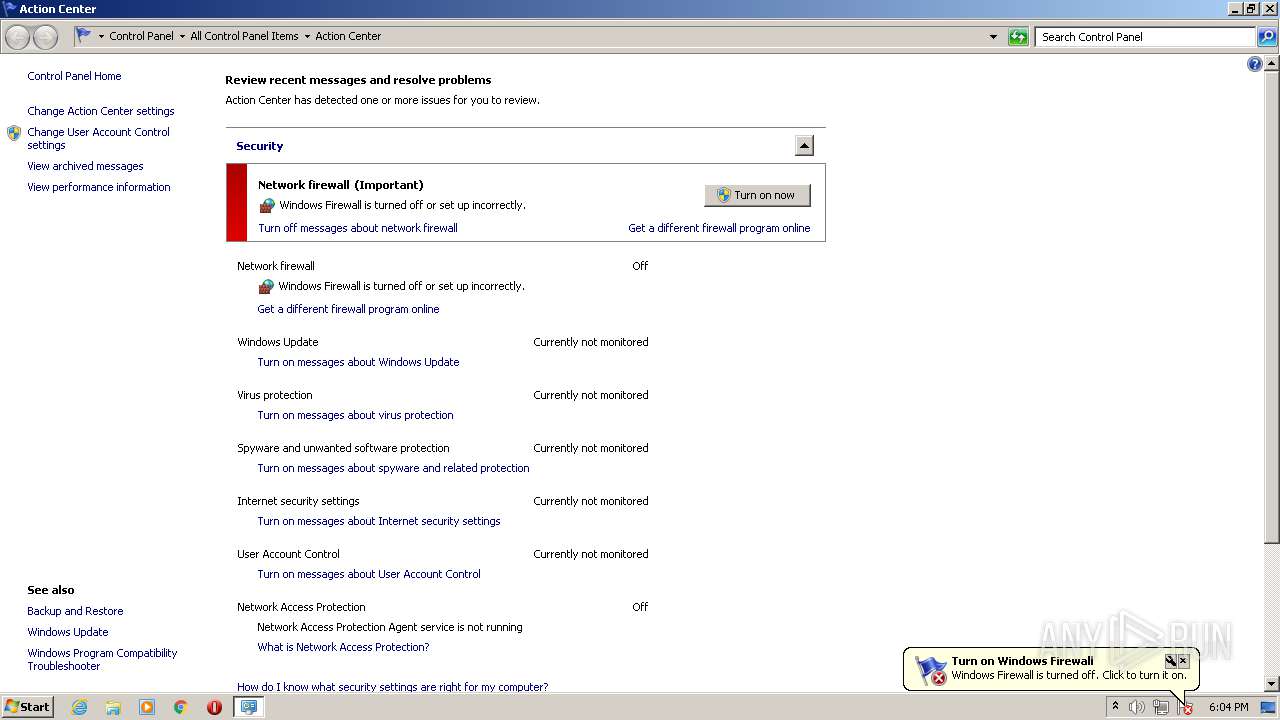
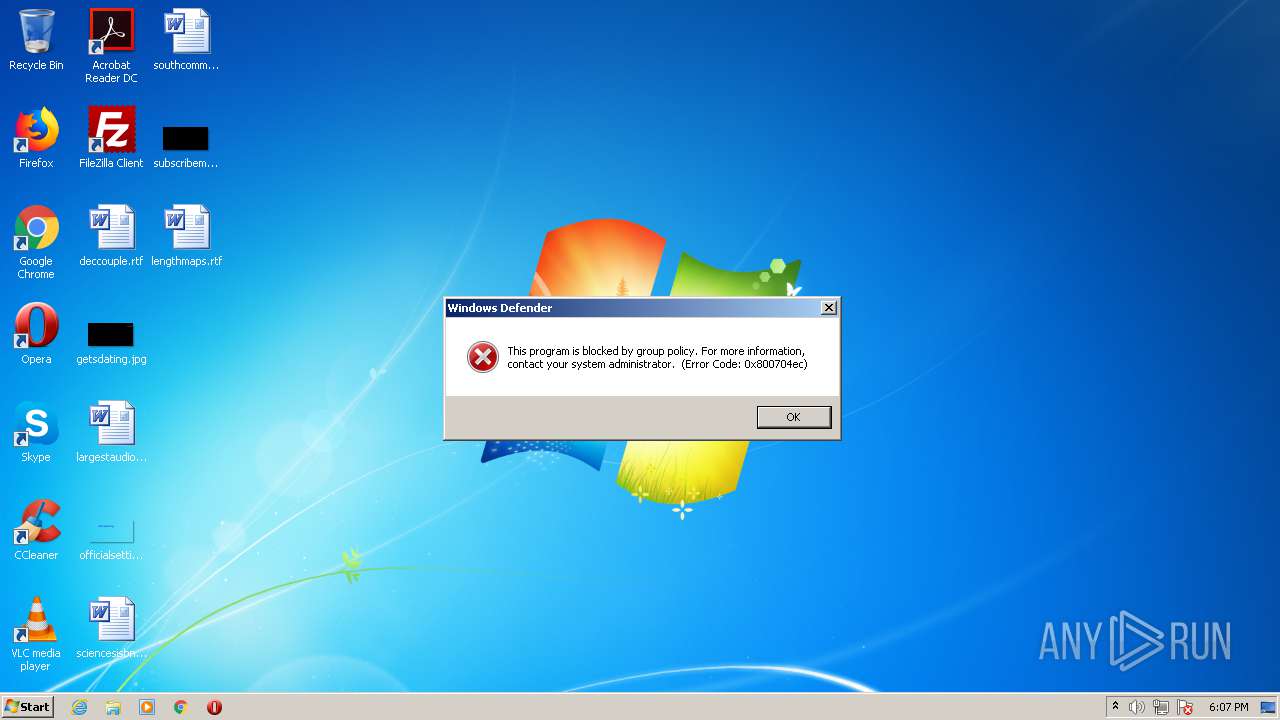
Changes the login/logoff helper path in the registry
- test.exe (PID: 1948)
Actions looks like stealing of personal data
- test.exe (PID: 1948)
Application was dropped or rewritten from another process
- test.exe (PID: 1948)
Writes to a start menu file
- test.exe (PID: 1948)
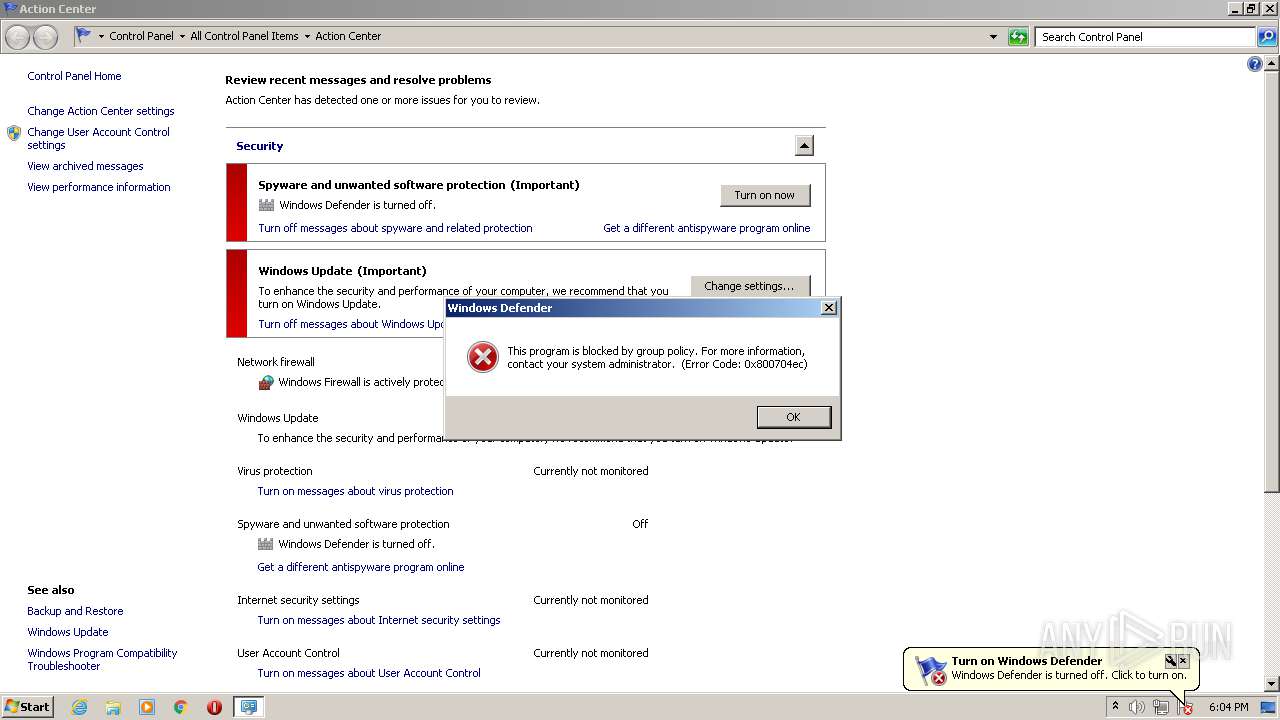
TEAMVIEWER was detected
- test.exe (PID: 1948)
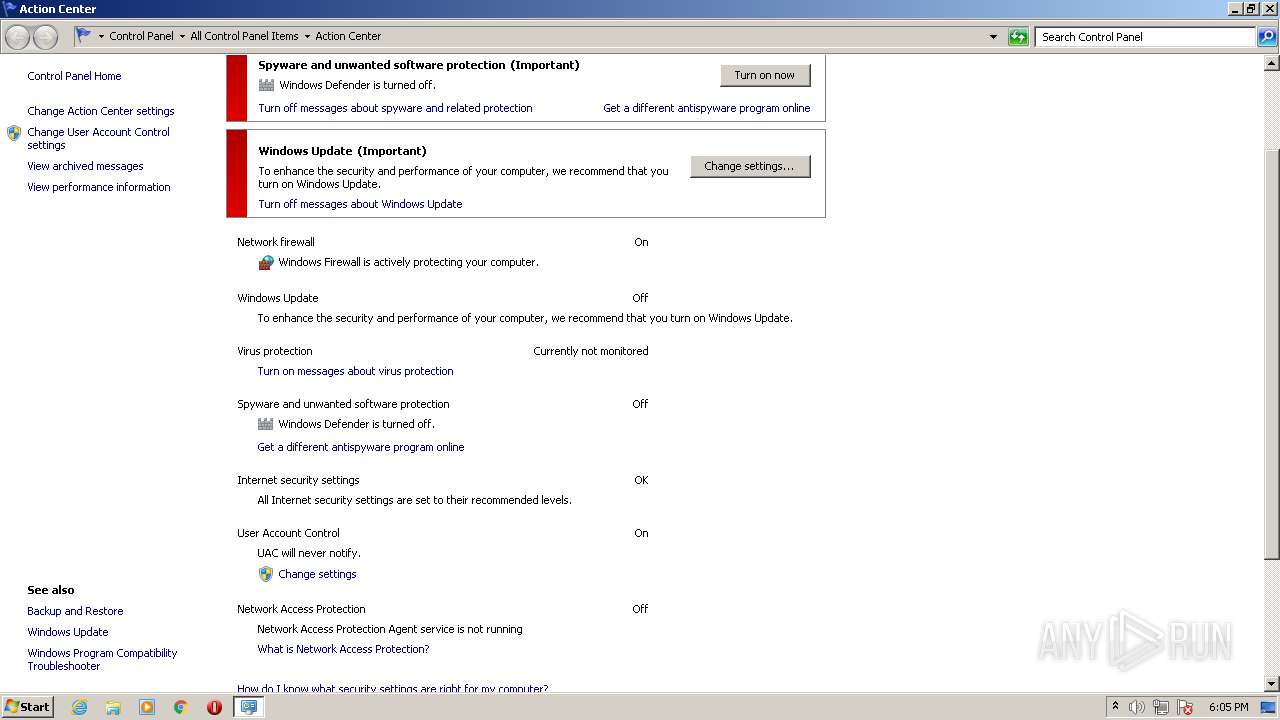
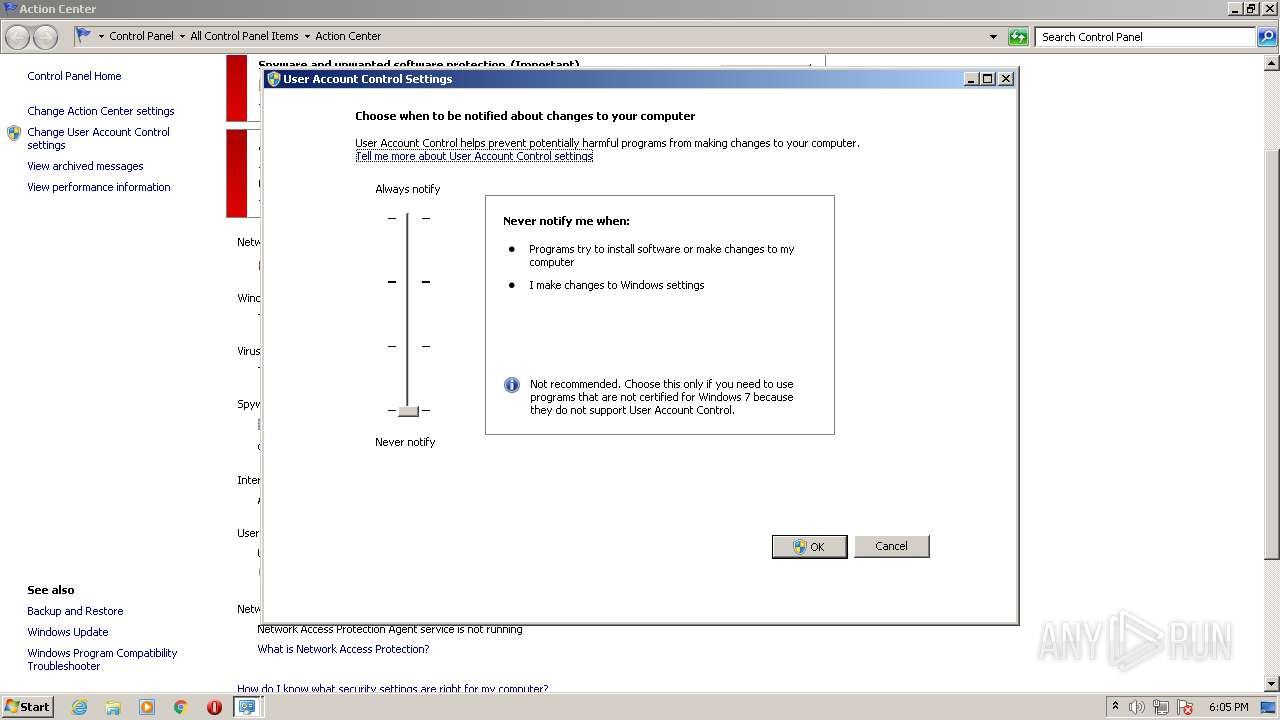
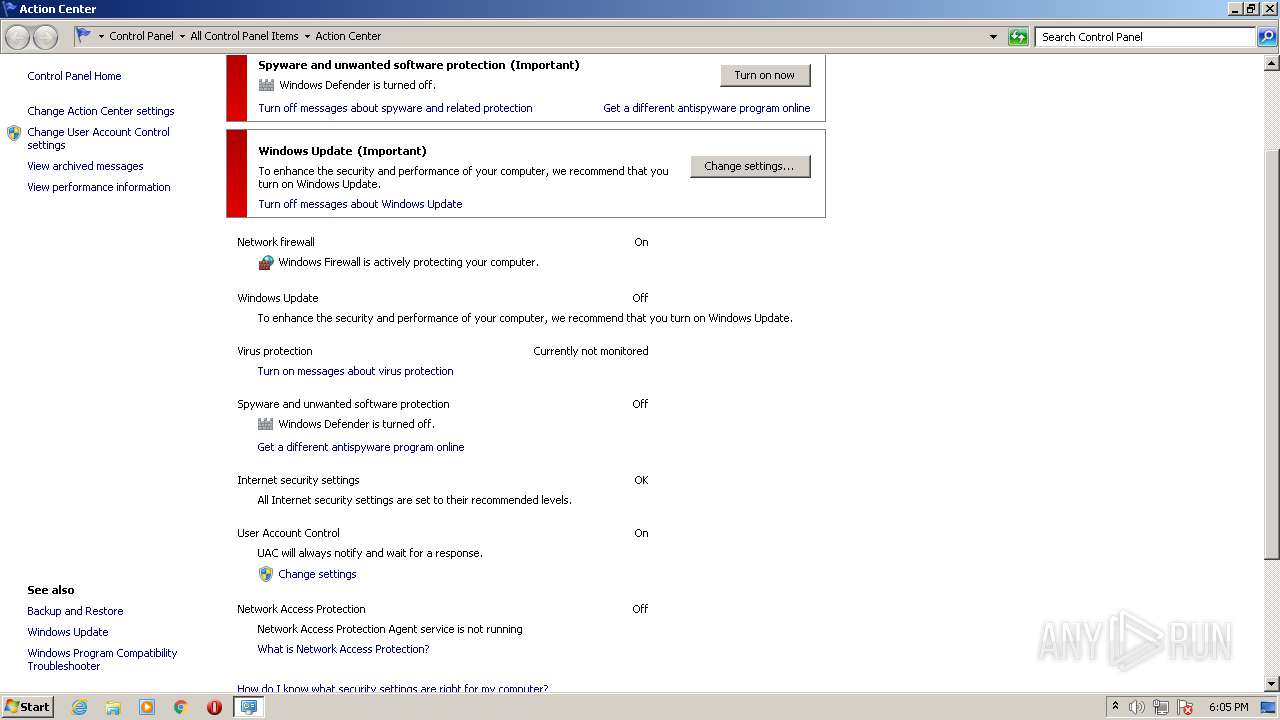
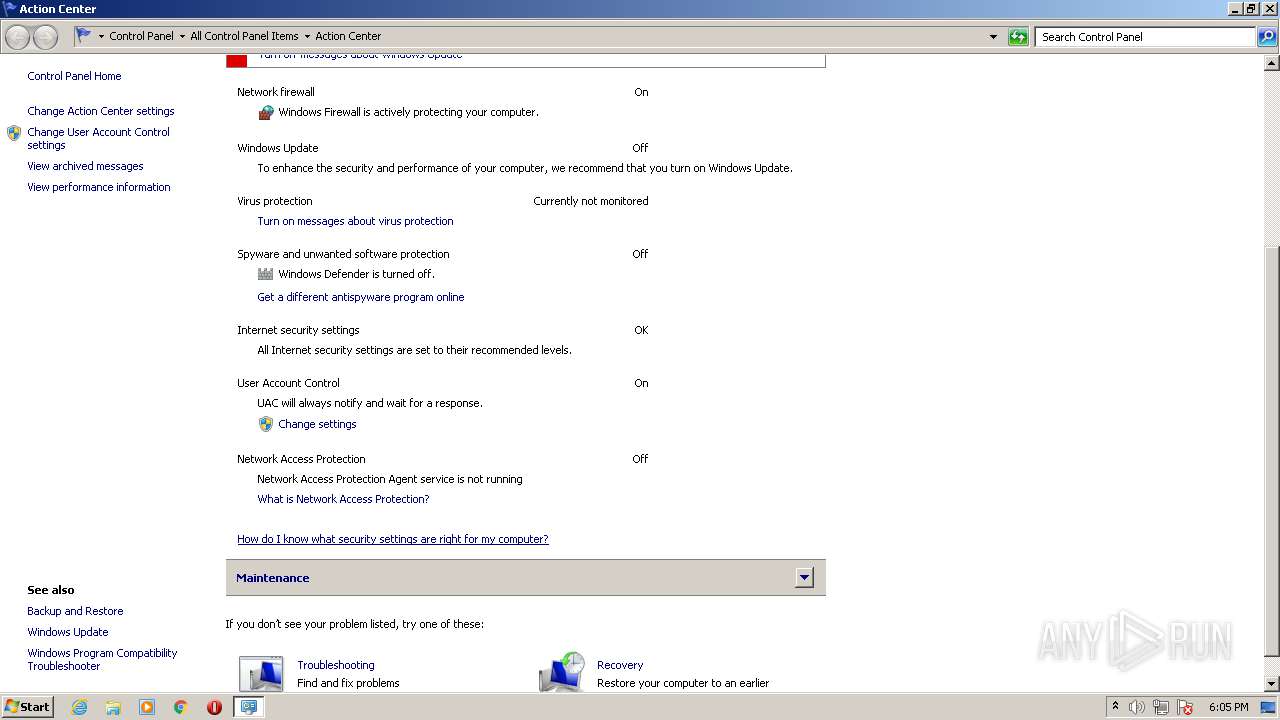
UAC/LUA settings modification
- DllHost.exe (PID: 1712)
Application was injected by another process
- svchost.exe (PID: 872)
- svchost.exe (PID: 1052)
- SearchIndexer.exe (PID: 332)
Runs injected code in another process
- sdclt.exe (PID: 3692)
Changes settings of System certificates
- svchost.exe (PID: 1052)
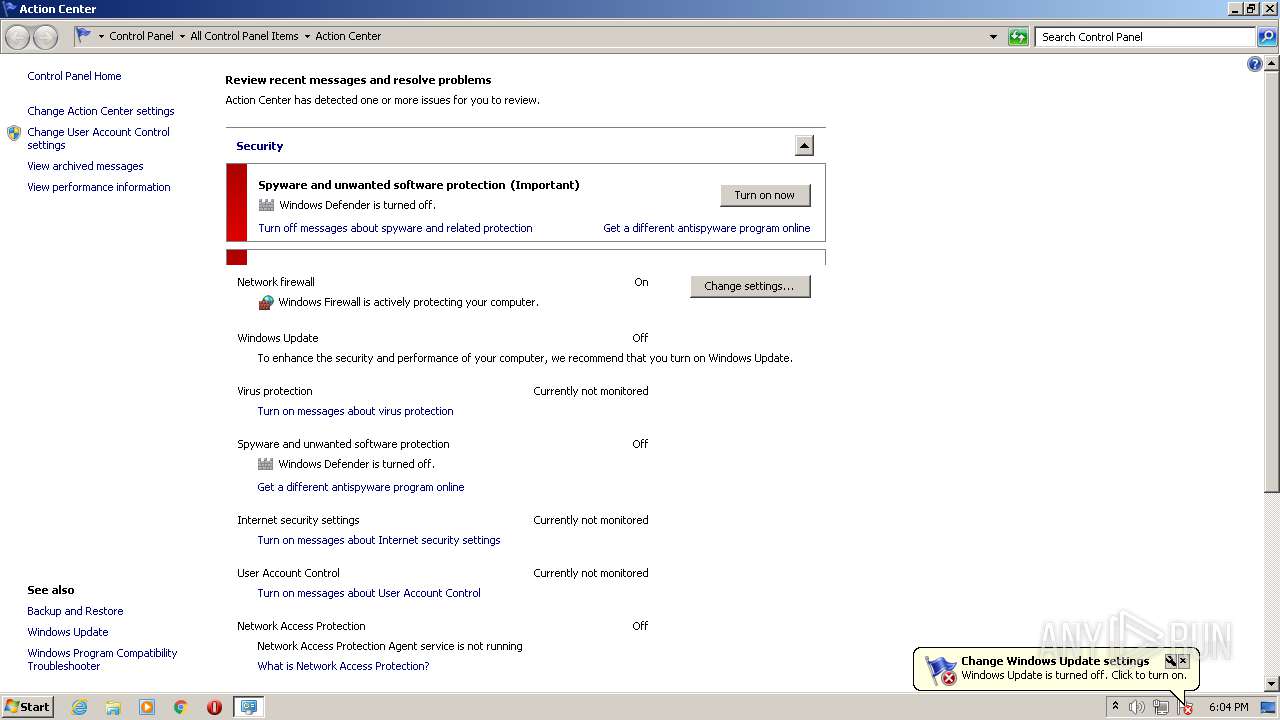
SUSPICIOUS
Creates files in the user directory
- BIN.exe (PID: 2664)
- test.exe (PID: 1948)
Executable content was dropped or overwritten
- BIN.exe (PID: 2664)
Reads Internet Cache Settings
- test.exe (PID: 1948)
Executed via COM
- DllHost.exe (PID: 2496)
- DllHost.exe (PID: 1712)
- DllHost.exe (PID: 2416)
- vdsldr.exe (PID: 2788)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 1856)
- DllHost.exe (PID: 1104)
Executed as Windows Service
- vds.exe (PID: 184)
- vssvc.exe (PID: 3816)
- wbengine.exe (PID: 1164)
Low-level read access rights to disk partition
- sdclt.exe (PID: 3692)
- wbengine.exe (PID: 1164)
- vds.exe (PID: 184)
Creates files in the Windows directory
- sdclt.exe (PID: 3692)
- svchost.exe (PID: 1052)
Removes files from Windows directory
