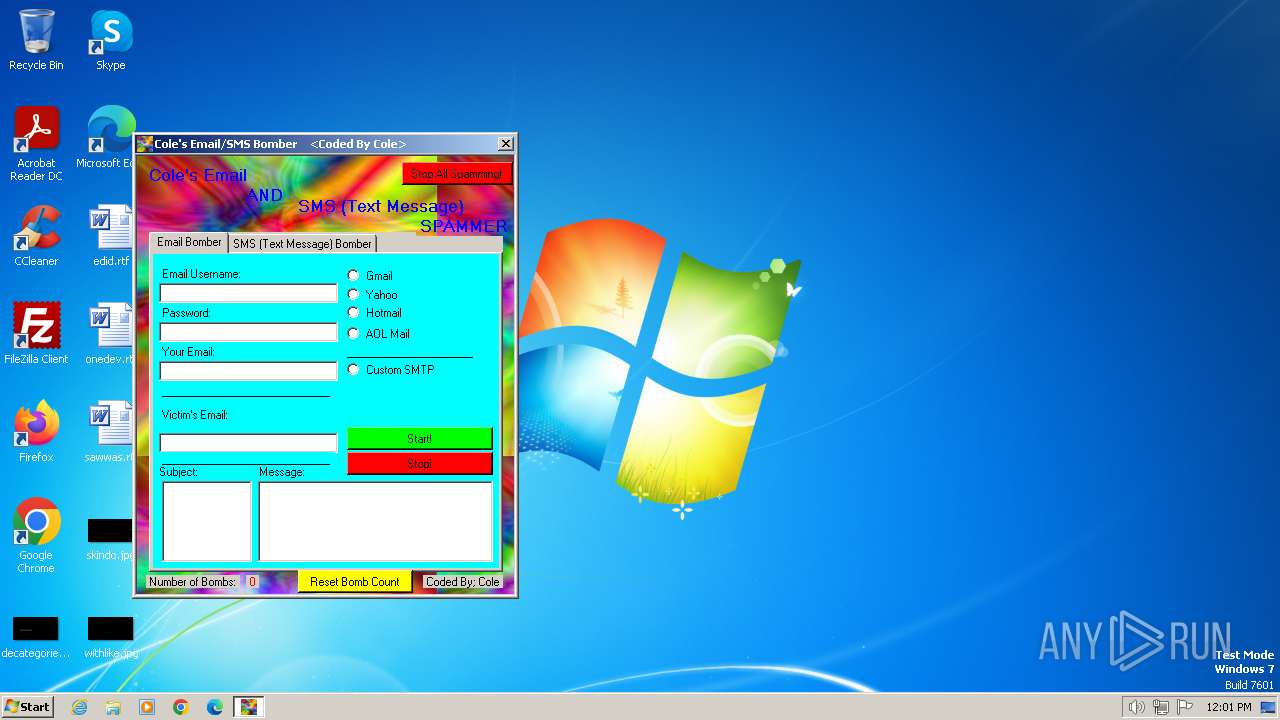
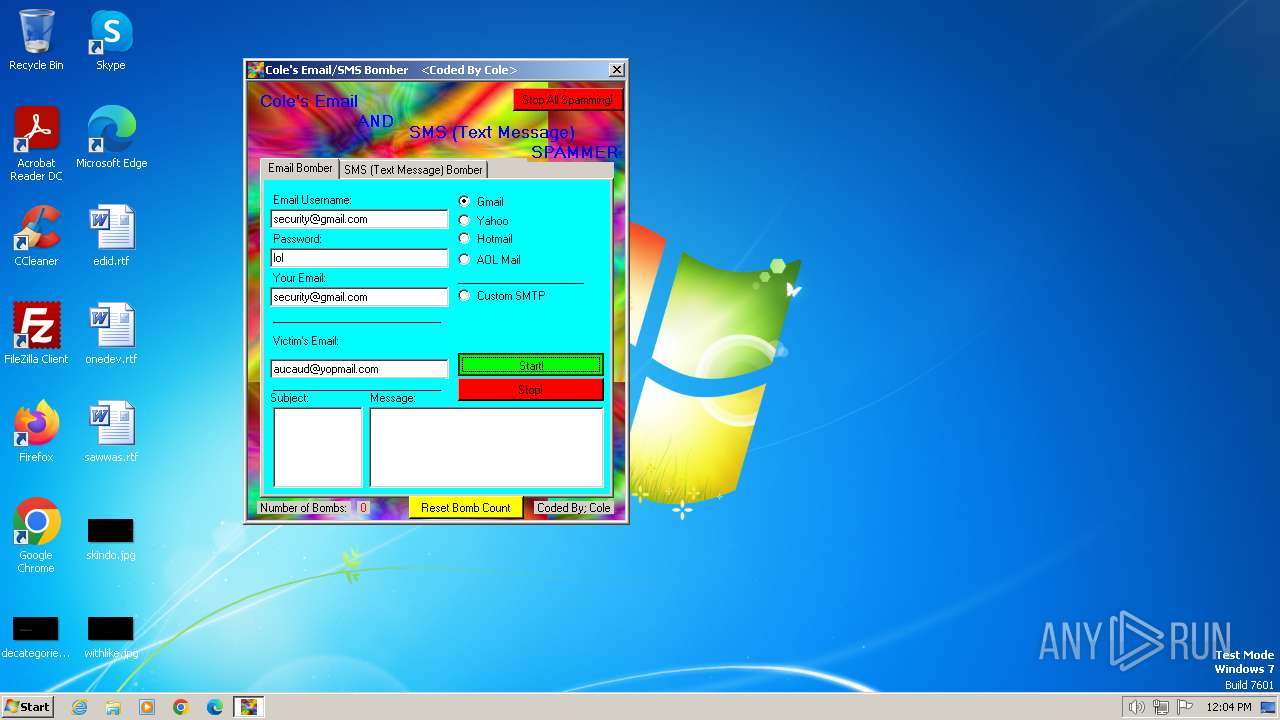
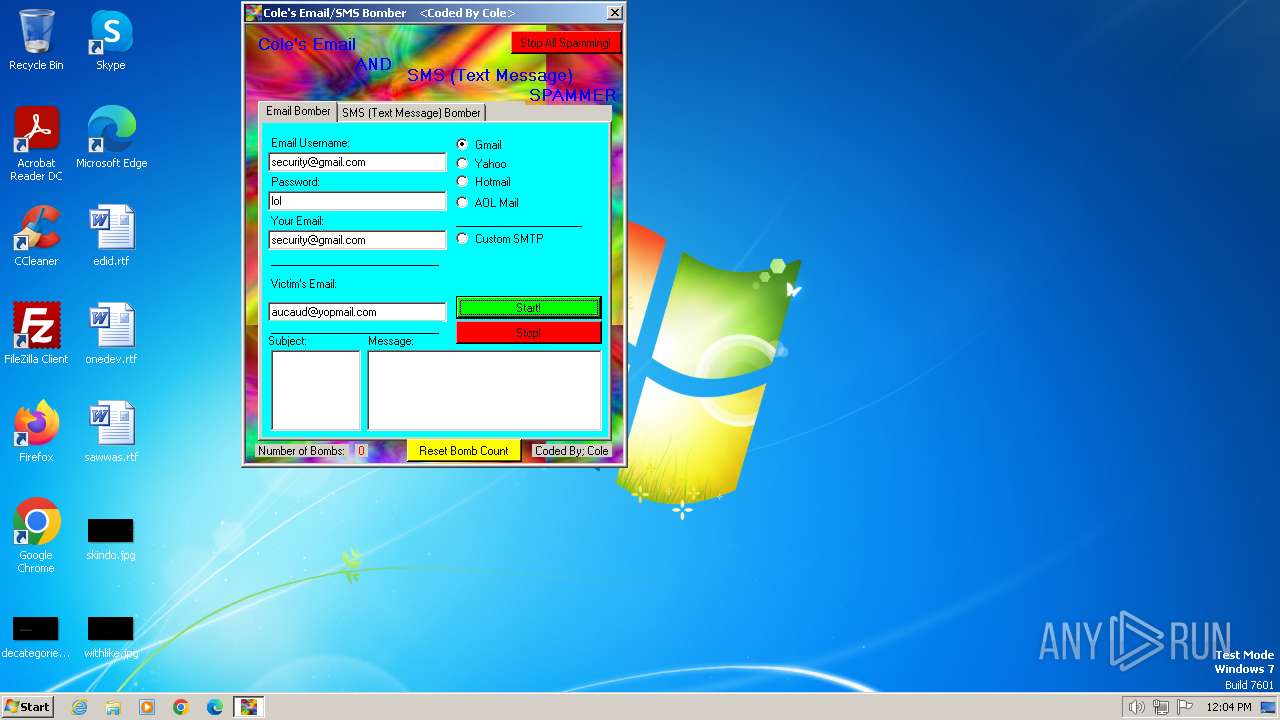
| File name: | SMS and Email Bomber by Cole.exe |
| Full analysis: | https://app.any.run/tasks/06f2dcf0-122f-4732-80a0-4d293158b9ff |
| Verdict: | Malicious activity |
| Threats: | Pony is a malware with two main functions — stealing information and dropping other viruses with different tasks on infected machines. It has been around since 2011, and it still actively attacks users in Europe and America. |
| Analysis date: | April 03, 2024, 11:01:43 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | 5F018C4A20B8EFD12F4EBE69762E7FC2 |
| SHA1: | 677FEE2557057167727352DE2B4A2AB6F1B4BC38 |
| SHA256: | 692F89239EA400E33FAA68851AA64F91954FEAF138F008FB34D9A2EAA8820FC9 |
| SSDEEP: | 24576:JvsvXn4Twwm4wixveFTBPFr5HBICy6SH/hpRA:JvsvX4Twwm4wix2BBPFr5HBICy6SH/hI |
MALICIOUS
Drops the executable file immediately after the start
- SMS and Email Bomber by Cole.exe (PID: 2124)
Pony/Fareit Trojan is detected
- SMS and Email Bomber by Cole.exe (PID: 1692)
Actions looks like stealing of personal data
- SMS and Email Bomber by Cole.exe (PID: 1692)
Steals credentials from Web Browsers
- SMS and Email Bomber by Cole.exe (PID: 1692)
SUSPICIOUS
Reads security settings of Internet Explorer
- SMS and Email Bomber by Cole.exe (PID: 2124)
- SMS and Email Bomber by Cole.exe (PID: 1692)
Reads the Internet Settings
- SMS and Email Bomber by Cole.exe (PID: 1692)
- SMS and Email Bomber by Cole.exe (PID: 2124)
Executing commands from a ".bat" file
- SMS and Email Bomber by Cole.exe (PID: 1692)
Starts CMD.EXE for commands execution
- SMS and Email Bomber by Cole.exe (PID: 1692)
Application launched itself
- SMS and Email Bomber by Cole.exe (PID: 2124)
Searches for installed software
- SMS and Email Bomber by Cole.exe (PID: 1692)
Accesses Microsoft Outlook profiles
- SMS and Email Bomber by Cole.exe (PID: 1692)
INFO
Checks supported languages
- SMS and Email Bomber by Cole.exe (PID: 2124)
- MQYSUW.exe (PID: 1836)
- SMS and Email Bomber by Cole.exe (PID: 1692)
Reads the computer name
- SMS and Email Bomber by Cole.exe (PID: 2124)
- SMS and Email Bomber by Cole.exe (PID: 1692)
- MQYSUW.exe (PID: 1836)
Create files in a temporary directory
- SMS and Email Bomber by Cole.exe (PID: 2124)
- SMS and Email Bomber by Cole.exe (PID: 1692)
Reads the machine GUID from the registry
- MQYSUW.exe (PID: 1836)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (38.2) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (37.5) |
| .dll | | | Win32 Dynamic Link Library (generic) (9.2) |
| .exe | | | Win32 Executable (generic) (6.3) |
| .exe | | | Win16/32 Executable Delphi generic (2.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 475136 |
| InitializedDataSize: | 8192 |
| UninitializedDataSize: | 937984 |
| EntryPoint: | 0x159330 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | A bomber for both SMS and Emails |
| CompanyName: | Zero Programming |
| FileDescription: | Coles Email And SMS Bomber |
| FileVersion: | 1.0.0.0 |
| InternalName: | Coles Email And SMS Bomber.exe |
| LegalCopyright: | Copyright © Zero Programming 2010 |
| LegalTrademarks: | ZP 2010 |
| OriginalFileName: | Coles Email And SMS Bomber.exe |
| ProductName: | Have Fun |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
40
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1496 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\1682171.bat" "C:\Users\admin\AppData\Local\Temp\SMS and Email Bomber by Cole.exe" " | C:\Windows\System32\cmd.exe | — | SMS and Email Bomber by Cole.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1692 | "C:\Users\admin\AppData\Local\Temp\SMS and Email Bomber by Cole.exe" | C:\Users\admin\AppData\Local\Temp\SMS and Email Bomber by Cole.exe | SMS and Email Bomber by Cole.exe | ||||||||||||
User: admin Company: Zero Programming Integrity Level: MEDIUM Description: Coles Email And SMS Bomber Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1836 | "C:\Users\admin\AppData\Local\Temp\MQYSUW.exe" | C:\Users\admin\AppData\Local\Temp\MQYSUW.exe | — | SMS and Email Bomber by Cole.exe | |||||||||||
User: admin Company: Zero Programming Integrity Level: MEDIUM Description: Coles Email And SMS Bomber Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2124 | "C:\Users\admin\AppData\Local\Temp\SMS and Email Bomber by Cole.exe" | C:\Users\admin\AppData\Local\Temp\SMS and Email Bomber by Cole.exe | — | explorer.exe | |||||||||||
User: admin Company: Zero Programming Integrity Level: MEDIUM Description: Coles Email And SMS Bomber Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
7 801
Read events
7 781
Write events
20
Delete events
0
Modification events
| (PID) Process: | (2124) SMS and Email Bomber by Cole.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2124) SMS and Email Bomber by Cole.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2124) SMS and Email Bomber by Cole.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2124) SMS and Email Bomber by Cole.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1692) SMS and Email Bomber by Cole.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR |
| Operation: | write | Name: | HWID |
Value: 7B39304342354233432D353642322D344142392D413246372D3042303536334344443045397D | |||
| (PID) Process: | (1692) SMS and Email Bomber by Cole.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1692) SMS and Email Bomber by Cole.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1692) SMS and Email Bomber by Cole.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1692) SMS and Email Bomber by Cole.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1692) SMS and Email Bomber by Cole.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
1
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2124 | SMS and Email Bomber by Cole.exe | C:\Users\admin\AppData\Local\Temp\MQYSUW.exe | executable | |
MD5:— | SHA256:— | |||
| 1692 | SMS and Email Bomber by Cole.exe | C:\Users\admin\AppData\Local\Temp\1682171.bat | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
8
DNS requests
4
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1692 | SMS and Email Bomber by Cole.exe | 49.13.77.253:80 | sodhbentmalek.org | Hetzner Online GmbH | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
sodhbentmalek.org |
| unknown |
dns.msftncsi.com |
| shared |
thaliamobles.com |
| unknown |