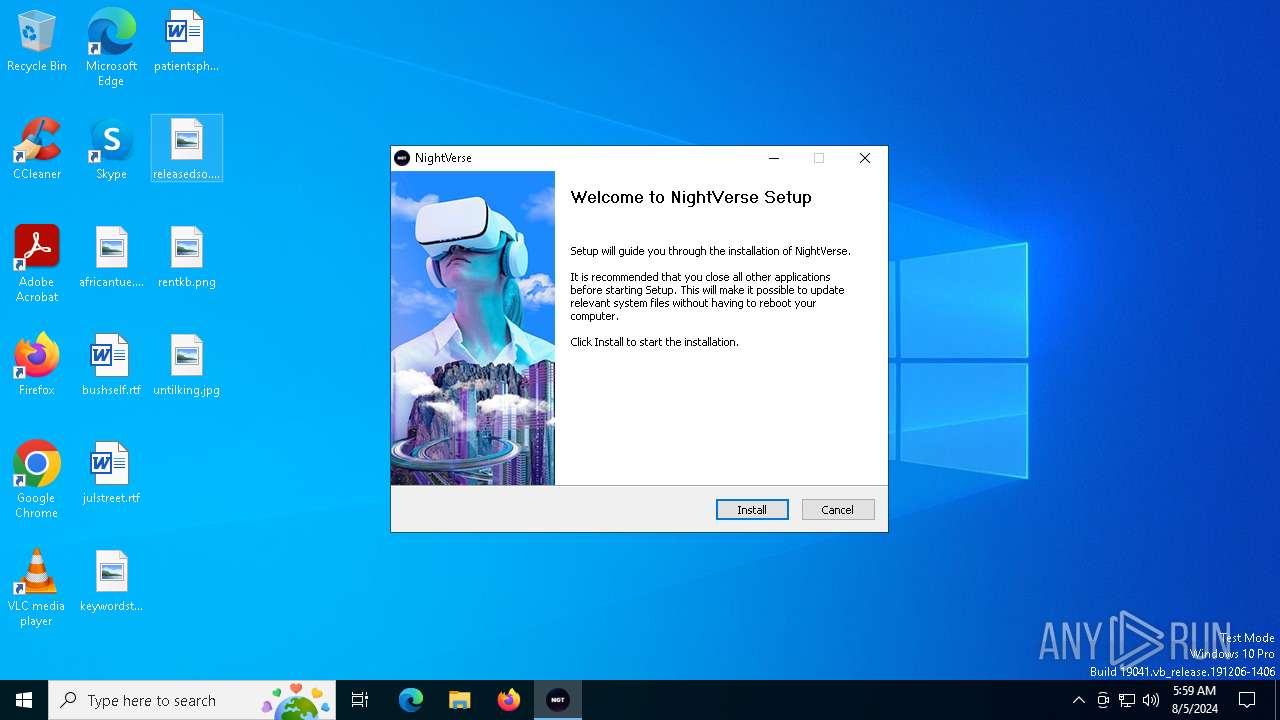
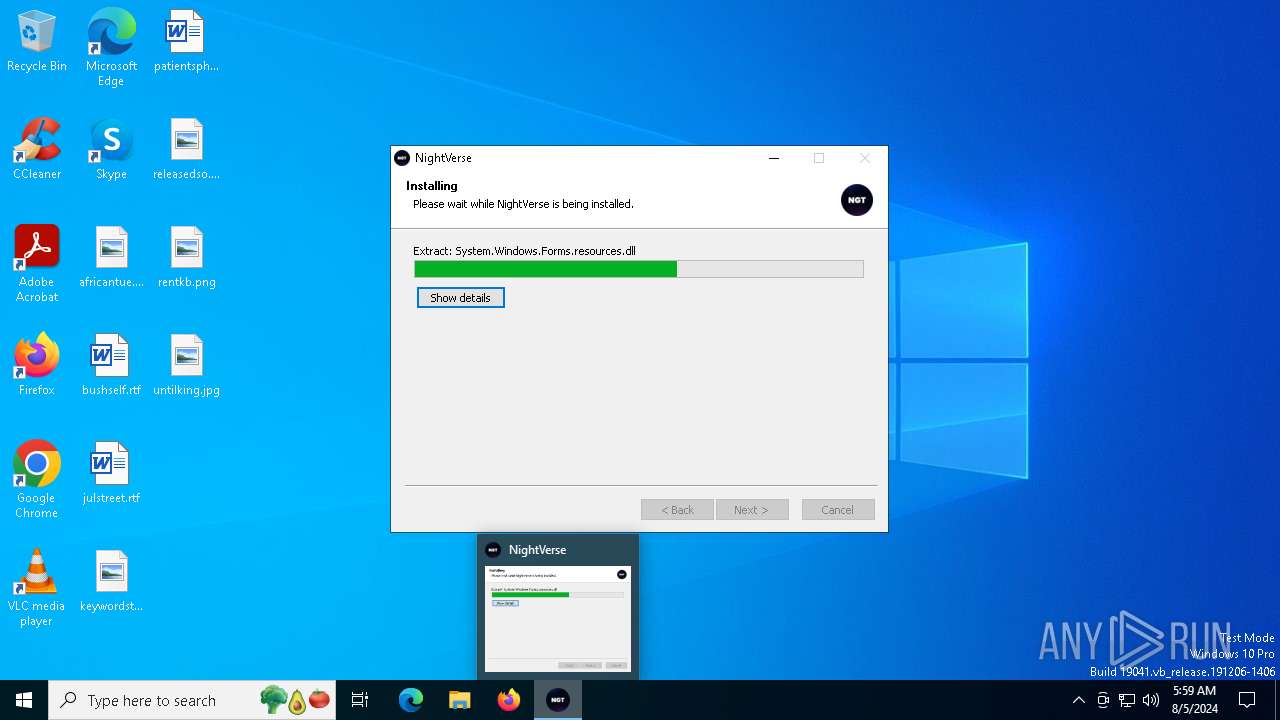
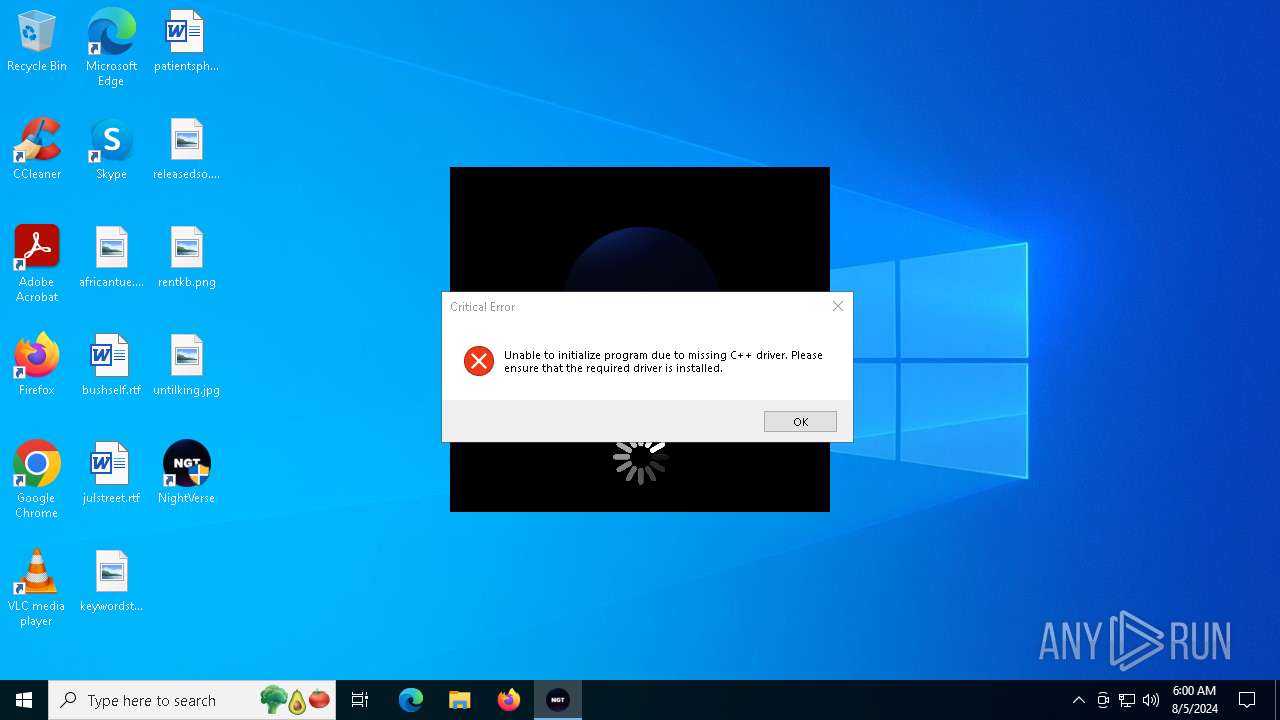
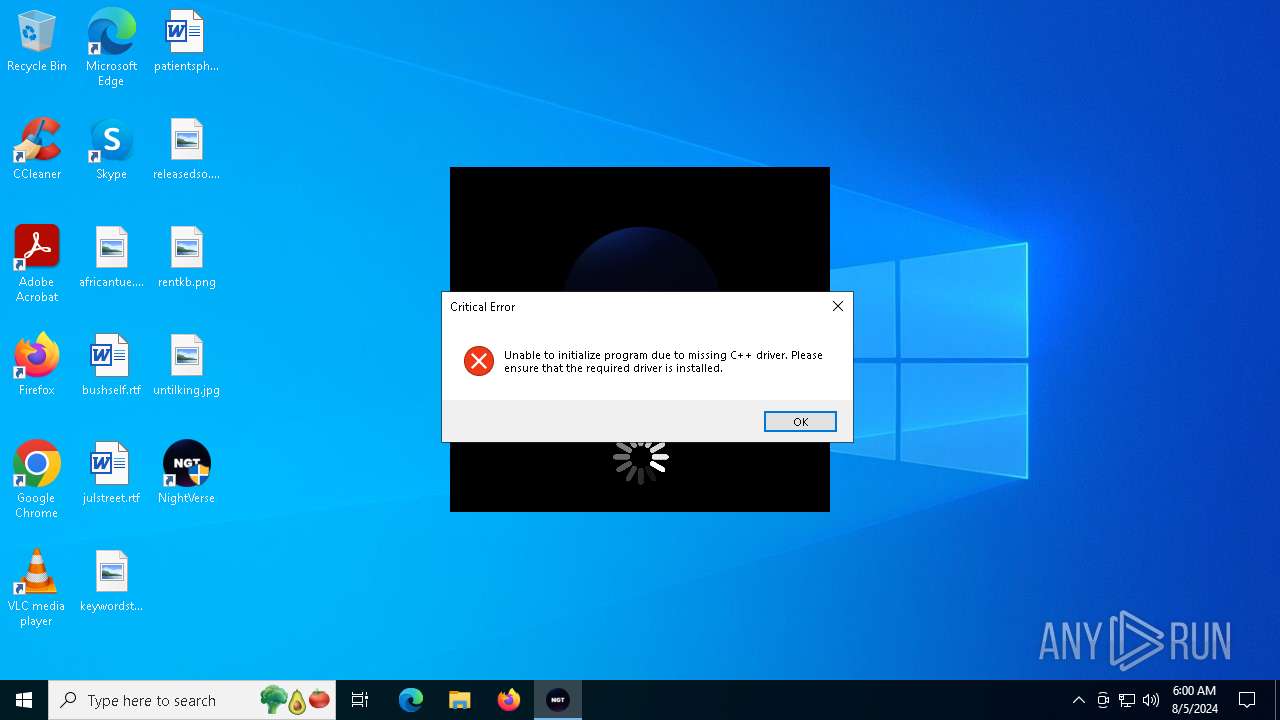
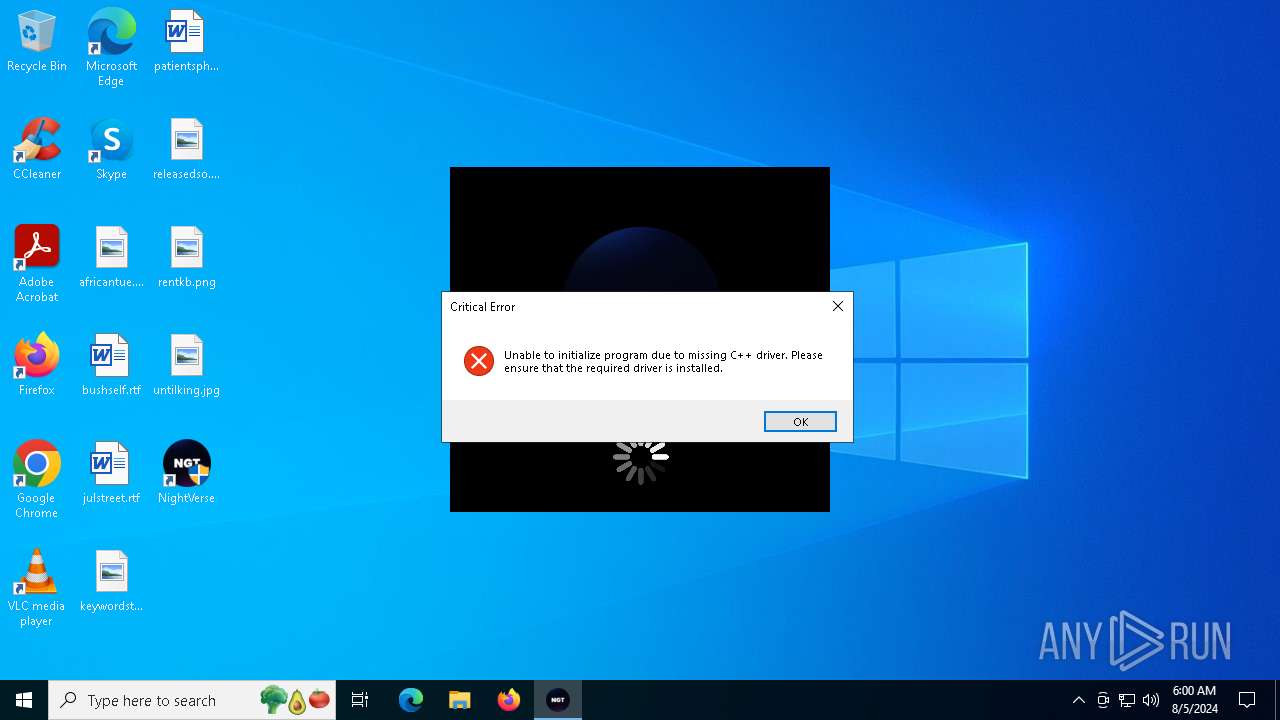
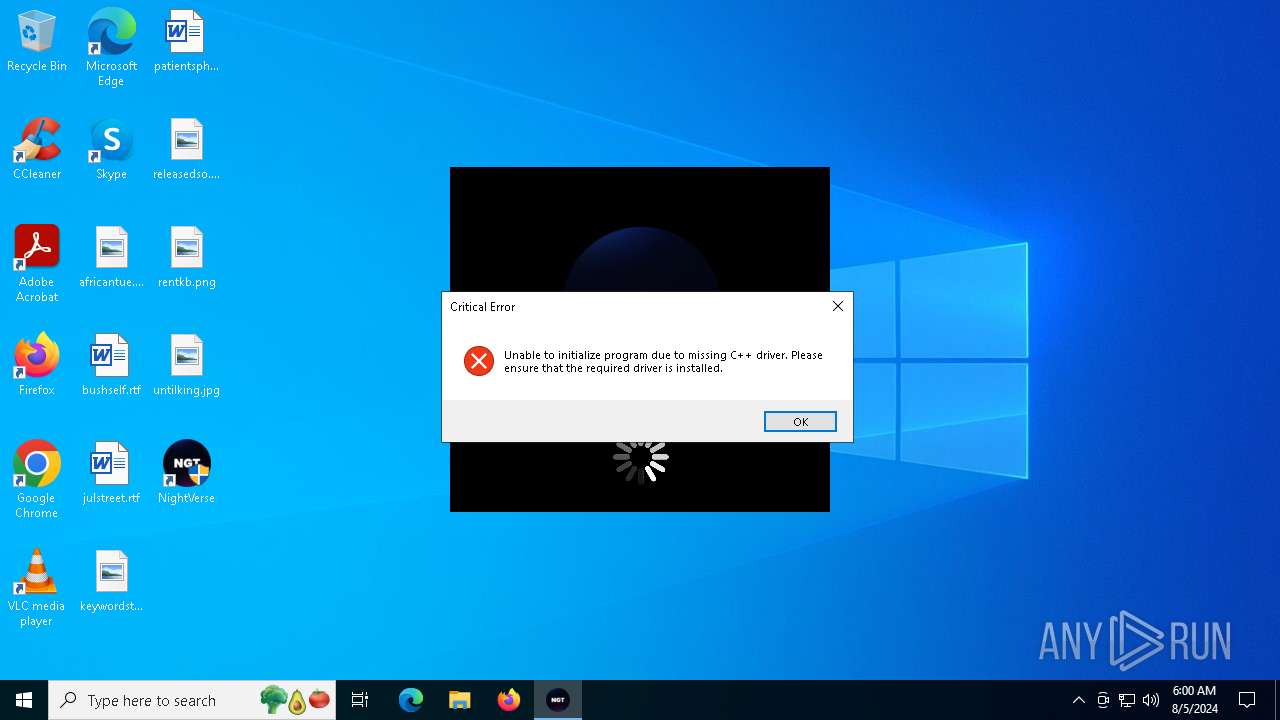
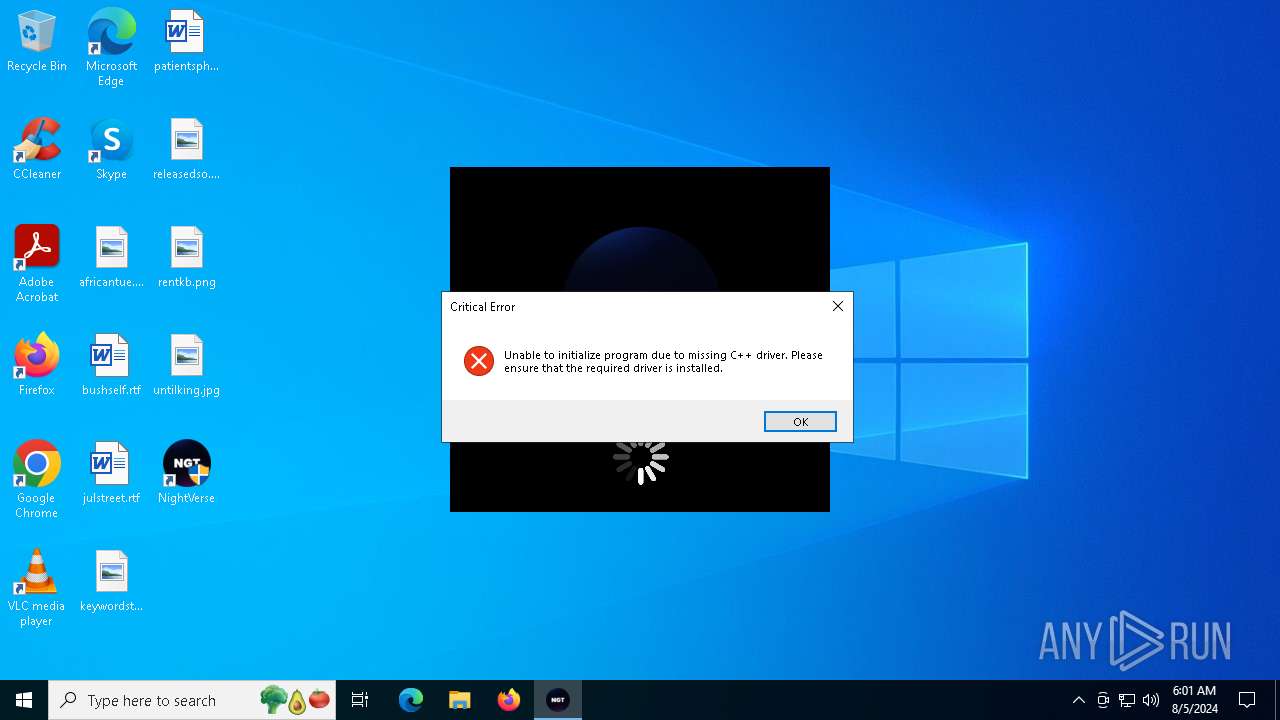
| File name: | NightVerse Setup.exe |
| Full analysis: | https://app.any.run/tasks/c69b5b79-4885-41e4-9ec8-29d513157825 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | August 05, 2024, 05:58:46 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 66A83A3A5E3D36A47A847B8FC5D01C53 |
| SHA1: | A94B75EF8D674F31628ED6266471AECB8B925753 |
| SHA256: | 693A9860B2D4887E92BE1C28FE63953E0569317936DFCC50255E494E45B6E933 |
| SSDEEP: | 393216:GxduNwV/RgqGxl8mM0SECa+NjiDwtNv/H23TlBKDxwBbruL+3w:sjV6qGx64SECahDwtt2DqyBbrvw |
MALICIOUS
Adds path to the Windows Defender exclusion list
- NightVerse.exe (PID: 4920)
- explorer.exe (PID: 6160)
Drops the executable file immediately after the start
- NightVerse.exe (PID: 4920)
- NightVerse Setup.exe (PID: 6648)
- msiexec.exe (PID: 7056)
- dpaw.exe (PID: 4788)
- scr_previw.exe (PID: 5196)
Stealers network behavior
- explorer.exe (PID: 2388)
- OOBE-Maintenance.exe (PID: 2768)
- explorer.exe (PID: 6160)
Connects to the CnC server
- explorer.exe (PID: 2388)
STEALC has been detected (SURICATA)
- explorer.exe (PID: 2388)
Steals credentials from Web Browsers
- explorer.exe (PID: 2388)
RHADAMANTHYS has been detected (SURICATA)
- OpenWith.exe (PID: 6292)
- OOBE-Maintenance.exe (PID: 2768)
RHADAMANTHYS has been detected (YARA)
- OOBE-Maintenance.exe (PID: 2768)
- rekeywiz.exe (PID: 6988)
ASYNCRAT has been detected (SURICATA)
- AppLaunch.exe (PID: 6368)
DANABOT has been detected (YARA)
- rekeywiz.exe (PID: 6988)
- explorer.exe (PID: 6160)
ASYNCRAT has been detected (YARA)
- AppLaunch.exe (PID: 6368)
Actions looks like stealing of personal data
- explorer.exe (PID: 6160)
- OOBE-Maintenance.exe (PID: 2768)
- explorer.exe (PID: 2388)
Change Internet Settings
- explorer.exe (PID: 6160)
DANABOT has been detected (SURICATA)
- explorer.exe (PID: 6160)
SUSPICIOUS
Process drops legitimate windows executable
- NightVerse Setup.exe (PID: 6648)
- explorer.exe (PID: 2388)
- msiexec.exe (PID: 7056)
- dpaw.exe (PID: 4788)
- scr_previw.exe (PID: 5196)
Executable content was dropped or overwritten
- NightVerse Setup.exe (PID: 6648)
- NightVerse.exe (PID: 4920)
- explorer.exe (PID: 2388)
- dpaw.exe (PID: 4788)
- scr_previw.exe (PID: 5196)
The process creates files with name similar to system file names
- NightVerse Setup.exe (PID: 6648)
The process drops C-runtime libraries
- NightVerse Setup.exe (PID: 6648)
- explorer.exe (PID: 2388)
Malware-specific behavior (creating "System.dll" in Temp)
- NightVerse Setup.exe (PID: 6648)
Creates a software uninstall entry
- NightVerse Setup.exe (PID: 6648)
Script adds exclusion path to Windows Defender
- NightVerse.exe (PID: 4920)
- explorer.exe (PID: 6160)
Starts POWERSHELL.EXE for commands execution
- NightVerse.exe (PID: 4920)
- explorer.exe (PID: 6160)
Checks for external IP
- svchost.exe (PID: 2256)
Starts CMD.EXE for commands execution
- snss1.exe (PID: 7008)
- snss2.exe (PID: 5408)
- dpaw.exe (PID: 7152)
- scr_previw.exe (PID: 6700)
Searches for installed software
- explorer.exe (PID: 2388)
- OOBE-Maintenance.exe (PID: 2768)
Windows Defender mutex has been found
- explorer.exe (PID: 2388)
Potential Corporate Privacy Violation
- explorer.exe (PID: 2388)
Contacting a server suspected of hosting an CnC
- explorer.exe (PID: 2388)
- OpenWith.exe (PID: 6292)
- OOBE-Maintenance.exe (PID: 2768)
- AppLaunch.exe (PID: 6368)
- explorer.exe (PID: 6160)
Process requests binary or script from the Internet
- explorer.exe (PID: 2388)
The process drops Mozilla's DLL files
- explorer.exe (PID: 2388)
The process checks if it is being run in the virtual environment
- OpenWith.exe (PID: 6292)
Connects to the server without a host name
- explorer.exe (PID: 2388)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 7056)
Loads DLL from Mozilla Firefox
- OOBE-Maintenance.exe (PID: 2768)
Starts itself from another location
- dpaw.exe (PID: 4788)
- scr_previw.exe (PID: 5196)
Connects to unusual port
- AppLaunch.exe (PID: 6368)
There is functionality for communication over UDP network (YARA)
- rekeywiz.exe (PID: 6988)
- explorer.exe (PID: 6160)
Found regular expressions for crypto-addresses (YARA)
- explorer.exe (PID: 6168)
Creates or modifies Windows services
- explorer.exe (PID: 6160)
Executes as Windows Service
- explorer.exe (PID: 6448)
Adds/modifies Windows certificates
- explorer.exe (PID: 6160)
INFO
Creates files in the program directory
- NightVerse Setup.exe (PID: 6648)
- NightVerse.exe (PID: 4920)
- explorer.exe (PID: 2388)
- dpaw.exe (PID: 4788)
- scr_previw.exe (PID: 5196)
Reads the computer name
- NightVerse Setup.exe (PID: 6648)
- NightVerse.exe (PID: 4920)
- snss1.exe (PID: 7008)
- snss2.exe (PID: 5408)
- msiexec.exe (PID: 7056)
- dpaw.exe (PID: 4788)
- dpaw.exe (PID: 7152)
- scr_previw.exe (PID: 5196)
- scr_previw.exe (PID: 6700)
- AppLaunch.exe (PID: 6368)
Creates files or folders in the user directory
- NightVerse Setup.exe (PID: 6648)
- explorer.exe (PID: 2388)
- OOBE-Maintenance.exe (PID: 2768)
- msiexec.exe (PID: 7056)
Checks supported languages
- NightVerse Setup.exe (PID: 6648)
- NightVerse.exe (PID: 4920)
- snss1.exe (PID: 7008)
- snss2.exe (PID: 5408)
- msiexec.exe (PID: 7056)
- dpaw.exe (PID: 7152)
- dpaw.exe (PID: 4788)
- scr_previw.exe (PID: 5196)
- wmpnscfg.exe (PID: 6816)
- scr_previw.exe (PID: 6700)
- AppLaunch.exe (PID: 6368)
Create files in a temporary directory
- NightVerse Setup.exe (PID: 6648)
- NightVerse.exe (PID: 4920)
- snss1.exe (PID: 7008)
- snss2.exe (PID: 5408)
- dpaw.exe (PID: 7152)
- scr_previw.exe (PID: 6700)
Reads the machine GUID from the registry
- NightVerse.exe (PID: 4920)
- wmpnscfg.exe (PID: 6816)
- AppLaunch.exe (PID: 6368)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6168)
- powershell.exe (PID: 3272)
- powershell.exe (PID: 1044)
- powershell.exe (PID: 2132)
- powershell.exe (PID: 6200)
Reads the software policy settings
- NightVerse.exe (PID: 4920)
- AppLaunch.exe (PID: 6368)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6168)
