| File name: | FreebieNotes.exe |
| Full analysis: | https://app.any.run/tasks/9c32957f-0262-47ef-a48c-1e392d66ebe5 |
| Verdict: | Malicious activity |
| Threats: | Lumma is an information stealer, developed using the C programming language. It is offered for sale as a malware-as-a-service, with several plans available. It usually targets cryptocurrency wallets, login credentials, and other sensitive information on a compromised system. The malicious software regularly gets updates that improve and expand its functionality, making it a serious stealer threat. |
| Analysis date: | January 10, 2025, 19:59:02 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows, 9 sections |
| MD5: | 32A6235DF0A558D1E91F00AF059BBD12 |
| SHA1: | 09823E9DC07C2504A373777B0C3B17CE88A513D5 |
| SHA256: | 658EC90E3630D87D5660FDE8C38E969D36143D53589D498D76F3B302EAE0A50F |
| SSDEEP: | 98304:0PtTEW4bEaON6YS/jLND0uLienFDyhFZ9uCsNGcJf+F+/O3JbeA2hNd2meaT4BSd:yZOJPFInF7Y |
MALICIOUS
LUMMA has been found (auto)
- FreebieNotes.exe (PID: 6700)
Executing a file with an untrusted certificate
- FreebieNotes.exe (PID: 6700)
Steals credentials from Web Browsers
- FreebieNotes.exe (PID: 6700)
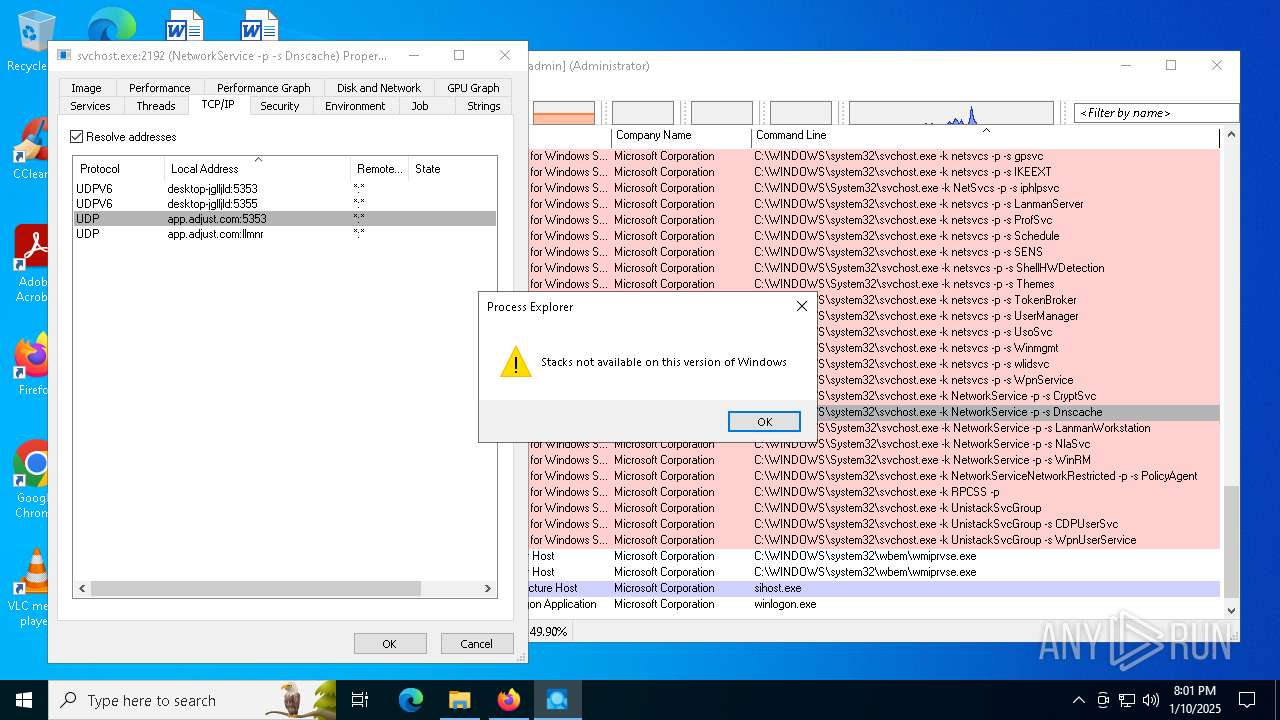
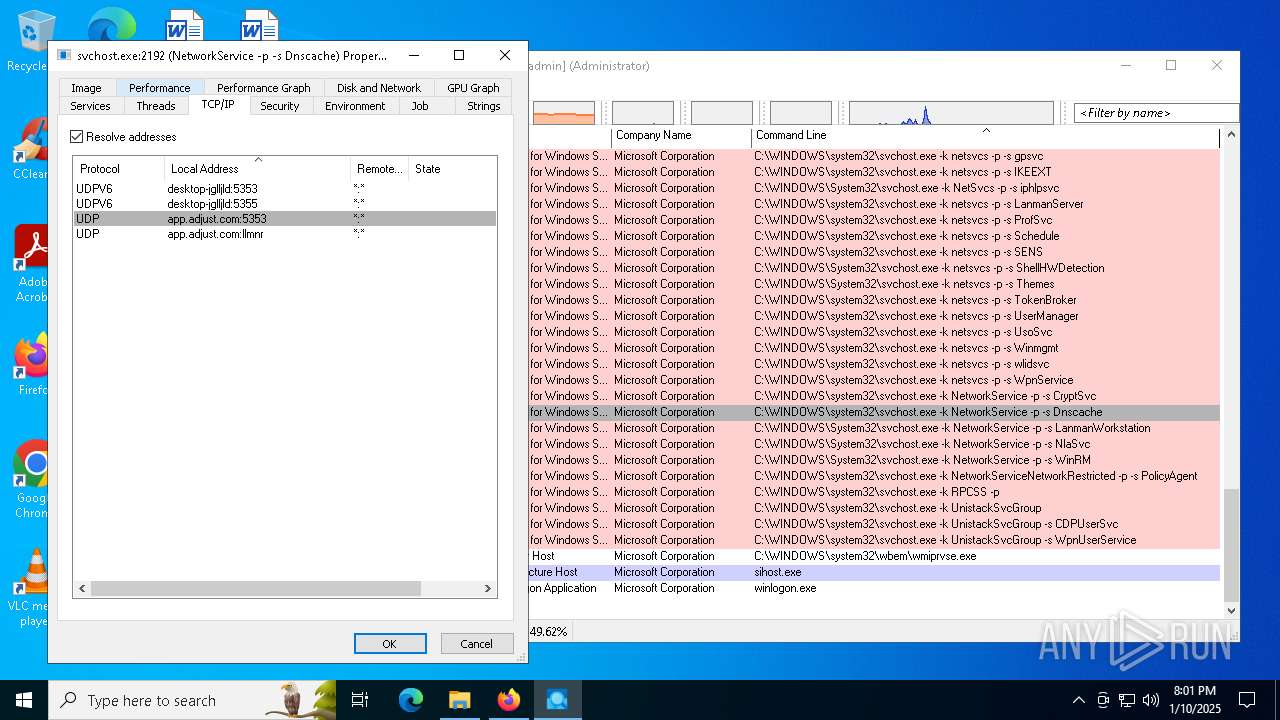
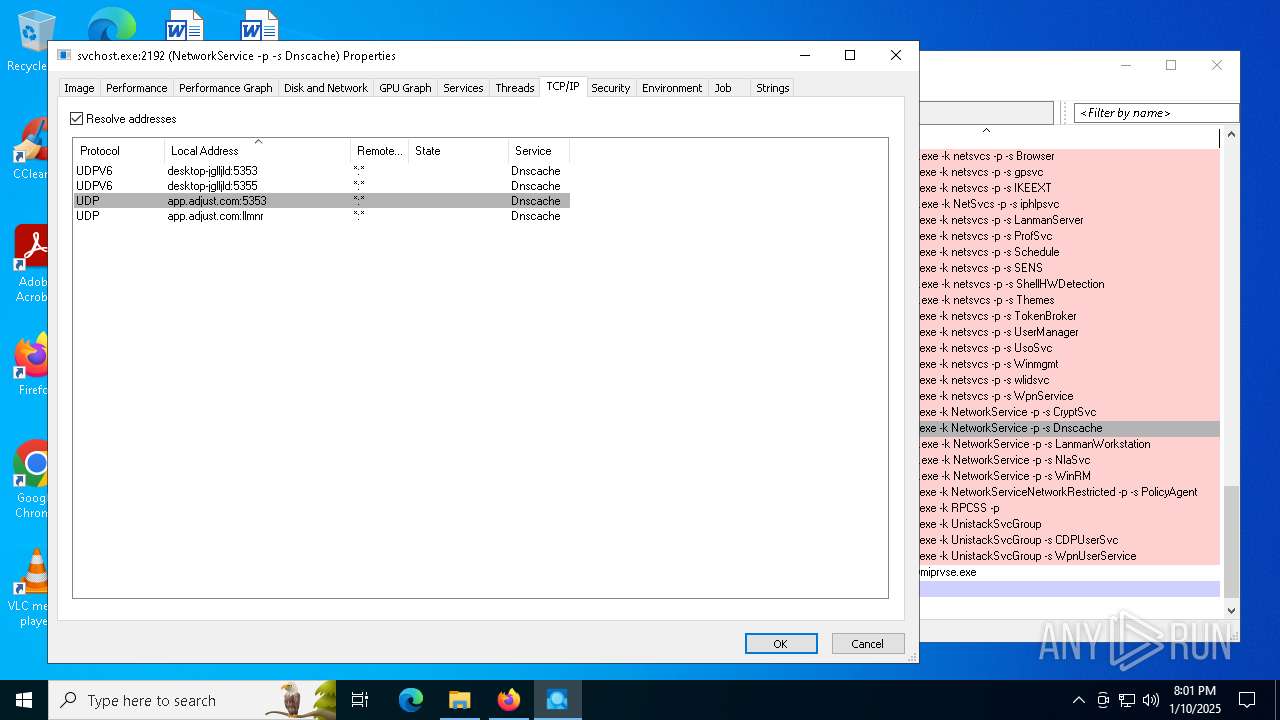
Connects to the CnC server
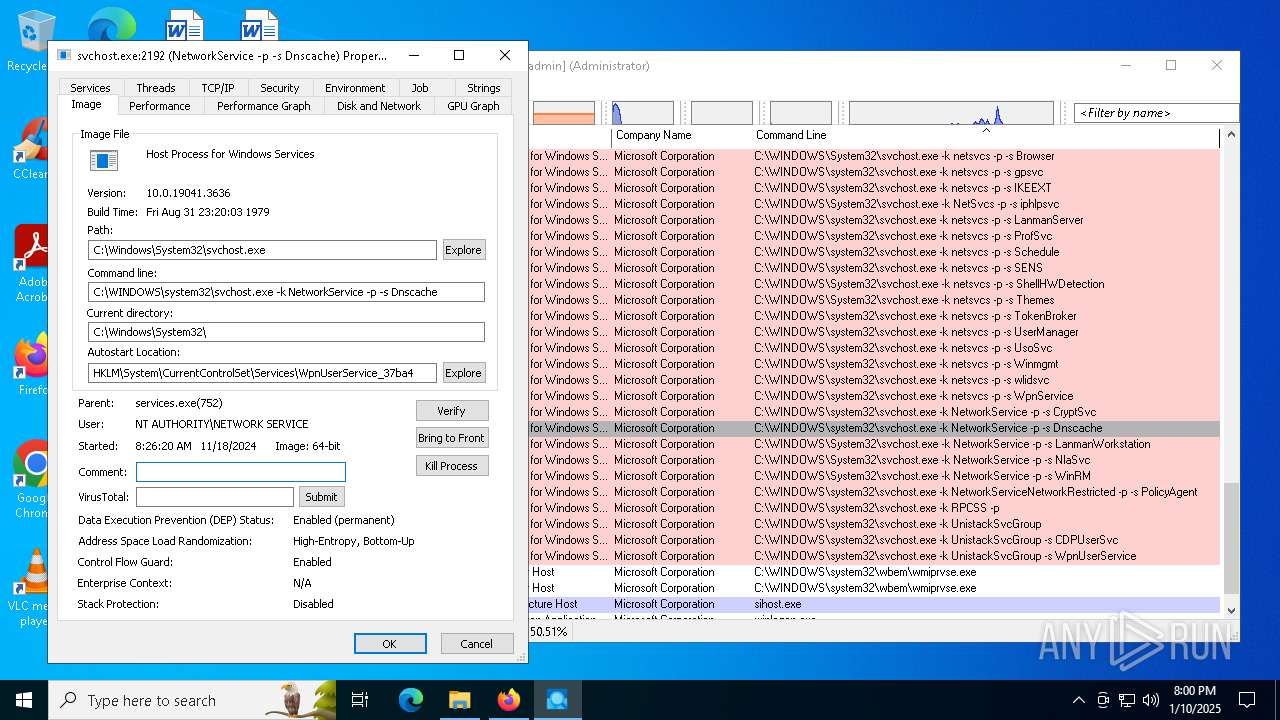
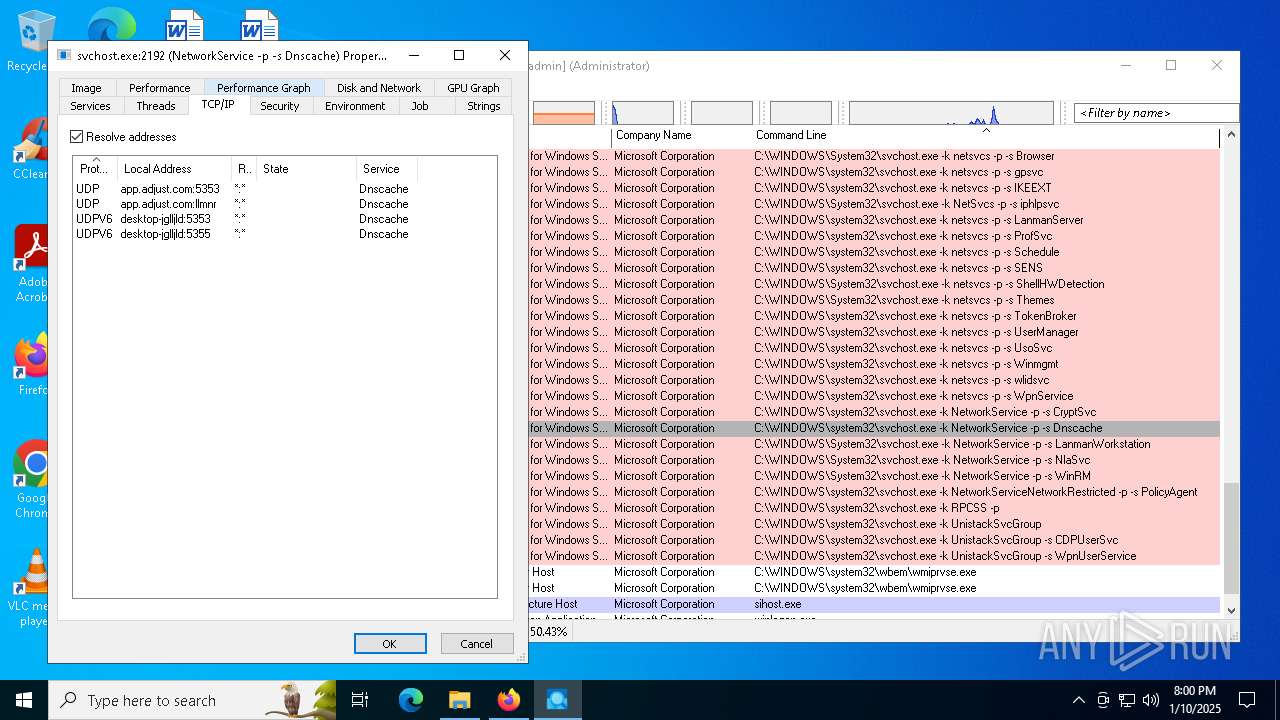
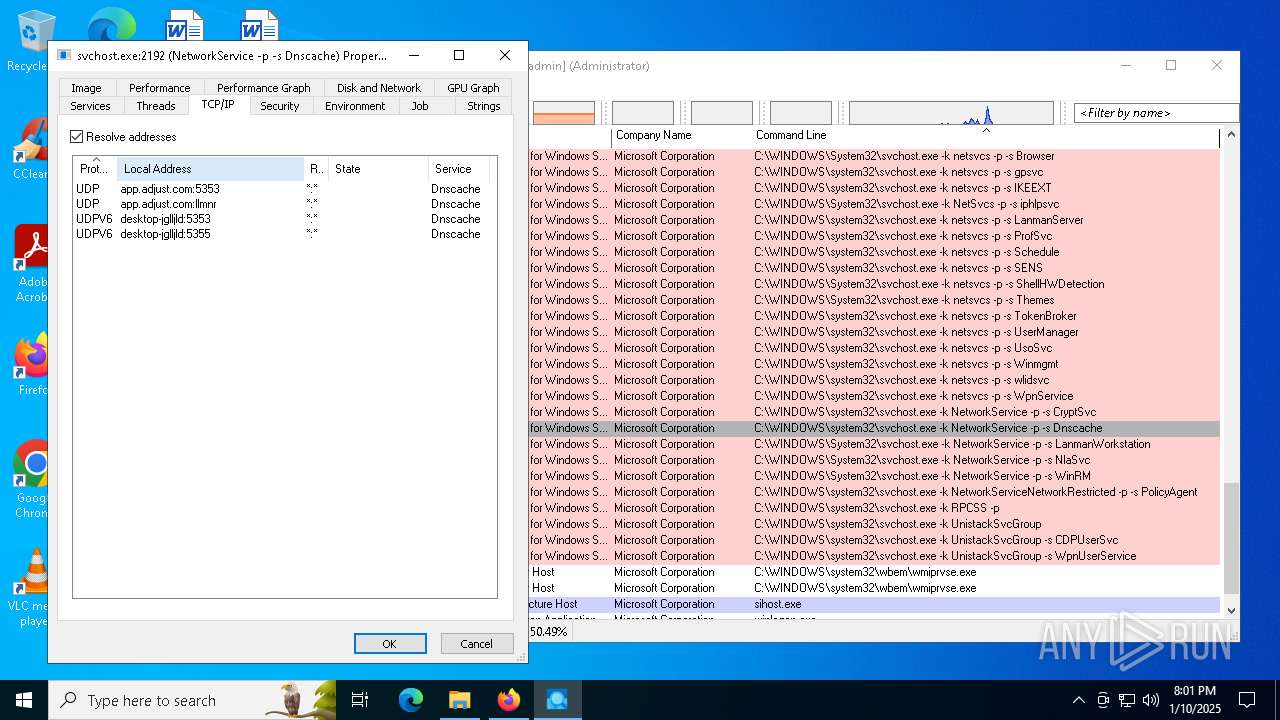
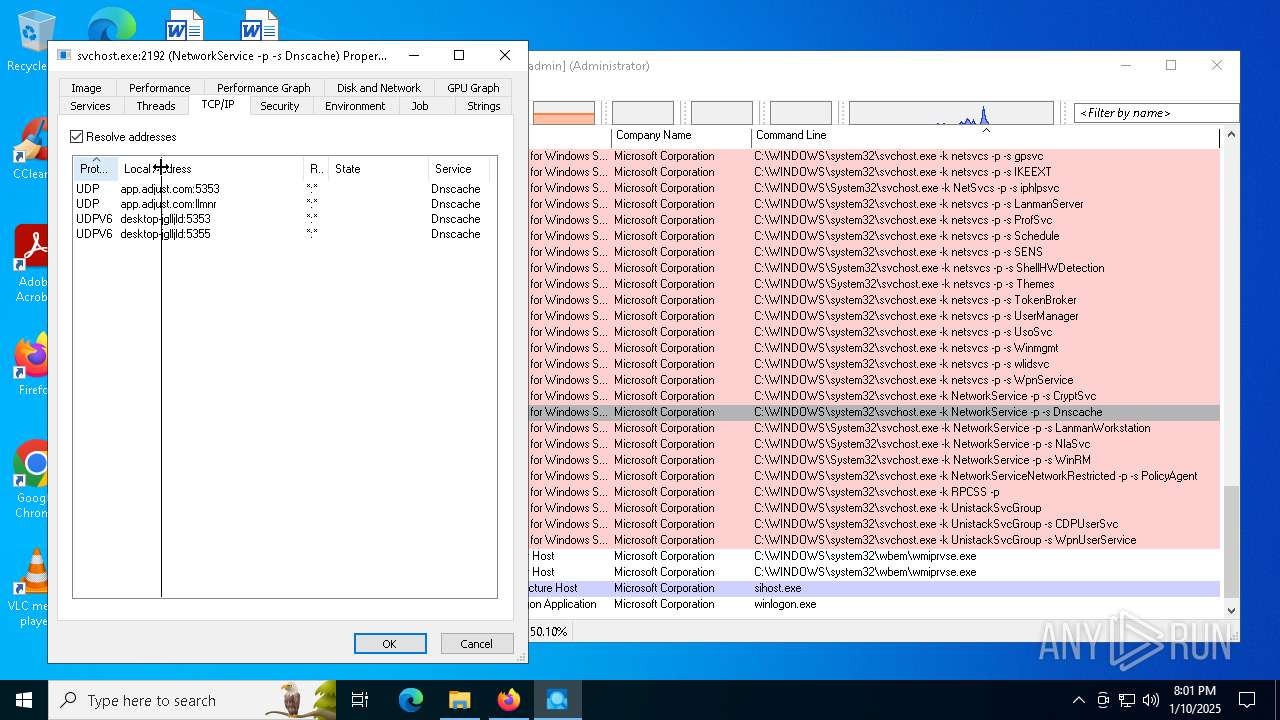
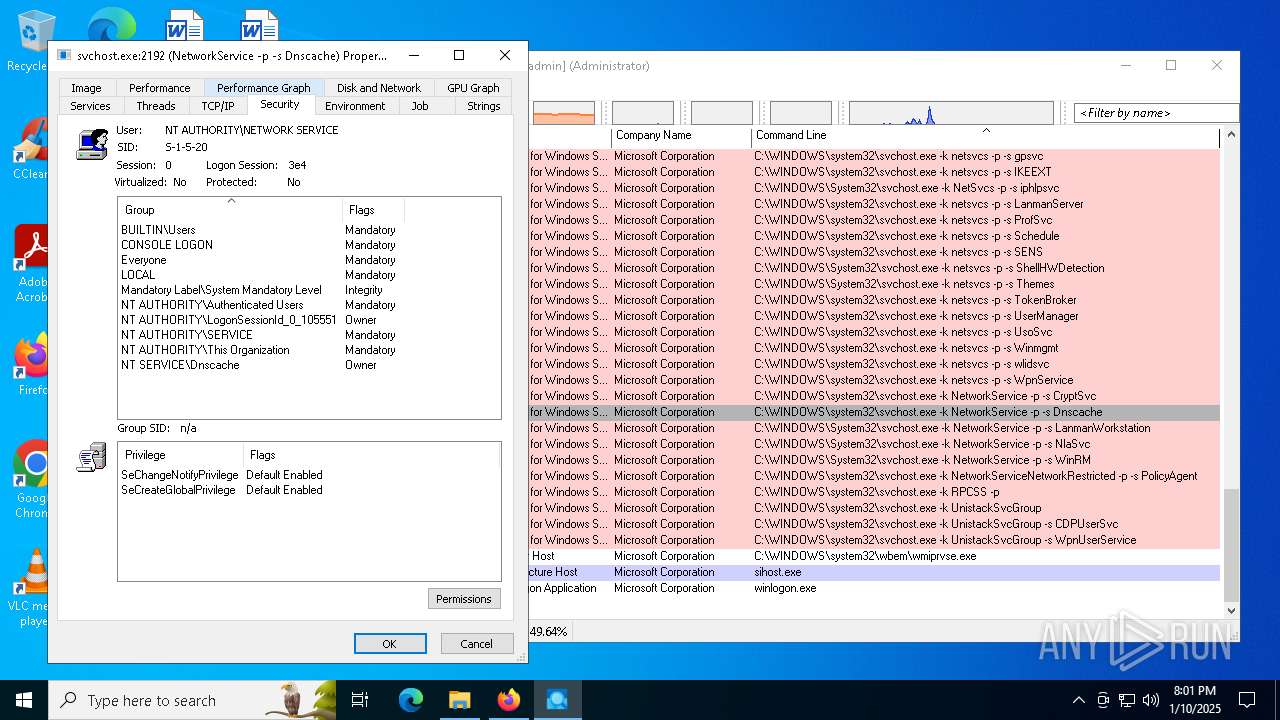
- svchost.exe (PID: 2192)
LUMMA has been detected (YARA)
- FreebieNotes.exe (PID: 6700)
Actions looks like stealing of personal data
- FreebieNotes.exe (PID: 6700)
LUMMA has been detected (SURICATA)
- FreebieNotes.exe (PID: 6700)
- svchost.exe (PID: 2192)
LUMMA mutex has been found
- FreebieNotes.exe (PID: 6700)
Runs injected code in another process
- PROCEXP64.exe (PID: 7980)
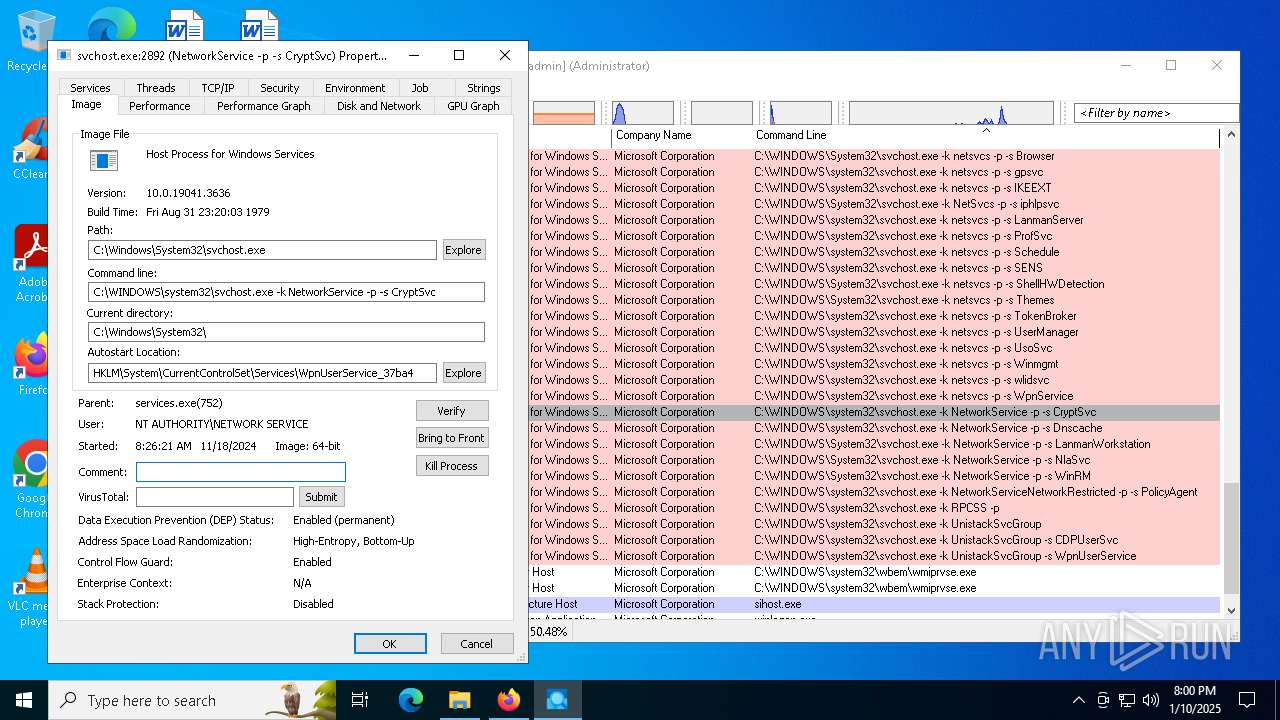
Application was injected by another process
- svchost.exe (PID: 2192)
SUSPICIOUS
The process checks if it is being run in the virtual environment
- procexp.exe (PID: 7436)
- procexp64.exe (PID: 7420)
- PROCEXP64.exe (PID: 7980)
- procexp.exe (PID: 7988)
Executable content was dropped or overwritten
- procexp.exe (PID: 7436)
- procexp64.exe (PID: 7420)
- procexp.exe (PID: 7988)
- PROCEXP64.exe (PID: 7980)
Drops a system driver (possible attempt to evade defenses)
- procexp64.exe (PID: 7420)
- PROCEXP64.exe (PID: 7980)
Reads security settings of Internet Explorer
- procexp64.exe (PID: 7420)
- PROCEXP64.exe (PID: 7980)
Reads the date of Windows installation
- procexp64.exe (PID: 7420)
Checks Windows Trust Settings
- procexp64.exe (PID: 7420)
- PROCEXP64.exe (PID: 7980)
Contacting a server suspected of hosting an CnC
- FreebieNotes.exe (PID: 6700)
- svchost.exe (PID: 2192)
Creates or modifies Windows services
- PROCEXP64.exe (PID: 7980)
Adds/modifies Windows certificates
- PROCEXP64.exe (PID: 7980)
Detected use of alternative data streams (AltDS)
- PROCEXP64.exe (PID: 7980)
INFO
The sample compiled with english language support
- FreebieNotes.exe (PID: 6700)
- firefox.exe (PID: 7148)
- WinRAR.exe (PID: 7472)
- procexp.exe (PID: 7436)
- procexp64.exe (PID: 7420)
- procexp.exe (PID: 7988)
- PROCEXP64.exe (PID: 7980)
Checks supported languages
- FreebieNotes.exe (PID: 6700)
- procexp64.exe (PID: 7420)
Reads the computer name
- FreebieNotes.exe (PID: 6700)
- procexp.exe (PID: 7436)
- PROCEXP64.exe (PID: 7980)
Application launched itself
- firefox.exe (PID: 7148)
- firefox.exe (PID: 7128)
The process uses the downloaded file
- firefox.exe (PID: 7148)
Manual execution by a user
- firefox.exe (PID: 7128)
- WinRAR.exe (PID: 7472)
- procexp.exe (PID: 7436)
- notepad.exe (PID: 7520)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7472)
Create files in a temporary directory
- procexp.exe (PID: 7436)
- procexp64.exe (PID: 7420)
- procexp.exe (PID: 7988)
Checks proxy server information
- procexp64.exe (PID: 7420)
- PROCEXP64.exe (PID: 7980)
Reads the machine GUID from the registry
- procexp64.exe (PID: 7420)
- PROCEXP64.exe (PID: 7980)
Reads Microsoft Office registry keys
- procexp64.exe (PID: 7420)
- PROCEXP64.exe (PID: 7980)
Reads the software policy settings
- procexp64.exe (PID: 7420)
- FreebieNotes.exe (PID: 6700)
- PROCEXP64.exe (PID: 7980)
Creates files or folders in the user directory
- procexp64.exe (PID: 7420)
- PROCEXP64.exe (PID: 7980)
Process checks computer location settings
- procexp64.exe (PID: 7420)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .scr | | | Windows screen saver (60.5) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (20.8) |
| .exe | | | Generic Win/DOS Executable (9.2) |
| .exe | | | DOS Executable Generic (9.2) |
| .vxd | | | VXD Driver (0.1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2014:11:25 03:03:43+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, 32-bit, No debug |
| PEType: | PE32 |
| LinkerVersion: | 5 |
| CodeSize: | 4694016 |
| InitializedDataSize: | 511488 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x23b0 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.69.5442.36223 |
| ProductVersionNumber: | 3.69.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | Power Soft |
| FileVersion: | 3.69.1.4480 |
| InternalName: | Freebie Notes |
| OriginalFileName: | FreebieNotes.exe |
| ProductName: | Freebie Notes |
| ProductVersion: | 3.69 |
Total processes
155
Monitored processes
22
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1620 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4300 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4232 -childID 2 -isForBrowser -prefsHandle 4244 -prefMapHandle 2584 -prefsLen 36588 -prefMapSize 244583 -jsInitHandle 1388 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {deaa3526-d00d-4132-8774-11fffecf08f7} 7148 "\\.\pipe\gecko-crash-server-pipe.7148" 1c65852e850 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 5028 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=1904 -parentBuildID 20240213221259 -prefsHandle 1836 -prefMapHandle 1828 -prefsLen 31031 -prefMapSize 244583 -appDir "C:\Program Files\Mozilla Firefox\browser" - {8def0818-c174-46db-a502-116579822137} 7148 "\\.\pipe\gecko-crash-server-pipe.7148" 1c6513ecb10 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 5460 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2720 -childID 1 -isForBrowser -prefsHandle 2756 -prefMapHandle 2752 -prefsLen 31447 -prefMapSize 244583 -jsInitHandle 1388 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {f2cabc79-6df5-4345-a56b-bdc6c1dcfaee} 7148 "\\.\pipe\gecko-crash-server-pipe.7148" 1c65619df50 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 5876 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5184 -childID 5 -isForBrowser -prefsHandle 5192 -prefMapHandle 5196 -prefsLen 31243 -prefMapSize 244583 -jsInitHandle 1388 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {d99b94e5-e1f6-4d50-b01f-8400d320fa91} 7148 "\\.\pipe\gecko-crash-server-pipe.7148" 1c65c4f2150 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 6216 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2148 -parentBuildID 20240213221259 -prefsHandle 2140 -prefMapHandle 2136 -prefsLen 31031 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {87194f80-3483-4b03-b751-0b25305f1764} 7148 "\\.\pipe\gecko-crash-server-pipe.7148" 1c644581910 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 6416 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4880 -parentBuildID 20240213221259 -sandboxingKind 0 -prefsHandle 3060 -prefMapHandle 4024 -prefsLen 36588 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {218855d7-eef4-47da-9d21-13728e24e554} 7148 "\\.\pipe\gecko-crash-server-pipe.7148" 1c65a178510 utility | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 6420 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5080 -childID 4 -isForBrowser -prefsHandle 5084 -prefMapHandle 5048 -prefsLen 31243 -prefMapSize 244583 -jsInitHandle 1388 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {7d567fc4-f2e3-4d11-8c63-8a6df8e3382c} 7148 "\\.\pipe\gecko-crash-server-pipe.7148" 1c65bfbff50 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 6580 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5020 -childID 3 -isForBrowser -prefsHandle 5024 -prefMapHandle 2592 -prefsLen 31243 -prefMapSize 244583 -jsInitHandle 1388 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {0e8e76a5-67c1-4d99-97d8-782428fb094b} 7148 "\\.\pipe\gecko-crash-server-pipe.7148" 1c65590c850 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
Total events
85 387
Read events
84 055
Write events
439
Delete events
893
Modification events
| (PID) Process: | (7148) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (7472) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7472) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7472) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7472) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7436) procexp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\Process Explorer |
| Operation: | write | Name: | Path |
Value: C:\Users\admin\AppData\Local\Temp\procexp64.exe | |||
| (PID) Process: | (7436) procexp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\Process Explorer |
| Operation: | write | Name: | OriginalPath |
Value: C:\Users\admin\Downloads\ProcessExplorer\procexp.exe | |||
| (PID) Process: | (7420) procexp64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\Process Explorer |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
| (PID) Process: | (7420) procexp64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\Process Explorer |
| Operation: | write | Name: | Windowplacement |
Value: 2C00000000000000010000000000000000000000FFFFFFFFFFFFFFFF6400000032000000840300008A020000 | |||
| (PID) Process: | (7420) procexp64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\Process Explorer |
| Operation: | write | Name: | FindWindowplacement |
Value: 2C00000000000000000000000000000000000000000000000000000096000000960000000000000000000000 | |||
Executable files
7
Suspicious files
231
Text files
42
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7148 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 7148 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 7148 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs-1.js | text | |
MD5:AA8E5A65CF188A00758DF82E087EBE0D | SHA256:50CFE6608A78560AB3B935D12DE0F4D3EAA08ABDEF143F6547E9A9A96F229AD9 | |||
| 7148 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs.js | text | |
MD5:AA8E5A65CF188A00758DF82E087EBE0D | SHA256:50CFE6608A78560AB3B935D12DE0F4D3EAA08ABDEF143F6547E9A9A96F229AD9 | |||
| 7148 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 7148 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 7148 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\scriptCache-child-current.bin | binary | |
MD5:C95DDC2B1A525D1A243E4C294DA2F326 | SHA256:3A5919E086BFB31E36110CF636D2D5109EB51F2C410B107F126126AB25D67363 | |||
| 7148 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:297E88D7CEB26E549254EC875649F4EB | SHA256:8B75D4FB1845BAA06122888D11F6B65E6A36B140C54A72CC13DF390FD7C95702 | |||
| 7148 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\2823318777ntouromlalnodry--naod.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 7148 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
68
TCP/UDP connections
129
DNS requests
186
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7148 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
7148 | firefox.exe | POST | 200 | 2.16.168.117:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
3700 | svchost.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3700 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7148 | firefox.exe | POST | — | 2.16.168.113:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
7148 | firefox.exe | POST | 200 | 142.250.185.227:80 | http://o.pki.goog/wr2 | unknown | — | — | whitelisted |
7148 | firefox.exe | POST | 200 | 2.16.168.113:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
7148 | firefox.exe | POST | 200 | 2.16.168.113:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 2.23.227.208:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3700 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4188 | RUXIMICS.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 40.126.32.133:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1076 | svchost.exe | 184.28.89.167:443 | go.microsoft.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
tailyoveriw.my |
| malicious |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
spocs.getpocket.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Domain Observed Used for C2 Detected | ET MALWARE Win32/Lumma Stealer Related CnC Domain in DNS Lookup (tailyoveriw .my) |
6700 | FreebieNotes.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (tailyoveriw .my in TLS SNI) |
6700 | FreebieNotes.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (tailyoveriw .my in TLS SNI) |
6700 | FreebieNotes.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (tailyoveriw .my in TLS SNI) |
6700 | FreebieNotes.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (tailyoveriw .my in TLS SNI) |
6700 | FreebieNotes.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (tailyoveriw .my in TLS SNI) |
6700 | FreebieNotes.exe | Domain Observed Used for C2 Detected | ET MALWARE Observed Win32/Lumma Stealer Related Domain (tailyoveriw .my in TLS SNI) |