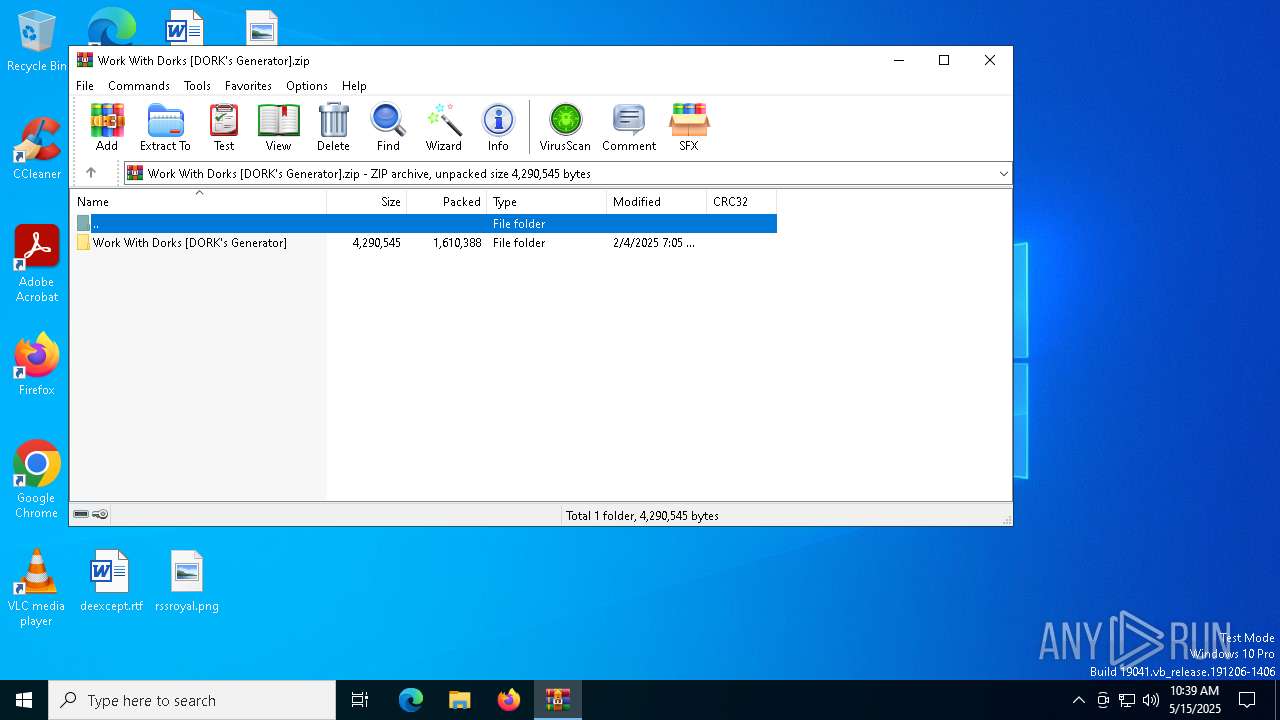
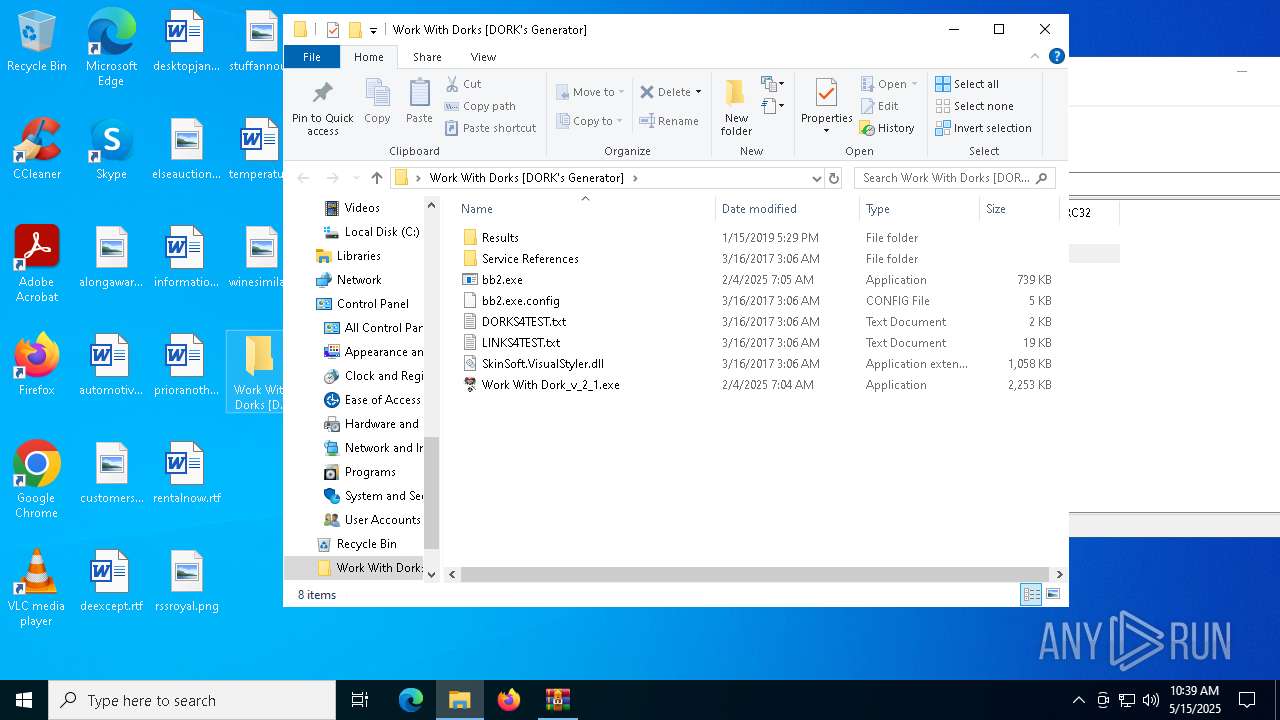
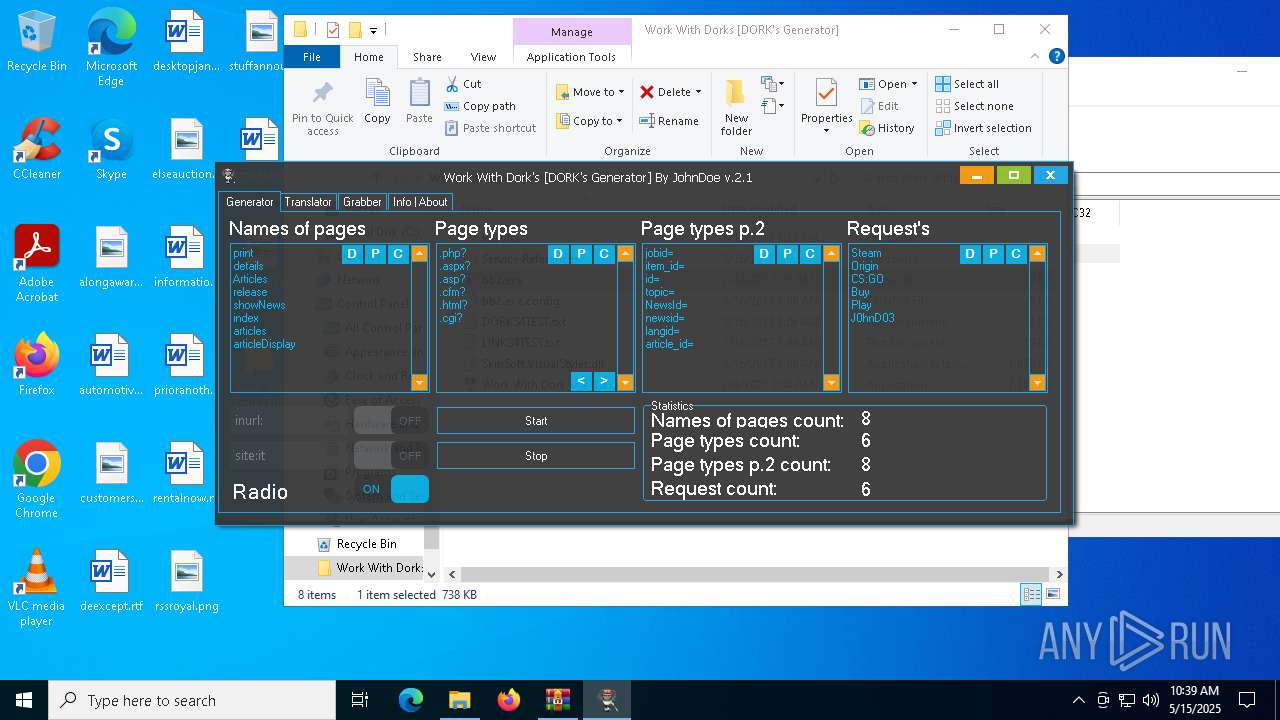
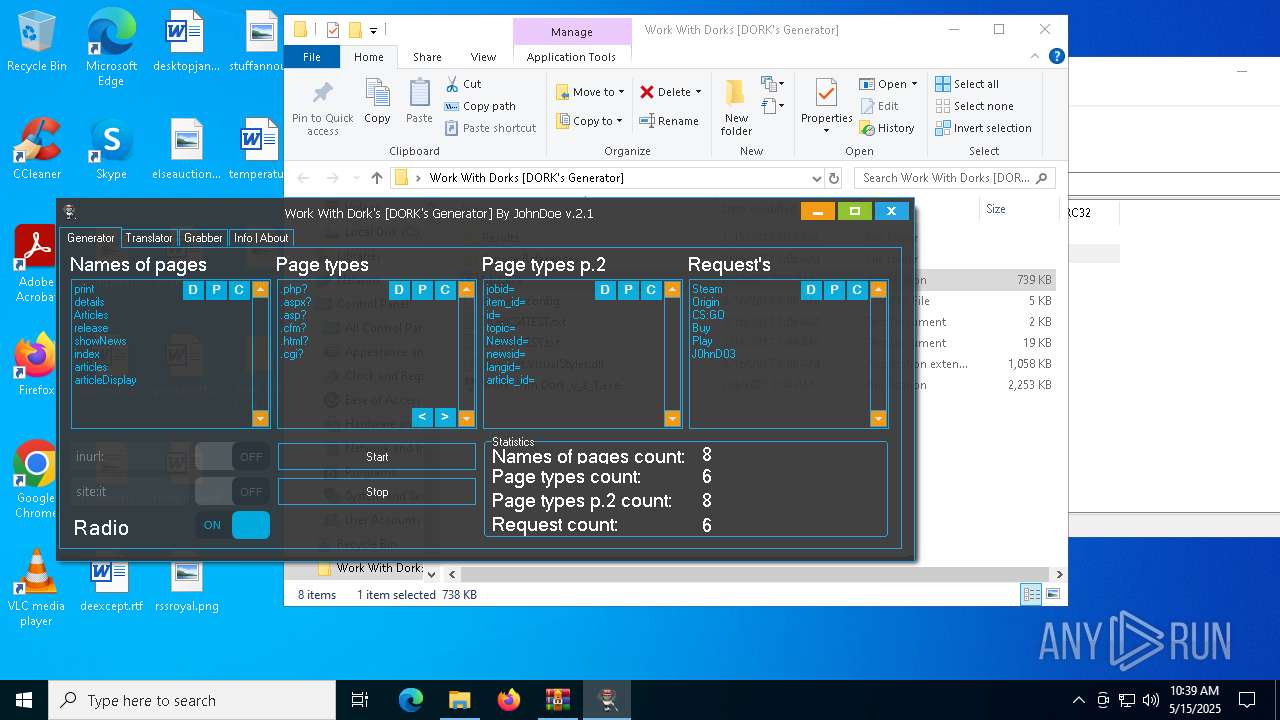
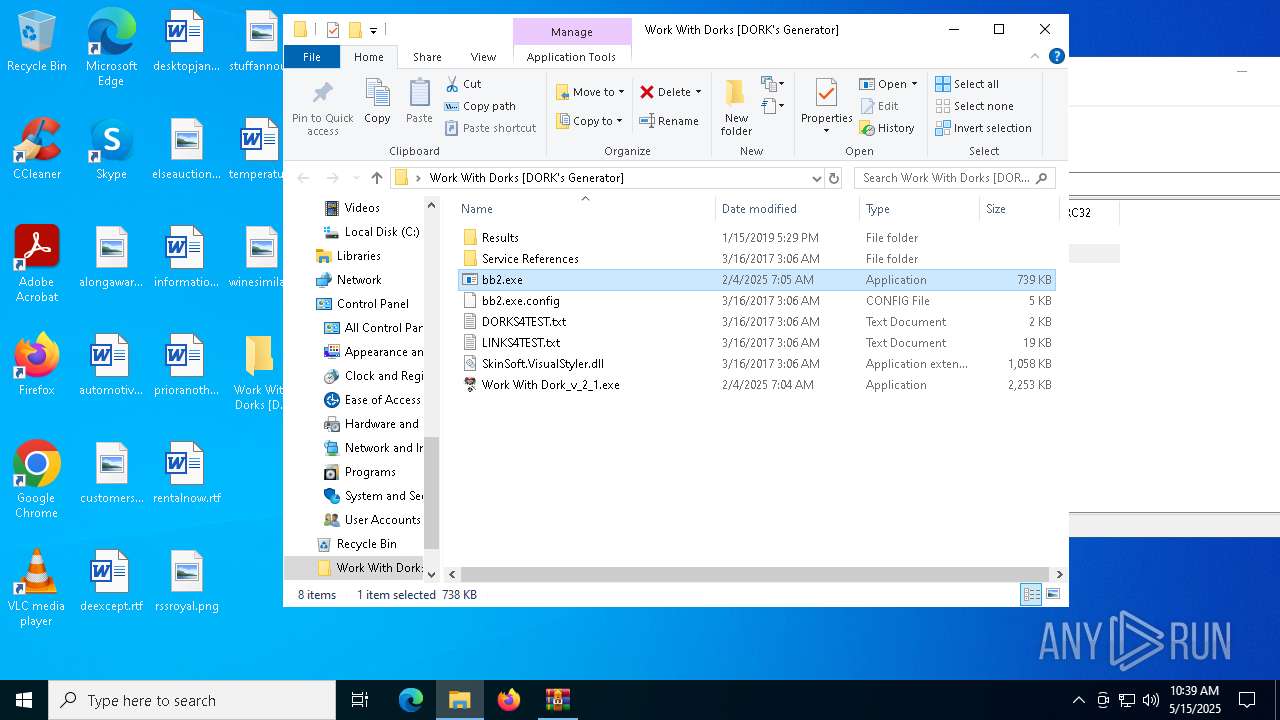
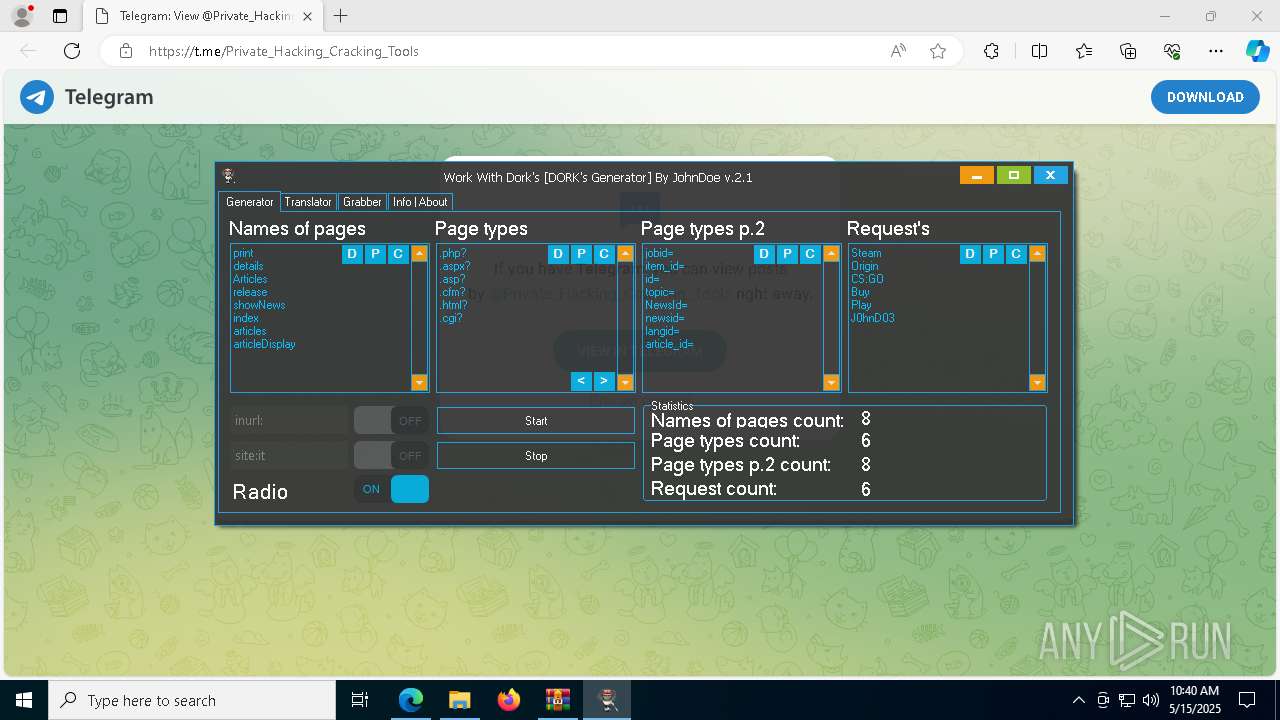
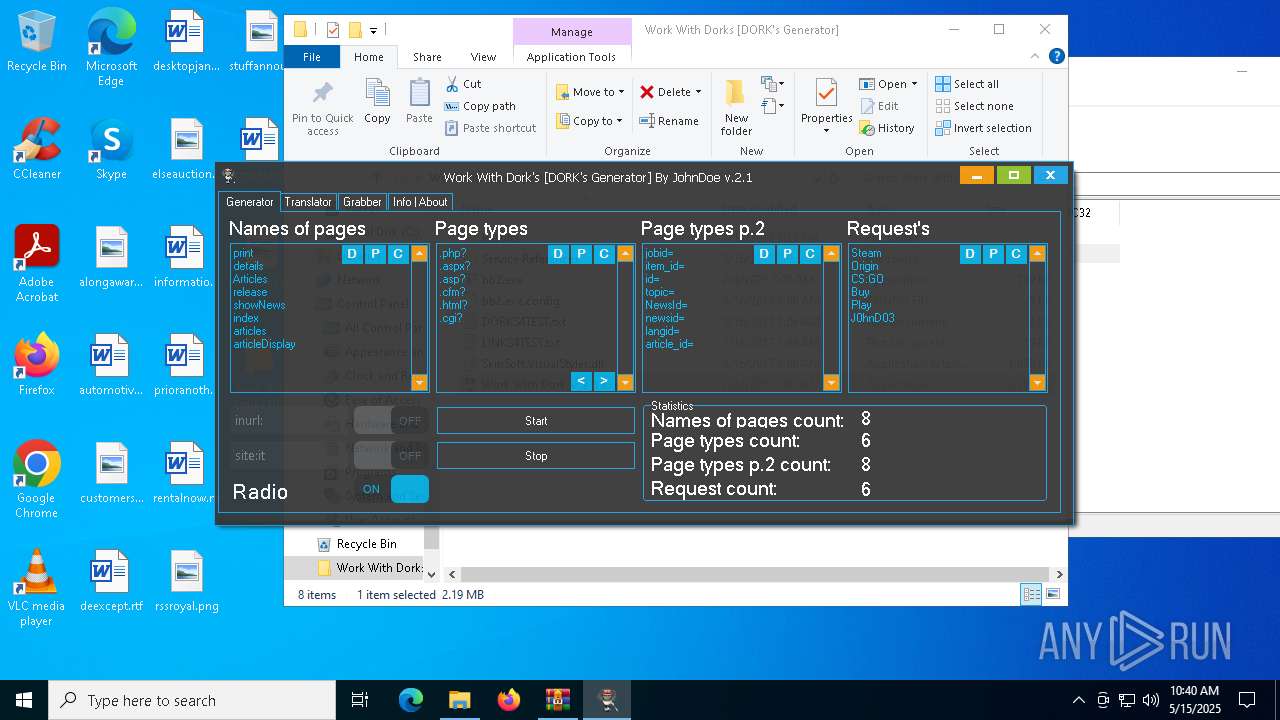
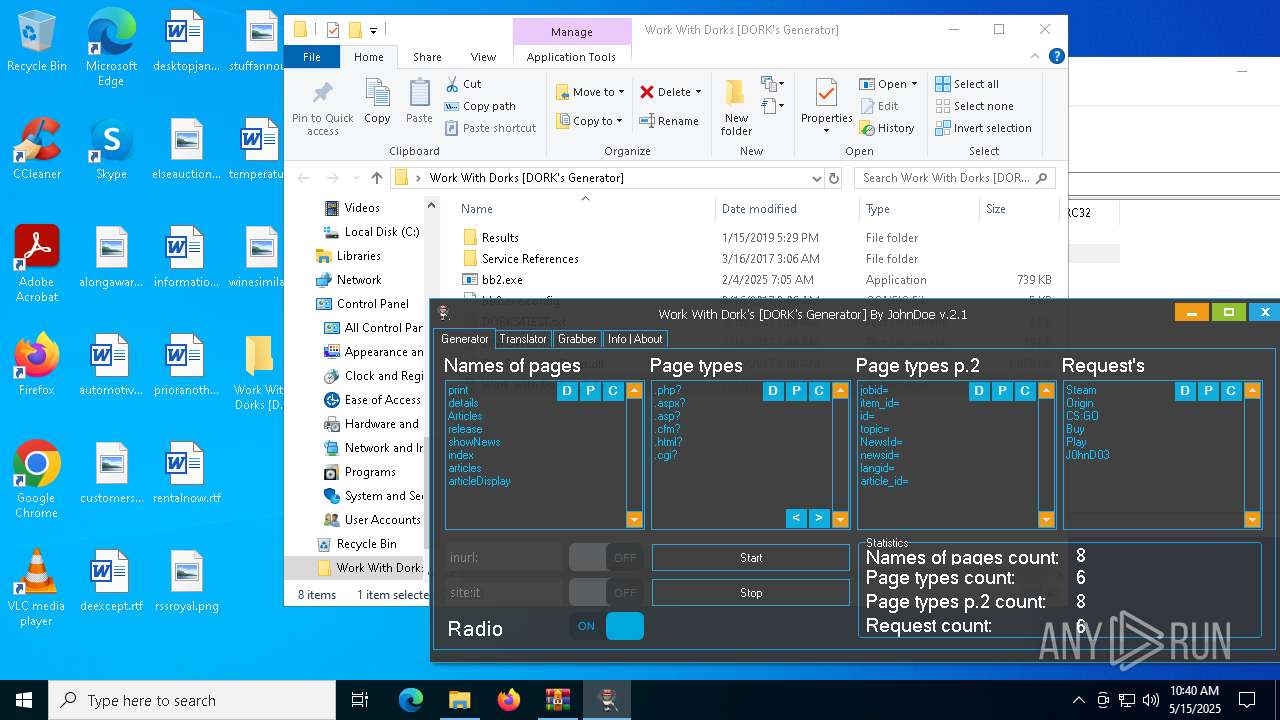
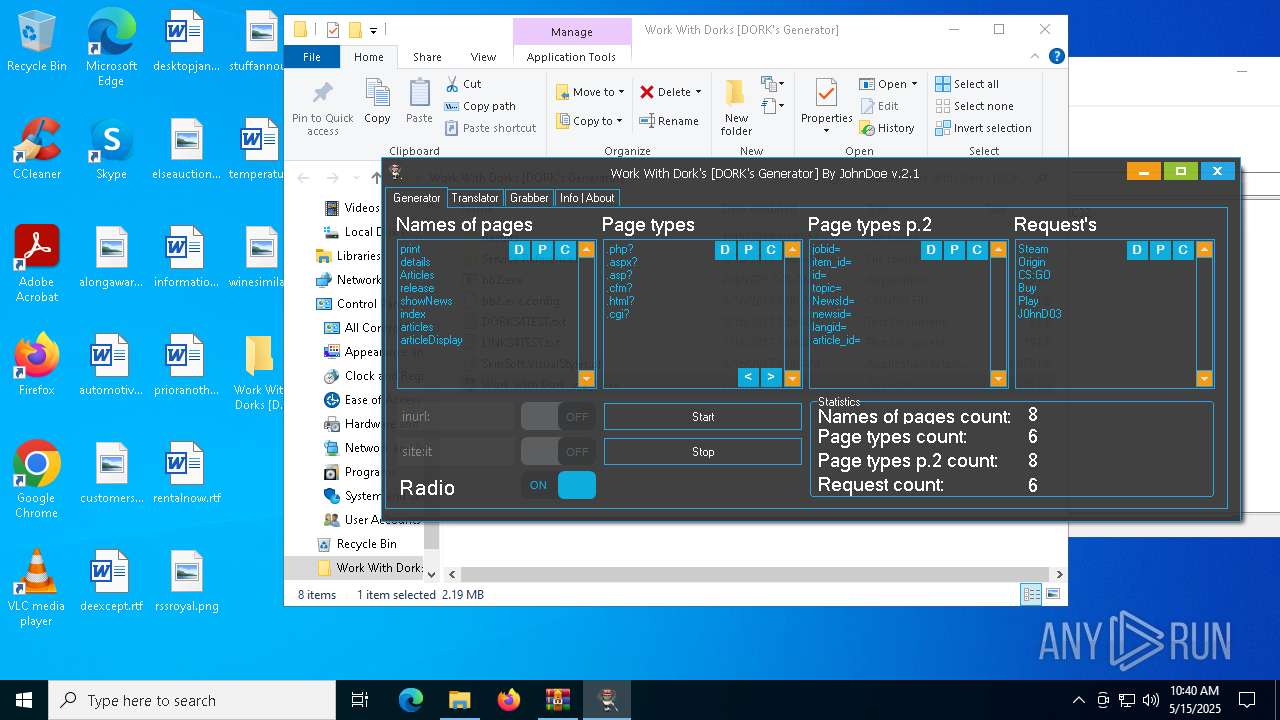
| File name: | Work With Dorks [DORK's Generator].zip |
| Full analysis: | https://app.any.run/tasks/ad8578fe-86ec-4e15-86a7-57c3937f20bc |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | May 15, 2025, 10:39:28 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 8116F53344E6BE2A0FC592DC40898A03 |
| SHA1: | 364FB9CEDC4E4EC0DB45E3E7C7886874EB3AAD48 |
| SHA256: | 66CD9E93515C5B36FD6BE40B7958F643319EDE23DB768C44DF2FF0CA6CF535E8 |
| SSDEEP: | 49152:TpgbPKNN4PGqt5Rt0epYvQwAumi/YDjOB0+FX4RLNiegxkw5xNQ5/PG9WQ9c/Sub:COXOGqt5Rt0tHmVqB0+FXyigwa529Wws |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7376)
Create files in the Startup directory
- Service.exe (PID: 8028)
RAT has been found (auto)
- GreenField.exe (PID: 7844)
Changes the autorun value in the registry
- GreenField.exe (PID: 7844)
ASYNCRAT has been detected (MUTEX)
- zxc.exe (PID: 6132)
SUSPICIOUS
Executable content was dropped or overwritten
- bb2.exe (PID: 7740)