- sdclt.exe (PID: 3692)
- svchost.exe (PID: 1052)
Creates files in the program directory
- svchost.exe (PID: 872)
Starts Internet Explorer
- FlashPlayerApp.exe (PID: 1416)
Adds / modifies Windows certificates
- svchost.exe (PID: 1052)
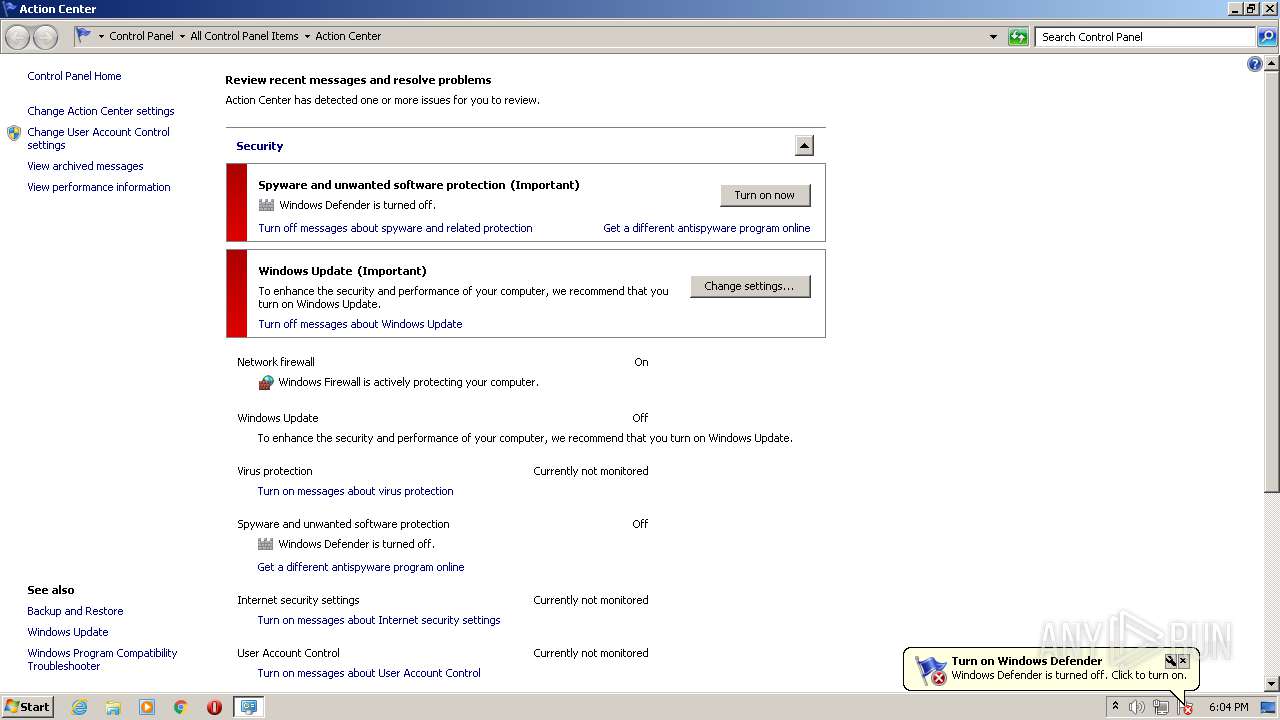
INFO
Manual execution by user
- MSASCui.exe (PID: 3480)
- iexplore.exe (PID: 2924)
- UserAccountControlSettings.exe (PID: 3188)
- sdclt.exe (PID: 3692)
- UserAccountControlSettings.exe (PID: 2644)
- RunDll32.exe (PID: 2860)
- rundll32.exe (PID: 3396)
- MSASCui.exe (PID: 2536)
Reads Internet Cache Settings
- iexplore.exe (PID: 2924)
- iexplore.exe (PID: 892)
- iexplore.exe (PID: 2004)
- iexplore.exe (PID: 3460)
Changes internet zones settings
- iexplore.exe (PID: 2924)
- iexplore.exe (PID: 2004)
Application launched itself
- iexplore.exe (PID: 2924)
- iexplore.exe (PID: 2004)
Reads settings of System Certificates
- iexplore.exe (PID: 892)
- iexplore.exe (PID: 2924)
- iexplore.exe (PID: 3460)
- iexplore.exe (PID: 2004)
Changes settings of System certificates
- iexplore.exe (PID: 2924)
- iexplore.exe (PID: 2004)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2924)
- iexplore.exe (PID: 2004)
Low-level read access rights to disk partition
- vssvc.exe (PID: 3816)
Reads internet explorer settings
- iexplore.exe (PID: 3460)
- iexplore.exe (PID: 892)
Creates files in the user directory
- iexplore.exe (PID: 3460)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 1856)
- iexplore.exe (PID: 892)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 2924)
- iexplore.exe (PID: 2004)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:06:25 12:38:24+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 200704 |
