| File name: | 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe |
| Full analysis: | https://app.any.run/tasks/80d0f5dc-95ab-4fe4-aec6-58c234c3ba23 |
| Verdict: | Malicious activity |
| Threats: | Phobos is a ransomware that locks or encrypts files to demand a ransom. It uses AES encryption with different extensions, which leaves no chance to recover the infected files. |
| Analysis date: | June 29, 2024, 22:33:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 2C78F28A0F3DBD0F45F96F4AEE72E8EE |
| SHA1: | F10803CF1D160020E3F611E9F2DD8BE93CB7D7EF |
| SHA256: | 6597018298AAAC827ABB1C58E4B6D7967993B4012EAA83B5540475E0F4F9D34F |
| SSDEEP: | 1536:KymNrLwC/WPYQ3CUXe3f/fgYoPPK2wxufMIzXofka:Kymdw49Q3teHfgYUK3xAzXe3 |
MALICIOUS
Drops the executable file immediately after the start
- 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe (PID: 3380)
- 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe (PID: 3372)
Create files in the Startup directory
- 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe (PID: 3372)
Changes the autorun value in the registry
- 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe (PID: 3372)
- 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe (PID: 3380)
Deletes shadow copies
- cmd.exe (PID: 2108)
PHOBOS has been detected
- 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe (PID: 3372)
Using BCDEDIT.EXE to modify recovery options
- cmd.exe (PID: 2108)
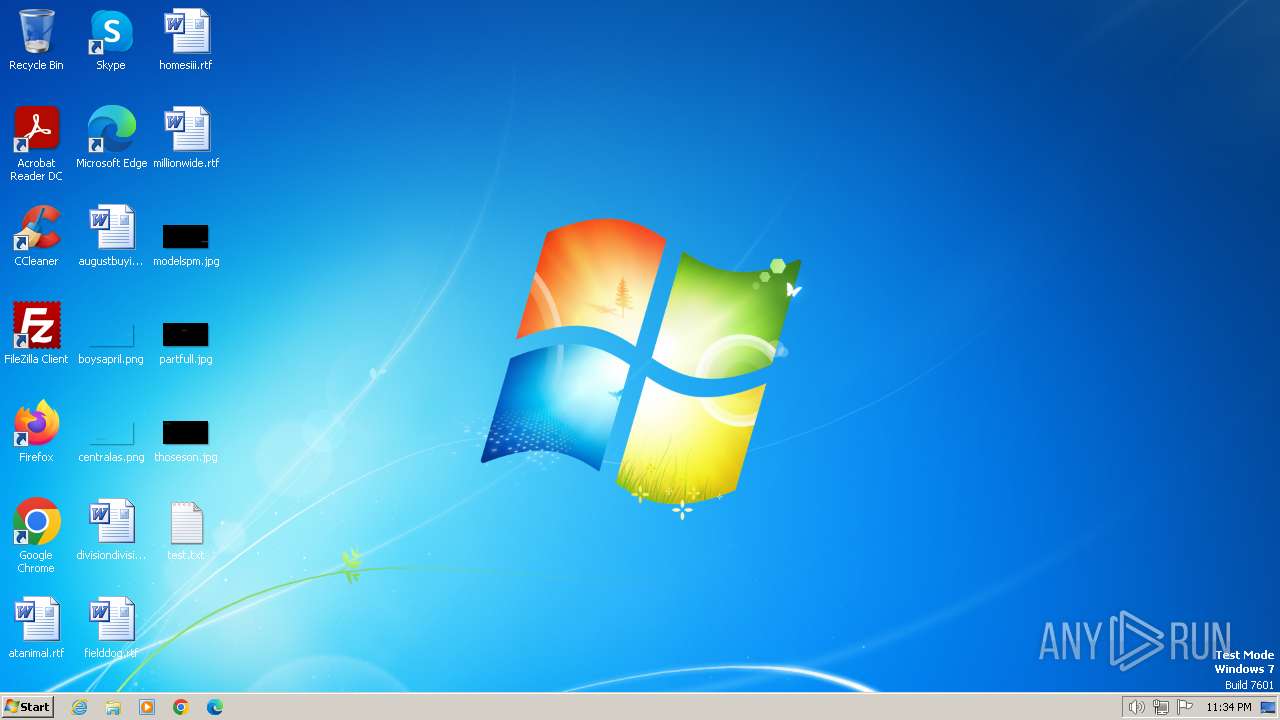
Renames files like ransomware
- 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe (PID: 3372)
Actions looks like stealing of personal data
- 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe (PID: 3372)
SUSPICIOUS
Reads security settings of Internet Explorer
- 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe (PID: 3400)
Reads the Internet Settings
- 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe (PID: 3400)
- notepad.exe (PID: 2856)
- WMIC.exe (PID: 4012)
Starts CMD.EXE for commands execution
- 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe (PID: 3372)
Application launched itself
- 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe (PID: 3400)
- 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe (PID: 3380)
Executable content was dropped or overwritten
- 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe (PID: 3372)
Creates file in the systems drive root
- 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe (PID: 3372)
Uses NETSH.EXE to change the status of the firewall
- cmd.exe (PID: 2300)
Executes as Windows Service
- VSSVC.exe (PID: 2852)
- wbengine.exe (PID: 2120)
- vds.exe (PID: 2328)
Reads browser cookies
- 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe (PID: 3372)
The process creates files with name similar to system file names
- 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe (PID: 3372)
Process drops legitimate windows executable
- 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe (PID: 3372)
INFO
Checks supported languages
- 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe (PID: 3400)
- 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe (PID: 3380)
- 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe (PID: 3372)
Reads the computer name
- 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe (PID: 3400)
- 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe (PID: 3372)
- 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe (PID: 3380)
Creates files or folders in the user directory
- 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe (PID: 3372)
Creates files in the program directory
- 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe (PID: 3372)
Manual execution by a user
- notepad.exe (PID: 2856)
- notepad.exe (PID: 832)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:03:31 14:17:25+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 34304 |
| InitializedDataSize: | 15872 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2fa7 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
63
Monitored processes
19
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 832 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\test.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1044 | vssadmin delete shadows /all /quiet | C:\Windows\System32\vssadmin.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Command Line Interface for Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1516 | bcdedit /set {default} bootstatuspolicy ignoreallfailures | C:\Windows\System32\bcdedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Boot Configuration Data Editor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2080 | netsh advfirewall set currentprofile state off | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2108 | "C:\Windows\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2120 | "C:\Windows\system32\wbengine.exe" | C:\Windows\System32\wbengine.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Block Level Backup Engine Service EXE Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2300 | "C:\Windows\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2328 | C:\Windows\System32\vds.exe | C:\Windows\System32\vds.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Virtual Disk Service Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2852 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2856 | "C:\Windows\system32\notepad.exe" | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
10 237
Read events
10 063
Write events
170
Delete events
4
Modification events
| (PID) Process: | (3400) 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3400) 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3400) 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3400) 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3372) 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f |
Value: C:\Users\admin\AppData\Local\6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe | |||
| (PID) Process: | (3372) 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f |
Value: C:\Users\admin\AppData\Local\6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe | |||
| (PID) Process: | (2080) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3676) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3380) 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f |
Value: C:\Users\admin\AppData\Local\6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe | |||
| (PID) Process: | (3380) 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f |
Value: C:\Users\admin\AppData\Local\6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe | |||
Executable files
174
Suspicious files
3 826
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3372 | 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe | C:\MSOCache\All Users\{90140000-0015-0407-0000-0000000FF1CE}-C\AccLR.cab.id[C4BA3647-3483].[recovery8files@onionmail.org].8base | — | |
MD5:— | SHA256:— | |||
| 3372 | 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe | C:\MSOCache\All Users\{90140000-0015-040C-0000-0000000FF1CE}-C\AccLR.cab.id[C4BA3647-3483].[recovery8files@onionmail.org].8base | — | |
MD5:— | SHA256:— | |||
| 3372 | 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe | C:\MSOCache\All Users\{90140000-0015-0410-0000-0000000FF1CE}-C\AccLR.cab.id[C4BA3647-3483].[recovery8files@onionmail.org].8base | — | |
MD5:— | SHA256:— | |||
| 3372 | 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe | C:\programdata\microsoft\windows\start menu\programs\startup\6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe | executable | |
MD5:2C78F28A0F3DBD0F45F96F4AEE72E8EE | SHA256:6597018298AAAC827ABB1C58E4B6D7967993B4012EAA83B5540475E0F4F9D34F | |||
| 3372 | 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe | C:\$Recycle.Bin\S-1-5-21-1302019708-1500728564-335382590-500\desktop.ini.id[C4BA3647-3483].[recovery8files@onionmail.org].8base | binary | |
MD5:8BB6B4704FEF80ECC613B6436E7AB315 | SHA256:F15255671D1E898D39B5BCB55EA494D9EE7CF381740545989519CCE24EB39581 | |||
| 3372 | 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe | C:\MSOCache\All Users\{90140000-0015-0411-0000-0000000FF1CE}-C\AccLR.cab.id[C4BA3647-3483].[recovery8files@onionmail.org].8base | — | |
MD5:— | SHA256:— | |||
| 3372 | 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe | C:\config.sys.id[C4BA3647-3483].[recovery8files@onionmail.org].8base | binary | |
MD5:611F11F10152F7F0EE80E7B161931D70 | SHA256:90DC68F11469ED828A0BD0DEB12FDC044BBEAE48D9F9CD315F7BE091A432BE65 | |||
| 3372 | 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe | C:\MSOCache\All Users\{90140000-0015-0407-0000-0000000FF1CE}-C\AccessMUI.msi.id[C4BA3647-3483].[recovery8files@onionmail.org].8base | executable | |
MD5:B68BD80A5A3B703BABC7FB19BAF104AB | SHA256:1CB1E08D560E9E6C62A7E48680A218D022F0D331EB52F3CE66504A167FAD652F | |||
| 3372 | 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe | C:\MSOCache\All Users\{90140000-0015-040C-0000-0000000FF1CE}-C\AccessMUI.msi.id[C4BA3647-3483].[recovery8files@onionmail.org].8base | executable | |
MD5:859AB199A959FB1487CB2B59885E4DA6 | SHA256:41817D9973027BA79057E641930B28A6C62408CB61599F5212A5690350681101 | |||
| 3372 | 6597018298aaac827abb1c58e4b6d7967993b4012eaa83b5540475e0f4f9d34f.exe | C:\autoexec.bat.id[C4BA3647-3483].[recovery8files@onionmail.org].8base | binary | |
MD5:485DBD0D5F11D728AA71581007A303A7 | SHA256:693E853AF4138EA2C7FA21222C9A298C4DE065C282C2F0C0B0C5C66D6CA44500 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
13
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a9f83325acc8ca75 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1372 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2564 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1372 | svchost.exe | 199.232.214.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
1372 | svchost.exe | 2.16.164.120:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
1372 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | unknown |
1060 | svchost.exe | 199.232.214.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |