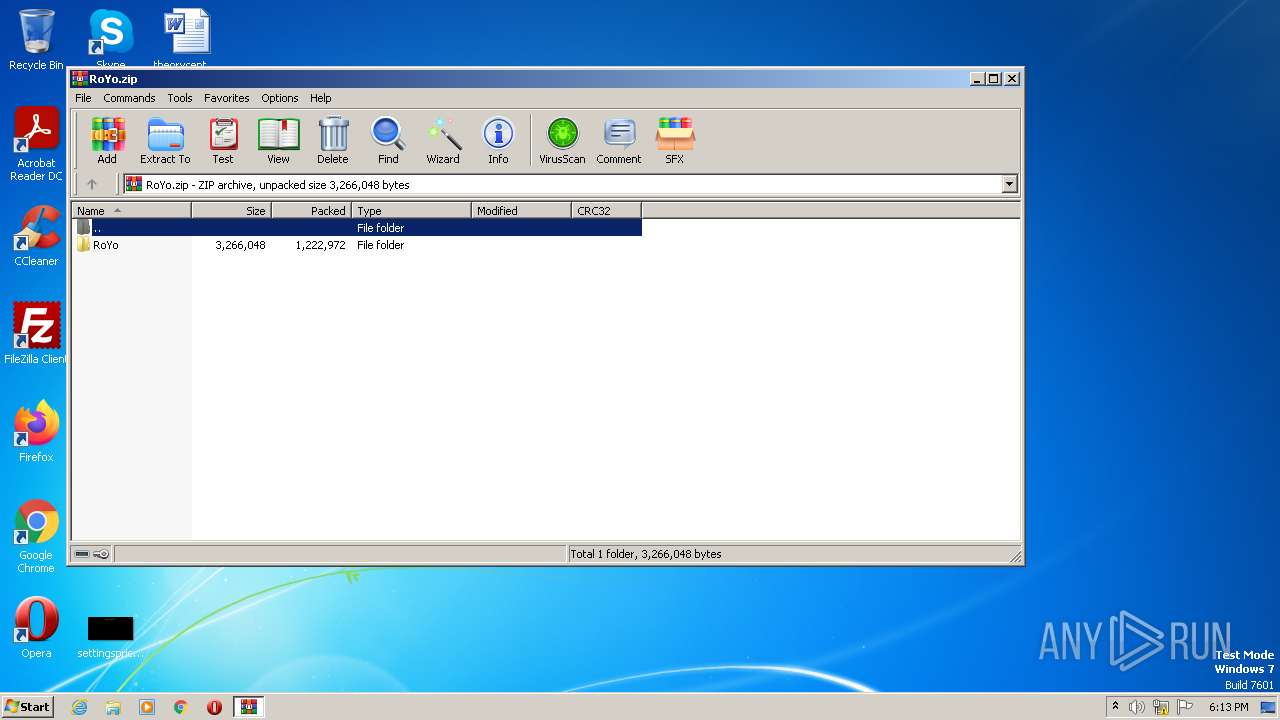
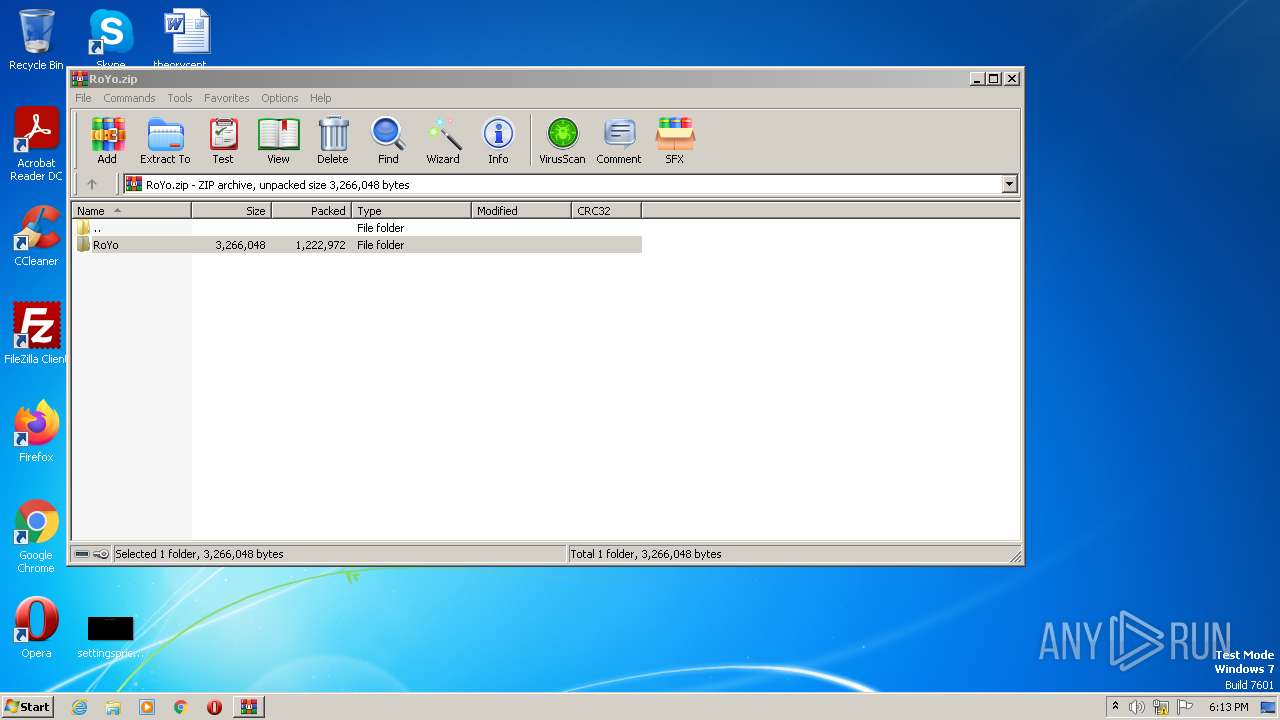
| File name: | RoYo.zip |
| Full analysis: | https://app.any.run/tasks/a70351b0-7546-4a02-a728-15f091224b4e |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | April 01, 2023, 17:13:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | EA8986395F4E341DBE4F4240615992CA |
| SHA1: | E6163093D3C0C14DC2682A27CA4BCAC451EDBFF4 |
| SHA256: | 65D78BD6EBA9E03C543AEBB7FD64BE32C7D99C30F4BBE9DE2569693E41E50E0E |
| SSDEEP: | 24576:SKt8Bzi7pb2kQFNL2kIeGQnw0xlh84kLoEMgxaMHYAnRH:Rqi7pFalh8ZoFgxvYWRH |
MALICIOUS
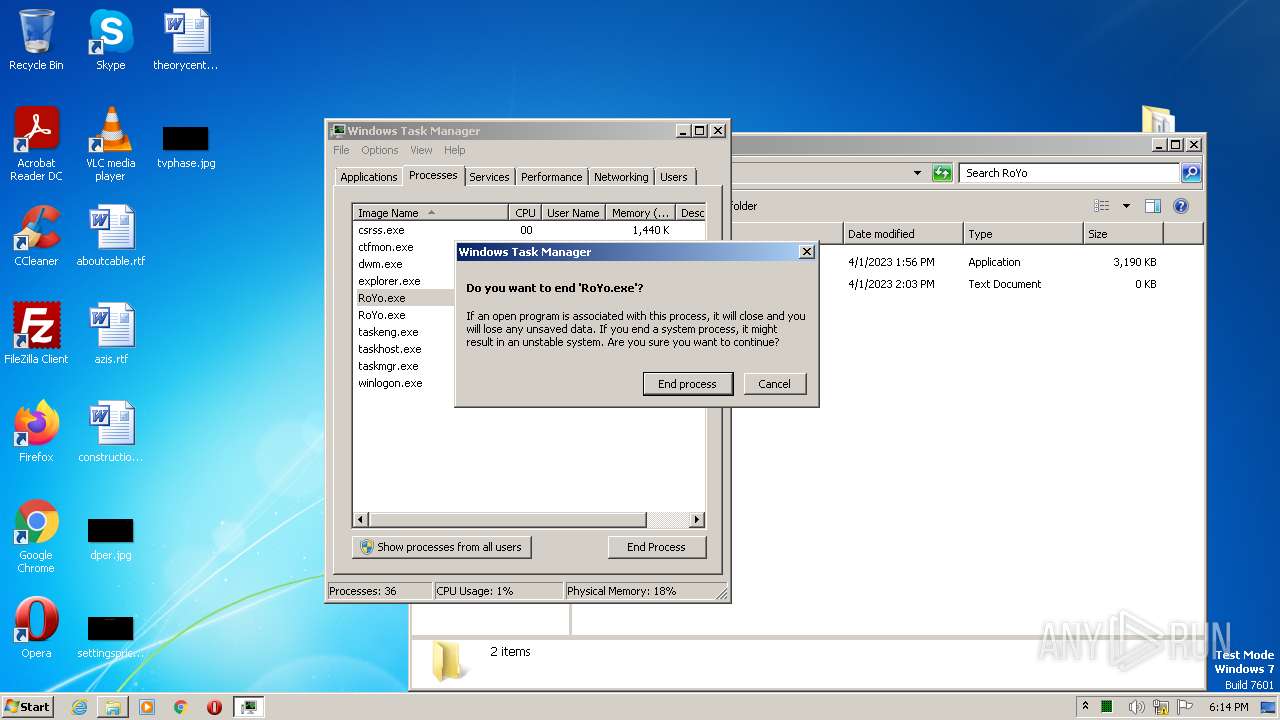
Application was dropped or rewritten from another process
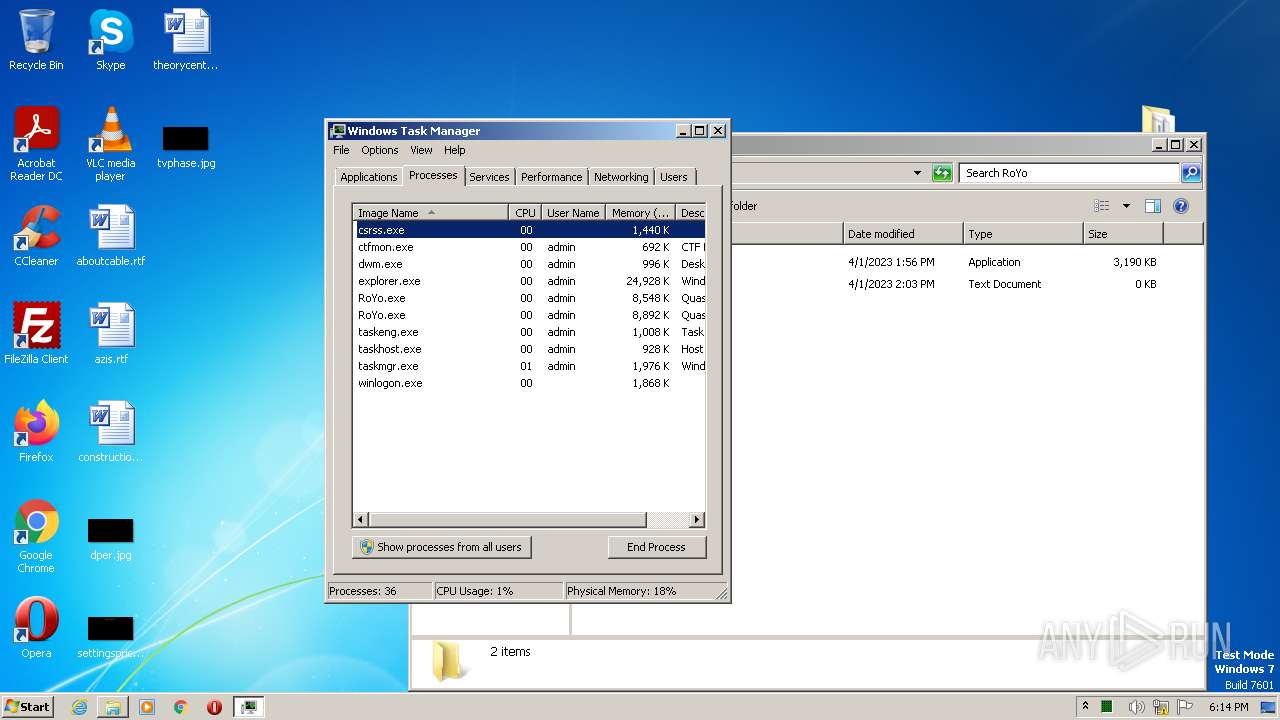
- RoYo.exe (PID: 3864)
- RoYo.exe (PID: 2952)
ASYNCRAT detected by memory dumps
- RoYo.exe (PID: 3864)
- RoYo.exe (PID: 2952)
QUASAR detected by memory dumps
- RoYo.exe (PID: 3864)
- RoYo.exe (PID: 2952)
SUSPICIOUS
No suspicious indicators.INFO
Manual execution by a user
- RoYo.exe (PID: 3864)
- RoYo.exe (PID: 2952)
- taskmgr.exe (PID: 3224)
Checks supported languages
- RoYo.exe (PID: 3864)
- RoYo.exe (PID: 2952)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2512)
Reads the computer name
- RoYo.exe (PID: 3864)
- RoYo.exe (PID: 2952)
Reads Environment values
- RoYo.exe (PID: 3864)
- RoYo.exe (PID: 2952)
The process checks LSA protection
- RoYo.exe (PID: 3864)
- RoYo.exe (PID: 2952)
Reads the machine GUID from the registry
- RoYo.exe (PID: 3864)
- RoYo.exe (PID: 2952)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Quasar
(PID) Process(3864) RoYo.exe
Version1.4.1
C2 (2)147.185.221.181:4782
Sub_DirSubDir
Install_NameDefenderSetup.exe
Mutex115c3855-a135-47d8-b491-a87b371fbb91
StartupOneDrive Support
TagOffice04
LogDirLogs
SignatureSN5sWBwo/25lV0Ek+IZyl6lkcCVPkB0H07HAVGQQbY33e0TLR/p3Ah1SD8n1x7YjhQCxfiIGdBY0AFtKgMcGapjGSeOd4aBVOhMSvAyRn7eGeBGfyPHQtIlistC54CFUgivo2DGDCtpaO64GIgYZJWw5G5AsMBNrjm/p1zkWPoXIDY9LdJyUY+1Z61pBVrLvI0lg4PDMrxis2Q0m7ZuB1W3KxzGvs4MPKYriPdCY/b7fztfo5OHm3TJ2gMYY9bVfc6v3RBUxU9tjtwcDeKxaTXELzIqd4iGS5d6jWR4W1Zl4...
