| File name: | YuZu V.5.2.exe |
| Full analysis: | https://app.any.run/tasks/d40149f2-b8e5-4ce7-b016-8ca92542f5e8 |
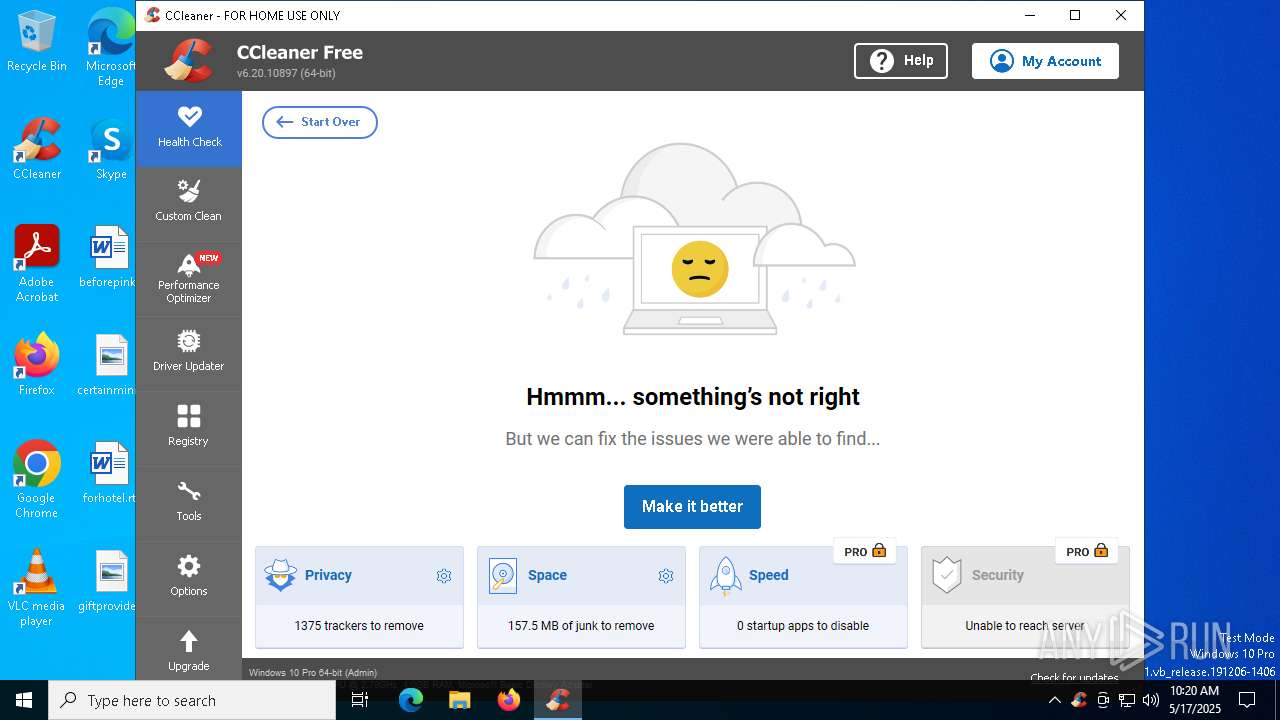
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | May 17, 2025, 10:18:55 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 9 sections |
| MD5: | 00EF3EC2A68FDBB8BE02CB6E9A391B25 |
| SHA1: | 56BDDCD1D7A7B19EB4CCEDB37AE538C47922B0D3 |
| SHA256: | 6654B30C64A8B88C844CE7A3E6958DBE979C8350D5D6EAA3C23960E6C24153FF |
| SSDEEP: | 49152:OokPSr7kuyXgBJG9LFI/SZ2j+EZKpx+auXgBJG9LFI/SZ2j+EZKpx+ac:OoJcgBJG9hOSqZKpx78gBJG9hOSqZKpO |
MALICIOUS
Connects to the CnC server
- svchost.exe (PID: 2196)
LUMMA has been detected (SURICATA)
- svchost.exe (PID: 2196)
- MSBuild.exe (PID: 2284)
LUMMA mutex has been found
- MSBuild.exe (PID: 2284)
Steals credentials from Web Browsers
- MSBuild.exe (PID: 2284)
LUMMA has been detected (YARA)
- MSBuild.exe (PID: 2284)
Changes the autorun value in the registry
- CCleaner64.exe (PID: 6240)
Actions looks like stealing of personal data
- MSBuild.exe (PID: 2284)
SUSPICIOUS
Contacting a server suspected of hosting an CnC
- svchost.exe (PID: 2196)
- MSBuild.exe (PID: 2284)
Reads security settings of Internet Explorer
- CCleaner64.exe (PID: 1012)
- CCleaner64.exe (PID: 920)
- CCleaner64.exe (PID: 6240)
Reads the date of Windows installation
- CCleaner64.exe (PID: 1012)
- CCleaner64.exe (PID: 920)
Application launched itself
- CCleaner64.exe (PID: 1012)
- CCleaner64.exe (PID: 920)
Executable content was dropped or overwritten
- CCleaner64.exe (PID: 920)
- CCleaner64.exe (PID: 6240)
Reads Internet Explorer settings
- CCleaner64.exe (PID: 920)
- CCleaner64.exe (PID: 6240)
Searches for installed software
- MSBuild.exe (PID: 2284)
- CCleaner64.exe (PID: 920)
- CCleaner64.exe (PID: 6240)
There is functionality for taking screenshot (YARA)
- MSBuild.exe (PID: 2284)
Checks for external IP
- CCleaner64.exe (PID: 920)
- svchost.exe (PID: 2196)
The process verifies whether the antivirus software is installed
- CCleaner64.exe (PID: 6240)
- CCleaner64.exe (PID: 920)
Starts application from unusual location
- CCleaner64.exe (PID: 920)
INFO
Checks supported languages
- YuZu V.5.2.exe (PID: 4244)
- MSBuild.exe (PID: 2284)
- CCleaner64.exe (PID: 1012)
- CCleaner64.exe (PID: 920)
- CCleaner64.exe (PID: 6240)
Reads the software policy settings
- MSBuild.exe (PID: 2284)
- slui.exe (PID: 6964)
- CCleaner64.exe (PID: 920)
- CCleaner64.exe (PID: 6240)
Reads the computer name
- MSBuild.exe (PID: 2284)
- CCleaner64.exe (PID: 1012)
- CCleaner64.exe (PID: 920)
- CCleaner64.exe (PID: 6240)
Reads Environment values
- CCleaner64.exe (PID: 1012)
- CCleaner64.exe (PID: 920)
- CCleaner64.exe (PID: 6240)
Process checks computer location settings
- CCleaner64.exe (PID: 1012)
- CCleaner64.exe (PID: 920)
The sample compiled with english language support
- CCleaner64.exe (PID: 920)
- CCleaner64.exe (PID: 6240)
Reads CPU info
- CCleaner64.exe (PID: 920)
- CCleaner64.exe (PID: 6240)
Reads product name
- CCleaner64.exe (PID: 920)
- CCleaner64.exe (PID: 6240)
