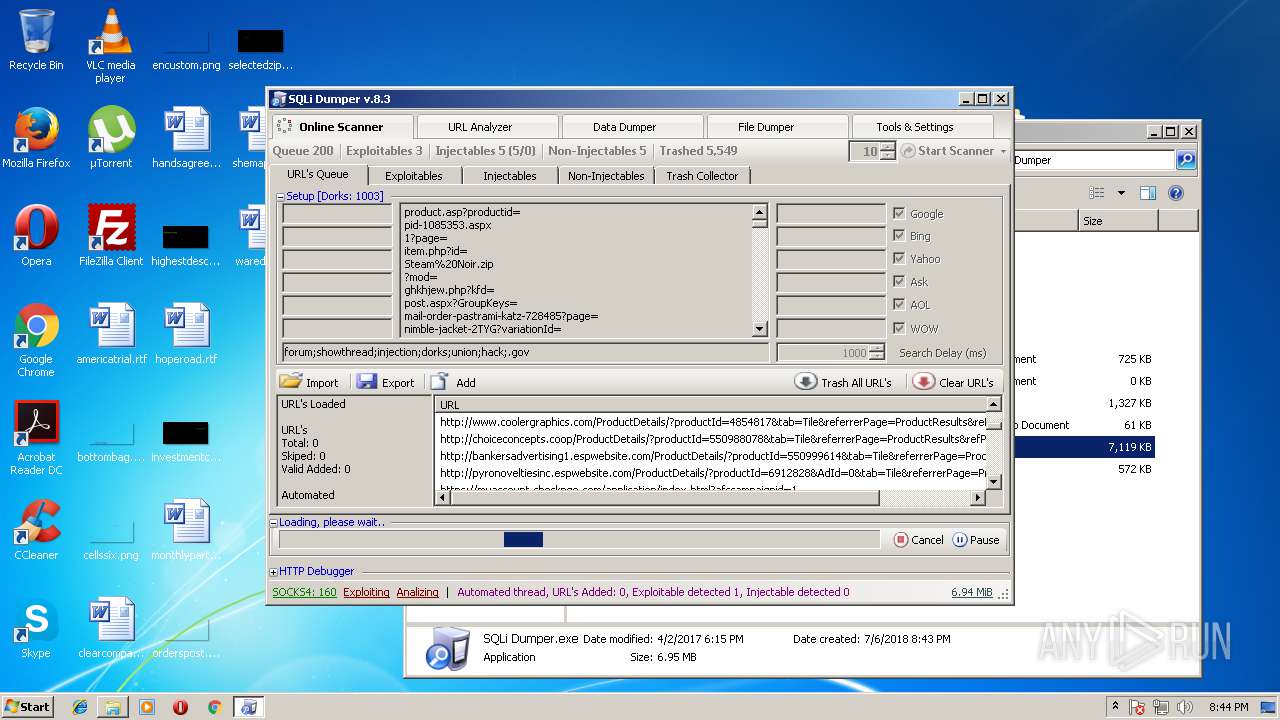
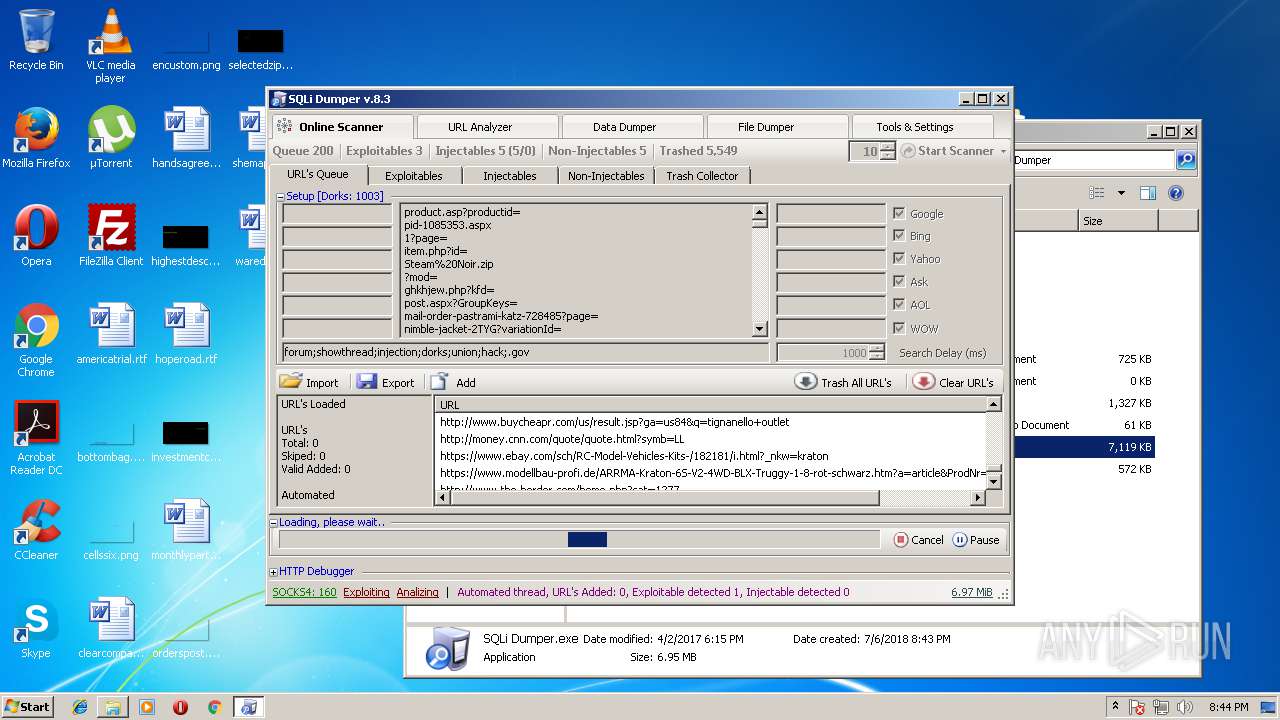
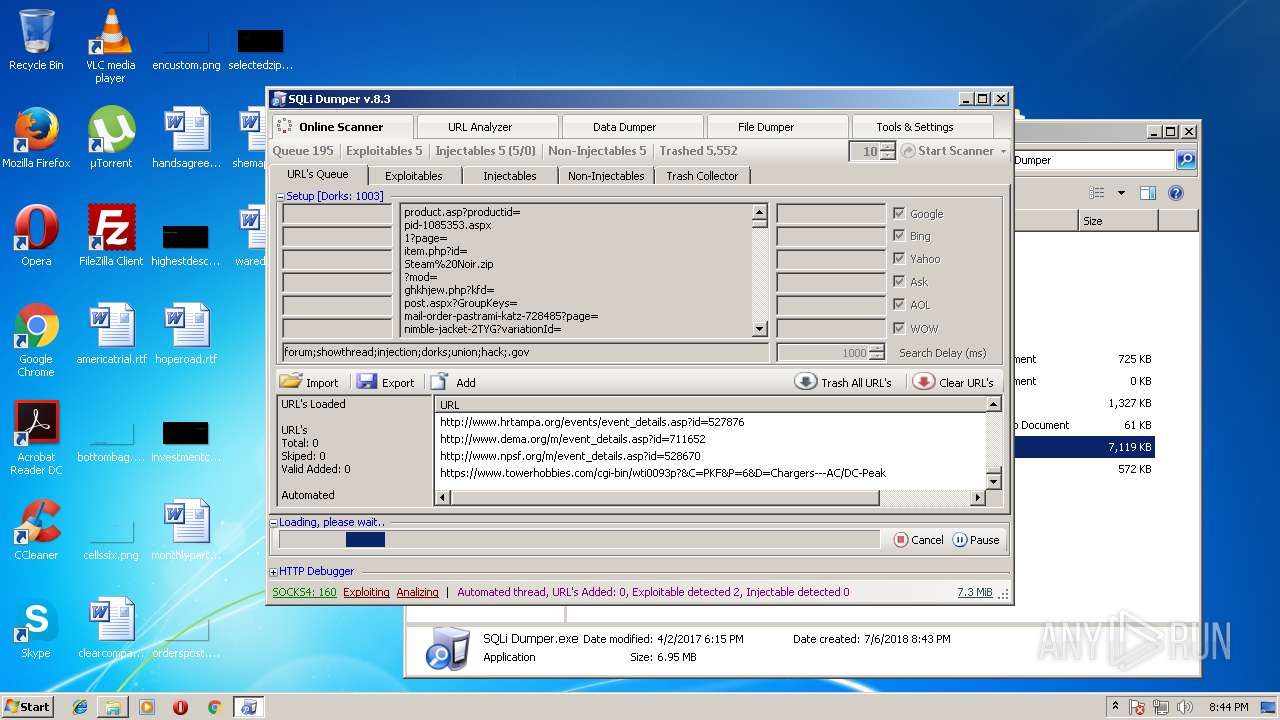
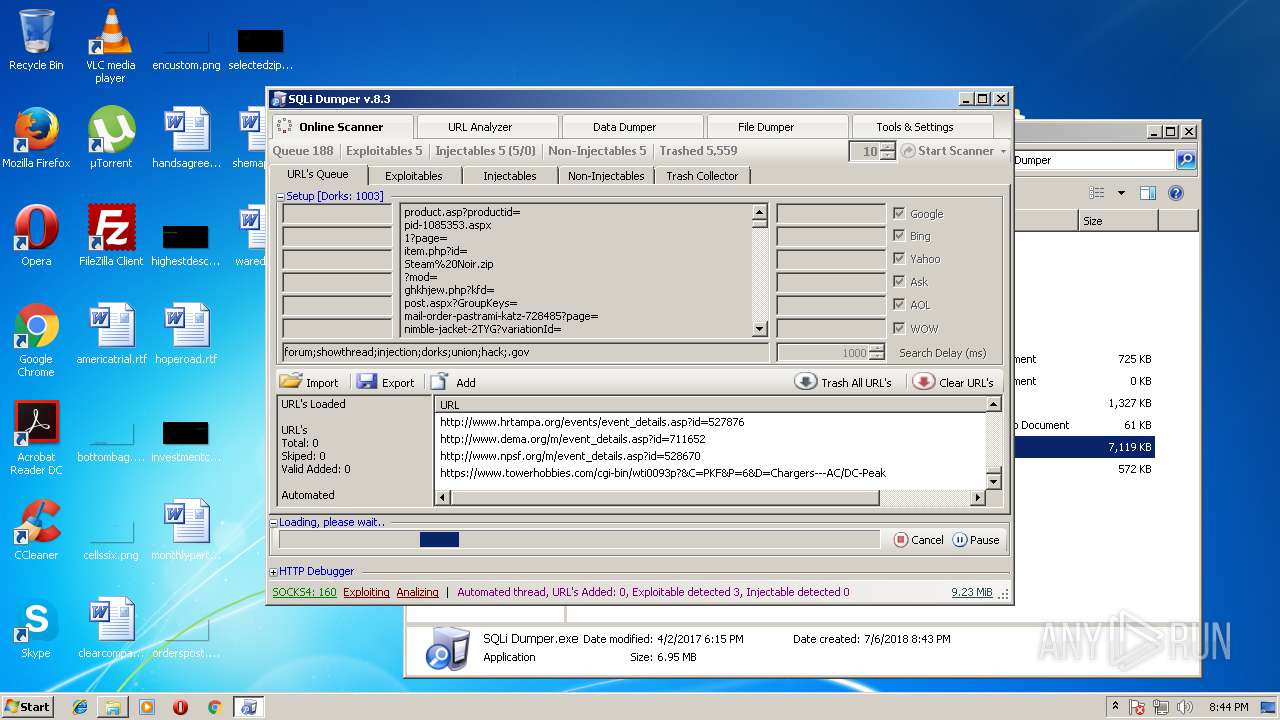
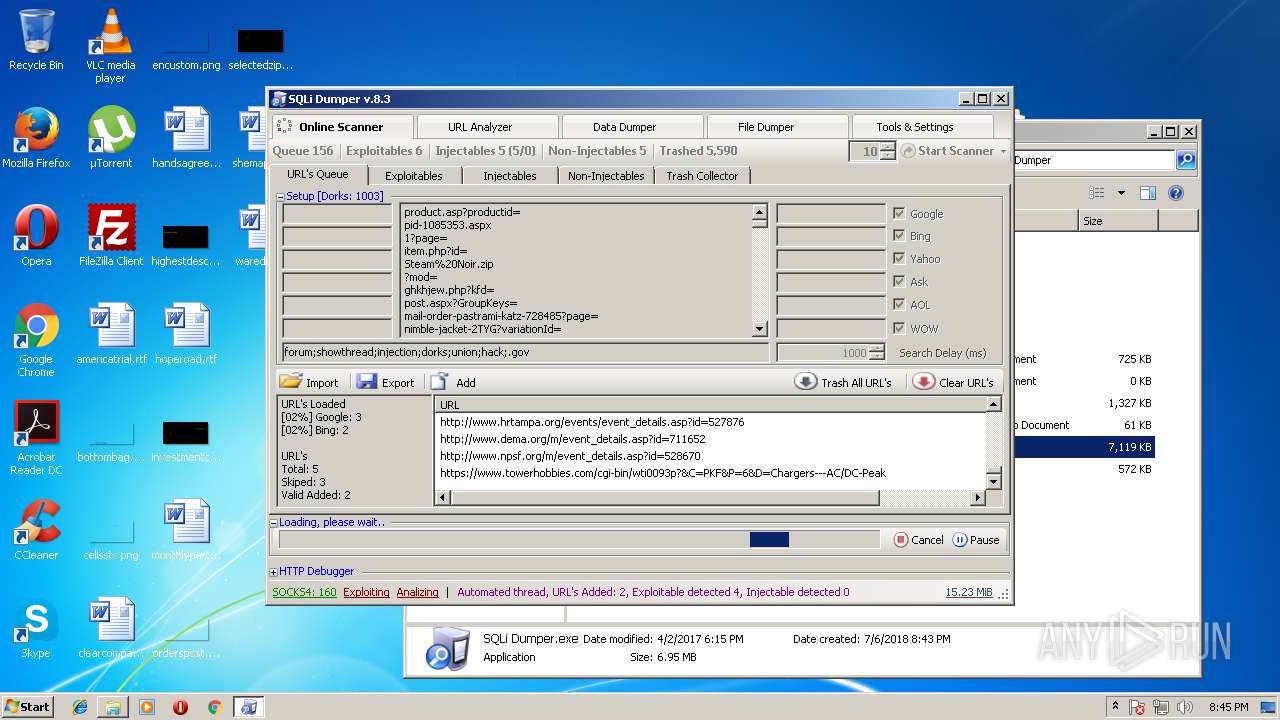
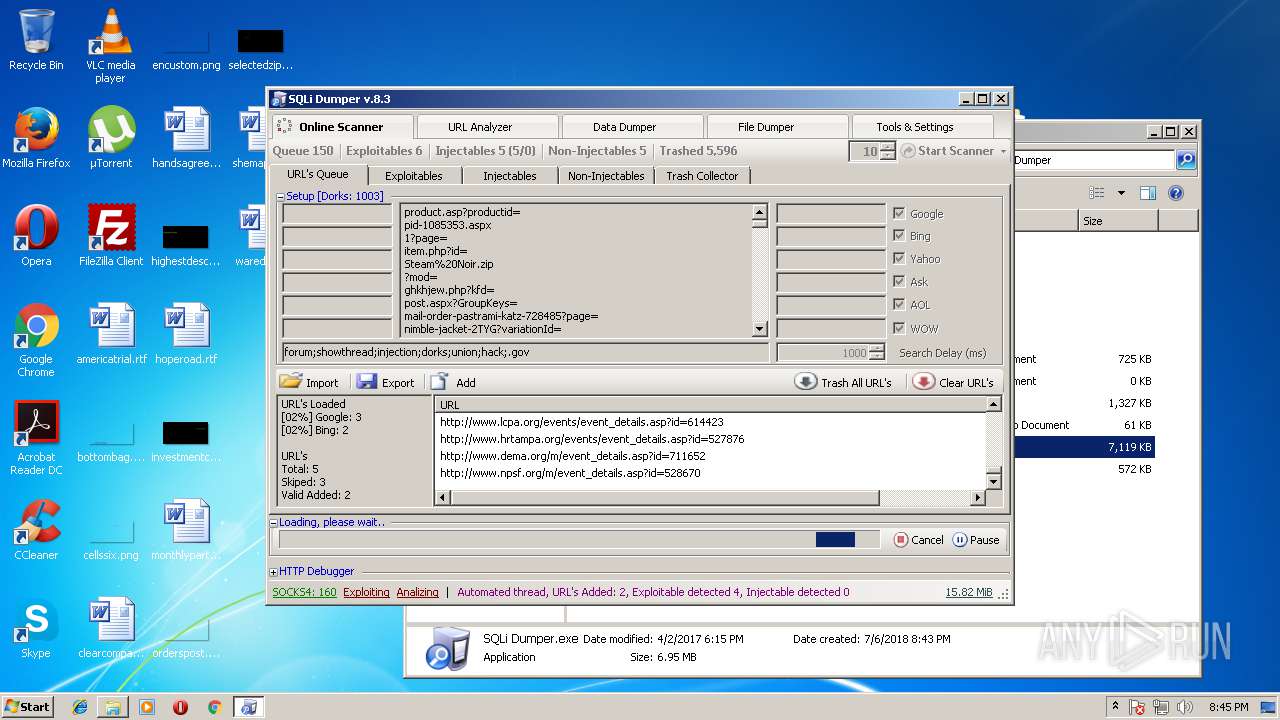
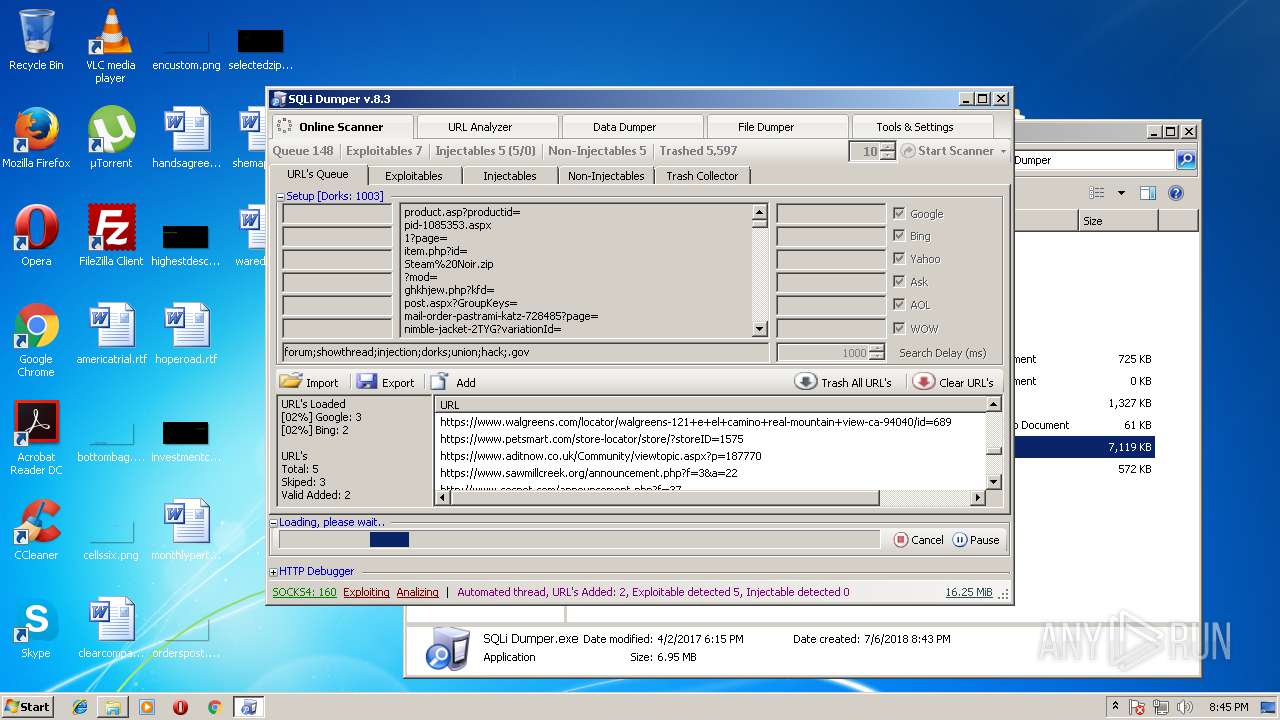
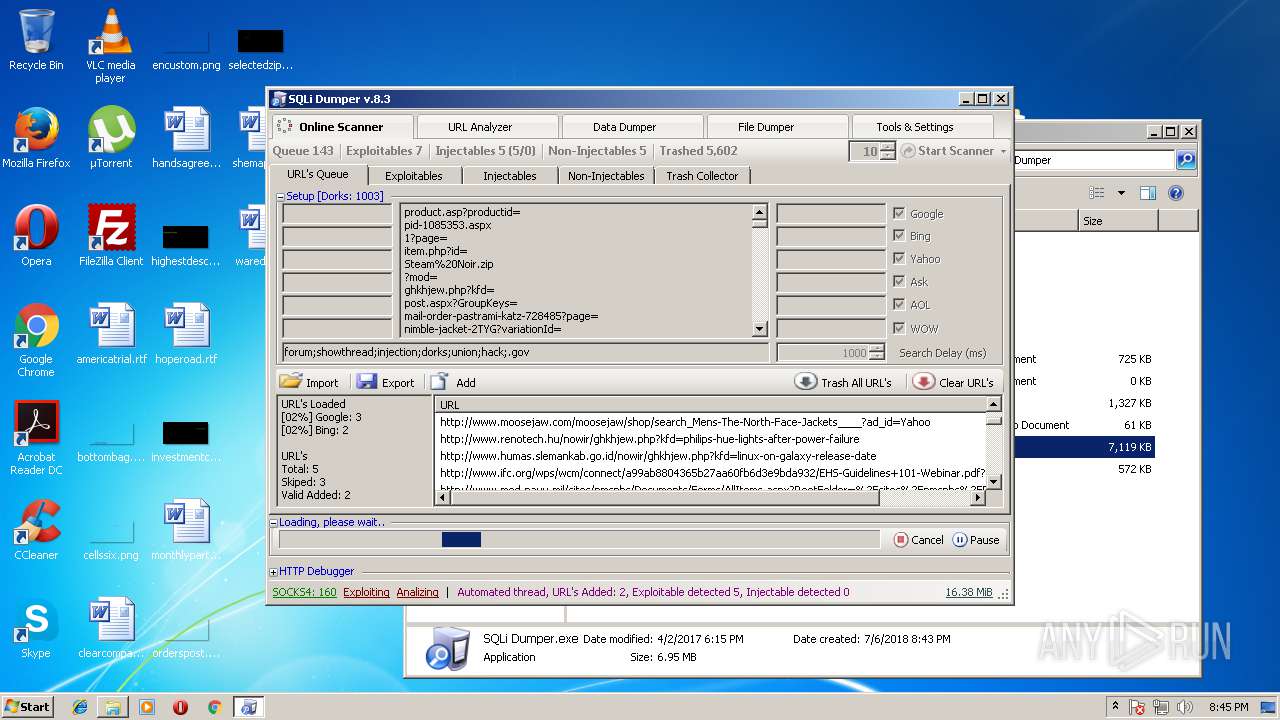
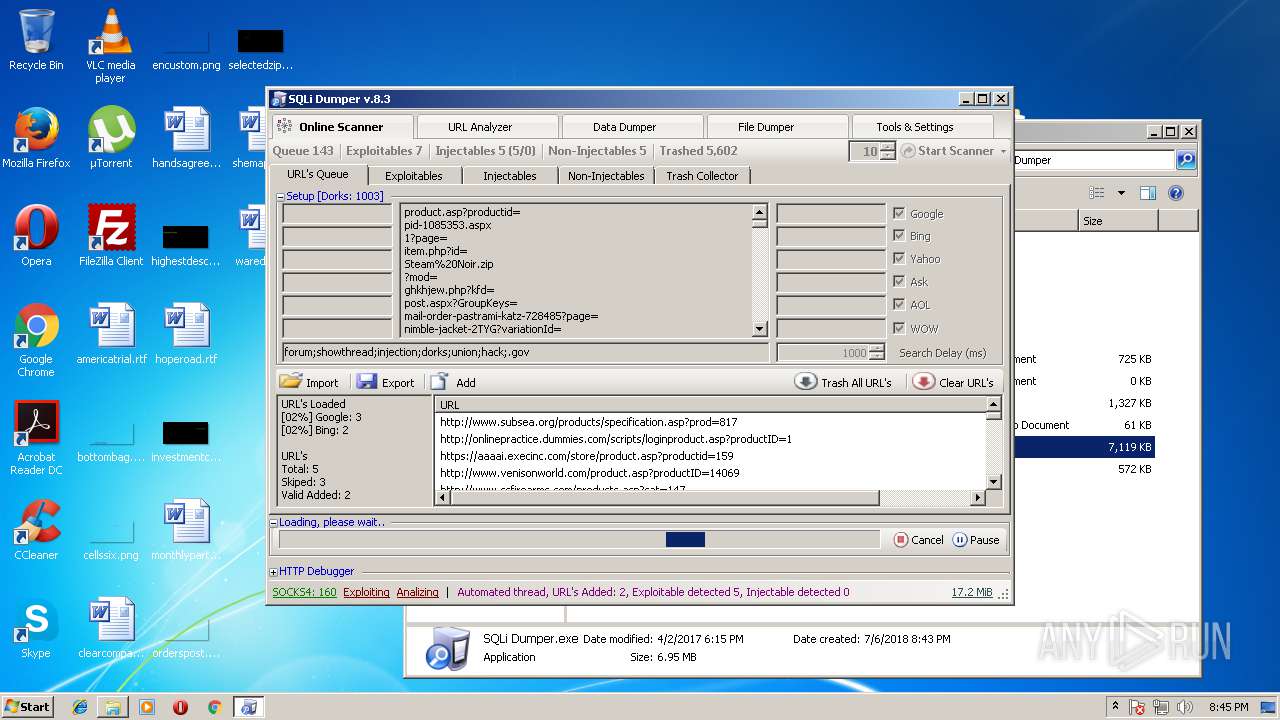
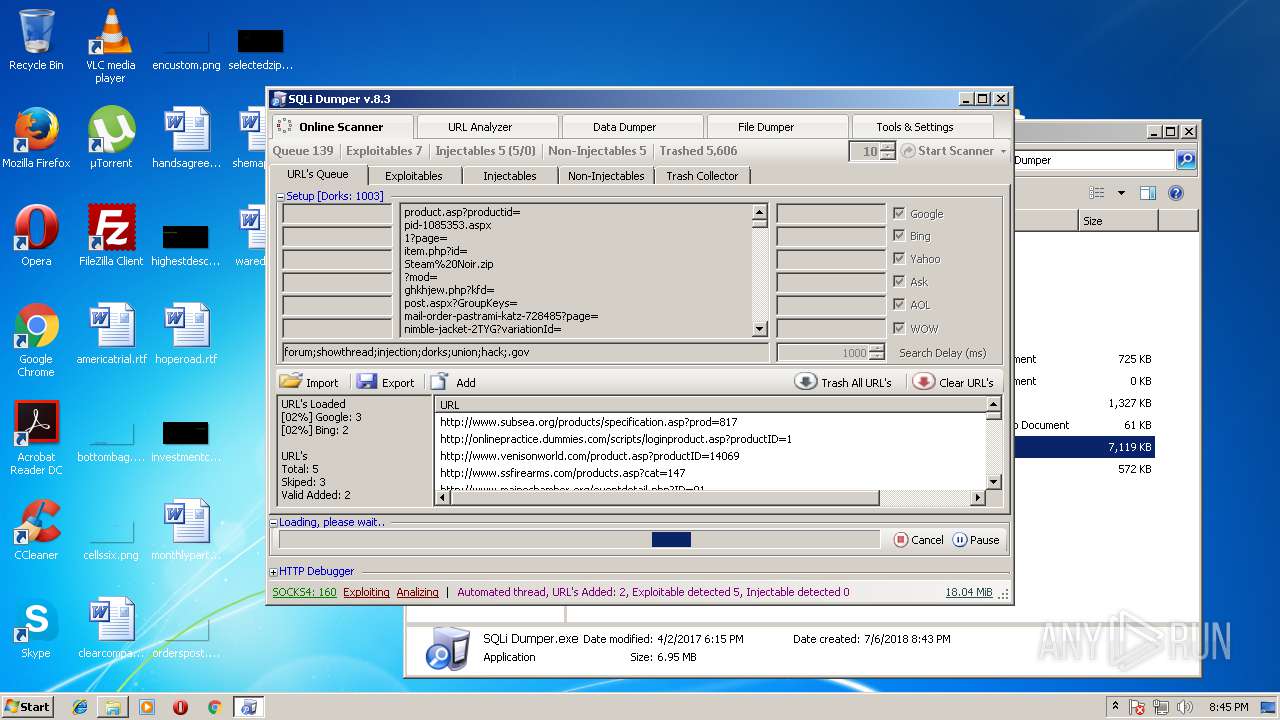
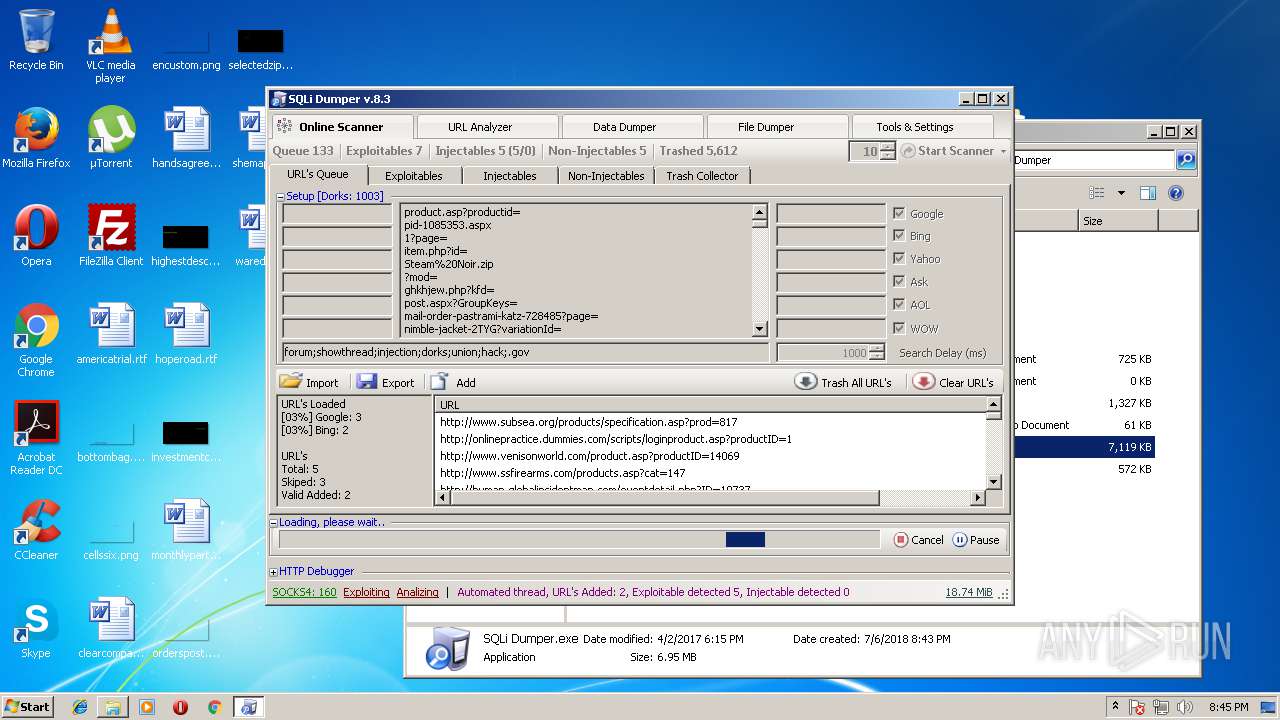
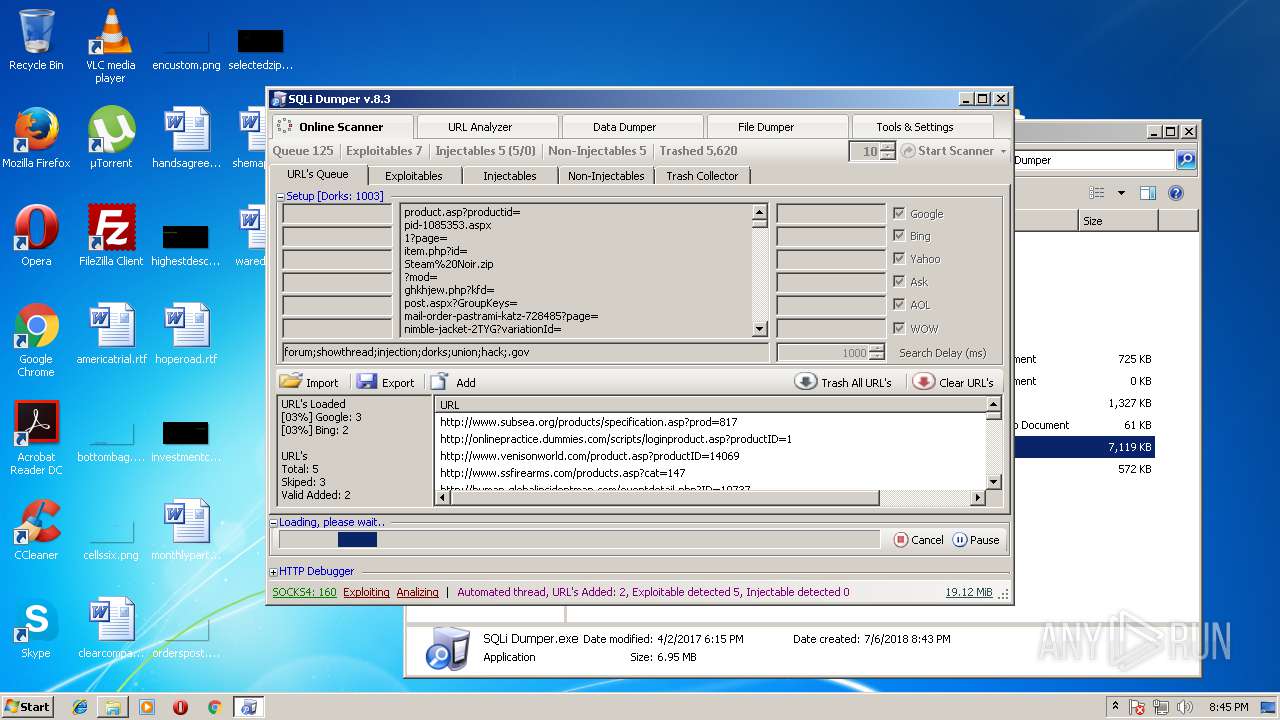
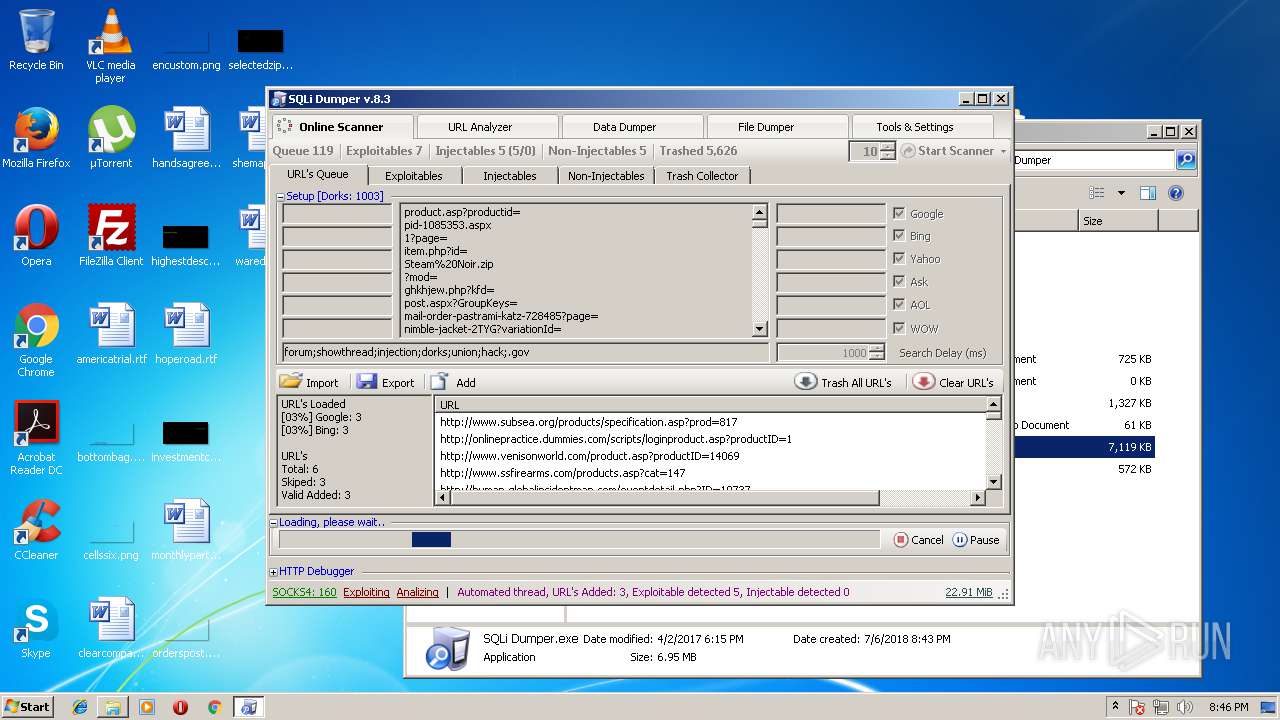
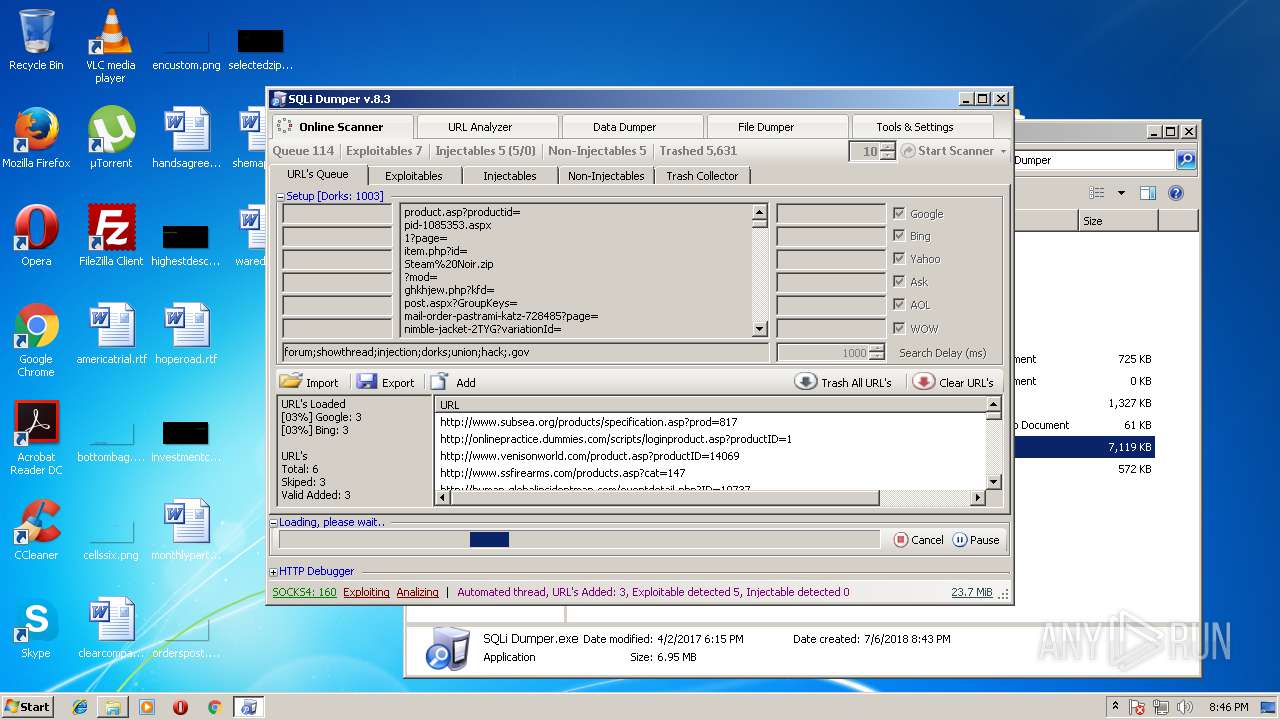
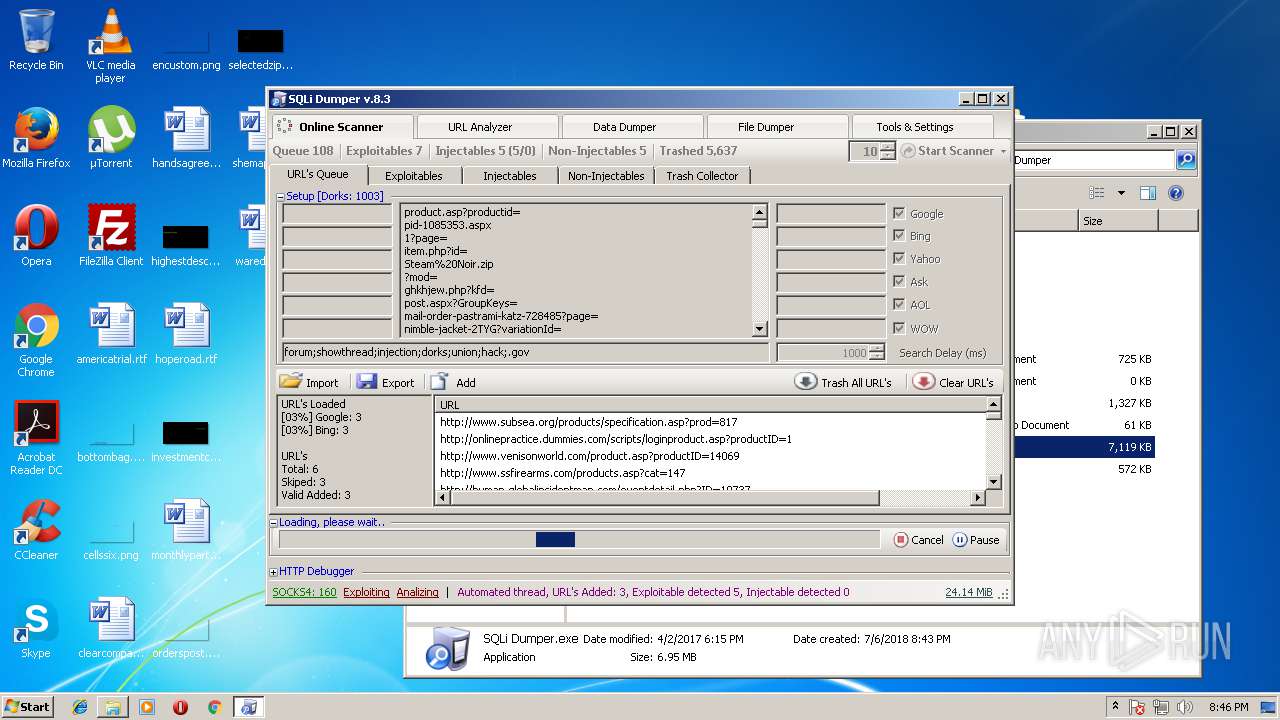
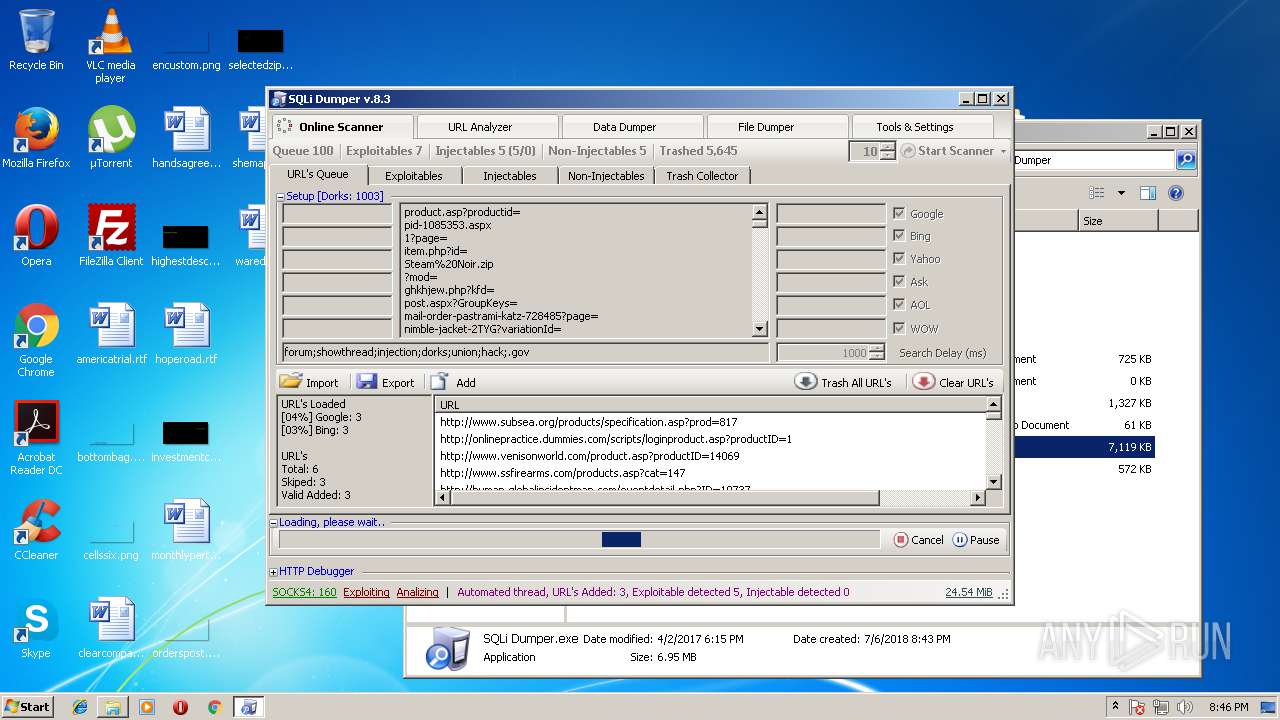
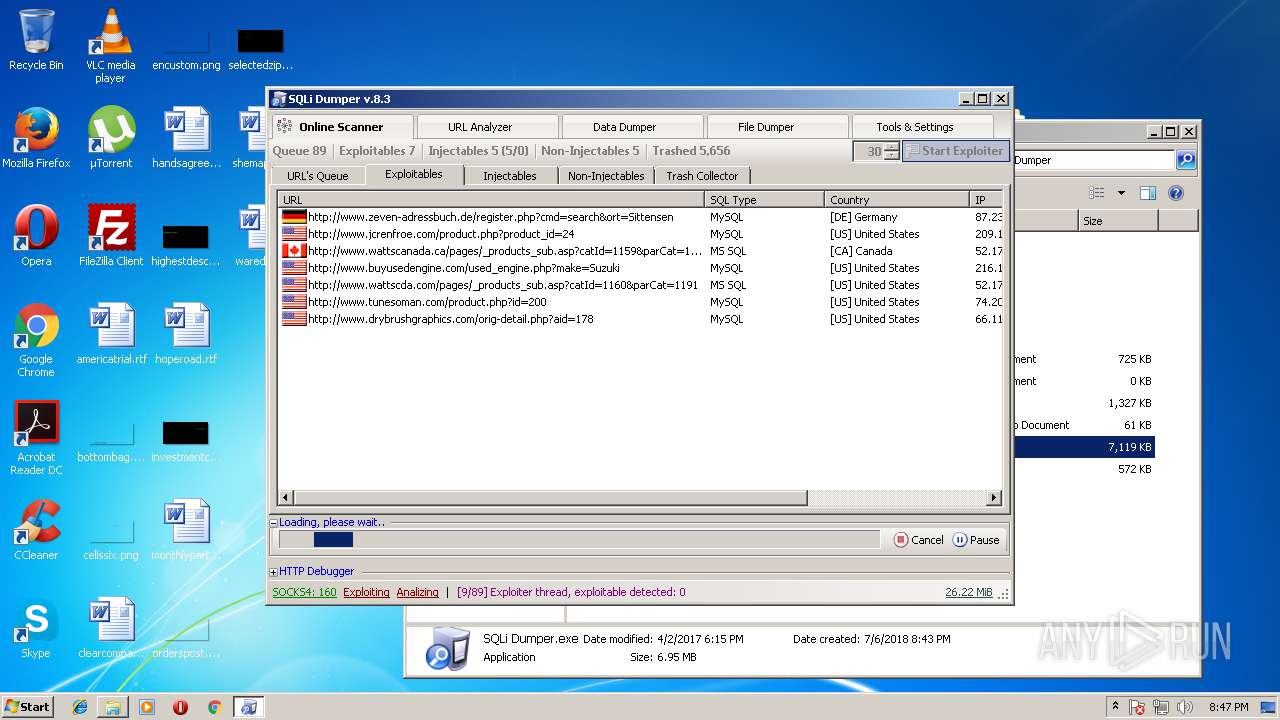
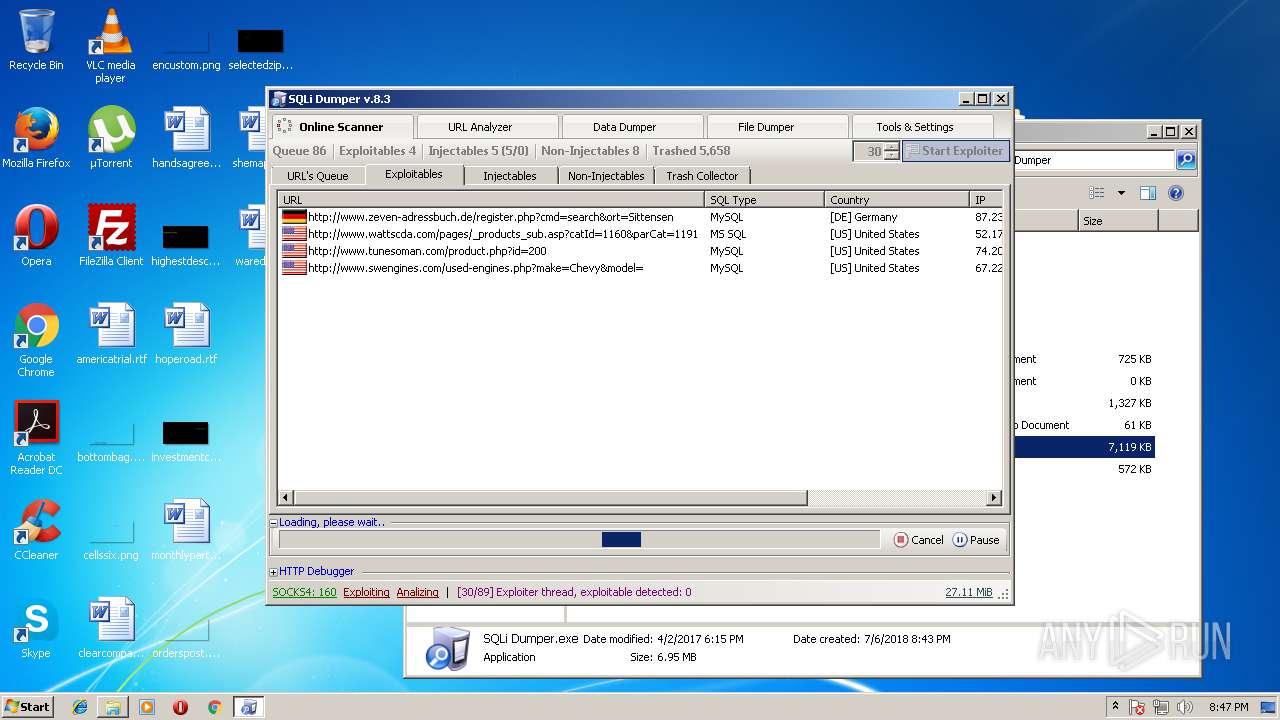
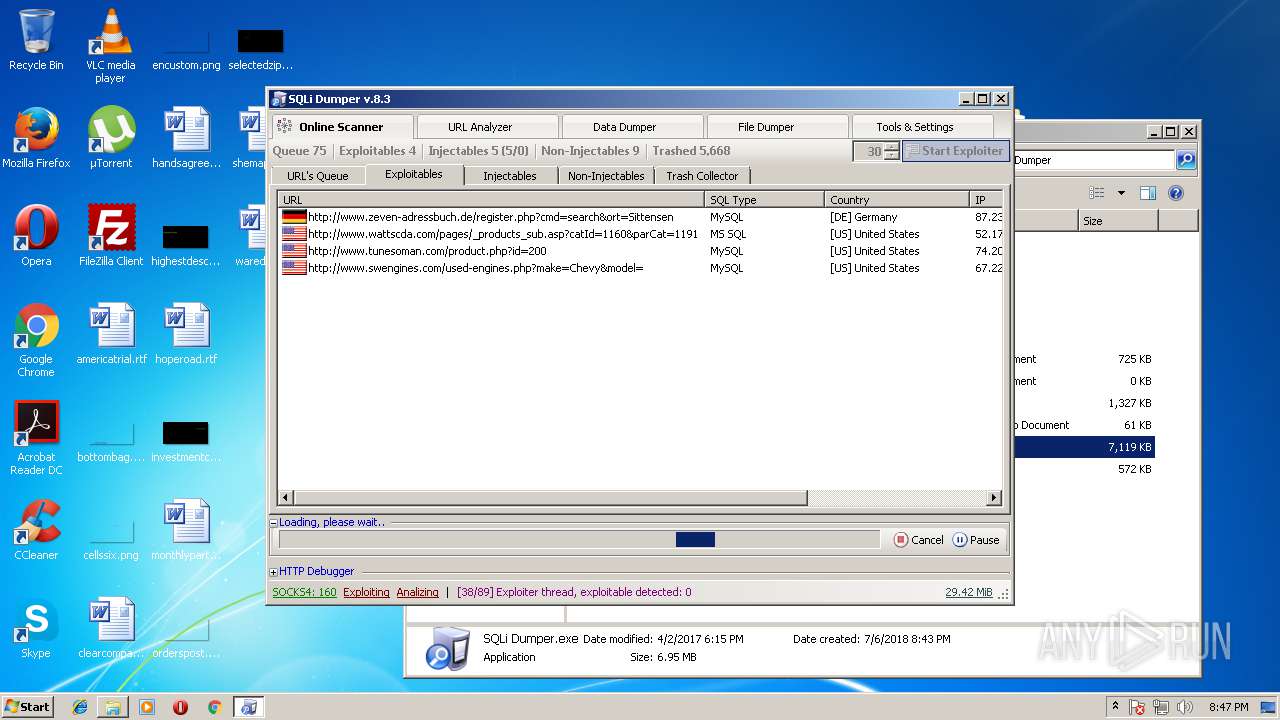
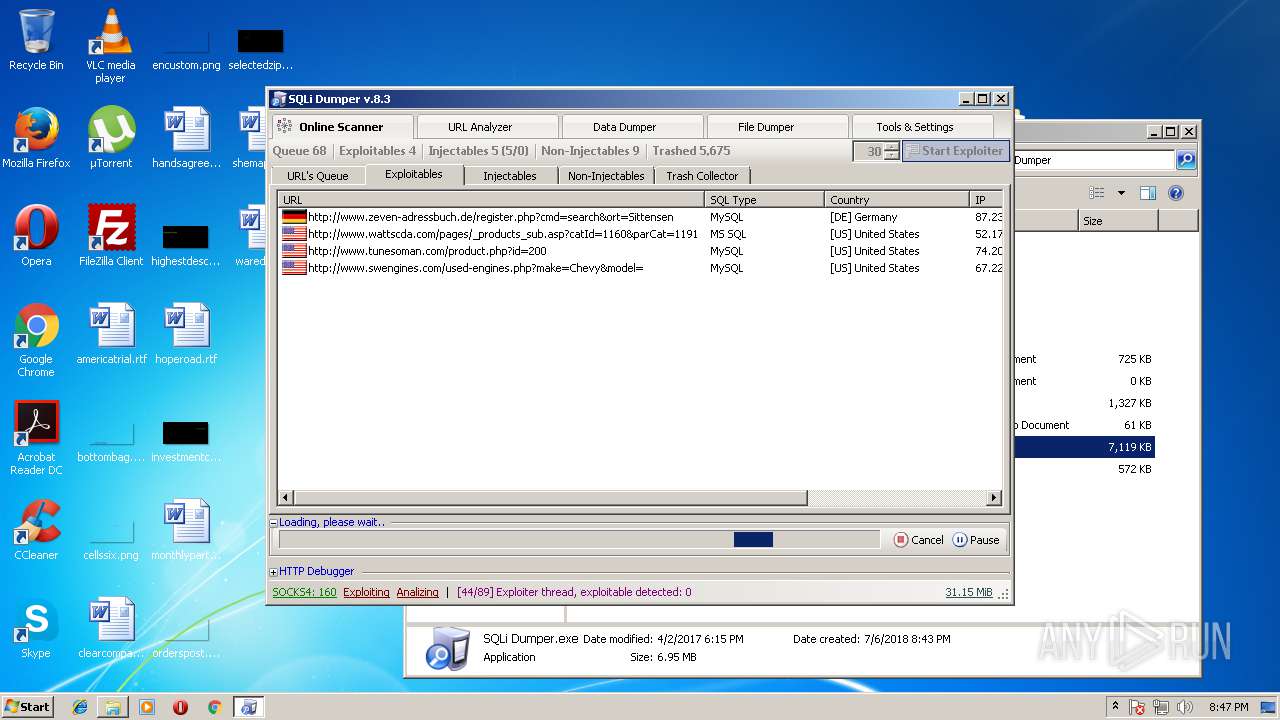
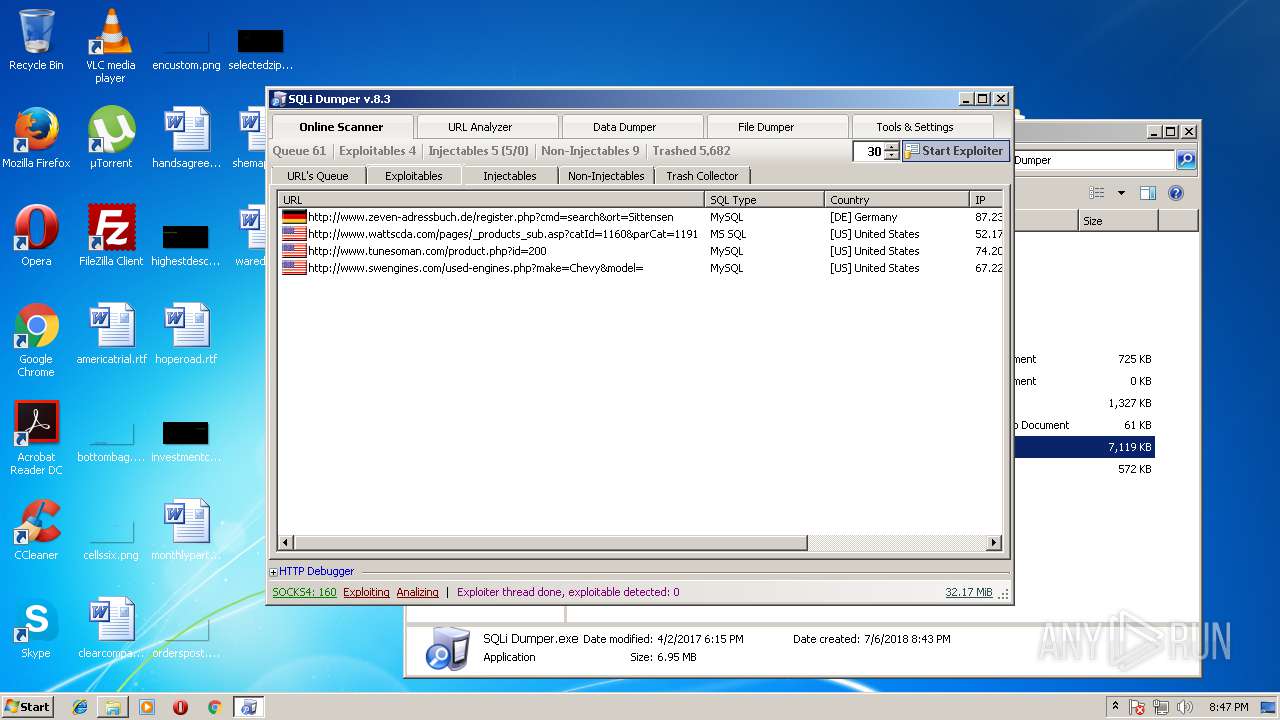
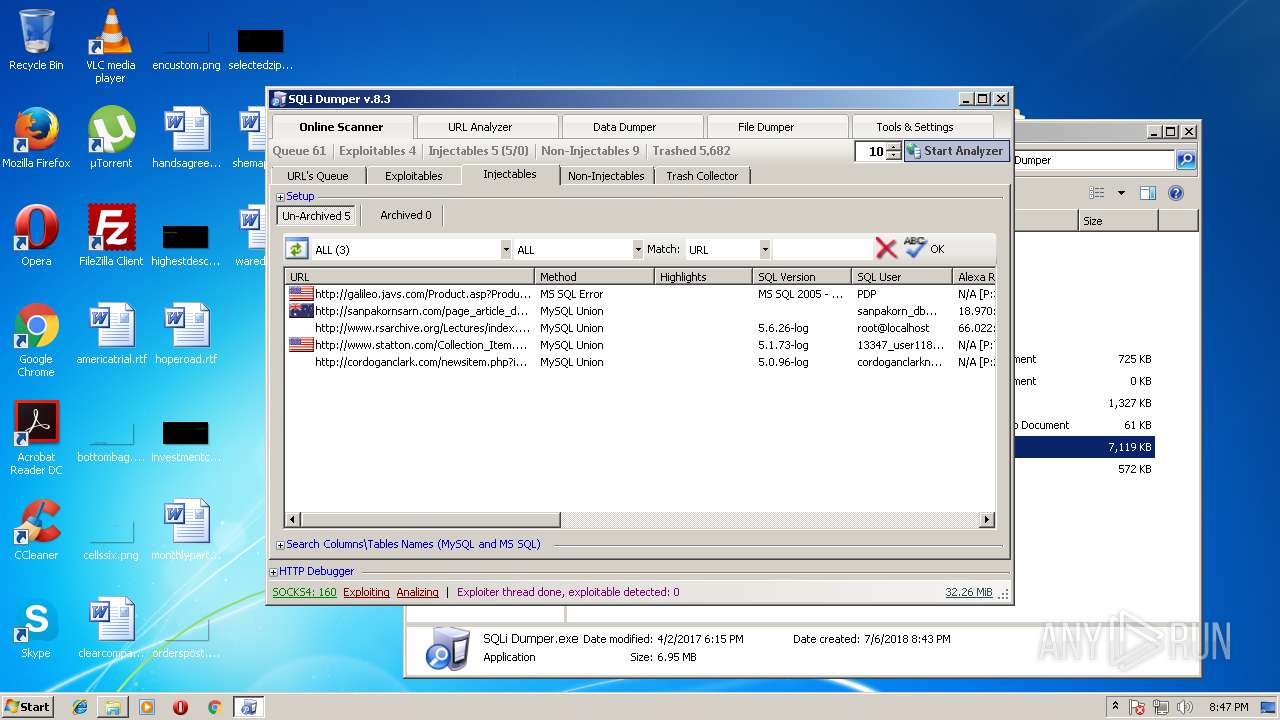
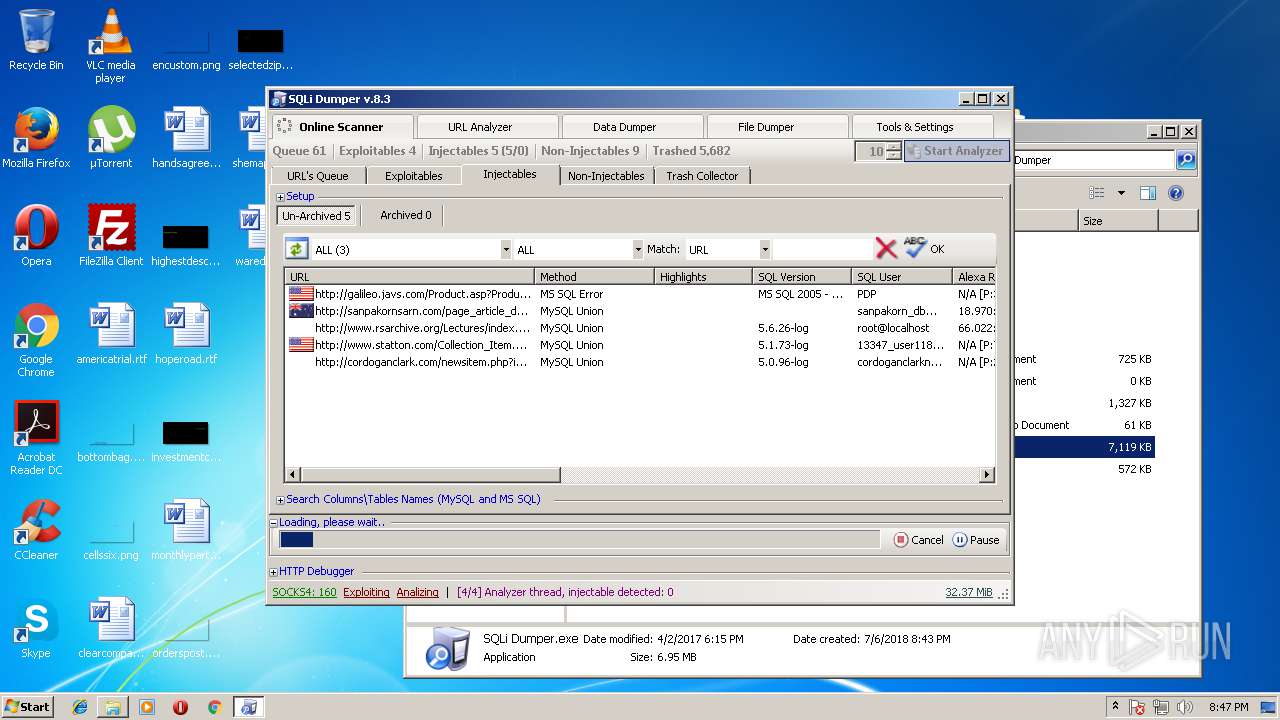
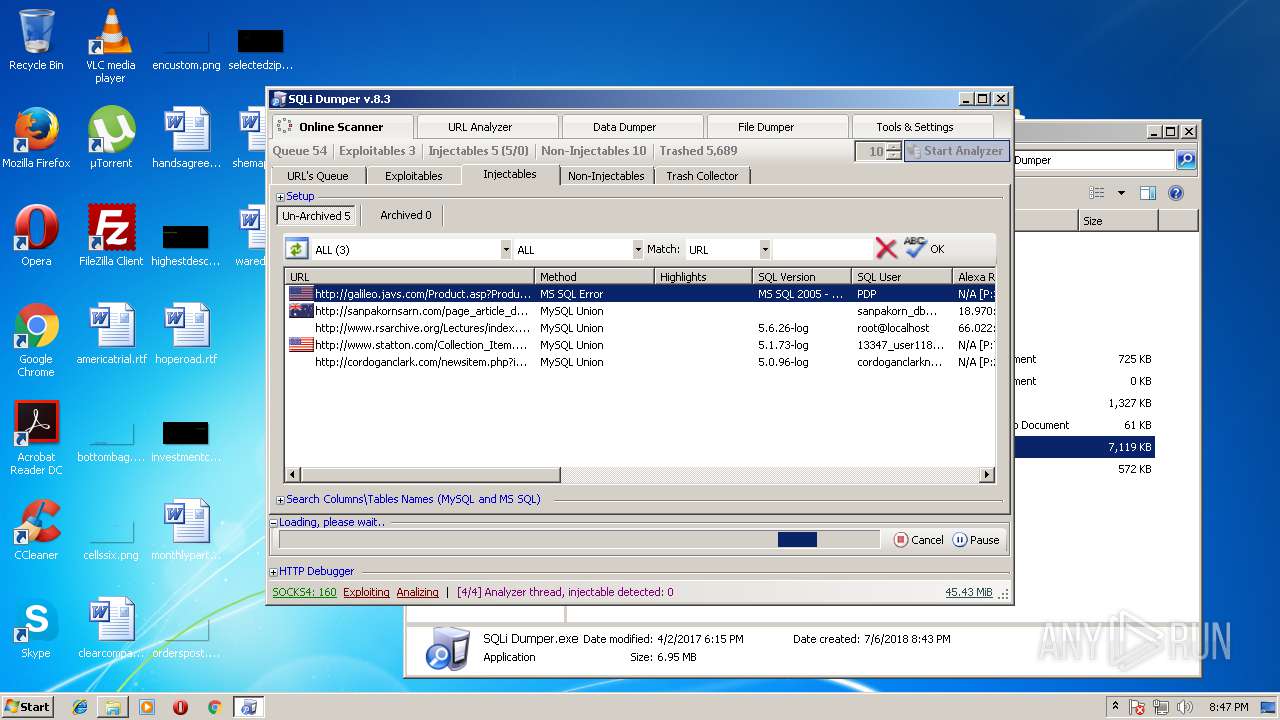
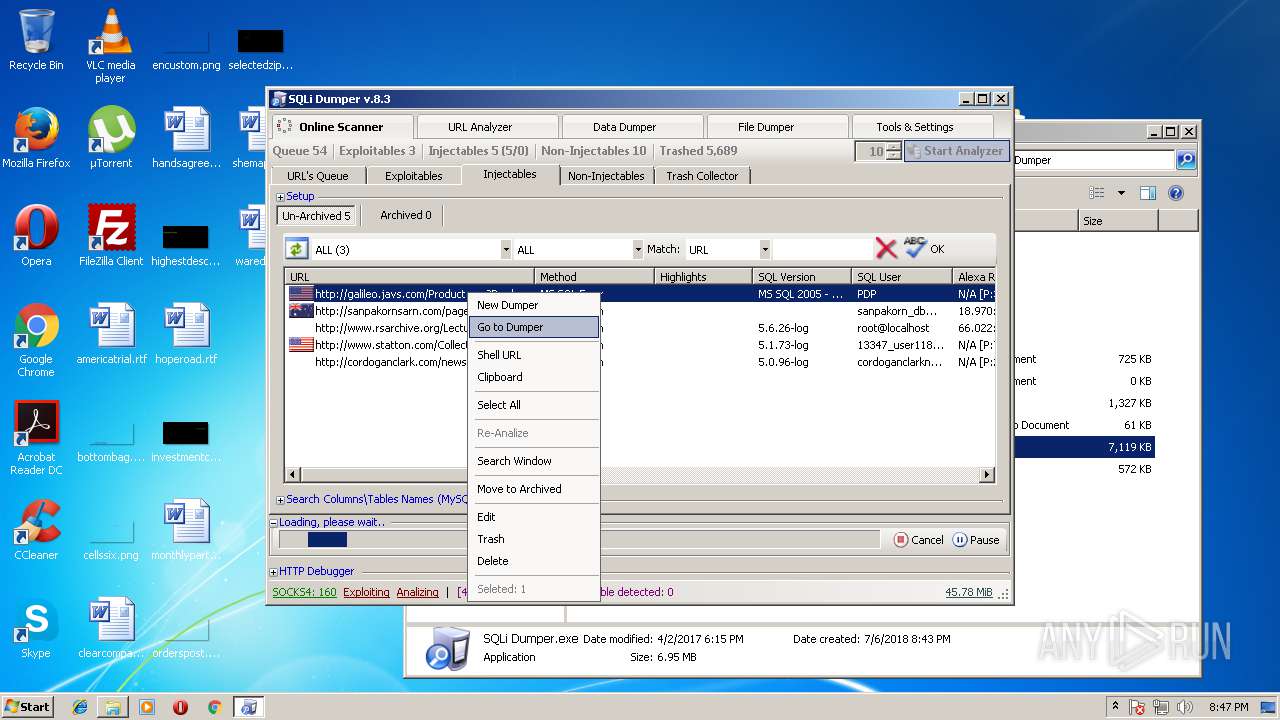
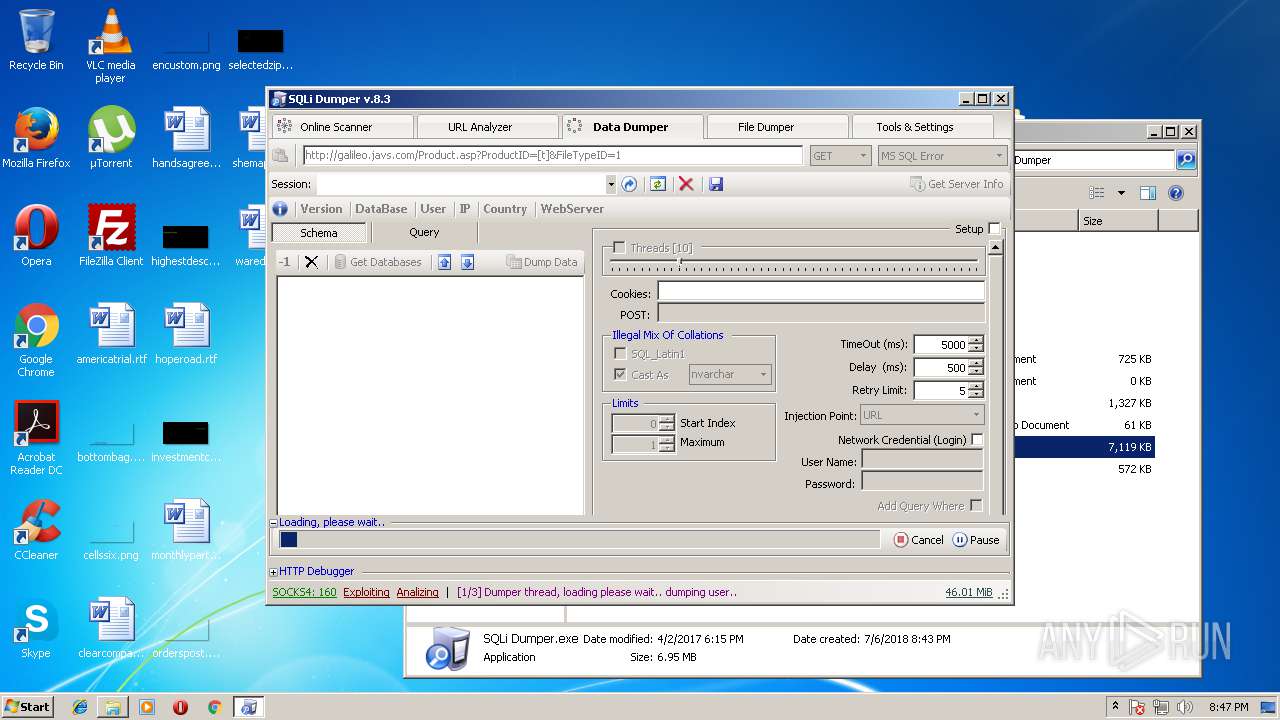
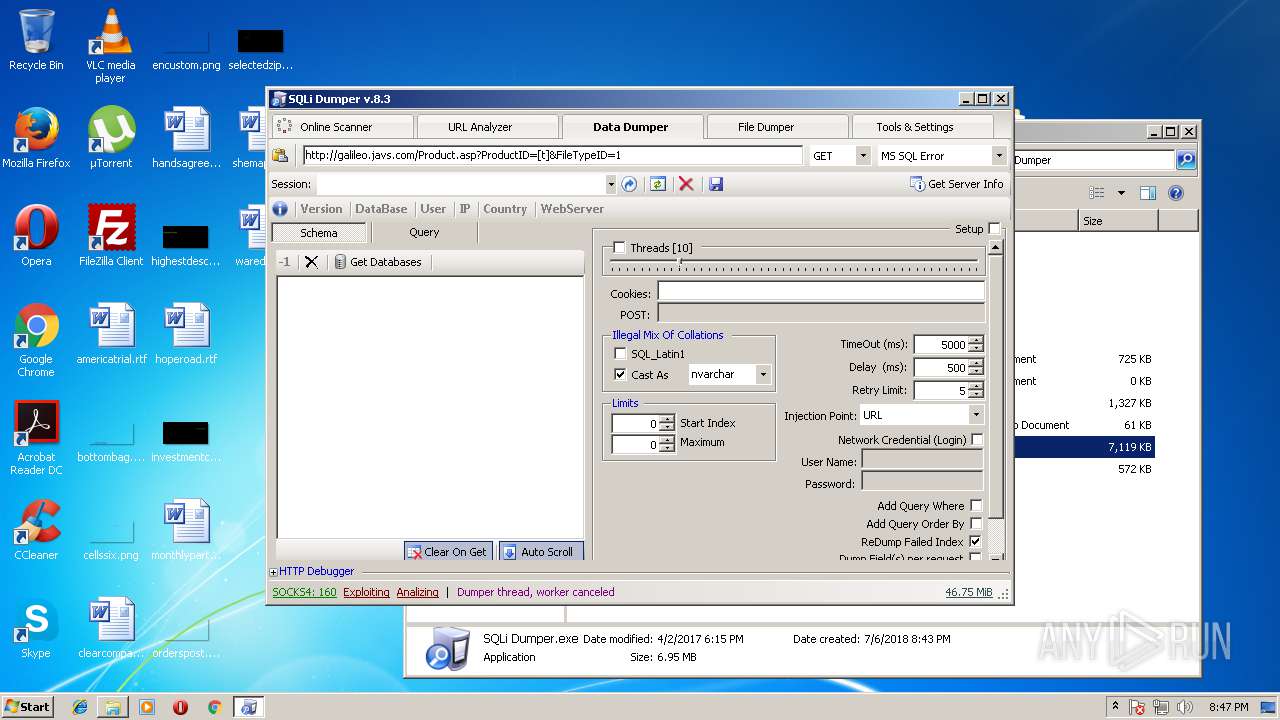
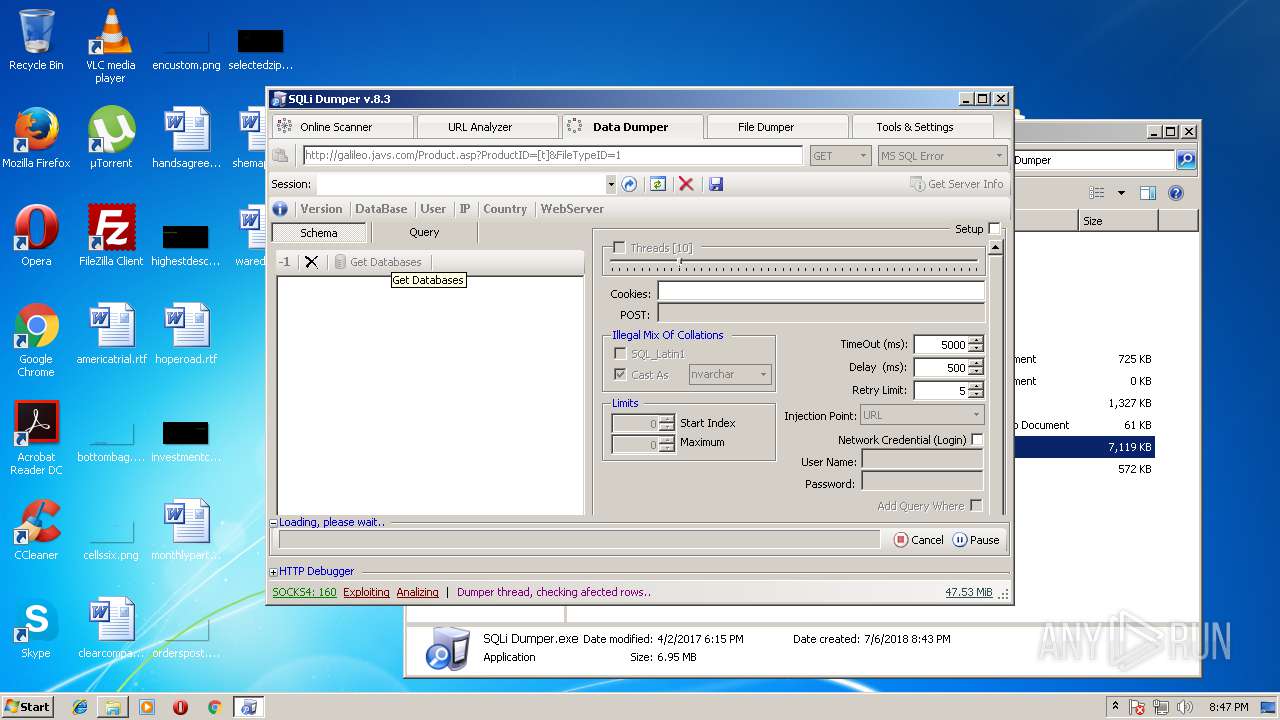
| download: | Sqli_Dumper.rar |
| Full analysis: | https://app.any.run/tasks/1369278a-872e-49f7-844c-0dfb35352da9 |
| Verdict: | Malicious activity |
| Threats: | Ransomware is a type of malicious software that locks users out of their system or data using different methods to force them to pay a ransom. Most often, such programs encrypt files on an infected machine and demand a fee to be paid in exchange for the decryption key. Additionally, such programs can be used to steal sensitive information from the compromised computer and even conduct DDoS attacks against affected organizations to pressure them into paying. |
| Analysis date: | July 06, 2018, 19:42:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 76743FA5F136E5991820A8D10BD07C97 |
| SHA1: | 156976110F13218CB03B20217804F7F50EB14716 |
| SHA256: | 64DF23E58C94EEDECA61C2198CAEAB17A33F3283EE60C02E2F4E8B1869C003ED |
| SSDEEP: | 196608:qAb6sAmjZSm2XieXpXjXMRxs+xGIW8xIa+CF0tWXe5Wl2FuH6UZ29y1ZR44hvrse:pDAmdShySVLMRxxbW8xIeytWXeJsatYX |
MALICIOUS
Application was dropped or rewritten from another process
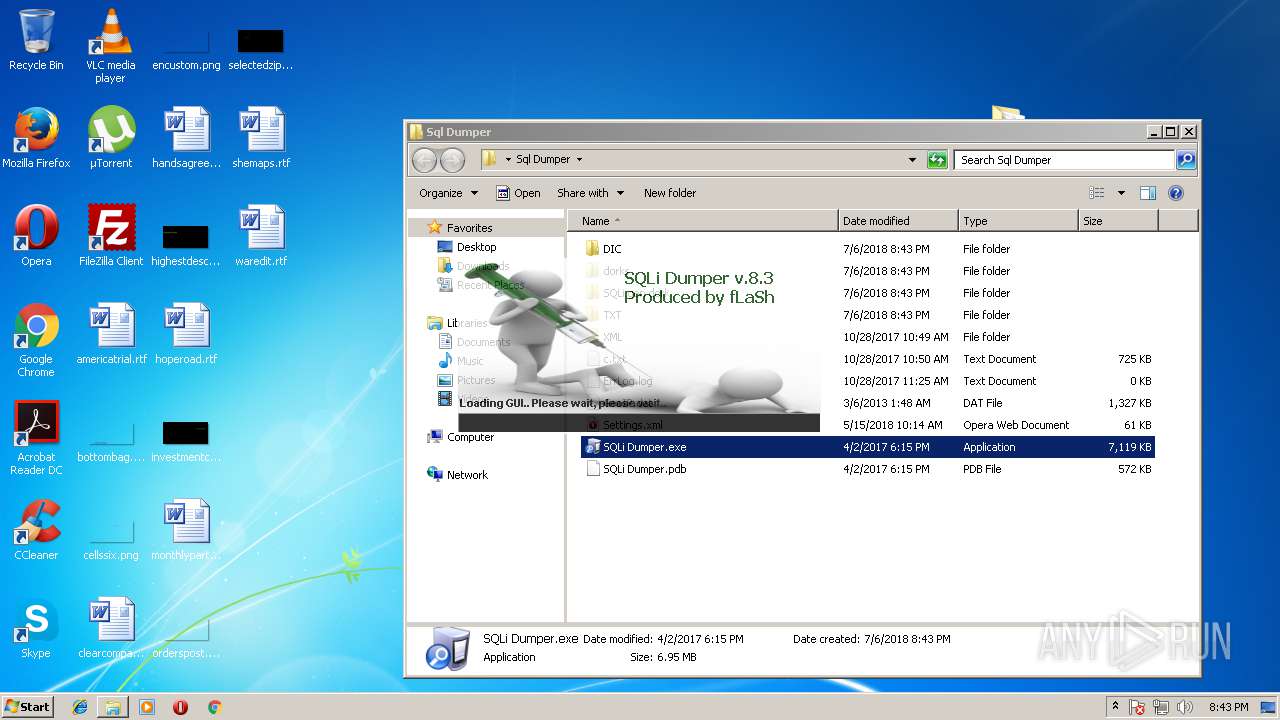
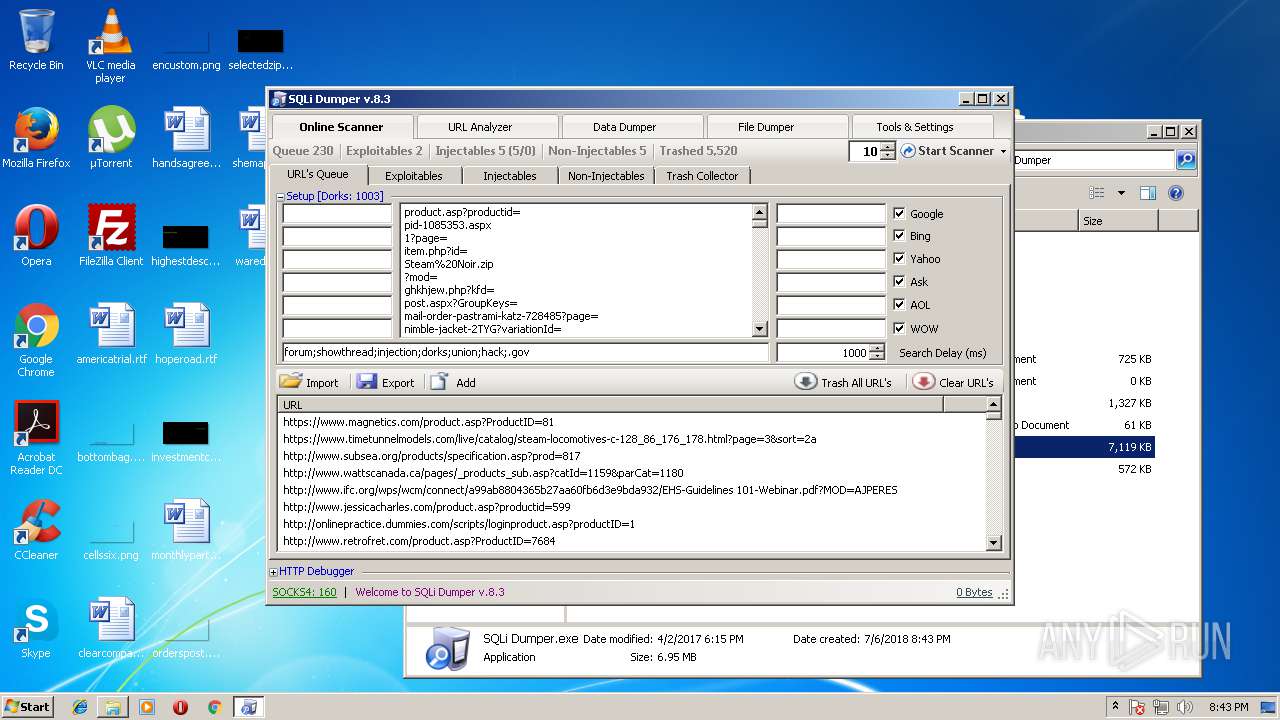
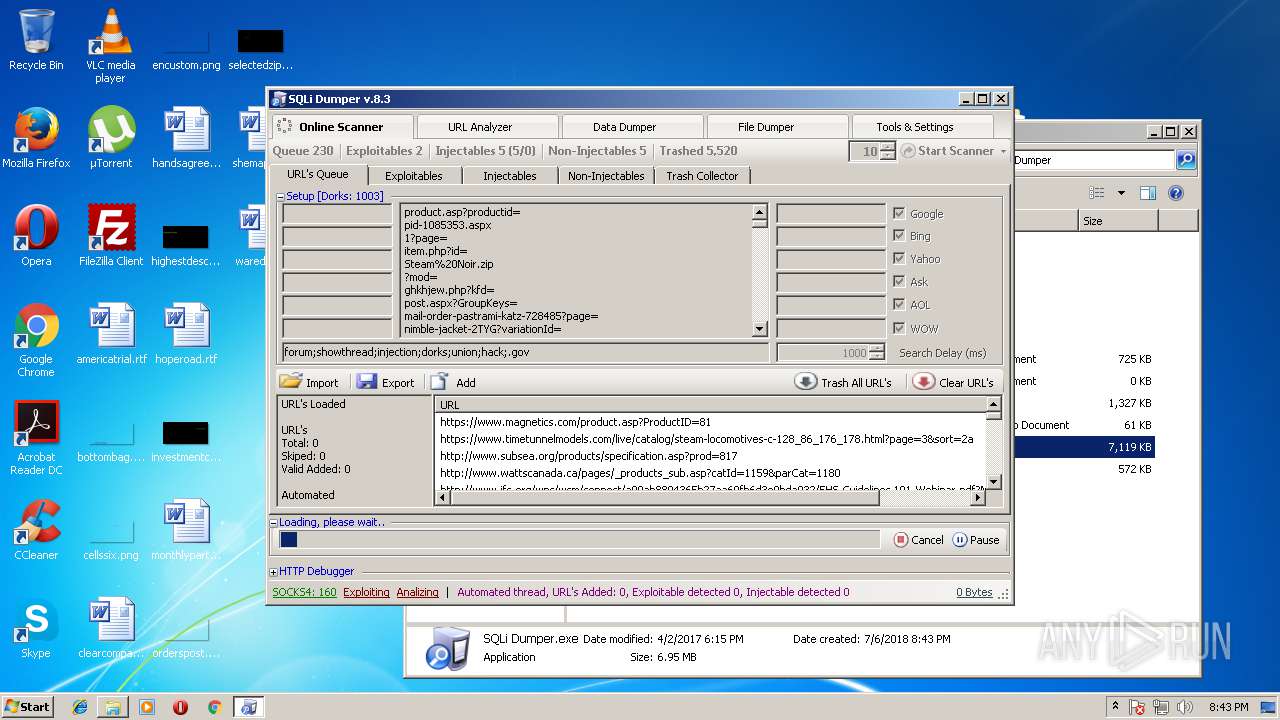
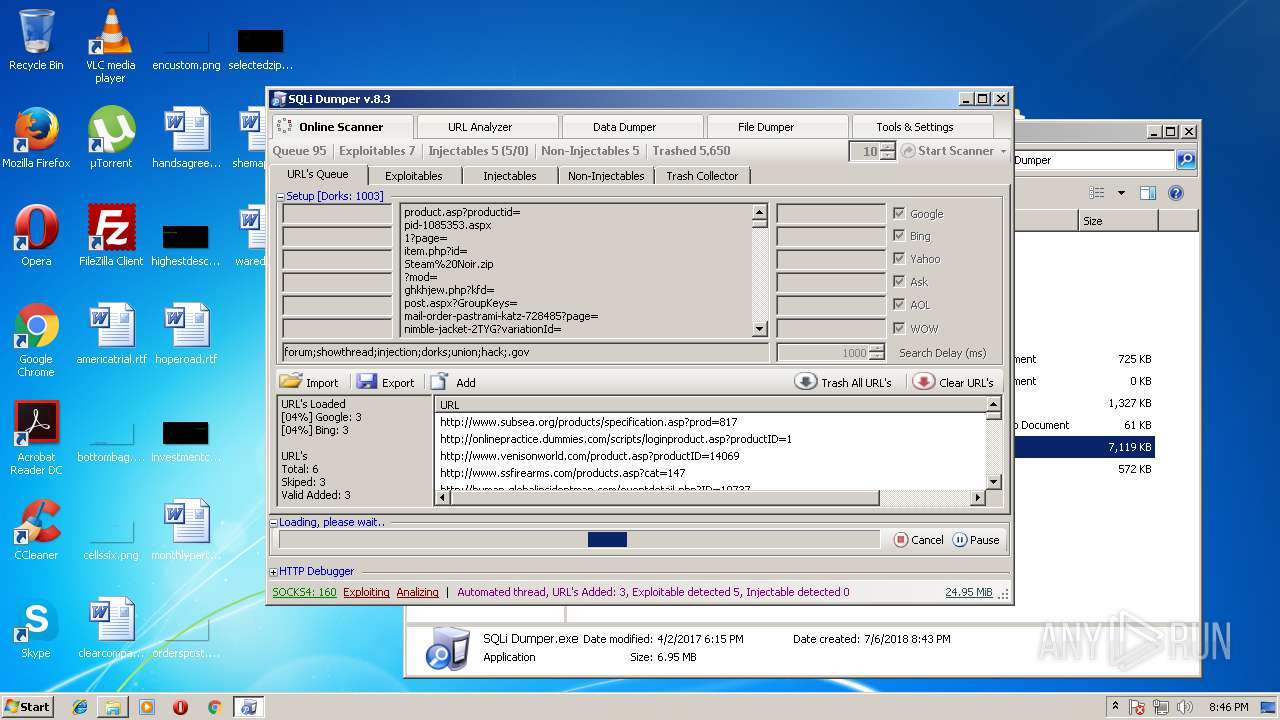
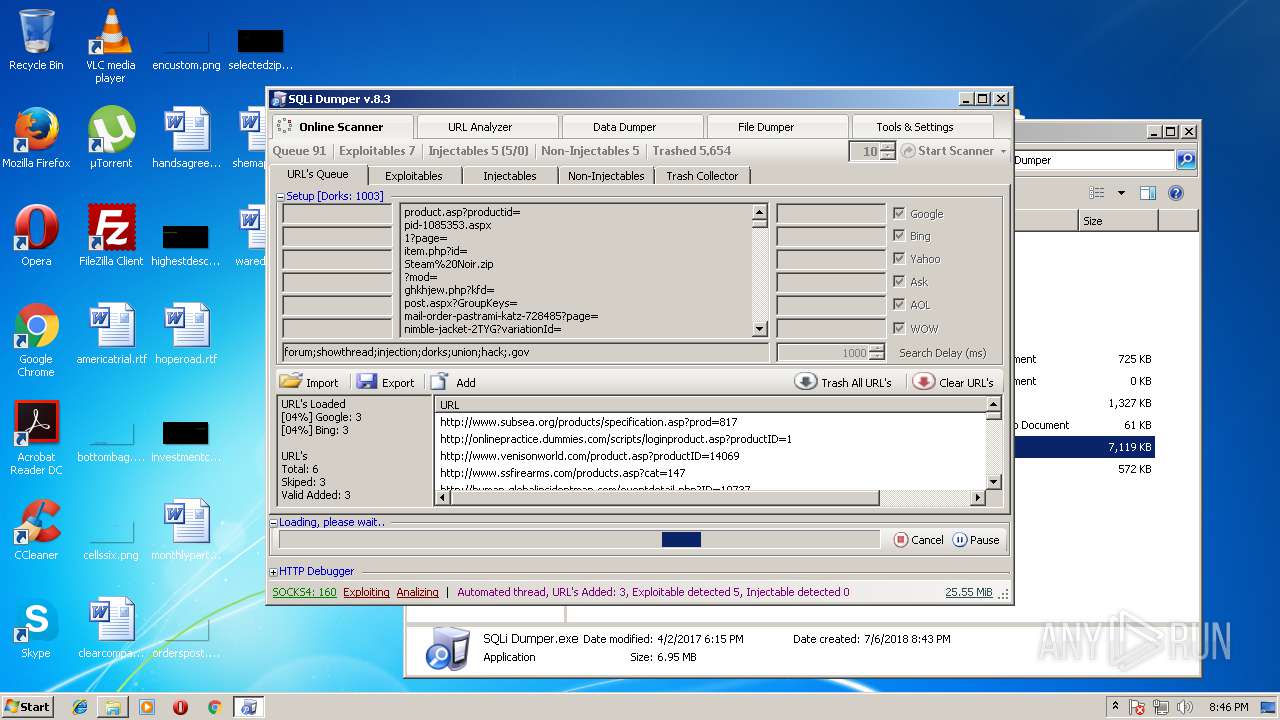
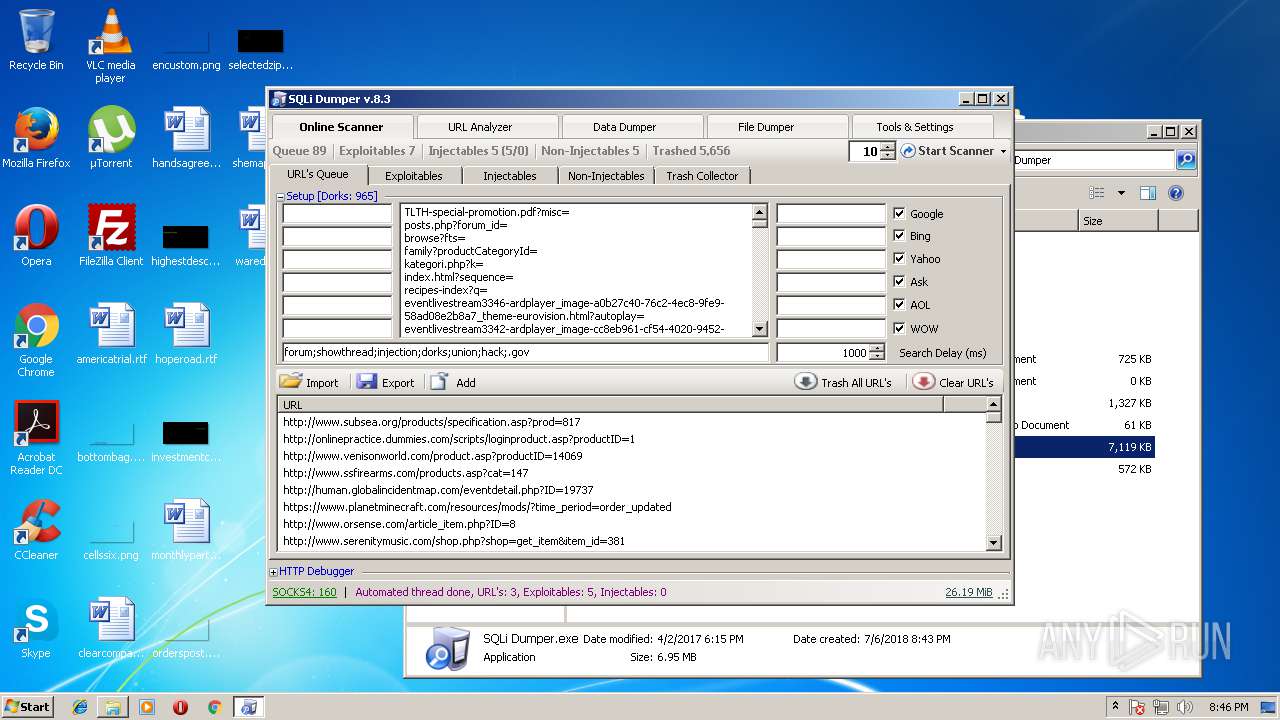
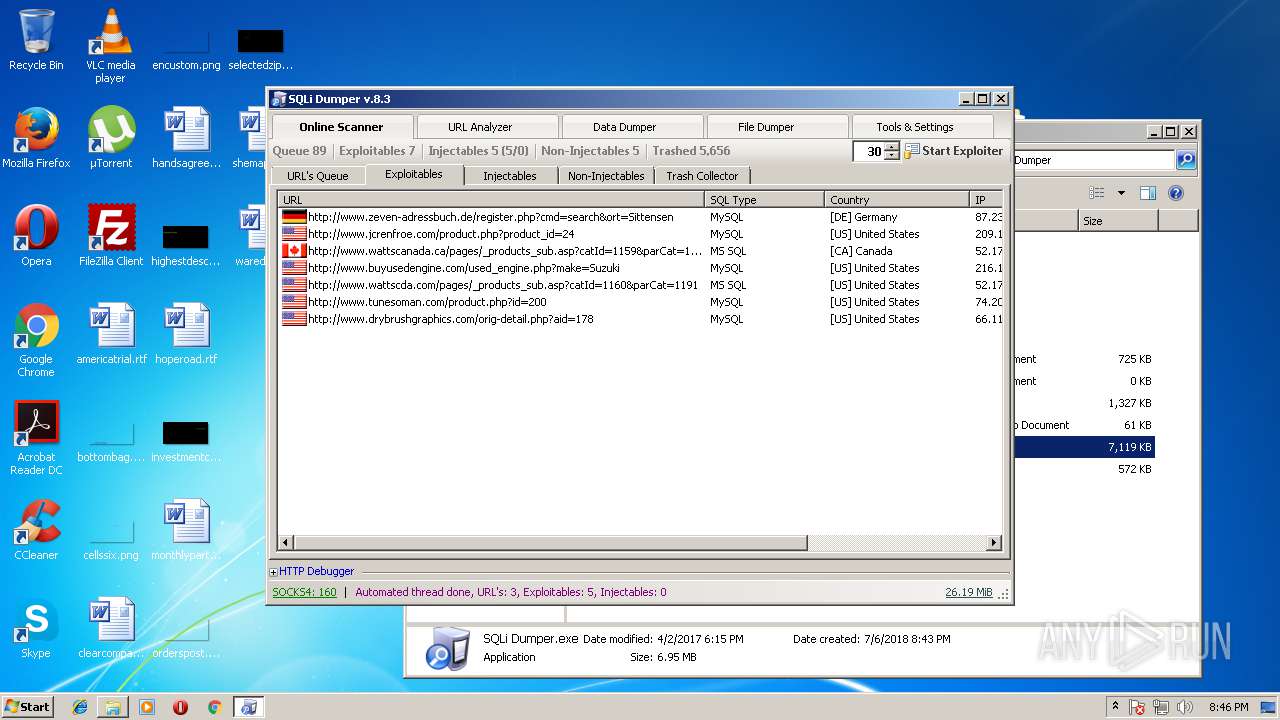
- SQLi Dumper.exe (PID: 3124)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 2488)
- SQLi Dumper.exe (PID: 3124)
Dropped file may contain instructions of ransomware
- SQLi Dumper.exe (PID: 3124)
SUSPICIOUS
Executable content was dropped or overwritten
- 7zFM.exe (PID: 3604)
- SQLi Dumper.exe (PID: 3124)
Reads internet explorer settings
- SQLi Dumper.exe (PID: 3124)
Connects to unusual port