CertificateMIIE9DCCAtygAwIBAgIQAJ0hC0VNIJLvW03Nv0KWgTANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTIzMDMzMDE2NDkyNFoYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAxRD+tQJsGG0NRD8tYPShMwFpG/KS0ofFA8nmFLLSbZfmGk6eQsNgt41GJqW0yGxNwFONytXa...
(PID) Process(2952) RoYo.exe
Version1.4.1
C2 (2)147.185.221.181:4782
Sub_DirSubDir
Install_NameDefenderSetup.exe
Mutex115c3855-a135-47d8-b491-a87b371fbb91
StartupOneDrive Support
TagOffice04
LogDirLogs
SignatureSN5sWBwo/25lV0Ek+IZyl6lkcCVPkB0H07HAVGQQbY33e0TLR/p3Ah1SD8n1x7YjhQCxfiIGdBY0AFtKgMcGapjGSeOd4aBVOhMSvAyRn7eGeBGfyPHQtIlistC54CFUgivo2DGDCtpaO64GIgYZJWw5G5AsMBNrjm/p1zkWPoXIDY9LdJyUY+1Z61pBVrLvI0lg4PDMrxis2Q0m7ZuB1W3KxzGvs4MPKYriPdCY/b7fztfo5OHm3TJ2gMYY9bVfc6v3RBUxU9tjtwcDeKxaTXELzIqd4iGS5d6jWR4W1Zl4...
CertificateMIIE9DCCAtygAwIBAgIQAJ0hC0VNIJLvW03Nv0KWgTANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTIzMDMzMDE2NDkyNFoYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAxRD+tQJsGG0NRD8tYPShMwFpG/KS0ofFA8nmFLLSbZfmGk6eQsNgt41GJqW0yGxNwFONytXa...
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | RoYo/RoYo.exe |
|---|---|
| ZipUncompressedSize: | 3266048 |
| ZipCompressedSize: | 1222972 |
| ZipCRC: | 0x01e157c3 |
| ZipModifyDate: | 2023:04:01 13:56:06 |
| ZipCompression: | Deflated |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
39
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2512 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\RoYo.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2952 | "C:\Users\admin\Desktop\RoYo\RoYo.exe" | C:\Users\admin\Desktop\RoYo\RoYo.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Quasar Client Exit code: 1 Version: 1.4.1 Modules
Quasar(PID) Process(2952) RoYo.exe Version1.4.1 C2 (2)147.185.221.181:4782 Sub_DirSubDir Install_NameDefenderSetup.exe Mutex115c3855-a135-47d8-b491-a87b371fbb91 StartupOneDrive Support TagOffice04 LogDirLogs SignatureSN5sWBwo/25lV0Ek+IZyl6lkcCVPkB0H07HAVGQQbY33e0TLR/p3Ah1SD8n1x7YjhQCxfiIGdBY0AFtKgMcGapjGSeOd4aBVOhMSvAyRn7eGeBGfyPHQtIlistC54CFUgivo2DGDCtpaO64GIgYZJWw5G5AsMBNrjm/p1zkWPoXIDY9LdJyUY+1Z61pBVrLvI0lg4PDMrxis2Q0m7ZuB1W3KxzGvs4MPKYriPdCY/b7fztfo5OHm3TJ2gMYY9bVfc6v3RBUxU9tjtwcDeKxaTXELzIqd4iGS5d6jWR4W1Zl4... CertificateMIIE9DCCAtygAwIBAgIQAJ0hC0VNIJLvW03Nv0KWgTANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTIzMDMzMDE2NDkyNFoYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAxRD+tQJsGG0NRD8tYPShMwFpG/KS0ofFA8nmFLLSbZfmGk6eQsNgt41GJqW0yGxNwFONytXa... | |||||||||||||||
| 3224 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\System32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3864 | "C:\Users\admin\Desktop\RoYo\RoYo.exe" | C:\Users\admin\Desktop\RoYo\RoYo.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Quasar Client Exit code: 1 Version: 1.4.1 Modules
Quasar(PID) Process(3864) RoYo.exe Version1.4.1 C2 (2)147.185.221.181:4782 Sub_DirSubDir Install_NameDefenderSetup.exe Mutex115c3855-a135-47d8-b491-a87b371fbb91 StartupOneDrive Support TagOffice04 LogDirLogs SignatureSN5sWBwo/25lV0Ek+IZyl6lkcCVPkB0H07HAVGQQbY33e0TLR/p3Ah1SD8n1x7YjhQCxfiIGdBY0AFtKgMcGapjGSeOd4aBVOhMSvAyRn7eGeBGfyPHQtIlistC54CFUgivo2DGDCtpaO64GIgYZJWw5G5AsMBNrjm/p1zkWPoXIDY9LdJyUY+1Z61pBVrLvI0lg4PDMrxis2Q0m7ZuB1W3KxzGvs4MPKYriPdCY/b7fztfo5OHm3TJ2gMYY9bVfc6v3RBUxU9tjtwcDeKxaTXELzIqd4iGS5d6jWR4W1Zl4... CertificateMIIE9DCCAtygAwIBAgIQAJ0hC0VNIJLvW03Nv0KWgTANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTIzMDMzMDE2NDkyNFoYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAxRD+tQJsGG0NRD8tYPShMwFpG/KS0ofFA8nmFLLSbZfmGk6eQsNgt41GJqW0yGxNwFONytXa... | |||||||||||||||
Total events
2 840
Read events
2 746
Write events
94
Delete events
0
Modification events
| (PID) Process: | (2512) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (2512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
2
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2512 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2512.21890\RoYo\RoYo.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report