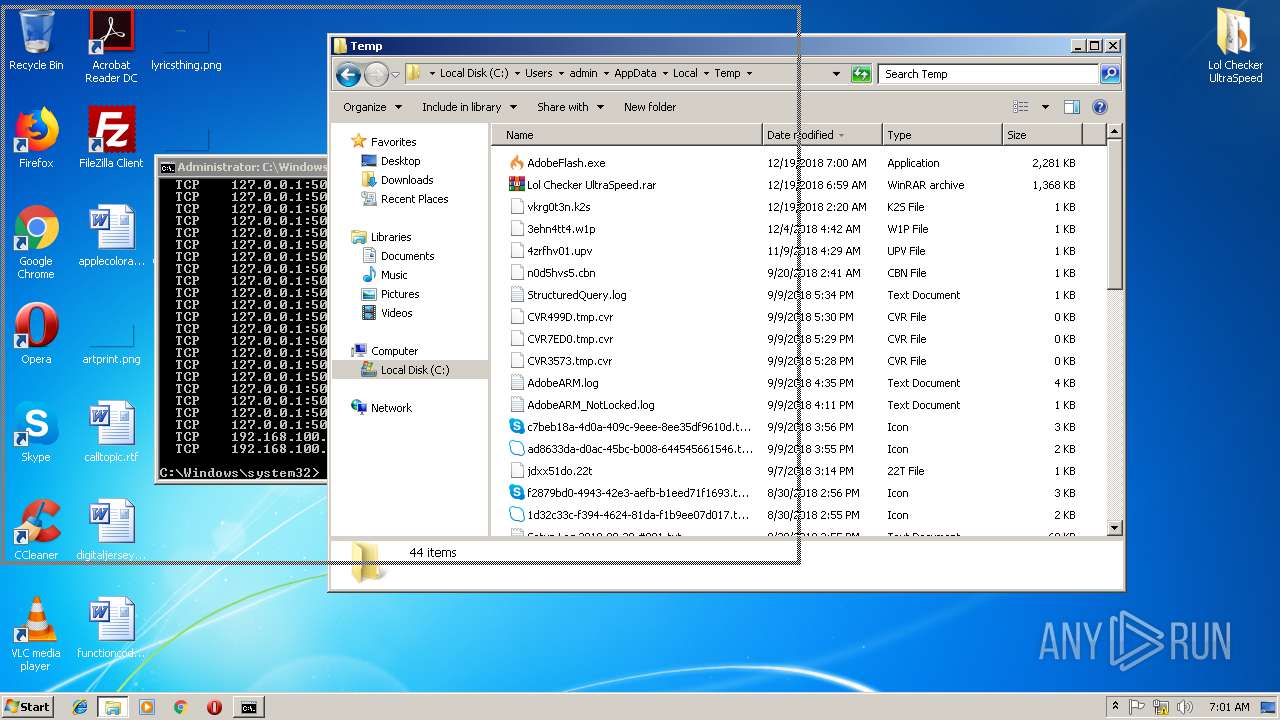
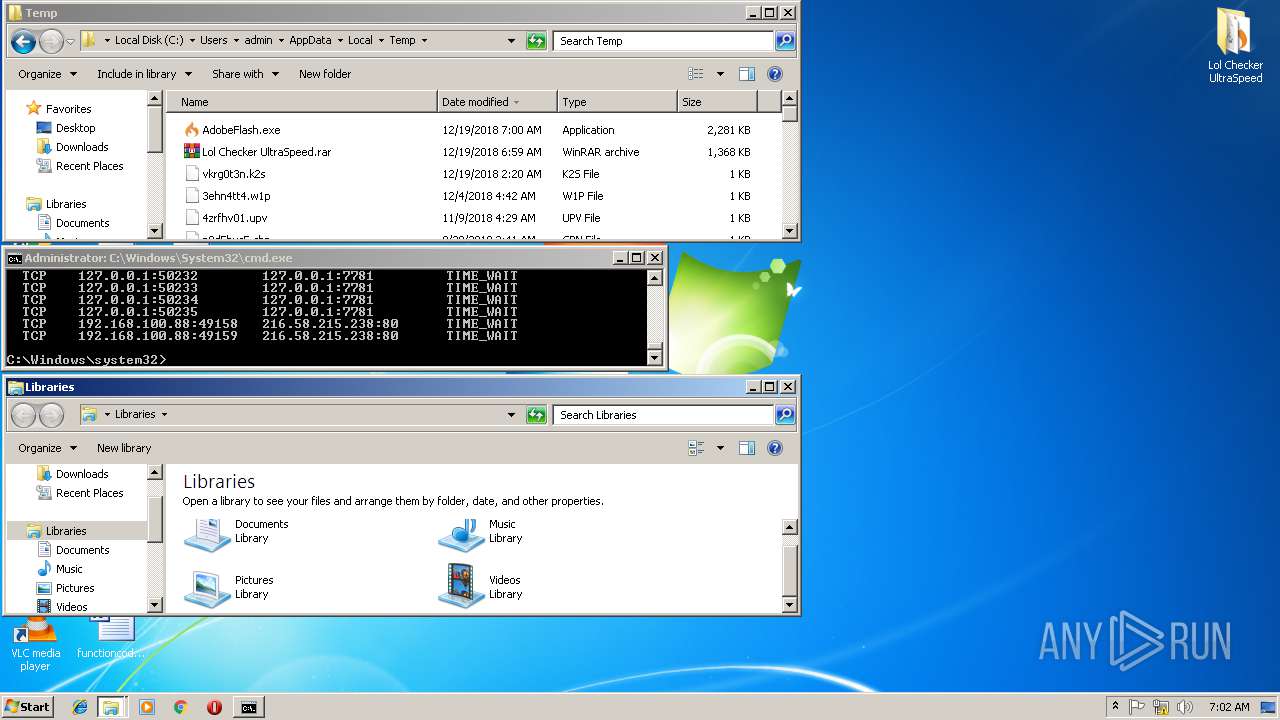
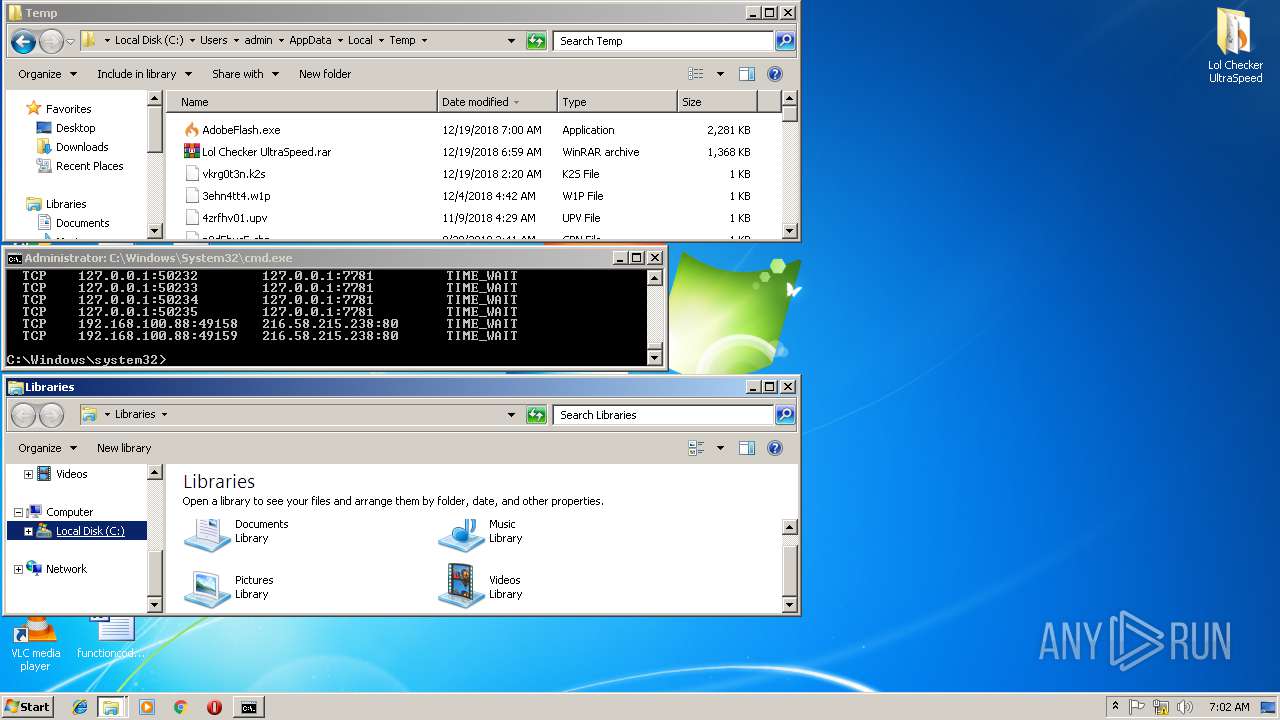
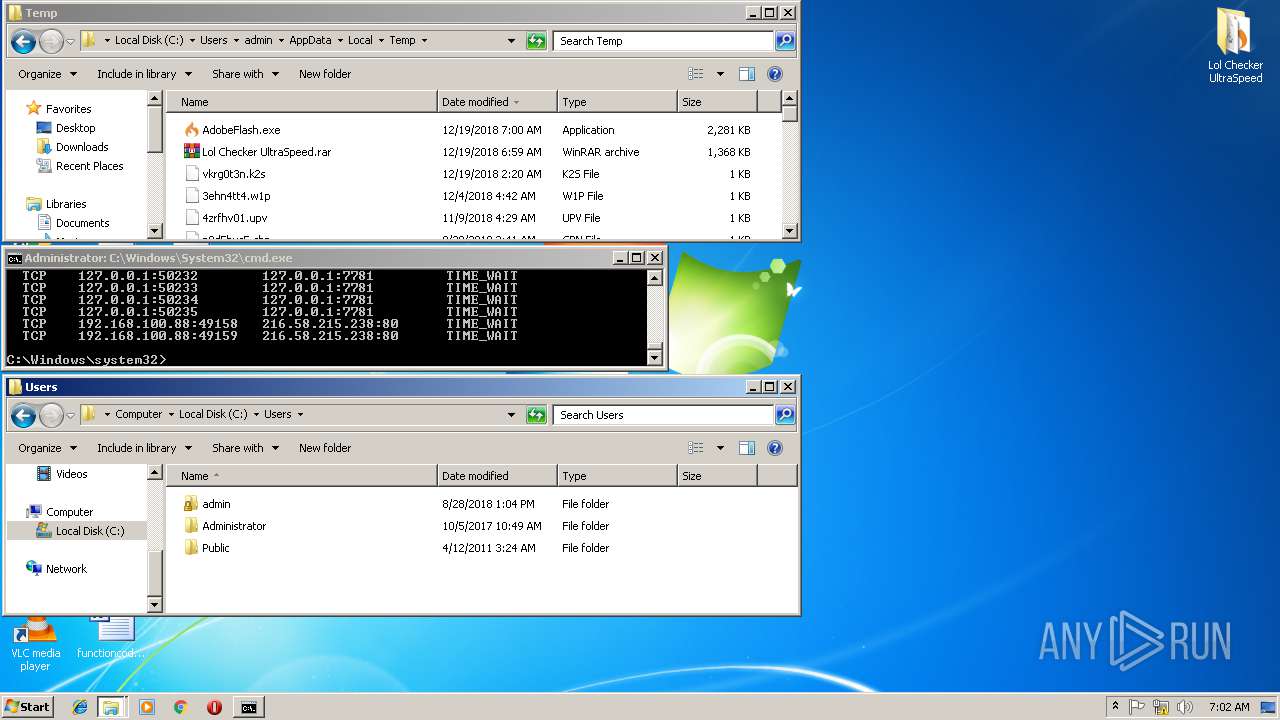
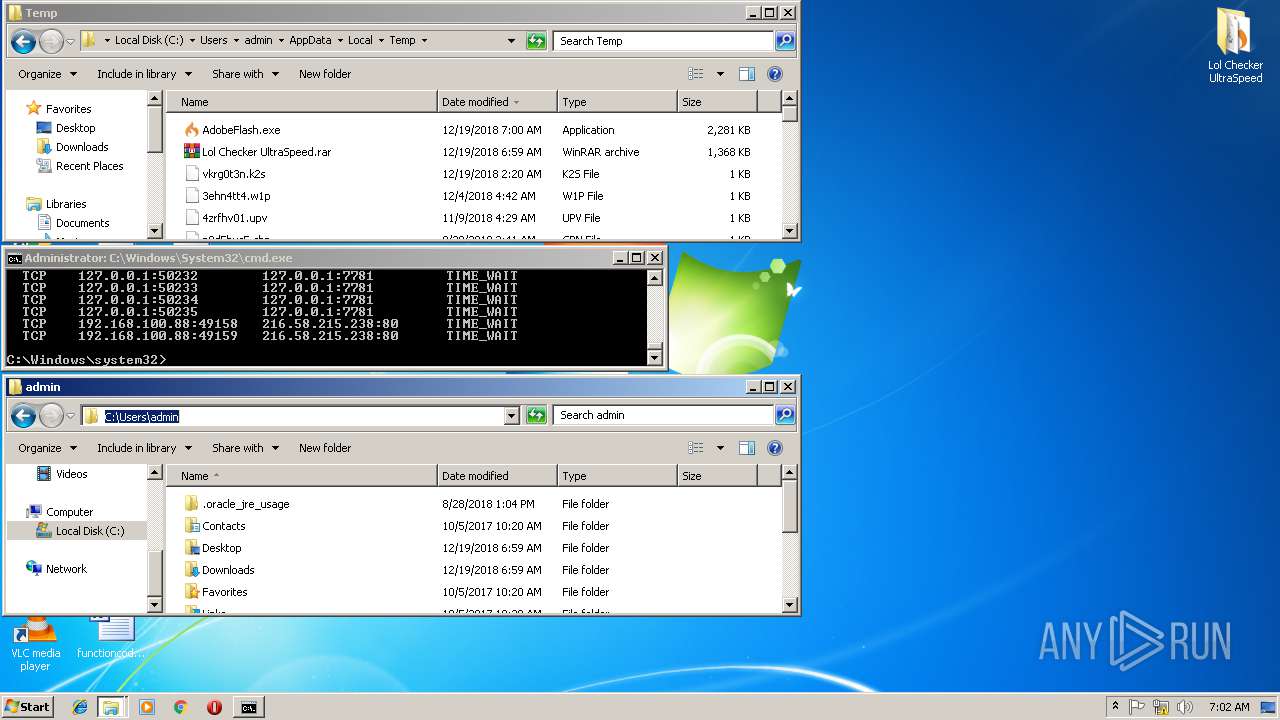
| File name: | Lol Checker UltraSpeed.rar |
| Full analysis: | https://app.any.run/tasks/7d552333-0d95-4537-8d8d-1274ec8d0cf3 |
| Verdict: | Malicious activity |
| Threats: | Quasar is a very popular RAT in the world thanks to its code being available in open-source. This malware can be used to control the victim’s computer remotely. |
| Analysis date: | December 19, 2018, 06:59:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 733E5CB097D684279B4F31A642367C61 |
| SHA1: | A45805C83ADB975D1D90F3F5AA78515375880AD5 |
| SHA256: | 658B9EEA082797716F2F4BF5BDA26AFFC0EC58900150A75147E227BCA72C0EBB |
| SSDEEP: | 24576:Xk2N8LW6o5Z+ixZm4/XqsaN/8zhv/nHklQFZnAOupbJfk2Volx0LZxljdN:fPLZ+14ism/8RfHklWZb69fNoH0vljdN |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 1376)
