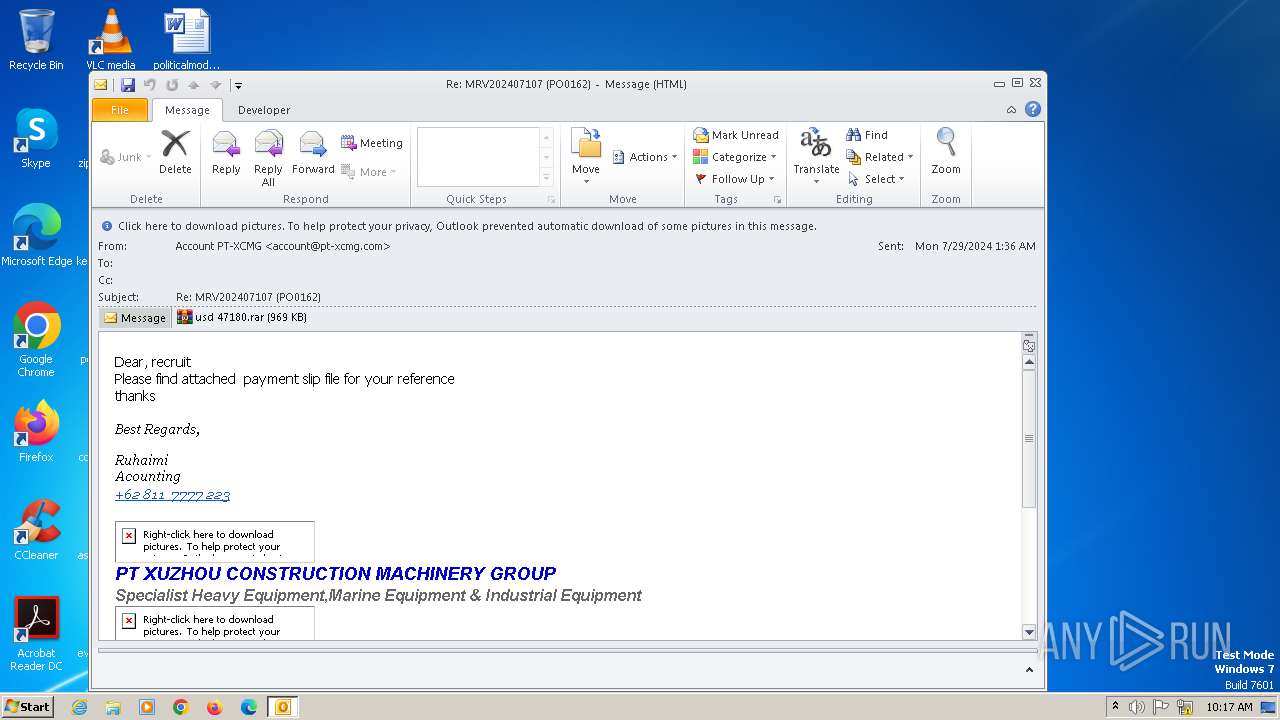
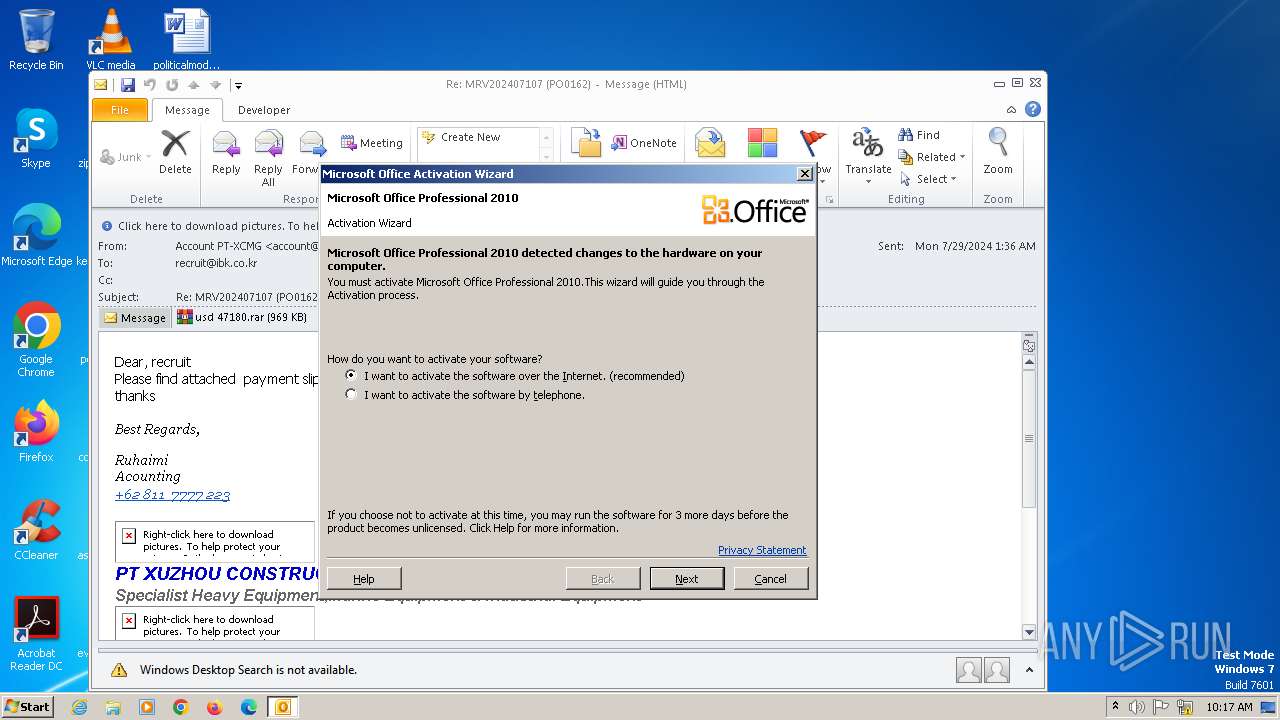
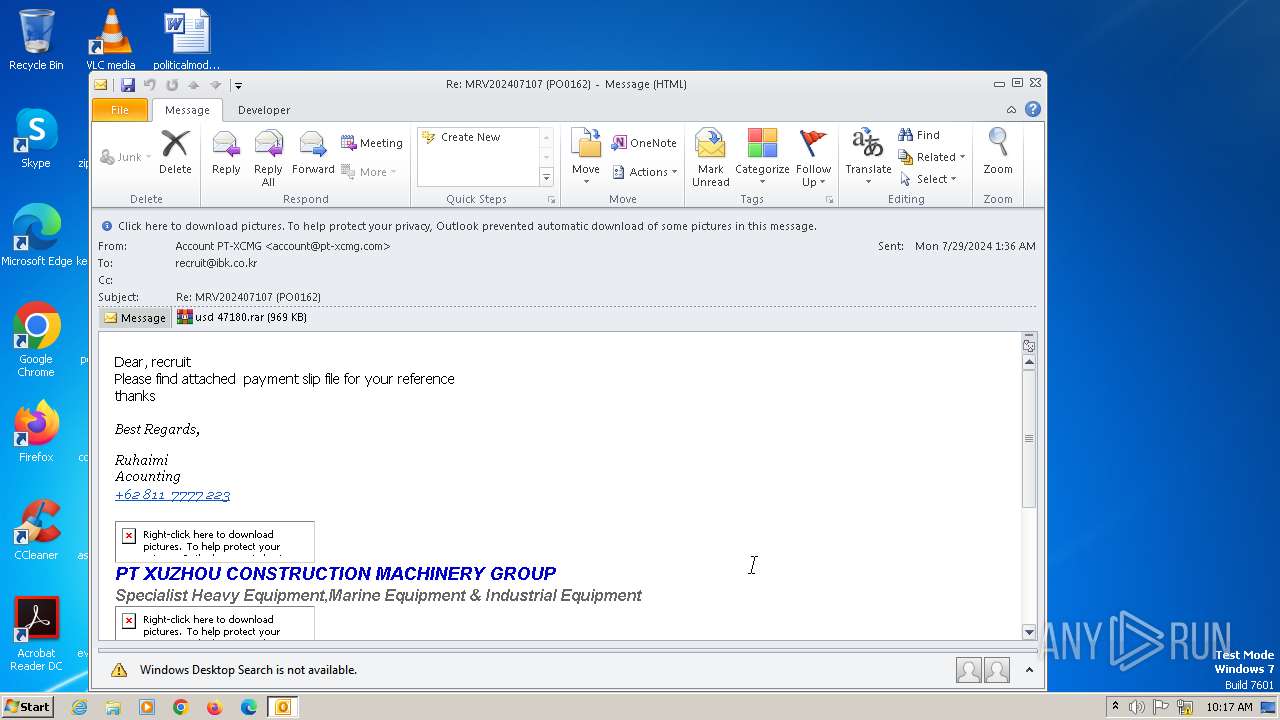
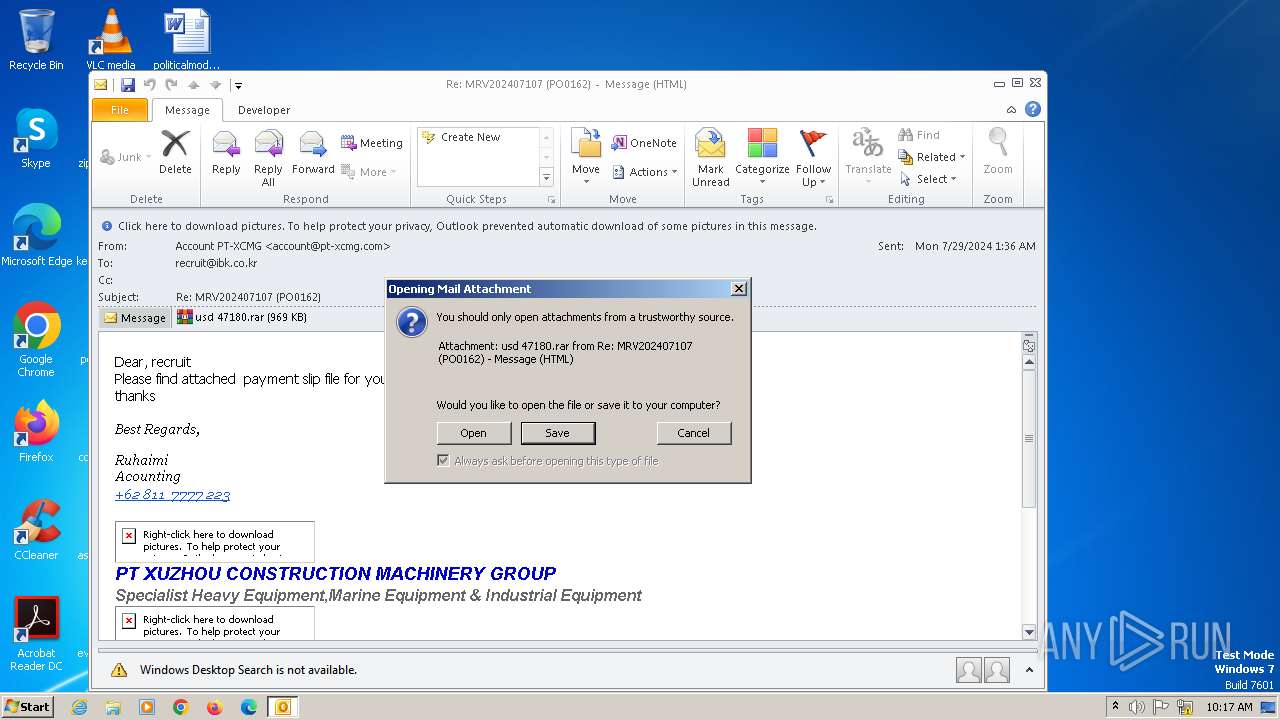
| File name: | Re MRV202407107 (PO0162).eml |
| Full analysis: | https://app.any.run/tasks/463c21ec-bddf-42cd-b47c-622d3df5401a |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | August 06, 2024, 10:17:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, ASCII text, with CRLF line terminators |
| MD5: | 5BEC3CD36EC134ECF81300138A679F8E |
| SHA1: | 5B0F4F19B8BADC1EE8B59955585DC6A1FFC49CA0 |
| SHA256: | 6963B9192DF3B889181DAE3940DAB7C3C074C4E3BCC4E8398AAF7627E82064EF |
| SSDEEP: | 24576:AlHR6L7dpd3cNC2gPYF/VqlzfqtsMqWarjkEVmeLbCOa44wNN:Ky7T1IwlzxMqiEAeLDNN |
MALICIOUS
Starts Visual C# compiler
- usd 47180.exe (PID: 2416)
FORMBOOK has been detected (YARA)
- wab.exe (PID: 2080)
- wmplayer.exe (PID: 2352)
- DpiScaling.exe (PID: 2716)
- DpiScaling.exe (PID: 2248)
Unusual execution from MS Outlook
- OUTLOOK.EXE (PID: 2440)
Changes the autorun value in the registry
- DpiScaling.exe (PID: 2804)
SUSPICIOUS
Process drops legitimate windows executable
- OUTLOOK.EXE (PID: 2440)
- WinRAR.exe (PID: 2500)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2500)
The process drops C-runtime libraries
- OUTLOOK.EXE (PID: 2440)
Starts CMD.EXE for commands execution
- usd 47180.exe (PID: 2416)
The process executes VB scripts
- usd 47180.exe (PID: 2416)
INFO
Drops the executable file immediately after the start
- OUTLOOK.EXE (PID: 2440)
- WinRAR.exe (PID: 2500)
The process uses the downloaded file
- OUTLOOK.EXE (PID: 2440)
- WinRAR.exe (PID: 2500)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2500)
Checks supported languages
- usd 47180.exe (PID: 2416)