| InitializedDataSize: | 114176 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1ea80 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 25-Jun-2020 10:38:24 |
| Debug artifacts: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000118 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 6 |
| Time date stamp: | 25-Jun-2020 10:38:24 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00030F2A | 0x00031000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.70442 |
.rdata | 0x00032000 | 0x0000A5F2 | 0x0000A600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.2593 |
.data | 0x0003D000 | 0x00023720 | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.70568 |
.didat | 0x00061000 | 0x00000188 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.29951 |
.rsrc | 0x00062000 | 0x0000E020 | 0x0000E200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.80352 |
.reloc | 0x00071000 | 0x00002264 | 0x00002400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.55675 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.25329 | 1875 | Latin 1 / Western European | UNKNOWN | RT_MANIFEST |
2 | 5.10026 | 2216 | Latin 1 / Western European | UNKNOWN | RT_ICON |
3 | 5.25868 | 3752 | Latin 1 / Western European | UNKNOWN | RT_ICON |
4 | 5.02609 | 1128 | Latin 1 / Western European | UNKNOWN | RT_ICON |
5 | 5.18109 | 4264 | Latin 1 / Western European | UNKNOWN | RT_ICON |
6 | 5.04307 | 9640 | Latin 1 / Western European | UNKNOWN | RT_ICON |
7 | 3.66634 | 508 | Latin 1 / Western European | UNKNOWN | RT_STRING |
8 | 3.71728 | 582 | Latin 1 / Western European | UNKNOWN | RT_STRING |
9 | 3.73856 | 422 | Latin 1 / Western European | UNKNOWN | RT_STRING |
10 | 3.55807 | 220 | Latin 1 / Western European | UNKNOWN | RT_STRING |
Imports
KERNEL32.dll |
