| File name: | NewOrder0578657875678788.exe |
| Full analysis: | https://app.any.run/tasks/0876077f-2708-4c32-a65d-2edb7de658a9 |
| Verdict: | Malicious activity |
| Threats: | DBatLoader is a loader malware used for distributing payloads of different types, including WarzoneRAT and Formbook. It is employed in multi-stage attacks that usually start with a phishing email carrying a malicious attachment. |
| Analysis date: | August 04, 2023, 21:16:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 2AF0D9CF826C6FB7A97F0B2AA092C6C2 |
| SHA1: | F4EB081A9D62D7448F8478602C67781BA35BBD5B |
| SHA256: | 63EF4597DD8F8958AB0C9C5F486E98A1BC7DE071927925F413A184A48178D017 |
| SSDEEP: | 24576:n8L2PlTQaGGtmlF/w/NConLI6HpJ/W7Dfavrjnpia2++:8LeqI/NCCLrW7mvrZ2++ |
MALICIOUS
DBATLOADER detected by memory dumps
- NewOrder0578657875678788.exe.scr (PID: 2692)
Application was dropped or rewritten from another process
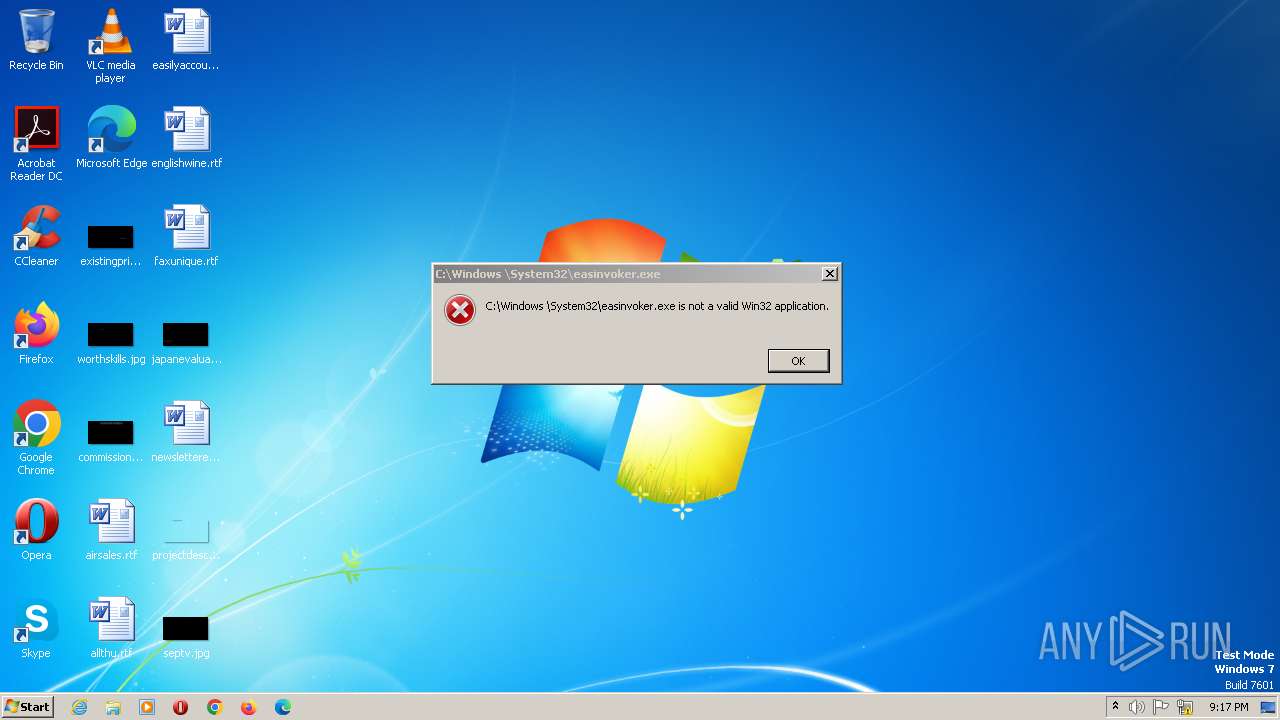
- easinvoker.exe (PID: 2228)
- easinvoker.exe (PID: 2044)
Connects to the CnC server
- colorcpl.exe (PID: 2928)
REMCOS was detected
- colorcpl.exe (PID: 2928)
Actions looks like stealing of personal data
- NewOrder0578657875678788.exe.scr (PID: 2692)
REMCOS detected by memory dumps
- colorcpl.exe (PID: 2928)
SUSPICIOUS
Executable content was dropped or overwritten
- NewOrder0578657875678788.exe.scr (PID: 2692)
- xcopy.exe (PID: 2820)
- xcopy.exe (PID: 1936)
Reads the Internet Settings
- NewOrder0578657875678788.exe.scr (PID: 2692)
- cmd.exe (PID: 1748)
- colorcpl.exe (PID: 2928)
Reads settings of System Certificates
- NewOrder0578657875678788.exe.scr (PID: 2692)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 1748)
- NewOrder0578657875678788.exe.scr (PID: 2692)
Executing commands from a ".bat" file
- NewOrder0578657875678788.exe.scr (PID: 2692)
Application launched itself
- cmd.exe (PID: 1748)
Connects to unusual port
- colorcpl.exe (PID: 2928)
Writes files like Keylogger logs
- colorcpl.exe (PID: 2928)
INFO
The process checks LSA protection
- NewOrder0578657875678788.exe.scr (PID: 2692)
- colorcpl.exe (PID: 2928)
Reads the computer name
- NewOrder0578657875678788.exe.scr (PID: 2692)
Checks supported languages
- NewOrder0578657875678788.exe.scr (PID: 2692)
Checks proxy server information
- NewOrder0578657875678788.exe.scr (PID: 2692)
- colorcpl.exe (PID: 2928)
Reads the machine GUID from the registry
- NewOrder0578657875678788.exe.scr (PID: 2692)
Creates files in the program directory
- colorcpl.exe (PID: 2928)
Creates files or folders in the user directory
- colorcpl.exe (PID: 2928)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
DBatLoader
(PID) Process(2692) NewOrder0578657875678788.exe.scr
C2https://onedrive.live.com/download?resid=76CFFFCF704AB84C%211144&authkey=!AJJyyiT_ZZO5Zoo
Remcos
(PID) Process(2928) colorcpl.exe
Hosts (1)moneymagnetjoe.duckdns.org:2404
BotnetRemoteHost
Connect_interval1
Install_flagFalse
Install_HKCU\RunTrue
Install_HKLM\RunTrue
Install_HKLM\Explorer\Run1
Install_HKLM\Winlogon\Shell100000
Setup_path%LOCALAPPDATA%
Copy_fileremcos.exe
Startup_valueFalse
Hide_fileFalse
Mutex_nameRmc-2TR947
Keylog_flag1
Keylog_path%LOCALAPPDATA%
Keylog_filelogs.dat
Keylog_cryptFalse
