| File name: | 2025-05-26_88931b509928b4a90937387d8a52b46c_agent-tesla_amadey_black-basta_cobalt-strike_darkgate_elex_hijackloader_luca-stealer |
| Full analysis: | https://app.any.run/tasks/eb2aa845-d20f-42b1-bd65-5af807260d78 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | May 26, 2025, 17:39:29 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 88931B509928B4A90937387D8A52B46C |
| SHA1: | D4EC0A3B6EE63F9040EB691E0CB0646CB4EAF87A |
| SHA256: | 67CC5C7C166AA2B7A2F27E6518DB1E231FFB5BBC5186CBA17693A12EF6CD7947 |
| SSDEEP: | 24576:5PPkzemDuoSut3Jh4+QQ/btosJwIA4hHmZlKH2Tw/Pq83zw0bCjvk9G661QGtIkM:5PPkzemqoSut3Jh4+QQ/btosJwIA4hHR |
MALICIOUS
Executing a file with an untrusted certificate
- 2025-05-26_88931b509928b4a90937387d8a52b46c_agent-tesla_amadey_black-basta_cobalt-strike_darkgate_elex_hijackloader_luca-stealer.exe (PID: 7412)
Run PowerShell with an invisible window
- powershell.exe (PID: 7644)
- powershell.exe (PID: 1272)
Starts NET.EXE to view/add/change user profiles
- cmd.exe (PID: 7800)
XWORM has been detected (YARA)
- iexpress.exe (PID: 7316)
ASYNCRAT has been detected (YARA)
- notepad.exe (PID: 2560)
Create files in the Startup directory
- powershell.exe (PID: 7884)
PUREHVNC has been detected (YARA)
- notepad.exe (PID: 7380)
SUSPICIOUS
Executing commands from a ".bat" file
- 2025-05-26_88931b509928b4a90937387d8a52b46c_agent-tesla_amadey_black-basta_cobalt-strike_darkgate_elex_hijackloader_luca-stealer.exe (PID: 7412)
- cmd.exe (PID: 7488)
- powershell.exe (PID: 7644)
- powershell.exe (PID: 1272)
Starts CMD.EXE for commands execution
- 2025-05-26_88931b509928b4a90937387d8a52b46c_agent-tesla_amadey_black-basta_cobalt-strike_darkgate_elex_hijackloader_luca-stealer.exe (PID: 7412)
- cmd.exe (PID: 7488)
- powershell.exe (PID: 7644)
- powershell.exe (PID: 1272)
Reads security settings of Internet Explorer
- 2025-05-26_88931b509928b4a90937387d8a52b46c_agent-tesla_amadey_black-basta_cobalt-strike_darkgate_elex_hijackloader_luca-stealer.exe (PID: 7412)
Application launched itself
- cmd.exe (PID: 7488)
Starts process via Powershell
- powershell.exe (PID: 7644)
- powershell.exe (PID: 1272)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7568)
- cmd.exe (PID: 7800)
- cmd.exe (PID: 5008)
Starts NET.EXE to map network drives
- cmd.exe (PID: 7800)
The process hides Powershell's copyright startup banner
- cmd.exe (PID: 7800)
Process drops legitimate windows executable
- cmd.exe (PID: 7800)
- powershell.exe (PID: 516)
- powershell.exe (PID: 4696)
Abuses WebDav for code execution
- svchost.exe (PID: 7900)
Uses RUNDLL32.EXE to load library
- svchost.exe (PID: 7900)
The process drops C-runtime libraries
- svchost.exe (PID: 7900)
- cmd.exe (PID: 7800)
- powershell.exe (PID: 516)
- powershell.exe (PID: 4696)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 7800)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 516)
Remote file execution via WebDAV
- net.exe (PID: 7864)
Executable content was dropped or overwritten
- powershell.exe (PID: 516)
- powershell.exe (PID: 4696)
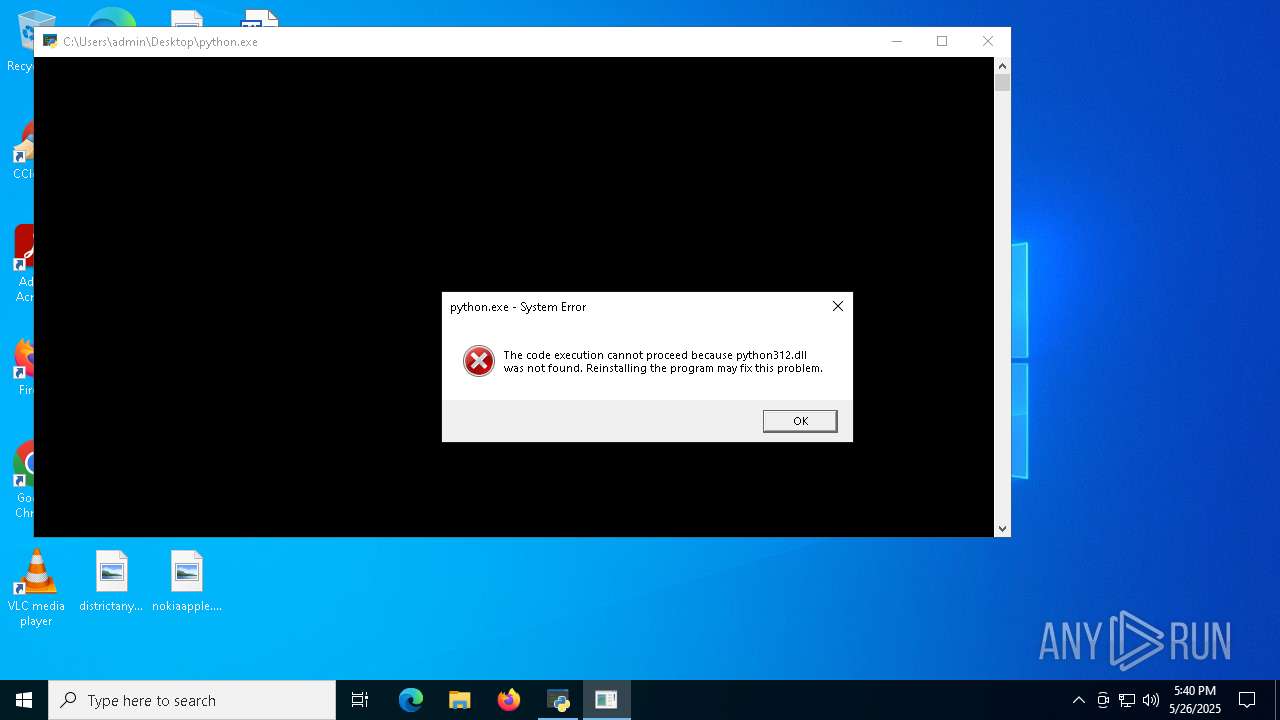
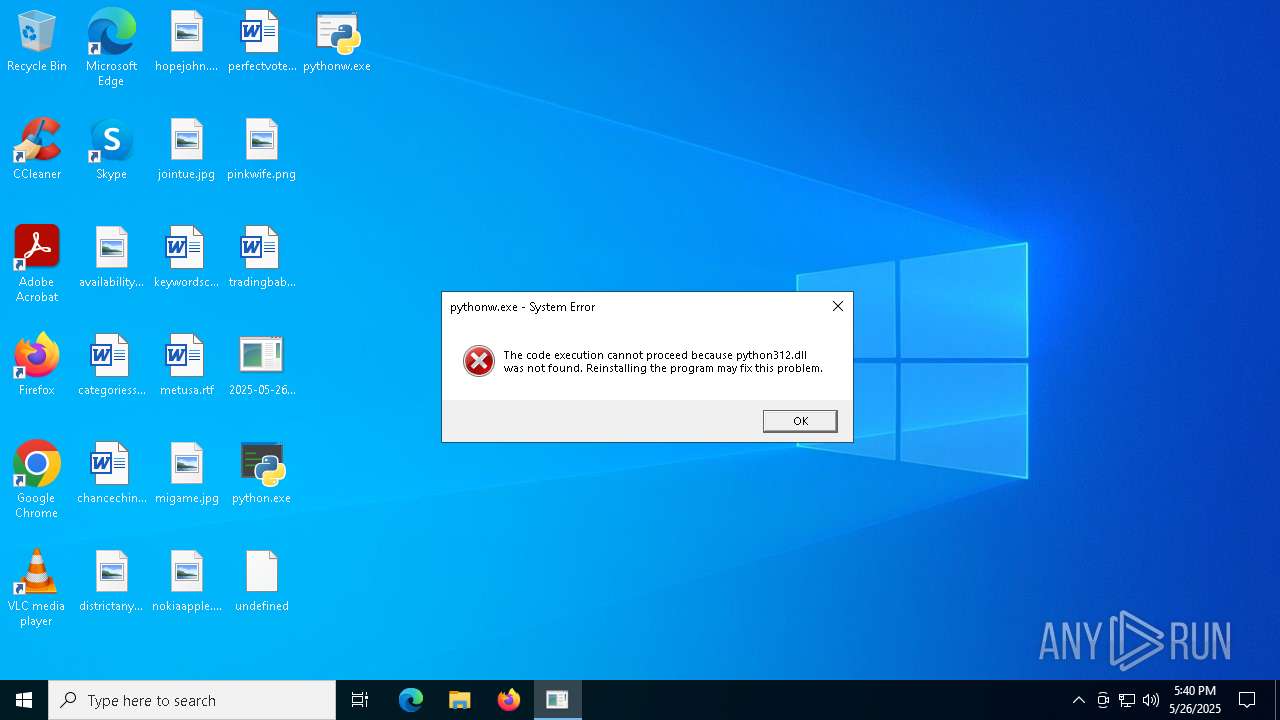
The executable file from the user directory is run by the CMD process
- python.exe (PID: 4300)
- python.exe (PID: 7284)
- python.exe (PID: 5776)
- python.exe (PID: 6132)
- python.exe (PID: 7528)
- python.exe (PID: 7692)
- python.exe (PID: 2420)
- python.exe (PID: 2552)
Loads Python modules
- python.exe (PID: 7284)
- python.exe (PID: 5776)
- python.exe (PID: 4300)
- python.exe (PID: 6132)
- python.exe (PID: 7528)
- python.exe (PID: 7692)
- python.exe (PID: 2420)
- python.exe (PID: 2552)
Process drops python dynamic module
- powershell.exe (PID: 516)
- powershell.exe (PID: 4696)
Connects to unusual port
- iexpress.exe (PID: 7316)
- notepad.exe (PID: 5260)
- notepad.exe (PID: 7764)
- notepad.exe (PID: 7548)
- RuntimeBroker.exe (PID: 8000)
- notepad.exe (PID: 2560)
There is functionality for taking screenshot (YARA)
- iexpress.exe (PID: 7316)
Downloads file from URI via Powershell
- powershell.exe (PID: 7884)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 7800)
INFO
The sample compiled with english language support
- 2025-05-26_88931b509928b4a90937387d8a52b46c_agent-tesla_amadey_black-basta_cobalt-strike_darkgate_elex_hijackloader_luca-stealer.exe (PID: 7412)
- svchost.exe (PID: 7900)
- cmd.exe (PID: 7800)
- powershell.exe (PID: 516)
- powershell.exe (PID: 4696)
Reads mouse settings
- 2025-05-26_88931b509928b4a90937387d8a52b46c_agent-tesla_amadey_black-basta_cobalt-strike_darkgate_elex_hijackloader_luca-stealer.exe (PID: 7412)
Reads the machine GUID from the registry
- 2025-05-26_88931b509928b4a90937387d8a52b46c_agent-tesla_amadey_black-basta_cobalt-strike_darkgate_elex_hijackloader_luca-stealer.exe (PID: 7412)
Checks supported languages
- 2025-05-26_88931b509928b4a90937387d8a52b46c_agent-tesla_amadey_black-basta_cobalt-strike_darkgate_elex_hijackloader_luca-stealer.exe (PID: 7412)
- python.exe (PID: 7284)
- python.exe (PID: 4300)
- python.exe (PID: 5776)
- python.exe (PID: 6132)
- python.exe (PID: 7692)
- python.exe (PID: 2420)
- python.exe (PID: 7528)
- python.exe (PID: 2552)
Checks proxy server information
- 2025-05-26_88931b509928b4a90937387d8a52b46c_agent-tesla_amadey_black-basta_cobalt-strike_darkgate_elex_hijackloader_luca-stealer.exe (PID: 7412)
- net.exe (PID: 7864)
- powershell.exe (PID: 7884)
Reads the computer name
- 2025-05-26_88931b509928b4a90937387d8a52b46c_agent-tesla_amadey_black-basta_cobalt-strike_darkgate_elex_hijackloader_luca-stealer.exe (PID: 7412)
Creates files or folders in the user directory
- 2025-05-26_88931b509928b4a90937387d8a52b46c_agent-tesla_amadey_black-basta_cobalt-strike_darkgate_elex_hijackloader_luca-stealer.exe (PID: 7412)
- python.exe (PID: 4300)
Reads the software policy settings
- 2025-05-26_88931b509928b4a90937387d8a52b46c_agent-tesla_amadey_black-basta_cobalt-strike_darkgate_elex_hijackloader_luca-stealer.exe (PID: 7412)
- net.exe (PID: 7864)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 516)
Reads security settings of Internet Explorer
- net.exe (PID: 7864)
- notepad.exe (PID: 7380)
- notepad.exe (PID: 7704)
- notepad.exe (PID: 7816)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 516)
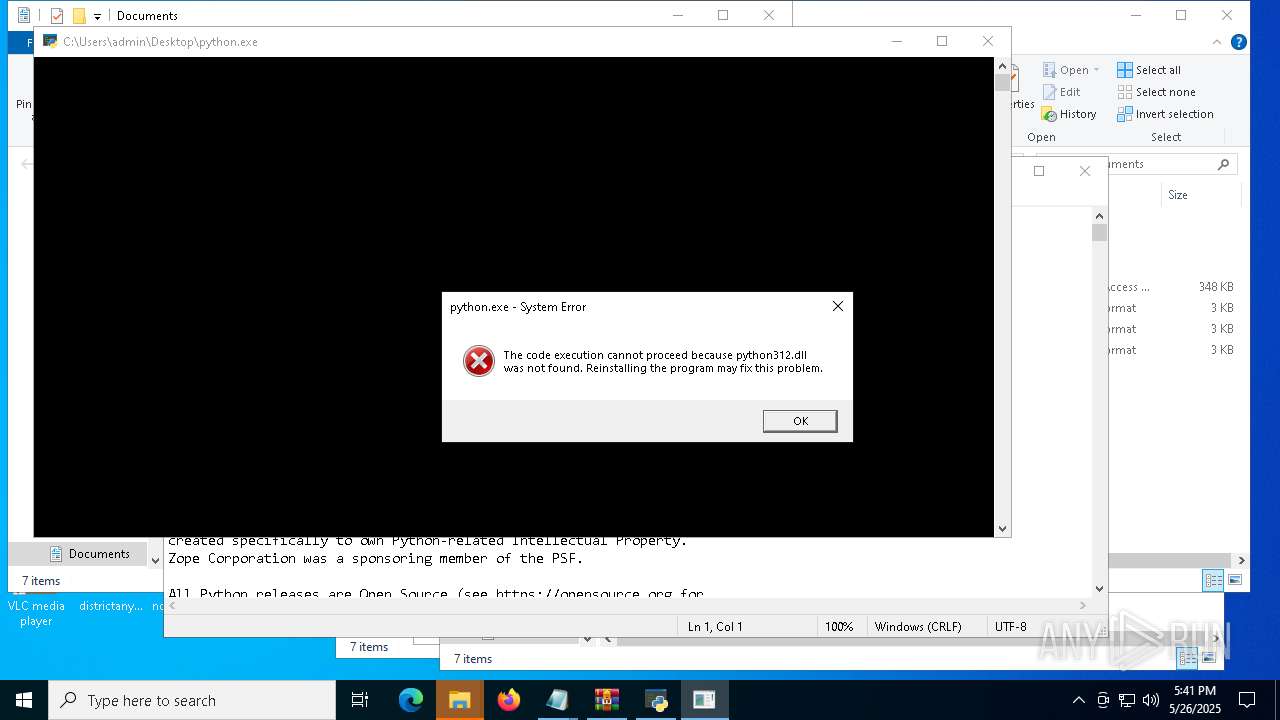
Python executable
- python.exe (PID: 4300)
- python.exe (PID: 7284)
- python.exe (PID: 7240)
- python.exe (PID: 5776)
- python.exe (PID: 6132)
- pythonw.exe (PID: 7432)
- python.exe (PID: 7528)
- python.exe (PID: 7692)
- python.exe (PID: 2420)
- python.exe (PID: 2552)
- python.exe (PID: 6944)
Manual execution by a user
- iexpress.exe (PID: 7316)
- notepad.exe (PID: 2560)
- python.exe (PID: 7240)
- notepad.exe (PID: 7380)
- pythonw.exe (PID: 7432)
- notepad.exe (PID: 7764)
- notepad.exe (PID: 7548)
- cmd.exe (PID: 7492)
- notepad.exe (PID: 7704)
- notepad.exe (PID: 7816)
- WinRAR.exe (PID: 7852)
- notepad.exe (PID: 5260)
- iexpress.exe (PID: 7788)
- RuntimeBroker.exe (PID: 8000)
- cmd.exe (PID: 5008)
- OpenWith.exe (PID: 5048)
- python.exe (PID: 6944)
- rundll32.exe (PID: 2980)
Disables trace logs
- powershell.exe (PID: 7884)
Auto-launch of the file from Startup directory
- powershell.exe (PID: 7884)
.NET Reactor protector has been detected
- notepad.exe (PID: 7380)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
XWorm
(PID) Process(7316) iexpress.exe
C2Welcome to the Adventure Game!:You are in a dark forest. Do you:
Keys
AES1. Go left
Options
Splitter2. Go right
USB drop name1
MutexYou walk left and find a treasure chest. Do you:
AsyncRat
(PID) Process(2560) notepad.exe
C2 (3)collegefordlincoln-gmbh.xyz
aserja.twilightparadox.com
laserjan.duckdns.org
Ports (1)2011
Version
Options
AutoRunfalse
MutexuQq6nfZ斯B5Δ6K德GqשΖy7aty
InstallFolder%AppData%
Certificates
Cert1MIICKTCCAZKgAwIBAgIVALuTRehVEwwhbWBlTN2tjQJuaebxMA0GCSqGSIb3DQEBDQUAMF0xDjAMBgNVBAMMBUVCT0xBMRMwEQYDVQQLDApxd3FkYW5jaHVuMRwwGgYDVQQKDBNEY1JhdCBCeSBxd3FkYW5jaHVuMQswCQYDVQQHDAJTSDELMAkGA1UEBhMCQ04wHhcNMjMwOTE1MTA0ODM0WhcNMzQwNjI0MTA0ODM0WjAQMQ4wDAYDVQQDDAVEY1JhdDCBnzANBgkqhkiG9w0BAQEFAAOBjQAwgYkCgYEA...
Server_SignatureQOu7GUl12Y8SVS+BP7TYAnD+JXHGp/uy0uqm8QcIe9Rl0gZBPxheDu8NZ07OkBEwsu7HiU4fwe9k8uR5RTts0dJbVH8NHMl2biHdu6hBCKT4SFLZPiWbphrnsc9wySHfhxJO0cLu7iXIVTeWv4dG1osBDPG3mpdTgpWY0uetX9E=
Keys
AESf0ef87dd49da3a47d56fc8025bca56af45b0be75b2a26be4e67c66be5ecbc568
SaltDcRatByqwqdanchun
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:05:26 11:13:59+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.16 |
| CodeSize: | 633856 |
| InitializedDataSize: | 282112 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x20577 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (British) |
| CharacterSet: | Unicode |
Total processes
179
Monitored processes
52
Malicious processes
9
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | powershell -nologo -noprofile -command "Expand-Archive -Path 'C:\Users\admin\AppData\Roaming\pyembed\ThunderB.zip' -DestinationPath 'C:\Users\admin\AppData\Roaming\pyembed' -Force" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1272 | powershell -WindowStyle Hidden -Command "Start-Process -FilePath 'C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\NFC.bat' -ArgumentList 'hidden' -WindowStyle Hidden" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2420 | "C:\Users\admin\AppData\Roaming\pyembed\Python312\python.exe" "C:\Users\admin\AppData\Roaming\pyembed\Python312\dCybx.py" ::7 | C:\Users\admin\AppData\Roaming\pyembed\python312\python.exe | — | cmd.exe | |||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python Exit code: 0 Version: 3.12.10 Modules
| |||||||||||||||
| 2552 | "C:\Users\admin\AppData\Roaming\pyembed\Python312\python.exe" "C:\Users\admin\AppData\Roaming\pyembed\Python312\aV35pCybx.py" ::8 | C:\Users\admin\AppData\Roaming\pyembed\python312\python.exe | — | cmd.exe | |||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python Exit code: 0 Version: 3.12.10 Modules
| |||||||||||||||
| 2560 | C:\Windows\System32\notepad.exe | C:\Windows\System32\notepad.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
AsyncRat(PID) Process(2560) notepad.exe C2 (3)collegefordlincoln-gmbh.xyz aserja.twilightparadox.com laserjan.duckdns.org Ports (1)2011 Version Options AutoRunfalse MutexuQq6nfZ斯B5Δ6K德GqשΖy7aty InstallFolder%AppData% Certificates Cert1MIICKTCCAZKgAwIBAgIVALuTRehVEwwhbWBlTN2tjQJuaebxMA0GCSqGSIb3DQEBDQUAMF0xDjAMBgNVBAMMBUVCT0xBMRMwEQYDVQQLDApxd3FkYW5jaHVuMRwwGgYDVQQKDBNEY1JhdCBCeSBxd3FkYW5jaHVuMQswCQYDVQQHDAJTSDELMAkGA1UEBhMCQ04wHhcNMjMwOTE1MTA0ODM0WhcNMzQwNjI0MTA0ODM0WjAQMQ4wDAYDVQQDDAVEY1JhdDCBnzANBgkqhkiG9w0BAQEFAAOBjQAwgYkCgYEA... Server_SignatureQOu7GUl12Y8SVS+BP7TYAnD+JXHGp/uy0uqm8QcIe9Rl0gZBPxheDu8NZ07OkBEwsu7HiU4fwe9k8uR5RTts0dJbVH8NHMl2biHdu6hBCKT4SFLZPiWbphrnsc9wySHfhxJO0cLu7iXIVTeWv4dG1osBDPG3mpdTgpWY0uetX9E= Keys AESf0ef87dd49da3a47d56fc8025bca56af45b0be75b2a26be4e67c66be5ecbc568 SaltDcRatByqwqdanchun | |||||||||||||||
| 2980 | "C:\WINDOWS\system32\rundll32.exe" cryptext.dll,CryptExtOpenCAT C:\Users\admin\Desktop\python.cat | C:\Windows\System32\rundll32.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4300 | "C:\Users\admin\AppData\Roaming\pyembed\Python312\python.exe" "C:\Users\admin\AppData\Roaming\pyembed\Python312\vv.py" ::1 | C:\Users\admin\AppData\Roaming\pyembed\python312\python.exe | — | cmd.exe | |||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python Exit code: 0 Version: 3.12.10 Modules
| |||||||||||||||
| 4696 | powershell -nologo -noprofile -command "Expand-Archive -Path 'C:\Users\admin\Contacts\wab\Startup.zip' -DestinationPath 'C:\Users\admin\Contacts\wab' -Force" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4988 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\NFC.bat" hidden " | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 9009 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
46 780
Read events
46 736
Write events
37
Delete events
7
Modification events
| (PID) Process: | (7412) 2025-05-26_88931b509928b4a90937387d8a52b46c_agent-tesla_amadey_black-basta_cobalt-strike_darkgate_elex_hijackloader_luca-stealer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7412) 2025-05-26_88931b509928b4a90937387d8a52b46c_agent-tesla_amadey_black-basta_cobalt-strike_darkgate_elex_hijackloader_luca-stealer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7412) 2025-05-26_88931b509928b4a90937387d8a52b46c_agent-tesla_amadey_black-basta_cobalt-strike_darkgate_elex_hijackloader_luca-stealer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (7864) net.exe | Key: | HKEY_CURRENT_USER\Network\R |
| Operation: | write | Name: | RemotePath |
Value: \\upgrades-huntington-shared-mil.trycloudflare.com@SSL\DavWWWRoot | |||
| (PID) Process: | (7864) net.exe | Key: | HKEY_CURRENT_USER\Network\R |
| Operation: | write | Name: | UserName |
Value: anonymous | |||
| (PID) Process: | (7864) net.exe | Key: | HKEY_CURRENT_USER\Network\R |
| Operation: | write | Name: | ProviderName |
Value: Web Client Network | |||
| (PID) Process: | (7864) net.exe | Key: | HKEY_CURRENT_USER\Network\R |
| Operation: | write | Name: | ProviderType |
Value: 3014656 | |||
| (PID) Process: | (7864) net.exe | Key: | HKEY_CURRENT_USER\Network\R |
| Operation: | write | Name: | ConnectionType |
Value: 1 | |||
| (PID) Process: | (7864) net.exe | Key: | HKEY_CURRENT_USER\Network\R |
| Operation: | write | Name: | ConnectFlags |
Value: 0 | |||
| (PID) Process: | (7864) net.exe | Key: | HKEY_CURRENT_USER\Network\R |
| Operation: | write | Name: | DeferFlags |
Value: 1 | |||
Executable files
64
Suspicious files
19
Text files
36
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7412 | 2025-05-26_88931b509928b4a90937387d8a52b46c_agent-tesla_amadey_black-basta_cobalt-strike_darkgate_elex_hijackloader_luca-stealer.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\cso[1].bat | text | |
MD5:E370F0BE8A9805D0FFE3444B62B6A681 | SHA256:263BE77B71FE1943F195FCD1C40FA4DA2D3BBA4A1B2860A50FA7F88D40DBDDE4 | |||
| 7644 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:1D101683348CD4AF9CE486ACB5D8E498 | SHA256:EA36FA9699D811825A5AB65F278FE5BFAAB3EED7950E520987585D44C31DAC4D | |||
| 516 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_an4rssyo.ul3.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7644 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_fnujpdvu.vfy.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7800 | cmd.exe | C:\Users\admin\AppData\Roaming\pyembed\ThunderB.zip | compressed | |
MD5:B38E36CA6B76879D335ABFBD0C22B11C | SHA256:25A9FD99F59495B5976F74F5190E6055E5EDAE0DA0AB6F124C31E78644540E33 | |||
| 516 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_43sslsxu.wwt.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7900 | svchost.exe | C:\Windows\ServiceProfiles\LocalService\AppData\Local\Temp\TfsStore\Tfs_DAV\{48E5B4F0-2CE6-423B-8968-DFDA3EDB54A7}.zip | compressed | |
MD5:B38E36CA6B76879D335ABFBD0C22B11C | SHA256:25A9FD99F59495B5976F74F5190E6055E5EDAE0DA0AB6F124C31E78644540E33 | |||
| 516 | powershell.exe | C:\Users\admin\AppData\Roaming\pyembed\python312\_bz2.pyd | executable | |
MD5:2BE172C3086EFE56C7E1D3279142295A | SHA256:7F20792D8600203F7AC0C229E1387E8D40328F9DA22D2ACBA95B3761B5E49950 | |||
| 516 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_0kwr31n3.2lf.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 516 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_113ssg5i.1u3.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
54
TCP/UDP connections
90
DNS requests
44
Threats
67
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | POST | 400 | 20.190.159.2:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 20.190.159.23:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 40.126.31.129:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 40.126.31.2:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 20.190.159.131:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | OPTIONS | 200 | 104.16.230.132:443 | https://upgrades-huntington-shared-mil.trycloudflare.com/ | unknown | — | — | unknown |
— | — | PROPFIND | 207 | 104.16.231.132:443 | https://upgrades-huntington-shared-mil.trycloudflare.com/ | unknown | xml | 779 b | whitelisted |
— | — | PROPFIND | 207 | 104.16.230.132:443 | https://upgrades-huntington-shared-mil.trycloudflare.com/ | unknown | xml | 779 b | whitelisted |
— | — | PROPFIND | 207 | 104.16.231.132:443 | https://upgrades-huntington-shared-mil.trycloudflare.com/ThunderB.zip | unknown | xml | 860 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1196 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7412 | 2025-05-26_88931b509928b4a90937387d8a52b46c_agent-tesla_amadey_black-basta_cobalt-strike_darkgate_elex_hijackloader_luca-stealer.exe | 104.16.230.132:443 | towers-railroad-tion-opportunity.trycloudflare.com | CLOUDFLARENET | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2104 | svchost.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1196 | RUXIMICS.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
towers-railroad-tion-opportunity.trycloudflare.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
upgrades-huntington-shared-mil.trycloudflare.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to Commonly Abused Cloudflare Domain (trycloudflare .com) |
7412 | 2025-05-26_88931b509928b4a90937387d8a52b46c_agent-tesla_amadey_black-basta_cobalt-strike_darkgate_elex_hijackloader_luca-stealer.exe | Misc activity | ET HUNTING TryCloudFlare Domain in TLS SNI |
7412 | 2025-05-26_88931b509928b4a90937387d8a52b46c_agent-tesla_amadey_black-basta_cobalt-strike_darkgate_elex_hijackloader_luca-stealer.exe | Misc activity | ET INFO Observed trycloudflare .com Domain in TLS SNI |
2196 | svchost.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Cloudflare Tunnel (TryCloudflare) |
— | — | Potential Corporate Privacy Violation | ET INFO Autoit Windows Automation tool User-Agent in HTTP Request - Possibly Hostile |
2196 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to Commonly Abused Cloudflare Domain (trycloudflare .com) |
2196 | svchost.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Cloudflare Tunnel (TryCloudflare) |
7864 | net.exe | Misc activity | ET HUNTING TryCloudFlare Domain in TLS SNI |
7864 | net.exe | Misc activity | ET INFO Observed trycloudflare .com Domain in TLS SNI |
— | — | Potential Corporate Privacy Violation | POLICY [ANY.RUN] WebDav activity has been detected |