| File name: | BoostWareWoofer.exe |
| Full analysis: | https://app.any.run/tasks/c9adc579-002f-4c4a-b18c-38c86c0031b5 |
| Verdict: | Malicious activity |
| Threats: | Orcus is a modular Remote Access Trojan with some unusual functions. This RAT enables attackers to create plugins using a custom development library and offers a robust core feature set that makes it one of the most dangerous malicious programs in its class. |
| Analysis date: | February 28, 2025, 11:24:51 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows, 4 sections |
| MD5: | 7A0DE259284A750BC1B9E489A3C549EE |
| SHA1: | 8BD17616907D5ADF94489D2D6C833C55425148D0 |
| SHA256: | 6929F40D7BD70CE7E5189F9C940767D1D4426BCADD66828D1298CA96FFA44EB2 |
| SSDEEP: | 196608:AJdnfzApIKcFUu3No9NZyVy3wec8t3yuJ2Ut/Bmr9:odnfzcIKcFUeNuNZyVygetCuJ2kwr |
MALICIOUS
Orcus is detected
- Rha4t.exe (PID: 6808)
- Skype.exe (PID: 5576)
- Skype.exe (PID: 7224)
- Skype.exe (PID: 7304)
Changes the autorun value in the registry
- Skype.exe (PID: 5576)
Actions looks like stealing of personal data
- Skype.exe (PID: 5576)
ORCUS has been detected (YARA)
- Skype.exe (PID: 5576)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- BoostWareWoofer.exe (PID: 6964)
- BoostWare.exe (PID: 1324)
BASE64 encoded PowerShell command has been detected
- BoostWareWoofer.exe (PID: 6964)
- BoostWare.exe (PID: 1324)
Base64-obfuscated command line is found
- BoostWareWoofer.exe (PID: 6964)
- BoostWare.exe (PID: 1324)
Executable content was dropped or overwritten
- BoostWareWoofer.exe (PID: 6964)
- Rha4t.exe (PID: 6808)
- Skype.exe (PID: 5576)
- BoostWare.exe (PID: 1324)
Reads security settings of Internet Explorer
- BoostWareWoofer.exe (PID: 6964)
- BoostWare.exe (PID: 1324)
- Rha4t.exe (PID: 6808)
- WindowsInput.exe (PID: 4408)
- Skype.exe (PID: 5576)
- Skype.exe (PID: 7304)
Reads the date of Windows installation
- Rha4t.exe (PID: 6808)
- Skype.exe (PID: 5576)
Starts itself from another location
- Rha4t.exe (PID: 6808)
The process executes via Task Scheduler
- Skype.exe (PID: 7224)
Executes as Windows Service
- WindowsInput.exe (PID: 2384)
Executes application which crashes
- perm spoofer.exe (PID: 6404)
Connects to unusual port
- Skype.exe (PID: 5576)
There is functionality for taking screenshot (YARA)
- Skype.exe (PID: 5576)
Application launched itself
- Skype.exe (PID: 7304)
INFO
Reads the computer name
- BoostWareWoofer.exe (PID: 6964)
- BoostWare.exe (PID: 1324)
- Rha4t.exe (PID: 6808)
- WindowsInput.exe (PID: 4408)
- WindowsInput.exe (PID: 2384)
- Skype.exe (PID: 5576)
- Skype.exe (PID: 7304)
- Skype.exe (PID: 7224)
- Skype.exe (PID: 7356)
- perm spoofer.exe (PID: 6404)
Checks supported languages
- BoostWare.exe (PID: 1324)
- BoostWareWoofer.exe (PID: 6964)
- Rha4t.exe (PID: 6808)
- WindowsInput.exe (PID: 4408)
- Skype.exe (PID: 7224)
- WindowsInput.exe (PID: 2384)
- Skype.exe (PID: 5576)
- Skype.exe (PID: 7304)
- Skype.exe (PID: 7356)
- perm spoofer.exe (PID: 6404)
Process checks computer location settings
- BoostWareWoofer.exe (PID: 6964)
- Rha4t.exe (PID: 6808)
- Skype.exe (PID: 5576)
- Skype.exe (PID: 7304)
- BoostWare.exe (PID: 1324)
Create files in a temporary directory
- BoostWareWoofer.exe (PID: 6964)
- BoostWare.exe (PID: 1324)
Reads the machine GUID from the registry
- Rha4t.exe (PID: 6808)
- perm spoofer.exe (PID: 6404)
- WindowsInput.exe (PID: 4408)
- WindowsInput.exe (PID: 2384)
- Skype.exe (PID: 5576)
- Skype.exe (PID: 7224)
Creates files in the program directory
- Rha4t.exe (PID: 6808)
Creates files or folders in the user directory
- WerFault.exe (PID: 5960)
- Skype.exe (PID: 5576)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 516)
- powershell.exe (PID: 960)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 960)
- powershell.exe (PID: 516)
Checks proxy server information
- slui.exe (PID: 7932)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Orcus
(PID) Process(5576) Skype.exe
C2 (1)82.9.246.24:8808
Keys
AES3354d672869ad7820230c8f2ec5c43886824794a1cb8eec831849a17d4fcfde5
Salt
Options
AutostartBuilderProperty
AutostartMethodRegistry
TaskSchedulerTaskNameOrcus
TaskHighestPrivilegestrue
RegistryHiddenStarttrue
RegistryKeyNameSkype
TryAllAutostartMethodsOnFailfalse
ChangeAssemblyInformationBuilderProperty
ChangeAssemblyInformationtrue
AssemblyTitleMicrosoft Coporation
AssemblyDescriptionSkype
AssemblyCompanyNameMicrosoft Coporation
AssemblyProductNameSkype
AssemblyCopyrightnull
AssemblyTrademarksnull
AssemblyProductVersion1.0.0.0
AssemblyFileVersion1.0.0.0
ChangeCreationDateBuilderProperty
IsEnabledfalse
NewCreationDate2025-02-24T22:41:00
ChangeIconBuilderProperty
ChangeIconfalse
IconPathnull
ClientTagBuilderProperty
ClientTagFortnite
DataFolderBuilderProperty
Path%appdata%\Skype
DefaultPrivilegesBuilderProperty
RequireAdministratorRightsfalse
DisableInstallationPromptBuilderProperty
IsDisabledtrue
FrameworkVersionBuilderProperty
FrameworkVersionNET48
HideFileBuilderProperty
HideFiletrue
InstallationLocationBuilderProperty
Path%programfiles%\Microsoft\Skype.exe
InstallBuilderProperty
Installtrue
KeyloggerBuilderProperty
IsEnabledfalse
MutexBuilderProperty
Mutexf65beca88ddb49089d3a6be2931bc598
ProxyBuilderProperty
ProxyOptionNone
ProxyAddressnull
ProxyPort1080
ProxyType2
ReconnectDelayProperty
Delay10000
RequireAdministratorPrivilegesInstallerBuilderProperty
RequireAdministratorPrivilegestrue
RespawnTaskBuilderProperty
IsEnabledtrue
TaskNameSkype
ServiceBuilderProperty
Installtrue
SetRunProgramAsAdminFlagBuilderProperty
SetFlagfalse
WatchdogBuilderProperty
IsEnabledtrue
NameSkype.exe
WatchdogLocationAppData
PreventFileDeletiontrue
Plugins (0)
TRiD
| .exe | | | Win64 Executable (generic) (61.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.6) |
| .exe | | | Win32 Executable (generic) (10) |
| .exe | | | Win16/32 Executable Delphi generic (4.6) |
| .exe | | | Generic Win/DOS Executable (4.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 0000:00:00 00:00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit, No debug |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 2048 |