Hide_keylogFalse
Screenshot_flagFalse
Screenshot_time5
Take_ScreenshotFalse
Screenshot_path%APPDATA%
Screenshot_fileScreenshots
Screenshot_cryptFalse
Mouse_optionFalse
Delete_fileFalse
Audio_record_time5
Audio_path%ProgramFiles%
Audio_dirMicRecords
Connect_delay0
Copy_dirRemcos
Keylog_dirjjjjjjjjjjjjooooooo
TRiD
| .scr | | | Windows screen saver (55.3) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (19) |
| .exe | | | Win16/32 Executable Delphi generic (8.7) |
| .exe | | | Generic Win/DOS Executable (8.4) |
| .exe | | | DOS Executable Generic (8.4) |
EXIF
EXE
| Subsystem: | Windows GUI |
|---|---|
| SubsystemVersion: | 4 |
| ImageVersion: | - |
| OSVersion: | 4 |
| EntryPoint: | 0x77be0 |
| UninitializedDataSize: | - |
| InitializedDataSize: | 670720 |
| CodeSize: | 483840 |
| LinkerVersion: | 2.25 |
| PEType: | PE32 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 19-Jun-1992 22:22:17 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 9 |
| Time date stamp: | 19-Jun-1992 22:22:17 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00073204 | 0x00073400 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.53394 |
.itext | 0x00075000 | 0x00002C28 | 0x00002E00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 5.48724 |
.data | 0x00078000 | 0x00086328 | 0x00086400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.10964 |
.bss | 0x000FF000 | 0x00003720 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.idata | 0x00103000 | 0x00002C22 | 0x00002E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.95447 |
.tls | 0x00106000 | 0x00000034 | 0x00000000 | IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rdata | 0x00107000 | 0x00000018 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 0.210826 |
.reloc | 0x00108000 | 0x00008AE4 | 0x00008C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.67931 |
.rsrc | 0x00111000 | 0x00011C00 | 0x00011C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 3.97188 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 2.6633 | 308 | UNKNOWN | English - United States | RT_CURSOR |
2 | 2.80231 | 308 | UNKNOWN | English - United States | RT_CURSOR |
3 | 3.00046 | 308 | UNKNOWN | English - United States | RT_CURSOR |
4 | 2.56318 | 308 | UNKNOWN | English - United States | RT_CURSOR |
5 | 2.6949 | 308 | UNKNOWN | English - United States | RT_CURSOR |
6 | 2.62527 | 308 | UNKNOWN | English - United States | RT_CURSOR |
7 | 2.91604 | 308 | UNKNOWN | English - United States | RT_CURSOR |
54 | 2.65894 | 5672 | UNKNOWN | UNKNOWN | RT_ICON |
56 | 2.48121 | 3752 | UNKNOWN | UNKNOWN | RT_ICON |
58 | 2.39908 | 2216 | UNKNOWN | UNKNOWN | RT_ICON |
Imports
C:\Windows\System32\ntdll.dll |
Kernel32 |
advapi32.dll |
comctl32.dll |
gdi32.dll |
kernel32.dll |
ntdll |
ole32.dll |
oleaut32.dll |
uRL |
Total processes
42
Monitored processes
11
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1108 | C:\Windows\system32\cmd.exe /S /D /c" ECHO F" | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1600 | xcopy "KDECO.bat" "C:\Windows \System32\" /K /D /H /Y | C:\Windows\SysWOW64\xcopy.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Extended Copy Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1748 | C:\Windows\system32\cmd.exe /c ""C:\Users\Public\Libraries\AnyoyvtqO.bat" " | C:\Windows\SysWOW64\cmd.exe | — | NewOrder0578657875678788.exe.scr | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1908 | C:\Windows\system32\cmd.exe /S /D /c" ECHO F" | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1936 | xcopy "netutils.dll" "C:\Windows \System32\" /K /D /H /Y | C:\Windows\SysWOW64\xcopy.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Extended Copy Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2036 | C:\Windows\system32\cmd.exe /S /D /c" ECHO F" | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2044 | "C:\Windows \System32\easinvoker.exe" | C:\Windows \System32\easinvoker.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Exchange ActiveSync Invoker Exit code: 0 Version: 6.3.9600.17415 (winblue_r4.141028-1500) Modules
| |||||||||||||||
| 2228 | "C:\Windows \System32\easinvoker.exe" | C:\Windows \System32\easinvoker.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Exchange ActiveSync Invoker Exit code: 0 Version: 6.3.9600.17415 (winblue_r4.141028-1500) Modules
| |||||||||||||||
| 2692 | "C:\Users\admin\AppData\Local\Temp\NewOrder0578657875678788.exe.scr" /S | C:\Users\admin\AppData\Local\Temp\NewOrder0578657875678788.exe.scr | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
DBatLoader(PID) Process(2692) NewOrder0578657875678788.exe.scr C2https://onedrive.live.com/download?resid=76CFFFCF704AB84C%211144&authkey=!AJJyyiT_ZZO5Zoo | |||||||||||||||
| 2820 | xcopy "easinvoker.exe" "C:\Windows \System32\" /K /D /H /Y | C:\Windows\SysWOW64\xcopy.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Extended Copy Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 093
Read events
1 068
Write events
25
Delete events
0
Modification events
| (PID) Process: | (2692) NewOrder0578657875678788.exe.scr | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\155\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1748) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1748) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1748) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1748) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2928) colorcpl.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2928) colorcpl.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000096000000010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2928) colorcpl.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2928) colorcpl.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2928) colorcpl.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
Executable files
5
Suspicious files
2
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2692 | NewOrder0578657875678788.exe.scr | C:\Users\Public\Libraries\AnyoyvtqO.bat | text | |
MD5:55ABA243E88F6A6813C117FFE1FA5979 | SHA256:5A11C5641C476891AA30E7ECFA57C2639F6827D8640061F73E9AFEC0ADBBD7D2 | |||
| 2692 | NewOrder0578657875678788.exe.scr | C:\Users\Public\Libraries\Anyoyvtq.PIF | executable | |
MD5:2AF0D9CF826C6FB7A97F0B2AA092C6C2 | SHA256:63EF4597DD8F8958AB0C9C5F486E98A1BC7DE071927925F413A184A48178D017 | |||
| 2692 | NewOrder0578657875678788.exe.scr | C:\Users\Public\Libraries\easinvoker.exe | executable | |
MD5:231CE1E1D7D98B44371FFFF407D68B59 | SHA256:30951DB8BFC21640645AA9144CFEAA294BB7C6980EF236D28552B6F4F3F92A96 | |||
| 2692 | NewOrder0578657875678788.exe.scr | C:\Users\Public\Libraries\KDECO.bat | text | |
MD5:213C60ADF1C9EF88DC3C9B2D579959D2 | SHA256:37C59C8398279916CFCE45F8C5E3431058248F5E3BEF4D9F5C0F44A7D564F82E | |||
| 2692 | NewOrder0578657875678788.exe.scr | C:\Users\Public\Libraries\Null | text | |
MD5:7C80F4DEAE360F881A1422A4D0471445 | SHA256:D01BBC67418C3877264F7D25CCD6CB6BA2BB71F9E0280A8989CB62E06E77683B | |||
| 2820 | xcopy.exe | C:\Windows \System32\easinvoker.exe | executable | |
MD5:231CE1E1D7D98B44371FFFF407D68B59 | SHA256:30951DB8BFC21640645AA9144CFEAA294BB7C6980EF236D28552B6F4F3F92A96 | |||
| 1936 | xcopy.exe | C:\Windows \System32\netutils.dll | executable | |
MD5:B23C6ED8594D6B0DBD479CB297F668C7 | SHA256:56277178277C1920310C4BD97C523B0EC9D2D4BA09CCF836F4F30E689D79C63F | |||
| 2692 | NewOrder0578657875678788.exe.scr | C:\Users\Public\Anyoyvtq.url | text | |
MD5:79E673EACA89840F4DB66FD7F20D2439 | SHA256:92C93609373585A0722C7AF352A06C2C6819C23C9898C6D4FC69343325109ACD | |||
| 2692 | NewOrder0578657875678788.exe.scr | C:\Users\Public\Libraries\netutils.dll | executable | |
MD5:B23C6ED8594D6B0DBD479CB297F668C7 | SHA256:56277178277C1920310C4BD97C523B0EC9D2D4BA09CCF836F4F30E689D79C63F | |||
| 2928 | colorcpl.exe | C:\ProgramData\jjjjjjjjjjjjooooooo\logs.dat | binary | |
MD5:6345E965BD1A89A76C6B40BAF3A33E5D | SHA256:829353737A865BEC6AFF85A137EAF214FAD97E9758812B45DB15281B65108CA9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
7
DNS requests
4
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2928 | colorcpl.exe | GET | 200 | 178.237.33.50:80 | http://geoplugin.net/json.gp | NL | binary | 941 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
328 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2692 | NewOrder0578657875678788.exe.scr | 13.107.42.13:443 | onedrive.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | malicious |
2692 | NewOrder0578657875678788.exe.scr | 13.107.42.12:443 | 11wxlw.bn.files.1drv.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | suspicious |
2928 | colorcpl.exe | 104.223.35.34:2404 | moneymagnetjoe.duckdns.org | ASN-QUADRANET-GLOBAL | NL | malicious |
2928 | colorcpl.exe | 178.237.33.50:80 | geoplugin.net | Schuberg Philis B.V. | NL | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
onedrive.live.com |
| shared |
11wxlw.bn.files.1drv.com |
| suspicious |
moneymagnetjoe.duckdns.org |
| malicious |
geoplugin.net |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2692 | NewOrder0578657875678788.exe.scr | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Downloading from a file sharing service is observed |
328 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.duckdns .org Domain |
328 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to *.duckdns. Domain |
2928 | colorcpl.exe | Malware Command and Control Activity Detected | ET MALWARE Remcos 3.x Unencrypted Checkin |
2928 | colorcpl.exe | Malware Command and Control Activity Detected | ET MALWARE Remcos 3.x Unencrypted Server Response |
1 ETPRO signatures available at the full report