- Work With Dork_v_2_1.exe (PID: 7948)
- Service.exe (PID: 8028)
- GreenField.exe (PID: 7844)
Reads security settings of Internet Explorer
- bb2.exe (PID: 7740)
- Work With Dork_v_2_1.exe (PID: 7948)
- Service.exe (PID: 8028)
- bb2.exe (PID: 7856)
- GreenField.exe (PID: 7844)
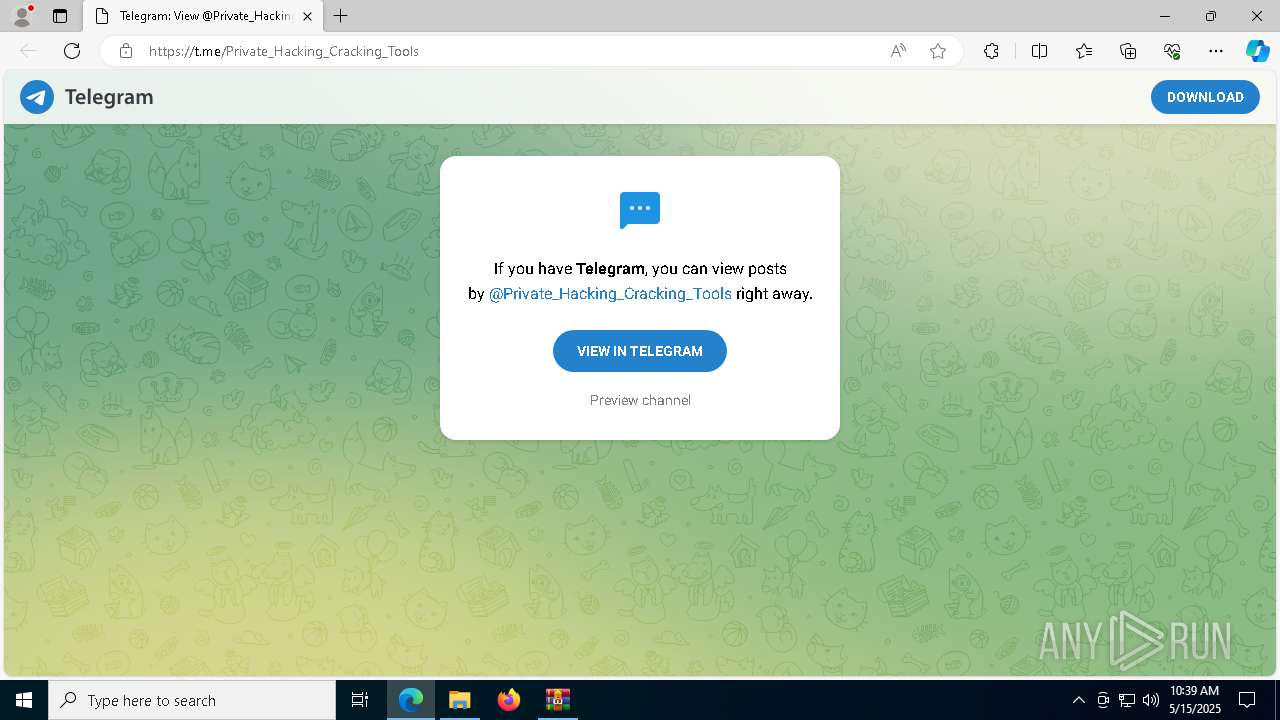
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- Work With Dork_v_2_1.exe (PID: 7948)
Application launched itself
- zxc.exe (PID: 7696)
Connects to unusual port
- zxc.exe (PID: 6132)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7376)
Reads the computer name
- bb2.exe (PID: 7740)
- Work With Dork_v_2_1.exe (PID: 7948)
- Service.exe (PID: 8028)
- zxc.exe (PID: 7696)
- GreenField.exe (PID: 7844)
- zxc.exe (PID: 6132)
- bb2.exe (PID: 7856)
- identity_helper.exe (PID: 6676)
- identity_helper.exe (PID: 4724)
- PhotoBox.exe (PID: 2108)
Creates files or folders in the user directory
- bb2.exe (PID: 7740)
- Service.exe (PID: 8028)
- Work With Dork_v_2_1.exe (PID: 7948)
- GreenField.exe (PID: 7844)
Checks supported languages
- bb2.exe (PID: 7740)
- Work With Dork_v_2_1.exe (PID: 7948)
- GreenField.exe (PID: 7844)
- Service.exe (PID: 8028)
- zxc.exe (PID: 7696)
- zxc.exe (PID: 6132)
- PhotoBox.exe (PID: 2108)
- bb2.exe (PID: 7856)
- identity_helper.exe (PID: 6676)
- identity_helper.exe (PID: 4724)
