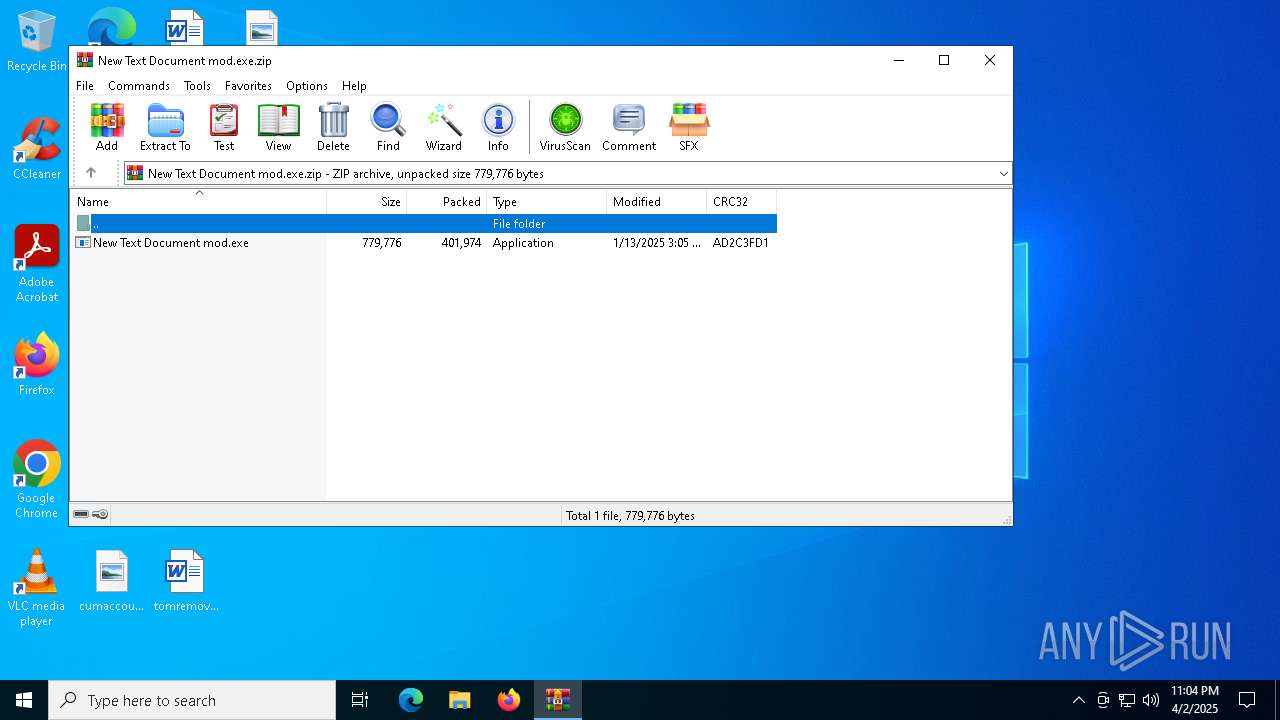
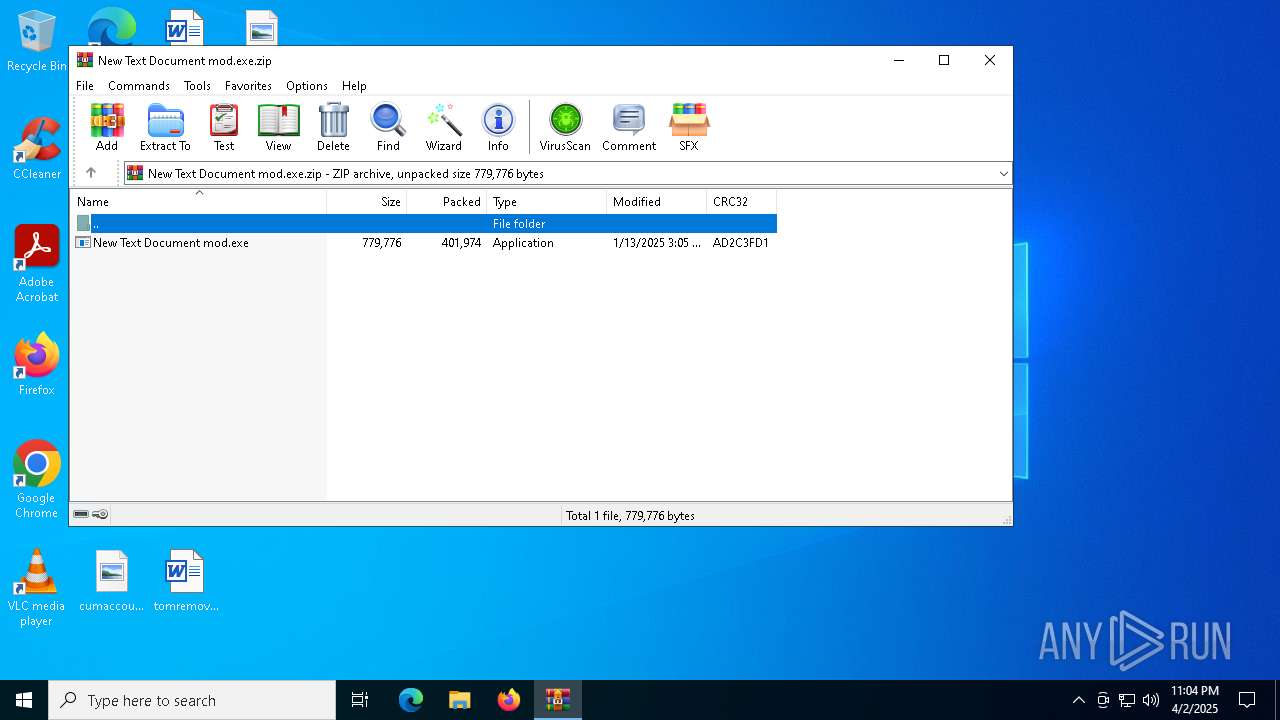
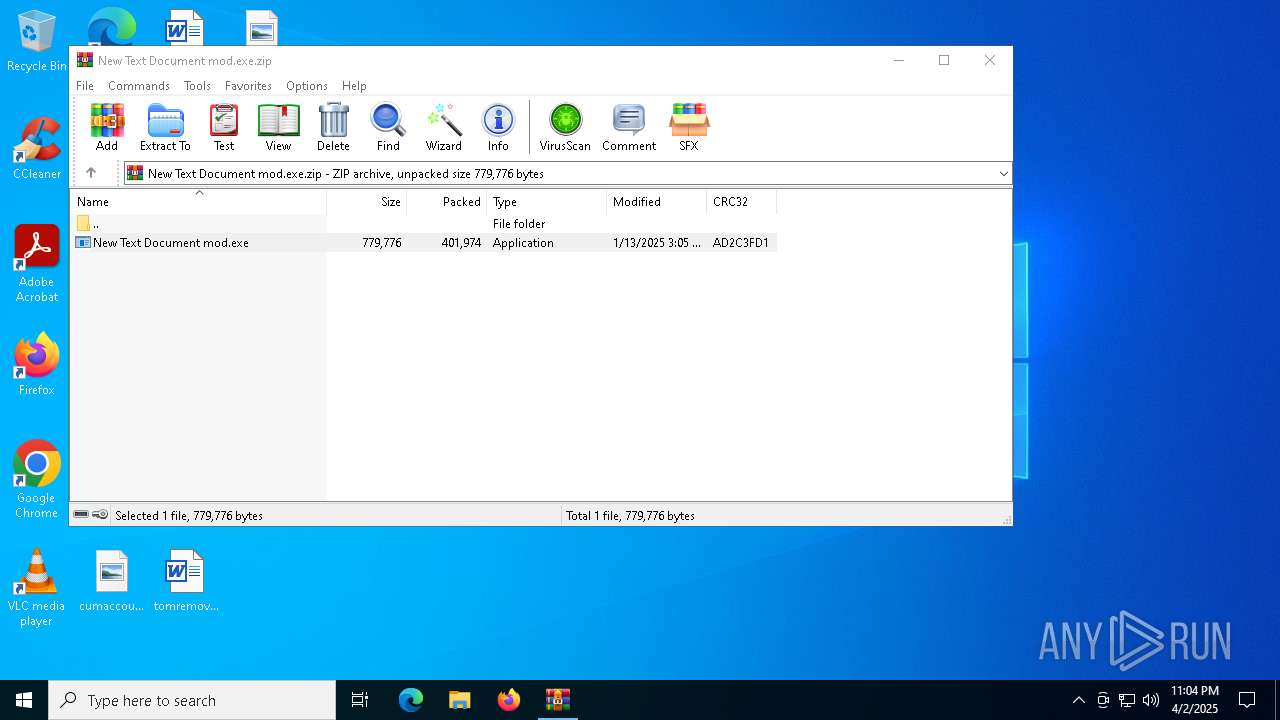
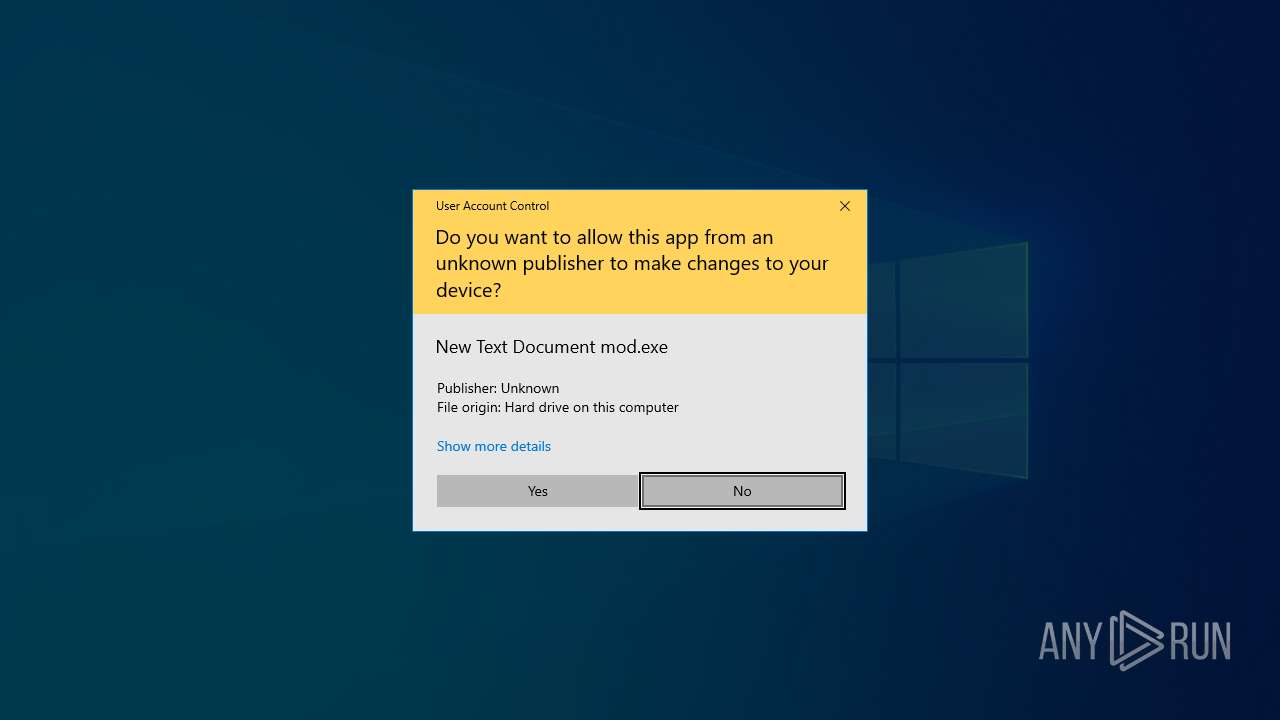
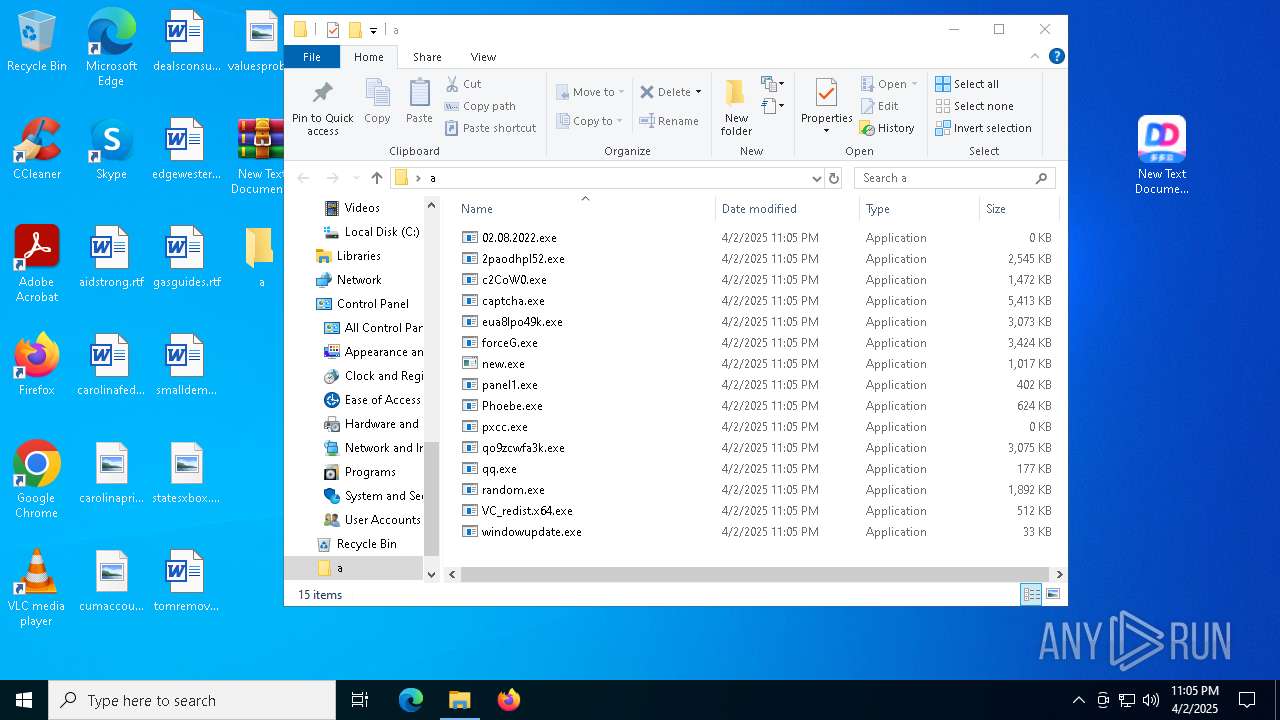
| File name: | New Text Document mod.exe.zip |
| Full analysis: | https://app.any.run/tasks/9f44fc0c-e073-484e-8956-4d1cc4637e8d |
| Verdict: | Malicious activity |
| Threats: | A backdoor is a type of cybersecurity threat that allows attackers to secretly compromise a system and conduct malicious activities, such as stealing data and modifying files. Backdoors can be difficult to detect, as they often use legitimate system applications to evade defense mechanisms. Threat actors often utilize special malware, such as PlugX, to establish backdoors on target devices. |
| Analysis date: | April 02, 2025, 23:04:15 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 209C2BED74CE311F3DE2C3040F5CBD8B |
| SHA1: | 676DBE2BBF178CA27210C8A2E37AA9652F4E17D5 |
| SHA256: | 672AD2D52AF206CC63CEBE2C801181D3B406AAE5891CC57BDAAFD5EEA3D61FE6 |
| SSDEEP: | 12288:oxT03atoNbFNepIoFulX5KzyAYqPbpW0VcFQVNLwqZCGrl6sZt0w/01:+T037NpNeCWulX5wyAYqPbpW0VvVNLxS |
MALICIOUS
XRED mutex has been found
- Synaptics.exe (PID: 5800)
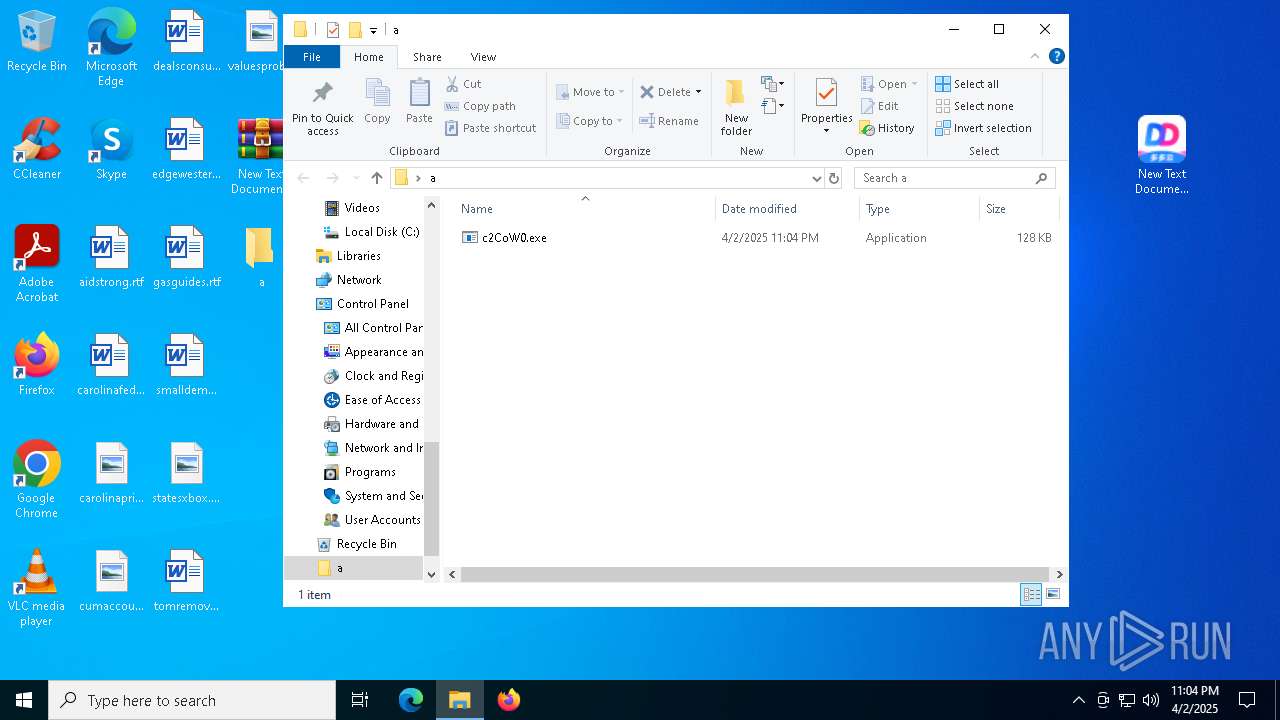
- New Text Document mod.exe (PID: 6040)
- New Text Document mod.exe (PID: 7316)
- New Text Document mod.exe (PID: 7784)
- New Text Document mod.exe (PID: 7832)
- New Text Document mod.exe (PID: 4112)
- New Text Document mod.exe (PID: 5452)
- New Text Document mod.exe (PID: 1012)
- New Text Document mod.exe (PID: 7788)
- New Text Document mod.exe (PID: 1276)
- New Text Document mod.exe (PID: 4696)
Stealers network behavior
- svchost.exe (PID: 2196)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2196)
- random.exe (PID: 4892)
Changes the autorun value in the registry
- New Text Document mod.exe (PID: 5452)
- qq.exe (PID: 2420)
Connects to the CnC server
- svchost.exe (PID: 2196)
LUMMA mutex has been found
- random.exe (PID: 4892)
- invoice.exe (PID: 8600)
Actions looks like stealing of personal data
- random.exe (PID: 4892)
- captcha.exe (PID: 7900)
- invoice.exe (PID: 8600)
Steals credentials from Web Browsers
- random.exe (PID: 4892)
- captcha.exe (PID: 7900)
- invoice.exe (PID: 8600)
SVCSTEALER mutex has been found
- qq.exe (PID: 2420)
Create files in the Startup directory
- raw_cbot.exe (PID: 8232)
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 8976)
Changes Windows Defender settings
- cmd.exe (PID: 8976)
Run PowerShell with an invisible window
- powershell.exe (PID: 9048)
XWORM has been detected (SURICATA)
- windowupdate.exe (PID: 7704)
SUSPICIOUS
Executable content was dropped or overwritten
- New Text Document mod.exe (PID: 5452)
- Synaptics.exe (PID: 5800)
- ._cache_New Text Document mod.exe (PID: 6576)
- ._cache_New Text Document mod.exe (PID: 7544)
- ._cache_New Text Document mod.exe (PID: 6828)
- ._cache_New Text Document mod.exe (PID: 5072)
- qq.exe (PID: 2420)
- VC_redist.x64.exe (PID: 6592)
- ._cache_New Text Document mod.exe (PID: 8000)