- SQLi Dumper.exe (PID: 3124)
INFO
Dropped object may contain Bitcoin addresses
- 7zFM.exe (PID: 3604)
- SQLi Dumper.exe (PID: 3124)
Dropped object may contain URL's
- SQLi Dumper.exe (PID: 3124)
- 7zFM.exe (PID: 3604)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 110716 |
|---|---|
| UncompressedSize: | 741809 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2017:10:28 10:50:08 |
| PackingMethod: | Normal |
| ArchivedFileName: | Sql Dumper\c.txt |
Total processes
38
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2488 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe3_ Global\UsGthrCtrlFltPipeMssGthrPipe3 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
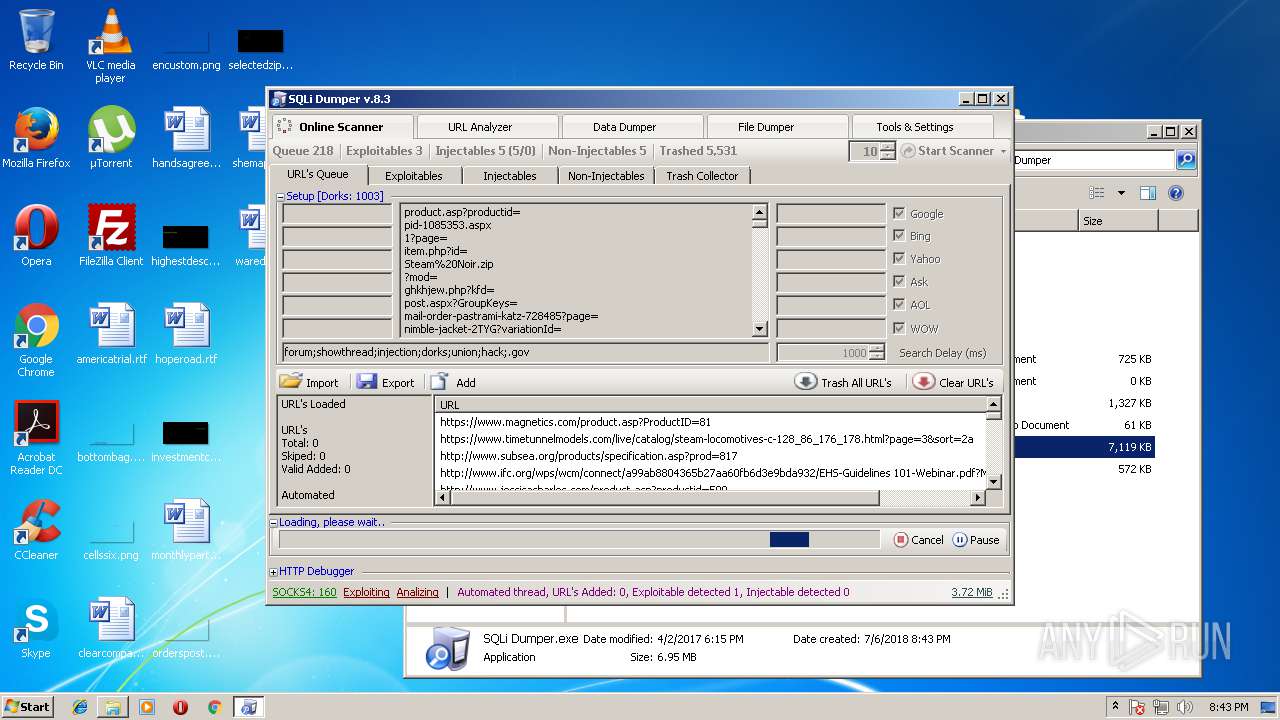
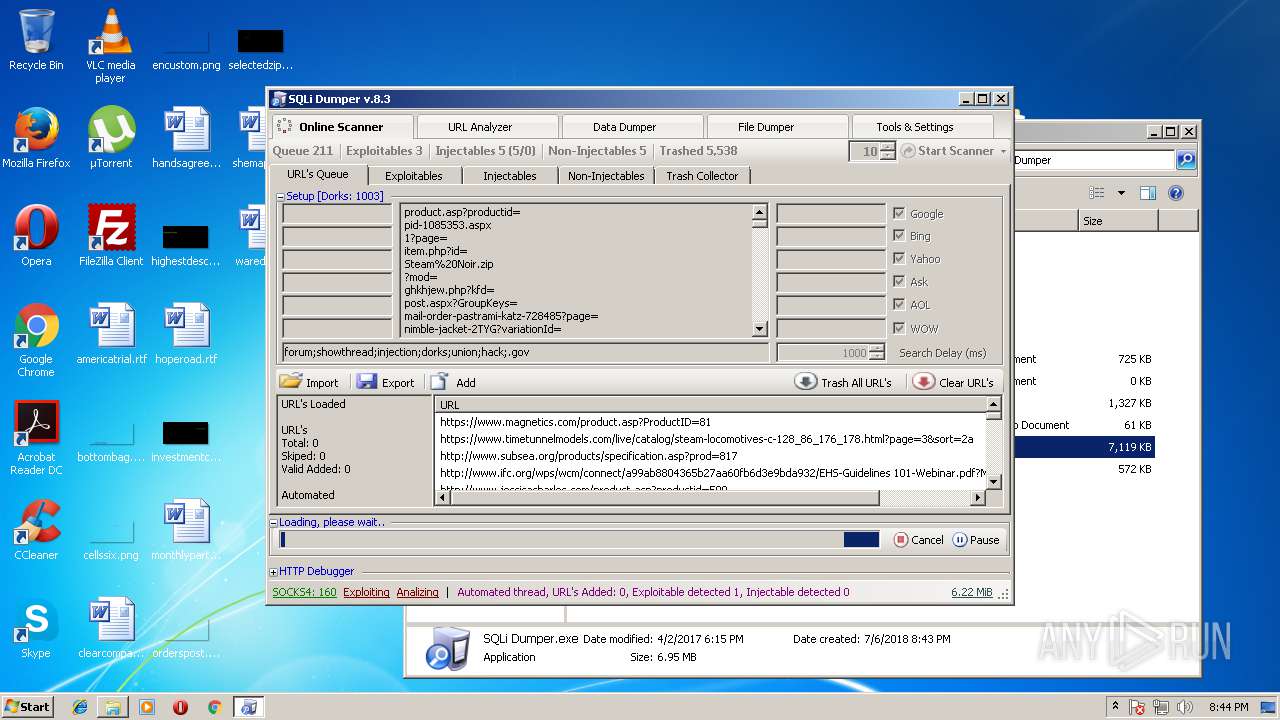
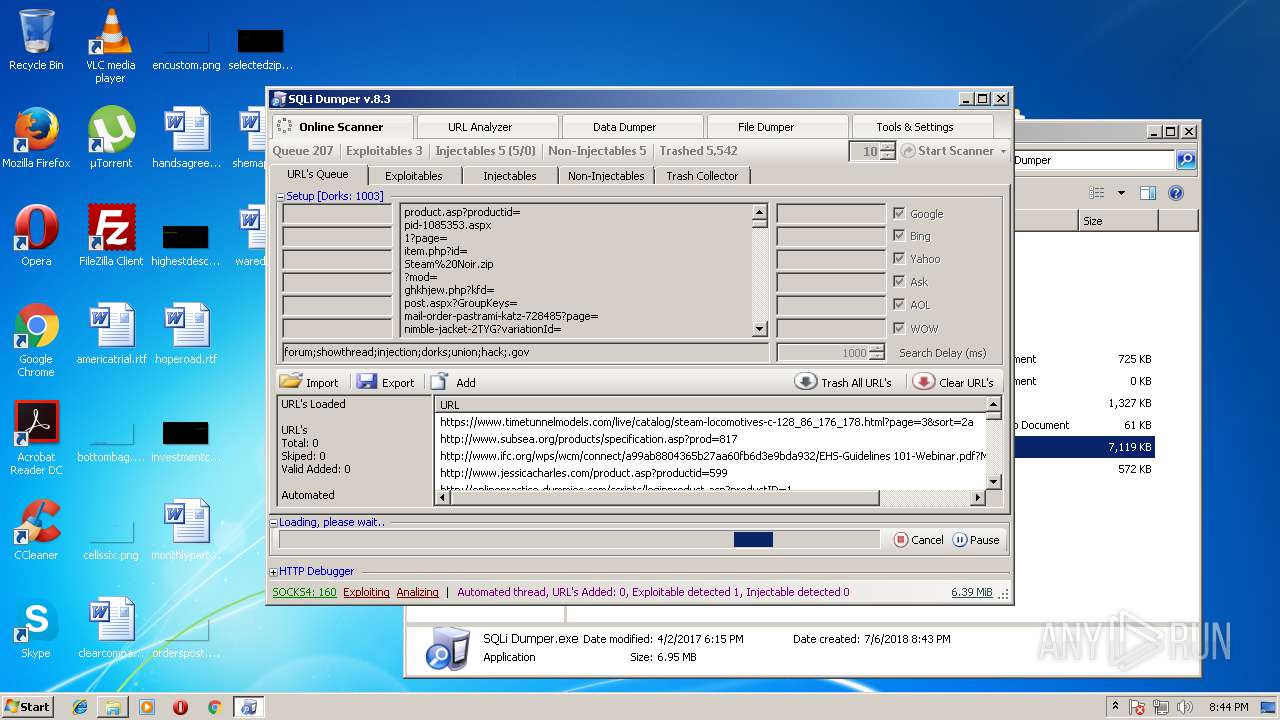
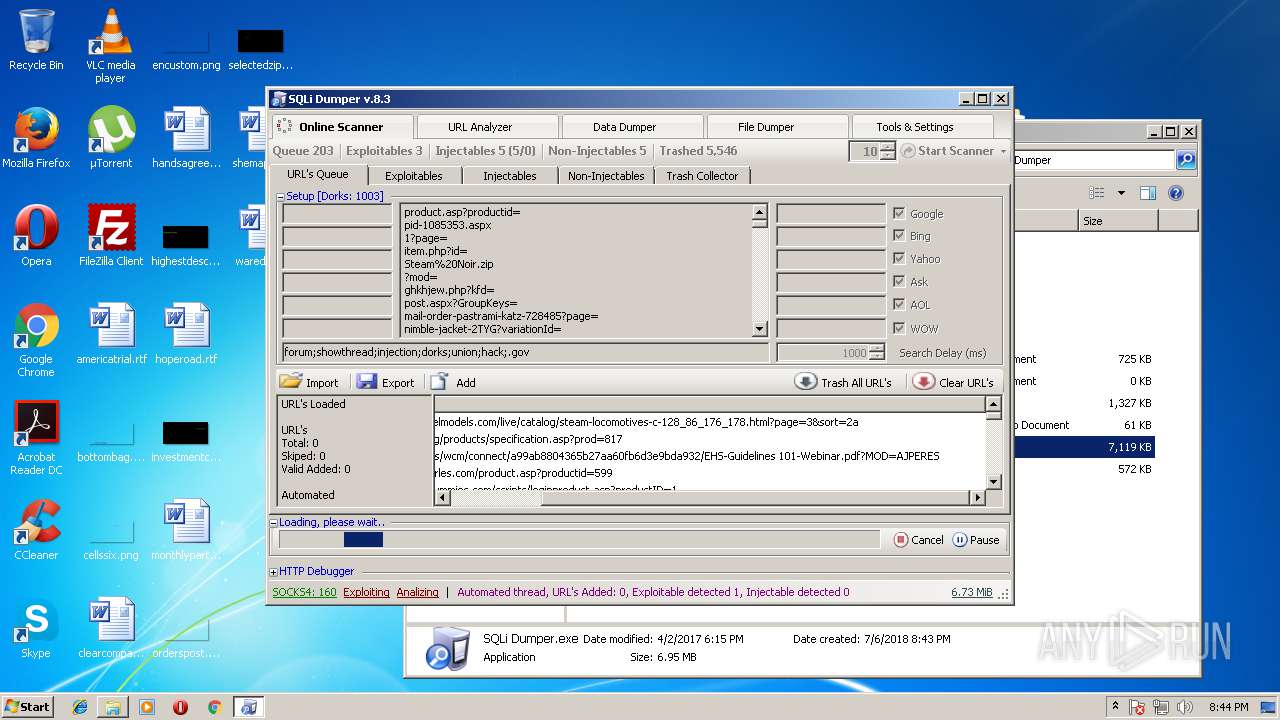
| 3124 | "C:\Users\admin\Desktop\Sql Dumper\SQLi Dumper.exe" | C:\Users\admin\Desktop\Sql Dumper\SQLi Dumper.exe | explorer.exe | ||||||||||||
User: admin Company: c4rl0s@jabber.ru Integrity Level: MEDIUM Description: SQLi Dumper Exit code: 0 Version: 8.3.0.0 Modules
| |||||||||||||||
| 3604 | "C:\Program Files\7-Zip\7zFM.exe" "C:\Users\admin\AppData\Local\Temp\Sqli_Dumper.rar" | C:\Program Files\7-Zip\7zFM.exe | explorer.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip File Manager Exit code: 0 Version: 16.04 Modules
| |||||||||||||||
Total events
472
Read events
453
Write events
19
Delete events
0