Application was dropped or rewritten from another process
- LolCheckerUltraSpeed.exe (PID: 3740)
- AdobeFlash.exe (PID: 3736)
QUASAR was detected
- Regasm.exe (PID: 3004)
Runs PING.EXE for delay simulation
- cmd.exe (PID: 2084)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3676)
- LolCheckerUltraSpeed.exe (PID: 3740)
Starts itself from another location
- LolCheckerUltraSpeed.exe (PID: 3740)
Creates files in the user directory
- Regasm.exe (PID: 3004)
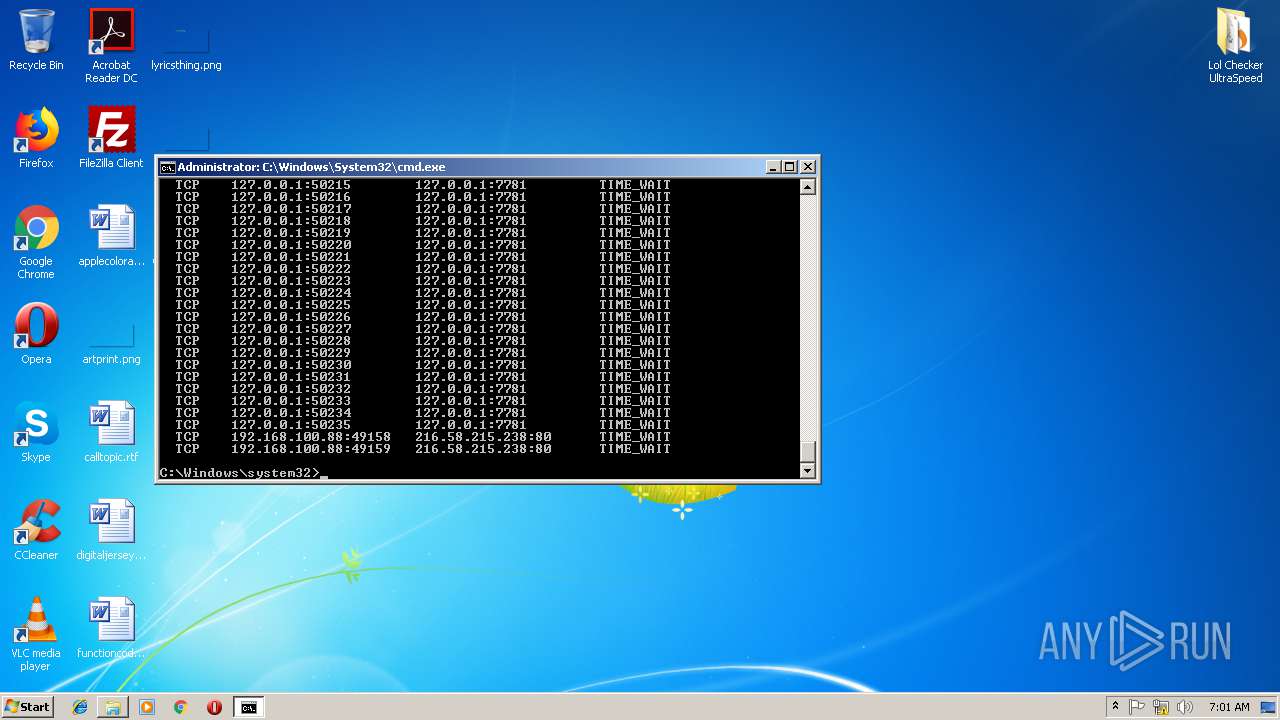
Checks for external IP
- Regasm.exe (PID: 3004)
Starts CMD.EXE for commands execution
- Regasm.exe (PID: 3004)
Starts application with an unusual extension
- cmd.exe (PID: 2084)
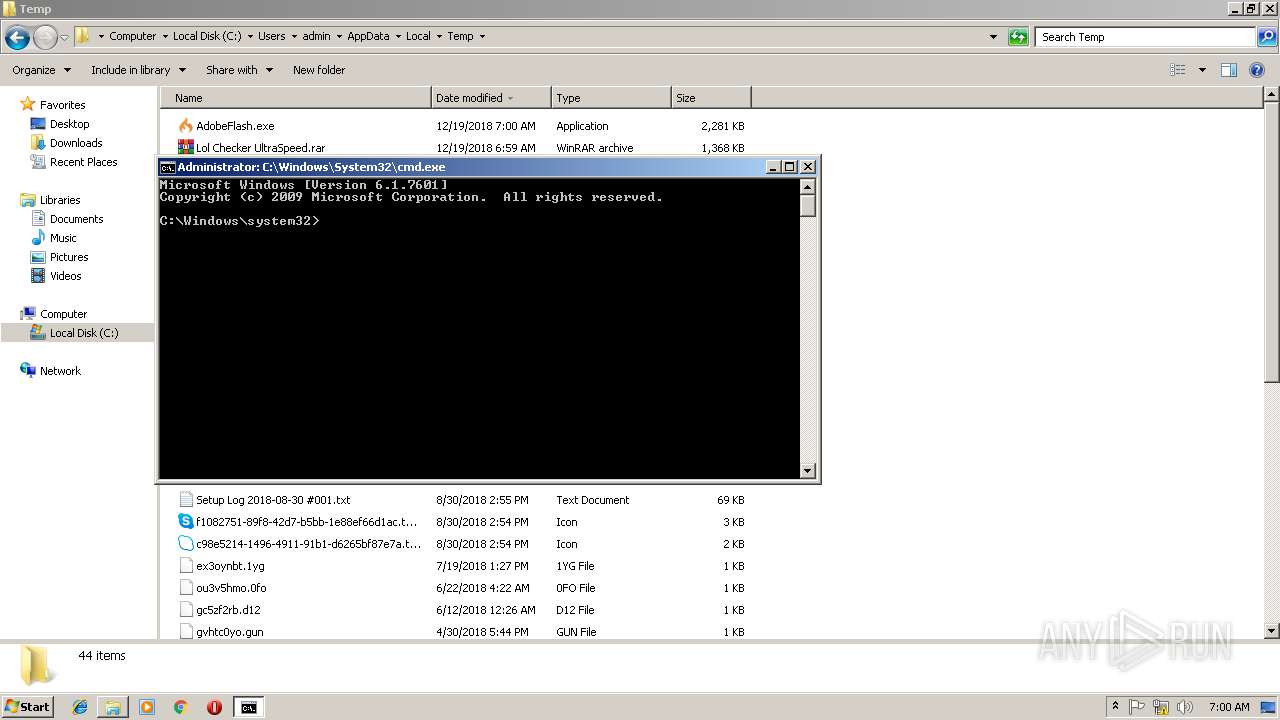
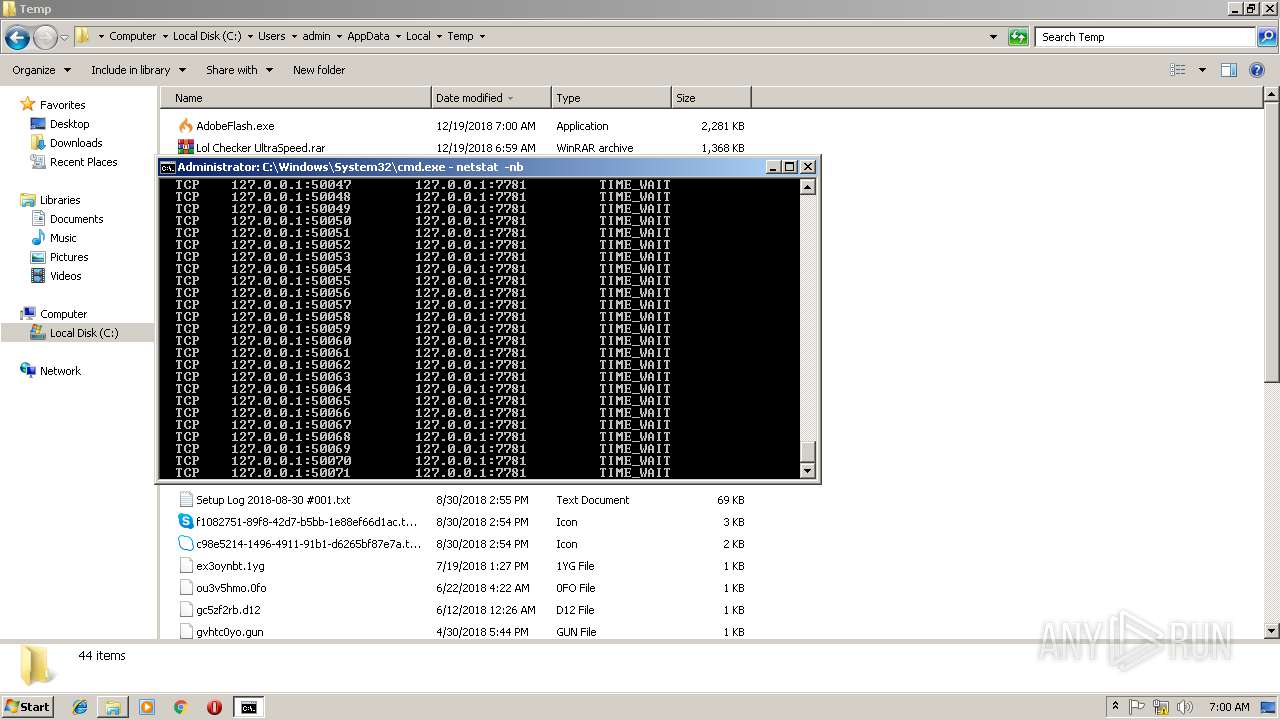
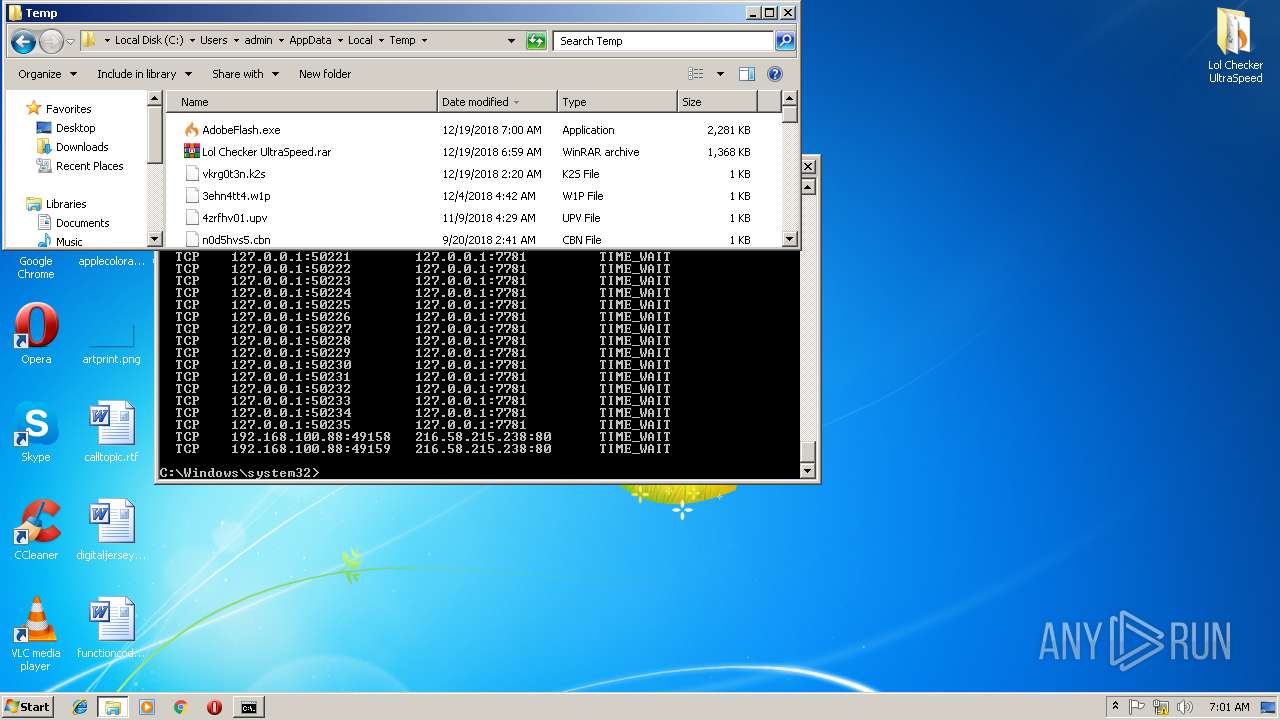
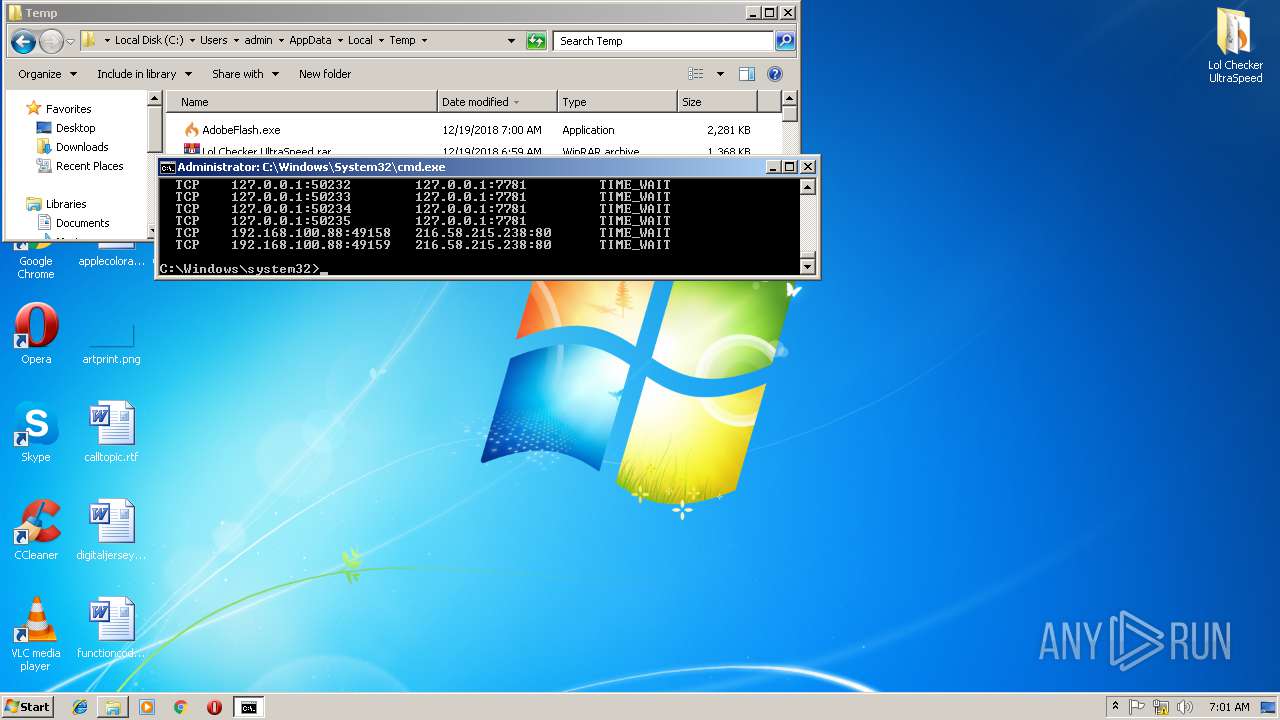
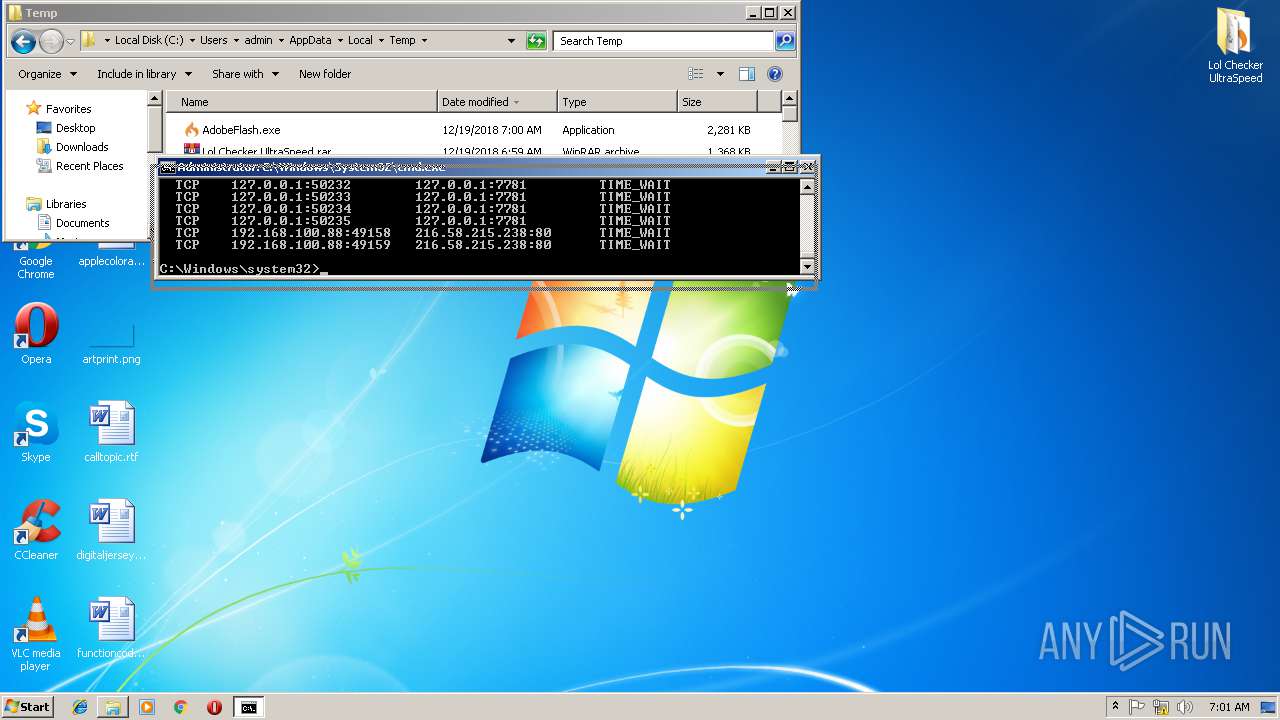
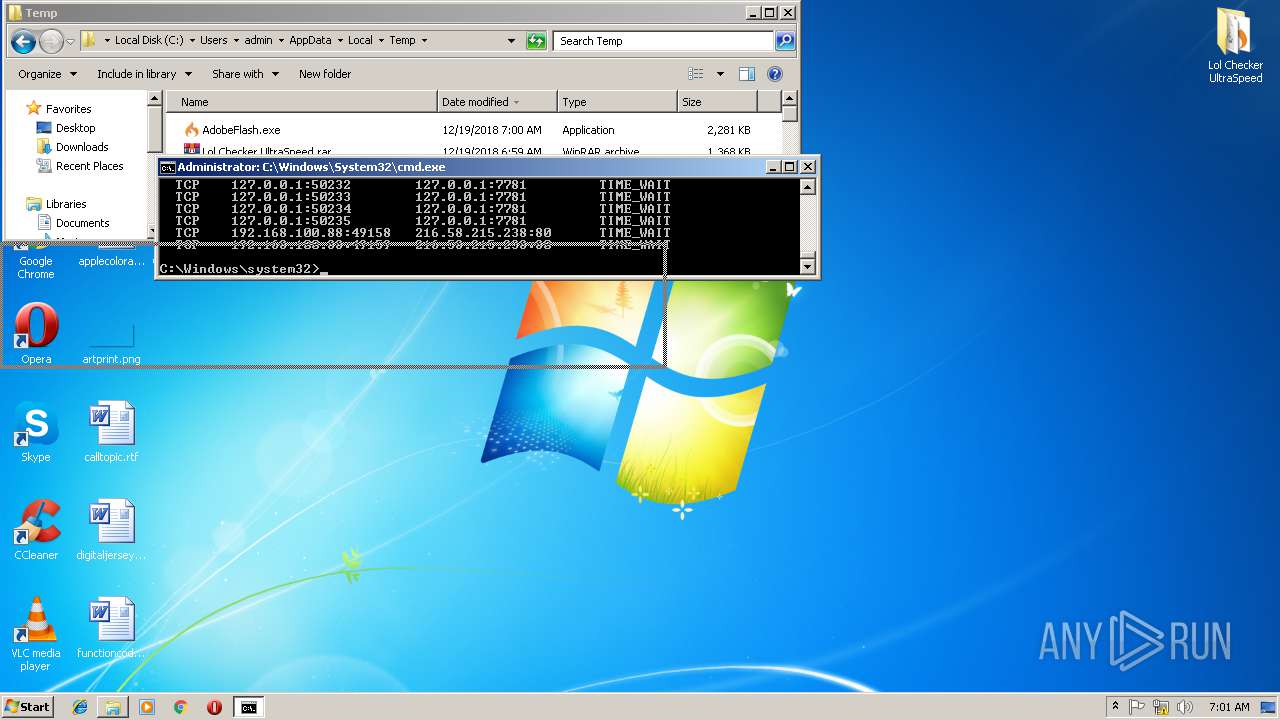
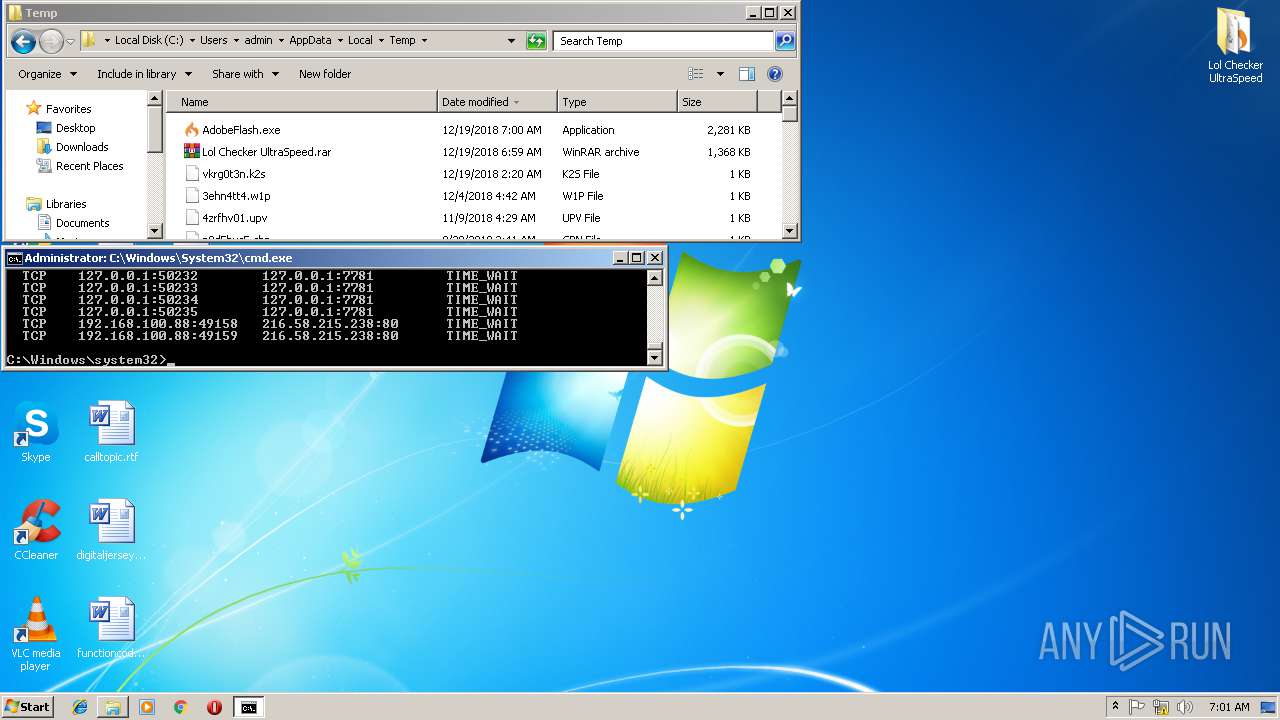
Uses NETSTAT.EXE to discover network connections
- cmd.exe (PID: 3072)
INFO
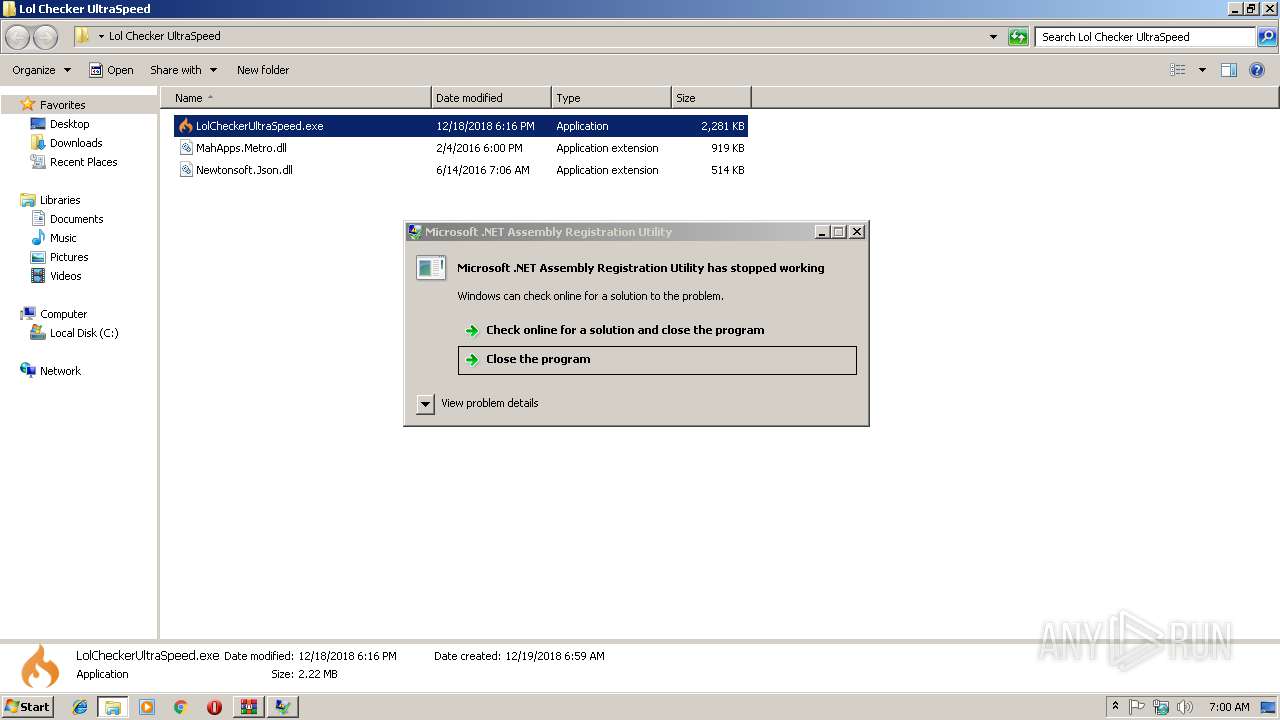
Application was crashed
- Regasm.exe (PID: 3004)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
57
Monitored processes
12
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1376 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe2_ Global\UsGthrCtrlFltPipeMssGthrPipe2 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1904 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\Regasm.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 4.6.1055.0 built by: NETFXREL2 Modules
| |||||||||||||||
| 2084 | cmd /c ""C:\Users\admin\AppData\Local\Temp\FRRqkHP51pY3.bat" " | C:\Windows\system32\cmd.exe | — | Regasm.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2372 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2740 | netstat -nb | C:\Windows\system32\NETSTAT.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Netstat Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2884 | chcp 65001 | C:\Windows\system32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Change CodePage Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3004 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\Regasm.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\Regasm.exe | AdobeFlash.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Assembly Registration Utility Exit code: 3762504530 Version: 4.6.1055.0 built by: NETFXREL2 Modules
| |||||||||||||||
| 3072 | "C:\Windows\System32\cmd.exe" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3324 | ping -n 10 localhost | C:\Windows\system32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3676 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Lol Checker UltraSpeed.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
1 599
Read events
1 558
Write events
41
Delete events
0
Modification events
| (PID) Process: | (3676) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3676) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3676) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3676) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Lol Checker UltraSpeed.rar | |||
| (PID) Process: | (3676) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3676) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3676) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3676) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3740) LolCheckerUltraSpeed.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\Run\CurrentVersion |
| Operation: | write | Name: | AdobeFlash.exe |
Value: C:\Users\admin\AppData\Local\Temp\AdobeFlash.exe | |||
| (PID) Process: | (3740) LolCheckerUltraSpeed.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
4
Suspicious files
1
Text files
1
Unknown types
0
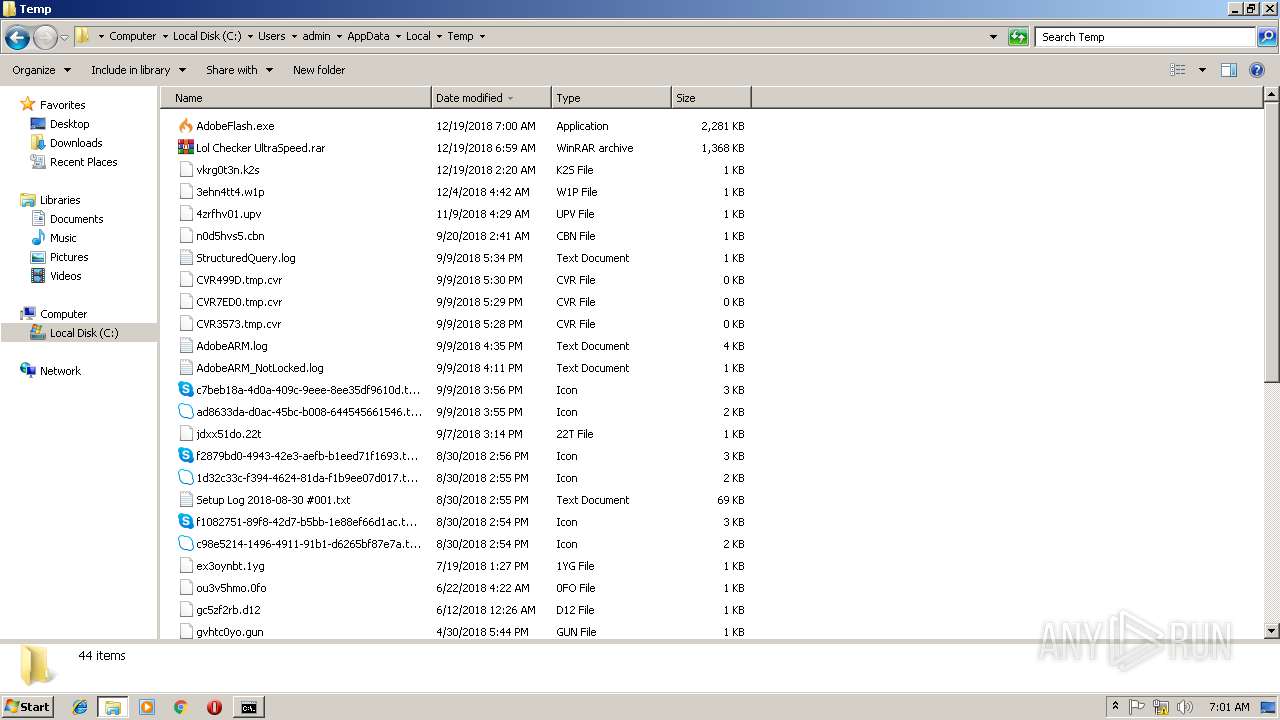
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3004 | Regasm.exe | C:\Users\admin\AppData\Local\Temp\FRRqkHP51pY3.bat | text | |
MD5:— | SHA256:— | |||
| 3676 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3676.29443\Lol Checker UltraSpeed\LolCheckerUltraSpeed.exe | executable | |
MD5:— | SHA256:— | |||
| 3676 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3676.29443\Lol Checker UltraSpeed\MahApps.Metro.dll | executable | |
MD5:FB1E8EEE84791CC015E043AB0CE32BBA | SHA256:0DE72DA4BC2D16D39C30368AF880D754FA0BD9745897652BA50213E589D265C5 | |||
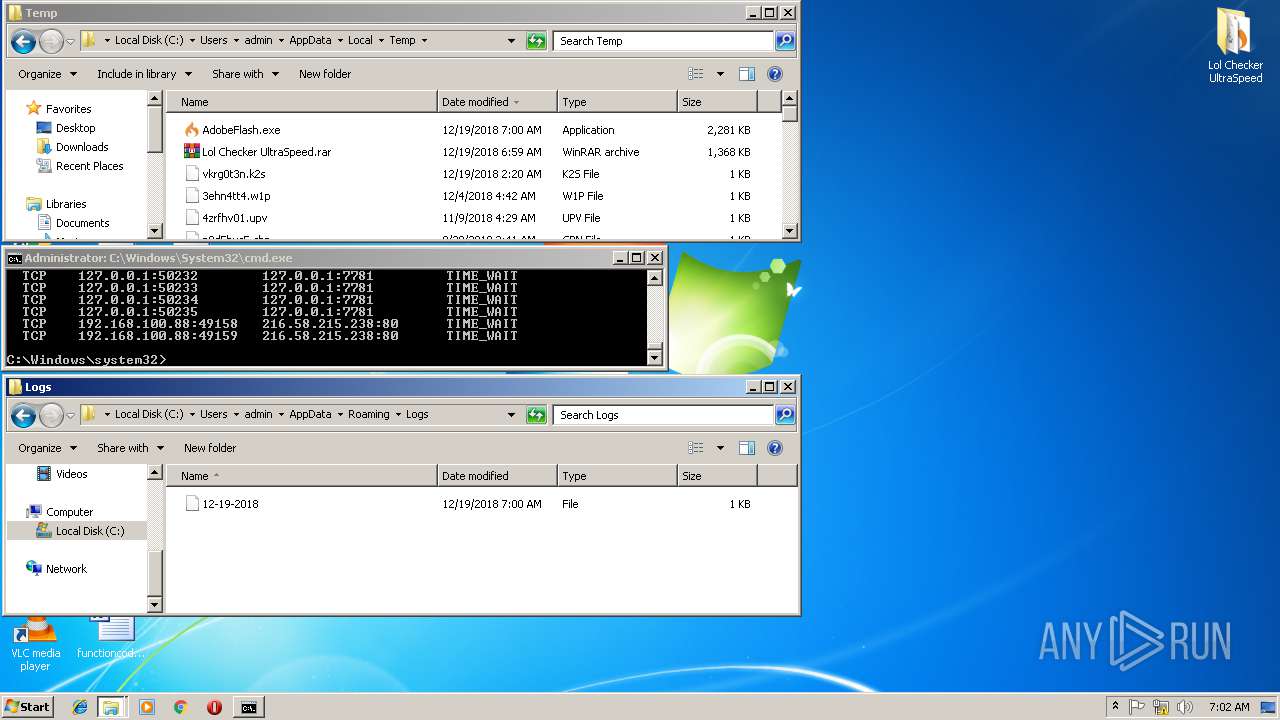
| 3004 | Regasm.exe | C:\Users\admin\AppData\Roaming\Logs\12-19-2018 | binary | |
MD5:— | SHA256:— | |||
| 3740 | LolCheckerUltraSpeed.exe | C:\Users\admin\AppData\Local\Temp\AdobeFlash.exe | executable | |
MD5:— | SHA256:— | |||
| 3676 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3676.29443\Lol Checker UltraSpeed\Newtonsoft.Json.dll | executable | |
MD5:C53737821B861D454D5248034C3C097C | SHA256:575E30F98E4EA42C9E516EDC8BBB29AD8B50B173A3E6B36B5BA39E133CCE9406 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
1
DNS requests
2
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3004 | Regasm.exe | GET | 200 | 185.194.141.58:80 | http://ip-api.com/json/ | DE | text | 310 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3004 | Regasm.exe | 185.194.141.58:80 | ip-api.com | netcup GmbH | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ip-api.com |
| malicious |
repmodz11.duckdns.org |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3004 | Regasm.exe | Potential Corporate Privacy Violation | ET POLICY External IP Lookup ip-api.com |
3004 | Regasm.exe | A Network Trojan was detected | MALWARE [PTsecurity] Quasar 1.3 RAT IP Lookup ip-api.com (HTTP headeer) |
1052 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
1 ETPRO signatures available at the full report
Process | Message |
|---|---|
LolCheckerUltraSpeed.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1391
|
LolCheckerUltraSpeed.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\identityauthority.cpp, line 278
|
LolCheckerUltraSpeed.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1391
|
LolCheckerUltraSpeed.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\identityauthority.cpp, line 278
|
LolCheckerUltraSpeed.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1391
|
LolCheckerUltraSpeed.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\identityauthority.cpp, line 278
|
LolCheckerUltraSpeed.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1391
|
LolCheckerUltraSpeed.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\identityauthority.cpp, line 278
|
AdobeFlash.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1391
|
AdobeFlash.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\identityauthority.cpp, line 278
|