| File name: | setup.ps1 |
| Full analysis: | https://app.any.run/tasks/7aa441ba-83b8-4d4b-a127-7509d2fbdc78 |
| Verdict: | Malicious activity |
| Threats: | AsyncRAT is a RAT that can monitor and remotely control infected systems. This malware was introduced on Github as a legitimate open-source remote administration software, but hackers use it for its many powerful malicious functions. |
| Analysis date: | September 03, 2024, 14:03:06 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | Unicode text, UTF-16, little-endian text, with very long lines (32767), with no line terminators |
| MD5: | 8743F6A63DCE2B0D13AC0D18223B9C30 |
| SHA1: | 396366A412608306F9BC0FCC99DDBCA6C9F80572 |
| SHA256: | 64F9AEEC01269185CFE6FF0A80D9D55025E5905751A779EB8955C0A181DF2C3A |
| SSDEEP: | 12288:BYmb0rrxpjtNSlK0J86cdd1Y8AhhTguYOgmhPYjyC5HLZdZz9cDYVBKiE2NykAEK:BYmb0nxpJNSlRC6ed67hhUu5gm6f7dZi |
MALICIOUS
ASYNCRAT has been detected (SURICATA)
- powershell.exe (PID: 6196)
SUSPICIOUS
Contacting a server suspected of hosting an CnC
- powershell.exe (PID: 6196)
Connects to unusual port
- powershell.exe (PID: 6196)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 6196)
Executable content was dropped or overwritten
- csc.exe (PID: 1920)
- csc.exe (PID: 2892)
Checks for external IP
- powershell.exe (PID: 6196)
INFO
Checks supported languages
- cvtres.exe (PID: 6752)
- csc.exe (PID: 1920)
- csc.exe (PID: 2892)
- cvtres.exe (PID: 2092)
Create files in a temporary directory
- csc.exe (PID: 1920)
- cvtres.exe (PID: 6752)
- csc.exe (PID: 2892)
- cvtres.exe (PID: 2092)
Reads the machine GUID from the registry
- csc.exe (PID: 1920)
- csc.exe (PID: 2892)
The process uses the downloaded file
- powershell.exe (PID: 6196)
Gets data length (POWERSHELL)
- powershell.exe (PID: 6196)
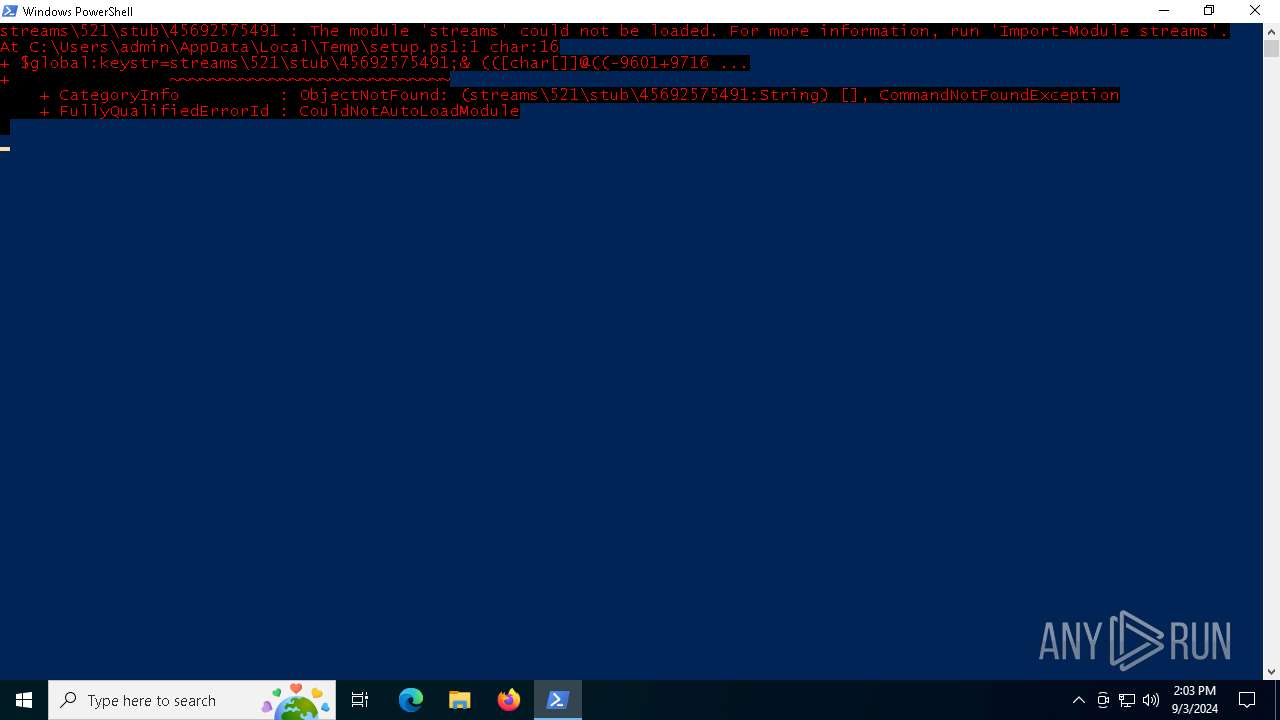
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6196)
Disables trace logs
- powershell.exe (PID: 6196)
Checks proxy server information
- powershell.exe (PID: 6196)
- slui.exe (PID: 6292)
Found Base64 encoded access to Marshal class via PowerShell (YARA)
- powershell.exe (PID: 6196)
Found Base64 encoded file access via PowerShell (YARA)
- powershell.exe (PID: 6196)
Found Base64 encoded access to Windows Identity via PowerShell (YARA)
- powershell.exe (PID: 6196)
Found Base64 encoded access to processes via PowerShell (YARA)
- powershell.exe (PID: 6196)
Potential remote process memory writing (Base64 Encoded 'WriteProcessMemory')
- powershell.exe (PID: 6196)
Found Base64 encoded reflection usage via PowerShell (YARA)
- powershell.exe (PID: 6196)
Found Base64 encoded text manipulation via PowerShell (YARA)
- powershell.exe (PID: 6196)
Found Base64 encoded network access via PowerShell (YARA)
- powershell.exe (PID: 6196)
Reads the software policy settings
- slui.exe (PID: 2612)
- slui.exe (PID: 6292)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .txt | | | Text - UTF-16 (LE) encoded (66.6) |
|---|---|---|
| .mp3 | | | MP3 audio (33.3) |
Total processes
139
Monitored processes
9
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1920 | "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\ytwtx5w3.cmdline" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 2092 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES201E.tmp" "c:\Users\admin\AppData\Local\Temp\CSC95ABE7EB2A9A4A659211383E6987B71.TMP" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.32.31326.0 Modules
| |||||||||||||||
| 2612 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2892 | "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\ggeudceh.cmdline" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 3028 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6152 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6196 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" C:\Users\admin\AppData\Local\Temp\setup.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6292 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6752 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RESC1C2.tmp" "c:\Users\admin\AppData\Local\Temp\CSCF3E4D80287EF47D49FFFAE37E2C8857C.TMP" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.32.31326.0 Modules
| |||||||||||||||
Total events
15 744
Read events
15 722
Write events
22
Delete events
0
Modification events
| (PID) Process: | (6196) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6196) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6196) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6196) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6196) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6196) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6196) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (6196) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (6196) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (6196) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
Executable files
2
Suspicious files
5
Text files
10
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6196 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\WL3A7BNZHI3Q6QO9EUNR.temp | binary | |
MD5:2944FB7138FDE2DE9D250BA3550095F3 | SHA256:AA4483787BAB6B1DC26FA8A27B9A5815D23735F9445CC1D801F277B10DA95DCC | |||
| 6196 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_vsyfzayg.mac.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6196 | powershell.exe | C:\Users\admin\AppData\Local\Temp\ytwtx5w3.cmdline | text | |
MD5:FAFFEAC288748E58DB3F0F8313A3CFF0 | SHA256:DDCED7E1DD1957CC547E36492C6A89D23A929C363C95551E1A1ABCC114B522E6 | |||
| 6196 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_r2fwxi2f.bnq.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6196 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF12a4f3.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 6752 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RESC1C2.tmp | binary | |
MD5:D2A6AA916A237789C73A5C6DAC8C6BF2 | SHA256:7F2611473CB197DFF6316284FC2ABDA450597AEDE4B71FF062013CFD20B216A6 | |||
| 2892 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSC95ABE7EB2A9A4A659211383E6987B71.TMP | res | |
MD5:9C214166103DCA5BD956905E15B7C6B6 | SHA256:4317391D5EA9FBE8298EB89430ED3B9F7A73F6915DDAD8B7AA3D91870F8014F2 | |||
| 6196 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_isb03yjf.xsp.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2892 | csc.exe | C:\Users\admin\AppData\Local\Temp\ggeudceh.dll | executable | |
MD5:B4471B16B4B94DA03A73EBE542CF7622 | SHA256:B3C653069CB7710EB05F940EEA0BA3040C2B26F162AA10EA2CF7A8E477EB20DF | |||
| 2892 | csc.exe | C:\Users\admin\AppData\Local\Temp\ggeudceh.out | text | |
MD5:377716CC2592DDCB6546C9F64C81DDBC | SHA256:DCE41205654A2D6B039572A7B527FD7C29AECAA16971FD6BC14184F22312F929 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
47
DNS requests
23
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7160 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7160 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3424 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6288 | RUXIMICS.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6056 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6056 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6196 | powershell.exe | 193.29.59.154:18414 | 6gjq2xnexz5j59a.top | IP-Projects GmbH & Co. KG | DE | unknown |
6196 | powershell.exe | 104.26.13.205:443 | api.ipify.org | CLOUDFLARENET | US | shared |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3424 | svchost.exe | 40.126.32.140:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
6gjq2xnexz5j59a.top |
| unknown |
api.ipify.org |
| shared |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6196 | powershell.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
6196 | powershell.exe | Domain Observed Used for C2 Detected | ET MALWARE Generic AsyncRAT Style SSL Cert |
2256 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
6196 | powershell.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
6196 | powershell.exe | Malware Command and Control Activity Detected | REMOTE [ANY.RUN] AsyncRAT Successful Connection |
1 ETPRO signatures available at the full report