Modification events
| (PID) Process: | (3604) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | FolderShortcuts |
Value: | |||
| (PID) Process: | (3604) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | FolderHistory |
Value: 43003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C00530071006C0069005F00440075006D007000650072002E007200610072005C000000 | |||
| (PID) Process: | (3604) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | PanelPath0 |
Value: C:\Users\admin\AppData\Local\Temp\ | |||
| (PID) Process: | (3604) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | FlatViewArc0 |
Value: 0 | |||
| (PID) Process: | (3604) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | PanelPath1 |
Value: | |||
| (PID) Process: | (3604) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | FlatViewArc1 |
Value: 0 | |||
| (PID) Process: | (3604) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | ListMode |
Value: 771 | |||
| (PID) Process: | (3604) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | Position |
Value: 1600000016000000D60300000B02000000000000 | |||
| (PID) Process: | (3604) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | Panels |
Value: 0100000000000000DA010000 | |||
| (PID) Process: | (3604) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM\Columns |
| Operation: | write | Name: | 7-Zip.Rar |
Value: 0100000004000000010000000400000001000000A00000000700000001000000640000000800000001000000640000000C00000001000000640000000A00000001000000640000000B00000001000000640000000900000001000000640000000F00000001000000640000000D00000001000000640000000E00000001000000640000001000000001000000640000001100000001000000640000001300000001000000640000001700000001000000640000001600000001000000640000002100000001000000640000001F0000000100000064000000200000000100000064000000 | |||
Executable files
9
Suspicious files
2
Text files
50
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3604 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE41EEB2FA\Sql Dumper\dorks\tdork\парсер дорок\Result\Result(2.46.53 PM)\Dorks.txt | — | |
MD5:— | SHA256:— | |||
| 3604 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE41EEB2FA\Sql Dumper\dorks\tdork\парсер дорок\Result\Result(2.47.20 PM)\Dorks.txt | — | |
MD5:— | SHA256:— | |||
| 3604 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE41EEB2FA\Sql Dumper\dorks\tdork\парсер дорок\Result\Result(2.47.43 PM)\Dorks.txt | — | |
MD5:— | SHA256:— | |||
| 3604 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE41EEB2FA\Sql Dumper\dorks\tdork\парсер дорок\Result\Result(7.31.01)\Dorks.txt | — | |
MD5:— | SHA256:— | |||
| 3604 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE41EEB2FA\Sql Dumper\dorks\tdork\парсер дорок\Result\Result(8.00.08)\Dorks.txt | — | |
MD5:— | SHA256:— | |||
| 3604 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE41EEB2FA\Sql Dumper\dorks\tdork\парсер дорок\Page names.ini | text | |
MD5:— | SHA256:— | |||
| 3604 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE41EEB2FA\Sql Dumper\dorks\tdork\парсер дорок\Pars.txt | text | |
MD5:— | SHA256:— | |||
| 3604 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE41EEB2FA\Sql Dumper\c.txt | text | |
MD5:— | SHA256:— | |||
| 3604 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE41EEB2FA\Sql Dumper\dorks\Dorks VIP HQ Gaming [Gadget Channel].txt | text | |
MD5:— | SHA256:— | |||
| 3604 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE41EEB2FA\Sql Dumper\dorks\tdork\парсер дорок\Options.ini | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
584
TCP/UDP connections
2 511
DNS requests
247
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3124 | SQLi Dumper.exe | GET | 504 | 52.214.130.163:80 | http://search.excite.com/excite.y.3/search/web?fcoid=417&fcop=topnav&fpid=27&q=indexing+html | IE | — | — | whitelisted |
3124 | SQLi Dumper.exe | GET | 302 | 37.187.174.101:80 | http://downloads.uk.aluk.com/downloads.php?product_type=4'A=0 | FR | — | — | unknown |
3124 | SQLi Dumper.exe | GET | 302 | 148.253.251.167:80 | http://www.korea.net/Government/Current-Affairs/National-Affairs?affairId=656 | US | — | — | malicious |
3124 | SQLi Dumper.exe | GET | 504 | 52.214.130.163:80 | http://search.excite.com/excite.y.3/search/web?fcoid=417&fcop=topnav&fpid=27&q=indexing+html | IE | — | — | whitelisted |
3124 | SQLi Dumper.exe | GET | 200 | 185.115.219.154:80 | http://www.yucon-solutions.be/nl/de-collectie/product.asp?productId=70 | BE | html | 5.50 Kb | unknown |
3124 | SQLi Dumper.exe | GET | 200 | 87.230.19.6:80 | http://www.zeven-adressbuch.de/register.php?cmd='0=A&ort=Sittensen | DE | html | 10.0 Kb | unknown |
3124 | SQLi Dumper.exe | GET | 200 | 2.16.186.66:80 | http://www.wctv.tv/video?videoid=315 | unknown | html | 18.1 Kb | whitelisted |
3124 | SQLi Dumper.exe | GET | 200 | 37.187.174.101:80 | http://downloads.uk.aluk.com/downloads.php?product_type=4 | FR | html | 28.2 Kb | unknown |
3124 | SQLi Dumper.exe | GET | 200 | 87.230.19.6:80 | http://www.zeven-adressbuch.de/register.php?cmd=search&ort='0=A | DE | html | 5.21 Kb | unknown |
3124 | SQLi Dumper.exe | GET | 200 | 70.42.219.29:80 | http://www.yext.com/pl/yahoo-claims/index.html?yh_source=srp_locallist_n | US | html | 591 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3124 | SQLi Dumper.exe | 178.63.120.76:1080 | — | Hetzner Online GmbH | DE | unknown |
3124 | SQLi Dumper.exe | 218.255.130.182:8882 | — | WTT HK Limited | HK | unknown |
3124 | SQLi Dumper.exe | 97.74.230.244:39763 | — | GoDaddy.com, LLC | US | unknown |
3124 | SQLi Dumper.exe | 194.67.207.42:1080 | — | MAROSNET Telecommunication Company LLC | RU | unknown |
3124 | SQLi Dumper.exe | 198.49.23.144:443 | www.amicis.com | Squarespace, Inc. | US | malicious |
3124 | SQLi Dumper.exe | 185.162.235.215:1080 | — | Serverius Holding B.V. | RU | unknown |
3124 | SQLi Dumper.exe | 2.16.186.66:80 | www.wctv.tv | Akamai International B.V. | — | whitelisted |
3124 | SQLi Dumper.exe | 87.230.19.6:80 | www.zeven-adressbuch.de | PlusServer GmbH | DE | unknown |
3124 | SQLi Dumper.exe | 199.64.234.27:443 | customer.honeywell.com | Honeywell International, Inc. | US | unknown |
3124 | SQLi Dumper.exe | 199.91.248.202:443 | marketplace.wisbar.org | SupraNet Communications, Inc. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.wctv.tv |
| whitelisted |
www.amicis.com |
| malicious |
marketplace.wisbar.org |
| unknown |
customer.honeywell.com |
| unknown |
www.zeven-adressbuch.de |
| unknown |
www.bihaku-net.com |
| unknown |
www.yucon-solutions.be |
| unknown |
downloads.uk.aluk.com |
| unknown |
rcheliclub.ru |
| malicious |
search.excite.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3124 | SQLi Dumper.exe | Potential Corporate Privacy Violation | ET POLICY Self Signed SSL Certificate (SomeOrganizationalUnit) |
3124 | SQLi Dumper.exe | Potential Corporate Privacy Violation | ET POLICY Self Signed SSL Certificate (SomeOrganizationalUnit) |
3124 | SQLi Dumper.exe | Potential Corporate Privacy Violation | ET POLICY Self Signed SSL Certificate (SomeOrganizationalUnit) |
3124 | SQLi Dumper.exe | Potential Corporate Privacy Violation | ET POLICY Self Signed SSL Certificate (SomeOrganizationalUnit) |
3124 | SQLi Dumper.exe | Potential Corporate Privacy Violation | ET POLICY Self Signed SSL Certificate (SomeOrganizationalUnit) |