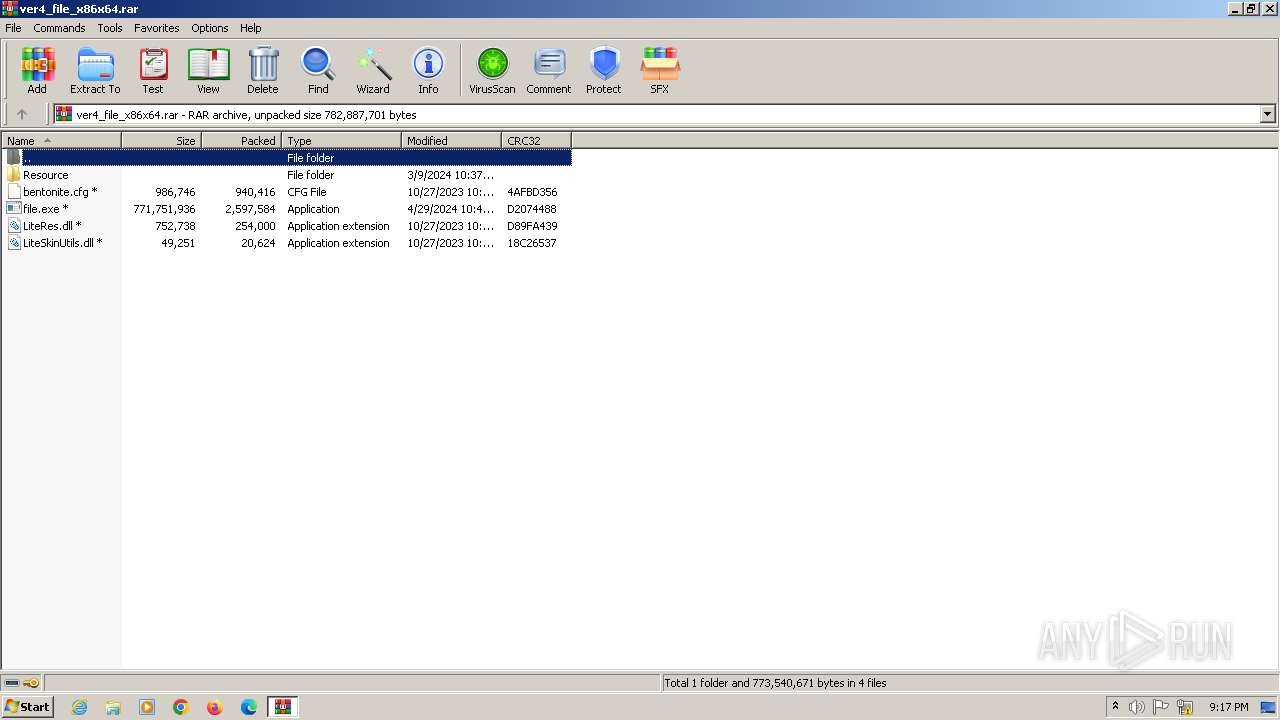
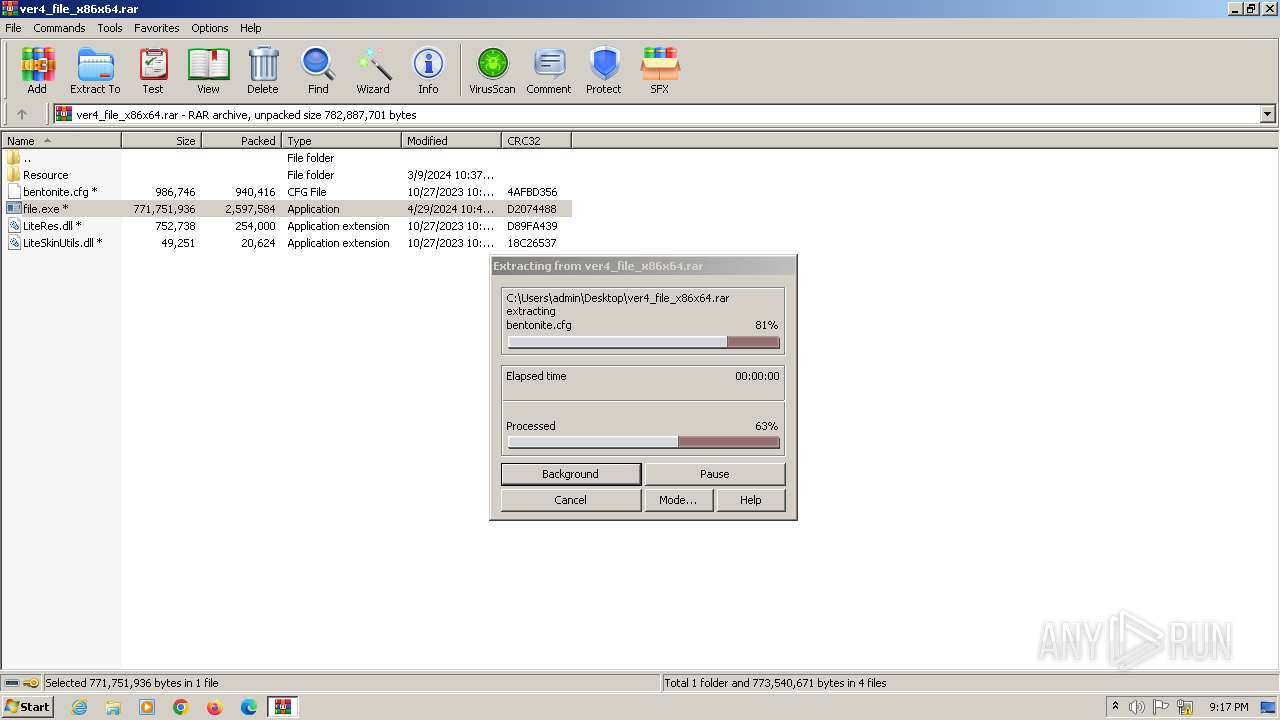
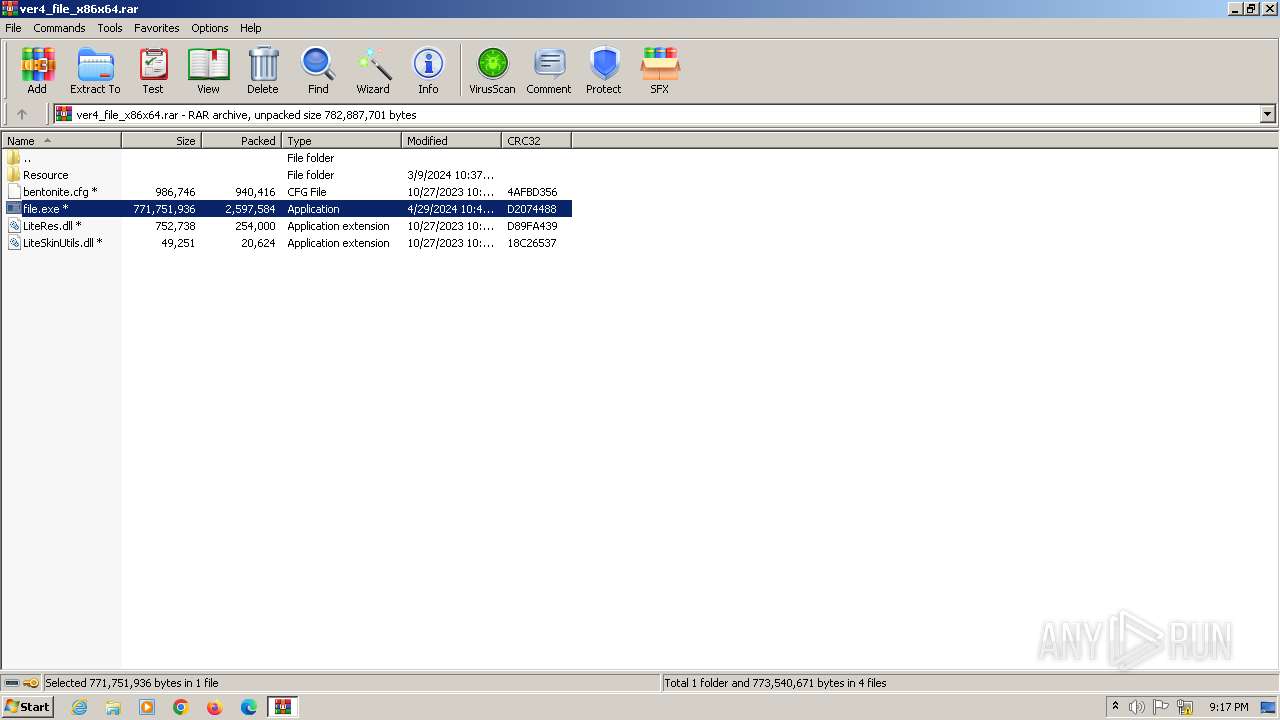
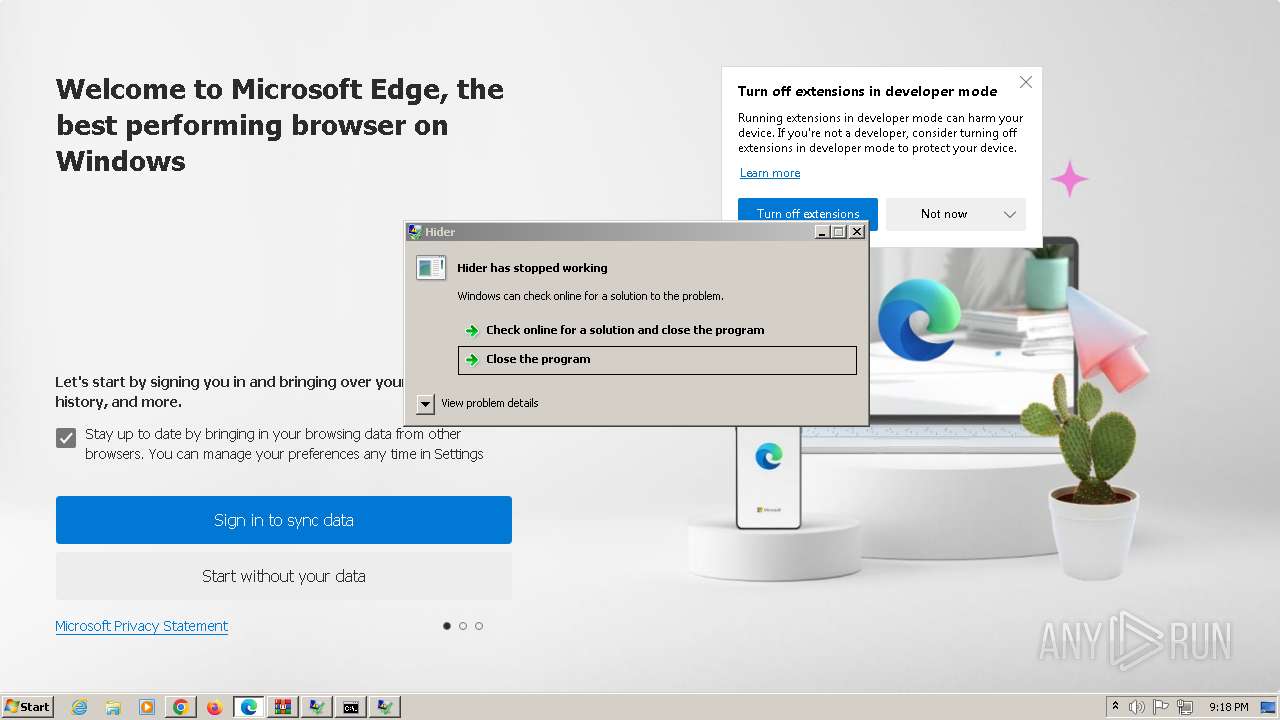
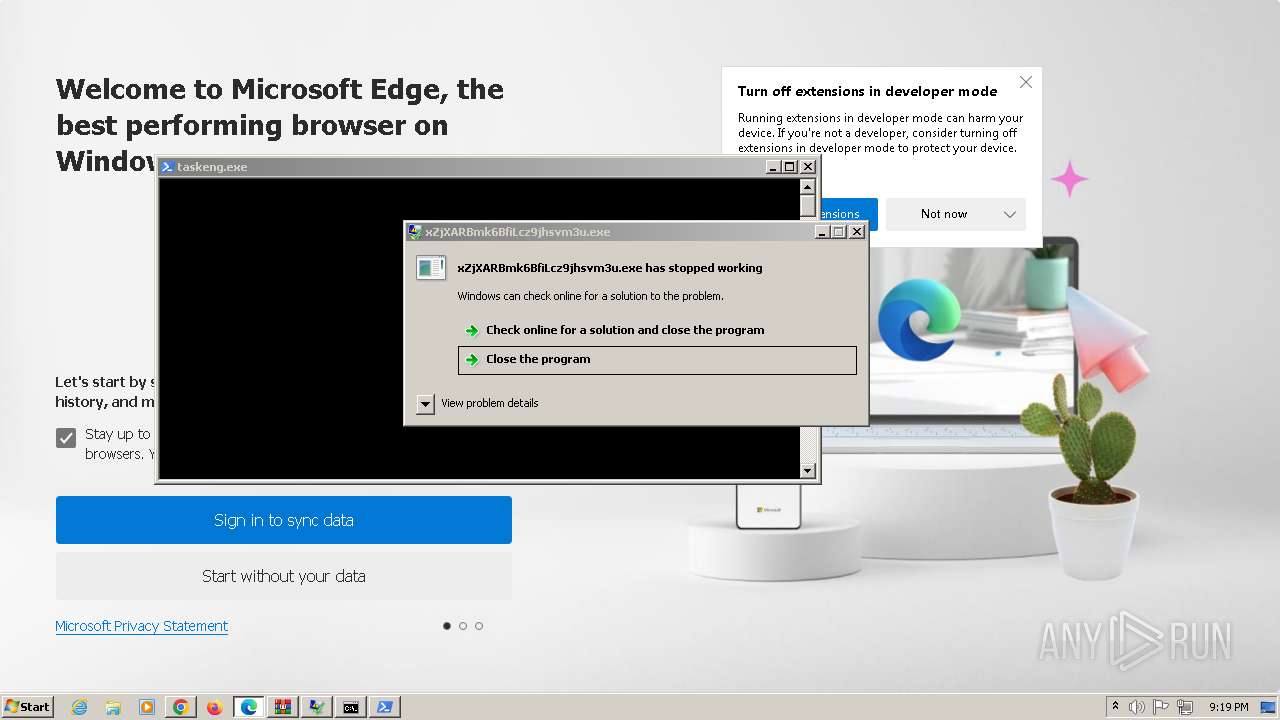
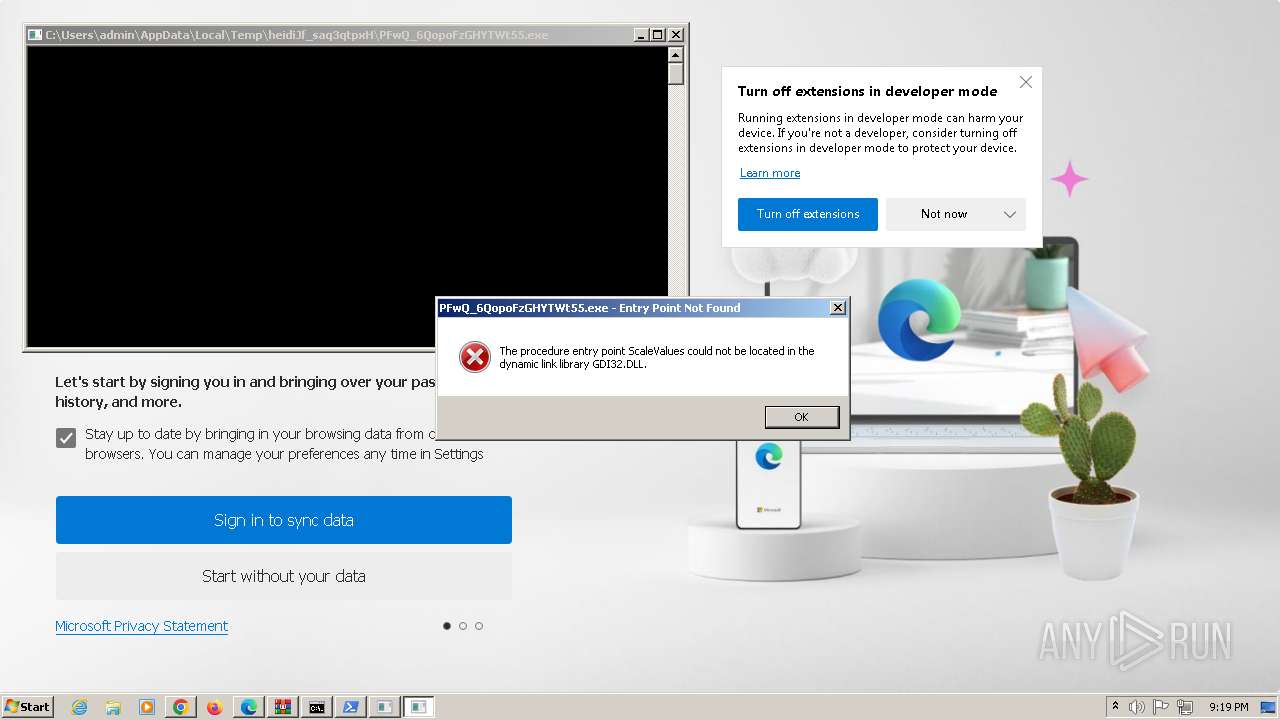
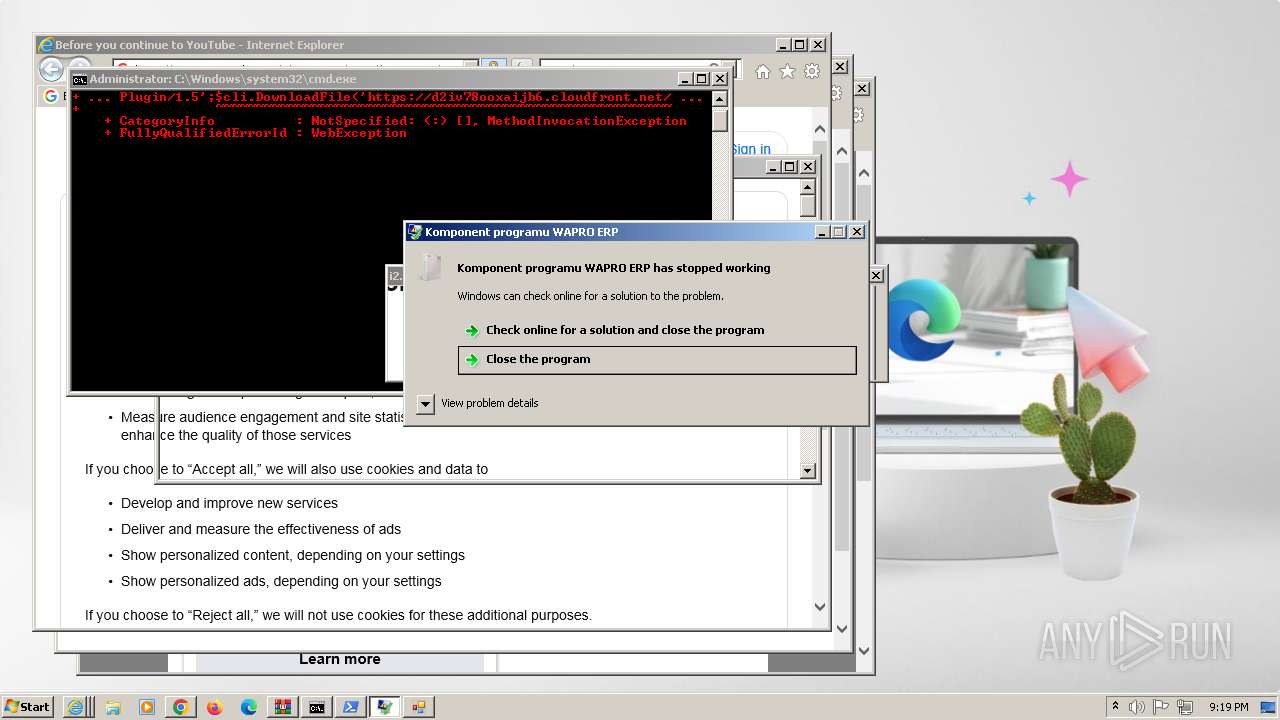
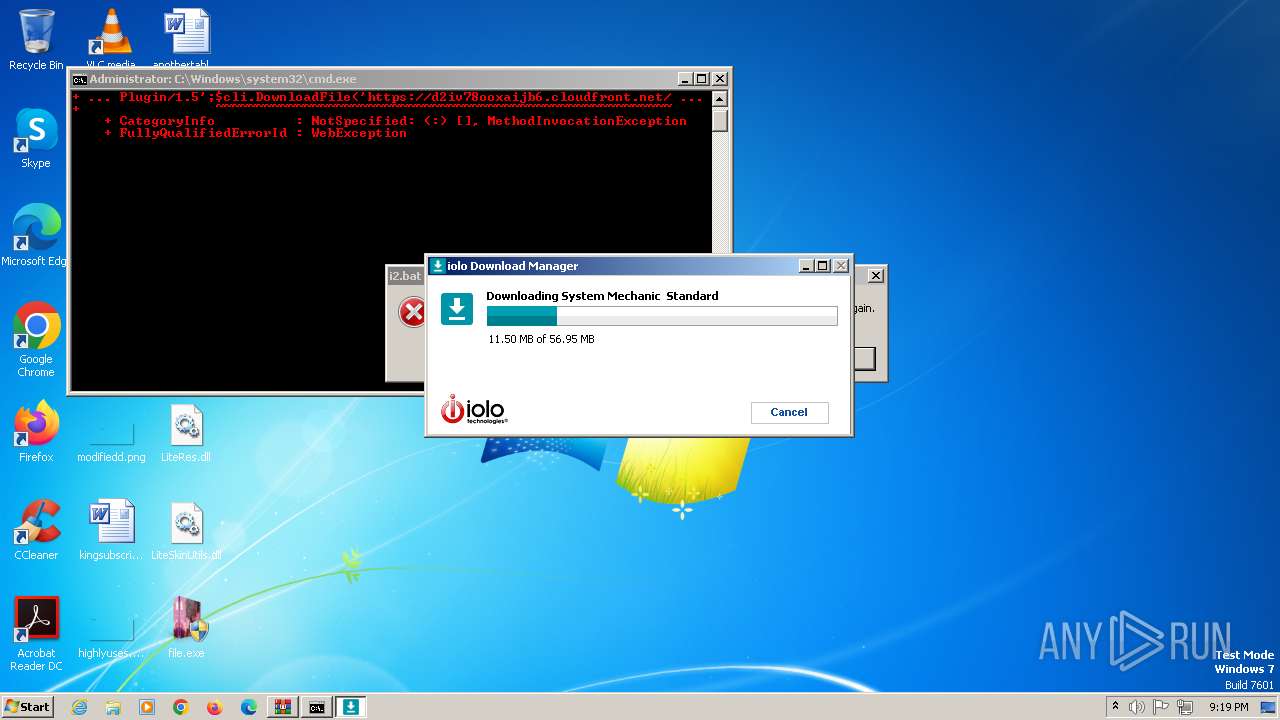
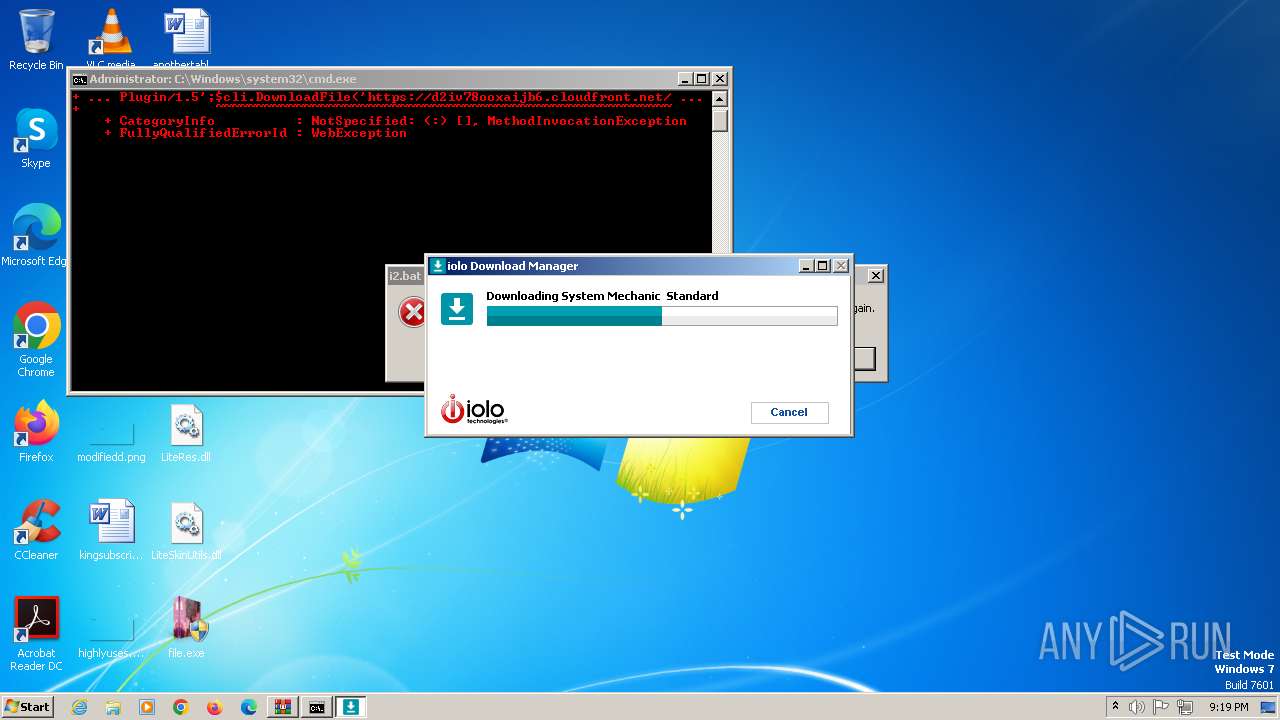
| File name: | ver4_file_x86x64.rar |
| Full analysis: | https://app.any.run/tasks/3a74e423-6968-4a77-bbd1-70ac1714aea0 |
| Verdict: | Malicious activity |
| Threats: | Adware is a form of malware that targets users with unwanted advertisements, often disrupting their browsing experience. It typically infiltrates systems through software bundling, malicious websites, or deceptive downloads. Once installed, it may track user activity, collect sensitive data, and display intrusive ads, including pop-ups or banners. Some advanced adware variants can bypass security measures and establish persistence on devices, making removal challenging. Additionally, adware can create vulnerabilities that other malware can exploit, posing a significant risk to user privacy and system security. |
| Analysis date: | April 30, 2024, 21:17:15 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 5AE053CD81560F67D718BAD44F6756F1 |
| SHA1: | DE8A87073236605302FC65BD66AF2A6FABA82947 |
| SHA256: | 6818DBC64DD5C92DEF6FC4364F5E79FD7A9F409EF9C37C5CA52A8FC0FE2B5820 |
| SSDEEP: | 98304:TuMJgyOWmRKdhbgAPT8xCN5Jg9eMQ4KY61q/YH/zAnnQxyje8sUvG4kfZN5R0OlG:p2M/dPSzMK7oD9WsNaiomnEBckJ |
MALICIOUS
Actions looks like stealing of personal data
- file.exe (PID: 2232)
- AsLcNNB.exe (PID: 4520)
- dVHu19pKeS2MAPlinmx5Uo0a.exe (PID: 2772)
- XXIM__e0G3DHfPWwNFbUHPL0.exe (PID: 2788)
- gyhJLw5s8IRyu5dmHKG8xWWi.exe (PID: 2860)
PRIVATELOADER has been detected (YARA)
- file.exe (PID: 2232)
Drops the executable file immediately after the start
- file.exe (PID: 2232)
- nQeEAuPuk5KsV_K43utERYXF.exe (PID: 2756)
- yWxYJivioOAk62qyoyBNuG_N.exe (PID: 2844)
- nQeEAuPuk5KsV_K43utERYXF.tmp (PID: 2872)
- D4d8KIRkzuDQdsQvfQwszMgb.exe (PID: 2828)
- MFOgNqK8oXigK80UoyDwiacL.exe (PID: 2740)
- XXIM__e0G3DHfPWwNFbUHPL0.exe (PID: 2788)
- Install.exe (PID: 3024)
- dVHu19pKeS2MAPlinmx5Uo0a.exe (PID: 2772)
- cmd.exe (PID: 2068)
- jenimvoxfree.exe (PID: 3032)
- Install.exe (PID: 2228)
- TsGjBt0ctBUisKO90p30_VW4.exe (PID: 2820)
- dckuybanmlgp.exe (PID: 4836)
- powershell.exe (PID: 4756)
- gyhJLw5s8IRyu5dmHKG8xWWi.exe (PID: 2860)
- i1.exe (PID: 4232)
- INy5MlIWJQ7M8Ba3SHyH.exe (PID: 2300)
- run.exe (PID: 4608)
- yxYEq9O29RuxLAvR29MkP_6T.exe (PID: 2804)
- amert.exe (PID: 5800)
- explorta.exe (PID: 4548)
- AsLcNNB.exe (PID: 4520)
- PEpnZQP.exe (PID: 6056)
PRIVATELOADER has been detected (SURICATA)
- file.exe (PID: 2232)
Changes the autorun value in the registry
- D4d8KIRkzuDQdsQvfQwszMgb.exe (PID: 2828)
- XXIM__e0G3DHfPWwNFbUHPL0.exe (PID: 2788)
- gyhJLw5s8IRyu5dmHKG8xWWi.exe (PID: 2860)
RISEPRO has been detected (SURICATA)
- D4d8KIRkzuDQdsQvfQwszMgb.exe (PID: 2828)
- KOoYYqzgOIoxSCT2nM4RAgnS.exe (PID: 2796)
- gyhJLw5s8IRyu5dmHKG8xWWi.exe (PID: 2860)
- XXIM__e0G3DHfPWwNFbUHPL0.exe (PID: 2788)
- TDotEEC0bLTHM57CBQOM.exe (PID: 4764)
- 1a3c06eca8.exe (PID: 3680)
Creates a writable file in the system directory
- file.exe (PID: 2232)
- powershell.exe (PID: 4896)
Create files in the Startup directory
- D4d8KIRkzuDQdsQvfQwszMgb.exe (PID: 2828)
- XXIM__e0G3DHfPWwNFbUHPL0.exe (PID: 2788)
Starts CMD.EXE for self-deleting
- i9tKTvv0y2SDJjlM5kmTn8uV.exe (PID: 2812)
Uses Task Scheduler to autorun other applications
- D4d8KIRkzuDQdsQvfQwszMgb.exe (PID: 2828)
- XXIM__e0G3DHfPWwNFbUHPL0.exe (PID: 2788)
- gyhJLw5s8IRyu5dmHKG8xWWi.exe (PID: 2860)
- PEpnZQP.exe (PID: 6056)
STEALC has been detected (SURICATA)
- dVHu19pKeS2MAPlinmx5Uo0a.exe (PID: 2772)
- u39k.0.exe (PID: 4348)
Connects to the CnC server
- dVHu19pKeS2MAPlinmx5Uo0a.exe (PID: 2772)
- XXIM__e0G3DHfPWwNFbUHPL0.exe (PID: 2788)
- gyhJLw5s8IRyu5dmHKG8xWWi.exe (PID: 2860)
- explorta.exe (PID: 4548)
- MSBuild.exe (PID: 3524)
- u39k.0.exe (PID: 4348)
Run PowerShell with an invisible window
- powershell.exe (PID: 2468)
- powershell.exe (PID: 1808)
- powershell.exe (PID: 4896)
- powershell.EXE (PID: 4848)