Reads the machine GUID from the registry
- bb2.exe (PID: 7740)
- Service.exe (PID: 8028)
- Work With Dork_v_2_1.exe (PID: 7948)
- bb2.exe (PID: 7856)
- GreenField.exe (PID: 7844)
- zxc.exe (PID: 6132)
- PhotoBox.exe (PID: 2108)
The sample compiled with english language support
- bb2.exe (PID: 7740)
Manual execution by a user
- bb2.exe (PID: 7740)
- Work With Dork_v_2_1.exe (PID: 7948)
Disables trace logs
- Work With Dork_v_2_1.exe (PID: 7948)
- GreenField.exe (PID: 7844)
Checks proxy server information
- Work With Dork_v_2_1.exe (PID: 7948)
- GreenField.exe (PID: 7844)
Application launched itself
- msedge.exe (PID: 8020)
- msedge.exe (PID: 7972)
Reads the software policy settings
- Work With Dork_v_2_1.exe (PID: 7948)
- GreenField.exe (PID: 7844)
Process checks computer location settings
- Service.exe (PID: 8028)
- GreenField.exe (PID: 7844)
Reads Environment values
- identity_helper.exe (PID: 6676)
- identity_helper.exe (PID: 4724)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:02:04 08:05:04 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Work With Dorks [DORK's Generator]/ |
Total processes
182
Monitored processes
57
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1052 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=3952 --field-trial-handle=2404,i,161797519364632126,4373107581604746650,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1128 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=13 --mojo-platform-channel-handle=5340 --field-trial-handle=2328,i,11346943437793476173,4318811515812207817,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1348 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6244 --field-trial-handle=2328,i,11346943437793476173,4318811515812207817,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2108 | "C:\Users\admin\AppData\Local\PhotoBox.exe" | C:\Users\admin\AppData\Local\PhotoBox.exe | — | GreenField.exe | |||||||||||
User: admin Company: NEWI Integrity Level: MEDIUM Description: WeatherSender Version: 4.0.0.11 Modules
| |||||||||||||||
| 2152 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5240 --field-trial-handle=2404,i,161797519364632126,4373107581604746650,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2504 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5440 --field-trial-handle=2404,i,161797519364632126,4373107581604746650,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2800 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5832 --field-trial-handle=2328,i,11346943437793476173,4318811515812207817,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3008 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5600 --field-trial-handle=2328,i,11346943437793476173,4318811515812207817,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3156 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --no-appcompat-clear --mojo-platform-channel-handle=5284 --field-trial-handle=2328,i,11346943437793476173,4318811515812207817,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
12 807
Read events
12 717
Write events
87
Delete events
3
Modification events
| (PID) Process: | (7376) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7376) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7376) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7376) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Work With Dorks [DORK's Generator].zip | |||
| (PID) Process: | (7376) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7376) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7376) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7376) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7740) bb2.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Media\WMSDK\General |
| Operation: | write | Name: | UniqueID |
Value: {161A1BD6-06EF-4A95-912A-126EEE45BF23} | |||
| (PID) Process: | (7740) bb2.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Media\WMSDK\General |
| Operation: | write | Name: | ComputerName |
Value: DESKTOP-JGLLJLD | |||
Executable files
20
Suspicious files
239
Text files
88
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7376 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7376.39310\Work With Dorks [DORK's Generator]\bb2.exe | executable | |
MD5:CCF8FC5C7A68B63BA0DD18A2A3FE75C6 | SHA256:EB19596F3FA1924A9AF2DC215DE9ECC37743EDE84E811859594A33B665829FA1 | |||
| 7376 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7376.39310\Work With Dorks [DORK's Generator]\Results\Dorks-15.01.19-09.29.41.txt | text | |
MD5:661CFBA62B94FE38FBA805305A026746 | SHA256:F77F3AFB506D5F7087D7BC857AA9D97A744E480B9DA6AD98CB02A8A1020CA21C | |||
| 7376 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7376.39310\Work With Dorks [DORK's Generator]\Service References\TranslatorService\configuration91.svcinfo | xml | |
MD5:3088E630D8B836EE5BACD9C867BC0AA3 | SHA256:297ECA8F517040AAD7FDA7CDBE12C3B7A0FD124CAC376C724871A2E2EA9CBAC5 | |||
| 7376 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7376.39310\Work With Dorks [DORK's Generator]\LINKS4TEST.txt | text | |
MD5:035C599BF2C8C0944C725902516B34E7 | SHA256:6EB7E96EA680BA66AA8FDAF4CC0B740F64EC188DAFB892C5F034523D420825D0 | |||
| 7376 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7376.39310\Work With Dorks [DORK's Generator]\Service References\TranslatorService\configuration.svcinfo | xml | |
MD5:D935CB832F65D86D7C2A57D1794F5953 | SHA256:42C0CA38FE255D41F4C1E5585C547D62C87FBE2E03BDDC17D16D42898819A32D | |||
| 7376 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7376.39310\Work With Dorks [DORK's Generator]\Service References\TranslatorService\soap.wsdl | xml | |
MD5:34E29BF87AB995613009041EE8EFBCCE | SHA256:E8FE1EDDB15B316C35A9D498C91081823212452226A42278B7A086CB2FC416CC | |||
| 7376 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7376.39310\Work With Dorks [DORK's Generator]\Service References\TranslatorService\Reference.svcmap | xml | |
MD5:09A372941AE01A4362EBA372D3C364B6 | SHA256:B94123D35DDB03C9D71D6BA4D58477280F457D4D139C3BC41A4CFEAA95BD9F4A | |||
| 7376 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7376.39310\Work With Dorks [DORK's Generator]\Service References\TranslatorService\SoapService.wsdl | xml | |
MD5:E5EF3231B2DEF3FB6B82B54C186E3463 | SHA256:1273852CF9B1560DE77A97403E7DEABE49454425EB7C8E0740586B3E1E71FE90 | |||
| 7376 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7376.39310\Work With Dorks [DORK's Generator]\Service References\TranslatorService\Reference.vb | text | |
MD5:3C79EE6CFDE291C2E03392CC15667D08 | SHA256:F2887D045B2FB51F8453118924B848CCB19E4A670DF526823BC923E50769BE3F | |||
| 7376 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7376.39310\Work With Dorks [DORK's Generator]\Work With Dork_v_2_1.exe | executable | |
MD5:7E42343481ED9573C81A1EF7B777E7E5 | SHA256:FC3AD430578F747DA84AA99B9B56AB1DF99049B467118CB89AA251A96917862E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
68
DNS requests
48
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.164.106:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6576 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6576 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6488 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.164.106:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7948 | Work With Dork_v_2_1.exe | 149.154.167.99:443 | t.me | Telegram Messenger Inc | GB | whitelisted |
7948 | Work With Dork_v_2_1.exe | 140.82.121.4:443 | github.com | GITHUB | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
t.me |
| whitelisted |
github.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7948 | Work With Dork_v_2_1.exe | Misc activity | ET INFO Observed Telegram Domain (t .me in TLS SNI) |
4944 | msedge.exe | Misc activity | ET INFO Observed Telegram Domain (t .me in TLS SNI) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.strangled .net Domain |