- wab.exe (PID: 1276)
- wmplayer.exe (PID: 2352)
- wab.exe (PID: 2080)
- wab.exe (PID: 2012)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
56
Monitored processes
24
Malicious processes
7
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 192 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\vbc.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\vbc.exe | — | usd 47180.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Basic Command Line Compiler Version: 14.8.3761.0 | |||||||||||||||
| 328 | "C:\Windows\SysWOW64\DpiScaling.exe" | C:\Windows\SysWOW64\DpiScaling.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Display Control Panel Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 836 | "C:\Windows\SysWOW64\DpiScaling.exe" | C:\Windows\SysWOW64\DpiScaling.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Display Control Panel Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 856 | "C:\Windows\System32\calc.exe" | C:\Windows\System32\calc.exe | — | usd 47180.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Calculator Version: 6.1.7600.16385 (win7_rtm.090713-1255) | |||||||||||||||
| 1276 | "C:\Program Files (x86)\Windows Mail\wab.exe" | C:\Program Files (x86)\Windows Mail\wab.exe | — | usd 47180.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Contacts Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1344 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\ilasm.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\ilasm.exe | — | usd 47180.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Framework IL assembler Version: 4.8.3761.0 built by: NET48REL1 | |||||||||||||||
| 1444 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe | — | usd 47180.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Version: 4.8.3761.0 built by: NET48REL1 | |||||||||||||||
| 1700 | "C:\Program Files (x86)\Internet Explorer\iexplore.exe" | C:\Program Files (x86)\Internet Explorer\iexplore.exe | — | usd 47180.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) | |||||||||||||||
| 1712 | "C:\Windows\System32\svchost.exe" | C:\Windows\System32\svchost.exe | — | usd 47180.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Version: 6.1.7600.16385 (win7_rtm.090713-1255) | |||||||||||||||
| 1796 | "C:\Windows\System32\cmd.exe" | C:\Windows\System32\cmd.exe | — | usd 47180.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) | |||||||||||||||
Total events
13 853
Read events
13 258
Write events
567
Delete events
28
Modification events
| (PID) Process: | (2440) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2440) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2440) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (2440) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2440) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2440) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2440) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2440) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2440) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2440) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
6
Suspicious files
6
Text files
11
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2440 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR5076.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2440 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 2440 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\{DF66B71A-17E0-4E58-A7EF-02F25D6B5233}\{1C306CB1-771E-4B4B-A902-86E897877F5B}.png | image | |
MD5:4C61C12EDBC453D7AE184976E95258E1 | SHA256:296526F9A716C1AA91BA5D6F69F0EB92FDF79C2CB2CFCF0CEB22B7CCBC27035F | |||
| 2440 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\FORMS\FRMDATA64.DAT | binary | |
MD5:C4643157E488AC6D771054CAD7D50D84 | SHA256:D4FF48EB72AA94E3BA215C87B198733048E75105D024CCA42960EF96A8E04EA6 | |||
| 2440 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | binary | |
MD5:9C0C676315E3BB56E6879DA436A80EE8 | SHA256:B833AE8266ABB3074BF8A74BBE61FFD90672FAC4D5CEE58B0C39406555EFB13F | |||
| 2440 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\5EWDCL3R\usd 47180.rar | compressed | |
MD5:364D5B5D04B67A26C7733460A3C66C3C | SHA256:17EEE8DA9A4AA7590796A6EC58D3A4F7C428CEE8C6922A12A69823D3A08B8D41 | |||
| 2440 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\tmp53A4.tmp | binary | |
MD5:8318F2094133768962D210272BB56157 | SHA256:3577611F8EB1B95923BED6F20ECF94E4EE431BA2F68C97D5C0C2903316D88E9F | |||
| 2440 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_AvailabilityOptions_2_BFB12C4D25D7A54593FC0D0104F98D06.dat | xml | |
MD5:EEAA832C12F20DE6AAAA9C7B77626E72 | SHA256:C4C9A90F2C961D9EE79CF08FBEE647ED7DE0202288E876C7BAAD00F4CA29CA16 | |||
| 2440 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\5EWDCL3R\usd 47180 (2).rar:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 2440 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\5EWDCL3R\usd 47180.rar:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
5
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2440 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2440 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
config.messenger.msn.com |
| whitelisted |