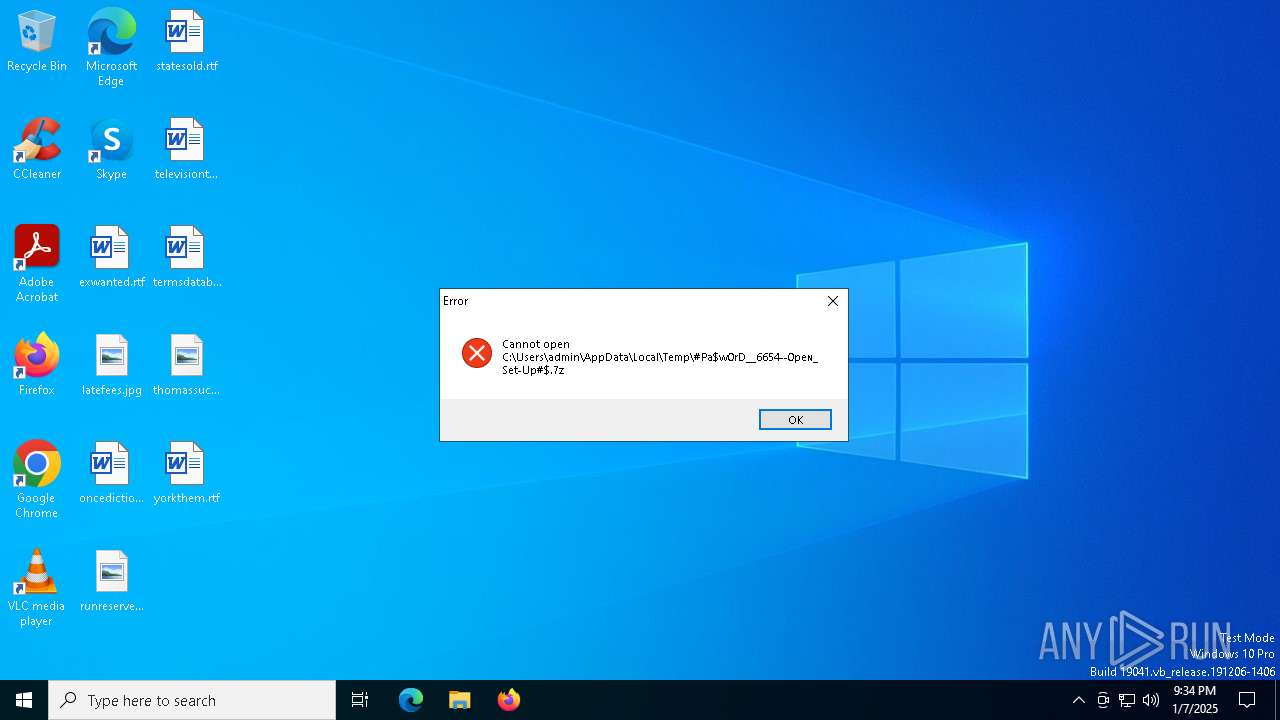
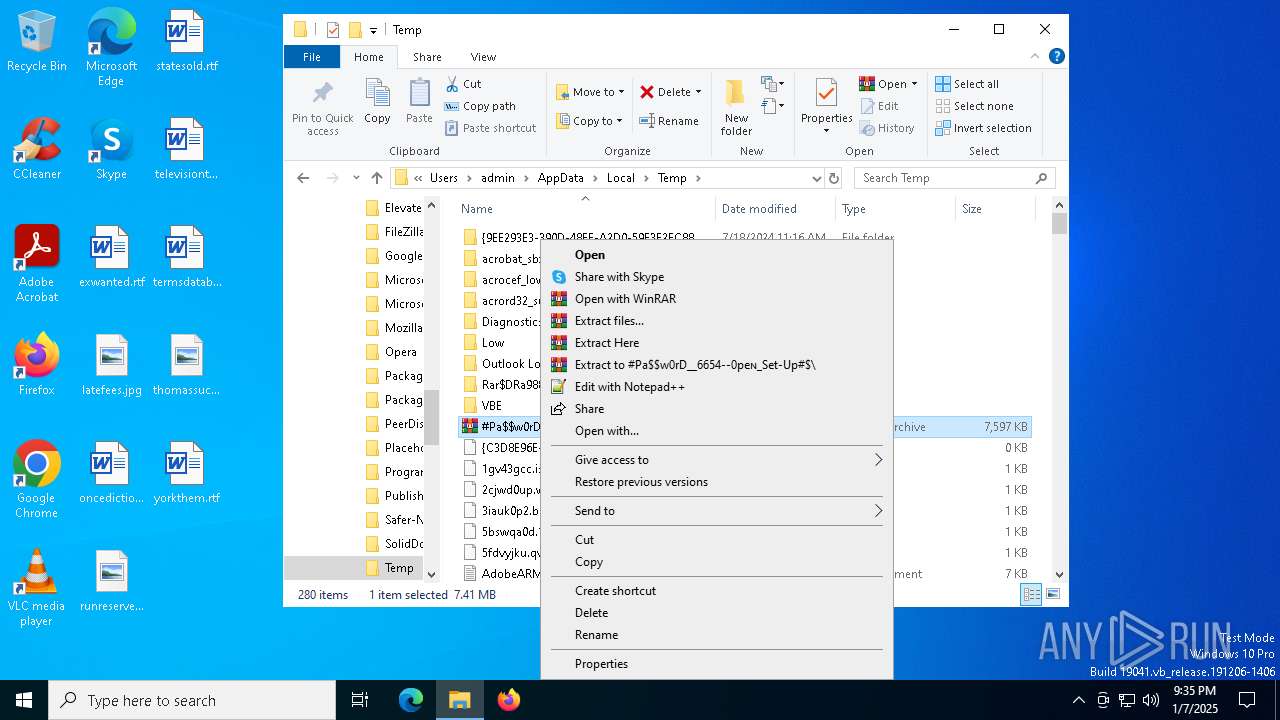
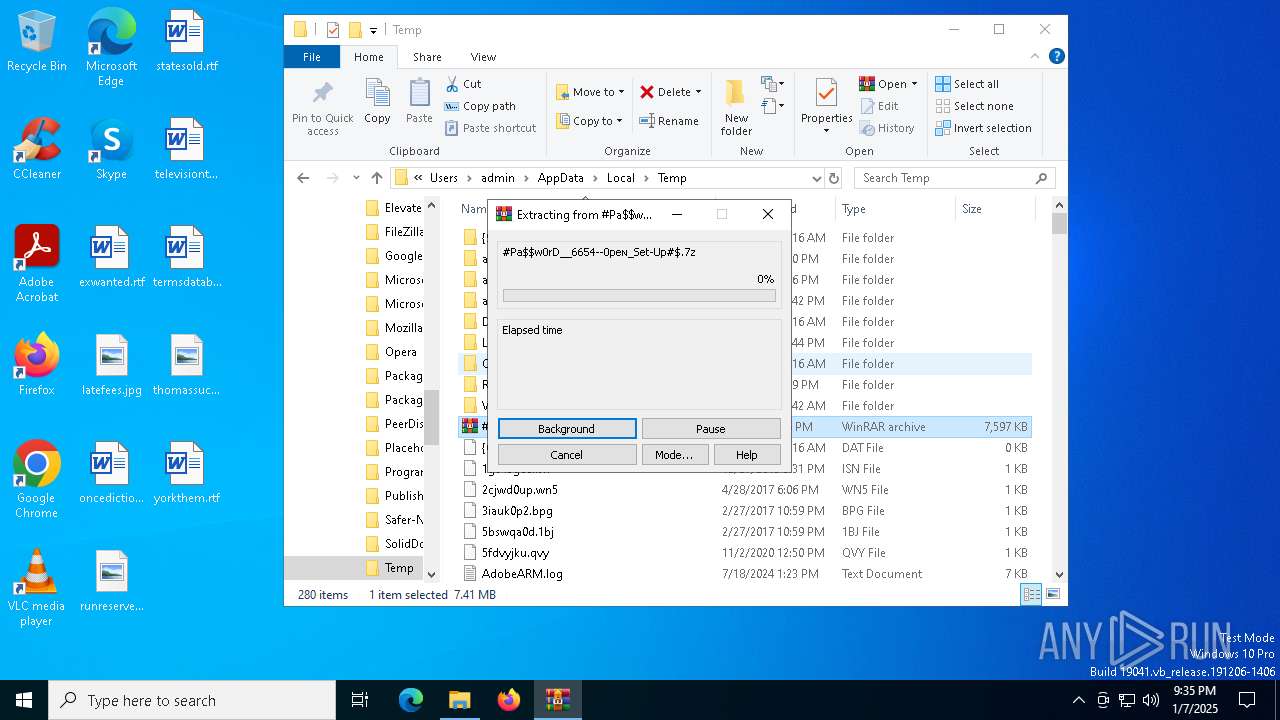
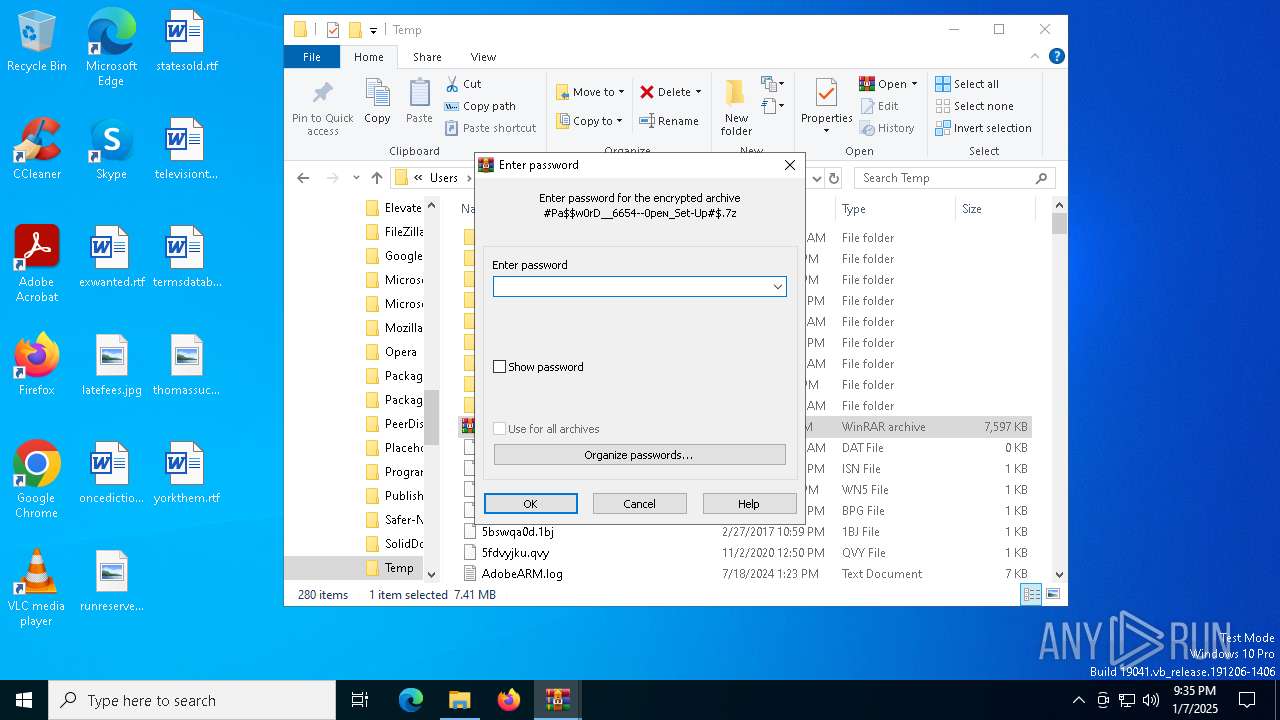
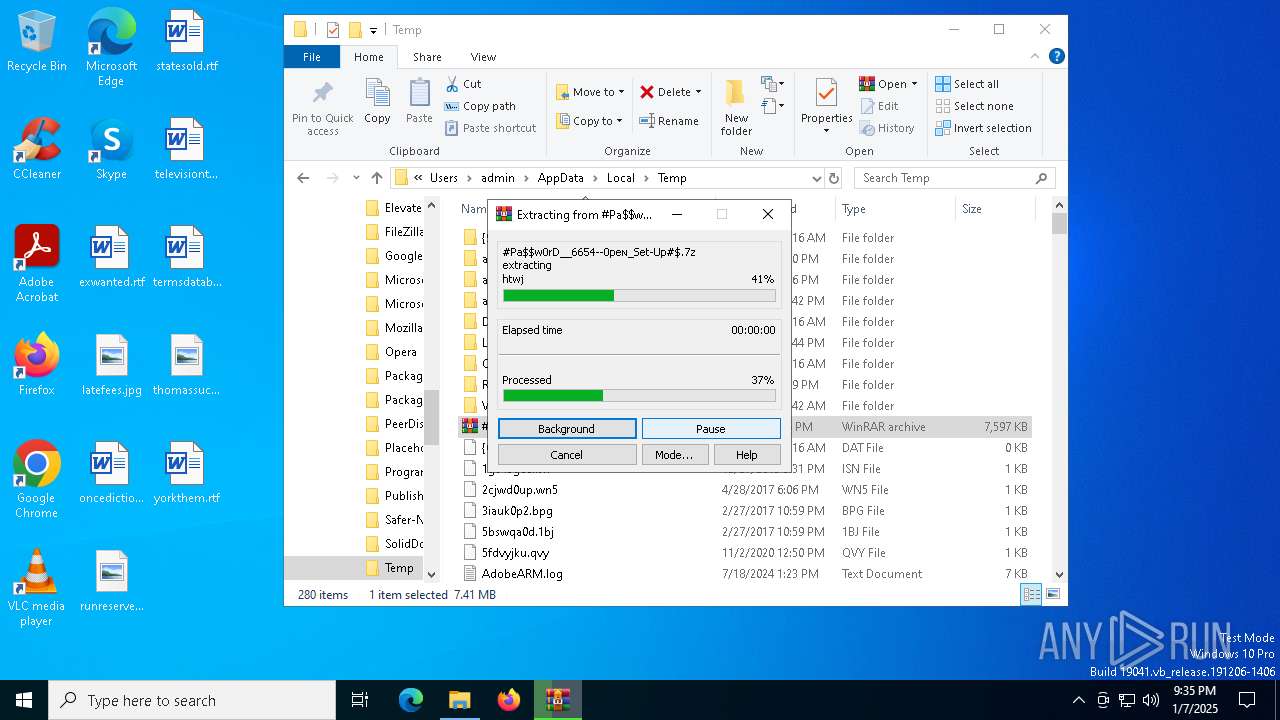
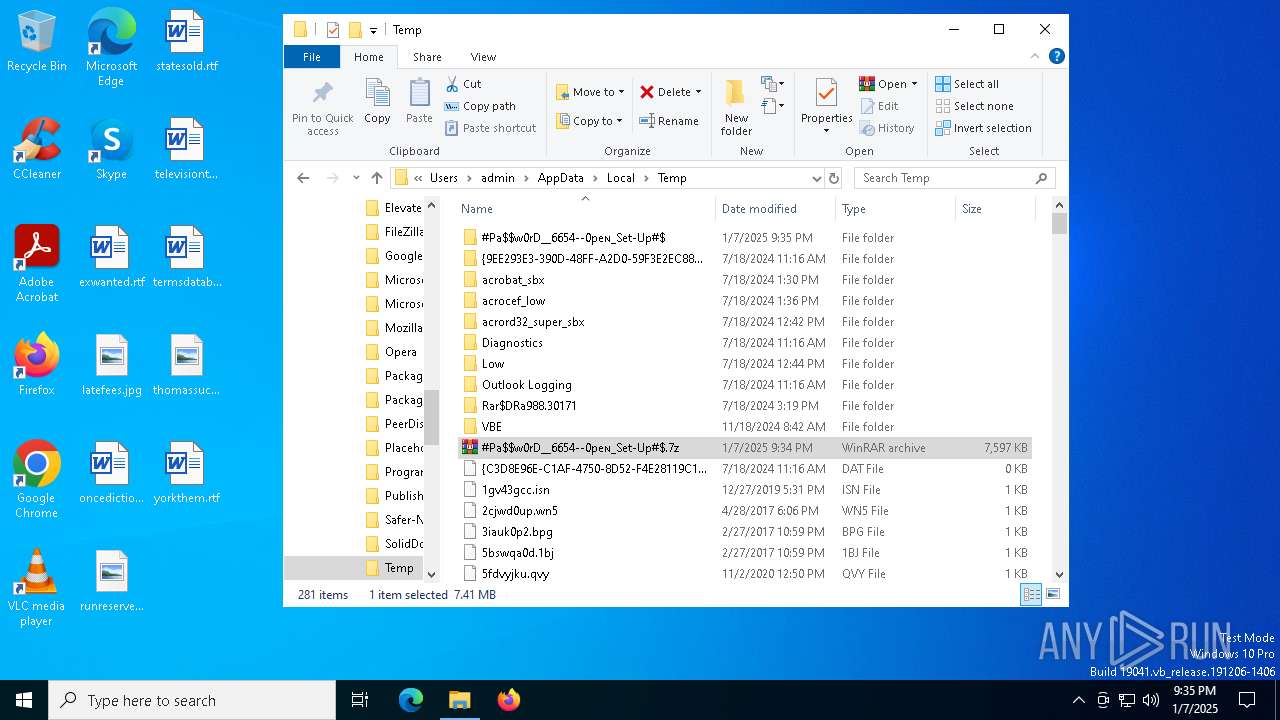
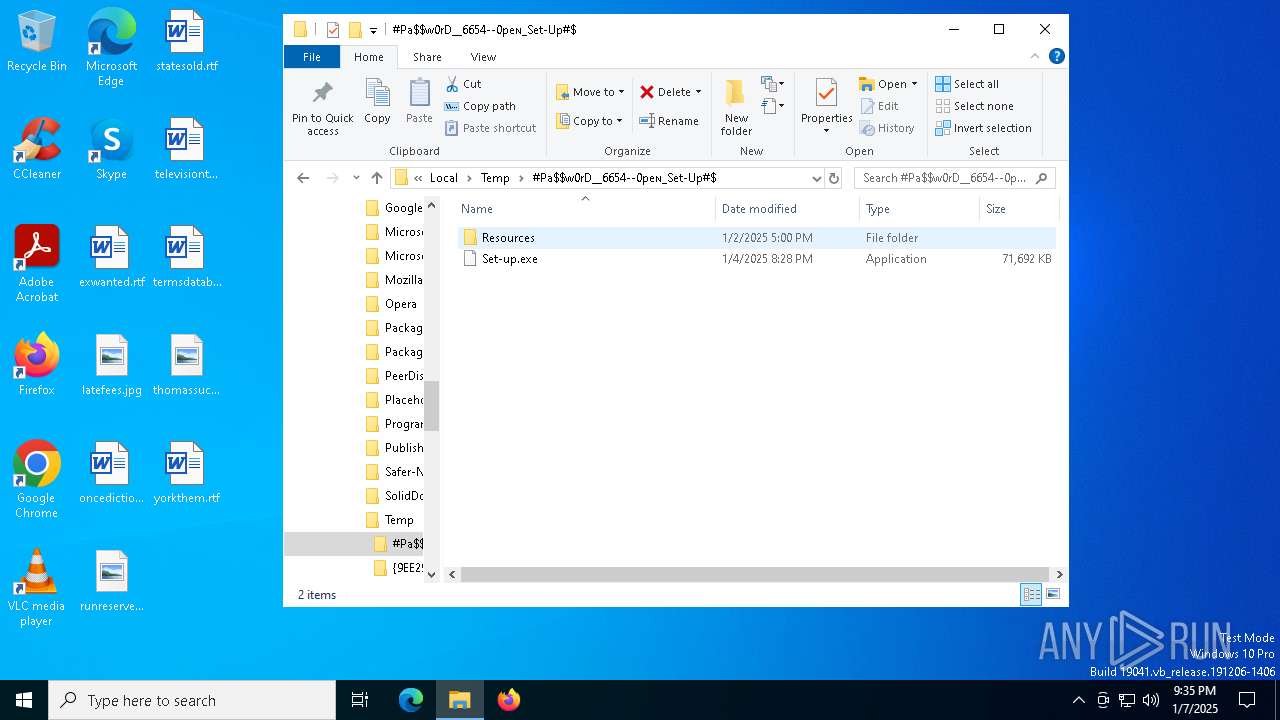
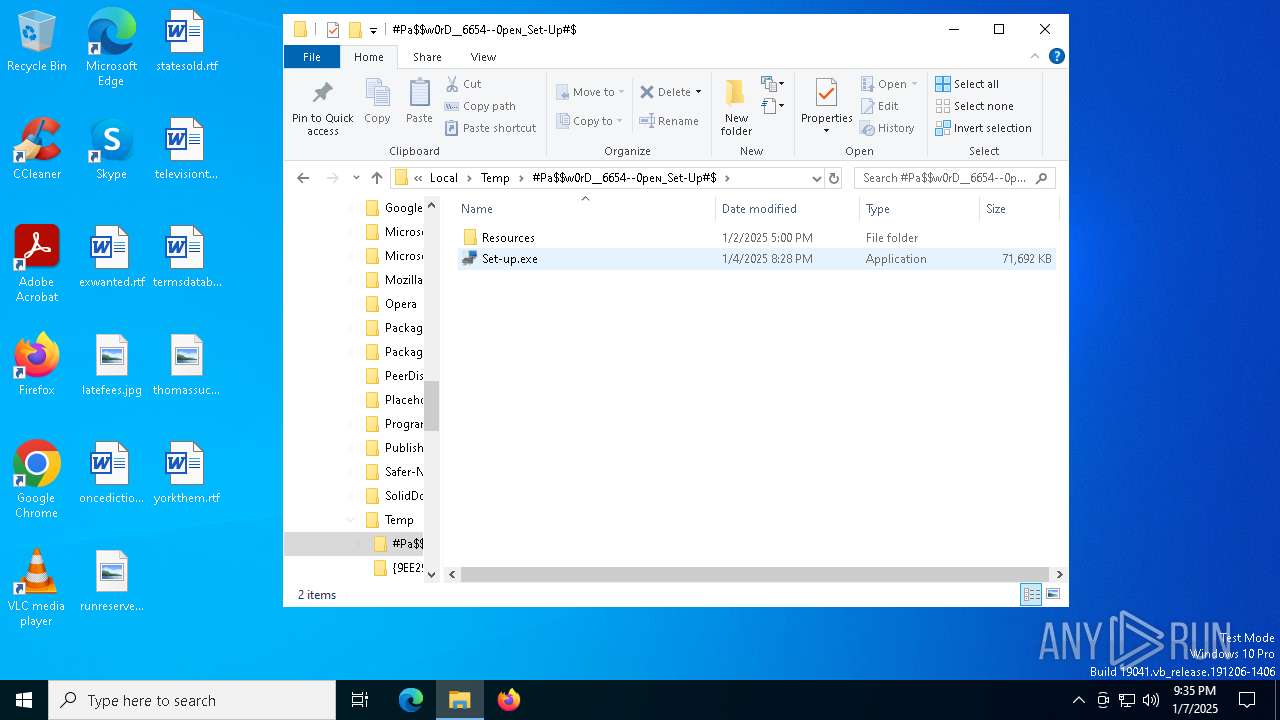
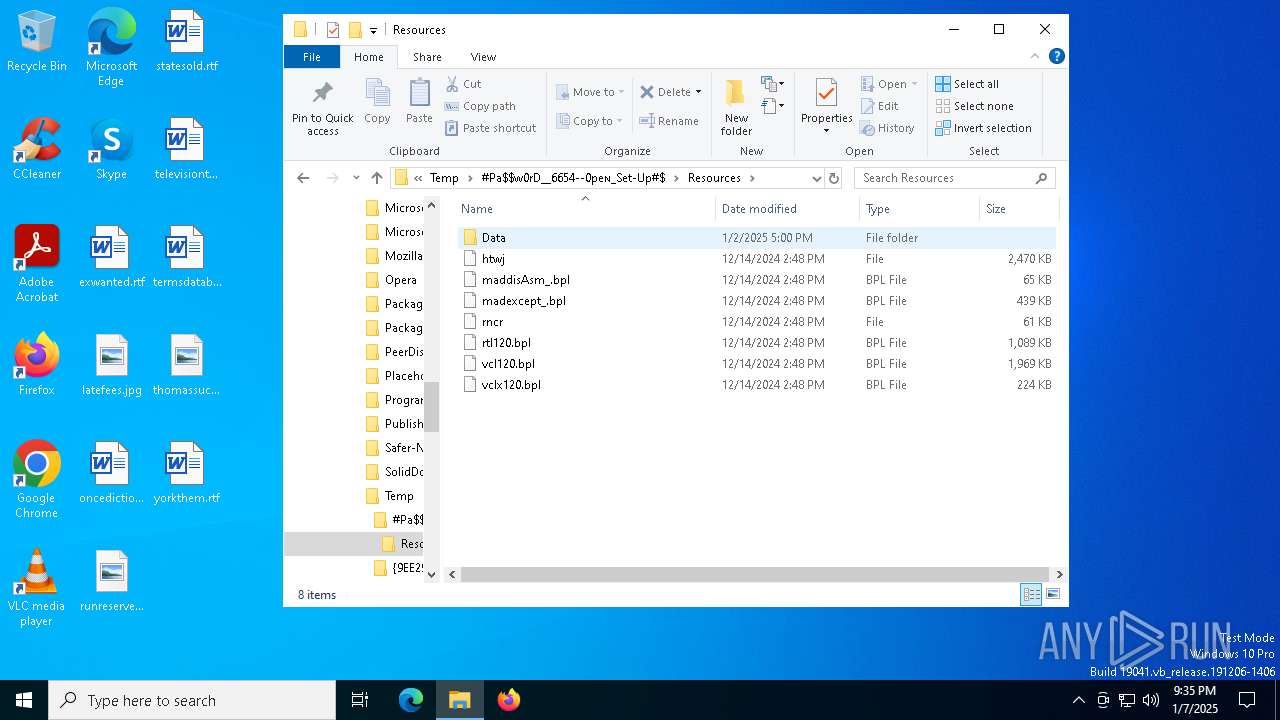
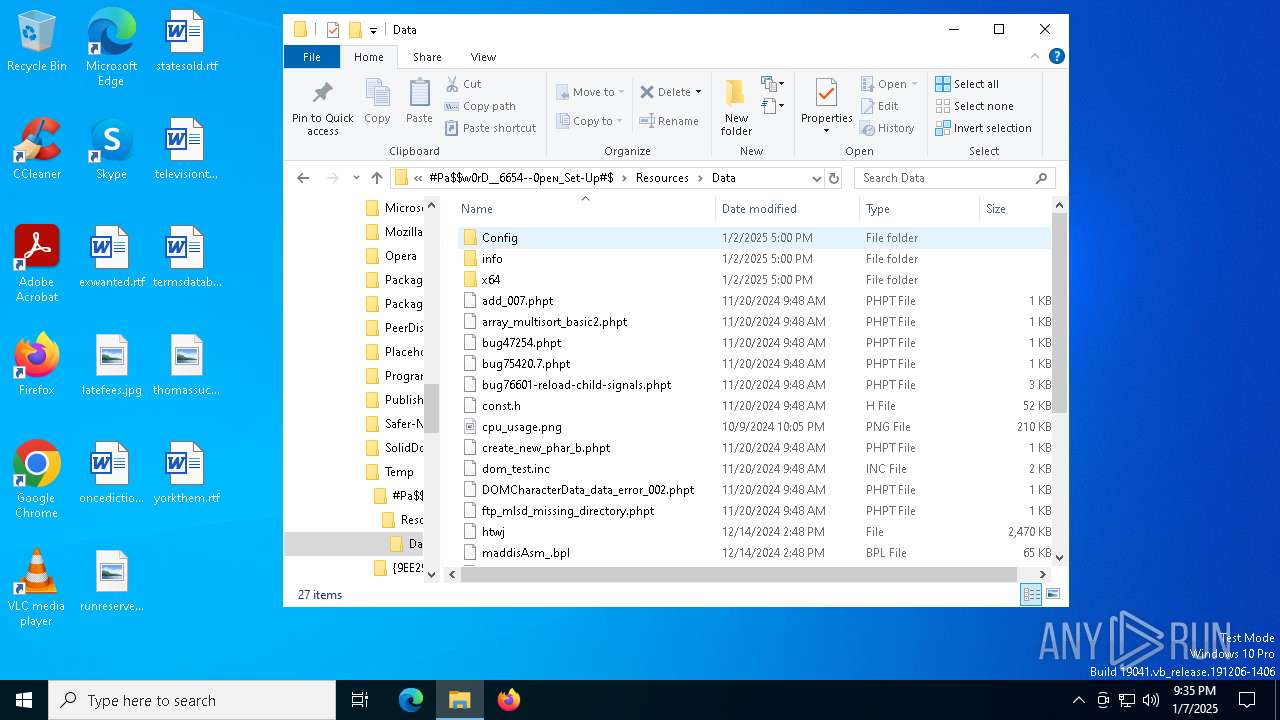
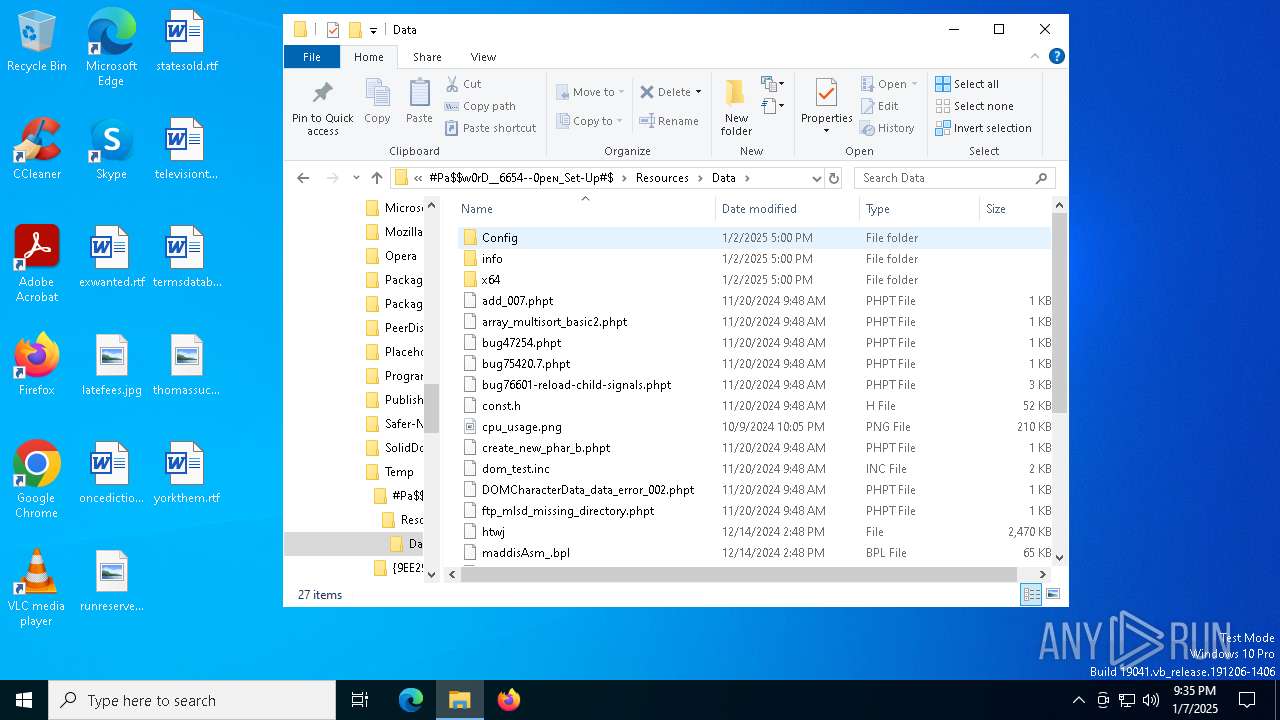
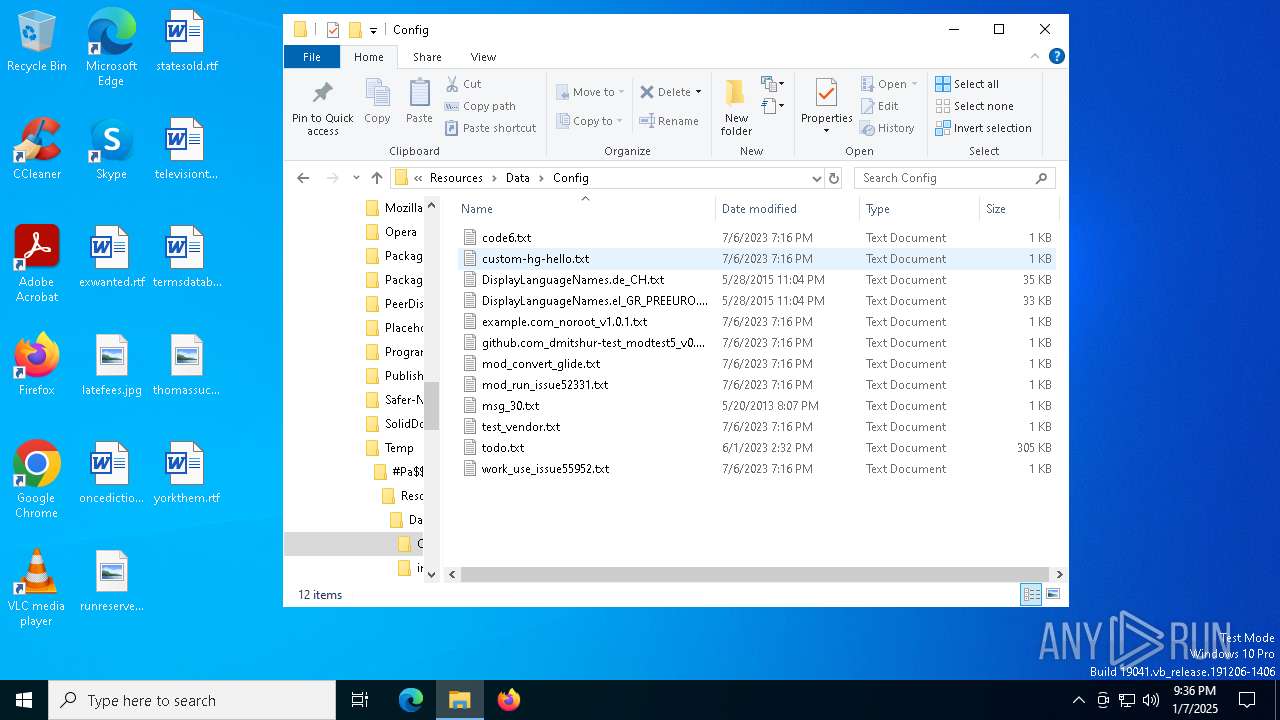
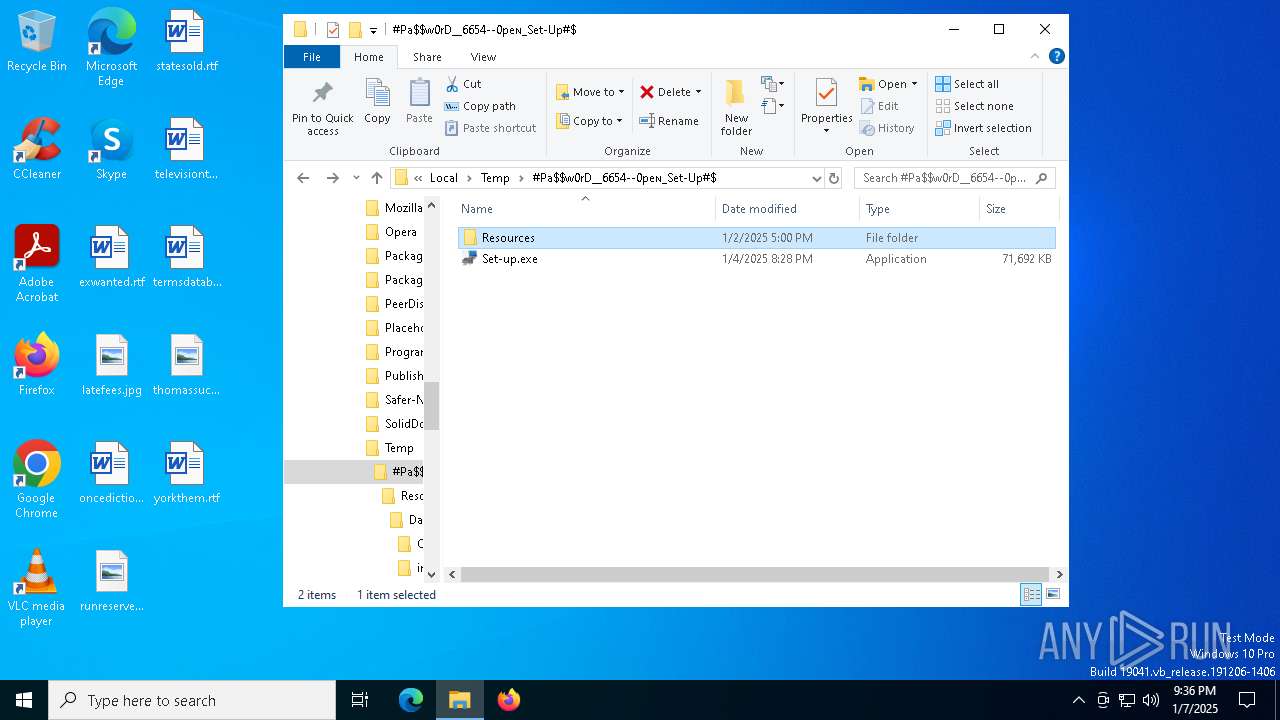
| File name: | #Pa$w0rD__6654--0peɴ_Set-Up#$.7z |
| Full analysis: | https://app.any.run/tasks/6b37bbf1-3d0a-4bc2-b72d-323a654c0106 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | January 07, 2025, 21:34:45 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | A387451874DF76D24BA542E7E04F0B89 |
| SHA1: | 939D3280ECB86CF1134C0C4C4EACB51BA9C783F4 |
| SHA256: | 695A8C1DDF37BB6C30618E4B10479CCCE363E29E95E43C774AC9B732D480A599 |
| SSDEEP: | 98304:4FqnAAaBe8xPjK7KLwM9rHjWwjh2Q+0kvX66A8moO2/42lQgS+OEXEMTHy7LTUrT:HYYgn21gjYpTsohF |
MALICIOUS
Executing a file with an untrusted certificate
- Set-up.exe (PID: 4444)
Connects to the CnC server
- svchost.exe (PID: 2192)
AutoIt loader has been detected (YARA)
- Establish.com (PID: 6772)
LUMMA mutex has been found
- Establish.com (PID: 6772)
Actions looks like stealing of personal data
- Establish.com (PID: 6772)
Steals credentials from Web Browsers
- Establish.com (PID: 6772)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2192)
SUSPICIOUS
The process creates files with name similar to system file names
- WinRAR.exe (PID: 4428)
Process drops legitimate windows executable
- WinRAR.exe (PID: 4428)
Reads security settings of Internet Explorer
- Set-up.exe (PID: 4444)
Executing commands from ".cmd" file
- Set-up.exe (PID: 4444)
Starts CMD.EXE for commands execution
- Set-up.exe (PID: 4444)
- cmd.exe (PID: 6004)
Get information on the list of running processes
- cmd.exe (PID: 6004)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 6004)
The executable file from the user directory is run by the CMD process
- Establish.com (PID: 6772)
Starts application with an unusual extension
- cmd.exe (PID: 6004)
Starts the AutoIt3 executable file
- cmd.exe (PID: 6004)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2192)
Application launched itself
- cmd.exe (PID: 6004)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 4428)
- Set-up.exe (PID: 4444)
Manual execution by a user
- WinRAR.exe (PID: 4428)
- Set-up.exe (PID: 4444)
- notepad.exe (PID: 1804)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4428)
Reads security settings of Internet Explorer
- notepad.exe (PID: 1804)
The sample compiled with english language support
- WinRAR.exe (PID: 4428)
Checks supported languages
- Set-up.exe (PID: 4444)
- Establish.com (PID: 6772)
- extrac32.exe (PID: 556)
Reads the computer name
- Set-up.exe (PID: 4444)
- extrac32.exe (PID: 556)
- Establish.com (PID: 6772)
Creates files or folders in the user directory
- Set-up.exe (PID: 4444)
- extrac32.exe (PID: 556)
Process checks computer location settings
- Set-up.exe (PID: 4444)
Creates a new folder
- cmd.exe (PID: 3732)
Reads mouse settings
- Establish.com (PID: 6772)
Reads the software policy settings
- Establish.com (PID: 6772)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|
Total processes
143
Monitored processes
19
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 556 | extrac32 /Y /E Relations | C:\Windows\SysWOW64\extrac32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® CAB File Extract Utility Exit code: 0 Version: 5.00 (WinBuild.160101.0800) Modules
| |||||||||||||||
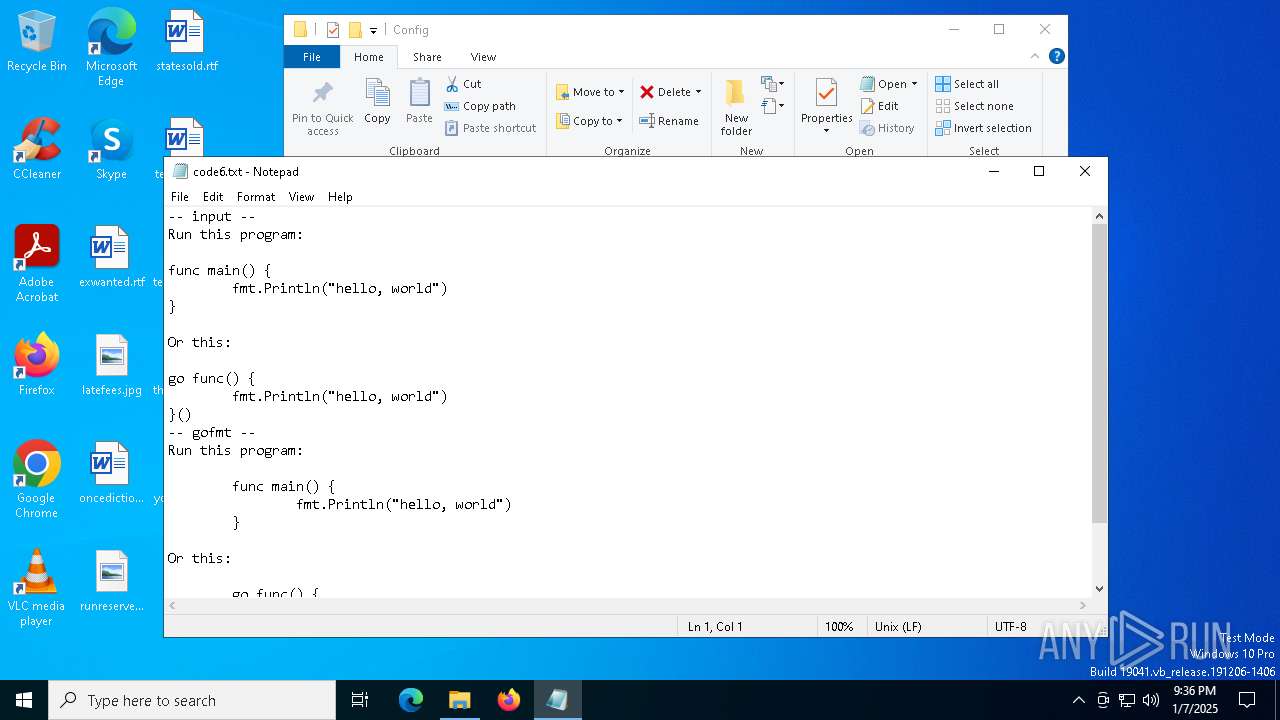
| 1804 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\#Pa$w0rD__6654--0peɴ_Set-Up#$\Resources\Data\Config\code6.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2060 | choice /d y /t 5 | C:\Windows\SysWOW64\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Offers the user a choice Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3488 | findstr /V "Onto" Lifetime | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3732 | cmd /c md 446130 | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4428 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\AppData\Local\Temp\#Pa$w0rD__6654--0peɴ_Set-Up#$.7z" C:\Users\admin\AppData\Local\Temp\#Pa$w0rD__6654--0peɴ_Set-Up#$\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 4444 | "C:\Users\admin\AppData\Local\Temp\#Pa$w0rD__6654--0peɴ_Set-Up#$\Set-up.exe" | C:\Users\admin\AppData\Local\Temp\#Pa$w0rD__6654--0peɴ_Set-Up#$\Set-up.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4976 | cmd /c copy /b 446130\Establish.com + Jon + Suggestion + Career + Biz + Build + Getting + Diving + Generation + Crossword + Betting + Lender 446130\Establish.com | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5236 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 998
Read events
2 986
Write events
12
Delete events
0
Modification events
| (PID) Process: | (6428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General\Toolbar\Layout |
| Operation: | write | Name: | Band76_0 |
Value: 4C000000730100000402000000000000F0F0F00000000000000000000000000000000000000000001003050000000000000000003B000000B402000000000000000000000000000001000000 | |||
| (PID) Process: | (6428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General\Toolbar\Layout |
| Operation: | write | Name: | Band76_1 |
Value: 4C000000730100000500000000000000F0F0F00000000000000000000000000000000000000000002A020C000000000000000000180000002A00000000000000000000000000000002000000 | |||
| (PID) Process: | (6428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General\Toolbar\Layout |
| Operation: | write | Name: | Band76_2 |
Value: 4C000000730100000400000000000000F0F0F0000000000000000000000000000000000000000000E40206000000000000000000180000006400000000000000000000000000000003000000 | |||
| (PID) Process: | (4428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (4428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
12
Suspicious files
44
Text files
60
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\#Pa$w0rD__6654--0peɴ_Set-Up#$\Resources\Data\Config\DisplayLanguageNames.de_CH.txt | text | |
MD5:25E1B7C45D5FB1DBE6FE4A533C4722CB | SHA256:8F302ADCBFC601A5410D7C09CEB3E2FF867E5EFC31204DBA637B25A090A1B55A | |||
| 4428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\#Pa$w0rD__6654--0peɴ_Set-Up#$\Resources\Data\bug75420.7.phpt | text | |
MD5:9B26AFADC7E9057F4A1CCAE684FBA4D0 | SHA256:14DF84CB519A2EAD9201DAAB647CB15EE3C4EBEC8523937A493FEFC4B43D00E0 | |||
| 4428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\#Pa$w0rD__6654--0peɴ_Set-Up#$\Resources\Data\Config\code6.txt | text | |
MD5:B9BABB266F182C22A4E2E80680B07B72 | SHA256:51FAB753A2F49BAB7B3D0745E27771DD9D58D5A5DD60C81390AE878FA95E094E | |||
| 4428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\#Pa$w0rD__6654--0peɴ_Set-Up#$\Resources\Data\Config\DisplayLanguageNames.el_GR_PREEURO.txt | text | |
MD5:46B3A1B71A26E53EA8869C855131A5FB | SHA256:210E62CF843F9E398E878FBD9502A68C66A2F2AB0EA2EB312B135C8F1807963D | |||
| 4428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\#Pa$w0rD__6654--0peɴ_Set-Up#$\Resources\Data\bug76601-reload-child-signals.phpt | text | |
MD5:CBB7D34D44AE04D69968E299CDFCDA71 | SHA256:E130AE7B8CFED7C1261E6BC1243724B59C86A241A57CDF8EAB3C97C11CD2481B | |||
| 4428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\#Pa$w0rD__6654--0peɴ_Set-Up#$\Resources\Data\Config\example.com_noroot_v1.0.1.txt | text | |
MD5:7288D609B53D947433D19929DC8A30F0 | SHA256:595975BC53A4F9094BB2793DD82BF51E80EBAF2D6B4C31D56FE77C0D9DB7533C | |||
| 4428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\#Pa$w0rD__6654--0peɴ_Set-Up#$\Resources\Data\bug47254.phpt | text | |
MD5:124566E01F194E82ED76A9621ED069C7 | SHA256:7158377B543F4B7EDBB25A4284CB580F10F995F42D69DA808FCC4D97C5881113 | |||
| 4428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\#Pa$w0rD__6654--0peɴ_Set-Up#$\Resources\Data\Config\mod_convert_glide.txt | text | |
MD5:F5DBC96107BE0223DFBE9EAD75586749 | SHA256:5E514F80EC4BBD5E93644F447B2E2B469F8EDF09C541B54AC52B2C25673154C5 | |||
| 4428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\#Pa$w0rD__6654--0peɴ_Set-Up#$\Resources\Data\Config\custom-hg-hello.txt | text | |
MD5:9716121C5042516CA7388FD526B81DF2 | SHA256:1058A99BD62D4B686C2F4602ACB85EAE6A5B6B05C2202150585A6E98CB1B2797 | |||
| 4428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\#Pa$w0rD__6654--0peɴ_Set-Up#$\Resources\Data\Config\test_vendor.txt | text | |
MD5:80AEC646E662ECDB8F7677B93F39AAB7 | SHA256:5912F1BA252BAC927720D0342E63B16A7E273B63E097BB3D1C8E68F9B0703742 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
41
DNS requests
31
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1468 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1468 | svchost.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3220 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7148 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7148 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1468 | svchost.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
4712 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | unknown |
1468 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | unknown |
5064 | SearchApp.exe | 2.19.96.128:443 | www.bing.com | Akamai International B.V. | DE | unknown |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1176 | svchost.exe | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (abruptyopsn .shop) |
2192 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (rabidcowse .shop) |
2192 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (noisycuttej .shop) |
2192 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (cloudewahsj .shop) |
2192 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (nearycrepso .shop) |
2192 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (framekgirus .shop) |
2192 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (tirepublicerj .shop) |
2192 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (wholersorie .shop) |