Manual execution by a user
- CCleaner64.exe (PID: 1012)
Checks proxy server information
- CCleaner64.exe (PID: 920)
Reads the machine GUID from the registry
- CCleaner64.exe (PID: 6240)
- CCleaner64.exe (PID: 920)
Creates files in the program directory
- CCleaner64.exe (PID: 920)
- CCleaner64.exe (PID: 6240)
Creates files or folders in the user directory
- CCleaner64.exe (PID: 920)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Lumma
(PID) Process(2284) MSBuild.exe
C2 (9)onehunqpom.life/zpxd
narrathfpt.top/tekq
featurlyin.top/pdal
overcovtcg.top/juhd
laminaflbx.shop/twoq
cornerdurv.top/adwq
posseswsnc.top/akds
jackthyfuc.run/xpas
blackswmxc.top/bgry
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:05:16 14:51:36+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14 |
| CodeSize: | 266240 |
| InitializedDataSize: | 69120 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2a3a0 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
142
Monitored processes
11
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 920 | "C:\Program Files\CCleaner\CCleaner64.exe" /uac | C:\Program Files\CCleaner\CCleaner64.exe | CCleaner64.exe | ||||||||||||
User: admin Company: Piriform Software Ltd Integrity Level: HIGH Description: CCleaner Exit code: 0 Version: 6.20.0.10897 Modules
| |||||||||||||||
| 1012 | "C:\Program Files\CCleaner\CCleaner64.exe" | C:\Program Files\CCleaner\CCleaner64.exe | — | explorer.exe | |||||||||||
User: admin Company: Piriform Software Ltd Integrity Level: MEDIUM Description: CCleaner Exit code: 0 Version: 6.20.0.10897 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2284 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | YuZu V.5.2.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Version: 4.8.9037.0 built by: NET481REL1 Modules
Lumma(PID) Process(2284) MSBuild.exe C2 (9)onehunqpom.life/zpxd narrathfpt.top/tekq featurlyin.top/pdal overcovtcg.top/juhd laminaflbx.shop/twoq cornerdurv.top/adwq posseswsnc.top/akds jackthyfuc.run/xpas blackswmxc.top/bgry | |||||||||||||||
| 2384 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | YuZu V.5.2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4244 | "C:\Users\admin\AppData\Local\Temp\YuZu V.5.2.exe" | C:\Users\admin\AppData\Local\Temp\YuZu V.5.2.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4560 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe | — | YuZu V.5.2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MSBuild.exe Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 4944 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5436 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6240 | "C:\Program Files\CCleaner\CCleaner64.exe" /monitor | C:\Program Files\CCleaner\CCleaner64.exe | CCleaner64.exe | ||||||||||||
User: admin Company: Piriform Software Ltd Integrity Level: HIGH Description: CCleaner Version: 6.20.0.10897 Modules
| |||||||||||||||
Total events
23 676
Read events
23 502
Write events
115
Delete events
59
Modification events
| (PID) Process: | (920) CCleaner64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Piriform\CCleaner |
| Operation: | write | Name: | UpdateBackground |
Value: 1 | |||
| (PID) Process: | (920) CCleaner64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Piriform\CCleaner |
| Operation: | write | Name: | DAST |
Value: 05/17/2025 10:20:10 | |||
| (PID) Process: | (920) CCleaner64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Piriform\CCleaner |
| Operation: | write | Name: | T8062 |
Value: 0 | |||
| (PID) Process: | (920) CCleaner64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Piriform\CCleaner |
| Operation: | delete value | Name: | GUID |
Value: | |||
| (PID) Process: | (920) CCleaner64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Piriform\CCleaner |
| Operation: | delete value | Name: | GD |
Value: | |||
| (PID) Process: | (920) CCleaner64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Piriform\CCleaner |
| Operation: | delete value | Name: | SetupGD |
Value: | |||
| (PID) Process: | (920) CCleaner64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Piriform\CCleaner |
| Operation: | write | Name: | NumOfOutdatedDrivers |
Value: 0 | |||
| (PID) Process: | (920) CCleaner64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRestore |
| Operation: | write | Name: | SystemRestorePointCreationFrequency |
Value: 0 | |||
| (PID) Process: | (920) CCleaner64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | CCleaner PostInstall |
Value: | |||
| (PID) Process: | (920) CCleaner64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Piriform\CCleaner |
| Operation: | write | Name: | FTU |
Value: 06/02/2024|3|1 | |||
Executable files
5
Suspicious files
59
Text files
21
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 920 | CCleaner64.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\ccc0fa1b9f86f7b3.customDestinations-ms~RF11cec6.TMP | binary | |
MD5:715D03F2C851242AE02F082C92170337 | SHA256:52F9047E9A072554A68045FD0215B8484C2D6D758FEE82543FBAA7C7F7D163D9 | |||
| 920 | CCleaner64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:36716215253D1E1D66BA86CE40EE9B44 | SHA256:D5BADAF4AC649A0AA5CF4D80E7E47ADF6EDE63C90D293C16D8C4950277F29D8A | |||
| 920 | CCleaner64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\05DDC6AA91765AACACDB0A5F96DF8199 | binary | |
MD5:8B6DE1E7AC8F3BBDCA003D274200C5FE | SHA256:7C9E8681F322C69934775500FF6C9B58A10D0DC1252EBEFB2CC1BD913E4DFA4B | |||
| 920 | CCleaner64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E573CDF4C6D731D56A665145182FD759_AFB3BE9383420FBAFF24AD413EEA555E | binary | |
MD5:CE9916B86D8E05B55E88A5B200326E67 | SHA256:AF3E418A7EF648D41468CABA2DD6A7F829A977E6308859A92D5513BCF8AD1F9E | |||
| 920 | CCleaner64.exe | — | ||
MD5:— | SHA256:— | |||
| 920 | CCleaner64.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\info[1].json | binary | |
MD5:83FF6B6B6D002B6F6266AA38575EC861 | SHA256:C3A48805B01507EA2C407AC1310C013348FD950782E37FF41D8ABCD0F811C067 | |||
| 6240 | CCleaner64.exe | C:\Program Files\CCleaner\gcapi_dll.dll | executable | |
