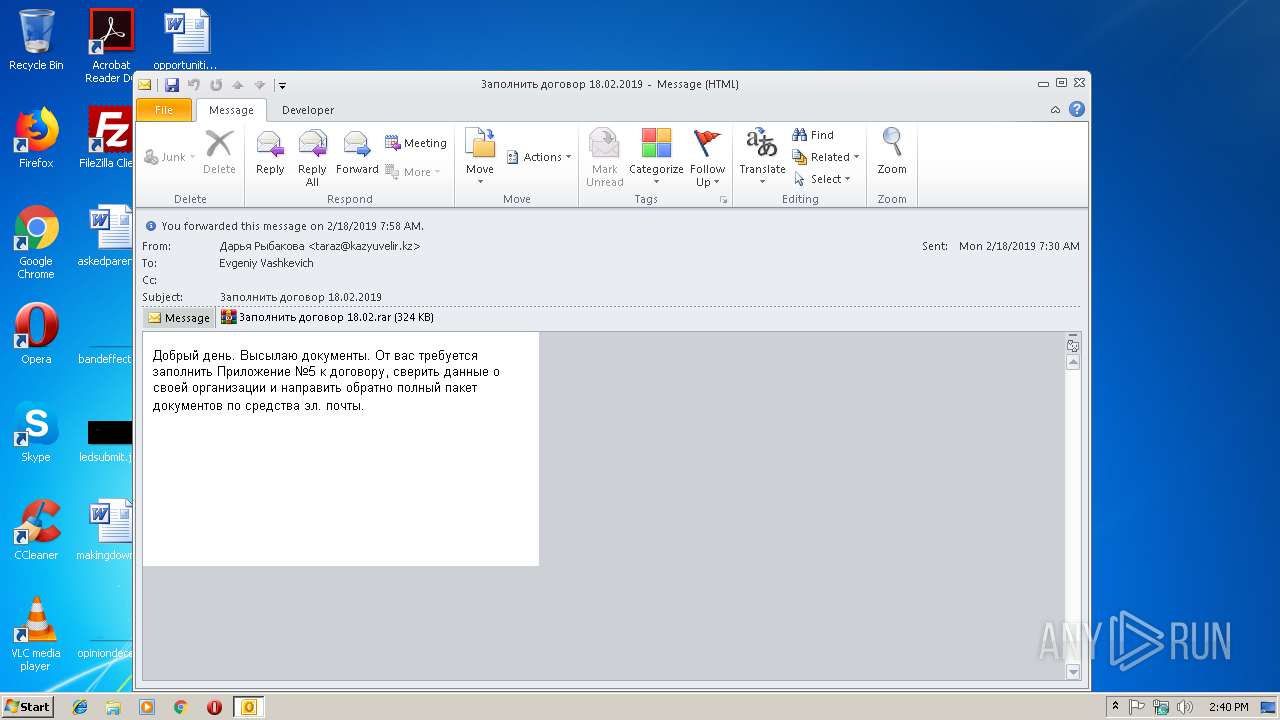
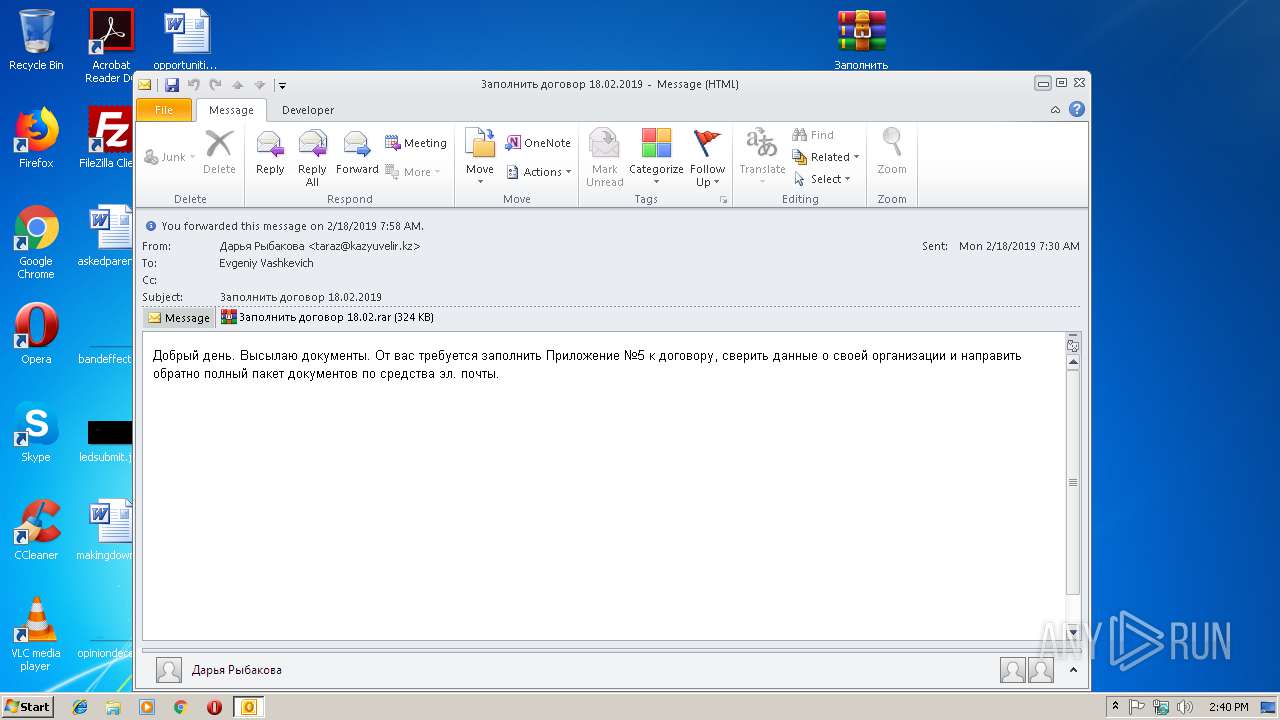
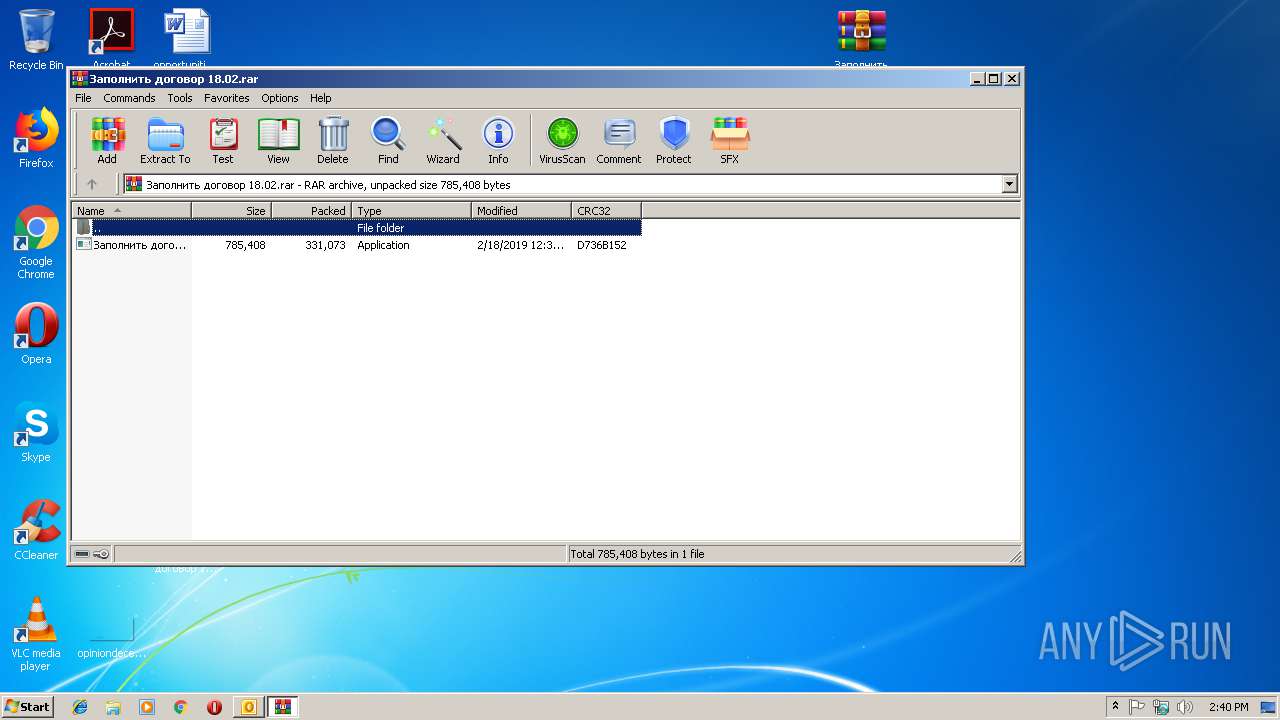
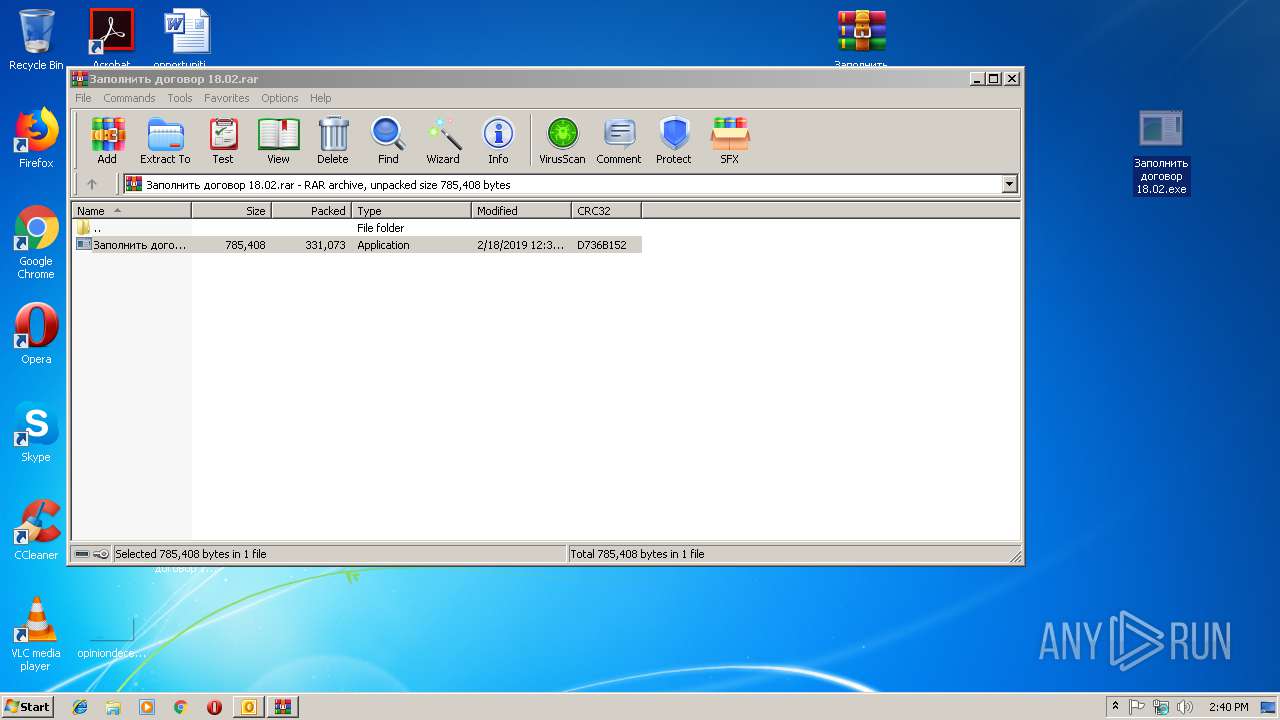
| File name: | Заполнить договор 18.02.2019.msg |
| Full analysis: | https://app.any.run/tasks/ff1995ce-9eb1-4c41-89d8-ea028880a923 |
| Verdict: | Malicious activity |
| Threats: | Ursnif is a banking Trojan that usually infects corporate victims. It is based on an old malware but was substantially updated over the years and became quite powerful. Today Ursnif is one of the most widely spread banking Trojans in the world. |
| Analysis date: | February 18, 2019, 14:39:43 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | 527F08E3E4B9B5E578758CC7AC2DEDFE |
| SHA1: | 785F6A7C5A6BAF52E45DCA7043BEE0B578CE8666 |
| SHA256: | 657B9FE398D411AFC789637DFE0F27F653D028E063EC579F3F0BDC3718A4B250 |
| SSDEEP: | 6144:1b0Vb/Fg01XYflKxGU7cZ/z4kVzhPG8ha0PpLObAsjwHaxOI0:0b/m01KlKxyZ/EkVzZRha4LRN/I |
MALICIOUS
Application was dropped or rewritten from another process
- Заполнить договор 18.02.exe (PID: 3328)
URSNIF was detected
- rundll32.exe (PID: 2956)
Loads the Task Scheduler COM API
- Заполнить договор 18.02.exe (PID: 3328)
SUSPICIOUS
Connects to unusual port
- rundll32.exe (PID: 2956)
Creates files in the program directory
- Заполнить договор 18.02.exe (PID: 3328)
Executable content was dropped or overwritten
- Заполнить договор 18.02.exe (PID: 3328)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 3096)
Creates files in the user directory
- OUTLOOK.EXE (PID: 3096)
INFO
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 3096)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
41
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2564 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Заполнить договор 18.02.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2956 | rundll32.exe "C:\ProgramData\2401bf603c90\2702bc633f93.dat",DllGetClassObject root | C:\Windows\system32\rundll32.exe | taskeng.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3096 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\Desktop\Заполнить договор 18.02.2019.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 3328 | "C:\Users\admin\Desktop\Заполнить договор 18.02.exe" | C:\Users\admin\Desktop\Заполнить договор 18.02.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
1 594
Read events
1 160
Write events
415
Delete events
19
Modification events
| (PID) Process: | (3096) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3096) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3096) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\Resiliency\StartupItems |
| Operation: | write | Name: | 0$0 |
Value: 30243000180C0000010000000000000000000000 | |||
| (PID) Process: | (3096) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook |
| Operation: | write | Name: | MTTT |
Value: 180C0000EE52E7D397C7D40100000000 | |||
| (PID) Process: | (3096) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionNumber |
Value: 0 | |||
| (PID) Process: | (3096) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionDate |
Value: 219915360 | |||
| (PID) Process: | (3096) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\0a0d020000000000c000000000000046 |
| Operation: | write | Name: | 00030429 |
Value: 03000000 | |||
| (PID) Process: | (3096) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | {ED475418-B0D6-11D2-8C3B-00104B2A6676} |
Value: | |||
| (PID) Process: | (3096) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | LastChangeVer |
Value: 1200000000000000 | |||
| (PID) Process: | (3096) OUTLOOK.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109A10090400000000000F01FEC\Usage |
| Operation: | write | Name: | OutlookMAPI2Intl_1033 |
Value: 1313996821 | |||
Executable files
2
Suspicious files
1
Text files
24
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3096 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR6821.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2564 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2564.33647\Заполнить договор 18.02.exe | — | |
MD5:— | SHA256:— | |||
| 2956 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\1D0.tmp | — | |
MD5:— | SHA256:— | |||
| 2956 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\amnibdaadnffjjnd | — | |
MD5:— | SHA256:— | |||
| 2956 | rundll32.exe | C:\Users\admin\Desktop\Заполнить договор 18.02.exe | — | |
MD5:— | SHA256:— | |||
| 2956 | rundll32.exe | C:\Users\admin\Desktop\gokdfgnlodhoodic | — | |
MD5:— | SHA256:— | |||
| 3328 | Заполнить договор 18.02.exe | C:\ProgramData\2401bf603c90\2702bc633f93.dat | executable | |
MD5:— | SHA256:— | |||
| 3328 | Заполнить договор 18.02.exe | C:\Users\admin\AppData\Local\Temp\1D0.tmp | executable | |
MD5:— | SHA256:— | |||
| 3096 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\ELD3374F\Заполнить договор 18 02.rar | compressed | |
MD5:— | SHA256:— | |||
| 3096 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_Calendar_2_BDAACACA878C5642927424A0A612F4FD.dat | xml | |
MD5:B21ED3BD946332FF6EBC41A87776C6BB | SHA256:B1AAC4E817CD10670B785EF8E5523C4A883F44138E50486987DC73054A46F6F4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
20
DNS requests
4
Threats
31
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3096 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
2956 | rundll32.exe | GET | 200 | 178.62.9.171:80 | http://myip.ru/index_small.php | GB | html | 325 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3096 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
2956 | rundll32.exe | 178.62.9.171:80 | myip.ru | Digital Ocean, Inc. | GB | malicious |
2956 | rundll32.exe | 217.31.161.55:8443 | — | Bahnhof Internet AB | SE | suspicious |
2956 | rundll32.exe | 145.239.1.97:443 | — | OVH SAS | DE | suspicious |
2956 | rundll32.exe | 81.84.174.240:19001 | — | Nos Comunicacoes, S.A. | PT | suspicious |
2956 | rundll32.exe | 178.62.52.233:9001 | — | Digital Ocean, Inc. | GB | suspicious |
2956 | rundll32.exe | 192.155.83.101:9001 | — | Linode, LLC | US | suspicious |
2956 | rundll32.exe | 159.69.2.239:443 | — | — | US | suspicious |
2956 | rundll32.exe | 212.8.243.229:9001 | — | Sivin Consult Ltd | RU | suspicious |
2956 | rundll32.exe | 81.17.31.210:3516 | — | Private Layer INC | CH | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
myip.ru |
| unknown |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2956 | rundll32.exe | Potential Corporate Privacy Violation | ET POLICY myip.ru IP lookup |
2956 | rundll32.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 354 |
2956 | rundll32.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 143 |
2956 | rundll32.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 600 |
2956 | rundll32.exe | Misc activity | ET POLICY TLS possible TOR SSL traffic |
2956 | rundll32.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 208 |
2956 | rundll32.exe | Misc activity | ET POLICY TLS possible TOR SSL traffic |
2956 | rundll32.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 258 |
2956 | rundll32.exe | Misc activity | ET POLICY TLS possible TOR SSL traffic |
2956 | rundll32.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 163 |