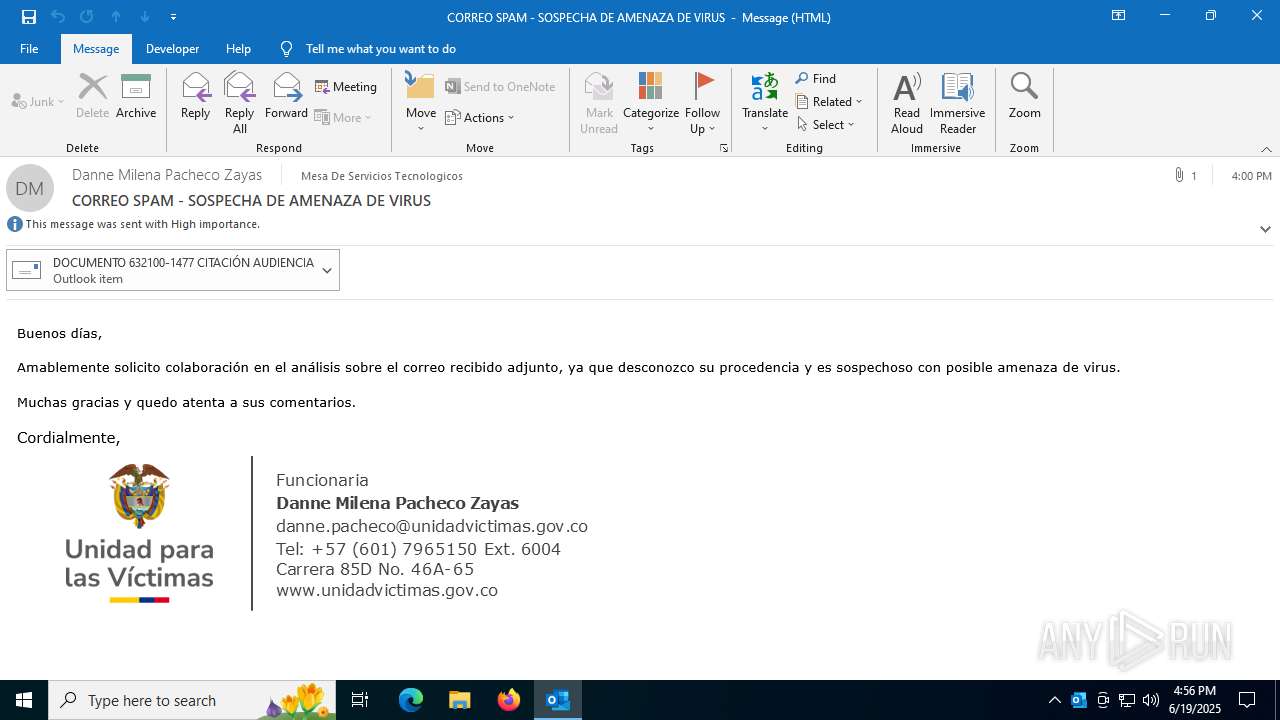
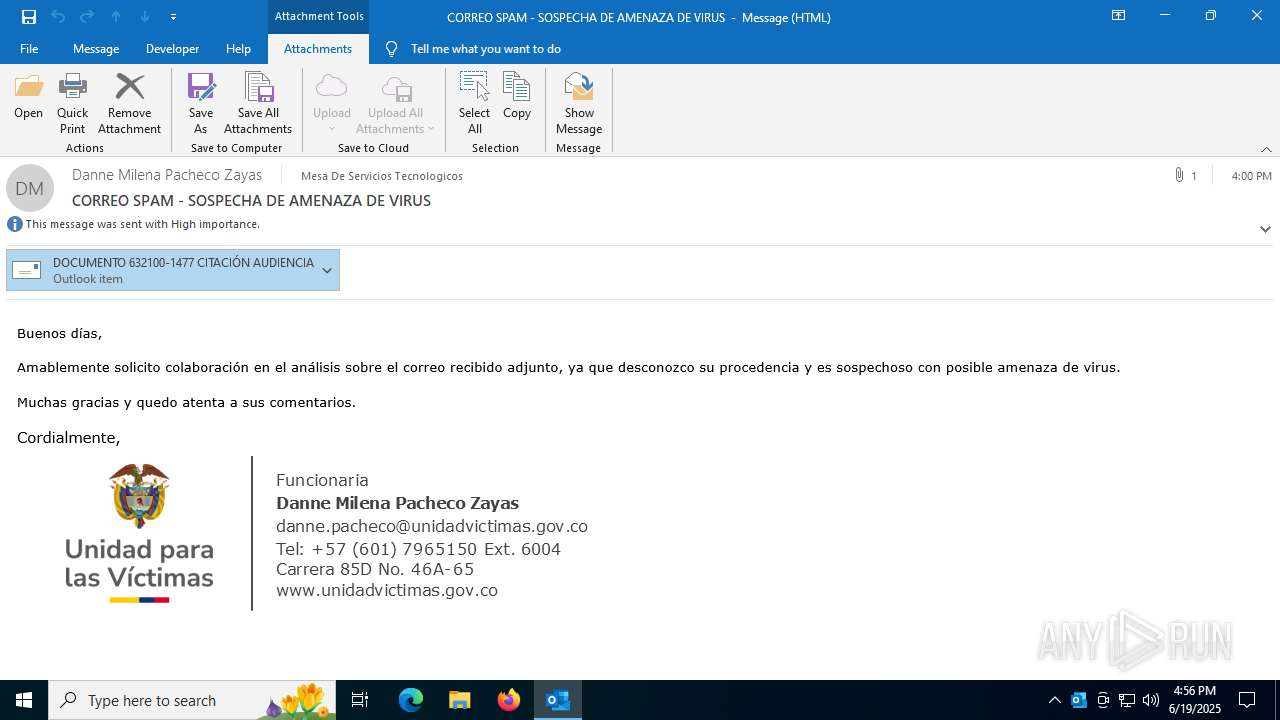
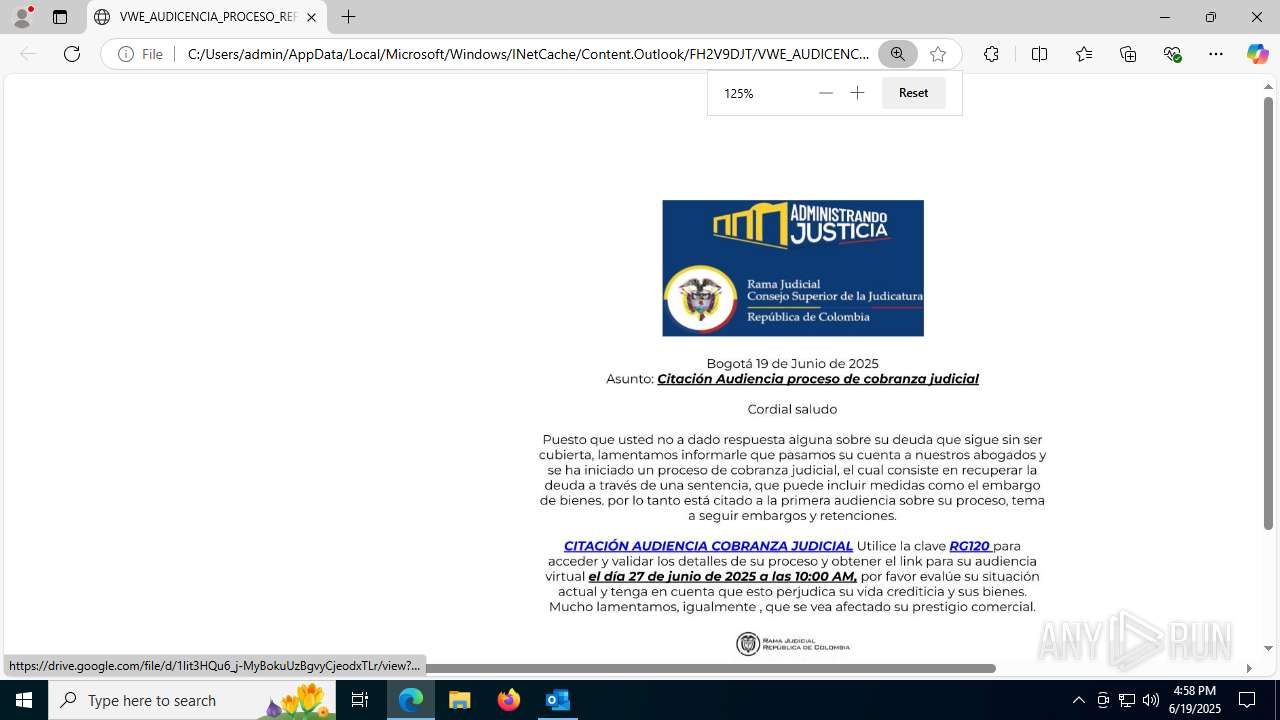
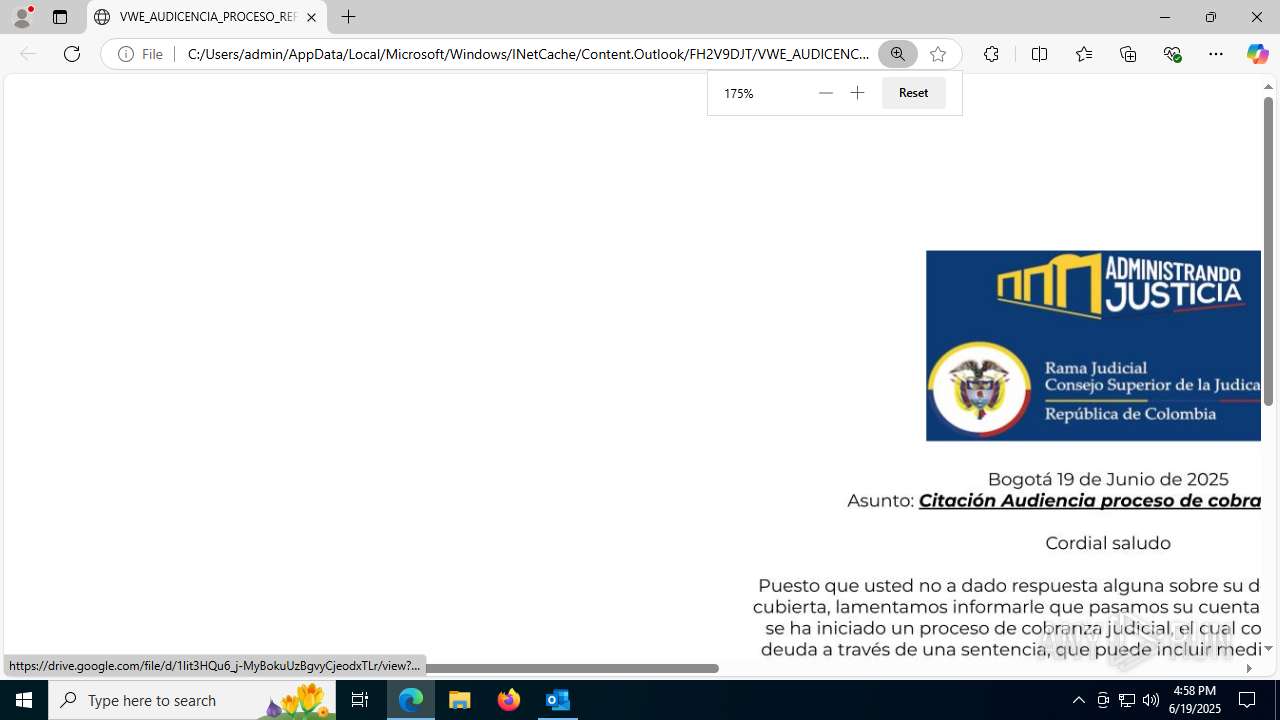
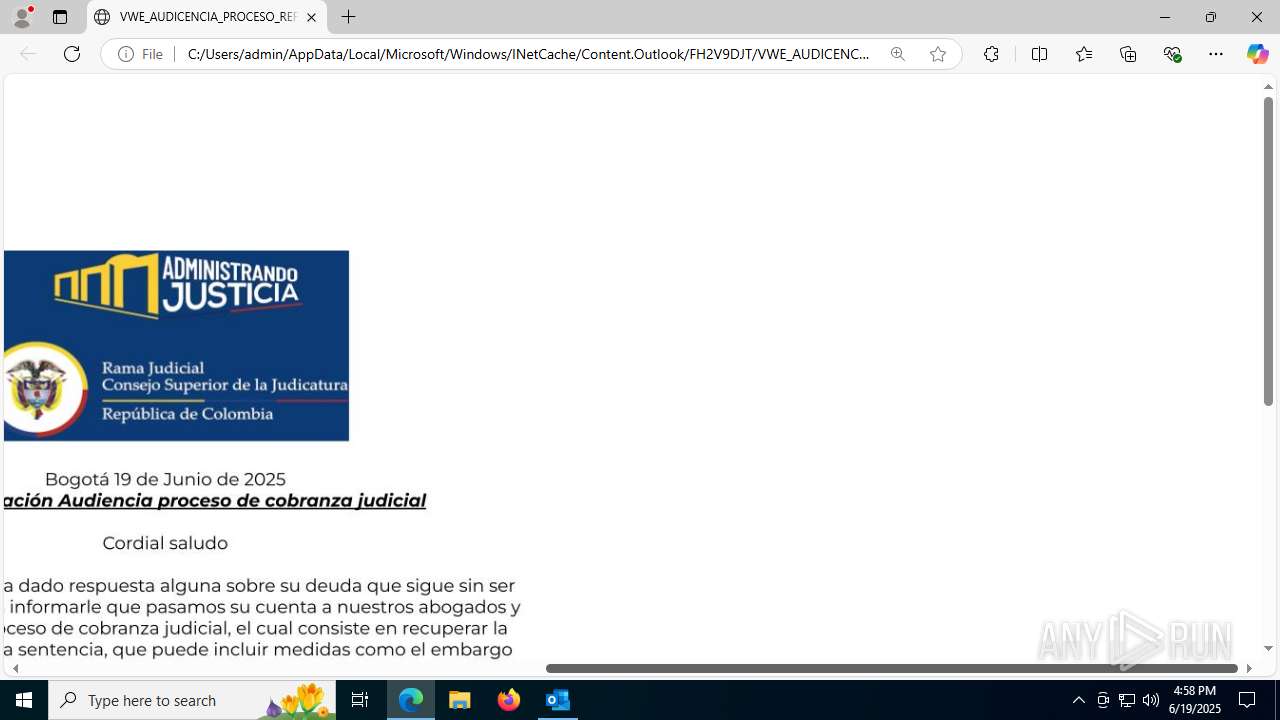
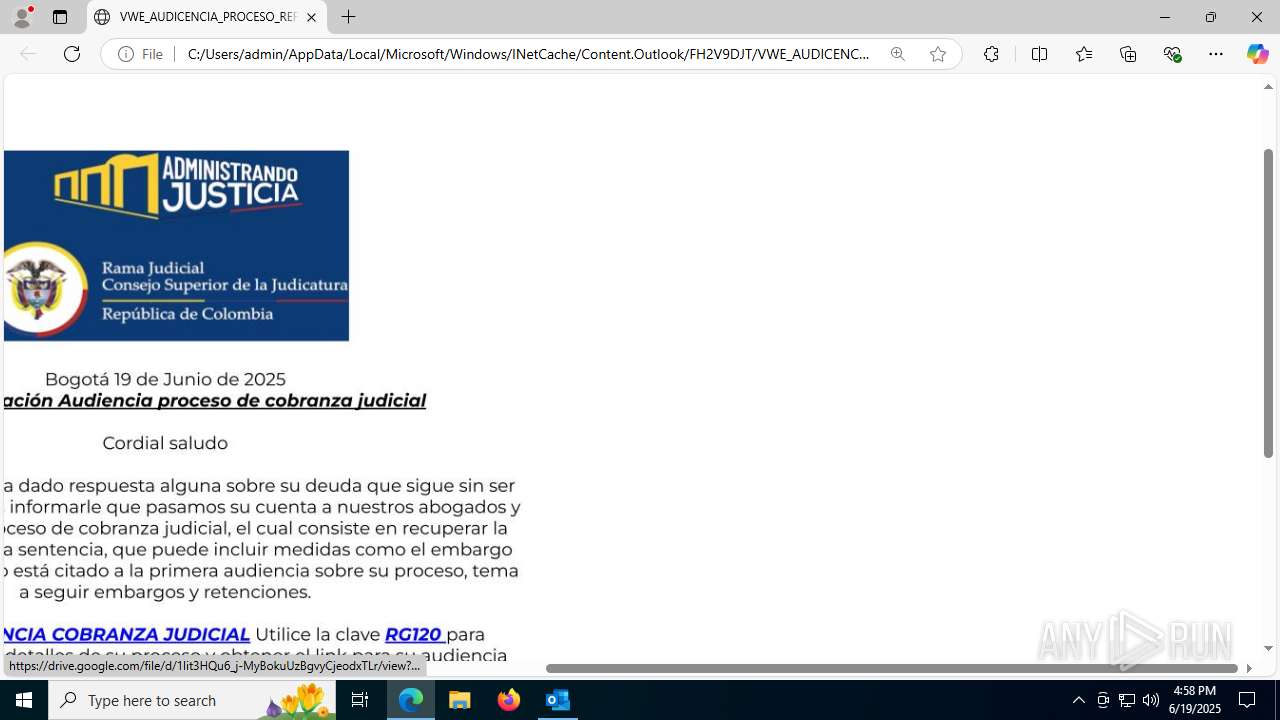
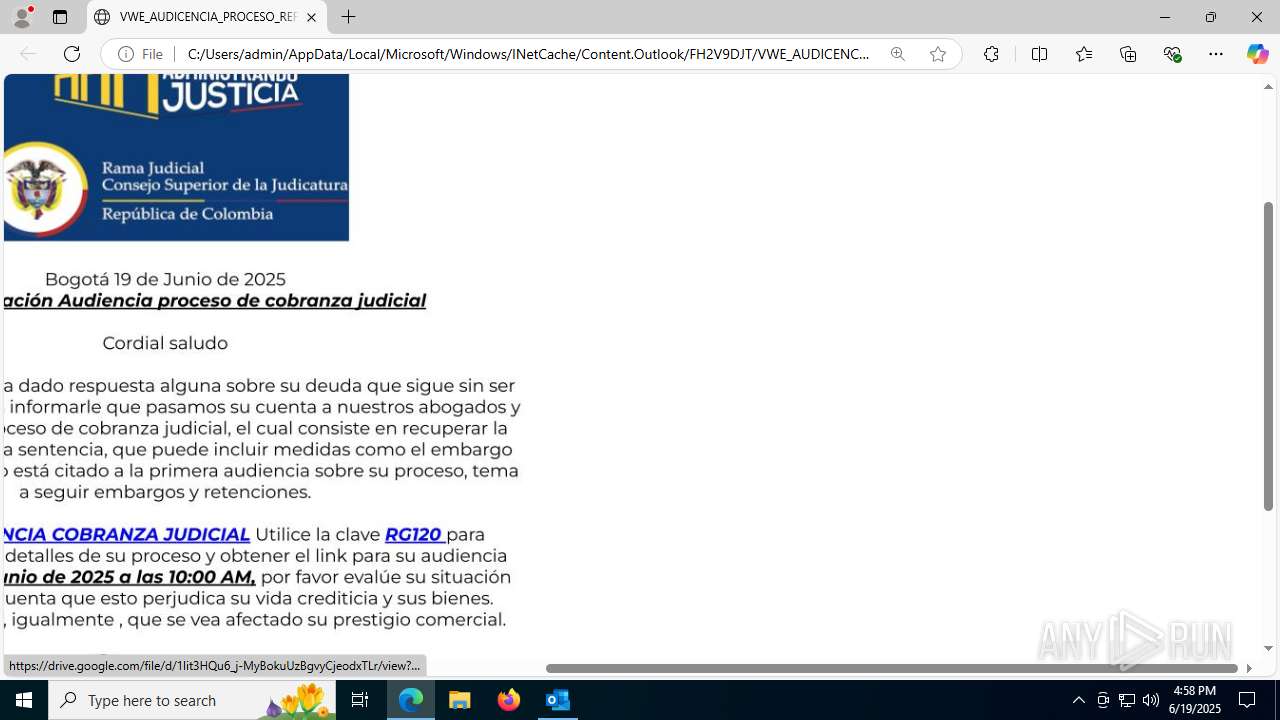
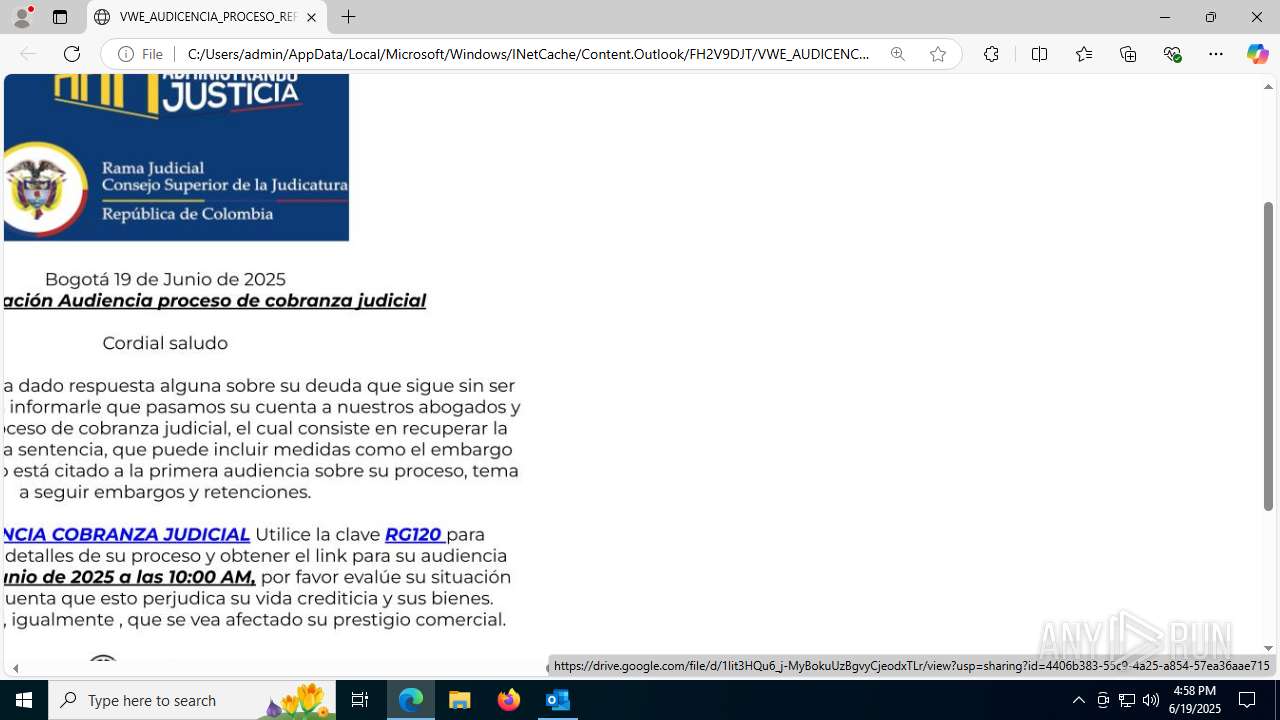
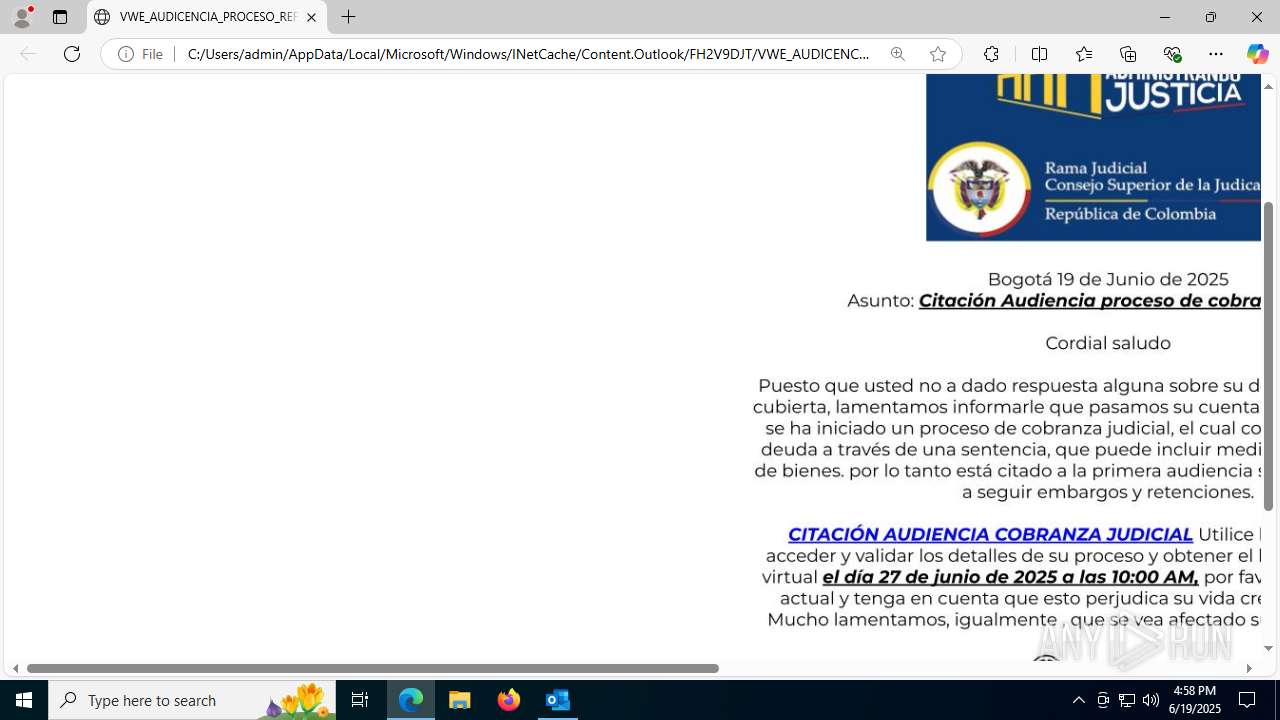
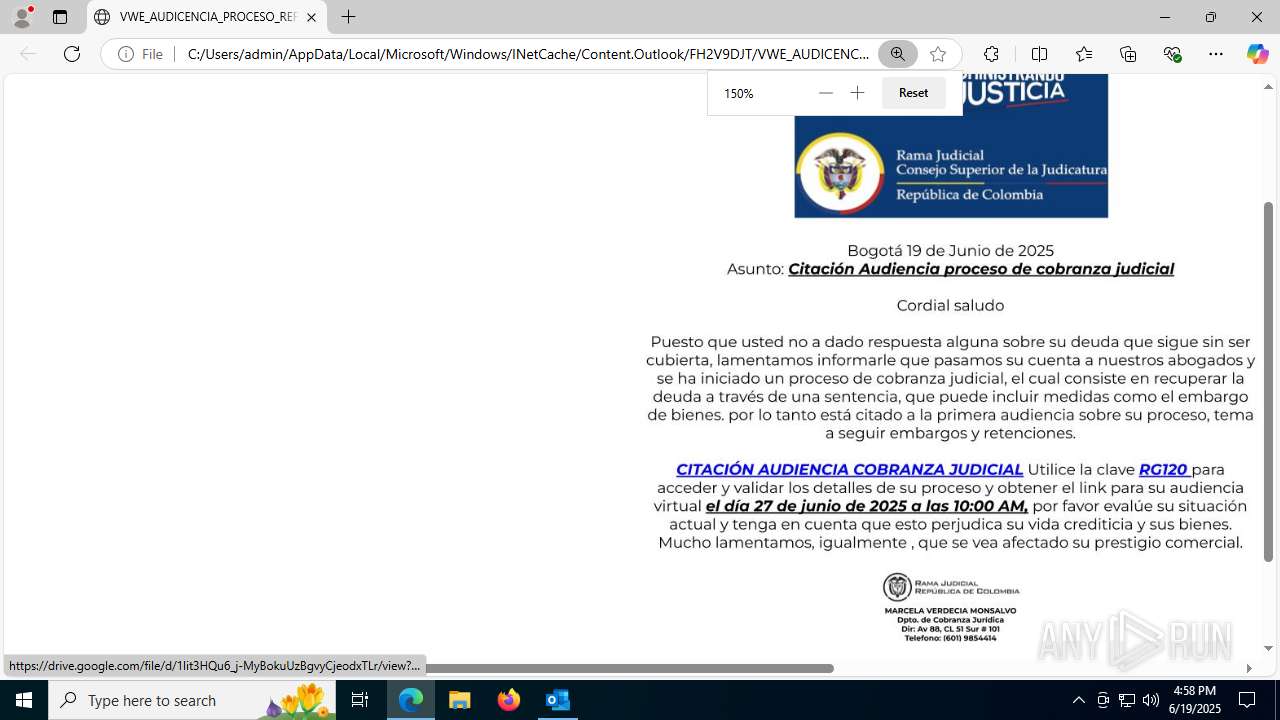
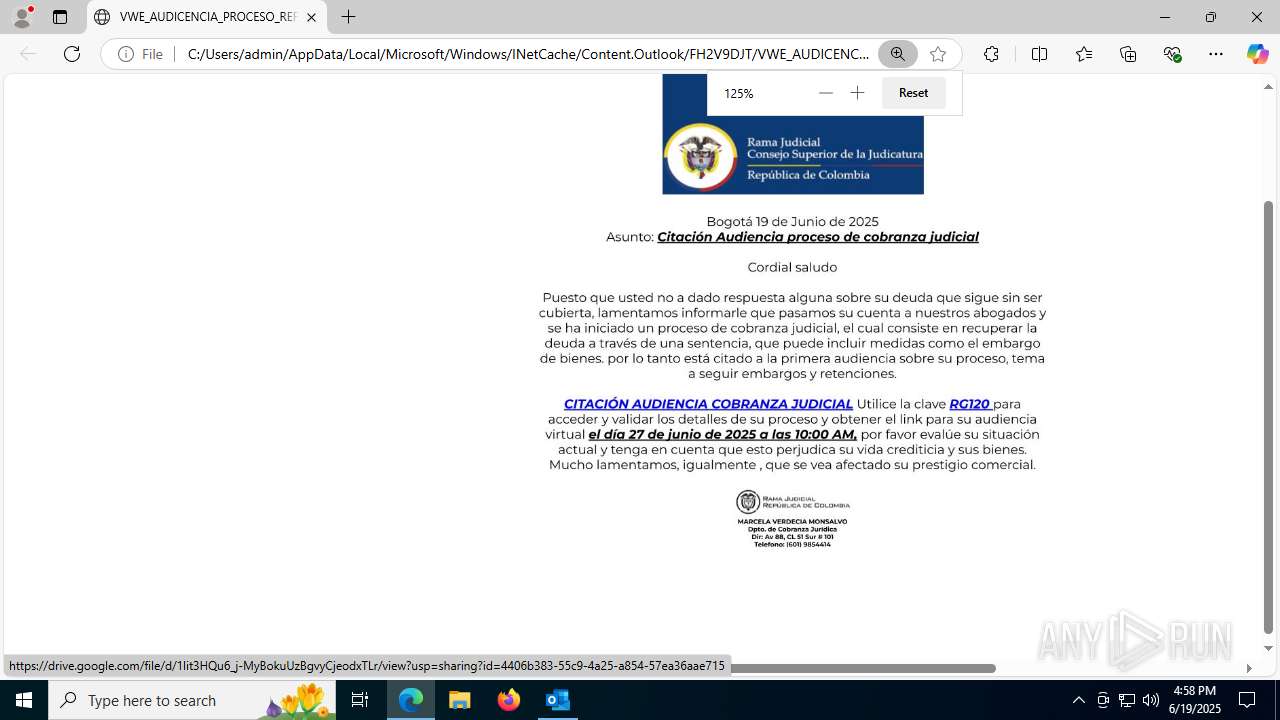
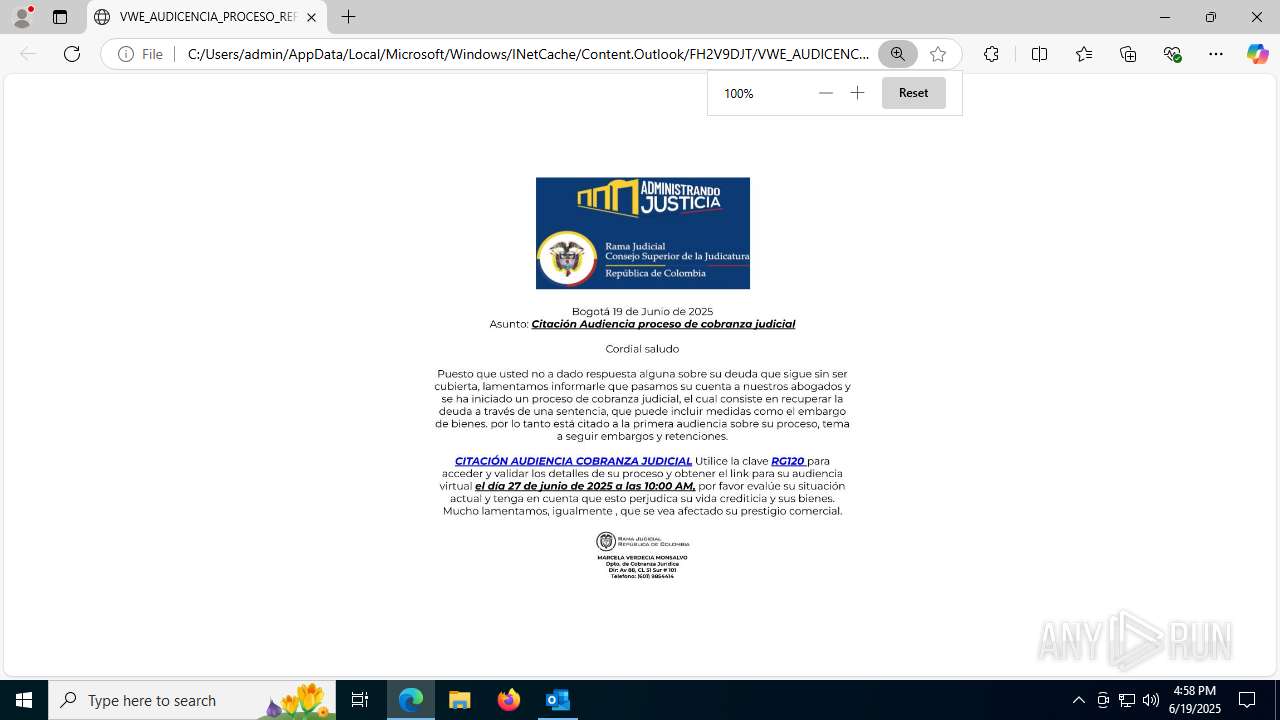
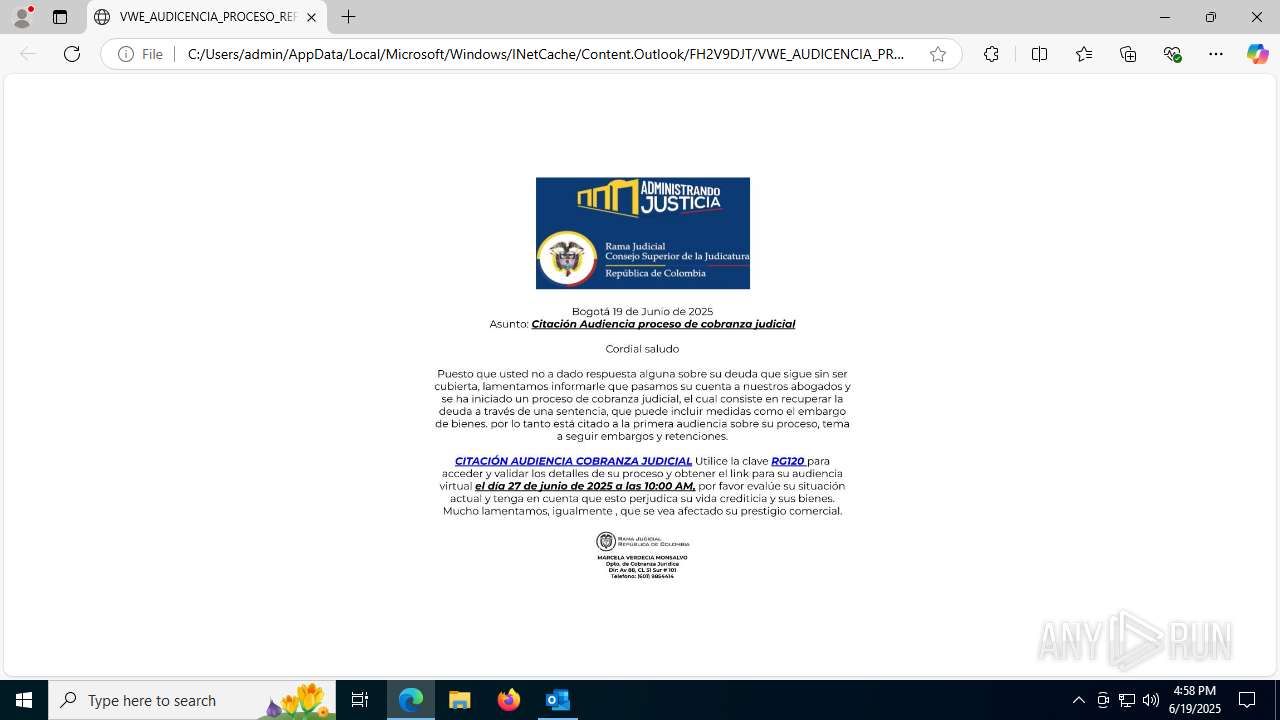
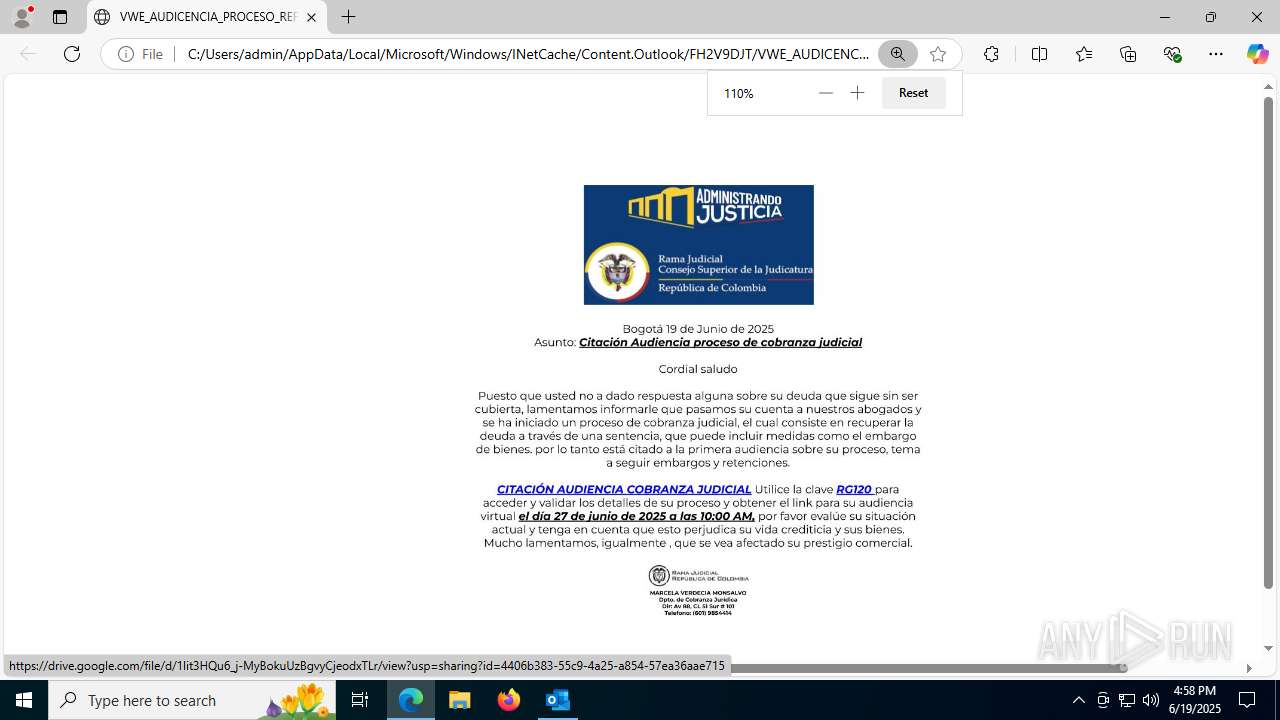
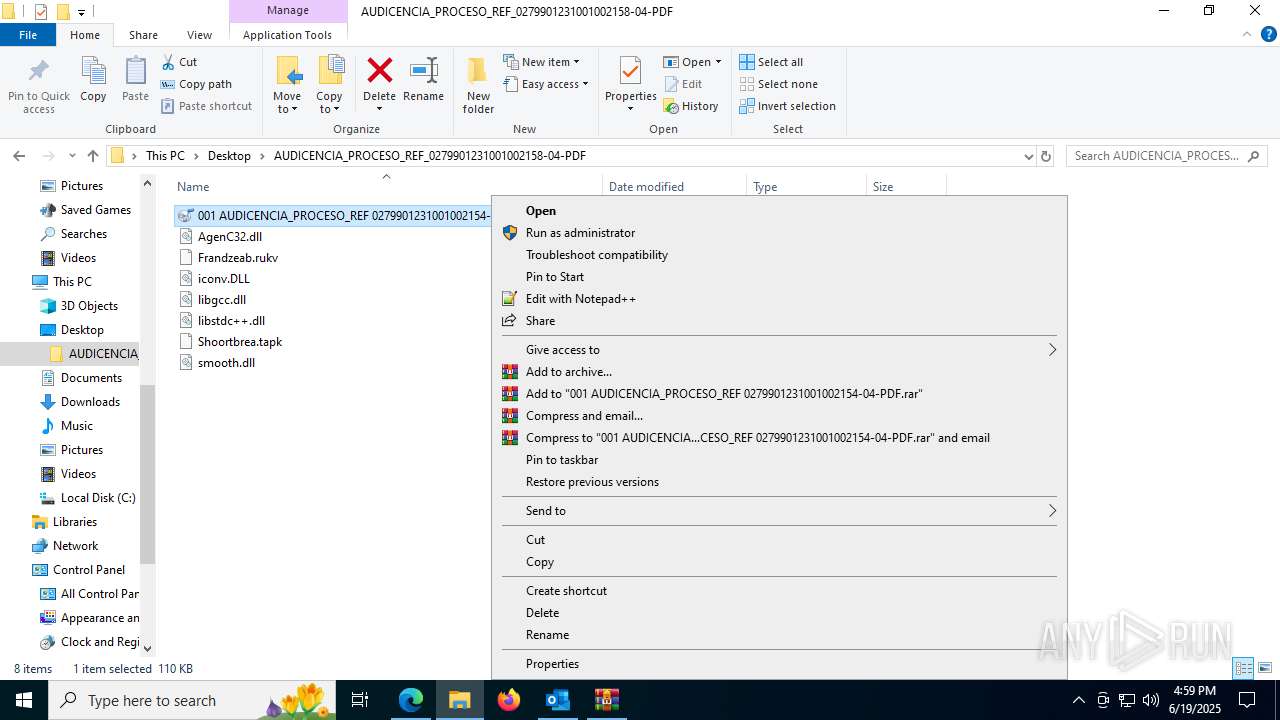
| File name: | CORREO SPAM - SOSPECHA DE AMENAZA DE VIRUS.msg |
| Full analysis: | https://app.any.run/tasks/940f55c6-0837-4bef-b36d-e2f67a21e016 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | June 19, 2025, 16:56:21 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | 737B52AA679CE955781283F97478BB40 |
| SHA1: | F038776DC8D51D24907BEBC2F1AB0BE886AB7367 |
| SHA256: | 67AA88315E2C63E0525BCB4D5F25F3D353F12770180D7DA2B939D9CE41B7D834 |
| SSDEEP: | 6144:iIe/rMNX1UG8sBU7BE4n1lxhQztM+Ph95k:iBrob8sBU7u4n1lfF6k |
MALICIOUS
GENERIC has been found (auto)
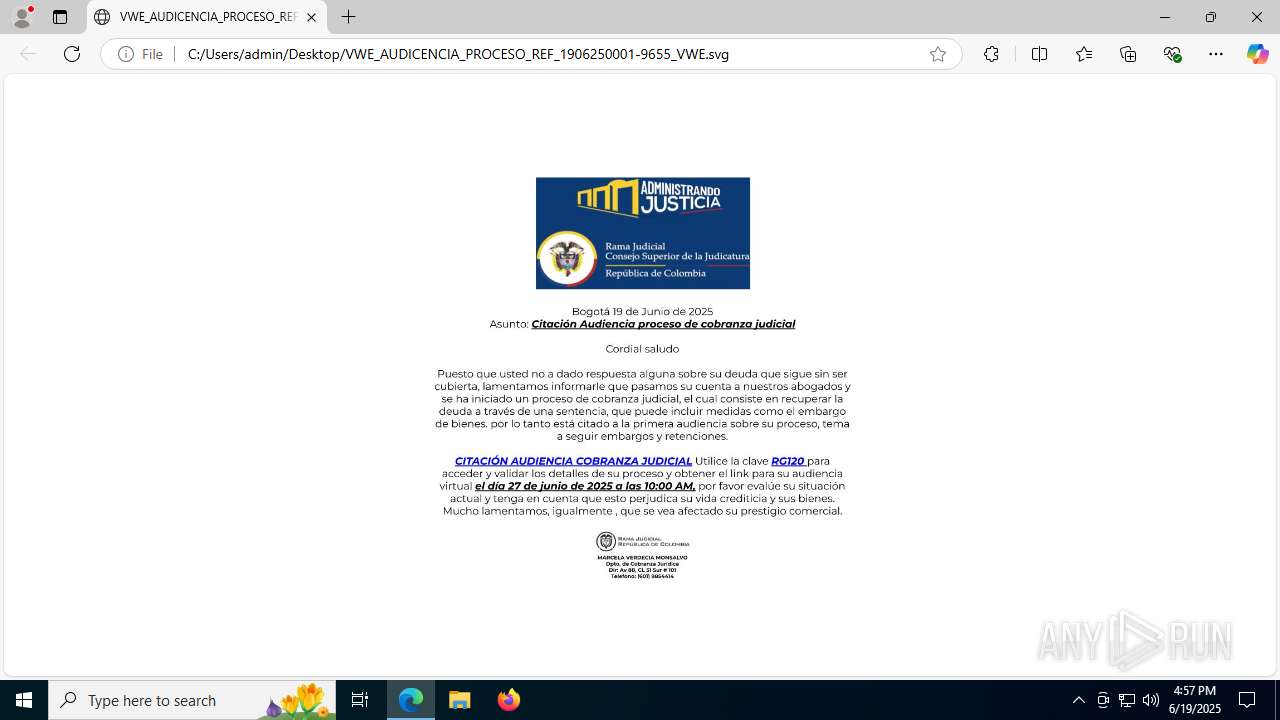
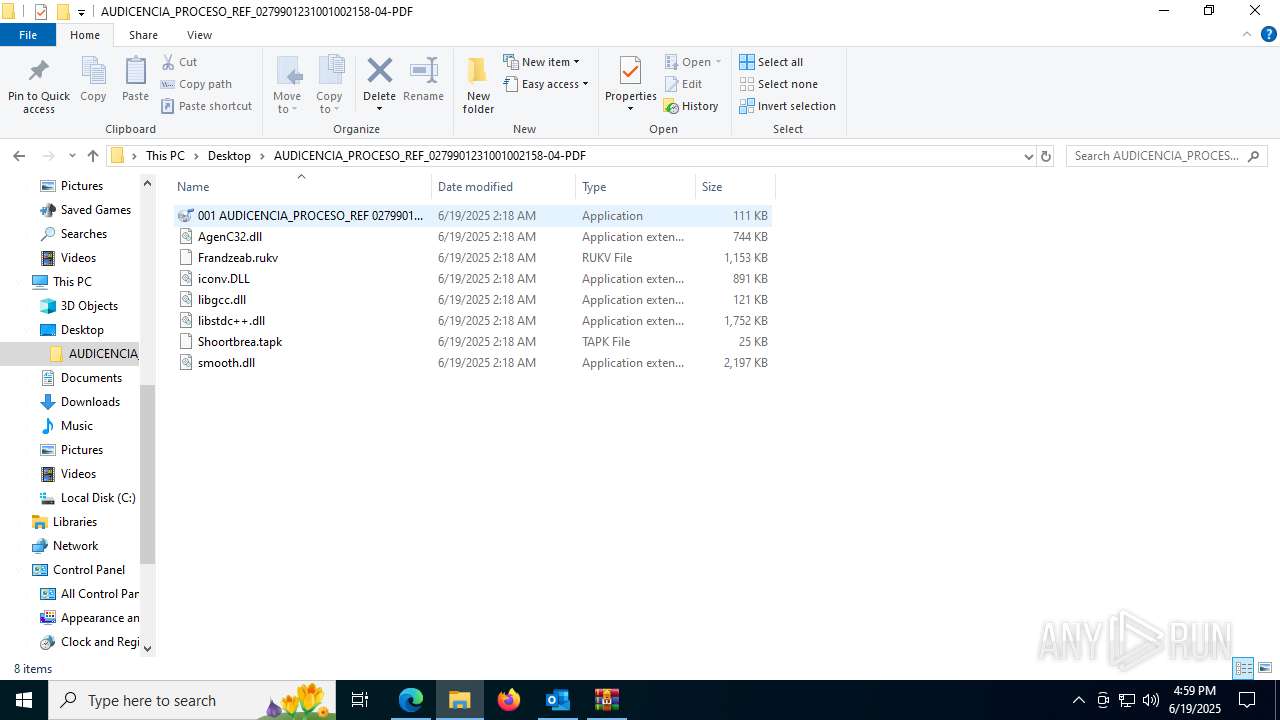
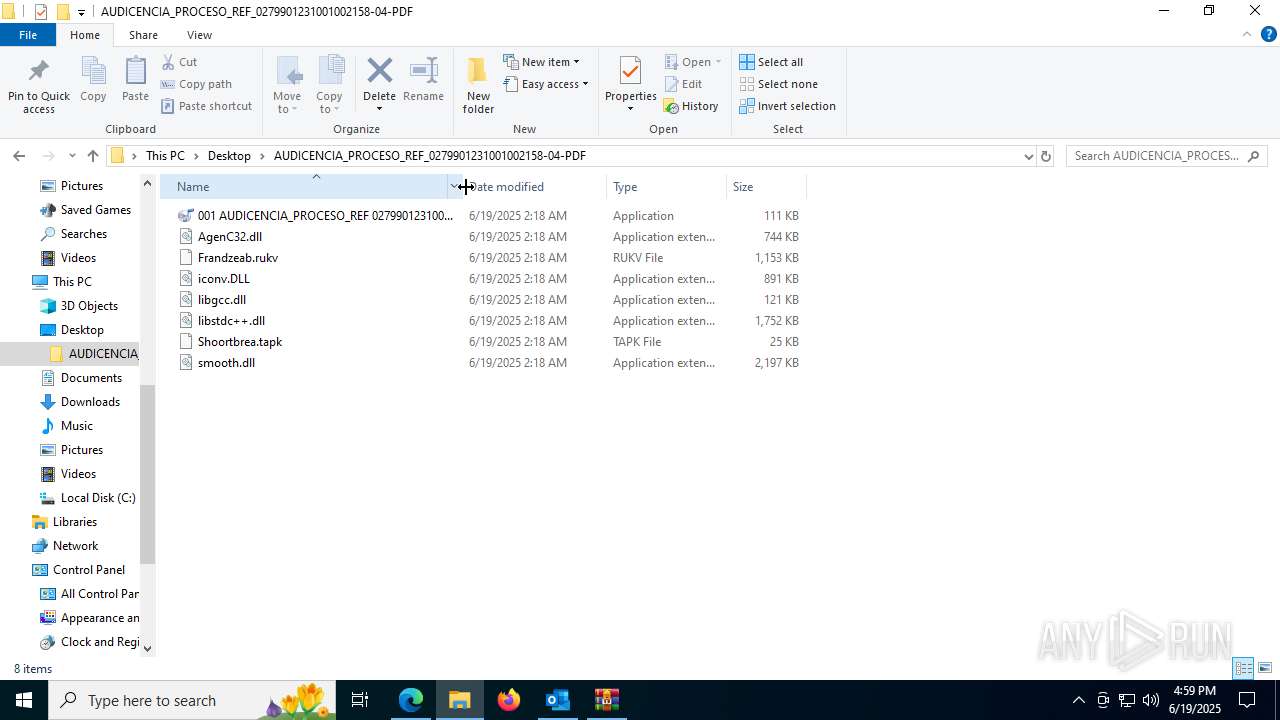
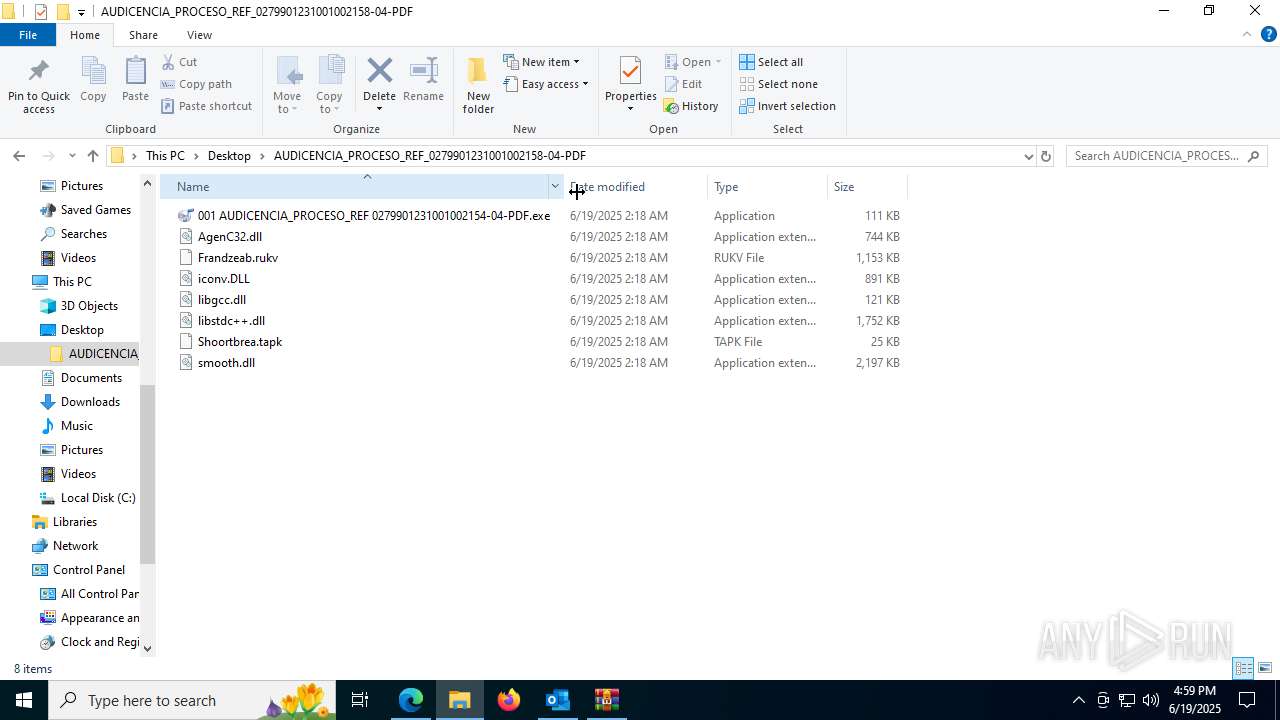
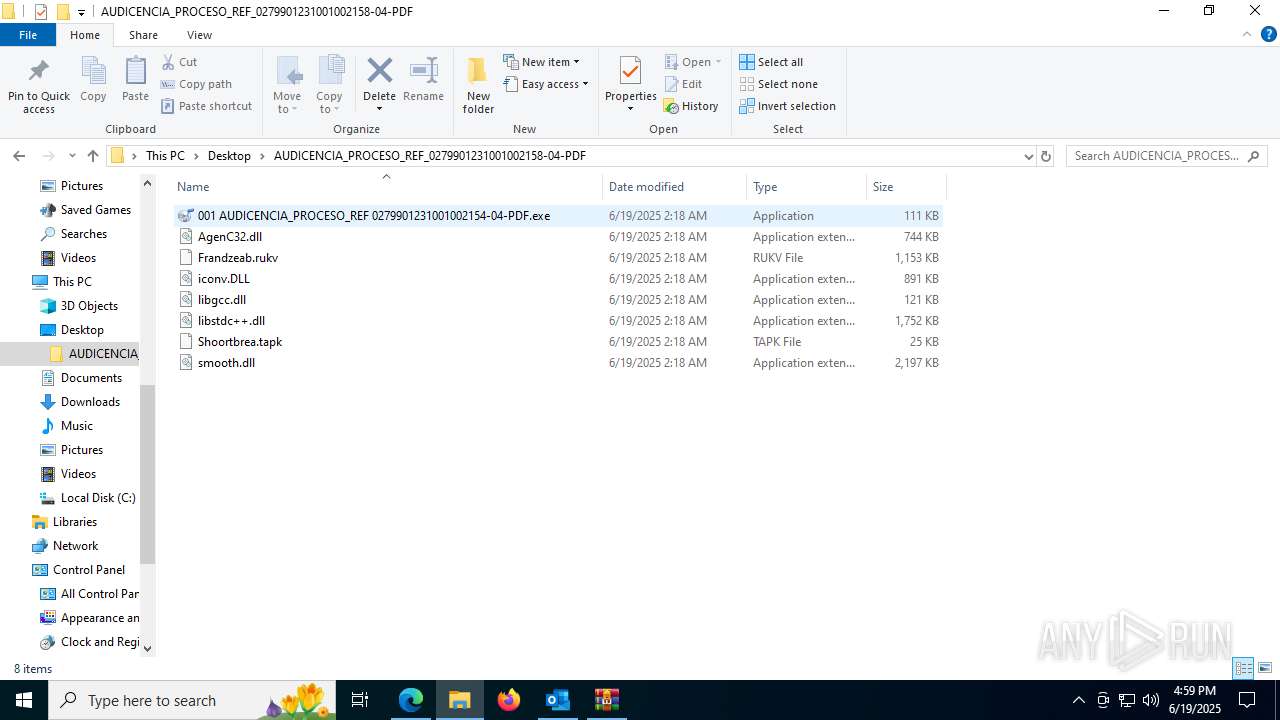
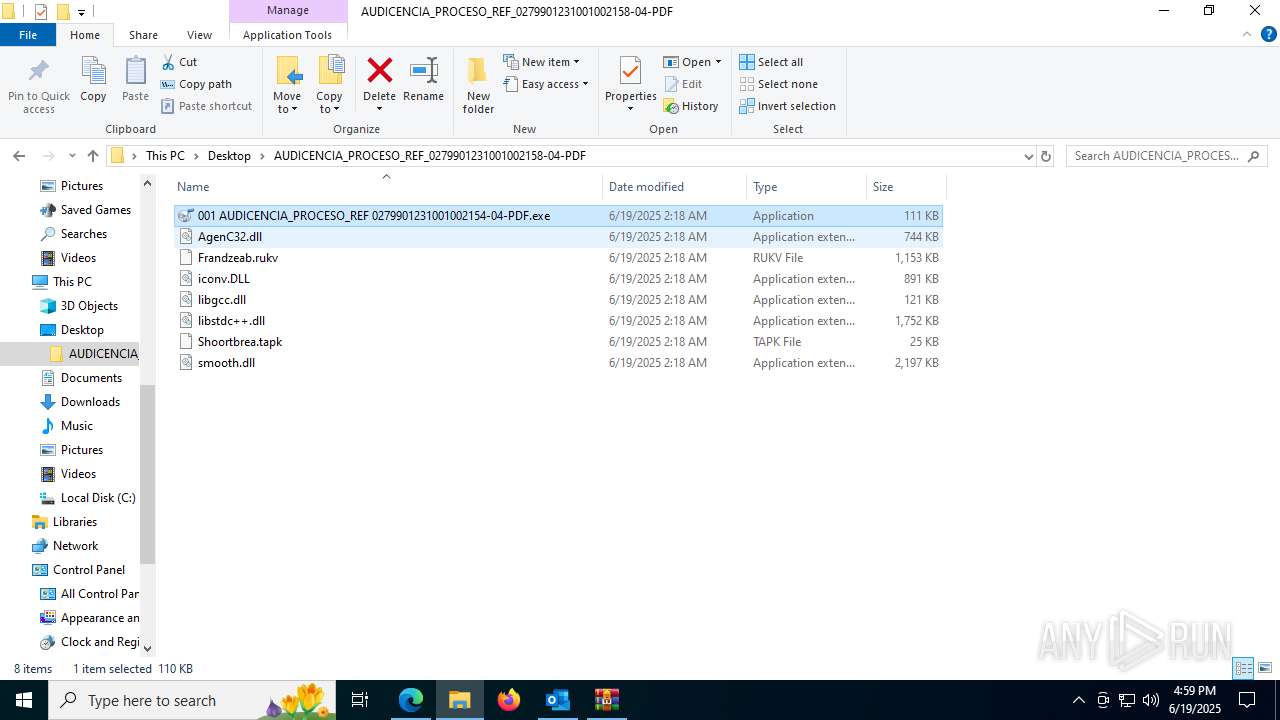
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 7608)
HIJACKLOADER has been detected (YARA)
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 7608)
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 1752)
Executing a file with an untrusted certificate
- XPFix.exe (PID: 1380)
- XPFix.exe (PID: 7400)
DCRAT mutex has been found
- OmegaFr.exe (PID: 7704)
- OmegaFr.exe (PID: 7900)
- OmegaFr.exe (PID: 8048)
- OmegaFr.exe (PID: 4944)
ASYNCRAT has been detected (SURICATA)
- OmegaFr.exe (PID: 7704)
SUSPICIOUS
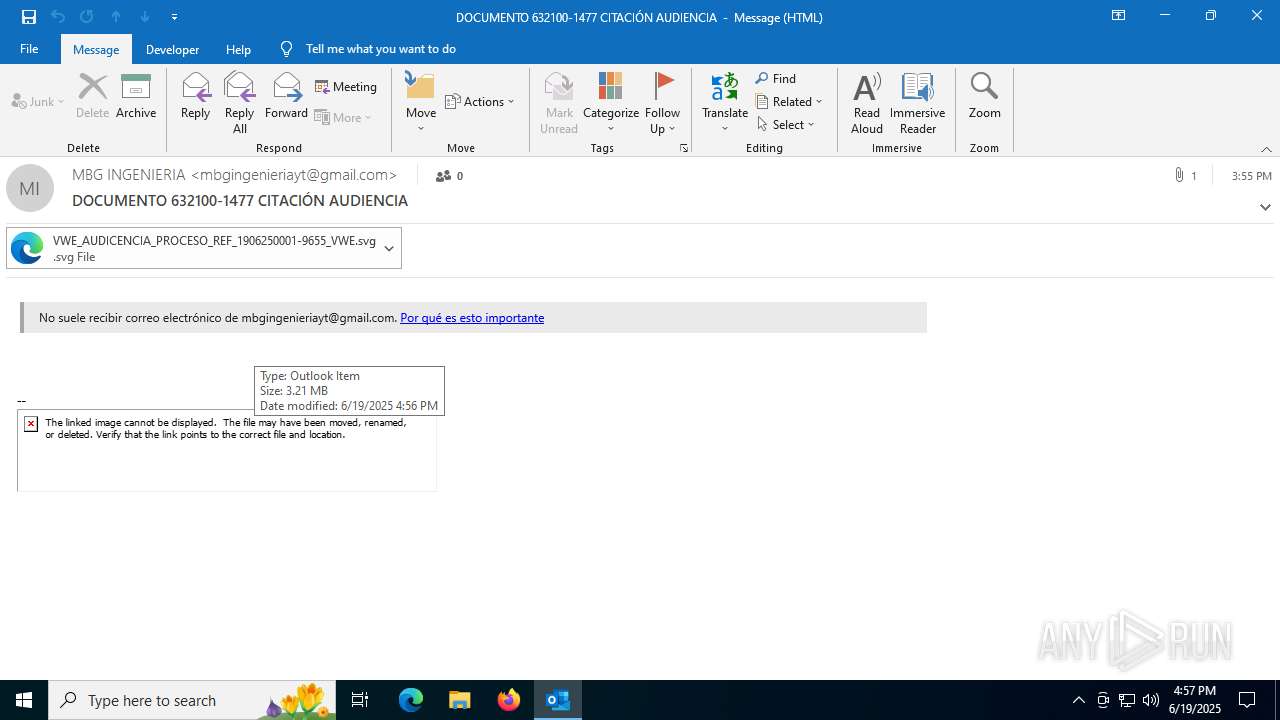
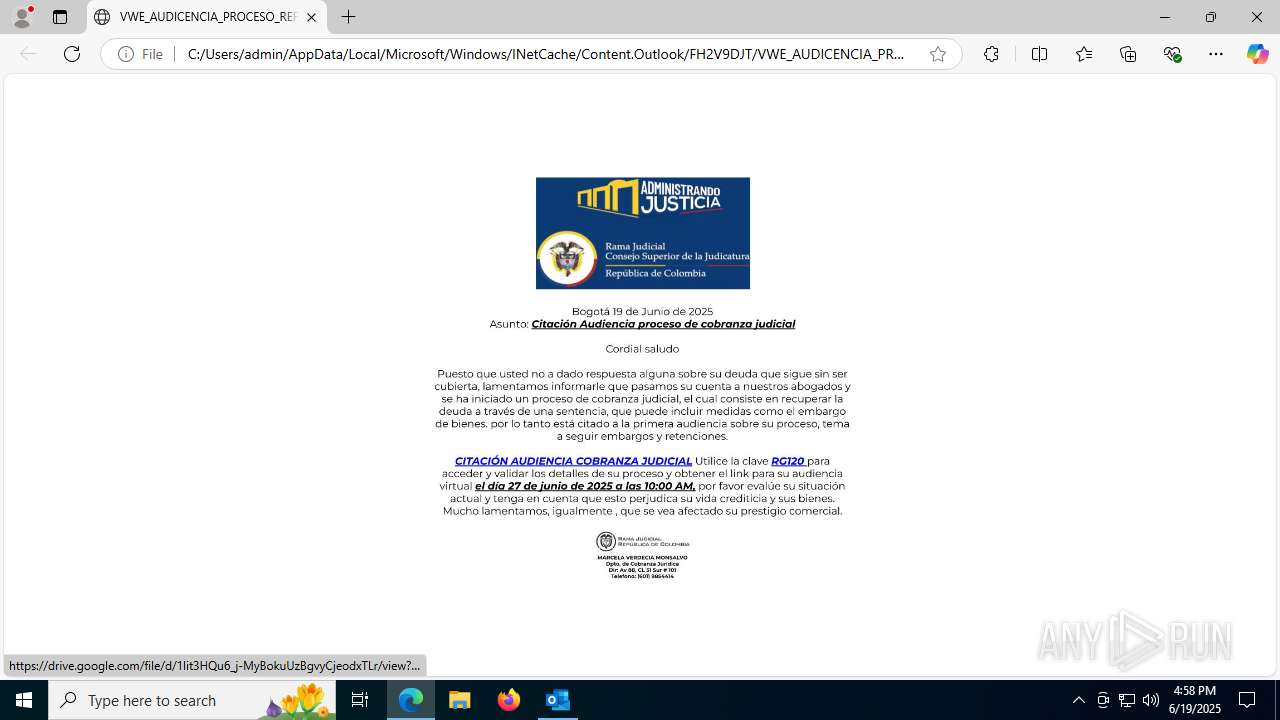
Email with suspicious attachment
- OUTLOOK.EXE (PID: 3640)
Executable content was dropped or overwritten
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 7608)
Working with threads in the GNU C Compiler (GCC) libraries related mutex has been found
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 7756)
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 7608)
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 7944)
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 8020)
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 7868)
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 1164)
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 1752)
Connects to unusual port
- OmegaFr.exe (PID: 7704)
Contacting a server suspected of hosting an CnC
- OmegaFr.exe (PID: 7704)
Possibly patching Antimalware Scan Interface function (YARA)
- OmegaFr.exe (PID: 7900)
- OmegaFr.exe (PID: 4944)
INFO
Email with attachments
- OUTLOOK.EXE (PID: 3640)
Manual execution by a user
- OUTLOOK.EXE (PID: 6304)
- msedge.exe (PID: 3388)
- OUTLOOK.EXE (PID: 6812)
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 7608)
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 7756)
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 7944)
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 8020)
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 7868)
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 1164)
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 1752)
Checks supported languages
- identity_helper.exe (PID: 1484)
- identity_helper.exe (PID: 7140)
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 7608)
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 7756)
- OmegaFr.exe (PID: 7704)
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 7944)
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 7868)
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 8020)
- OmegaFr.exe (PID: 8048)
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 1164)
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 1752)
- OmegaFr.exe (PID: 7900)
- OmegaFr.exe (PID: 1840)
- OmegaFr.exe (PID: 1812)
- OmegaFr.exe (PID: 4944)
- XPFix.exe (PID: 1380)
Reads the computer name
- identity_helper.exe (PID: 1484)
- identity_helper.exe (PID: 7140)
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 7608)
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 7756)
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 7944)
- OmegaFr.exe (PID: 7704)
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 7868)
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 8020)
- OmegaFr.exe (PID: 7900)
- OmegaFr.exe (PID: 8048)
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 1164)
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 1752)
- OmegaFr.exe (PID: 4944)
- XPFix.exe (PID: 1380)
- OmegaFr.exe (PID: 1840)
- OmegaFr.exe (PID: 1812)
- OmegaFr.exe (PID: 7352)
Application launched itself
- msedge.exe (PID: 3388)
- msedge.exe (PID: 6516)
Reads Environment values
- identity_helper.exe (PID: 1484)
- identity_helper.exe (PID: 7140)
Checks proxy server information
- slui.exe (PID: 888)
Reads the software policy settings
- slui.exe (PID: 888)
- OmegaFr.exe (PID: 7704)
Launching a file from the Downloads directory
- msedge.exe (PID: 6516)
Reads Microsoft Office registry keys
- msedge.exe (PID: 6516)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7200)
Creates files in the program directory
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 7608)
Create files in a temporary directory
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 7608)
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 7756)
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 7868)
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 7944)
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 8020)
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 1164)
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 1752)
- XPFix.exe (PID: 1380)
Creates files or folders in the user directory
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 7608)
The sample compiled with chinese language support
- 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe (PID: 7608)
Reads the machine GUID from the registry
- OmegaFr.exe (PID: 7704)
- OmegaFr.exe (PID: 7900)
- OmegaFr.exe (PID: 8048)
- OmegaFr.exe (PID: 4944)
- OmegaFr.exe (PID: 1840)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
224
Monitored processes
75
Malicious processes
9
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 472 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=133.0.6943.142 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 --annotation=prod=Edge --annotation=ver=133.0.3065.92 --initial-client-data=0x294,0x298,0x29c,0x28c,0x2a4,0x7ffc4565f208,0x7ffc4565f214,0x7ffc4565f220 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 592 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=133.0.6943.142 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 --annotation=prod=Edge --annotation=ver=133.0.3065.92 --initial-client-data=0x304,0x308,0x30c,0x2fc,0x314,0x7ffc4565f208,0x7ffc4565f214,0x7ffc4565f220 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 888 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1028 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=5860,i,3782052407954145836,10300426711917813584,262144 --variations-seed-version --mojo-platform-channel-handle=5944 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1056 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --string-annotations --gpu-preferences=UAAAAAAAAADgAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --always-read-main-dll --field-trial-handle=2388,i,3782052407954145836,10300426711917813584,262144 --variations-seed-version --mojo-platform-channel-handle=2380 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1164 | "C:\Users\admin\Desktop\AUDICENCIA_PROCESO_REF_0279901231001002158-04-PDF\001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe" | C:\Users\admin\Desktop\AUDICENCIA_PROCESO_REF_0279901231001002158-04-PDF\001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: fre:ac - free audio converter Version: 1.1.7.5891 Modules
| |||||||||||||||
| 1204 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --extension-process --renderer-sub-type=extension --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --always-read-main-dll --field-trial-handle=4296,i,13166577416897229734,3816219342838010240,262144 --variations-seed-version --mojo-platform-channel-handle=4304 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1380 | "C:\Users\admin\AppData\Roaming\Ozsecurity_dbg\XPFix.exe" "C:\Users\admin\AppData\Roaming\Ozsecurity_dbg\XPFix.exe" /u | C:\Users\admin\AppData\Roaming\Ozsecurity_dbg\XPFix.exe | — | 001 AUDICENCIA_PROCESO_REF 0279901231001002154-04-PDF.exe | |||||||||||
User: admin Company: 360.cn Integrity Level: MEDIUM Description: 360安全卫士 安全防护中心模块 Exit code: 0 Version: 1, 0, 0, 1013 Modules
| |||||||||||||||
| 1484 | "C:\Program Files (x86)\Microsoft\Edge\Application\133.0.3065.92\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=6040,i,13166577416897229734,3816219342838010240,262144 --variations-seed-version --mojo-platform-channel-handle=6104 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\133.0.3065.92\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1508 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --extension-process --renderer-sub-type=extension --pdf-upsell-enabled --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=20 --always-read-main-dll --field-trial-handle=6796,i,3782052407954145836,10300426711917813584,262144 --variations-seed-version --mojo-platform-channel-handle=6860 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
Total events
51 416
Read events
49 553
Write events
1 583
Delete events
280
Modification events
| (PID) Process: | (3640) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (3640) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\3640 |
| Operation: | write | Name: | 0 |
Value: 0B0E109D9C781C623433459A46AC862DC05B74230046C9FAD6D3B1A7F8ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511B81CD2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (3640) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (3640) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (3640) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3640) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | CantBootResolution |
Value: BootSuccess | |||
| (PID) Process: | (3640) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (3640) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | SessionId |
Value: C3D8E96E-C1AF-4750-8D52-F4E28119C131 | |||
| (PID) Process: | (3640) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | BootDiagnosticsLogFile |
Value: C:\Users\admin\AppData\Local\Temp\Outlook Logging\OUTLOOK_16_0_16026_20146-20240718T1116060318-1644.etl | |||
| (PID) Process: | (3640) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | ProfileBeingOpened |
Value: | |||
Executable files
13
Suspicious files
196
Text files
113
Unknown types
70
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3640 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 3640 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DFEF7996CC426288D1.TMP | gmc | |
MD5:D2311A4696D6945154298BC70403B570 | SHA256:9CDFBDBA230986BEB9130B07D5FD4B69355AC70AF0915BE0F1FE131B3FEC5FAC | |||
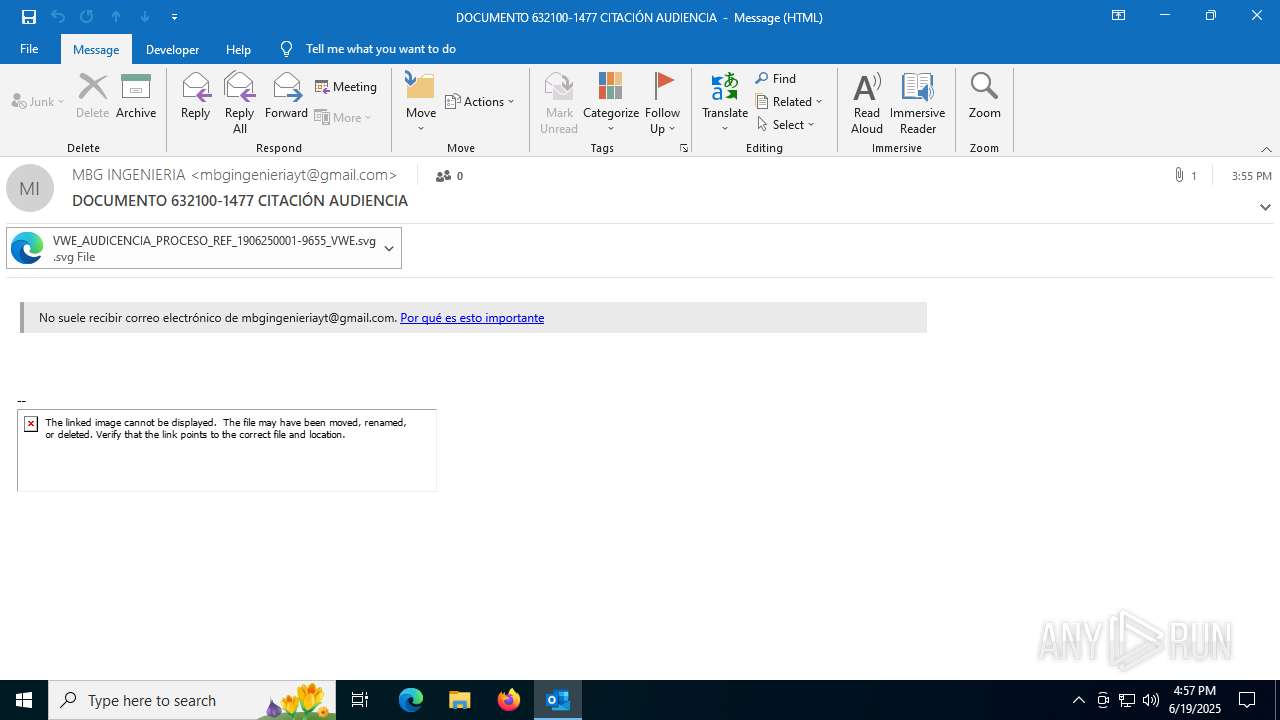
| 3640 | OUTLOOK.EXE | C:\Users\admin\Desktop\DOCUMENTO 632100-1477 CITACIÓN AUDIENCIA.msg | msg | |
MD5:2BCBE072F52A8AB4463D026C66549C51 | SHA256:506F2630863E846BD9E687B55A5845857A1101054D55EDF40DB00F92340E38D6 | |||
| 3640 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:BDD72661234D112615073BD3791069EB | SHA256:746DD1554679881463BA49F75DFCD9F23FD25A51B1BEC19DF19219C828339294 | |||
| 3640 | OUTLOOK.EXE | C:\Users\admin\Desktop\DOCUMENTO 632100-1477 CITACIÓN AUDIENCIA.msg:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 3640 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_363582827213C09529A76F35FB615187 | der | |
MD5:EA40D8ADEADC12F691EB0F588D492FC4 | SHA256:9076225C437BA40F4A4E82A2186A7A84BF9F694B02F0B44472C8981B13A2683A | |||
| 3640 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\8EB9C4DE.dat | image | |
MD5:E6174CDCF85663AF1DE3DA783129856B | SHA256:4DDB58E56D7DDBD50E60C691204F5C74FE2514632DD66AF1CDD4E2B69A92D971 | |||
| 3640 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:62D21CF0B967E15FC549FCA06865343B | SHA256:6060189C9678B0E05BAD21611AEC3352ECE86E450BAA1DAC61F62ADCA4E8F24D | |||
| 3640 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:DF1C9F6D3B2649A94CA2CE4573275738 | SHA256:9E0E84E629870756EC14CFF9268A4949D1578070E2EEAA55B189A4037F48BCB2 | |||
| 3640 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_TableViewPreviewPrefs_2_8BE1775CFD09344D8F3F97C759E54CB9.dat | xml | |
MD5:0E092DB99AEE99FDFF9B5B222C732CFD | SHA256:D1614AD99ADED9F6F5C1BE7FE7FFA5124BD04A526580DA3818EA8A954E852AA6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
22
TCP/UDP connections
106
DNS requests
114
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2288 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.24.77.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3640 | OUTLOOK.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
760 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
760 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6304 | OUTLOOK.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
1712 | msedge.exe | GET | 200 | 150.171.27.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:YeiU_sY2KQdDLz9a0Vp0lepECDFjZevwfe9qFRDVkYI&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
1868 | svchost.exe | HEAD | 200 | 208.89.74.23:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1750781231&P2=404&P3=2&P4=m9qEGNIVoz3hR2osP0TpaGL58F00%2bZdq8X8zJVfQ8tit4O1p%2fXBh9NXXQlyFnoZmL7hD0CDmLwHrgNorFo%2fLBQ%3d%3d | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2468 | RUXIMICS.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3640 | OUTLOOK.EXE | 52.123.128.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3640 | OUTLOOK.EXE | 23.50.131.87:443 | omex.cdn.office.net | Akamai International B.V. | DE | whitelisted |
3640 | OUTLOOK.EXE | 52.111.240.16:443 | messaging.lifecycle.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
2288 | svchost.exe | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2288 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
ecs.office.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.duckdns .org Domain |
2200 | svchost.exe | Misc activity | ET DYN_DNS DYNAMIC_DNS Query to *.duckdns. Domain |
7704 | OmegaFr.exe | Domain Observed Used for C2 Detected | REMOTE [ANY.RUN] AsyncRAT SSL certificate |
2200 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.duckdns .org Domain |
2200 | svchost.exe | Misc activity | ET DYN_DNS DYNAMIC_DNS Query to *.duckdns. Domain |
7704 | OmegaFr.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 5 |
7704 | OmegaFr.exe | A Network Trojan was detected | ET MALWARE Observed Malicious SSL Cert (Various RAT) |
7704 | OmegaFr.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Malicious SSL Cert (AsyncRAT) |
7704 | OmegaFr.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] AsyncRAT Successful Connection |