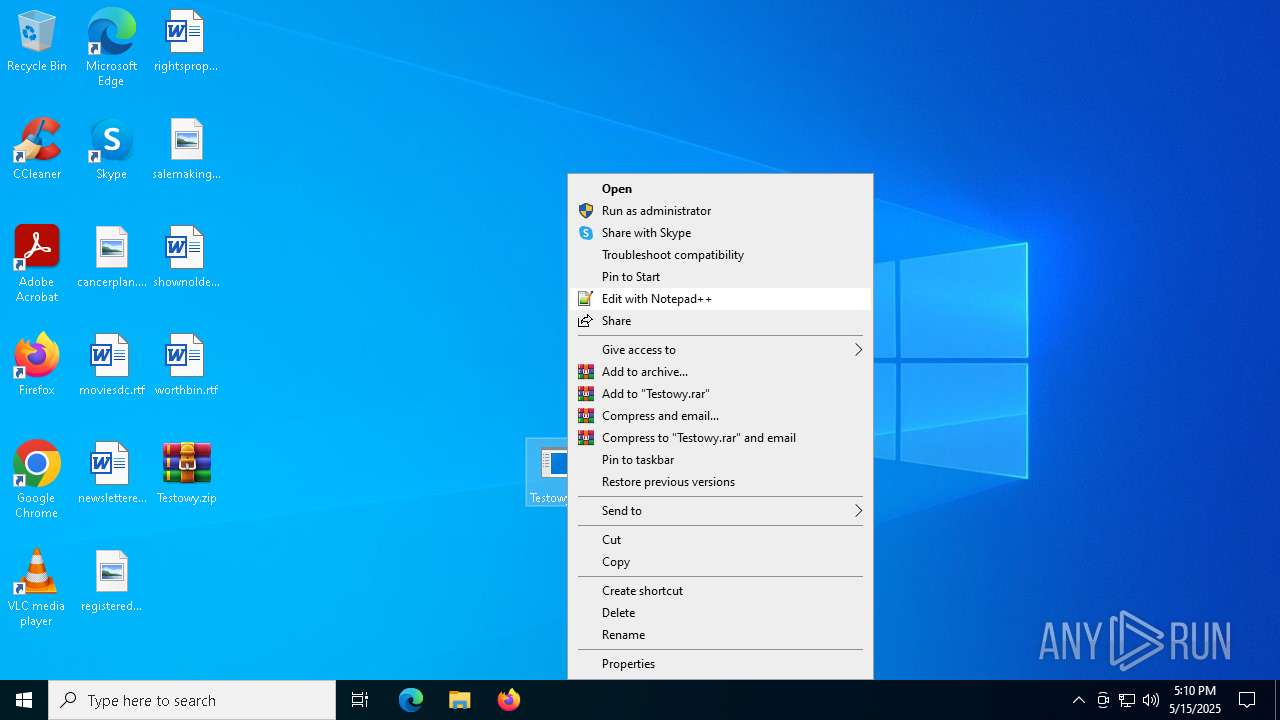
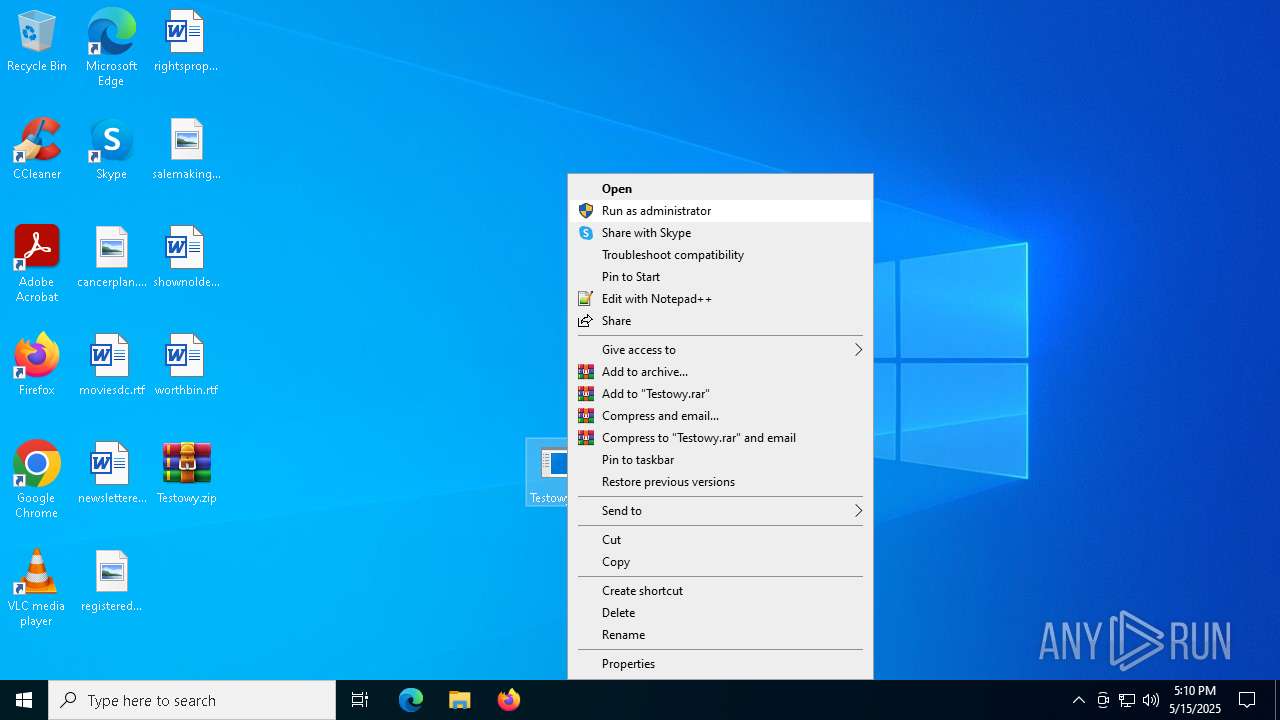
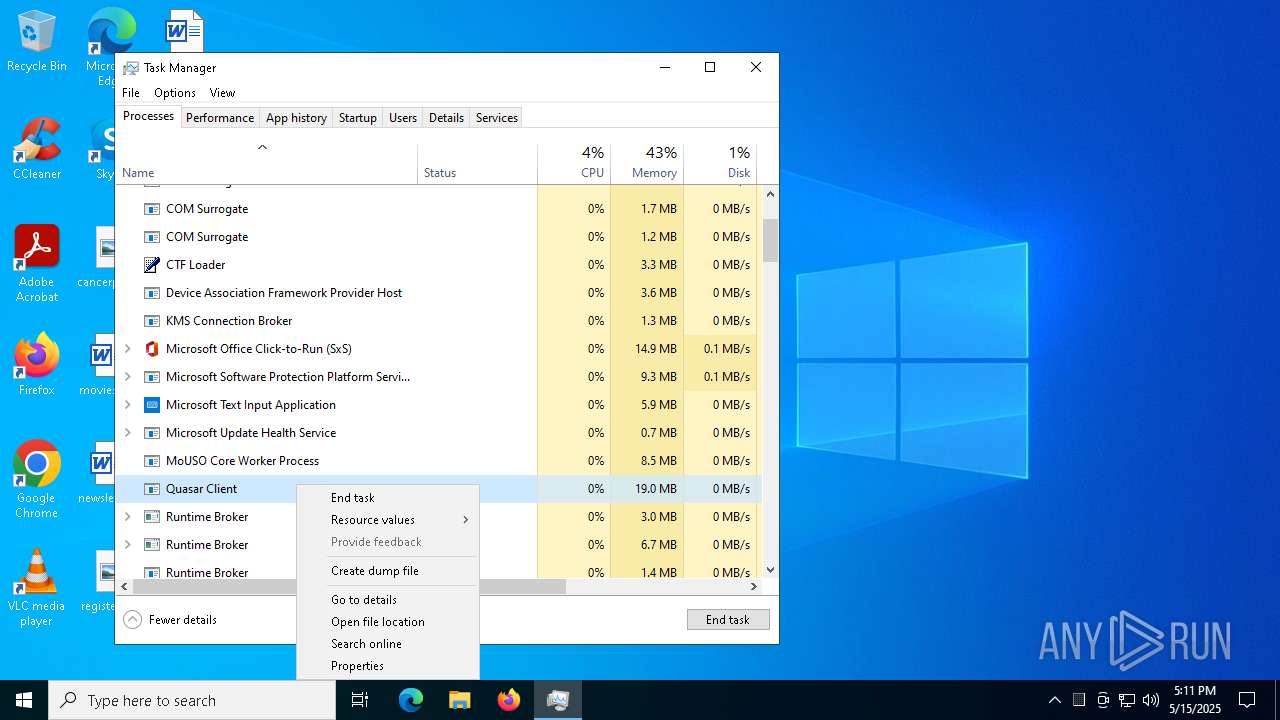
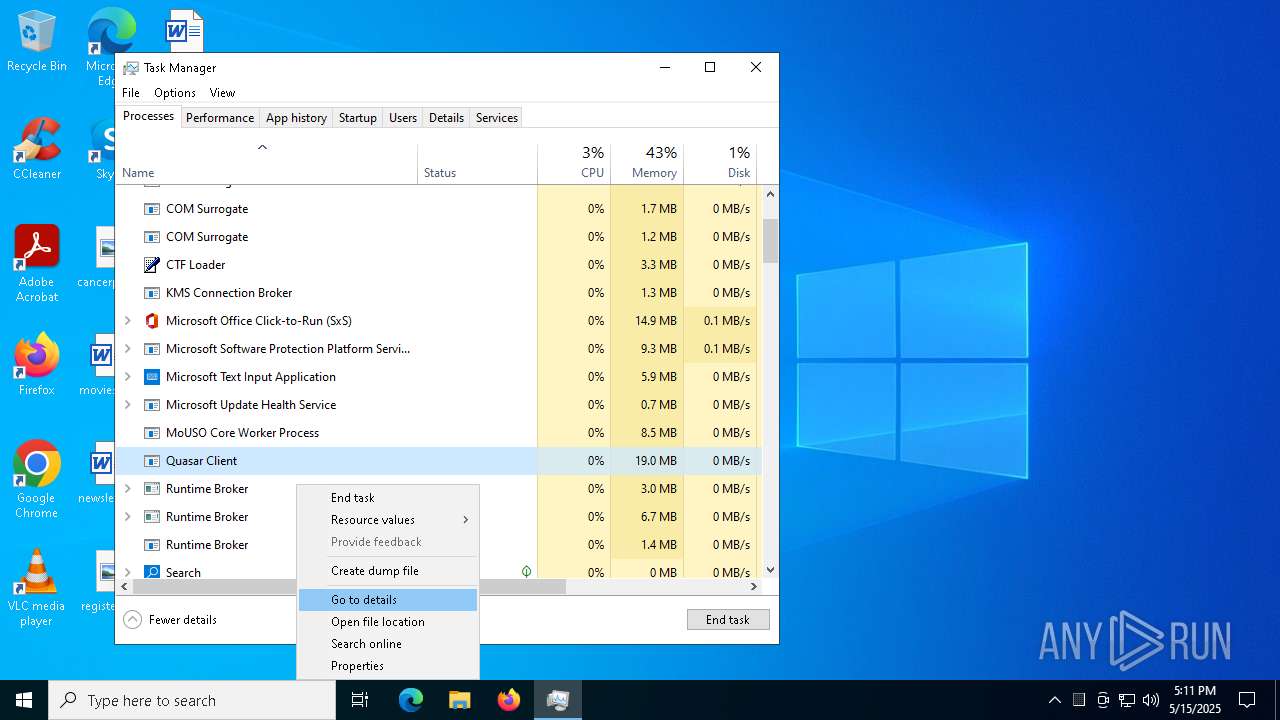
| File name: | Testowy.zip |
| Full analysis: | https://app.any.run/tasks/df63afc8-b7bf-4d5e-8742-6a7f454764be |
| Verdict: | Malicious activity |
| Threats: | Quasar is a very popular RAT in the world thanks to its code being available in open-source. This malware can be used to control the victim’s computer remotely. |
| Analysis date: | May 15, 2025, 17:09:39 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
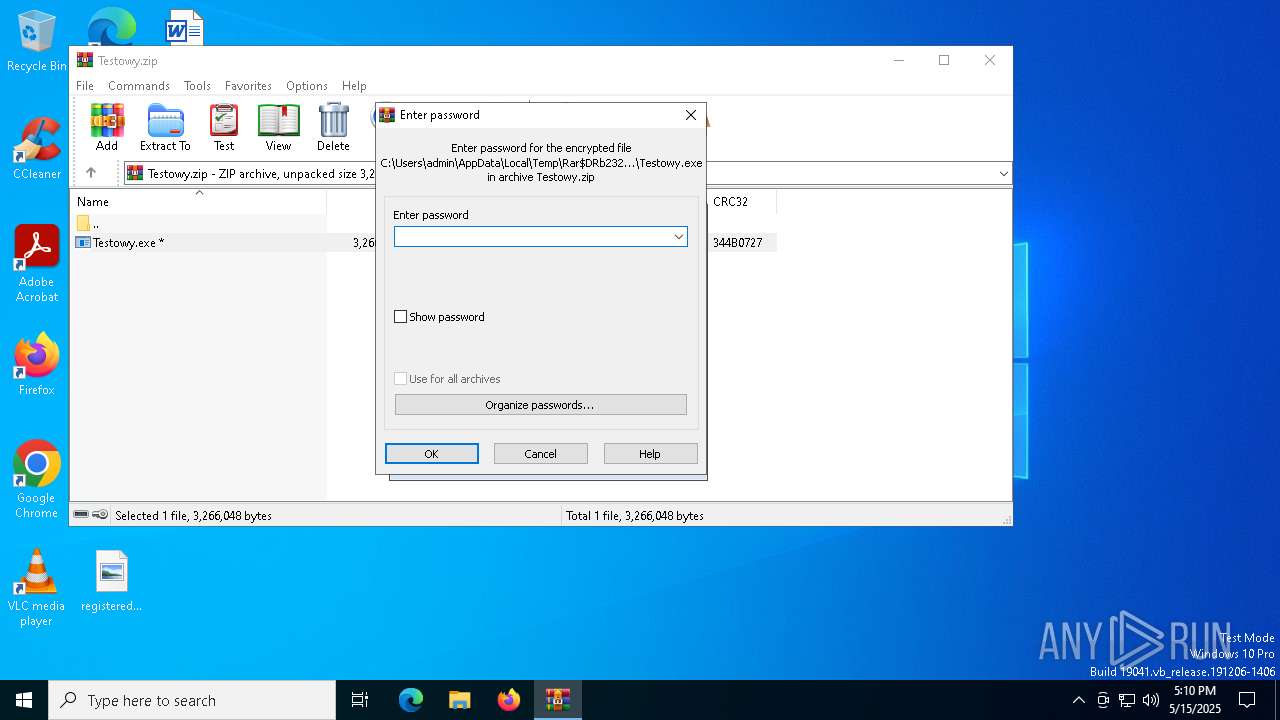
| File info: | Zip archive data, at least v2.0 to extract, compression method=AES Encrypted |
| MD5: | 7F01174A39831A668E1A496E71B45152 |
| SHA1: | BF641E15B27307DA8CCC09CFC55C74B866FCB0ED |
| SHA256: | 6440023B69DCCA8AE9F0EF2B5B08F6A70671040D0EBCB28CAD705A98532F2826 |
| SSDEEP: | 49152:hbhynFljmCPLTajTbttKUQFs1oemXUUmxN2MoWGsb/piuRxIexVie9rI0dRdikI+:hIFJmCfaPbbkImE5xJGsrpiwxIy3rr7J |
MALICIOUS
Uses Task Scheduler to autorun other applications
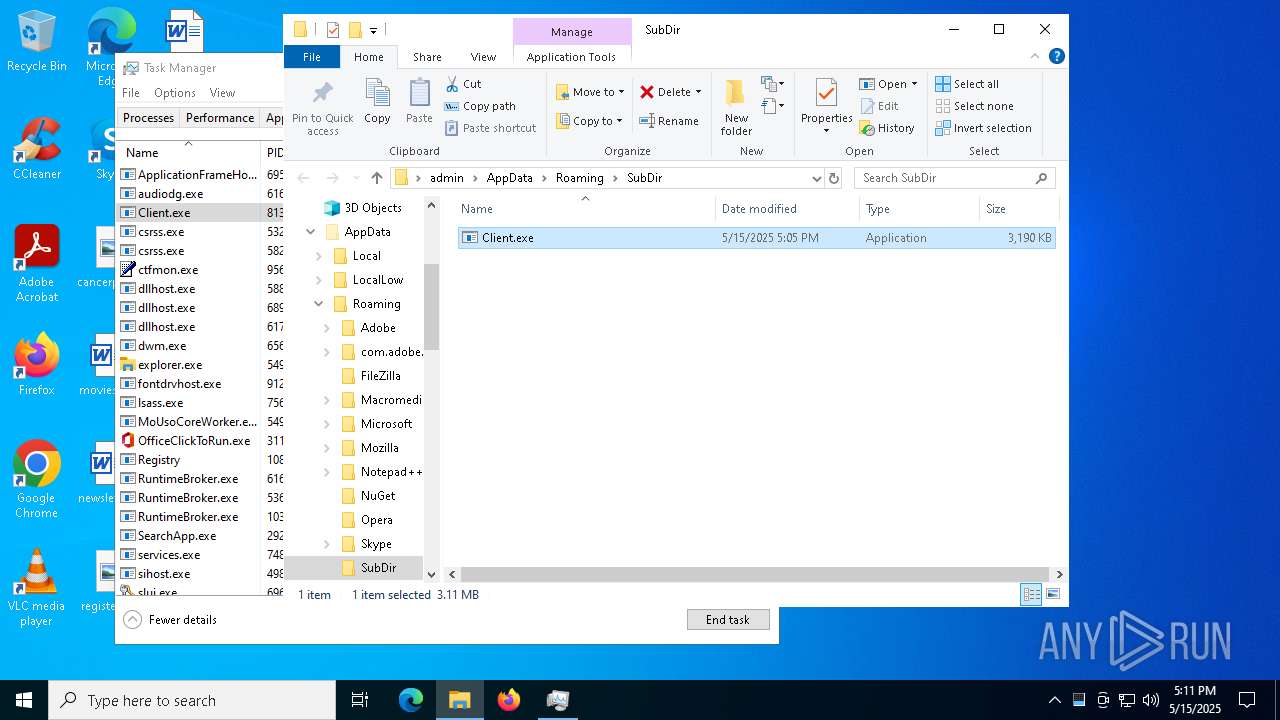
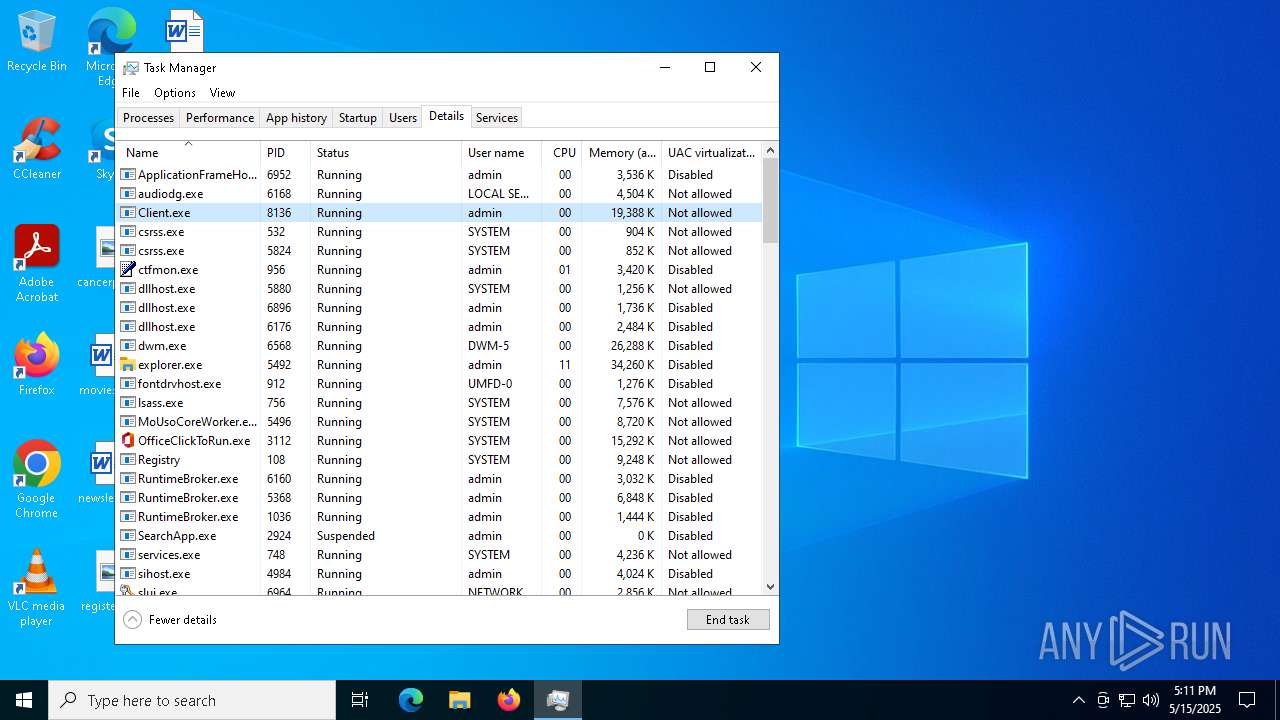
- Testowy.exe (PID: 7884)
- Client.exe (PID: 8136)
QUASAR has been detected (YARA)
- Client.exe (PID: 8136)
SUSPICIOUS
Executable content was dropped or overwritten
- Testowy.exe (PID: 7884)
Starts itself from another location
- Testowy.exe (PID: 7884)
There is functionality for taking screenshot (YARA)
- Client.exe (PID: 8136)
Connects to unusual port
- Client.exe (PID: 8136)
INFO
Manual execution by a user
- Testowy.exe (PID: 7884)
- Testowy.exe (PID: 1040)
- Taskmgr.exe (PID: 6068)
- Taskmgr.exe (PID: 5988)
- Client.exe (PID: 6192)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2320)
Reads the machine GUID from the registry
- Testowy.exe (PID: 7884)
- Client.exe (PID: 8136)
- Testowy.exe (PID: 1040)
- Client.exe (PID: 6192)
Checks supported languages
- Testowy.exe (PID: 7884)
- Client.exe (PID: 8136)
- Testowy.exe (PID: 1040)
- Client.exe (PID: 6192)
Reads Environment values
- Testowy.exe (PID: 7884)
- Client.exe (PID: 8136)
- Testowy.exe (PID: 1040)
- Client.exe (PID: 6192)
Reads the computer name
- Testowy.exe (PID: 7884)
- Client.exe (PID: 8136)
- Testowy.exe (PID: 1040)
- Client.exe (PID: 6192)
Creates files or folders in the user directory
- Testowy.exe (PID: 7884)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 5988)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Quasar
(PID) Process(8136) Client.exe
Version1.4.1
C2 (2)213.134.190.18:4782
Sub_DirSubDir
Install_NameClient.exe
Mutex1f265eea-5c30-48c2-a6cf-6ebaa5287da7
StartupQuasar Client Startup
TagTestMarcin01
LogDirLogs
SignatureC8phl3ATEznYLynH3HKAisi4oXnKlsswvjV/hE3MWvlKkXngBC0mTcLrJ2M+wM1vwZzq+CcqPB+sKCngox8723LR9j7O+egtMLBK1xPzSEAXdM9vGg9rr677iRIPmwHbhhYumuyaHejhwDCwLxvQvXNOjc8fXcOIjPoWqP2B4VLAZhqeqyQymgLvz6zYMmPKgccrcb3QQ6l3i1o/odAWGB2NxT/sPwwf2yt+lG0QsfMIfRGytKQ9O3lL5IHBpNaWqQgNNBN4gGh3ze47tpu4WbS+drN5xdcL2S7bB1339tsC...