| InitializedDataSize: | 10449408 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x14d1 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
149
Monitored processes
20
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -EncodedCommand "PAAjAGUAZwBlACMAPgBBAGQAZAAtAE0AcABQAHIAZQBmAGUAcgBlAG4AYwBlACAAPAAjAHUAZABiACMAPgAgAC0ARQB4AGMAbAB1AHMAaQBvAG4AUABhAHQAaAAgAEAAKAAkAGUAbgB2ADoAVQBzAGUAcgBQAHIAbwBmAGkAbABlACwAJABlAG4AdgA6AFMAeQBzAHQAZQBtAEQAcgBpAHYAZQApACAAPAAjAGcAcAB4ACMAPgAgAC0ARgBvAHIAYwBlACAAPAAjAHUAbABrACMAPgA=" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | BoostWareWoofer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 960 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -EncodedCommand "PAAjAGQAbAByACMAPgBBAGQAZAAtAE0AcABQAHIAZQBmAGUAcgBlAG4AYwBlACAAPAAjAHMAagBmACMAPgAgAC0ARQB4AGMAbAB1AHMAaQBvAG4AUABhAHQAaAAgAEAAKAAkAGUAbgB2ADoAVQBzAGUAcgBQAHIAbwBmAGkAbABlACwAJABlAG4AdgA6AFMAeQBzAHQAZQBtAEQAcgBpAHYAZQApACAAPAAjAGYAdQBqACMAPgAgAC0ARgBvAHIAYwBlACAAPAAjAHQAZABrACMAPgA=" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | BoostWare.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1116 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1324 | "C:\Users\admin\AppData\Local\Temp\BoostWare.exe" | C:\Users\admin\AppData\Local\Temp\BoostWare.exe | BoostWareWoofer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2384 | "C:\WINDOWS\SysWOW64\WindowsInput.exe" | C:\Windows\SysWOW64\WindowsInput.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Integrity Level: SYSTEM Description: Windows Input Version: 0.1.0 Modules
| |||||||||||||||
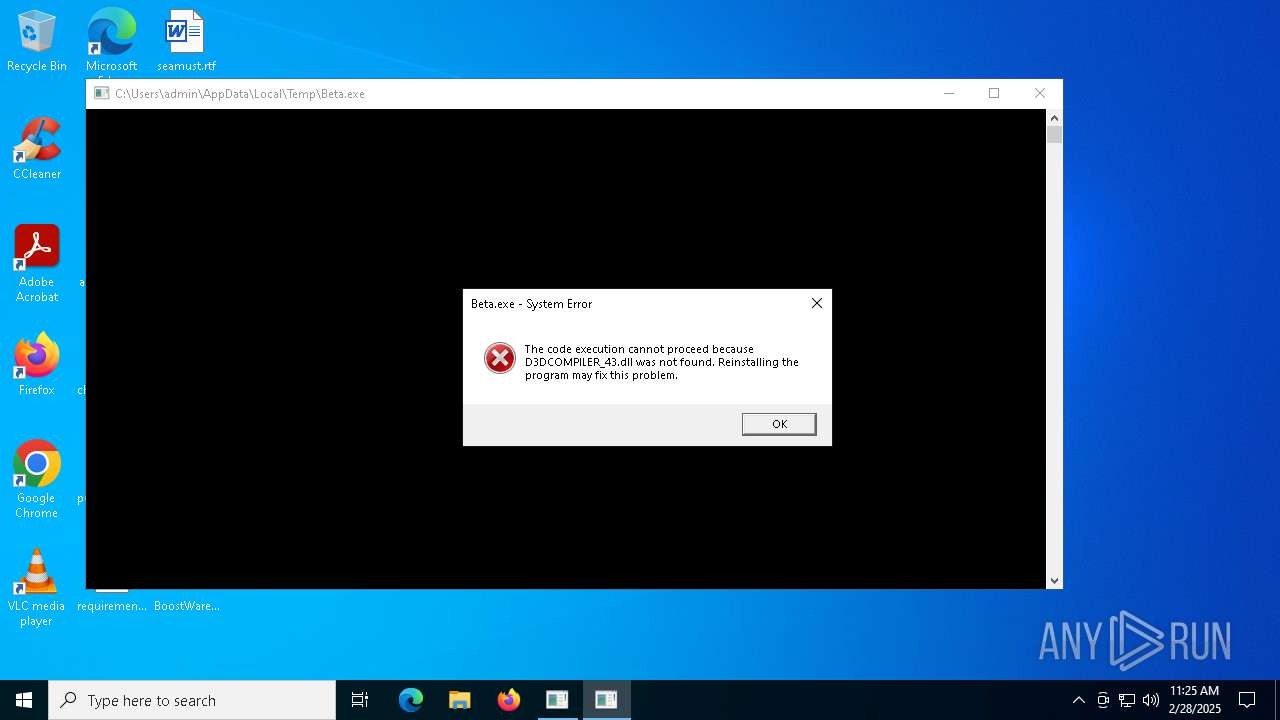
| 3768 | "C:\Users\admin\AppData\Local\Temp\Beta.exe" | C:\Users\admin\AppData\Local\Temp\Beta.exe | — | BoostWare.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225781 Modules
| |||||||||||||||
| 4408 | "C:\WINDOWS\SysWOW64\WindowsInput.exe" --install | C:\Windows\SysWOW64\WindowsInput.exe | — | Rha4t.exe | |||||||||||
User: admin Company: Microsoft Integrity Level: HIGH Description: Windows Input Exit code: 0 Version: 0.1.0 Modules
| |||||||||||||||
| 4696 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5352 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Beta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5576 | "C:\Program Files\Microsoft\Skype.exe" | C:\Program Files\Microsoft\Skype.exe | Rha4t.exe | ||||||||||||
User: admin Company: Microsoft Coporation Integrity Level: HIGH Description: Skype Version: 1.0.0.0 Modules
Orcus(PID) Process(5576) Skype.exe C2 (1)82.9.246.24:8808 Keys AES3354d672869ad7820230c8f2ec5c43886824794a1cb8eec831849a17d4fcfde5 Salt Options AutostartBuilderProperty AutostartMethodRegistry TaskSchedulerTaskNameOrcus TaskHighestPrivilegestrue RegistryHiddenStarttrue RegistryKeyNameSkype TryAllAutostartMethodsOnFailfalse ChangeAssemblyInformationBuilderProperty ChangeAssemblyInformationtrue AssemblyTitleMicrosoft Coporation AssemblyDescriptionSkype AssemblyCompanyNameMicrosoft Coporation AssemblyProductNameSkype AssemblyCopyrightnull AssemblyTrademarksnull AssemblyProductVersion1.0.0.0 AssemblyFileVersion1.0.0.0 ChangeCreationDateBuilderProperty IsEnabledfalse NewCreationDate2025-02-24T22:41:00 ChangeIconBuilderProperty ChangeIconfalse IconPathnull ClientTagBuilderProperty ClientTagFortnite DataFolderBuilderProperty Path%appdata%\Skype DefaultPrivilegesBuilderProperty RequireAdministratorRightsfalse DisableInstallationPromptBuilderProperty IsDisabledtrue FrameworkVersionBuilderProperty FrameworkVersionNET48 HideFileBuilderProperty HideFiletrue InstallationLocationBuilderProperty Path%programfiles%\Microsoft\Skype.exe InstallBuilderProperty Installtrue KeyloggerBuilderProperty IsEnabledfalse MutexBuilderProperty Mutexf65beca88ddb49089d3a6be2931bc598 ProxyBuilderProperty ProxyOptionNone ProxyAddressnull ProxyPort1080 ProxyType2 ReconnectDelayProperty Delay10000 RequireAdministratorPrivilegesInstallerBuilderProperty RequireAdministratorPrivilegestrue RespawnTaskBuilderProperty IsEnabledtrue TaskNameSkype ServiceBuilderProperty Installtrue SetRunProgramAsAdminFlagBuilderProperty SetFlagfalse WatchdogBuilderProperty IsEnabledtrue NameSkype.exe WatchdogLocationAppData PreventFileDeletiontrue Plugins (0) | |||||||||||||||
Total events
20 512
Read events
20 484
Write events
25
Delete events
3
Modification events
| (PID) Process: | (4408) WindowsInput.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\EventLog\Application\WindowsInput |
| Operation: | write | Name: | EventMessageFile |
Value: C:\Windows\Microsoft.NET\Framework64\v4.0.30319\EventLogMessages.dll | |||
| (PID) Process: | (5960) WerFault.exe | Key: | \REGISTRY\A\{563e4178-bedc-cd5a-2f23-f4723ef04797}\Root\InventoryApplicationFile |
| Operation: | write | Name: | WritePermissionsCheck |
Value: 1 | |||
| (PID) Process: | (5960) WerFault.exe | Key: | \REGISTRY\A\{563e4178-bedc-cd5a-2f23-f4723ef04797}\Root\InventoryApplicationFile\PermissionsCheckTestKey |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (5960) WerFault.exe | Key: | \REGISTRY\A\{563e4178-bedc-cd5a-2f23-f4723ef04797}\Root\InventoryApplicationFile\perm spoofer.exe|a10a38e6ddf82130 |
| Operation: | write | Name: | ProgramId |
Value: 00068cf020db3fcdcf7ef847a1db0fa3774b00000000 | |||
| (PID) Process: | (5960) WerFault.exe | Key: | \REGISTRY\A\{563e4178-bedc-cd5a-2f23-f4723ef04797}\Root\InventoryApplicationFile\perm spoofer.exe|a10a38e6ddf82130 |
| Operation: | write | Name: | FileId |
Value: 0000446cbfee65258c61c2f0e932d4242b429f77866d | |||
| (PID) Process: | (5960) WerFault.exe | Key: | \REGISTRY\A\{563e4178-bedc-cd5a-2f23-f4723ef04797}\Root\InventoryApplicationFile\perm spoofer.exe|a10a38e6ddf82130 |
| Operation: | write | Name: | LowerCaseLongPath |
Value: c:\users\admin\appdata\local\temp\perm spoofer.exe | |||
| (PID) Process: | (5960) WerFault.exe | Key: | \REGISTRY\A\{563e4178-bedc-cd5a-2f23-f4723ef04797}\Root\InventoryApplicationFile\perm spoofer.exe|a10a38e6ddf82130 |
| Operation: | write | Name: | LongPathHash |
Value: perm spoofer.exe|a10a38e6ddf82130 | |||
| (PID) Process: | (5960) WerFault.exe | Key: | \REGISTRY\A\{563e4178-bedc-cd5a-2f23-f4723ef04797}\Root\InventoryApplicationFile\perm spoofer.exe|a10a38e6ddf82130 |
| Operation: | write | Name: | Name |
Value: perm spoofer.exe | |||
| (PID) Process: | (5960) WerFault.exe | Key: | \REGISTRY\A\{563e4178-bedc-cd5a-2f23-f4723ef04797}\Root\InventoryApplicationFile\perm spoofer.exe|a10a38e6ddf82130 |
| Operation: | write | Name: | OriginalFileName |
Value: loader.exe | |||
| (PID) Process: | (5960) WerFault.exe | Key: | \REGISTRY\A\{563e4178-bedc-cd5a-2f23-f4723ef04797}\Root\InventoryApplicationFile\perm spoofer.exe|a10a38e6ddf82130 |
| Operation: | write | Name: | Publisher |
Value: 22727 | |||
Executable files
7
Suspicious files
4
Text files
13
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5960 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_perm spoofer.exe_609fb9afbe3653fbf5d9eaabf77495552c9fd9_2b851d02_a4c6ee7f-684b-4560-8325-837cf230a98e\Report.wer | — | |
MD5:— | SHA256:— | |||
| 5960 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\perm spoofer.exe.6404.dmp | — | |
MD5:— | SHA256:— | |||
| 6808 | Rha4t.exe | C:\Windows\SysWOW64\WindowsInput.exe | executable | |
MD5:A80BE96476032D2EAA901D180FE9FB73 | SHA256:D6075C1ED6F285F5DE01CE0CC6A817B59054DA8B19F20BC7081CFE7FB2B1AF42 | |||
| 516 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_q0bv5kgv.5uf.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4408 | WindowsInput.exe | C:\Windows\SysWOW64\WindowsInput.InstallState | xml | |
MD5:362CE475F5D1E84641BAD999C16727A0 | SHA256:1F78F1056761C6EBD8965ED2C06295BAFA704B253AFF56C492B93151AB642899 | |||
| 6964 | BoostWareWoofer.exe | C:\Users\admin\AppData\Local\Temp\BoostWare.exe | executable | |
MD5:1DC82CDF4C25C697678C3D95E12C494A | SHA256:5CF6FF4162D3EB61D3877CA0F2AB3174B95E210A8424134D4BC8698BA33E0FF3 | |||
| 5960 | WerFault.exe | C:\Windows\appcompat\Programs\Amcache.hve | binary | |
MD5:7247DDFB8FEE0A52A77D3E6504EBCDE4 | SHA256:08261E16F5ABB4B7702CE6B6EB75A8E1D1B0674D75DE73493C7DA3068E282689 | |||
| 5960 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERD6F9.tmp.dmp | binary | |
MD5:D0A2205525923709514C5B876CE66F31 | SHA256:D797E26EFA09AA037D35DD7C8C05D0C81799F93683362C7643DA6784EFFAB8B1 | |||
| 5576 | Skype.exe | C:\Users\admin\AppData\Roaming\Skype.exe.config | xml | |
MD5:740DDE6369B1C855EA2F8E171FA888C8 | SHA256:E03C480B46464159387618445CA9FD9870B53E092E2278837F2D5A54DAF06CAE | |||
| 6808 | Rha4t.exe | C:\Program Files\Microsoft\Skype.exe.config | xml | |
MD5:A2B76CEA3A59FA9AF5EA21FF68139C98 | SHA256:F99EF5BF79A7C43701877F0BB0B890591885BB0A3D605762647CC8FFBF10C839 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
33
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
5576 | Skype.exe | 82.9.246.24:8808 | — | Virgin Media Limited | GB | malicious |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
976 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7932 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |