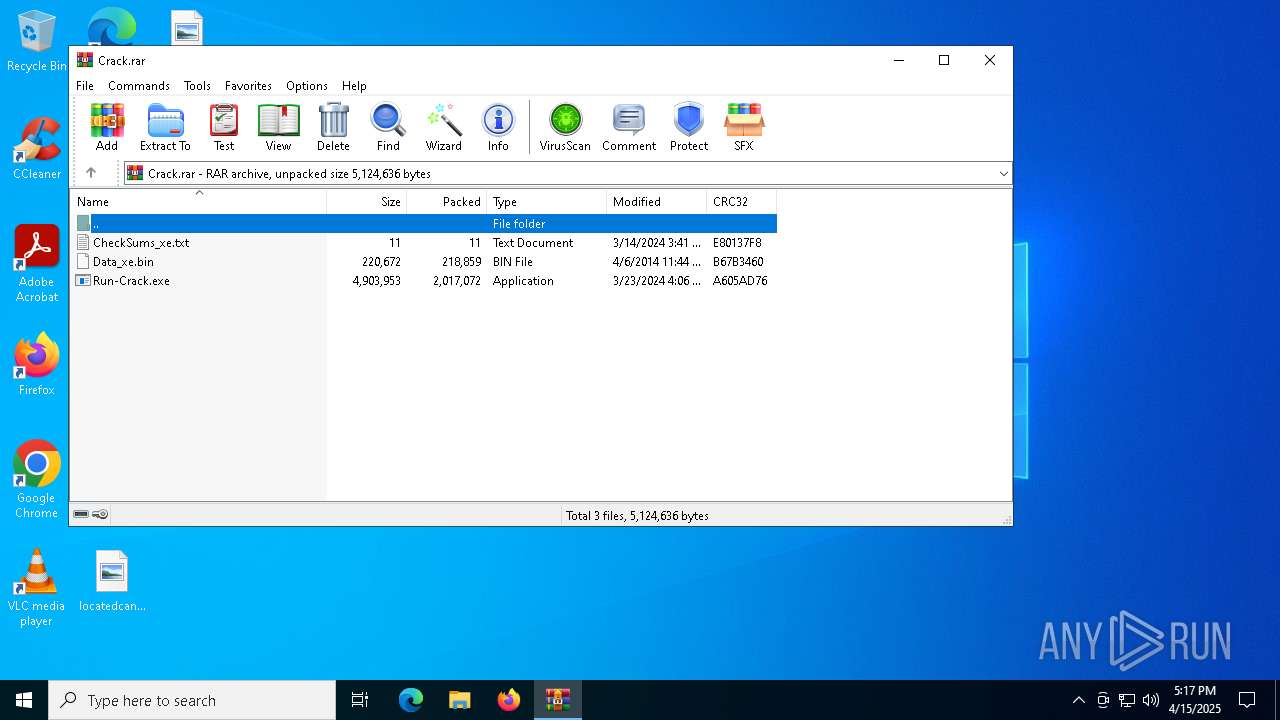
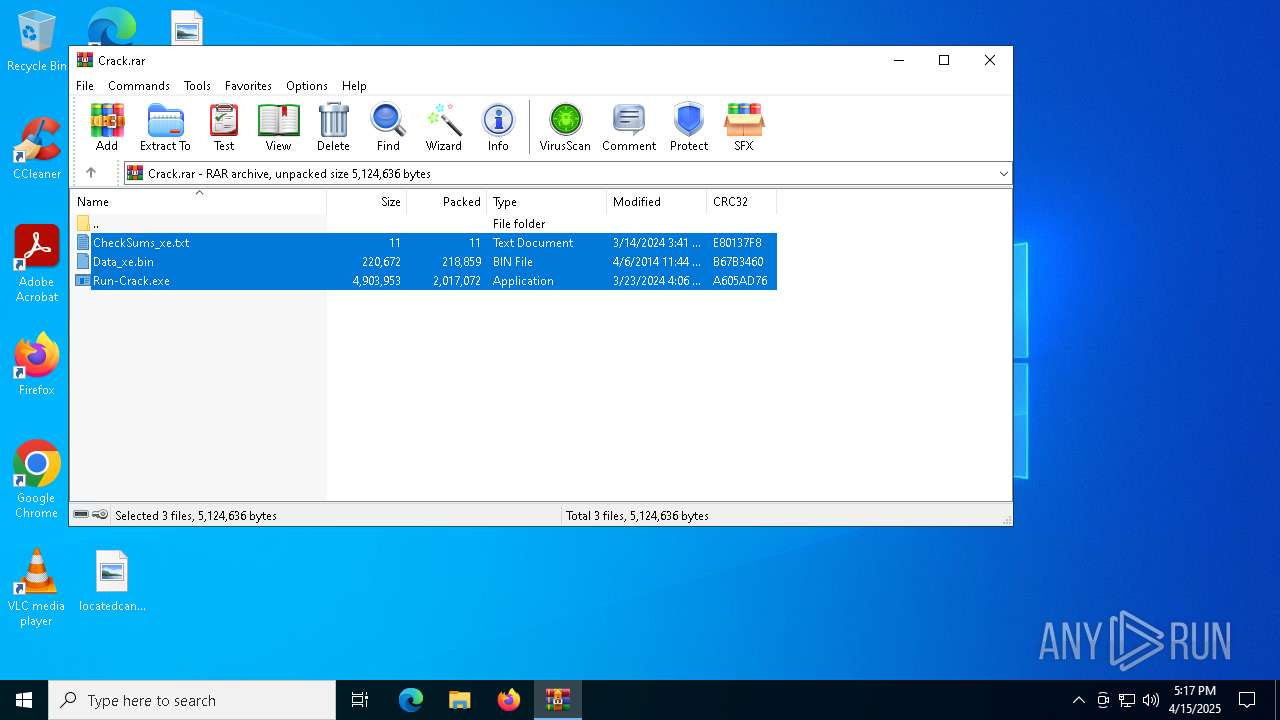
| File name: | Crack.rar |
| Full analysis: | https://app.any.run/tasks/778d15fe-f49d-4935-9510-c15d518ef04a |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | April 15, 2025, 17:17:15 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | B9509AE27DE55C440CEF3863E07EEF62 |
| SHA1: | 196A1BF991E7CFF2F8275889FAF2A5423D2483D2 |
| SHA256: | 6936993D55EBE741563D5EB0CF91DF0255C3407B17B00B6F33003C737ABF9BDE |
| SSDEEP: | 98304:JoZWm0pztF8SAVQBDlkP9g1W2EqHaTmthYzLa5ht5d/XpwaiaPON4r/pYRwKFz1K:lj |
MALICIOUS
Opens a text file (SCRIPT)
- msiexec.exe (PID: 7944)
Changes powershell execution policy (Bypass)
- msiexec.exe (PID: 8080)
Bypass execution policy to execute commands
- powershell.exe (PID: 8172)
Creates a new scheduled task via Registry
- msiexec.exe (PID: 8080)
Vulnerable driver has been detected
- WindowsService.exe (PID: 5892)
MINER has been detected (SURICATA)
- cmd.exe (PID: 680)
Connects to the CnC server
- cmd.exe (PID: 680)
SUSPICIOUS
Executable content was dropped or overwritten
- Run-Crack.exe (PID: 7660)
- WindowsService.exe (PID: 5892)
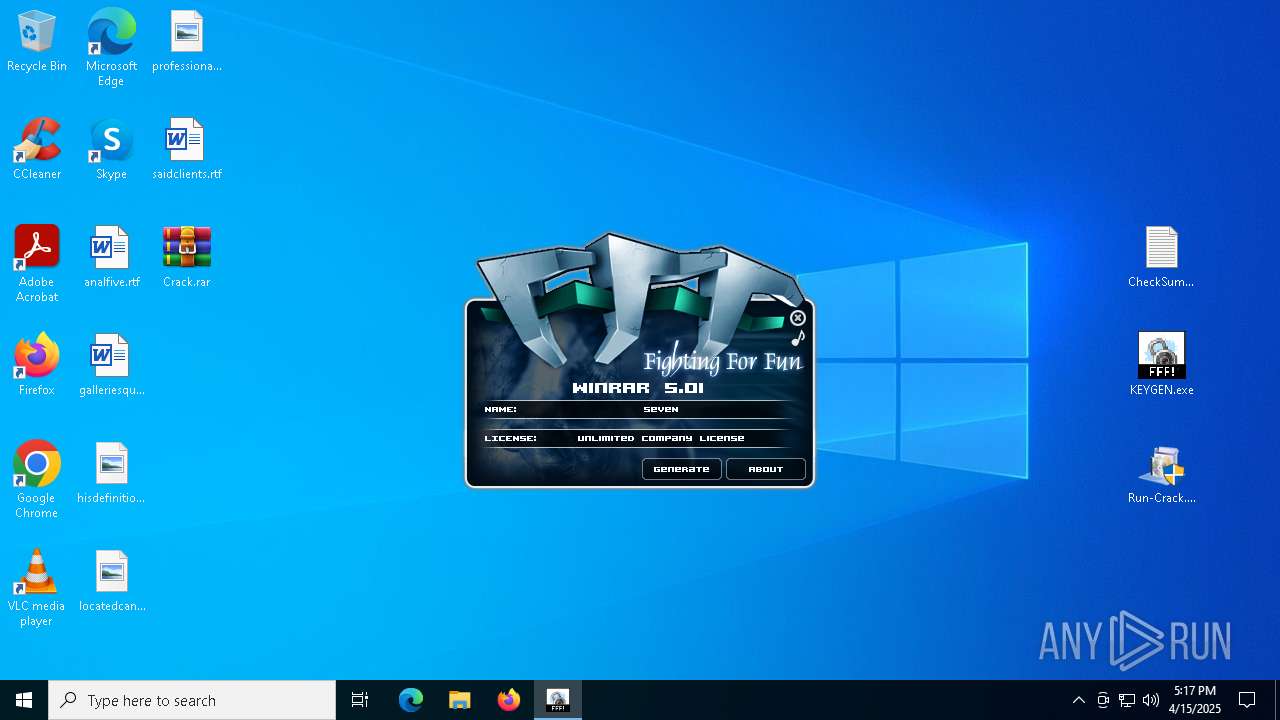
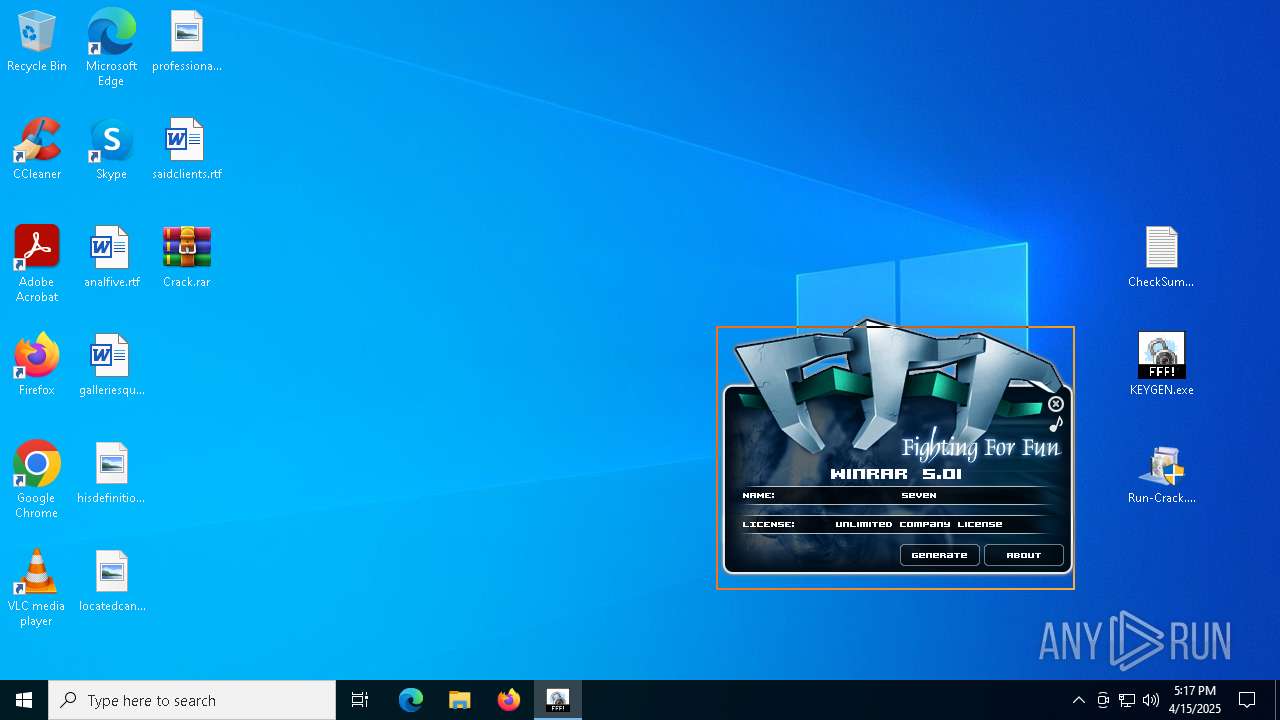
ADVANCEDINSTALLER mutex has been found
- Run-Crack.exe (PID: 7660)
Reads the Windows owner or organization settings
- Run-Crack.exe (PID: 7660)
- msiexec.exe (PID: 7748)
Process drops legitimate windows executable
- Run-Crack.exe (PID: 7660)
Creates FileSystem object to access computer's file system (SCRIPT)
- msiexec.exe (PID: 7944)
Checks whether a specific file exists (SCRIPT)
- msiexec.exe (PID: 7944)
Reads data from a binary Stream object (SCRIPT)
- msiexec.exe (PID: 7944)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 7944)
- WindowsService.exe (PID: 5892)
Runs shell command (SCRIPT)
- msiexec.exe (PID: 7944)
Starts POWERSHELL.EXE for commands execution
- msiexec.exe (PID: 8080)
The process bypasses the loading of PowerShell profile settings
- msiexec.exe (PID: 8080)
The process hide an interactive prompt from the user
- msiexec.exe (PID: 8080)
The process executes Powershell scripts
- msiexec.exe (PID: 8080)
Gets path to any of the special folders (POWERSHELL)
- powershell.exe (PID: 8172)
Drops a system driver (possible attempt to evade defenses)
- WindowsService.exe (PID: 5892)
Starts CMD.EXE for commands execution
- WindowsService.exe (PID: 5892)
Potential Corporate Privacy Violation
- cmd.exe (PID: 680)
Connects to unusual port
- cmd.exe (PID: 680)
- WindowsService.exe (PID: 5892)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 4880)
- Run-Crack.exe (PID: 7660)
- msiexec.exe (PID: 7748)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4880)
- msiexec.exe (PID: 7748)
- msiexec.exe (PID: 7944)
Checks supported languages
- Run-Crack.exe (PID: 7660)
- msiexec.exe (PID: 7748)
- msiexec.exe (PID: 7832)
- msiexec.exe (PID: 7944)
- KEYGEN.exe (PID: 8056)
- msiexec.exe (PID: 8080)
- WindowsService.exe (PID: 5892)
Manual execution by a user
- Run-Crack.exe (PID: 7592)
- Run-Crack.exe (PID: 7660)
Reads the computer name
- Run-Crack.exe (PID: 7660)
- msiexec.exe (PID: 7832)
- msiexec.exe (PID: 7748)
- msiexec.exe (PID: 8080)
- KEYGEN.exe (PID: 8056)
- WindowsService.exe (PID: 5892)
- msiexec.exe (PID: 7944)
Creates files or folders in the user directory
- Run-Crack.exe (PID: 7660)
- msiexec.exe (PID: 7748)
- WindowsService.exe (PID: 5892)
Create files in a temporary directory
- Run-Crack.exe (PID: 7660)
- powershell.exe (PID: 8172)
Reads Environment values
- msiexec.exe (PID: 7832)
- msiexec.exe (PID: 7944)
- msiexec.exe (PID: 8080)
- Run-Crack.exe (PID: 7660)
Process checks computer location settings
- msiexec.exe (PID: 7944)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 8172)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 8172)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 8172)
Reads the software policy settings
- powershell.exe (PID: 8172)
The sample compiled with japanese language support
- WindowsService.exe (PID: 5892)
Checks proxy server information
- WindowsService.exe (PID: 5892)
Creates files in the program directory
- cmd.exe (PID: 680)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 11 |
| UncompressedSize: | 11 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | CheckSums_xe.txt |
Total processes
145
Monitored processes
17
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 680 | "C:\Windows\System32\cmd.exe" | C:\Windows\System32\cmd.exe | WindowsService.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2600 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WindowsService.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4880 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Crack.rar | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 5892 | "C:\Users\admin\AppData\Local\Updates\WindowsService.exe" | C:\Users\admin\AppData\Local\Updates\WindowsService.exe | msiexec.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 7188 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7220 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7592 | "C:\Users\admin\Desktop\Run-Crack.exe" | C:\Users\admin\Desktop\Run-Crack.exe | — | explorer.exe | |||||||||||
User: admin Company: Getintopc.com Integrity Level: MEDIUM Description: EXE - Step 3 - Setup_Install Installer Exit code: 3221226540 Version: 1.0.0 Modules
| |||||||||||||||
| 7660 | "C:\Users\admin\Desktop\Run-Crack.exe" | C:\Users\admin\Desktop\Run-Crack.exe | explorer.exe | ||||||||||||
User: admin Company: Getintopc.com Integrity Level: HIGH Description: EXE - Step 3 - Setup_Install Installer Exit code: 0 Version: 1.0.0 Modules
| |||||||||||||||
| 7748 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
9 104
Read events
9 052
Write events
41
Delete events
11
Modification events
| (PID) Process: | (4880) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4880) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4880) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4880) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Crack.rar | |||
| (PID) Process: | (4880) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4880) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4880) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4880) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7748) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 441E00006B2B4D452AAEDB01 | |||
| (PID) Process: | (7748) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 7B60781B93F4957215A51D3DC24DB920BFD78FDEE386A6B311C18EAD705570E9 | |||
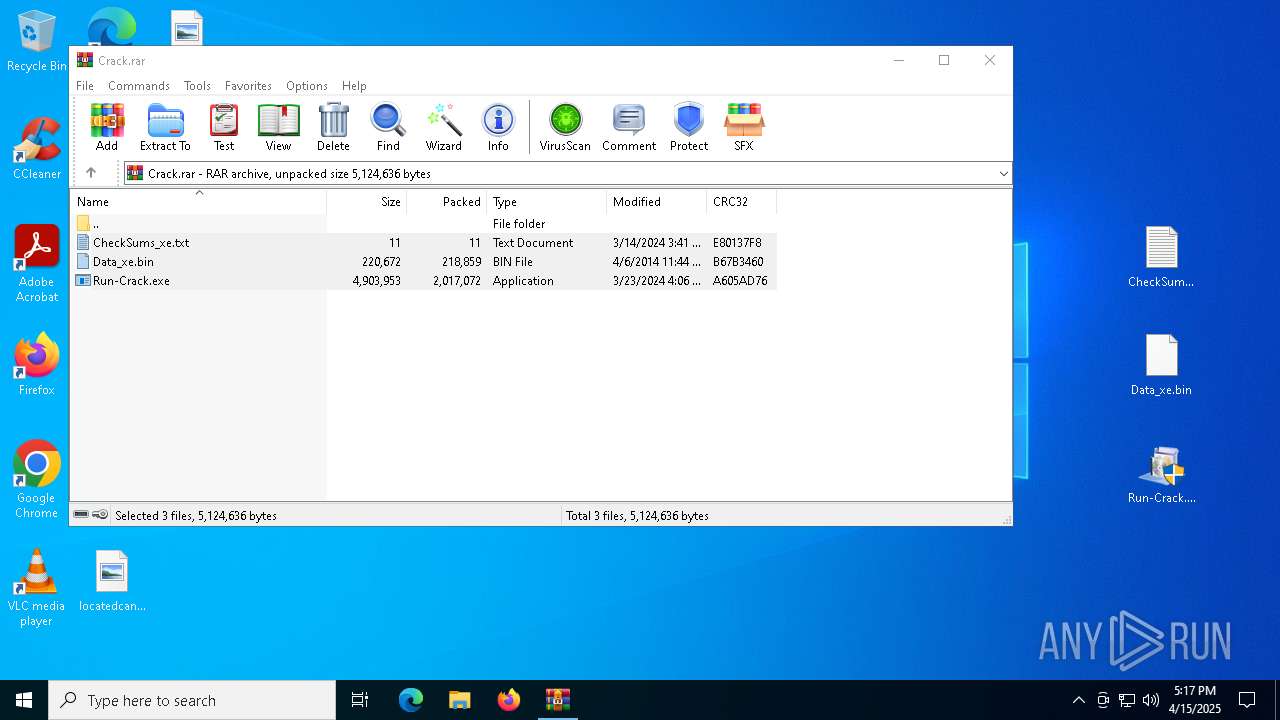
Executable files
20
Suspicious files
19
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4880 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4880.25734\Run-Crack.exe | executable | |
MD5:A0023254D52F0F0AE306EAA788F4D628 | SHA256:383ED6C9CDF8590845730198DFDE66CD799EC047CA8850CB5ECDFED293FA287C | |||
| 7748 | msiexec.exe | C:\Windows\Installer\MSIE553.tmp | executable | |
MD5:5A1F2196056C0A06B79A77AE981C7761 | SHA256:52F41817669AF7AC55B1516894EE705245C3148F2997FA0E6617E9CC6353E41E | |||
| 7944 | msiexec.exe | C:\Users\admin\Desktop\KEYGEN.exe | executable | |
MD5:2257D9B1D98795C90AEEA996D98A8D9C | SHA256:144BD20A74A86304809B57A1E28595E0E172308A3D620874CAC5E160E7A7B488 | |||
| 4880 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4880.25734\CheckSums_xe.txt | text | |
MD5:3742D17AA84FD928733471D76660E74F | SHA256:7E312C08CB5E5213C222815EE6BBAA4F9E478181BF337EDA0154DF1DA9198388 | |||
| 7660 | Run-Crack.exe | C:\Users\admin\AppData\Roaming\Getintopc.com\EXE - Step 3 - Setup_Install 1.0.0\install\A9F990C\LocalAppDataFolder\Updates\WindowsService.exe | executable | |
MD5:9CEADCFE7E7535B2088F1FCF3C4B30C7 | SHA256:5AF9E89A7BFCFCAE1C75DE6ACB7194B667D13776B61E79EA8AEAB95F0AF76BC7 | |||
| 8080 | msiexec.exe | C:\Windows\SystemTemp\msiEA33.txt | — | |
MD5:— | SHA256:— | |||
| 8080 | msiexec.exe | C:\Windows\SystemTemp\scrEA34.ps1 | — | |
MD5:— | SHA256:— | |||
| 8080 | msiexec.exe | C:\Windows\SystemTemp\scrEA35.txt | — | |
MD5:— | SHA256:— | |||
| 8080 | msiexec.exe | C:\Windows\SystemTemp\pssEA36.ps1 | — | |
MD5:— | SHA256:— | |||
| 7748 | msiexec.exe | C:\Windows\Installer\MSIE457.tmp | executable | |
MD5:5A1F2196056C0A06B79A77AE981C7761 | SHA256:52F41817669AF7AC55B1516894EE705245C3148F2997FA0E6617E9CC6353E41E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