CertificateMIIE9DCCAtygAwIBAgIQAPWt5S5ZA0gf0iId7KdLhzANBgkqhkiG9w0BAQ0FADAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMCAXDTI1MDUxMzE2NTQwNVoYDzk5OTkxMjMxMjM1OTU5WjAbMRkwFwYDVQQDDBBRdWFzYXIgU2VydmVyIENBMIICIjANBgkqhkiG9w0BAQEFAAOCAg8AMIICCgKCAgEAmRIFy3SLnHO1nhcfXfp3em9vWYvqsjzqo1+OvU4opT55bVHiGQqO1+Xva0XJ9t1MBM9QJBHb...
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2025:05:15 19:05:02 |
| ZipCRC: | 0x344b0727 |
| ZipCompressedSize: | 1209107 |
| ZipUncompressedSize: | 3266048 |
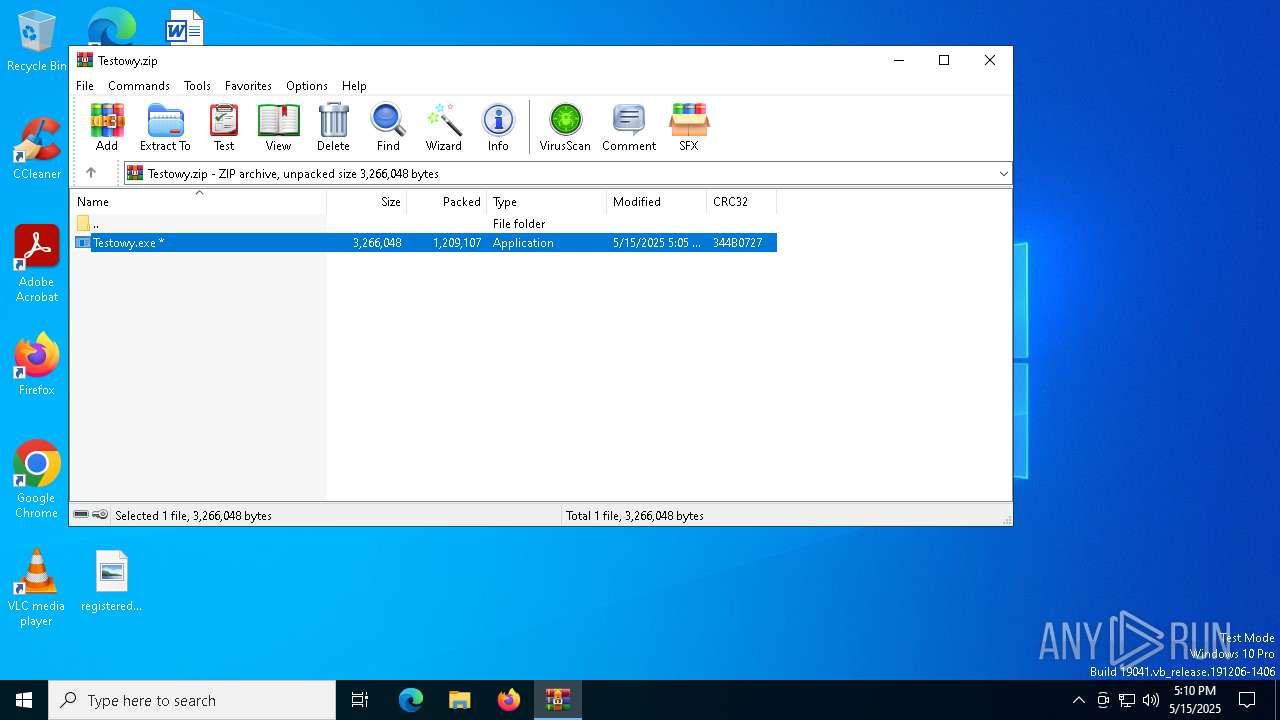
| ZipFileName: | Testowy.exe |
Total processes
147
Monitored processes
13
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1040 | "C:\Users\admin\Desktop\Testowy.exe" | C:\Users\admin\Desktop\Testowy.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Quasar Client Exit code: 2 Version: 1.4.1 Modules
| |||||||||||||||