USER32.dll (delay-loaded) |
gdiplus.dll |
Total processes
78
Monitored processes
31
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 184 | C:\Windows\System32\vds.exe | C:\Windows\System32\vds.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Virtual Disk Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 332 | C:\Windows\system32\SearchIndexer.exe /Embedding | C:\Windows\System32\SearchIndexer.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Indexer Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 872 | C:\Windows\system32\svchost.exe -k netsvcs | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 892 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2924 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1052 | C:\Windows\system32\svchost.exe -k NetworkService | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1104 | C:\Windows\system32\DllHost.exe /Processid:{A4B07E49-6567-4FB8-8D39-01920E3B2357} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1164 | "C:\Windows\system32\wbengine.exe" | C:\Windows\system32\wbengine.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Block Level Backup Engine Service EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1416 | "C:\Windows\system32\FlashPlayerApp.exe" | C:\Windows\system32\FlashPlayerApp.exe | — | rundll32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Flash Player Control Panel Applet Exit code: 0 Version: 26,0,0,131 Modules
| |||||||||||||||
| 1608 | "C:\Windows\system32\UserAccountControlSettings.exe" /applySettings | C:\Windows\system32\UserAccountControlSettings.exe | DllHost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: UserAccountControlSettings Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1712 | C:\Windows\system32\DllHost.exe /Processid:{EA2C6B24-C590-457B-BAC8-4A0F9B13B5B8} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
3 104
Read events
2 705
Write events
394
Delete events
5
Modification events
| (PID) Process: | (1052) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList\Nla\Cache\Intranet |
| Operation: | write | Name: | {4040CF00-1B3E-486A-B407-FA14C56B6FC0} |
Value: 525400363EFF | |||
| (PID) Process: | (2664) BIN.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2664) BIN.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (1948) test.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Winlogon |
| Operation: | write | Name: | ParseAutoexec |
Value: 1 | |||
| (PID) Process: | (1948) test.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Winlogon |
| Operation: | write | Name: | Shell |
Value: explorer.exe, "C:\Users\admin\AppData\Roaming\test.exe" | |||
| (PID) Process: | (1948) test.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1948) test.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (1948) test.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A5000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (872) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList\S-1-5-21-1302019708-1500728564-335382590-1000 |
| Operation: | write | Name: | RefCount |
Value: 3 | |||
| (PID) Process: | (872) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList\S-1-5-21-1302019708-1500728564-335382590-1000 |
| Operation: | write | Name: | RefCount |
Value: 2 | |||
Executable files
13
Suspicious files
80
Text files
190
Unknown types
68
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 872 | svchost.exe | C:\Windows\appcompat\programs\RecentFileCache.bcf | txt | |
MD5:— | SHA256:— | |||
| 2664 | BIN.exe | C:\Users\admin\AppData\Roaming\VPN\x64\teamviewervpn.cat | cat | |
MD5:5CFFE65F36B60BC151486C90382F1627 | SHA256:AA7C09A817EB54E3CC5C342454608364A679E231824F83BA5A2D0278EDCC1851 | |||
| 2664 | BIN.exe | C:\Users\admin\AppData\Roaming\tv_x64.dll | executable | |
MD5:DCD8CDA46BB20FF09C8C8BE8BE2F3098 | SHA256:A21DAFAB3D25F88D7001DE9437F0A01C72D66DB0C1A190DD5ACDB2CC38EA9513 | |||
| 2664 | BIN.exe | C:\Users\admin\AppData\Roaming\tvr.cfg | binary | |
MD5:4C9E3C0AB490E85393AFD8A06F60DD27 | SHA256:7CD542687D0ECFFEEF26100046B45C293DB828E9AEBF6D2265F5CB87CD40C1F0 | |||
| 2664 | BIN.exe | C:\Users\admin\AppData\Roaming\test.exe | executable | |
MD5:75C738B78021EEC28F7A9EEAADE02CFE | SHA256:9EBC2CE3BFFC2E689742A304308FB41543609A9F0EE2E19DD56AF94AB0CAB1CC | |||
| 2664 | BIN.exe | C:\Users\admin\AppData\Roaming\tv_x64.exe | executable | |
MD5:E0331B54A56E7AA48F97B4956BCEF769 | SHA256:7A487C2CBA93E7D6963930C5734F14D6CF17E85FC2316D6AECCD617100A1FF9F | |||
| 2664 | BIN.exe | C:\Users\admin\AppData\Roaming\vpn.exe | executable | |
MD5:694F241B7BEAF7C8C7524FB80E442D41 | SHA256:3A9283AB360DC54977102A2B6103C115B064DED8D5631E3FEAB3D5CE482A4550 | |||
| 2664 | BIN.exe | C:\Users\admin\AppData\Roaming\VPN\x64\teamviewervpn.sys | executable | |
MD5:F5520DBB47C60EE83024B38720ABDA24 | SHA256:B8E555D92440BF93E3B55A66E27CEF936477EF7528F870D3B78BD3B294A05CC0 | |||
| 2664 | BIN.exe | C:\Users\admin\AppData\Roaming\VPN\x64\run.exe | executable | |
MD5:112B0C8B6B0C0A6C24F90081CC8A77D0 | SHA256:F627380E9DE14AF3EB5331BB9A4D559B2C970ABACFF038EA464044CA1EF62163 | |||
| 892 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar90D7.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
33
TCP/UDP connections
141
DNS requests
39
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
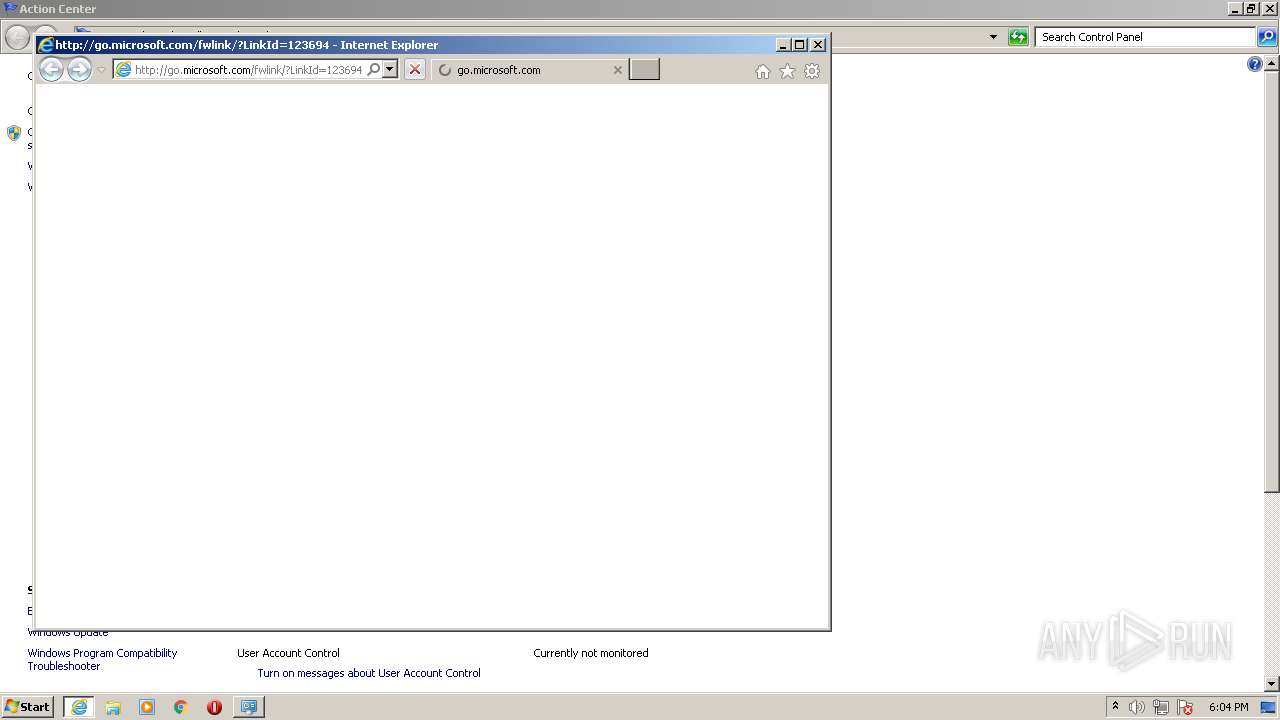
892 | iexplore.exe | GET | 302 | 88.221.62.148:80 | http://go.microsoft.com/fwlink/?LinkId=123694 | unknown | — | — | whitelisted |
2860 | RunDll32.exe | GET | — | 52.255.148.73:80 | http://watson.microsoft.com/StageOne/Generic/PnPRequestAdditionalSoftware/x86/USB_VID_0627_PID_0001_REV_0000/6_1_1_0/0409/input_inf/_.htm?LCID=1033&OS=6.1.7601.2.00010100.1.0.48.17514&SM=DELL&SPN=DELL&BV=DELL&MID=3ADE2C42-4AB9-49B7-B142-BE9AEEA69063&Queue=1 | US | — | — | whitelisted |
— | — | GET | — | 52.255.148.73:80 | http://watson.microsoft.com/StageOne/Generic/PnPRequestAdditionalSoftware/x86/USB_VID_0627_PID_0001_REV_0000/6_1_1_0/0409/input_inf/_.htm?LCID=1033&OS=6.1.7601.2.00010100.1.0.48.17514&SM=DELL&SPN=DELL&BV=DELL&MID=3ADE2C42-4AB9-49B7-B142-BE9AEEA69063&Queue=1 | US | — | — | whitelisted |
892 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAtb9ltrp%2FvQiykNkEU33uA%3D | US | der | 471 b | whitelisted |
892 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
892 | iexplore.exe | GET | 304 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAtb9ltrp%2FvQiykNkEU33uA%3D | US | der | 1.47 Kb | whitelisted |
892 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
3460 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQQX6Z6gAidtSefNc6DC0OInqPHDQQUD4BhHIIxYdUvKOeNRji0LOHG2eICEAZ2JfwMCbGcYKxKdYCjCAA%3D | US | der | 471 b | whitelisted |
3460 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
892 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1948 | test.exe | 185.188.32.5:5938 | master5.teamviewer.com | TeamViewer GmbH | DE | suspicious |
1948 | test.exe | 188.172.219.158:5938 | ping3.teamviewer.com | ANEXIA Internetdienstleistungs GmbH | NL | suspicious |
— | — | 185.188.32.5:5938 | master5.teamviewer.com | TeamViewer GmbH | DE | suspicious |
892 | iexplore.exe | 88.221.62.148:80 | go.microsoft.com | Akamai Technologies, Inc. | — | malicious |
892 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
892 | iexplore.exe | 23.210.249.93:443 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
892 | iexplore.exe | 13.107.246.10:443 | wcpstatic.microsoft.com | Microsoft Corporation | US | whitelisted |
892 | iexplore.exe | 2.16.186.40:443 | img-prod-cms-rt-microsoft-com.akamaized.net | Akamai International B.V. | — | whitelisted |
892 | iexplore.exe | 40.90.23.206:443 | login.live.com | Microsoft Corporation | US | unknown |
892 | iexplore.exe | 40.77.226.250:443 | web.vortex.data.microsoft.com | Microsoft Corporation | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ping3.teamviewer.com |
| shared |
master5.teamviewer.com |
| shared |
go.microsoft.com |
| whitelisted |
support.microsoft.com |
| malicious |
ocsp.digicert.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
statics-marketingsites-neu-ms-com.akamaized.net |
| whitelisted |
wcpstatic.microsoft.com |
| whitelisted |
mem.gfx.ms |
| whitelisted |
img-prod-cms-rt-microsoft-com.akamaized.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1948 | test.exe | Potential Corporate Privacy Violation | REMOTE [PTsecurity] TeamViewer |
2860 | RunDll32.exe | Potential Corporate Privacy Violation | ET POLICY Application Crash Report Sent to Microsoft |
2860 | RunDll32.exe | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
— | — | Potential Corporate Privacy Violation | ET POLICY Application Crash Report Sent to Microsoft |