22
DNS requests
15
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5892 | WindowsService.exe | GET | 200 | 188.138.25.13:83 | http://www.google.com.kvgwxazr0imtdpj9.fast-dns-host.com:83/md5_GIP.txt | unknown | — | — | unknown |
5892 | WindowsService.exe | GET | 200 | 188.138.25.13:83 | http://www.google.com.z78sbhum9pl0qtjy.fast-dns-host.com:83/Resource_GIP.bin | unknown | — | — | unknown |
7332 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7332 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5892 | WindowsService.exe | GET | 200 | 188.138.25.13:83 | http://www.google.com.kvgwxazr0imtdpj9.fast-dns-host.com:83/md5_GIP.txt | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.google.com.c4w8vzx9j6phlisf.fast-dns-host.com |
| unknown |
www.google.com.kvgwxazr0imtdpj9.fast-dns-host.com |
| unknown |
www.google.com.z78sbhum9pl0qtjy.fast-dns-host.com |
| unknown |
www.google.com.backend-aplha.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Suspected malicious based on domain name abuse (google.com.*) |
2196 | svchost.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Suspected malicious based on domain name abuse (google.com.*) |
2196 | svchost.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Suspected malicious based on domain name abuse (google.com.*) |
2196 | svchost.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Suspected malicious based on domain name abuse (google.com.*) |
680 | cmd.exe | Potential Corporate Privacy Violation | ET INFO Cryptocurrency Miner Checkin |
680 | cmd.exe | Potential Corporate Privacy Violation | ET INFO Cryptocurrency Miner Checkin |