- powershell.exe (PID: 2132)
- powershell.exe (PID: 3272)
- powershell.exe (PID: 1044)
- powershell.exe (PID: 6200)
Checks proxy server information
- NightVerse.exe (PID: 4920)
- explorer.exe (PID: 2388)
- explorer.exe (PID: 6160)
Reads mouse settings
- snss1.exe (PID: 7008)
Potential remote process memory writing (Base64 Encoded 'WriteProcessMemory')
- NightVerse.exe (PID: 4920)
Potential remote process memory interaction (Base64 Encoded 'VirtualAllocEx')
- NightVerse.exe (PID: 4920)
Potential access to remote process (Base64 Encoded 'OpenProcess')
- NightVerse.exe (PID: 4920)
Potential library load (Base64 Encoded 'LoadLibrary')
- NightVerse.exe (PID: 4920)
Potential dynamic function import (Base64 Encoded 'GetProcAddress')
- NightVerse.exe (PID: 4920)
Reads security settings of Internet Explorer
- explorer.exe (PID: 2388)
- OOBE-Maintenance.exe (PID: 2768)
- explorer.exe (PID: 6160)
.NET Reactor protector has been detected
- NightVerse.exe (PID: 4920)
Potential remote process memory reading (Base64 Encoded 'ReadProcessMemory')
- NightVerse.exe (PID: 4920)
Drops the executable file immediately after the start
- explorer.exe (PID: 2388)
Reads Microsoft Office registry keys
- OOBE-Maintenance.exe (PID: 2768)
Executable content was dropped or overwritten
- msiexec.exe (PID: 7056)
Creates a software uninstall entry
- msiexec.exe (PID: 7056)
Reads Environment values
- AppLaunch.exe (PID: 6368)
Reads Windows Product ID
- explorer.exe (PID: 6160)
Reads the time zone
- explorer.exe (PID: 6448)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
AsyncRat
(PID) Process(6368) AppLaunch.exe
C2 (1)85.192.63.68
Ports (1)8245
Version0.5.8
BotnetDefault
Options
AutoRunfalse
MutexLFs3tAXovKDK
InstallFolder%AppData%
BSoDfalse
AntiVMtrue
Certificates
Cert1MIIE4DCCAsigAwIBAgIQALLvjtCZHzFARtdMuD4D9TANBgkqhkiG9w0BAQ0FADARMQ8wDQYDVQQDDAZTZXJ2ZXIwIBcNMjQwNzEyMDgxODM0WhgPOTk5OTEyMzEyMzU5NTlaMBExDzANBgNVBAMMBlNlcnZlcjCCAiIwDQYJKoZIhvcNAQEBBQADggIPADCCAgoCggIBAKxbGertDiPtLHGFUcSq7TdyuJxLgKnGUeCtUxiI7P90/qmVfUd6ms0P/aCWQGKZCKv+/dT2ENEMSj8wkD94AETP3KvhXqPSvZA6...
Server_SignaturemGHK9NzT6383ckP8iN8yBNB/fHCvRnFWdDYRpGfrAbiTtnlcUv34wU1KqF+JG5E8mWvhbjx/o9AktS+61WRoMDIer4ohBTpu9r9gHiQDQjCgMJIx/AC9Dm0B1Vf8ouDhFJdpzOqHuUlTFvrn36SeF2LMM3sF+f7sQzUeoIL1tTgRVuV1dRpY0eWblCGTj8szvu6dy5QUuoUSKRcgvJ27Gd4MI3VnJ596Hb6TNVy6sAa1/N5D7OGO2UwrDKMiRj57KUFyzQyxnrOy8vtwPYuTQvd0bvsIa7EuHB4wrT9bZxdJ...
Keys
AESedc7eeae28553d5aa15ef66746434def65f5caa5aae9471f897919e29ab07bb9
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
DanaBot
(PID) Process(6160) explorer.exe
C2 (3)81.19.137.7:443
23.94.225.177:443
89.169.52.59:443
Attributes
(19)0123456789ABCDEF0123456789abcdef
77777777777777777777777777777777
424a0d380332858ee55bdebc4af3789f
74e70a2b3ba1cf29d84b9b4bcf3e2e37
00001111222233334444555566667777
20142015201620172018201920202021
20222023202420252026202720282029
20302031203220332034203520362037
20132012201120102009200820072006
20052004200320022001200019991998
19971996199519941993199219911990
19891988198719861985198419831982
19811980197919781977197619751974
19731972197119701969196819671966
19651964196319621961196019591958
19571956195519541953195219511950
F70C77D46DEF9D46A6C7B43F0228AA7C
319BE5C4E9A566DE15DBA0957CFD9B65
F34493F167DD6A5B065D516FF3EB198E
Certificates
(29)-----BEGIN CERTIFICATE-----
MIICvDCCAiUCEEoZ0jiMglkcpV1zXxVd3KMwDQYJKoZIhvcNAQEEBQAwgZ4xHzAd
BgNVBAoTFlZlcmlTaWduIFRydXN0IE5ldHdvcmsxFzAVBgNVBAsTDlZlcmlTaWdu
LCBJbmMuMSwwKgYDVQQLEyNWZXJpU2lnbiBUaW1lIFN0YW1waW5nIFNlcnZpY2Ug
Um9vdDE0MDIGA1UECxMrTk8gTElBQklMSVRZIEFDQ0VQVEVELCAoYyk5NyBWZXJp
U2lnbiw...
-----BEGIN CERTIFICATE-----
MIIEZjCCA06gAwIBAgIQRL4Mi1AAJLQR0zYt4LNfGzANBgkqhkiG9w0BAQUFADCB
lTELMAkGA1UEBhMCVVMxCzAJBgNVBAgTAlVUMRcwFQYDVQQHEw5TYWx0IExha2Ug
Q2l0eTEeMBwGA1UEChMVVGhlIFVTRVJUUlVTVCBOZXR3b3JrMSEwHwYDVQQLExho
dHRwOi8vd3d3LnVzZXJ0cnVzdC5jb20xHTAbBgNVBAMTFFVUTi1VU0VSRmlyc3Qt
T2JqZWN...
-----BEGIN CERTIFICATE-----
MIIDVDCCAjygAwIBAgIDAjRWMA0GCSqGSIb3DQEBBQUAMEIxCzAJBgNVBAYTAlVT
MRYwFAYDVQQKEw1HZW9UcnVzdCBJbmMuMRswGQYDVQQDExJHZW9UcnVzdCBHbG9i
YWwgQ0EwHhcNMDIwNTIxMDQwMDAwWhcNMjIwNTIxMDQwMDAwWjBCMQswCQYDVQQG
EwJVUzEWMBQGA1UEChMNR2VvVHJ1c3QgSW5jLjEbMBkGA1UEAxMSR2VvVHJ1c3Qg
R2xvYmF...
-----BEGIN CERTIFICATE-----
MIIFujCCA6KgAwIBAgIJALtAHEP1Xk+wMA0GCSqGSIb3DQEBBQUAMEUxCzAJBgNV
BAYTAkNIMRUwEwYDVQQKEwxTd2lzc1NpZ24gQUcxHzAdBgNVBAMTFlN3aXNzU2ln
biBHb2xkIENBIC0gRzIwHhcNMDYxMDI1MDgzMDM1WhcNMzYxMDI1MDgzMDM1WjBF
MQswCQYDVQQGEwJDSDEVMBMGA1UEChMMU3dpc3NTaWduIEFHMR8wHQYDVQQDExZT
d2lzc1N...
-----BEGIN CERTIFICATE-----
MIIDdzCCAl+gAwIBAgIEAgAAuTANBgkqhkiG9w0BAQUFADBaMQswCQYDVQQGEwJJ
RTESMBAGA1UEChMJQmFsdGltb3JlMRMwEQYDVQQLEwpDeWJlclRydXN0MSIwIAYD
VQQDExlCYWx0aW1vcmUgQ3liZXJUcnVzdCBSb290MB4XDTAwMDUxMjE4NDYwMFoX
DTI1MDUxMjIzNTkwMFowWjELMAkGA1UEBhMCSUUxEjAQBgNVBAoTCUJhbHRpbW9y
ZTETMBE...
-----BEGIN CERTIFICATE-----
MIIDIDCCAomgAwIBAgIENd70zzANBgkqhkiG9w0BAQUFADBOMQswCQYDVQQGEwJV
UzEQMA4GA1UEChMHRXF1aWZheDEtMCsGA1UECxMkRXF1aWZheCBTZWN1cmUgQ2Vy
dGlmaWNhdGUgQXV0aG9yaXR5MB4XDTk4MDgyMjE2NDE1MVoXDTE4MDgyMjE2NDE1
MVowTjELMAkGA1UEBhMCVVMxEDAOBgNVBAoTB0VxdWlmYXgxLTArBgNVBAsTJEVx
dWlmYXg...
-----BEGIN CERTIFICATE-----
MIIFtzCCA5+gAwIBAgICBQkwDQYJKoZIhvcNAQEFBQAwRTELMAkGA1UEBhMCQk0x
GTAXBgNVBAoTEFF1b1ZhZGlzIExpbWl0ZWQxGzAZBgNVBAMTElF1b1ZhZGlzIFJv
b3QgQ0EgMjAeFw0wNjExMjQxODI3MDBaFw0zMTExMjQxODIzMzNaMEUxCzAJBgNV
BAYTAkJNMRkwFwYDVQQKExBRdW9WYWRpcyBMaW1pdGVkMRswGQYDVQQDExJRdW9W
YWRpcyB...
-----BEGIN CERTIFICATE-----
MIID3TCCAsWgAwIBAgIBADANBgkqhkiG9w0BAQsFADCBjzELMAkGA1UEBhMCVVMx
EDAOBgNVBAgTB0FyaXpvbmExEzARBgNVBAcTClNjb3R0c2RhbGUxJTAjBgNVBAoT
HFN0YXJmaWVsZCBUZWNobm9sb2dpZXMsIEluYy4xMjAwBgNVBAMTKVN0YXJmaWVs
ZCBSb290IENlcnRpZmljYXRlIEF1dGhvcml0eSAtIEcyMB4XDTA5MDkwMTAwMDAw
MFoXDTM...
-----BEGIN CERTIFICATE-----
MIIEkTCCA3mgAwIBAgIERWtQVDANBgkqhkiG9w0BAQUFADCBsDELMAkGA1UEBhMC
VVMxFjAUBgNVBAoTDUVudHJ1c3QsIEluYy4xOTA3BgNVBAsTMHd3dy5lbnRydXN0
Lm5ldC9DUFMgaXMgaW5jb3Jwb3JhdGVkIGJ5IHJlZmVyZW5jZTEfMB0GA1UECxMW
KGMpIDIwMDYgRW50cnVzdCwgSW5jLjEtMCsGA1UEAxMkRW50cnVzdCBSb290IENl
cnRpZml...
-----BEGIN CERTIFICATE-----
MIIDdTCCAl2gAwIBAgILBAAAAAABFUtaw5QwDQYJKoZIhvcNAQEFBQAwVzELMAkG
A1UEBhMCQkUxGTAXBgNVBAoTEEdsb2JhbFNpZ24gbnYtc2ExEDAOBgNVBAsTB1Jv
b3QgQ0ExGzAZBgNVBAMTEkdsb2JhbFNpZ24gUm9vdCBDQTAeFw05ODA5MDExMjAw
MDBaFw0yODAxMjgxMjAwMDBaMFcxCzAJBgNVBAYTAkJFMRkwFwYDVQQKExBHbG9i
YWxTaWd...
-----BEGIN CERTIFICATE-----
MIIF2DCCA8CgAwIBAgIQTKr5yttjb+Af907YWwOGnTANBgkqhkiG9w0BAQwFADCB
hTELMAkGA1UEBhMCR0IxGzAZBgNVBAgTEkdyZWF0ZXIgTWFuY2hlc3RlcjEQMA4G
A1UEBxMHU2FsZm9yZDEaMBgGA1UEChMRQ09NT0RPIENBIExpbWl0ZWQxKzApBgNV
BAMTIkNPTU9ETyBSU0EgQ2VydGlmaWNhdGlvbiBBdXRob3JpdHkwHhcNMTAwMTE5
MDAwMDA...
-----BEGIN CERTIFICATE-----
MIIEDzCCAvegAwIBAgIBADANBgkqhkiG9w0BAQUFADBoMQswCQYDVQQGEwJVUzEl
MCMGA1UEChMcU3RhcmZpZWxkIFRlY2hub2xvZ2llcywgSW5jLjEyMDAGA1UECxMp
U3RhcmZpZWxkIENsYXNzIDIgQ2VydGlmaWNhdGlvbiBBdXRob3JpdHkwHhcNMDQw
NjI5MTczOTE2WhcNMzQwNjI5MTczOTE2WjBoMQswCQYDVQQGEwJVUzElMCMGA1UE
ChMcU3R...
-----BEGIN CERTIFICATE-----
MIIDrzCCApegAwIBAgIQCDvgVpBCRrGhdWrJWZHHSjANBgkqhkiG9w0BAQUFADBh
MQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMRkwFwYDVQQLExB3
d3cuZGlnaWNlcnQuY29tMSAwHgYDVQQDExdEaWdpQ2VydCBHbG9iYWwgUm9vdCBD
QTAeFw0wNjExMTAwMDAwMDBaFw0zMTExMTAwMDAwMDBaMGExCzAJBgNVBAYTAlVT
MRUwEwY...
-----BEGIN CERTIFICATE-----
MIIEIDCCAwigAwIBAgIQNE7VVyDV7exJ9C/ON9srbTANBgkqhkiG9w0BAQUFADCB
qTELMAkGA1UEBhMCVVMxFTATBgNVBAoTDHRoYXd0ZSwgSW5jLjEoMCYGA1UECxMf
Q2VydGlmaWNhdGlvbiBTZXJ2aWNlcyBEaXZpc2lvbjE4MDYGA1UECxMvKGMpIDIw
MDYgdGhhd3RlLCBJbmMuIC0gRm9yIGF1dGhvcml6ZWQgdXNlIG9ubHkxHzAdBgNV
BAMTFnR...
-----BEGIN CERTIFICATE-----
MIIEPjCCAyagAwIBAgIESlOMKDANBgkqhkiG9w0BAQsFADCBvjELMAkGA1UEBhMC
VVMxFjAUBgNVBAoTDUVudHJ1c3QsIEluYy4xKDAmBgNVBAsTH1NlZSB3d3cuZW50
cnVzdC5uZXQvbGVnYWwtdGVybXMxOTA3BgNVBAsTMChjKSAyMDA5IEVudHJ1c3Qs
IEluYy4gLSBmb3IgYXV0aG9yaXplZCB1c2Ugb25seTEyMDAGA1UEAxMpRW50cnVz
dCBSb29...
-----BEGIN CERTIFICATE-----
MIIDuDCCAqCgAwIBAgIQDPCOXAgWpa1Cf/DrJxhZ0DANBgkqhkiG9w0BAQUFADBI
MQswCQYDVQQGEwJVUzEgMB4GA1UEChMXU2VjdXJlVHJ1c3QgQ29ycG9yYXRpb24x
FzAVBgNVBAMTDlNlY3VyZVRydXN0IENBMB4XDTA2MTEwNzE5MzExOFoXDTI5MTIz
MTE5NDA1NVowSDELMAkGA1UEBhMCVVMxIDAeBgNVBAoTF1NlY3VyZVRydXN0IENv
cnBvcmF...
-----BEGIN CERTIFICATE-----
MIIDnzCCAoegAwIBAgIBJjANBgkqhkiG9w0BAQUFADBxMQswCQYDVQQGEwJERTEc
MBoGA1UEChMTRGV1dHNjaGUgVGVsZWtvbSBBRzEfMB0GA1UECxMWVC1UZWxlU2Vj
IFRydXN0IENlbnRlcjEjMCEGA1UEAxMaRGV1dHNjaGUgVGVsZWtvbSBSb290IENB
IDIwHhcNOTkwNzA5MTIxMTAwWhcNMTkwNzA5MjM1OTAwWjBxMQswCQYDVQQGEwJE
RTEcMBo...
-----BEGIN CERTIFICATE-----
MIICPDCCAaUCEHC65B0Q2Sk0tjjKewPMur8wDQYJKoZIhvcNAQECBQAwXzELMAkG
A1UEBhMCVVMxFzAVBgNVBAoTDlZlcmlTaWduLCBJbmMuMTcwNQYDVQQLEy5DbGFz
cyAzIFB1YmxpYyBQcmltYXJ5IENlcnRpZmljYXRpb24gQXV0aG9yaXR5MB4XDTk2
MDEyOTAwMDAwMFoXDTI4MDgwMTIzNTk1OVowXzELMAkGA1UEBhMCVVMxFzAVBgNV
BAoTDlZ...
-----BEGIN CERTIFICATE-----
MIIDkjCCAnqgAwIBAgIRAIW9S/PY2uNp9pTXX8OlRCMwDQYJKoZIhvcNAQEFBQAw
PTELMAkGA1UEBhMCRlIxETAPBgNVBAoTCENlcnRwbHVzMRswGQYDVQQDExJDbGFz
cyAyIFByaW1hcnkgQ0EwHhcNOTkwNzA3MTcwNTAwWhcNMTkwNzA2MjM1OTU5WjA9
MQswCQYDVQQGEwJGUjERMA8GA1UEChMIQ2VydHBsdXMxGzAZBgNVBAMTEkNsYXNz
IDIgUHJ...
-----BEGIN CERTIFICATE-----
MIIDJzCCApCgAwIBAgIBATANBgkqhkiG9w0BAQQFADCBzjELMAkGA1UEBhMCWkEx
FTATBgNVBAgTDFdlc3Rlcm4gQ2FwZTESMBAGA1UEBxMJQ2FwZSBUb3duMR0wGwYD
VQQKExRUaGF3dGUgQ29uc3VsdGluZyBjYzEoMCYGA1UECxMfQ2VydGlmaWNhdGlv
biBTZXJ2aWNlcyBEaXZpc2lvbjEhMB8GA1UEAxMYVGhhd3RlIFByZW1pdW0gU2Vy
dmVyIEN...
-----BEGIN CERTIFICATE-----
MIIDxTCCAq2gAwIBAgIQAqxcJmoLQJuPC3nyrkYldzANBgkqhkiG9w0BAQUFADBs
MQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMRkwFwYDVQQLExB3
d3cuZGlnaWNlcnQuY29tMSswKQYDVQQDEyJEaWdpQ2VydCBIaWdoIEFzc3VyYW5j
ZSBFViBSb290IENBMB4XDTA2MTExMDAwMDAwMFoXDTMxMTExMDAwMDAwMFowbDEL
MAkGA1U...
-----BEGIN CERTIFICATE-----
MIIEKjCCAxKgAwIBAgIEOGPe+DANBgkqhkiG9w0BAQUFADCBtDEUMBIGA1UEChML
RW50cnVzdC5uZXQxQDA+BgNVBAsUN3d3dy5lbnRydXN0Lm5ldC9DUFNfMjA0OCBp
bmNvcnAuIGJ5IHJlZi4gKGxpbWl0cyBsaWFiLikxJTAjBgNVBAsTHChjKSAxOTk5
IEVudHJ1c3QubmV0IExpbWl0ZWQxMzAxBgNVBAMTKkVudHJ1c3QubmV0IENlcnRp
ZmljYXR...
-----BEGIN CERTIFICATE-----
MIIE0zCCA7ugAwIBAgIQGNrRniZ96LtKIVjNzGs7SjANBgkqhkiG9w0BAQUFADCB
yjELMAkGA1UEBhMCVVMxFzAVBgNVBAoTDlZlcmlTaWduLCBJbmMuMR8wHQYDVQQL
ExZWZXJpU2lnbiBUcnVzdCBOZXR3b3JrMTowOAYDVQQLEzEoYykgMjAwNiBWZXJp
U2lnbiwgSW5jLiAtIEZvciBhdXRob3JpemVkIHVzZSBvbmx5MUUwQwYDVQQDEzxW
ZXJpU2l...
-----BEGIN CERTIFICATE-----
MIIDxTCCAq2gAwIBAgIBADANBgkqhkiG9w0BAQsFADCBgzELMAkGA1UEBhMCVVMx
EDAOBgNVBAgTB0FyaXpvbmExEzARBgNVBAcTClNjb3R0c2RhbGUxGjAYBgNVBAoT
EUdvRGFkZHkuY29tLCBJbmMuMTEwLwYDVQQDEyhHbyBEYWRkeSBSb290IENlcnRp
ZmljYXRlIEF1dGhvcml0eSAtIEcyMB4XDTA5MDkwMTAwMDAwMFoXDTM3MTIzMTIz
NTk1OVo...
-----BEGIN CERTIFICATE-----
MIIHyTCCBbGgAwIBAgIBATANBgkqhkiG9w0BAQUFADB9MQswCQYDVQQGEwJJTDEW
MBQGA1UEChMNU3RhcnRDb20gTHRkLjErMCkGA1UECxMiU2VjdXJlIERpZ2l0YWwg
Q2VydGlmaWNhdGUgU2lnbmluZzEpMCcGA1UEAxMgU3RhcnRDb20gQ2VydGlmaWNh
dGlvbiBBdXRob3JpdHkwHhcNMDYwOTE3MTk0NjM2WhcNMzYwOTE3MTk0NjM2WjB9
MQswCQY...
-----BEGIN CERTIFICATE-----
MIIEADCCAuigAwIBAgIBADANBgkqhkiG9w0BAQUFADBjMQswCQYDVQQGEwJVUzEh
MB8GA1UEChMYVGhlIEdvIERhZGR5IEdyb3VwLCBJbmMuMTEwLwYDVQQLEyhHbyBE
YWRkeSBDbGFzcyAyIENlcnRpZmljYXRpb24gQXV0aG9yaXR5MB4XDTA0MDYyOTE3
MDYyMFoXDTM0MDYyOTE3MDYyMFowYzELMAkGA1UEBhMCVVMxITAfBgNVBAoTGFRo
ZSBHbyB...
-----BEGIN CERTIFICATE-----
MIIDtzCCAp+gAwIBAgIQDOfg5RfYRv6P5WD8G/AwOTANBgkqhkiG9w0BAQUFADBl
MQswCQYDVQQGEwJVUzEVMBMGA1UEChMMRGlnaUNlcnQgSW5jMRkwFwYDVQQLExB3
d3cuZGlnaWNlcnQuY29tMSQwIgYDVQQDExtEaWdpQ2VydCBBc3N1cmVkIElEIFJv
b3QgQ0EwHhcNMDYxMTEwMDAwMDAwWhcNMzExMTEwMDAwMDAwWjBlMQswCQYDVQQG
EwJVUzE...
-----BEGIN CERTIFICATE-----
MIIEdDCCA1ygAwIBAgIQRL4Mi1AAJLQR0zYq/mUK/TANBgkqhkiG9w0BAQUFADCB
lzELMAkGA1UEBhMCVVMxCzAJBgNVBAgTAlVUMRcwFQYDVQQHEw5TYWx0IExha2Ug
Q2l0eTEeMBwGA1UEChMVVGhlIFVTRVJUUlVTVCBOZXR3b3JrMSEwHwYDVQQLExho
dHRwOi8vd3d3LnVzZXJ0cnVzdC5jb20xHzAdBgNVBAMTFlVUTi1VU0VSRmlyc3Qt
SGFyZHd...
-----BEGIN CERTIFICATE-----
MIIENjCCAx6gAwIBAgIBATANBgkqhkiG9w0BAQUFADBvMQswCQYDVQQGEwJTRTEU
MBIGA1UEChMLQWRkVHJ1c3QgQUIxJjAkBgNVBAsTHUFkZFRydXN0IEV4dGVybmFs
IFRUUCBOZXR3b3JrMSIwIAYDVQQDExlBZGRUcnVzdCBFeHRlcm5hbCBDQSBSb290
MB4XDTAwMDUzMDEwNDgzOFoXDTIwMDUzMDEwNDgzOFowbzELMAkGA1UEBhMCU0Ux
FDASBgN...
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:07:02 02:09:43+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26624 |
| InitializedDataSize: | 139776 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x3645 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.2.0.0 |
| ProductVersionNumber: | 1.2.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | NightVerse Team |
| FileDescription: | NightVerse |
| FileVersion: | 1.2.0.0 |
| LegalCopyright: | Copyright 2024 © NightVerse |
| ProductName: | NightVerse |
Total processes
183
Monitored processes
43
Malicious processes
19
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1044 | "powershell" /command Add-MpPreference -ExclusionPath 'C:\Users\admin'; Add-MpPreference -ExclusionPath 'C:\Users\admin\AppData\Roaming' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | NightVerse.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1184 | C:\WINDOWS\SysWOW64\cmd.exe | C:\Windows\SysWOW64\cmd.exe | — | snss2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1488 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | OOBE-Maintenance.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2132 | "powershell" /command Add-MpPreference -ExclusionPath 'C:\Users\admin'; Add-MpPreference -ExclusionPath 'C:\Users\admin\AppData\Roaming' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | NightVerse.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2272 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2388 | C:\WINDOWS\SysWOW64\explorer.exe | C:\Windows\SysWOW64\explorer.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Explorer Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2532 | C:\WINDOWS\SysWOW64\cmd.exe | C:\Windows\SysWOW64\cmd.exe | — | snss1.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2628 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2768 | "C:\WINDOWS\system32\OOBE-Maintenance.exe" | C:\Windows\System32\OOBE-Maintenance.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: OOBE-Maintenance Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
58 492
Read events
57 911
Write events
562
Delete events
19
Modification events
| (PID) Process: | (6648) NightVerse Setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\NightVerse |
| Operation: | write | Name: | DisplayName |
Value: NightVerse | |||
| (PID) Process: | (6648) NightVerse Setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\NightVerse |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files (x86)\NightVerse\NightVerse.exe | |||
| (PID) Process: | (6648) NightVerse Setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\NightVerse |
| Operation: | write | Name: | DisplayVersion |
Value: 1.2.0.0 | |||
| (PID) Process: | (6648) NightVerse Setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\NightVerse |
| Operation: | write | Name: | Publisher |
Value: NightVerse Team | |||
| (PID) Process: | (6648) NightVerse Setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\NightVerse |
| Operation: | write | Name: | URLInfoAbout |
Value: | |||
| (PID) Process: | (6648) NightVerse Setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\NightVerse |
| Operation: | write | Name: | Installer Language |
Value: 1033 | |||
| (PID) Process: | (4920) NightVerse.exe | Key: | HKEY_CURRENT_USER\MicrosoftUpdatesService |
| Operation: | write | Name: | Count |
Value: 1 | |||
| (PID) Process: | (2388) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2388) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2388) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
487
Suspicious files
43
Text files
17
Unknown types
12
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6648 | NightVerse Setup.exe | C:\Users\admin\AppData\Local\Temp\nsj7973.tmp\ioSpecial.ini | ini | |
MD5:E2D5070BC28DB1AC745613689FF86067 | SHA256:D95AED234F932A1C48A2B1B0D98C60CA31F962310C03158E2884AB4DDD3EA1E0 | |||
| 6648 | NightVerse Setup.exe | C:\Users\admin\AppData\Local\Temp\nsj7973.tmp\LangDLL.dll | executable | |
MD5:50016010FB0D8DB2BC4CD258CEB43BE5 | SHA256:32230128C18574C1E860DFE4B17FE0334F685740E27BC182E0D525A8948C9C2E | |||
| 6648 | NightVerse Setup.exe | C:\Program Files (x86)\NightVerse\D3DCompiler_47_cor3.dll | executable | |
MD5:03A60A6652CAF4F49EA5912CE4E1B33C | SHA256:B23E7B820ED5C6EA7DCD77817E2CD79F1CEC9561D457172287EE634A8BD658C3 | |||
| 6648 | NightVerse Setup.exe | C:\Program Files (x86)\NightVerse\DirectWriteForwarder.dll | executable | |
MD5:69044C681EA1EEDCA54D13ED97E1452A | SHA256:778936B5BAF157C3A040955BC637936952E7B68C5AFF83536D4B613ED9691CDE | |||
| 6648 | NightVerse Setup.exe | C:\Program Files (x86)\NightVerse\Microsoft.DiaSymReader.Native.amd64.dll | executable | |
MD5:804B9539F7BE4ECE92993DC95C8486F5 | SHA256:76D0DA51C2ED6CE4DE34F0F703AF564CBEFD54766572A36B5A45494A88479E0B | |||
| 6648 | NightVerse Setup.exe | C:\Program Files (x86)\NightVerse\Microsoft.CSharp.dll | executable | |
MD5:8E7612CC8019D952A93D9B777E71B802 | SHA256:DF495F74456AD5AE30A5BAC440B4D3808FA2D13C377CCE1AFC0146B8319DED6E | |||
| 6648 | NightVerse Setup.exe | C:\Users\admin\AppData\Local\Temp\nsj7973.tmp\modern-wizard.bmp | image | |
MD5:E51AA821EBC60C88B030E4067378B4BE | SHA256:14C6A373AC1D2BC8B990656EF1C8F3B7A73E3058680E0E0143A6E1B57B182433 | |||
| 6648 | NightVerse Setup.exe | C:\Program Files (x86)\NightVerse\Microsoft.VisualBasic.dll | executable | |
MD5:E5CE0F3A5D15D8B6693724C40197A9FE | SHA256:9D20CA17355838FF3D2F3C89FBAF7C705BD01D297D1EB589489A84F6430DA894 | |||
| 6648 | NightVerse Setup.exe | C:\Users\admin\AppData\Local\Temp\nsj7973.tmp\InstallOptions.dll | executable | |
MD5:D095B082B7C5BA4665D40D9C5042AF6D | SHA256:B2091205E225FC07DAF1101218C64CE62A4690CACAC9C3D0644D12E93E4C213C | |||
| 6648 | NightVerse Setup.exe | C:\Program Files (x86)\NightVerse\Microsoft.VisualBasic.Core.dll | executable | |
MD5:3A037C21AF5742650933CEBF0521F3D6 | SHA256:34271825351D9871583DEAD758B44676EF2BAC56C4B7AC7124FADB087EA44F6E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
30
TCP/UDP connections
69
DNS requests
22
Threats
44
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2388 | explorer.exe | POST | 200 | 195.211.124.201:80 | http://195.211.124.201/be7c600e19a47f1c.php | unknown | — | — | unknown |
2388 | explorer.exe | POST | 200 | 195.211.124.201:80 | http://195.211.124.201/be7c600e19a47f1c.php | unknown | — | — | unknown |
2388 | explorer.exe | GET | 200 | 195.211.124.201:80 | http://195.211.124.201/a011f7f7085e3930/msvcp140.dll | unknown | — | — | unknown |
2388 | explorer.exe | GET | 200 | 195.211.124.201:80 | http://195.211.124.201/a011f7f7085e3930/freebl3.dll | unknown | — | — | unknown |
2388 | explorer.exe | GET | 200 | 195.211.124.201:80 | http://195.211.124.201/a011f7f7085e3930/mozglue.dll | unknown | — | — | unknown |
2388 | explorer.exe | GET | 200 | 195.211.124.201:80 | http://195.211.124.201/a011f7f7085e3930/nss3.dll | unknown | — | — | unknown |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2636 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2636 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6748 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1664 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5336 | SearchApp.exe | 2.23.209.179:443 | www.bing.com | Akamai International B.V. | GB | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2636 | svchost.exe | 40.126.31.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3260 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
th.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Potentially Bad Traffic | ET INFO External IP Lookup Domain in DNS Lookup (ipwho .is) |
2388 | explorer.exe | Malware Command and Control Activity Detected | STEALER [ANY.RUN] Stealc HTTP POST Request |
2388 | explorer.exe | Malware Command and Control Activity Detected | ET MALWARE Win32/Stealc Requesting browsers Config from C2 |
2388 | explorer.exe | Malware Command and Control Activity Detected | ET MALWARE Win32/Stealc Requesting plugins Config from C2 |
2388 | explorer.exe | Malware Command and Control Activity Detected | ET MALWARE [SEKOIA.IO] Win32/Stealc C2 Check-in |
2388 | explorer.exe | Malware Command and Control Activity Detected | ET MALWARE Win32/Stealc Submitting System Information to C2 |
2388 | explorer.exe | Potentially Bad Traffic | ET INFO Dotted Quad Host DLL Request |
2388 | explorer.exe | A suspicious filename was detected | ET HUNTING HTTP GET Request for sqlite3.dll - Possible Infostealer Activity |
2388 | explorer.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2388 | explorer.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
13 ETPRO signatures available at the full report