- raw_cbot.exe (PID: 8232)
- ._cache_New Text Document mod.exe (PID: 1764)
- forceG.exe (PID: 9136)
Reads security settings of Internet Explorer
- New Text Document mod.exe (PID: 5452)
- Synaptics.exe (PID: 5800)
- New Text Document mod.exe (PID: 6040)
- New Text Document mod.exe (PID: 7832)
- New Text Document mod.exe (PID: 7316)
- New Text Document mod.exe (PID: 7784)
- New Text Document mod.exe (PID: 1012)
- New Text Document mod.exe (PID: 4112)
- New Text Document mod.exe (PID: 7788)
- New Text Document mod.exe (PID: 1276)
- New Text Document mod.exe (PID: 4696)
- ._cache_New Text Document mod.exe (PID: 7712)
- ._cache_New Text Document mod.exe (PID: 6576)
- new.exe (PID: 2340)
- ._cache_New Text Document mod.exe (PID: 5072)
- ._cache_New Text Document mod.exe (PID: 8000)
- VC_redist.x64.exe (PID: 6592)
- ._cache_New Text Document mod.exe (PID: 6828)
- panel1.exe (PID: 4008)
- forceGB.exe (PID: 6208)
- VC_redist.x64.exe (PID: 6708)
- ._cache_New Text Document mod.exe (PID: 1764)
- ._cache_New Text Document mod.exe (PID: 7320)
- ._cache_New Text Document mod.exe (PID: 7544)
- dotNetFx45_Full_setup.exe (PID: 9116)
Connects to the server without a host name
- ._cache_New Text Document mod.exe (PID: 8000)
- ._cache_New Text Document mod.exe (PID: 6576)
- ._cache_New Text Document mod.exe (PID: 7544)
- ._cache_New Text Document mod.exe (PID: 7320)
- ._cache_New Text Document mod.exe (PID: 5072)
- ._cache_New Text Document mod.exe (PID: 1764)
- ._cache_New Text Document mod.exe (PID: 7712)
Potential Corporate Privacy Violation
- ._cache_New Text Document mod.exe (PID: 8000)
- ._cache_New Text Document mod.exe (PID: 6576)
- ._cache_New Text Document mod.exe (PID: 7320)
- ._cache_New Text Document mod.exe (PID: 7544)
- ._cache_New Text Document mod.exe (PID: 7712)
- ._cache_New Text Document mod.exe (PID: 6828)
- ._cache_New Text Document mod.exe (PID: 5072)
- panel1.exe (PID: 4008)
- ._cache_New Text Document mod.exe (PID: 1764)
Process requests binary or script from the Internet
- ._cache_New Text Document mod.exe (PID: 8000)
- ._cache_New Text Document mod.exe (PID: 6576)
- ._cache_New Text Document mod.exe (PID: 7544)
- ._cache_New Text Document mod.exe (PID: 7320)
- ._cache_New Text Document mod.exe (PID: 6828)
- ._cache_New Text Document mod.exe (PID: 5072)
- panel1.exe (PID: 4008)
- ._cache_New Text Document mod.exe (PID: 1764)
- ._cache_New Text Document mod.exe (PID: 7712)
Reads the date of Windows installation
- ._cache_New Text Document mod.exe (PID: 7712)
- ._cache_New Text Document mod.exe (PID: 6576)
- ._cache_New Text Document mod.exe (PID: 8000)
- ._cache_New Text Document mod.exe (PID: 5072)
- ._cache_New Text Document mod.exe (PID: 6828)
- panel1.exe (PID: 4008)
- VC_redist.x64.exe (PID: 6708)
- ._cache_New Text Document mod.exe (PID: 1764)
- dotNetFx45_Full_setup.exe (PID: 9116)
Process drops legitimate windows executable
- ._cache_New Text Document mod.exe (PID: 6576)
- qq.exe (PID: 2420)
- ._cache_New Text Document mod.exe (PID: 8000)
- ._cache_New Text Document mod.exe (PID: 5072)
- raw_cbot.exe (PID: 8232)
- forceG.exe (PID: 9136)
Reads the BIOS version
- random.exe (PID: 4892)
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2196)
- random.exe (PID: 4892)
- windowupdate.exe (PID: 7704)
Starts a Microsoft application from unusual location
- qq.exe (PID: 2420)
- raw_cbot.exe (PID: 8232)
- raw_cbot_debug.exe (PID: 3024)
- cbot.exe (PID: 8272)
- cbot_debug.exe (PID: 8424)
Connects to unusual port
- ._cache_New Text Document mod.exe (PID: 6576)
- ._cache_New Text Document mod.exe (PID: 6828)
- raw_cbot.exe (PID: 8232)
- windowupdate.exe (PID: 7704)
- oi.exe (PID: 8256)
Starts CMD.EXE for commands execution
- captcha.exe (PID: 7900)
- panel1.exe (PID: 4008)
- VC_redist.x64.exe (PID: 6708)
Detected use of alternative data streams (AltDS)
- cmd.exe (PID: 4268)
The process checks if it is being run in the virtual environment
- captcha.exe (PID: 7900)
Loads DLL from Mozilla Firefox
- captcha.exe (PID: 7900)
Searches for installed software
- random.exe (PID: 4892)
- invoice.exe (PID: 8600)
Starts POWERSHELL.EXE for commands execution
- captcha.exe (PID: 7900)
- cmd.exe (PID: 8976)
Probably obfuscated PowerShell command line is found
- captcha.exe (PID: 7900)
Executing commands from a ".bat" file
- panel1.exe (PID: 4008)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 8976)
Get information on the list of running processes
- captcha.exe (PID: 7900)
The process drops C-runtime libraries
- forceG.exe (PID: 9136)
The executable file from the user directory is run by the CMD process
- VC_redist.x64.exe (PID: 9176)
Uses TASKKILL.EXE to kill Browsers
- captcha.exe (PID: 7900)
Uses TASKKILL.EXE to kill process
- captcha.exe (PID: 7900)
Process drops python dynamic module
- forceG.exe (PID: 9136)
The process creates files with name similar to system file names
- OOBebroker.exe (PID: 3008)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7460)
The sample compiled with turkish language support
- WinRAR.exe (PID: 7460)
- New Text Document mod.exe (PID: 5452)
- Synaptics.exe (PID: 5800)
Reads the computer name
- Synaptics.exe (PID: 5800)
- New Text Document mod.exe (PID: 5452)
- New Text Document mod.exe (PID: 6040)
- ._cache_New Text Document mod.exe (PID: 7212)
- New Text Document mod.exe (PID: 7316)
- ._cache_New Text Document mod.exe (PID: 1764)
- New Text Document mod.exe (PID: 7832)
- New Text Document mod.exe (PID: 7784)
- ._cache_New Text Document mod.exe (PID: 7712)
- ._cache_New Text Document mod.exe (PID: 8000)
- New Text Document mod.exe (PID: 4112)
- ._cache_New Text Document mod.exe (PID: 6576)
- New Text Document mod.exe (PID: 1012)
- New Text Document mod.exe (PID: 7788)
- ._cache_New Text Document mod.exe (PID: 1660)
- ._cache_New Text Document mod.exe (PID: 7544)
- New Text Document mod.exe (PID: 1276)
- New Text Document mod.exe (PID: 4696)
- ._cache_New Text Document mod.exe (PID: 7320)
- ._cache_New Text Document mod.exe (PID: 6828)
- ._cache_New Text Document mod.exe (PID: 5072)
- new.exe (PID: 2340)
- windowupdate.exe (PID: 7704)
- random.exe (PID: 4892)
- captcha.exe (PID: 7900)
- VC_redist.x64.exe (PID: 6592)
- VC_redist.x64.exe (PID: 6708)
- pxcc.exe (PID: 7256)
- forceGB.exe (PID: 6208)
- panel1.exe (PID: 4008)
- raw_cbot.exe (PID: 8232)
- forceG.exe (PID: 9136)
- oi.exe (PID: 8256)
- invoice.exe (PID: 8600)
- RegSvcs.exe (PID: 8448)
- OOBebroker.exe (PID: 3008)
- dotNetFx45_Full_setup.exe (PID: 9116)
- VC_redist.x64.exe (PID: 9176)
Checks supported languages
- Synaptics.exe (PID: 5800)
- New Text Document mod.exe (PID: 5452)
- New Text Document mod.exe (PID: 6040)
- ._cache_New Text Document mod.exe (PID: 7212)
- New Text Document mod.exe (PID: 7316)
- ._cache_New Text Document mod.exe (PID: 1764)
- New Text Document mod.exe (PID: 7832)
- New Text Document mod.exe (PID: 7784)
- ._cache_New Text Document mod.exe (PID: 7712)
- New Text Document mod.exe (PID: 4112)
- ._cache_New Text Document mod.exe (PID: 8000)
- New Text Document mod.exe (PID: 1012)
- ._cache_New Text Document mod.exe (PID: 6576)
- New Text Document mod.exe (PID: 7788)
- ._cache_New Text Document mod.exe (PID: 1660)
- New Text Document mod.exe (PID: 1276)
- ._cache_New Text Document mod.exe (PID: 7320)
- ._cache_New Text Document mod.exe (PID: 7544)
- New Text Document mod.exe (PID: 4696)
- ._cache_New Text Document mod.exe (PID: 6828)
- ._cache_New Text Document mod.exe (PID: 5072)
- new.exe (PID: 2340)
- random.exe (PID: 4892)
- captcha.exe (PID: 7900)
- windowupdate.exe (PID: 7704)
- qq.exe (PID: 2420)
- panel1.exe (PID: 4008)
- VC_redist.x64.exe (PID: 6592)
- VC_redist.x64.exe (PID: 6708)
- pxcc.exe (PID: 7256)
- forceGB.exe (PID: 6208)
- raw_cbot.exe (PID: 8232)
- raw_cbot_debug.exe (PID: 3024)
- cbot.exe (PID: 8272)
- cbot_debug.exe (PID: 8424)
- invoice.exe (PID: 8600)
- forceG.exe (PID: 9136)
- oi.exe (PID: 8256)
- VC_redist.x64.exe (PID: 9176)
- dotNetFx45_Full_setup.exe (PID: 9116)
- tsjghdiaghdtyZYUSw2hsulpdgwxuo.exe (PID: 6404)
- OOBebroker.exe (PID: 3008)
- RegSvcs.exe (PID: 8448)
Manual execution by a user
- New Text Document mod.exe (PID: 5452)
- New Text Document mod.exe (PID: 6040)
- New Text Document mod.exe (PID: 7316)
- New Text Document mod.exe (PID: 7832)
- New Text Document mod.exe (PID: 7784)
- New Text Document mod.exe (PID: 4112)
- New Text Document mod.exe (PID: 1012)
- New Text Document mod.exe (PID: 7788)
- New Text Document mod.exe (PID: 1276)
- New Text Document mod.exe (PID: 4696)
Reads the machine GUID from the registry
- ._cache_New Text Document mod.exe (PID: 1660)
- ._cache_New Text Document mod.exe (PID: 7212)
- ._cache_New Text Document mod.exe (PID: 1764)
- ._cache_New Text Document mod.exe (PID: 7712)
- ._cache_New Text Document mod.exe (PID: 8000)
- ._cache_New Text Document mod.exe (PID: 6576)
- ._cache_New Text Document mod.exe (PID: 7544)
- ._cache_New Text Document mod.exe (PID: 7320)
- ._cache_New Text Document mod.exe (PID: 6828)
- ._cache_New Text Document mod.exe (PID: 5072)
- new.exe (PID: 2340)
- windowupdate.exe (PID: 7704)
- VC_redist.x64.exe (PID: 6708)
- forceGB.exe (PID: 6208)
- raw_cbot.exe (PID: 8232)
- raw_cbot_debug.exe (PID: 3024)
- cbot.exe (PID: 8272)
- cbot_debug.exe (PID: 8424)
- oi.exe (PID: 8256)
- VC_redist.x64.exe (PID: 9176)
- dotNetFx45_Full_setup.exe (PID: 9116)
Disables trace logs
- ._cache_New Text Document mod.exe (PID: 1660)
- ._cache_New Text Document mod.exe (PID: 7212)
- ._cache_New Text Document mod.exe (PID: 1764)
- ._cache_New Text Document mod.exe (PID: 7712)
- ._cache_New Text Document mod.exe (PID: 8000)
- ._cache_New Text Document mod.exe (PID: 6576)
- ._cache_New Text Document mod.exe (PID: 7544)
- ._cache_New Text Document mod.exe (PID: 7320)
- ._cache_New Text Document mod.exe (PID: 6828)
- ._cache_New Text Document mod.exe (PID: 5072)
Checks proxy server information
- ._cache_New Text Document mod.exe (PID: 1660)
- Synaptics.exe (PID: 5800)
- ._cache_New Text Document mod.exe (PID: 7212)
- ._cache_New Text Document mod.exe (PID: 1764)
- ._cache_New Text Document mod.exe (PID: 7712)
- ._cache_New Text Document mod.exe (PID: 8000)
- ._cache_New Text Document mod.exe (PID: 6576)
- ._cache_New Text Document mod.exe (PID: 7544)
- ._cache_New Text Document mod.exe (PID: 7320)
- ._cache_New Text Document mod.exe (PID: 5072)
- new.exe (PID: 2340)
- panel1.exe (PID: 4008)
- captcha.exe (PID: 7900)
- forceGB.exe (PID: 6208)
- ._cache_New Text Document mod.exe (PID: 6828)
Reads the software policy settings
- ._cache_New Text Document mod.exe (PID: 1660)
- ._cache_New Text Document mod.exe (PID: 7212)
- ._cache_New Text Document mod.exe (PID: 1764)
- ._cache_New Text Document mod.exe (PID: 7712)
- ._cache_New Text Document mod.exe (PID: 8000)
- ._cache_New Text Document mod.exe (PID: 6576)
- ._cache_New Text Document mod.exe (PID: 7544)
- ._cache_New Text Document mod.exe (PID: 7320)
- ._cache_New Text Document mod.exe (PID: 6828)
- ._cache_New Text Document mod.exe (PID: 5072)
- new.exe (PID: 2340)
- random.exe (PID: 4892)
- captcha.exe (PID: 7900)
- forceGB.exe (PID: 6208)
- powershell.exe (PID: 5984)
- invoice.exe (PID: 8600)
- slui.exe (PID: 7640)
Creates files in the program directory
- Synaptics.exe (PID: 5800)
- New Text Document mod.exe (PID: 5452)
Reads Environment values
- ._cache_New Text Document mod.exe (PID: 1660)
- ._cache_New Text Document mod.exe (PID: 7212)
- ._cache_New Text Document mod.exe (PID: 1764)
- ._cache_New Text Document mod.exe (PID: 7712)
- ._cache_New Text Document mod.exe (PID: 8000)
- ._cache_New Text Document mod.exe (PID: 6576)
- ._cache_New Text Document mod.exe (PID: 7544)
- ._cache_New Text Document mod.exe (PID: 7320)
- ._cache_New Text Document mod.exe (PID: 6828)
- ._cache_New Text Document mod.exe (PID: 5072)
Process checks computer location settings
- New Text Document mod.exe (PID: 6040)
- New Text Document mod.exe (PID: 7316)
- New Text Document mod.exe (PID: 7832)
- New Text Document mod.exe (PID: 7784)
- New Text Document mod.exe (PID: 4112)
- New Text Document mod.exe (PID: 1012)
- New Text Document mod.exe (PID: 5452)
- New Text Document mod.exe (PID: 7788)
- New Text Document mod.exe (PID: 1276)
- New Text Document mod.exe (PID: 4696)
- ._cache_New Text Document mod.exe (PID: 7712)
- ._cache_New Text Document mod.exe (PID: 6576)
- ._cache_New Text Document mod.exe (PID: 5072)
- ._cache_New Text Document mod.exe (PID: 8000)
- VC_redist.x64.exe (PID: 6592)
- ._cache_New Text Document mod.exe (PID: 6828)
- panel1.exe (PID: 4008)
- ._cache_New Text Document mod.exe (PID: 1764)
- VC_redist.x64.exe (PID: 6708)
- dotNetFx45_Full_setup.exe (PID: 9116)
Creates files or folders in the user directory
- new.exe (PID: 2340)
- qq.exe (PID: 2420)
- panel1.exe (PID: 4008)
- raw_cbot.exe (PID: 8232)
- forceGB.exe (PID: 6208)
The sample compiled with english language support
- ._cache_New Text Document mod.exe (PID: 6576)
- qq.exe (PID: 2420)
- ._cache_New Text Document mod.exe (PID: 8000)
- raw_cbot.exe (PID: 8232)
- ._cache_New Text Document mod.exe (PID: 5072)
- ._cache_New Text Document mod.exe (PID: 1764)
- forceG.exe (PID: 9136)
Reads mouse settings
- new.exe (PID: 2340)
- panel1.exe (PID: 4008)
- forceGB.exe (PID: 6208)
- tsjghdiaghdtyZYUSw2hsulpdgwxuo.exe (PID: 6404)
Create files in a temporary directory
- VC_redist.x64.exe (PID: 6592)
- panel1.exe (PID: 4008)
- captcha.exe (PID: 7900)
- forceGB.exe (PID: 6208)
- Synaptics.exe (PID: 5800)
- powershell.exe (PID: 5984)
- tsjghdiaghdtyZYUSw2hsulpdgwxuo.exe (PID: 6404)
- forceG.exe (PID: 9136)
Reads security settings of Internet Explorer
- powershell.exe (PID: 5984)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 9048)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:01:13 03:05:54 |
| ZipCRC: | 0xad2c3fd1 |
| ZipCompressedSize: | 401974 |
| ZipUncompressedSize: | 779776 |
| ZipFileName: | New Text Document mod.exe |
Total processes
264
Monitored processes
132
Malicious processes
29
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | "taskkill" /IM slimjet.exe | C:\Windows\System32\taskkill.exe | — | captcha.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 680 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 900 | "tasklist" | C:\Windows\System32\tasklist.exe | — | captcha.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1012 | "C:\Users\admin\Desktop\New Text Document mod.exe" | C:\Users\admin\Desktop\New Text Document mod.exe | explorer.exe | ||||||||||||
User: admin Company: Synaptics Integrity Level: MEDIUM Description: Synaptics Pointing Device Driver Exit code: 0 Version: 1.0.0.4 Modules
| |||||||||||||||
| 1244 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | ._cache_New Text Document mod.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1276 | "C:\Users\admin\Desktop\New Text Document mod.exe" | C:\Users\admin\Desktop\New Text Document mod.exe | explorer.exe | ||||||||||||
User: admin Company: Synaptics Integrity Level: MEDIUM Description: Synaptics Pointing Device Driver Exit code: 0 Version: 1.0.0.4 Modules
| |||||||||||||||
| 1660 | "C:\Users\admin\Desktop\._cache_New Text Document mod.exe" | C:\Users\admin\Desktop\._cache_New Text Document mod.exe | New Text Document mod.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Version: 0.0.0.0 Modules
| |||||||||||||||
| 1764 | "C:\Users\admin\Desktop\._cache_New Text Document mod.exe" | C:\Users\admin\Desktop\._cache_New Text Document mod.exe | New Text Document mod.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Version: 0.0.0.0 Modules
| |||||||||||||||
| 2040 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | ._cache_New Text Document mod.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2108 | "net" statistics workstation | C:\Windows\System32\net.exe | — | captcha.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
40 853
Read events
40 795
Write events
58
Delete events
0
Modification events
| (PID) Process: | (7460) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7460) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7460) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7460) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\New Text Document mod.exe.zip | |||
| (PID) Process: | (7460) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7460) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7460) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7460) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7460) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (7460) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
89
Suspicious files
31
Text files
13
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7460 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7460.38918\New Text Document mod.exe | executable | |
MD5:C6040234EE8EAEDBE618632818C3B1B3 | SHA256:BB459869E5EF6D6DD6F0329080D7CB12542C4B37163AE2CD782620ADCD7D55A0 | |||
| 5800 | Synaptics.exe | C:\Users\admin\Desktop\a\Phoebe.exe | executable | |
MD5:A0DECF24BFF2B4E026CAB7929974E2F2 | SHA256:— | |||
| 5452 | New Text Document mod.exe | C:\ProgramData\Synaptics\RCX247D.tmp | executable | |
MD5:80421089B46D27AD31BBA48F8946AF3F | SHA256:11F931102F640EA8406D95C2EEBEADD1462FD205BC651DAC57AC1BCAC922E8F5 | |||
| 6576 | ._cache_New Text Document mod.exe | C:\Users\admin\Desktop\a\captcha.exe | executable | |
MD5:6D6AB273AD660A8C0D43263B02B3640D | SHA256:D748B6BD2FF94D6DD26AB5BD965D05FC734E33EEBD34EFA15B66C39FF71C5AED | |||
| 6828 | ._cache_New Text Document mod.exe | C:\Users\admin\Desktop\a\2paodhpl52.exe | executable | |
MD5:9ADA3EE2E789E5C96A83DF0B49A1F425 | SHA256:DEAA2C567F3FCA480B39388FF6D860B00587FEEE6C9FD10B7DC87BA986A56BF8 | |||
| 2340 | new.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:8A9BA6508BBA9E8D7191CA9301F805A1 | SHA256:E14282E5585337A7CD0EF298187A7BF69161DDB6C5168F068643790908242B5B | |||
| 2340 | new.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:182ECA65FFFC125DE478B70C25E373B1 | SHA256:950689E7B45D05BA13D8F53743513E2036D58E67788616FEFE4FD21E5985F6B3 | |||
| 2340 | new.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:971C514F84BBA0785F80AA1C23EDFD79 | SHA256:F157ED17FCAF8837FA82F8B69973848C9B10A02636848F995698212A08F31895 | |||
| 6576 | ._cache_New Text Document mod.exe | C:\Users\admin\Desktop\a\qq.exe | executable | |
MD5:A84B1C3B52CCA1E711F6AB96B6CAB2B2 | SHA256:AAD22AB6EECB71E84BA9D6F098303174B88627C778116A39D6490C9A22541A5B | |||
| 2420 | qq.exe | C:\Users\admin\AppData\Roaming\Winserv\winserv.exe | executable | |
MD5:A84B1C3B52CCA1E711F6AB96B6CAB2B2 | SHA256:AAD22AB6EECB71E84BA9D6F098303174B88627C778116A39D6490C9A22541A5B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
26
TCP/UDP connections
90
DNS requests
36
Threats
135
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 184.24.77.37:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7344 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7344 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5800 | Synaptics.exe | GET | 200 | 69.42.215.252:80 | http://freedns.afraid.org/api/?action=getdyndns&sha=a30fa98efc092684e8d1c5cff797bcc613562978 | unknown | — | — | whitelisted |
8000 | ._cache_New Text Document mod.exe | GET | — | 77.239.125.78:80 | http://77.239.125.78/assets/captcha.exe | unknown | — | — | unknown |
6576 | ._cache_New Text Document mod.exe | GET | 200 | 176.113.115.7:80 | http://176.113.115.7/files/shailudshai_dream/random.exe | unknown | — | — | malicious |
7544 | ._cache_New Text Document mod.exe | GET | 200 | 94.154.34.249:80 | http://94.154.34.249/eua8lpo49k.exe | unknown | — | — | unknown |
7320 | ._cache_New Text Document mod.exe | GET | 200 | 94.154.34.249:80 | http://94.154.34.249/qo9zcwfa3k.exe | unknown | — | — | unknown |
7712 | ._cache_New Text Document mod.exe | GET | 200 | 94.154.34.249:80 | http://94.154.34.249/2paodhpl52.exe | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 184.24.77.37:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.172.255.217:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6544 | svchost.exe | 40.126.31.129:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
urlhaus.abuse.ch |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | A Network Trojan was detected | STEALER [ANY.RUN] Domain has been identified as part of Lumma Stealer's infrastructure (cvrsystem .fr) |
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to Abused Domain *.mooo.com |
2196 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to Commonly Abused Cloudflare Domain (trycloudflare .com) |
1764 | ._cache_New Text Document mod.exe | Misc activity | ET INFO Observed trycloudflare .com Domain in TLS SNI |
2196 | svchost.exe | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] Cloudflare Tunnel (TryCloudflare) |
1764 | ._cache_New Text Document mod.exe | Misc activity | ET HUNTING TryCloudFlare Domain in TLS SNI |
7712 | ._cache_New Text Document mod.exe | Misc activity | ET INFO Observed trycloudflare .com Domain in TLS SNI |
7712 | ._cache_New Text Document mod.exe | Misc activity | ET HUNTING TryCloudFlare Domain in TLS SNI |
8000 | ._cache_New Text Document mod.exe | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
8000 | ._cache_New Text Document mod.exe | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |