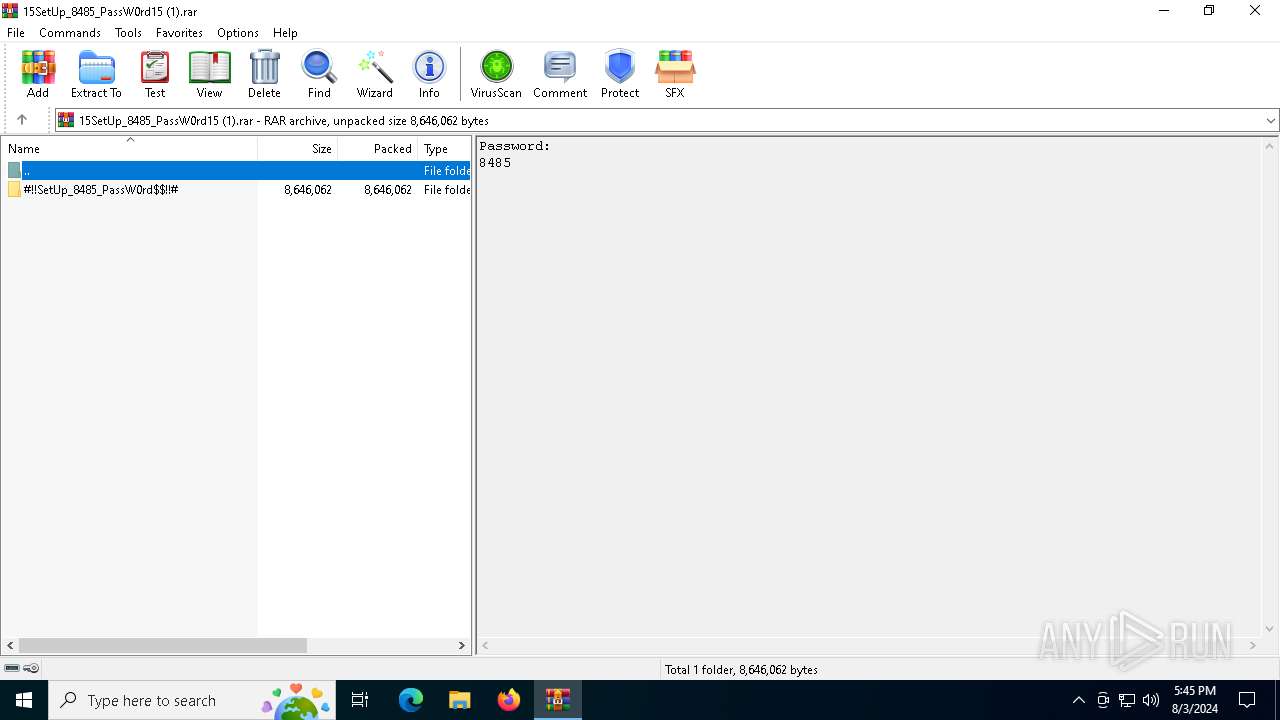
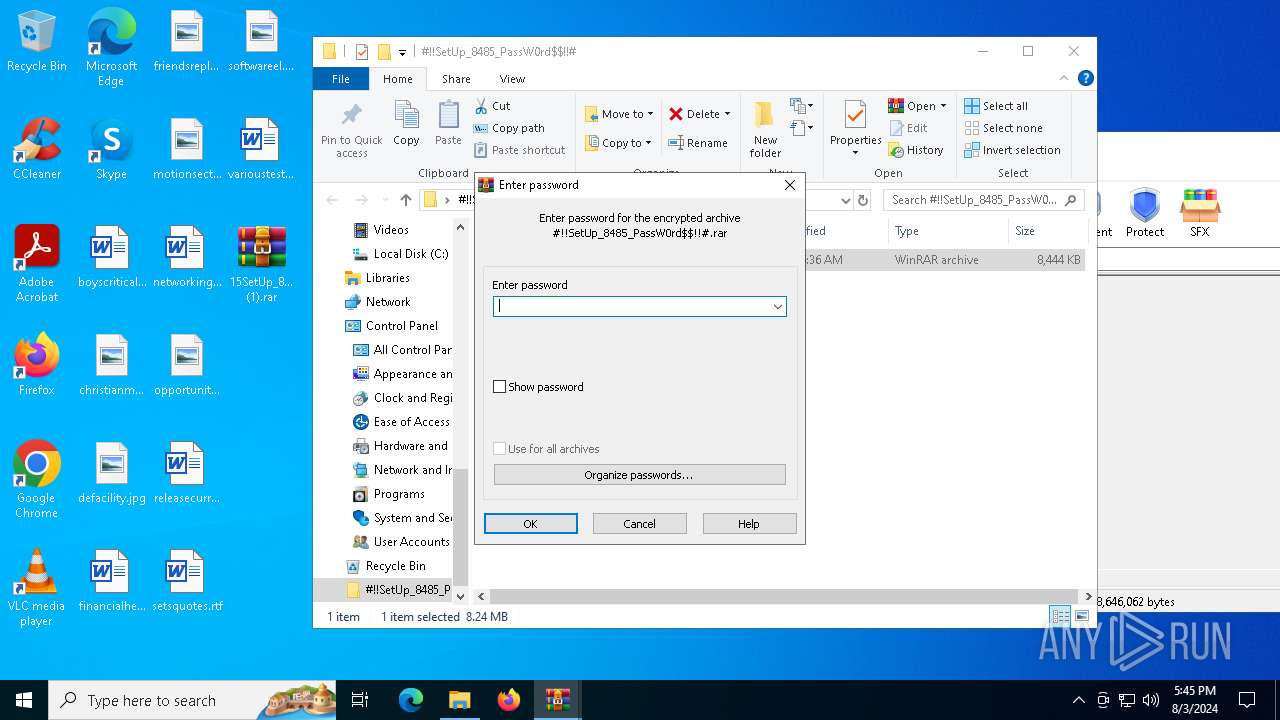
| File name: | 15SetUp_8485_PassW0rd15 (1).rar |
| Full analysis: | https://app.any.run/tasks/e4e9a585-33dd-4d64-a629-bba59b7131e8 |
| Verdict: | Malicious activity |
| Threats: | CryptBot is an advanced Windows-targeting infostealer delivered via pirate sites with "cracked" software. It has been first observed in the wild in 2019. |
| Analysis date: | August 03, 2024, 17:45:10 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | FA94F306588989FDB1E9556B7247C807 |
| SHA1: | BE6D4AD045079516C67F60578D8718CAC956F340 |
| SHA256: | 63EF571D12EB121FF621B70B3F71A4E2E73396078D9DA6BDB4B42A670AF0AB11 |
| SSDEEP: | 98304:68HeUZapaWLKEZYLYt06s1mtXJVCowO6sYjI8QVr9MtHeZND5kuX6gL2dA3QZ3V3:FgQR5N9CkQQDiiJZPPCWp |
MALICIOUS
CRYPTBOT has been detected (SURICATA)
- run.exe (PID: 6172)
Connects to the CnC server
- run.exe (PID: 6172)
Actions looks like stealing of personal data
- run.exe (PID: 6172)
SUSPICIOUS
Searches for installed software
- run.exe (PID: 6172)
Process drops legitimate windows executable
- WinRAR.exe (PID: 5796)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5796)
Manual execution by a user
- WinRAR.exe (PID: 5796)
- run.exe (PID: 6172)
Checks supported languages
- run.exe (PID: 6172)
Reads CPU info
- run.exe (PID: 6172)
Reads the computer name
- run.exe (PID: 6172)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 5796)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
132
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5796 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\#!!SetUp_8485_PassW0rd$!!#\#!!SetUp_8485_PassW0rd$!!#.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6172 | "C:\Users\admin\Desktop\#!!SetUp_8485_PassW0rd$!!#\#!!SetUp_8485_PassW0rd$!!#\run.exe" | C:\Users\admin\Desktop\#!!SetUp_8485_PassW0rd$!!#\#!!SetUp_8485_PassW0rd$!!#\run.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6456 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\15SetUp_8485_PassW0rd15 (1).rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6756 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 797
Read events
7 767
Write events
30
Delete events
0
Modification events
| (PID) Process: | (6456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\15SetUp_8485_PassW0rd15 (1).rar | |||
| (PID) Process: | (6456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6456) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5796) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (5796) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
Executable files
14
Suspicious files
3
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6456 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6456.43850\#!!SetUp_8485_PassW0rd$!!#\#!!SetUp_8485_PassW0rd$!!#.rar | — | |
MD5:— | SHA256:— | |||
| 5796 | WinRAR.exe | C:\Users\admin\Desktop\#!!SetUp_8485_PassW0rd$!!#\#!!SetUp_8485_PassW0rd$!!#\plugins\lang-1049.dll | executable | |
MD5:0AC98A4BFC717523E344010A42C2F4BA | SHA256:68546336232AA2BE277711AFA7C1F08ECD5FCC92CC182F90459F0C61FB39507F | |||
| 5796 | WinRAR.exe | C:\Users\admin\Desktop\#!!SetUp_8485_PassW0rd$!!#\#!!SetUp_8485_PassW0rd$!!#\run.exe | executable | |
MD5:3697E8A9CBA73E1D1324A5270FFA8A52 | SHA256:77B6A8F25AF26DC5495B29ED423459A5A723B136D1E2022CD88CE3C103F3E8DD | |||
| 5796 | WinRAR.exe | C:\Users\admin\Desktop\#!!SetUp_8485_PassW0rd$!!#\#!!SetUp_8485_PassW0rd$!!#\plugins\Microsoft.VisualStudio.VsWebProtocol | executable | |
MD5:91ACF072FE60B3EF9867FAEC1A7A8CB0 | SHA256:1F49ADC807A564E7C1ECF32F58074A1230A6FE4764E8F54CE7FFA8C2E880DCCA | |||
| 5796 | WinRAR.exe | C:\Users\admin\Desktop\#!!SetUp_8485_PassW0rd$!!#\#!!SetUp_8485_PassW0rd$!!#\plugins\lang-1058.dll | executable | |
MD5:41C75E831A5571C3F72287794391A0E6 | SHA256:B3AD99AFDAEE3B9365E7A3FFCC44C2761E22A4F92DFF5E5EFDC52F6B08EA0105 | |||
| 5796 | WinRAR.exe | C:\Users\admin\Desktop\#!!SetUp_8485_PassW0rd$!!#\#!!SetUp_8485_PassW0rd$!!#\plugins\StartupHelper | executable | |
MD5:14934CACA84D5FE0288F27EFB31DCBF8 | SHA256:7FA86147035627BAE39576BCBE619D045E94A48C4DB8CA131968C20BB4DE4A36 | |||
| 5796 | WinRAR.exe | C:\Users\admin\Desktop\#!!SetUp_8485_PassW0rd$!!#\#!!SetUp_8485_PassW0rd$!!#\carferry.flv | binary | |
MD5:16A30926E4EBC495D3659854C3731F63 | SHA256:DC260B93C358E10FC6F74C0B9F487DD0C2FD58E791EC5B0925B0546258923B36 | |||
| 5796 | WinRAR.exe | C:\Users\admin\Desktop\#!!SetUp_8485_PassW0rd$!!#\#!!SetUp_8485_PassW0rd$!!#\plugins\FlowSshC32.dll | executable | |
MD5:C4C176F948AAEFDBAC2007BE7540F807 | SHA256:B7CE745085DA1EA321BA210178F90C7FBDA7419A64452A887219B6FDC7EF762C | |||
| 5796 | WinRAR.exe | C:\Users\admin\Desktop\#!!SetUp_8485_PassW0rd$!!#\#!!SetUp_8485_PassW0rd$!!#\rtl120.bpl | executable | |
MD5:ADF82ED333FB5567F8097C7235B0E17F | SHA256:D6DD7A4F46F2CFDE9C4EB9463B79D5FF90FC690DA14672BA1DA39708EE1B9B50 | |||
| 5796 | WinRAR.exe | C:\Users\admin\Desktop\#!!SetUp_8485_PassW0rd$!!#\#!!SetUp_8485_PassW0rd$!!#\plugins\NvStWiz | executable | |
MD5:9E82E3B658393BED3F7E4F090DF1FBE7 | SHA256:C2AD5BD189DF04B39BE18DEC5CD251CF79B066010706AD26D99DF7E49FD07762 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
40
DNS requests
16
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4540 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4540 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6816 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6844 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6172 | run.exe | POST | 200 | 80.249.145.207:80 | http://fifx15pt.top/v1/upload.php | unknown | — | — | unknown |
6884 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6172 | run.exe | POST | 200 | 80.249.145.207:80 | http://fifx15pt.top/v1/upload.php | unknown | — | — | unknown |
6172 | run.exe | POST | 200 | 80.249.145.207:80 | http://fifx15pt.top/v1/upload.php | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4084 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1184 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5336 | SearchApp.exe | 104.126.37.130:443 | www.bing.com | Akamai International B.V. | DE | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4540 | svchost.exe | 20.190.159.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
th.bing.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
6172 | run.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
6172 | run.exe | A Network Trojan was detected | ET MALWARE Win32/Cryptbotv2 CnC Activity (POST) M4 |
6172 | run.exe | A Network Trojan was detected | ET MALWARE Win32/Cryptbotv2 CnC Activity (POST) M4 |
6172 | run.exe | A Network Trojan was detected | ET MALWARE Win32/Cryptbotv2 CnC Activity (POST) M4 |