- powershell.exe (PID: 5880)
- powershell.exe (PID: 3100)
- powershell.exe (PID: 4160)
- powershell.exe (PID: 3128)
Antivirus name has been found in the command line (generic signature)
- findstr.exe (PID: 1396)
- findstr.exe (PID: 1764)
Steals credentials from Web Browsers
- gyhJLw5s8IRyu5dmHKG8xWWi.exe (PID: 2860)
- XXIM__e0G3DHfPWwNFbUHPL0.exe (PID: 2788)
- dVHu19pKeS2MAPlinmx5Uo0a.exe (PID: 2772)
Steals credentials
- dVHu19pKeS2MAPlinmx5Uo0a.exe (PID: 2772)
- gyhJLw5s8IRyu5dmHKG8xWWi.exe (PID: 2860)
- XXIM__e0G3DHfPWwNFbUHPL0.exe (PID: 2788)
Uses WMIC.EXE to add exclusions to the Windows Defender
- powershell.exe (PID: 1808)
- powershell.exe (PID: 5880)
- powershell.exe (PID: 3128)
- powershell.exe (PID: 4160)
RISEPRO has been detected (YARA)
- XXIM__e0G3DHfPWwNFbUHPL0.exe (PID: 2788)
- KOoYYqzgOIoxSCT2nM4RAgnS.exe (PID: 2796)
- gyhJLw5s8IRyu5dmHKG8xWWi.exe (PID: 2860)
Generic malware mutex has been detected
- yxYEq9O29RuxLAvR29MkP_6T.exe (PID: 2804)
HIJACKLOADER has been detected (YARA)
- cmd.exe (PID: 2856)
AMADEY has been detected (YARA)
- explorta.exe (PID: 4548)
GCLEANER has been detected (SURICATA)
- i1.exe (PID: 4232)
AMADEY has been detected (SURICATA)
- explorta.exe (PID: 4548)
METASTEALER has been detected (SURICATA)
- MSBuild.exe (PID: 2024)
ARECHCLIENT2 has been detected (SURICATA)
- MSBuild.exe (PID: 3524)
Unusual connection from system programs
- rundll32.exe (PID: 3916)
NEOREKLAMI has been detected (SURICATA)
- rundll32.exe (PID: 3916)
SUSPICIOUS
Reads the Internet Settings
- file.exe (PID: 2232)
- i9tKTvv0y2SDJjlM5kmTn8uV.exe (PID: 2812)
- w9zXOICRdqOdOE4xUhiSEdw7.exe (PID: 2748)
- yWxYJivioOAk62qyoyBNuG_N.exe (PID: 2844)
- dVHu19pKeS2MAPlinmx5Uo0a.exe (PID: 2772)
- G5caP7T_37p_VCCtaWUeSa0V.exe (PID: 2852)
- Install.exe (PID: 2228)
- Labs.pif (PID: 2320)
- XXIM__e0G3DHfPWwNFbUHPL0.exe (PID: 2788)
- gyhJLw5s8IRyu5dmHKG8xWWi.exe (PID: 2860)
- WMIC.exe (PID: 4876)
- powershell.exe (PID: 2468)
- powershell.exe (PID: 2264)
- powershell.exe (PID: 4756)
- powershell.exe (PID: 4936)
- cmd.exe (PID: 1572)
- i1.exe (PID: 4232)
- u39k.0.exe (PID: 4348)
- aaLjl9PoCYJEEkIeU_fY.exe (PID: 4924)
- INy5MlIWJQ7M8Ba3SHyH.exe (PID: 2300)
- explorta.exe (PID: 4548)
- u39k.3.exe (PID: 4616)
Checks for external IP
- file.exe (PID: 2232)
- gyhJLw5s8IRyu5dmHKG8xWWi.exe (PID: 2860)
- XXIM__e0G3DHfPWwNFbUHPL0.exe (PID: 2788)
- TDotEEC0bLTHM57CBQOM.exe (PID: 4764)
- 1a3c06eca8.exe (PID: 3680)
Reads the BIOS version
- file.exe (PID: 2232)
- gyhJLw5s8IRyu5dmHKG8xWWi.exe (PID: 2860)
- KOoYYqzgOIoxSCT2nM4RAgnS.exe (PID: 2796)
- Install.exe (PID: 2228)
- INy5MlIWJQ7M8Ba3SHyH.exe (PID: 2300)
- explorta.exe (PID: 4548)
- TDotEEC0bLTHM57CBQOM.exe (PID: 4764)
Reads settings of System Certificates
- file.exe (PID: 2232)
- yWxYJivioOAk62qyoyBNuG_N.exe (PID: 2844)
- gyhJLw5s8IRyu5dmHKG8xWWi.exe (PID: 2860)
- XXIM__e0G3DHfPWwNFbUHPL0.exe (PID: 2788)
- Labs.pif (PID: 2320)
Connects to the server without a host name
- file.exe (PID: 2232)
- i9tKTvv0y2SDJjlM5kmTn8uV.exe (PID: 2812)
- dVHu19pKeS2MAPlinmx5Uo0a.exe (PID: 2772)
Device Retrieving External IP Address Detected
- file.exe (PID: 2232)
- gyhJLw5s8IRyu5dmHKG8xWWi.exe (PID: 2860)
- XXIM__e0G3DHfPWwNFbUHPL0.exe (PID: 2788)
- TDotEEC0bLTHM57CBQOM.exe (PID: 4764)
- 1a3c06eca8.exe (PID: 3680)
Reads security settings of Internet Explorer
- file.exe (PID: 2232)
- WinRAR.exe (PID: 1796)
- w9zXOICRdqOdOE4xUhiSEdw7.exe (PID: 2748)
- i9tKTvv0y2SDJjlM5kmTn8uV.exe (PID: 2812)
- yWxYJivioOAk62qyoyBNuG_N.exe (PID: 2844)
- G5caP7T_37p_VCCtaWUeSa0V.exe (PID: 2852)
- dVHu19pKeS2MAPlinmx5Uo0a.exe (PID: 2772)
- Install.exe (PID: 2228)
- Labs.pif (PID: 2320)
- XXIM__e0G3DHfPWwNFbUHPL0.exe (PID: 2788)
- gyhJLw5s8IRyu5dmHKG8xWWi.exe (PID: 2860)
- AsLcNNB.exe (PID: 4520)
- i1.exe (PID: 4232)
- INy5MlIWJQ7M8Ba3SHyH.exe (PID: 2300)
- u39k.0.exe (PID: 4348)
- explorta.exe (PID: 4548)
Process requests binary or script from the Internet
- file.exe (PID: 2232)
- dVHu19pKeS2MAPlinmx5Uo0a.exe (PID: 2772)
Checks Windows Trust Settings
- file.exe (PID: 2232)
- yWxYJivioOAk62qyoyBNuG_N.exe (PID: 2844)
- Labs.pif (PID: 2320)
Process drops legitimate windows executable
- file.exe (PID: 2232)
- nQeEAuPuk5KsV_K43utERYXF.tmp (PID: 2872)
- XXIM__e0G3DHfPWwNFbUHPL0.exe (PID: 2788)
- dVHu19pKeS2MAPlinmx5Uo0a.exe (PID: 2772)
- explorta.exe (PID: 4548)
Executable content was dropped or overwritten
- file.exe (PID: 2232)
- nQeEAuPuk5KsV_K43utERYXF.exe (PID: 2756)
- yWxYJivioOAk62qyoyBNuG_N.exe (PID: 2844)
- nQeEAuPuk5KsV_K43utERYXF.tmp (PID: 2872)
- D4d8KIRkzuDQdsQvfQwszMgb.exe (PID: 2828)
- MFOgNqK8oXigK80UoyDwiacL.exe (PID: 2740)
- Install.exe (PID: 3024)
- XXIM__e0G3DHfPWwNFbUHPL0.exe (PID: 2788)
- cmd.exe (PID: 2068)
- jenimvoxfree.exe (PID: 3032)
- dVHu19pKeS2MAPlinmx5Uo0a.exe (PID: 2772)
- Install.exe (PID: 2228)
- TsGjBt0ctBUisKO90p30_VW4.exe (PID: 2820)
- dckuybanmlgp.exe (PID: 4836)
- gyhJLw5s8IRyu5dmHKG8xWWi.exe (PID: 2860)
- powershell.exe (PID: 4756)
- i1.exe (PID: 4232)
- INy5MlIWJQ7M8Ba3SHyH.exe (PID: 2300)
- run.exe (PID: 4608)
- yxYEq9O29RuxLAvR29MkP_6T.exe (PID: 2804)
- amert.exe (PID: 5800)
- explorta.exe (PID: 4548)
- AsLcNNB.exe (PID: 4520)
- PEpnZQP.exe (PID: 6056)
Executes as Windows Service
- raserver.exe (PID: 2520)
- dckuybanmlgp.exe (PID: 4836)
- raserver.exe (PID: 5808)
- raserver.exe (PID: 5852)
Drops 7-zip archiver for unpacking
- file.exe (PID: 2232)
- MFOgNqK8oXigK80UoyDwiacL.exe (PID: 2740)
Reads the Windows owner or organization settings
- nQeEAuPuk5KsV_K43utERYXF.tmp (PID: 2872)
Windows Defender mutex has been found
- dVHu19pKeS2MAPlinmx5Uo0a.exe (PID: 2772)
- u39k.0.exe (PID: 4348)
Starts itself from another location
- MFOgNqK8oXigK80UoyDwiacL.exe (PID: 2740)
- INy5MlIWJQ7M8Ba3SHyH.exe (PID: 2300)
Contacting a server suspected of hosting an CnC
- D4d8KIRkzuDQdsQvfQwszMgb.exe (PID: 2828)
- dVHu19pKeS2MAPlinmx5Uo0a.exe (PID: 2772)
- KOoYYqzgOIoxSCT2nM4RAgnS.exe (PID: 2796)
- gyhJLw5s8IRyu5dmHKG8xWWi.exe (PID: 2860)
- XXIM__e0G3DHfPWwNFbUHPL0.exe (PID: 2788)
- u39k.0.exe (PID: 4348)
- 1a3c06eca8.exe (PID: 3680)
- explorta.exe (PID: 4548)
- TDotEEC0bLTHM57CBQOM.exe (PID: 4764)
- MSBuild.exe (PID: 3524)
Executing commands from ".cmd" file
- G5caP7T_37p_VCCtaWUeSa0V.exe (PID: 2852)
Connects to unusual port
- D4d8KIRkzuDQdsQvfQwszMgb.exe (PID: 2828)
- KOoYYqzgOIoxSCT2nM4RAgnS.exe (PID: 2796)
- gyhJLw5s8IRyu5dmHKG8xWWi.exe (PID: 2860)
- XXIM__e0G3DHfPWwNFbUHPL0.exe (PID: 2788)
- TDotEEC0bLTHM57CBQOM.exe (PID: 4764)
- MSBuild.exe (PID: 2024)
- 1a3c06eca8.exe (PID: 3680)
- MSBuild.exe (PID: 3524)
Potential Corporate Privacy Violation
- file.exe (PID: 2232)
- dVHu19pKeS2MAPlinmx5Uo0a.exe (PID: 2772)
- gyhJLw5s8IRyu5dmHKG8xWWi.exe (PID: 2860)
- powershell.exe (PID: 4756)
- i1.exe (PID: 4232)
- XXIM__e0G3DHfPWwNFbUHPL0.exe (PID: 2788)
- explorta.exe (PID: 4548)
Adds/modifies Windows certificates
- file.exe (PID: 2232)
- powershell.exe (PID: 2264)
Starts CMD.EXE for commands execution
- G5caP7T_37p_VCCtaWUeSa0V.exe (PID: 2852)
- forfiles.exe (PID: 2180)
- i9tKTvv0y2SDJjlM5kmTn8uV.exe (PID: 2812)
- yWxYJivioOAk62qyoyBNuG_N.exe (PID: 2844)
- Install.exe (PID: 2228)
- forfiles.exe (PID: 1432)
- forfiles.exe (PID: 2632)
- forfiles.exe (PID: 1972)
- forfiles.exe (PID: 2560)
- cmd.exe (PID: 2068)
- forfiles.exe (PID: 2372)
- forfiles.exe (PID: 4120)
- AsLcNNB.exe (PID: 4520)
- forfiles.exe (PID: 4616)
- forfiles.exe (PID: 4696)
- forfiles.exe (PID: 4744)
- forfiles.exe (PID: 4788)
- forfiles.exe (PID: 4880)
- run.exe (PID: 4608)
- forfiles.exe (PID: 5820)
- PEpnZQP.exe (PID: 6056)
- forfiles.exe (PID: 5840)
- forfiles.exe (PID: 5384)
- forfiles.exe (PID: 5952)
- forfiles.exe (PID: 5988)
- forfiles.exe (PID: 5388)
- forfiles.exe (PID: 4116)
- forfiles.exe (PID: 3896)
Searches for installed software
- dVHu19pKeS2MAPlinmx5Uo0a.exe (PID: 2772)
- gyhJLw5s8IRyu5dmHKG8xWWi.exe (PID: 2860)
- XXIM__e0G3DHfPWwNFbUHPL0.exe (PID: 2788)
The process drops C-runtime libraries
- nQeEAuPuk5KsV_K43utERYXF.tmp (PID: 2872)
- dVHu19pKeS2MAPlinmx5Uo0a.exe (PID: 2772)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2204)
Searches and executes a command on selected files
- forfiles.exe (PID: 2180)
- forfiles.exe (PID: 1432)
- forfiles.exe (PID: 1972)
- forfiles.exe (PID: 2632)
- forfiles.exe (PID: 2560)
- forfiles.exe (PID: 2372)
- forfiles.exe (PID: 4120)
- forfiles.exe (PID: 4616)
- forfiles.exe (PID: 4696)
- forfiles.exe (PID: 4744)
- forfiles.exe (PID: 4880)
- forfiles.exe (PID: 4788)
- forfiles.exe (PID: 5820)
- forfiles.exe (PID: 5384)
- forfiles.exe (PID: 5840)
- forfiles.exe (PID: 5952)
- forfiles.exe (PID: 5988)
- forfiles.exe (PID: 5388)
- forfiles.exe (PID: 4116)
- forfiles.exe (PID: 3896)
Found strings related to reading or modifying Windows Defender settings
- forfiles.exe (PID: 2180)
- Install.exe (PID: 2228)
- forfiles.exe (PID: 1972)
- forfiles.exe (PID: 2632)
- forfiles.exe (PID: 1432)
- forfiles.exe (PID: 2372)
- forfiles.exe (PID: 4616)
- forfiles.exe (PID: 4696)
- forfiles.exe (PID: 4744)
- AsLcNNB.exe (PID: 4520)
- forfiles.exe (PID: 4788)
- forfiles.exe (PID: 5820)
- PEpnZQP.exe (PID: 6056)
- forfiles.exe (PID: 5840)
- forfiles.exe (PID: 5384)
- forfiles.exe (PID: 5952)
- forfiles.exe (PID: 5988)
- forfiles.exe (PID: 4116)
- forfiles.exe (PID: 3896)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2188)
- cmd.exe (PID: 2512)
- cmd.exe (PID: 1212)
- cmd.exe (PID: 2664)
- cmd.exe (PID: 4628)
- cmd.exe (PID: 4716)
- cmd.exe (PID: 4828)
- cmd.exe (PID: 4752)
- wscript.exe (PID: 3980)
- cmd.exe (PID: 5820)
- cmd.exe (PID: 3968)
- cmd.exe (PID: 3080)
- cmd.exe (PID: 2940)
- cmd.exe (PID: 3348)
- cmd.exe (PID: 5924)
- cmd.exe (PID: 5960)
- cmd.exe (PID: 5996)
Executing commands from a ".bat" file
- yWxYJivioOAk62qyoyBNuG_N.exe (PID: 2844)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1572)
- cmd.exe (PID: 2732)
- cmd.exe (PID: 2840)
- cmd.exe (PID: 4888)
- cmd.exe (PID: 5868)
- cmd.exe (PID: 5920)
- cmd.exe (PID: 4640)
- cmd.exe (PID: 5132)
Probably download files using WebClient
- cmd.exe (PID: 1572)
Powershell scripting: start process
- cmd.exe (PID: 2732)
- cmd.exe (PID: 4888)
- cmd.exe (PID: 5920)
Get information on the list of running processes
- cmd.exe (PID: 2068)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 2068)
Application launched itself
- cmd.exe (PID: 2068)
- explorta.exe (PID: 4548)
Drops a file with a rarely used extension (PIF)
- cmd.exe (PID: 2068)
Suspicious file concatenation
- cmd.exe (PID: 2644)
Starts application with an unusual extension
- cmd.exe (PID: 2068)
The executable file from the user directory is run by the CMD process
- Labs.pif (PID: 2320)
- i1.exe (PID: 4232)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 2068)
Reads browser cookies
- gyhJLw5s8IRyu5dmHKG8xWWi.exe (PID: 2860)
Accesses Microsoft Outlook profiles
- gyhJLw5s8IRyu5dmHKG8xWWi.exe (PID: 2860)
- XXIM__e0G3DHfPWwNFbUHPL0.exe (PID: 2788)
The process drops Mozilla's DLL files
- dVHu19pKeS2MAPlinmx5Uo0a.exe (PID: 2772)
The process connected to a server suspected of theft
- XXIM__e0G3DHfPWwNFbUHPL0.exe (PID: 2788)
- dVHu19pKeS2MAPlinmx5Uo0a.exe (PID: 2772)
- gyhJLw5s8IRyu5dmHKG8xWWi.exe (PID: 2860)
- MSBuild.exe (PID: 2024)
Uses powercfg.exe to modify the power settings
- TsGjBt0ctBUisKO90p30_VW4.exe (PID: 2820)
- dckuybanmlgp.exe (PID: 4836)
The process executes via Task Scheduler
- AsLcNNB.exe (PID: 4520)
- powershell.EXE (PID: 4848)
- PEpnZQP.exe (PID: 6056)
- rundll32.exe (PID: 836)
Starts SC.EXE for service management
- TsGjBt0ctBUisKO90p30_VW4.exe (PID: 2820)
The process verifies whether the antivirus software is installed
- dVHu19pKeS2MAPlinmx5Uo0a.exe (PID: 2772)
Drops a system driver (possible attempt to evade defenses)
- dckuybanmlgp.exe (PID: 4836)
Starts a Microsoft application from unusual location
- TDotEEC0bLTHM57CBQOM.exe (PID: 4764)
Reads the date of Windows installation
- u39k.3.exe (PID: 4616)
Unusual connection from system programs
- powershell.exe (PID: 2264)
- powershell.exe (PID: 4936)
- powershell.exe (PID: 4756)
The Powershell connects to the Internet
- powershell.exe (PID: 4756)
- powershell.exe (PID: 4936)
- powershell.exe (PID: 2264)
Access to an unwanted program domain was detected
- rundll32.exe (PID: 3916)
INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1796)
- WinRAR.exe (PID: 2548)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1796)
- WinRAR.exe (PID: 2548)
Create files in a temporary directory
- file.exe (PID: 2232)
- nQeEAuPuk5KsV_K43utERYXF.exe (PID: 2756)
- MFOgNqK8oXigK80UoyDwiacL.exe (PID: 2740)
- yWxYJivioOAk62qyoyBNuG_N.exe (PID: 2844)
- nQeEAuPuk5KsV_K43utERYXF.tmp (PID: 2872)
- w9zXOICRdqOdOE4xUhiSEdw7.exe (PID: 2748)
- D4d8KIRkzuDQdsQvfQwszMgb.exe (PID: 2828)
- Install.exe (PID: 3024)
- XXIM__e0G3DHfPWwNFbUHPL0.exe (PID: 2788)
- gyhJLw5s8IRyu5dmHKG8xWWi.exe (PID: 2860)
- Install.exe (PID: 2228)
- i1.exe (PID: 4232)
- INy5MlIWJQ7M8Ba3SHyH.exe (PID: 2300)
- yxYEq9O29RuxLAvR29MkP_6T.exe (PID: 2804)
- u39k.3.exe (PID: 4616)
Checks proxy server information
- file.exe (PID: 2232)
- i9tKTvv0y2SDJjlM5kmTn8uV.exe (PID: 2812)
- yWxYJivioOAk62qyoyBNuG_N.exe (PID: 2844)
- dVHu19pKeS2MAPlinmx5Uo0a.exe (PID: 2772)
- Labs.pif (PID: 2320)
- XXIM__e0G3DHfPWwNFbUHPL0.exe (PID: 2788)
- gyhJLw5s8IRyu5dmHKG8xWWi.exe (PID: 2860)
- u39k.0.exe (PID: 4348)
- u39k.3.exe (PID: 4616)
- explorta.exe (PID: 4548)
Process checks computer location settings
- file.exe (PID: 2232)
Process checks whether UAC notifications are on
- file.exe (PID: 2232)
- gyhJLw5s8IRyu5dmHKG8xWWi.exe (PID: 2860)
- KOoYYqzgOIoxSCT2nM4RAgnS.exe (PID: 2796)
Manual execution by a user
- WinRAR.exe (PID: 2548)
- msedge.exe (PID: 3376)
- Labs.pif (PID: 3564)
Creates files or folders in the user directory
- file.exe (PID: 2232)
- G5caP7T_37p_VCCtaWUeSa0V.exe (PID: 2852)
- D4d8KIRkzuDQdsQvfQwszMgb.exe (PID: 2828)
- nQeEAuPuk5KsV_K43utERYXF.tmp (PID: 2872)
- XXIM__e0G3DHfPWwNFbUHPL0.exe (PID: 2788)
- i9tKTvv0y2SDJjlM5kmTn8uV.exe (PID: 2812)
- yWxYJivioOAk62qyoyBNuG_N.exe (PID: 2844)
- gyhJLw5s8IRyu5dmHKG8xWWi.exe (PID: 2860)
- Labs.pif (PID: 2320)
- dVHu19pKeS2MAPlinmx5Uo0a.exe (PID: 2772)
- run.exe (PID: 4608)
Checks supported languages
- TsGjBt0ctBUisKO90p30_VW4.exe (PID: 2820)
- w9zXOICRdqOdOE4xUhiSEdw7.exe (PID: 2748)
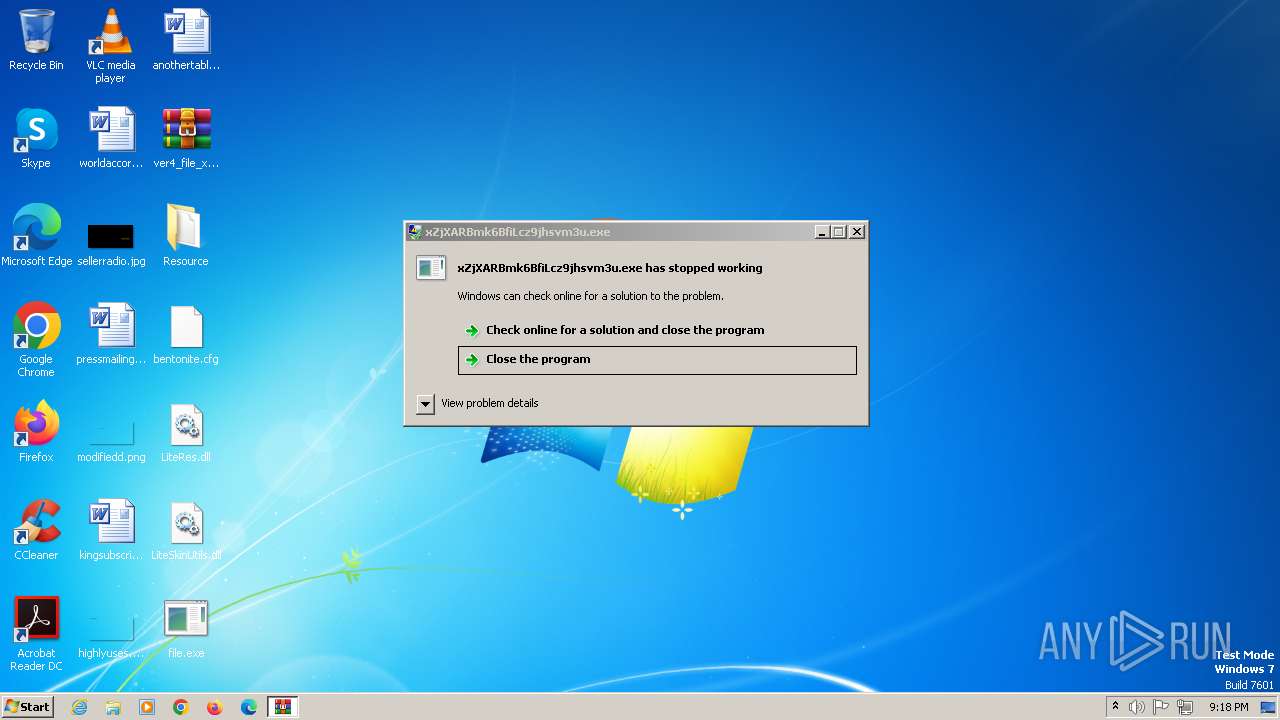
- xZjXARBmk6BfiLcz9jhsvm3u.exe (PID: 2780)
- 9P8AYb2DuJTtAbqm5O1opS9A.exe (PID: 2836)
- D4d8KIRkzuDQdsQvfQwszMgb.exe (PID: 2828)
- yxYEq9O29RuxLAvR29MkP_6T.exe (PID: 2804)
- MFOgNqK8oXigK80UoyDwiacL.exe (PID: 2740)
- nQeEAuPuk5KsV_K43utERYXF.exe (PID: 2756)
- dVHu19pKeS2MAPlinmx5Uo0a.exe (PID: 2772)
- i9tKTvv0y2SDJjlM5kmTn8uV.exe (PID: 2812)
- yWxYJivioOAk62qyoyBNuG_N.exe (PID: 2844)
- G5caP7T_37p_VCCtaWUeSa0V.exe (PID: 2852)
- gyhJLw5s8IRyu5dmHKG8xWWi.exe (PID: 2860)
- KOoYYqzgOIoxSCT2nM4RAgnS.exe (PID: 2796)
- nQeEAuPuk5KsV_K43utERYXF.tmp (PID: 2872)
- XXIM__e0G3DHfPWwNFbUHPL0.exe (PID: 2788)
- Install.exe (PID: 3024)
- file.exe (PID: 2232)
- Install.exe (PID: 2228)
- jenimvoxfree.exe (PID: 3032)
- Labs.pif (PID: 2320)
- jenimvoxfree.exe (PID: 2536)
- AsLcNNB.exe (PID: 4520)
- dckuybanmlgp.exe (PID: 4836)
- i1.exe (PID: 4232)
- u39k.0.exe (PID: 4348)
- aaLjl9PoCYJEEkIeU_fY.exe (PID: 4924)
- INy5MlIWJQ7M8Ba3SHyH.exe (PID: 2300)
- TDotEEC0bLTHM57CBQOM.exe (PID: 4764)
- explorta.exe (PID: 4548)
- run.exe (PID: 4608)
- MSBuild.exe (PID: 2024)
- u39k.3.exe (PID: 4616)
Reads the computer name
- w9zXOICRdqOdOE4xUhiSEdw7.exe (PID: 2748)
- yxYEq9O29RuxLAvR29MkP_6T.exe (PID: 2804)
- G5caP7T_37p_VCCtaWUeSa0V.exe (PID: 2852)
- i9tKTvv0y2SDJjlM5kmTn8uV.exe (PID: 2812)
- yWxYJivioOAk62qyoyBNuG_N.exe (PID: 2844)
- XXIM__e0G3DHfPWwNFbUHPL0.exe (PID: 2788)
- dVHu19pKeS2MAPlinmx5Uo0a.exe (PID: 2772)
- D4d8KIRkzuDQdsQvfQwszMgb.exe (PID: 2828)
- nQeEAuPuk5KsV_K43utERYXF.tmp (PID: 2872)
- 9P8AYb2DuJTtAbqm5O1opS9A.exe (PID: 2836)
- file.exe (PID: 2232)
- Install.exe (PID: 2228)
- gyhJLw5s8IRyu5dmHKG8xWWi.exe (PID: 2860)
- KOoYYqzgOIoxSCT2nM4RAgnS.exe (PID: 2796)
- jenimvoxfree.exe (PID: 3032)
- Labs.pif (PID: 2320)
- AsLcNNB.exe (PID: 4520)
- i1.exe (PID: 4232)
- u39k.0.exe (PID: 4348)
- INy5MlIWJQ7M8Ba3SHyH.exe (PID: 2300)
- aaLjl9PoCYJEEkIeU_fY.exe (PID: 4924)
- run.exe (PID: 4608)
- MSBuild.exe (PID: 2024)
- u39k.3.exe (PID: 4616)
- explorta.exe (PID: 4548)
Reads the machine GUID from the registry
- w9zXOICRdqOdOE4xUhiSEdw7.exe (PID: 2748)
- i9tKTvv0y2SDJjlM5kmTn8uV.exe (PID: 2812)
- file.exe (PID: 2232)
- yWxYJivioOAk62qyoyBNuG_N.exe (PID: 2844)
- 9P8AYb2DuJTtAbqm5O1opS9A.exe (PID: 2836)
- dVHu19pKeS2MAPlinmx5Uo0a.exe (PID: 2772)
- XXIM__e0G3DHfPWwNFbUHPL0.exe (PID: 2788)
- KOoYYqzgOIoxSCT2nM4RAgnS.exe (PID: 2796)
- gyhJLw5s8IRyu5dmHKG8xWWi.exe (PID: 2860)
- Install.exe (PID: 2228)
- Labs.pif (PID: 2320)
- i1.exe (PID: 4232)
- u39k.0.exe (PID: 4348)
- yxYEq9O29RuxLAvR29MkP_6T.exe (PID: 2804)
- explorta.exe (PID: 4548)
- MSBuild.exe (PID: 2024)
Creates files in the program directory
- XXIM__e0G3DHfPWwNFbUHPL0.exe (PID: 2788)
- D4d8KIRkzuDQdsQvfQwszMgb.exe (PID: 2828)
- dVHu19pKeS2MAPlinmx5Uo0a.exe (PID: 2772)
- jenimvoxfree.exe (PID: 3032)
- TsGjBt0ctBUisKO90p30_VW4.exe (PID: 2820)
- gyhJLw5s8IRyu5dmHKG8xWWi.exe (PID: 2860)
- u39k.3.exe (PID: 4616)
Reads Environment values
- dVHu19pKeS2MAPlinmx5Uo0a.exe (PID: 2772)
- gyhJLw5s8IRyu5dmHKG8xWWi.exe (PID: 2860)
- XXIM__e0G3DHfPWwNFbUHPL0.exe (PID: 2788)
Reads product name
- dVHu19pKeS2MAPlinmx5Uo0a.exe (PID: 2772)
- gyhJLw5s8IRyu5dmHKG8xWWi.exe (PID: 2860)
- XXIM__e0G3DHfPWwNFbUHPL0.exe (PID: 2788)
Reads CPU info
- dVHu19pKeS2MAPlinmx5Uo0a.exe (PID: 2772)
- gyhJLw5s8IRyu5dmHKG8xWWi.exe (PID: 2860)
- XXIM__e0G3DHfPWwNFbUHPL0.exe (PID: 2788)
Creates a software uninstall entry
- nQeEAuPuk5KsV_K43utERYXF.tmp (PID: 2872)
Application launched itself
- chrome.exe (PID: 1832)
- msedge.exe (PID: 2580)
- msedge.exe (PID: 3376)
- chrome.exe (PID: 2564)
Reads mouse settings
- Labs.pif (PID: 2320)
- aaLjl9PoCYJEEkIeU_fY.exe (PID: 4924)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 4936)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Amadey
(PID) Process(4548) explorta.exe
C2193.233.132.139
URLhttp://193.233.132.139/sev56rkm/index.php
Version4.20
Options
Drop directory5454e6f062
Drop nameexplorta.exe
Strings (113)explorta.exe
------
Norton
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
un:
Programs
193.233.132.139
2019
"
cred.dll|clip.dll|
rundll32
0123456789
" && ren
e1
ESET
CurrentBuild
AVG
"
Content-Type: application/octet-stream
360TotalSecurity
-%lu
#
lv:
&& Exit"
vs:
"taskkill /f /im "
<d>
\App
/sev56rkm/index.php
Sophos
ProgramData\
/Plugins/
st=s
=
+++
kernel32.dll
5454e6f062
Rem
Main
SYSTEM\CurrentControlSet\Control\UnitedVideo\CONTROL\VIDEO\
abcdefghijklmnopqrstuvwxyz0123456789-_
.jpg
ps1
%-lu
exe
Content-Type: multipart/form-data; boundary=----
wb
sd:
%USERPROFILE%
VideoID
4.20
AVAST Software
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
?scr=1
Doctor Web
av:
SOFTWARE\Microsoft\Windows NT\CurrentVersion
" && timeout 1 && del
ar:
rb
------
2022
shutdown -s -t 0
SOFTWARE\Microsoft\Windows\CurrentVersion\Run
:::
S-%lu-
DefaultSettings.YResolution
shell32.dll
Content-Type: application/x-www-form-urlencoded
ProductName
Content-Disposition: form-data; name="data"; filename="
pc:
2016
dll
Startup
-executionpolicy remotesigned -File "
\
|
GET
Comodo
dm:
Kaspersky Lab
Panda Security
<c>
-unicode-
cmd /C RMDIR /s/q
rundll32.exe
Bitdefender
&&
&unit=
https://
cmd
bi:
/k
\0000
Avira
WinDefender
SYSTEM\ControlSet001\Services\BasicDisplay\Video
random
og:
http://
--
SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
d1
os:
POST
id:
Powershell.exe
DefaultSettings.XResolution
r=
GetNativeSystemInfo
e0
SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
ComputerName
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
428
Monitored processes
276
Malicious processes
40
Suspicious processes
24
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 408 | REG ADD "HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Exclusions\Paths" /f /v "C:\Windows\Temp\TtNtWPRQARDvDBvI" /t REG_DWORD /d 0 /reg:64 | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 408 | "C:\Windows\system32\gpupdate.exe" /force | C:\Windows\SysWOW64\gpupdate.exe | — | powershell.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Group Policy Update Utility Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 632 | "C:\Windows\system32\gpupdate.exe" /force | C:\Windows\System32\gpupdate.exe | — | powershell.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Group Policy Update Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 700 | schtasks /DELETE /F /TN "kRLTqYWysAZjVOw" | C:\Windows\SysWOW64\schtasks.exe | — | PEpnZQP.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 788 | "C:\Windows\System32\reg.exe" ADD "HKLM\SOFTWARE\Microsoft\Windows Defender\Exclusions\Paths" /f /v "C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Extensions" /t REG_DWORD /d 0 /reg:64 | C:\Windows\SysWOW64\reg.exe | — | wscript.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 836 | C:\Windows\system32\rundll32.EXE "C:\Windows\Temp\TtNtWPRQARDvDBvI\hvqltPcn\XRofjhj.dll",#1 /pdidijqR 525403 | C:\Windows\System32\rundll32.exe | — | taskeng.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 860 | "C:\Windows\System32\reg.exe" ADD "HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Exclusions\Paths" /f /v "C:\ProgramData\ypvfxRdiVpdIIEVB" /t REG_DWORD /d 0 /reg:64 | C:\Windows\SysWOW64\reg.exe | — | wscript.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 868 | schtasks /create /f /RU "admin" /tr "C:\ProgramData\WinTrackerSP\WinTrackerSP.exe" /tn "WinTrackerSP HR" /sc HOURLY /rl HIGHEST | C:\Windows\SysWOW64\schtasks.exe | — | D4d8KIRkzuDQdsQvfQwszMgb.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 972 | schtasks /create /f /RU "admin" /tr "C:\ProgramData\MSIUpdaterV131_a5899eff6c87eb6c8acb1b5c9328dfae\MSIUpdaterV131.exe" /tn "MSIUpdaterV131_a5899eff6c87eb6c8acb1b5c9328dfae LG" /sc ONLOGON /rl HIGHEST | C:\Windows\SysWOW64\schtasks.exe | — | XXIM__e0G3DHfPWwNFbUHPL0.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1212 | /C reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Threats\ThreatIDDefaultAction" /f /v 2147780199 /t REG_SZ /d 6 | C:\Windows\SysWOW64\cmd.exe | — | forfiles.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
116 046
Read events
114 968
Write events
881
Delete events
197
Modification events
| (PID) Process: | (1796) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1796) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1796) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\15A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1796) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (1796) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\Win7AndW2K8R2-KB3191566-x64.zip | |||
| (PID) Process: | (1796) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (1796) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_3-win64-mingw.zip | |||
| (PID) Process: | (1796) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\ver4_file_x86x64.rar | |||
| (PID) Process: | (1796) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1796) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
139
Suspicious files
427
Text files
433
Unknown types
274
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1796 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1796.17911\Resource\Font\CourierStd-BoldOblique.otf | otf | |
MD5:6804E7413898972E05823ADD91B1DFC5 | SHA256:698FD9169AD62BD6FAEDD1C8E8637ABC9CC65B3B1A5BA8698242B1447303FBEE | |||
| 1796 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1796.17911\Resource\CMap\UniKS-UTF16-V | ps | |
MD5:ABA47550AFFB435A1DCC6B70EFAB5B52 | SHA256:7E403DAE40DF21FE3F9B221F7CE750F7F5BFF9CC73D82D011C4BCC48A0DB60ED | |||
| 1796 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1796.17911\Resource\CMap\UCS2-GBK-EUC | binary | |
MD5:FB9D6CD4449EC7478EE8AD1BD7465BF5 | SHA256:66CDCAED3AA94525C59A82A39A93B96885883BFFADEA1E572464D559D21443A6 | |||
| 1796 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1796.17911\Resource\Font\CourierStd-Bold.otf | otf | |
MD5:404952EC4D0AE00DD2F58FB980A99326 | SHA256:A3C25F2EC60F8D44F150CD4E478067B06CC7267FBAAF844DA600CE1C31C6E5C1 | |||
| 1796 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1796.17911\Resource\CMap\Identity-V | binary | |
MD5:B5084CBF0AB0C3DEAC97E06CD3CB2ECC | SHA256:7483DB44E4449A7AE232B30D6CBA0D8746592757D0E91BE82EC45B646C608807 | |||
| 1796 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1796.17911\Resource\Font\CourierStd-Oblique.otf | binary | |
MD5:71EC484296A30C9379607E36158CA809 | SHA256:C54815A2729D633E400A6835679613090C20B91DA6CB40FA761AAA475EFB77F5 | |||
| 1796 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1796.17911\Resource\Font\MinionPro-Regular.otf | otf | |
MD5:A4EA2690CFD854B24C968AC6CDCE9C33 | SHA256:327CB2238A82A89176FF6601139CBD0A5CDD8F8E1E057343EAE13FA9B1E10AB8 | |||
| 1796 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1796.17911\Resource\Font\CourierStd.otf | otf | |
MD5:F4C2D3851E2781B2B3FF60A2E34E81AC | SHA256:54CB5C8E9775CB432AFE32B0AF688536354AD04EF9C9F1450EE7C88A73BC884D | |||
| 1796 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1796.17911\Resource\Font\MinionPro-It.otf | binary | |
MD5:45E2315E99F24AB596F9D3AED29A0FC3 | SHA256:90DEF22F2B7B3E4AA78A160084A7A2C8F28883B700ABAEDC004DC74CBC2D9B4C | |||
| 1796 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1796.17911\Resource\Font\MyriadPro-BoldIt.otf | otf | |
MD5:01E3D8472C3CBC43799FED290B0DC219 | SHA256:7BCFA54CB8FB5B64DFE36F411D5265F7F71DC6F3B685C7ED0EB3753EE194BB45 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
93
TCP/UDP connections
260
DNS requests
204
Threats
207
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2232 | file.exe | GET | 200 | 85.192.56.26:80 | http://85.192.56.26/api/bing_release.php | unknown | — | — | unknown |
2232 | file.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?fedc2ea20a18172d | unknown | — | — | unknown |
2232 | file.exe | HEAD | — | 185.172.128.203:80 | http://185.172.128.203/dl.php | unknown | — | — | unknown |
2232 | file.exe | POST | 200 | 85.192.56.26:80 | http://85.192.56.26/api/flash.php | unknown | — | — | unknown |
2232 | file.exe | HEAD | 200 | 5.42.65.64:80 | http://5.42.65.64/download.php?pub=inte | unknown | — | — | unknown |
2232 | file.exe | POST | 200 | 85.192.56.26:80 | http://85.192.56.26/api/flash.php | unknown | — | — | unknown |
2232 | file.exe | GET | — | 193.233.132.139:80 | http://193.233.132.139/padla/fiona.exe | unknown | — | — | unknown |
2232 | file.exe | GET | — | 5.42.66.10:80 | http://5.42.66.10/download/th/retail.php | unknown | — | — | unknown |
2232 | file.exe | GET | — | 185.172.128.203:80 | http://185.172.128.203/dl.php | unknown | — | — | unknown |
2232 | file.exe | HEAD | — | 188.114.97.3:80 | http://sextipolar.sbs/qwqw | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
2232 | file.exe | 85.192.56.26:80 | — | AEZA GROUP Ltd | NL | unknown |
360 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2232 | file.exe | 104.26.8.59:443 | api.myip.com | CLOUDFLARENET | US | unknown |
2232 | file.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
2232 | file.exe | 34.117.186.192:443 | ipinfo.io | GOOGLE-CLOUD-PLATFORM | US | unknown |
2232 | file.exe | 5.42.65.64:80 | — | CJSC Kolomna-Sviaz TV | RU | unknown |
2232 | file.exe | 87.240.137.164:80 | vk.com | VKontakte Ltd | RU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.myip.com |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
ipinfo.io |
| shared |
teredo.ipv6.microsoft.com |
| whitelisted |
sextipolar.sbs |
| unknown |
dkgxxh1czdosr.cloudfront.net |
| unknown |
vk.com |
| whitelisted |
zanzibarpivo.com |
| unknown |
monoblocked.com |
| unknown |
dod.fastbutters.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2232 | file.exe | Device Retrieving External IP Address Detected | ET INFO Observed External IP Lookup Domain in TLS SNI (api .myip .com) |
2232 | file.exe | Device Retrieving External IP Address Detected | ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
2232 | file.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Lookup SSL Cert Observed (ipinfo .io) |
— | — | A Network Trojan was detected | ET MALWARE Suspected PrivateLoader Activity (POST) |
— | — | A Network Trojan was detected | ET MALWARE Suspected PrivateLoader Activity (POST) |
— | — | A Network Trojan was detected | LOADER [ANY.RUN] PrivateLoader Check-in |
2232 | file.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 32 |
2232 | file.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 1 |
— | — | Misc activity | ET INFO EXE - Served Attached HTTP |
— | — | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
8 ETPRO signatures available at the full report
Process | Message |
|---|---|
gyhJLw5s8IRyu5dmHKG8xWWi.exe | #@#^@#TGRERTERYERY |
gyhJLw5s8IRyu5dmHKG8xWWi.exe | td ydrthrhfty |
gyhJLw5s8IRyu5dmHKG8xWWi.exe | ewetwertyer eytdryrtdy |
gyhJLw5s8IRyu5dmHKG8xWWi.exe | 45 hgfch rtdyt gfch |
XXIM__e0G3DHfPWwNFbUHPL0.exe | Dk43l_dwmk438* |
XXIM__e0G3DHfPWwNFbUHPL0.exe | ewetwertyer eytdryrtdy |
XXIM__e0G3DHfPWwNFbUHPL0.exe | td ydrthrhfty |
XXIM__e0G3DHfPWwNFbUHPL0.exe | er ert 346 34634 6ch |
gyhJLw5s8IRyu5dmHKG8xWWi.exe | drthdrthdrthdr hrtd hr |
INy5MlIWJQ7M8Ba3SHyH.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|