MD5:F17F96322F8741FE86699963A1812897 | SHA256:8B6CE3A640E2D6F36B0001BE2A1ABB765AE51E62C314A15911E75138CBB544BB | |||
| 920 | CCleaner64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:2E6DA905564CB0718DB304685804079D | SHA256:25D16205BF0F8F7EFD0B7E2E426E9323E9F8FAD757F006C11D9CF7825FA21ED7 | |||
| 920 | CCleaner64.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\CEQ2DXCZ.txt | text | |
MD5:A8D158D95D0E6853CEDAB255DD9D74F4 | SHA256:E361847BBA5BA5957BB258FB85C981AC10973310218490AF73514E42EBEE42C9 | |||
| 920 | CCleaner64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\F44F0D8080C8C3429C5AB2379F33E907_36516A32D5B34401A68F7B7E010B64C8 | binary | |
MD5:80B48A84A6C7F7755F88339EEE1DEDDA | SHA256:F660C9579D2DBC85D103D84F076AB4E29E15F7D15BF315CA5546E205C3BB54FF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
53
DNS requests
46
Threats
14
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.36:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3332 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
920 | CCleaner64.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | — | — | whitelisted |
3332 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
920 | CCleaner64.exe | GET | 200 | 23.50.131.88:80 | http://ncc.avast.com/ncc.txt | unknown | — | — | whitelisted |
920 | CCleaner64.exe | GET | 200 | 142.250.184.227:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | whitelisted |
920 | CCleaner64.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTk45WiKdPUwcMf8JgMC07ACYqr2AQUt2ui6qiqhIx56rTaD5iyxZV2ufQCEAXfj0A2M0oL7zuU%2F%2F2jetU%3D | unknown | — | — | whitelisted |
920 | CCleaner64.exe | GET | 200 | 142.250.185.99:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.36:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2284 | MSBuild.exe | 104.21.32.1:443 | cornerdurv.top | CLOUDFLARENET | — | unknown |
6544 | svchost.exe | 20.190.160.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2284 | MSBuild.exe | 104.21.83.105:443 | narrathfpt.top | CLOUDFLARENET | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
cornerdurv.top |
| unknown |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
narrathfpt.top |
| unknown |
jackthyfuc.run |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2196 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (cornerdurv .top) |
2284 | MSBuild.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (cornerdurv .top) in TLS SNI |
2284 | MSBuild.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (laminaflbx .shop) in TLS SNI |
2196 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (overcovtcg .top) |
2196 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (laminaflbx .shop) |
2284 | MSBuild.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (overcovtcg .top) in TLS SNI |
2284 | MSBuild.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (overcovtcg .top) in TLS SNI |
2284 | MSBuild.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (overcovtcg .top) in TLS SNI |
2284 | MSBuild.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (overcovtcg .top) in TLS SNI |