| 1128 | "schtasks" /create /tn "Quasar Client Startup" /sc ONLOGON /tr "C:\Users\admin\AppData\Roaming\SubDir\Client.exe" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | Client.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1180 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1328 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2320 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Testowy.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 5988 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6068 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6192 | "C:\Users\admin\AppData\Roaming\SubDir\Client.exe" | C:\Users\admin\AppData\Roaming\SubDir\Client.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Quasar Client Exit code: 2 Version: 1.4.1 Modules
| |||||||||||||||
| 7884 | "C:\Users\admin\Desktop\Testowy.exe" | C:\Users\admin\Desktop\Testowy.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Quasar Client Exit code: 3 Version: 1.4.1 Modules
| |||||||||||||||
Total events
4 492
Read events
4 470
Write events
21
Delete events
1
Modification events
| (PID) Process: | (2320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Testowy.zip | |||
| (PID) Process: | (2320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2320) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
2
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5988 | Taskmgr.exe | C:\Users\admin\AppData\Local\D3DSCache\3534848bb9f4cb71\F4EB2D6C-ED2B-4BDD-AD9D-F913287E6768.lock | text | |
MD5:F49655F856ACB8884CC0ACE29216F511 | SHA256:7852FCE59C67DDF1D6B8B997EAA1ADFAC004A9F3A91C37295DE9223674011FBA | |||
| 7884 | Testowy.exe | C:\Users\admin\AppData\Roaming\SubDir\Client.exe | executable | |
MD5:D74762443C94EA11D7E16EF4885D6B13 | SHA256:7D409F8691C72147D07183E15E6692311030A3DCFEB606BE1AF960AE98FC5A5D | |||
| 2320 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2320.31052\Testowy.exe | executable | |
MD5:D74762443C94EA11D7E16EF4885D6B13 | SHA256:7D409F8691C72147D07183E15E6692311030A3DCFEB606BE1AF960AE98FC5A5D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
23
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7892 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7892 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3304 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |