| File name: | HSBC Payment Advice.xls |
| Full analysis: | https://app.any.run/tasks/bcf96db2-85c1-430f-ae3f-15d04fc06a76 |
| Verdict: | Malicious activity |
| Threats: | GuLoader is an advanced downloader written in shellcode. It’s used by criminals to distribute other malware, notably trojans, on a large scale. It’s infamous for using anti-detection and anti-analysis capabilities. |
| Analysis date: | May 09, 2024, 00:17:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-excel |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, Code page: 1252, Name of Creating Application: Microsoft Excel, Create Time/Date: Sat Sep 16 00:00:00 2006, Last Saved Time/Date: Wed May 8 09:07:17 2024, Security: 1 |
| MD5: | BF5ED68E4639C6C8CE1A8F223A86B575 |
| SHA1: | 1E10534D92D9B98D8C7DAB9BB15F4F3355A6ED0A |
| SHA256: | 6423DE0A6A5AC517F691CACF849C3E9E660BDCD7190D2CE14B40EE4C9F0A0D18 |
| SSDEEP: | 6144:1TnXWrPOxIEsozUpdvU38u/YdZoDoChPRY0BeQees1RXu:1DXCOxIEsoMduDYdZeRYJemU |
MALICIOUS
Equation Editor starts application (likely CVE-2017-11882)
- EQNEDT32.EXE (PID: 1852)
Drops the executable file immediately after the start
- EQNEDT32.EXE (PID: 1852)
- hjv.exe (PID: 1884)
Suspicious connection from the Equation Editor
- EQNEDT32.EXE (PID: 1852)
GULOADER SHELLCODE has been detected (YARA)
- hjv.exe (PID: 1884)
GULOADER has been detected (YARA)
- hjv.exe (PID: 1884)
SUSPICIOUS
Reads security settings of Internet Explorer
- EQNEDT32.EXE (PID: 1852)
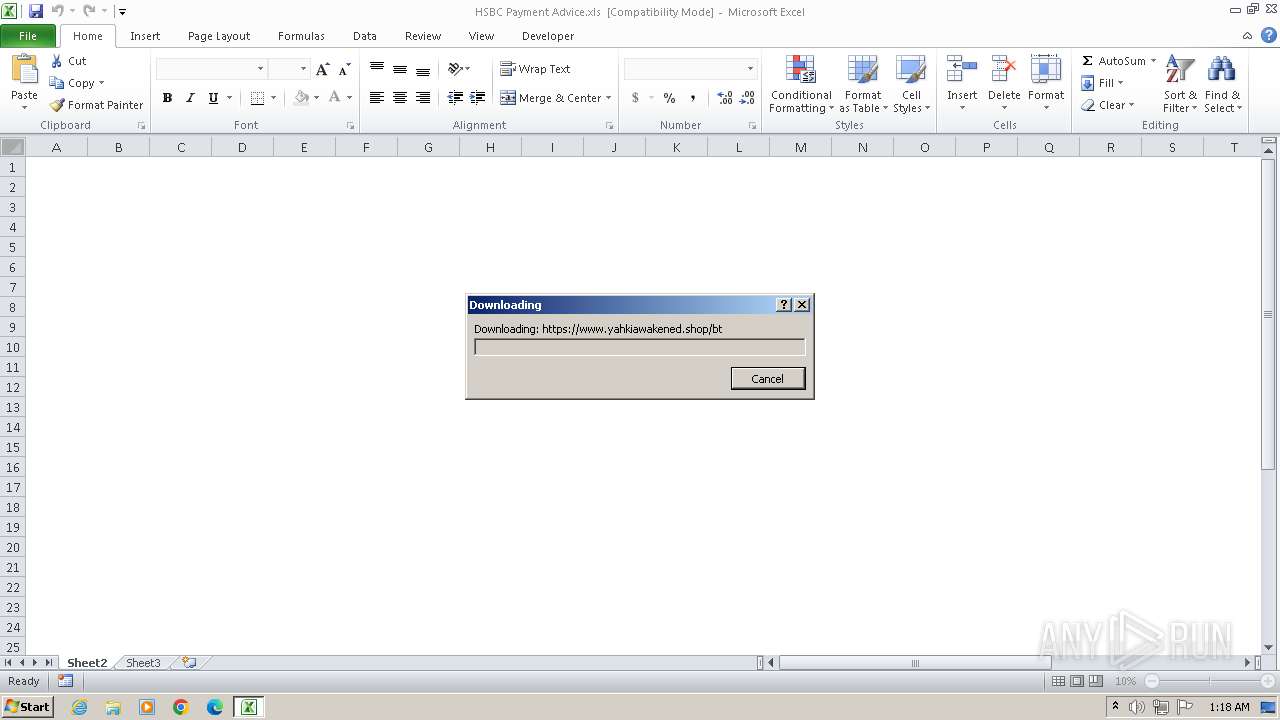
Connects to the server without a host name
- WINWORD.EXE (PID: 2024)
- EQNEDT32.EXE (PID: 1852)
Process requests binary or script from the Internet
- EQNEDT32.EXE (PID: 1852)
Executable content was dropped or overwritten
- EQNEDT32.EXE (PID: 1852)
- hjv.exe (PID: 1884)
Malware-specific behavior (creating "System.dll" in Temp)
- hjv.exe (PID: 1884)
The process creates files with name similar to system file names
- hjv.exe (PID: 1884)
Reads the Internet Settings
- EQNEDT32.EXE (PID: 1852)
INFO
Reads the computer name
- wmpnscfg.exe (PID: 308)
- hjv.exe (PID: 1884)
- EQNEDT32.EXE (PID: 1852)
Manual execution by a user
- wmpnscfg.exe (PID: 308)
Creates files or folders in the user directory
- EQNEDT32.EXE (PID: 1852)
Checks supported languages
- hjv.exe (PID: 1884)
- wmpnscfg.exe (PID: 308)
- EQNEDT32.EXE (PID: 1852)
Create files in a temporary directory
- hjv.exe (PID: 1884)
Reads the machine GUID from the registry
- EQNEDT32.EXE (PID: 1852)
Checks proxy server information
- EQNEDT32.EXE (PID: 1852)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
guloader
(PID) Process(1884) hjv.exe
C2 (1)http://www.qeintechnologies.com/NmBkxeAZlIrfpt226.bin
Strings (23)\Microsoft.NET\Framework\\msbuild.exe
_Yc
Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:121.0) Gecko/20100101 Firefox/121.0
wininet.dll
KERNELBASE.DLL
Msi.dll
psapi.dll
user32
advapi32
shell32
Publisher
windir=
TEMP=
mshtml.dll
SYSTEM\ControlSet001\Enum\ACPI\PNP0C0C
\system32\
\syswow64\
Startup key
Software\Microsoft\Windows\CurrentVersion\RunOnce
C:\Program Files\qga\qga.exe
C:\Program Files\Qemu-ga\qemu-ga.exe
CONOUT$
CONIN$
TRiD
| .xls | | | Microsoft Excel sheet (78.9) |
|---|
EXIF
FlashPix
| LastPrinted: | 2020:01:14 14:57:59 |
|---|---|
| ThumbnailClip: | (Binary data 21388 bytes, use -b option to extract) |
| Company: | - |
| Author: | - |
| LastModifiedBy: | - |
| Software: | Microsoft Excel |
| CreateDate: | 2006:09:16 00:00:00 |
| ModifyDate: | 2024:05:08 09:07:17 |
| Security: | Password protected |
| CodePage: | Windows Latin 1 (Western European) |
| AppVersion: | 12 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: |
|
| HeadingPairs: |
|
| CompObjUserTypeLen: | 38 |
| CompObjUserType: | Microsoft Office Excel 2003 Worksheet |
Total processes
45
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 308 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1852 | "C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE" -Embedding | C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE | svchost.exe | ||||||||||||
User: admin Company: Design Science, Inc. Integrity Level: MEDIUM Description: Microsoft Equation Editor Exit code: 0 Version: 00110900 Modules
| |||||||||||||||
| 1884 | "C:\Users\admin\AppData\Roaming\hjv.exe" | C:\Users\admin\AppData\Roaming\hjv.exe | EQNEDT32.EXE | ||||||||||||
User: admin Company: uddelighed havingness Integrity Level: MEDIUM Modules
guloader(PID) Process(1884) hjv.exe C2 (1)http://www.qeintechnologies.com/NmBkxeAZlIrfpt226.bin Strings (23)\Microsoft.NET\Framework\\msbuild.exe _Yc Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:121.0) Gecko/20100101 Firefox/121.0 wininet.dll KERNELBASE.DLL Msi.dll psapi.dll user32 advapi32 shell32 Publisher windir= TEMP= mshtml.dll SYSTEM\ControlSet001\Enum\ACPI\PNP0C0C \system32\ \syswow64\ Startup key Software\Microsoft\Windows\CurrentVersion\RunOnce C:\Program Files\qga\qga.exe C:\Program Files\Qemu-ga\qemu-ga.exe CONOUT$ CONIN$ | |||||||||||||||
| 2024 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" -Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3976 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
18 475
Read events
17 219
Write events
692
Delete events
564
Modification events
| (PID) Process: | (3976) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | j? |
Value: 7F6A3F00880F0000010000000000000000000000 | |||
| (PID) Process: | (3976) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3976) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3976) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3976) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3976) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3976) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3976) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3976) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3976) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
3
Suspicious files
30
Text files
5
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3976 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR3EDF.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2024 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR4A88.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2024 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\FSD-CNRY.FSD | — | |
MD5:— | SHA256:— | |||
| 2024 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\LocalCacheFileEditManager\FSD-CNRY.FSD | — | |
MD5:— | SHA256:— | |||
| 3976 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | der | |
MD5:098E3FFF2705346ECE787C21AC03D0F3 | SHA256:16ED7A2C43F928BCC7EC8F7E93082ABDA7106A63B87E747DCCA57F1CEE05CCC9 | |||
| 3976 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | binary | |
MD5:4A9AE9538FA1ECC7878153183BA62586 | SHA256:41214BFA1190A4A9B2B5B9294E70B493692A4F46C669BD45F38D2245632EACBD | |||
| 3976 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | der | |
MD5:8202A1CD02E7D69597995CABBE881A12 | SHA256:58F381C3A0A0ACE6321DA22E40BD44A597BD98B9C9390AB9258426B5CF75A7A5 | |||
| 3976 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\6D0BC7DC.emf | binary | |
MD5:D1041285BC749446173E17967C0F1995 | SHA256:C767B9E9F3B3303898E1B9B746A3502BA121E56520FAB21BCDD1C748AEC68E22 | |||
| 3976 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:DD2FF0BDEC5A64F49ED239DB8CEDC0BC | SHA256:3E0517AAE5241AC36E853A331B01C8097D1A4314BA6D27FDC6493CD68103EC0B | |||
| 2024 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{AC211262-1DA7-4F65-88D1-3FE1CBE3413E} | binary | |
MD5:4BF10F3DDBADAEB9B3DC542AC84F5D8E | SHA256:160DA107AB6B82396631B25B84C69255A3C9E969D9536B77DB5BCADF3C997C5B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
15
DNS requests
4
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3976 | EXCEL.EXE | GET | 200 | 142.250.184.227:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | unknown |
3976 | EXCEL.EXE | GET | 304 | 2.21.240.200:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?2e6f53ba3d3c2c74 | unknown | — | — | unknown |
3976 | EXCEL.EXE | GET | 200 | 142.250.184.227:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | — | — | unknown |
3976 | EXCEL.EXE | GET | 200 | 172.245.208.36:80 | http://172.245.208.36/xampp/bg/verygoodnewisshewasreadytomarrythepersonwhoshelovedalotwithentirethingssheisverybeautifulwomenwhosheloved____sheisbeautifulgirlssheis.doc | unknown | — | — | unknown |
2024 | WINWORD.EXE | HEAD | 200 | 172.245.208.36:80 | http://172.245.208.36/xampp/bg/verygoodnewisshewasreadytomarrythepersonwhoshelovedalotwithentirethingssheisverybeautifulwomenwhosheloved____sheisbeautifulgirlssheis.doc | unknown | — | — | unknown |
1088 | svchost.exe | GET | 304 | 2.21.240.200:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?cf4d0ada8a8d9c72 | unknown | — | — | unknown |
1852 | EQNEDT32.EXE | GET | 200 | 172.245.208.36:80 | http://172.245.208.36/20777/hjv.exe | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3976 | EXCEL.EXE | 172.67.170.209:443 | www.yahkiawakened.shop | CLOUDFLARENET | US | unknown |
3976 | EXCEL.EXE | 2.21.240.200:80 | ctldl.windowsupdate.com | Akamai International B.V. | SE | unknown |
3976 | EXCEL.EXE | 142.250.184.227:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
3976 | EXCEL.EXE | 172.245.208.36:80 | — | AS-COLOCROSSING | US | unknown |
2024 | WINWORD.EXE | 172.67.170.209:443 | www.yahkiawakened.shop | CLOUDFLARENET | US | unknown |
840 | svchost.exe | 172.67.170.209:443 | www.yahkiawakened.shop | CLOUDFLARENET | US | unknown |
2024 | WINWORD.EXE | 172.245.208.36:80 | — | AS-COLOCROSSING | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.yahkiawakened.shop |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3976 | EXCEL.EXE | Potentially Bad Traffic | ET INFO Dotted Quad Host DOC Request |
3976 | EXCEL.EXE | Misc Attack | EXPLOIT [ANY.RUN] Obfuscated RTF document including the CLSID of the Equation Editor (CVE-2017-11882) |
— | — | Potentially Bad Traffic | ET INFO Dotted Quad Host DOC Request |
— | — | Misc activity | ET USER_AGENTS Microsoft Office Existence Discovery User-Agent |
1852 | EQNEDT32.EXE | Potentially Bad Traffic | ET INFO Executable Download from dotted-quad Host |
1852 | EQNEDT32.EXE | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |
1852 | EQNEDT32.EXE | A Network Trojan was detected | ET MALWARE Likely Evil EXE download from dotted Quad by MSXMLHTTP M1 |
— | — | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
— | — | A Network Trojan was detected | ET MALWARE Likely Evil EXE download from dotted Quad by MSXMLHTTP M2 |
— | — | Potentially Bad Traffic | ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response |