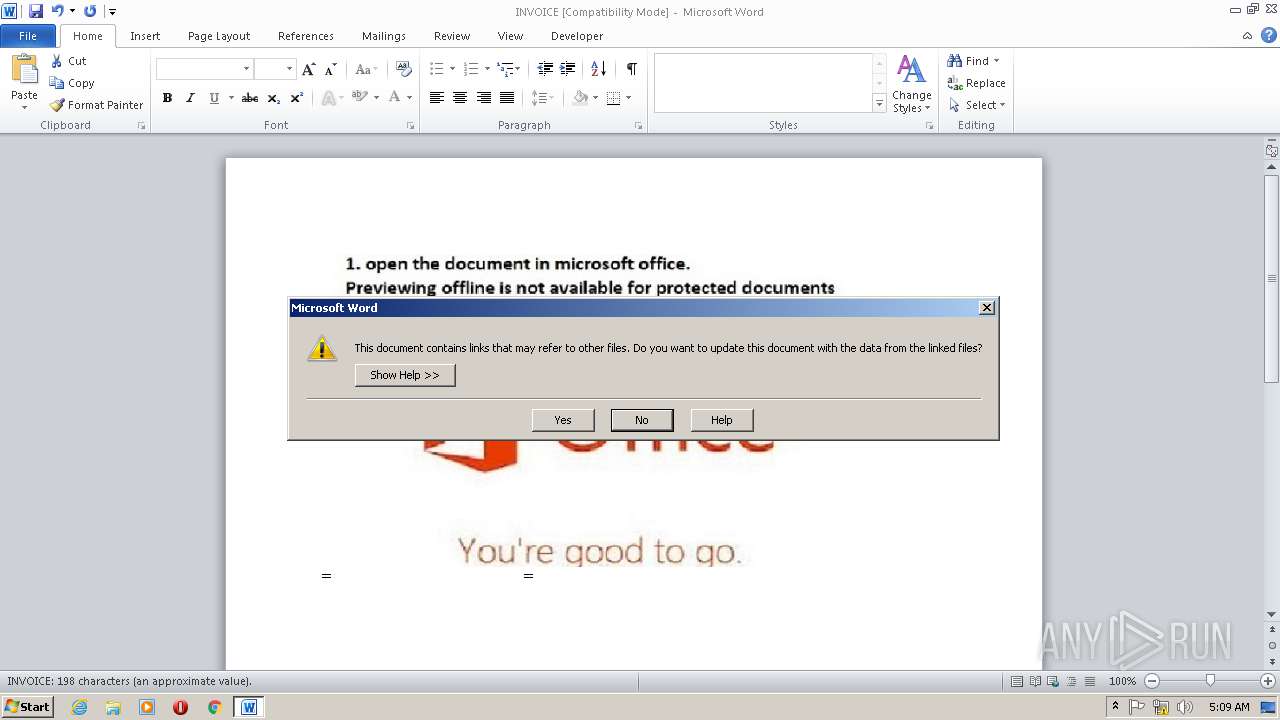
| File name: | INVOICE.doc |
| Full analysis: | https://app.any.run/tasks/216c78da-91a9-4743-b231-2b6f453ea714 |
| Verdict: | Malicious activity |
| Threats: | AZORult can steal banking information, including passwords and credit card details, as well as cryptocurrency. This constantly updated information stealer malware should not be taken lightly, as it continues to be an active threat. |
| Analysis date: | January 18, 2019, 05:09:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/rtf |
| File info: | Rich Text Format data, version 1, unknown character set |
| MD5: | 0D23E732B9C94A63054DE00FEDAFACB4 |
| SHA1: | 3A25FC868C01D3D75EF0FC27D642B785A9AD62E6 |
| SHA256: | 63C5CE3013980E8412918D25F41E1CA43D52EFE66E540B0E7AAC1C96569DBD2C |
| SSDEEP: | 12288:4h6jIdvQBYa0G2h5U3YOteYKixFKXtyBe6Q1OjIROdXPZ:wfdvUYaHoqTtBnFKXof3dB |
MALICIOUS
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 3060)
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 3060)
Runs app for hidden code execution
- cmd.exe (PID: 2980)
- cmd.exe (PID: 1248)
Application was dropped or rewritten from another process
- saver.scr (PID: 2968)
AZORULT was detected
- saver.scr (PID: 2968)
Connects to CnC server
- saver.scr (PID: 2968)
Actions looks like stealing of personal data
- saver.scr (PID: 2968)
Stealing of credential data
- saver.scr (PID: 2968)
Loads dropped or rewritten executable
- saver.scr (PID: 2968)
SUSPICIOUS
Starts CMD.EXE for commands execution
- cmd.exe (PID: 2980)
- cmd.exe (PID: 2656)
- cmd.exe (PID: 1248)
- cmd.exe (PID: 2948)
- saver.scr (PID: 2968)
Executes scripts
- cmd.exe (PID: 2948)
Reads the machine GUID from the registry
- cscript.exe (PID: 2320)
Executable content was dropped or overwritten
- cscript.exe (PID: 2320)
- saver.scr (PID: 2968)
Uses TASKKILL.EXE to kill Office Apps
- cmd.exe (PID: 2948)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 2948)
- cmd.exe (PID: 2724)
- cmd.exe (PID: 2512)
- cmd.exe (PID: 2944)
- cmd.exe (PID: 2444)
- cmd.exe (PID: 2584)
- cmd.exe (PID: 1472)
Application launched itself
- cmd.exe (PID: 2948)
Starts Microsoft Office Application
- cmd.exe (PID: 2948)
Starts application with an unusual extension
- cmd.exe (PID: 2948)
Reads the cookies of Google Chrome
- saver.scr (PID: 2968)
INFO
Reads the machine GUID from the registry
- WINWORD.EXE (PID: 3060)
- WINWORD.EXE (PID: 3056)
Creates files in the user directory
- WINWORD.EXE (PID: 3060)
- WINWORD.EXE (PID: 3056)
Dropped object may contain Bitcoin addresses
- cscript.exe (PID: 2320)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3060)
- WINWORD.EXE (PID: 3056)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rtf | | | Rich Text Format (100) |
|---|
Total processes
83
Monitored processes
42
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 472 | TASkKILL /F /IM winword.exe | C:\Windows\system32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1248 | "C:\Windows\System32\cmd.exe" /C CmD < "C:\Users\admin\AppData\Local\Temp\ufFm.cMD" | C:\Windows\System32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1472 | C:\Windows\system32\cmd.exe /c REG QUERY "HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\15.0\Word\File MRU" /v "Item 1" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2076 | TIMEOUT /T 1 | C:\Windows\system32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2080 | TIMEOUT /T 1 | C:\Windows\system32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2112 | TIMEOUT /T 1 | C:\Windows\system32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2140 | reg delete HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\12.0\Word\Resiliency /f | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2320 | cscript //nologo "C:\Users\admin\AppData\Local\Temp\_.vbs" | C:\Windows\system32\cscript.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2328 | reg delete HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\14.0\Word\Resiliency /f | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2328 | reg delete HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\15.0\Word\Resiliency /f | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
16 459
Read events
16 049
Write events
394
Delete events
16
Modification events
| (PID) Process: | (3060) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | /t' |
Value: 2F742700F40B0000010000000000000000000000 | |||
| (PID) Process: | (3060) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3060) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3060) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000100000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1311899690 | |||
| (PID) Process: | (3060) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000100000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1311899774 | |||
| (PID) Process: | (3060) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000100000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1311899775 | |||
| (PID) Process: | (3060) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: F40B000096C43C0BECAED40100000000 | |||
| (PID) Process: | (3060) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | cx' |
Value: 63782700F40B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3060) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | cx' |
Value: 63782700F40B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3060) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
49
Suspicious files
4
Text files
22
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3060 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRFC2F.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2948 | cmd.exe | C:\Users\admin\Desktop\INVOICE.doc\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 3060 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\a.ScT | xml | |
MD5:— | SHA256:— | |||
| 3060 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\uffm.cmd | text | |
MD5:— | SHA256:— | |||
| 3056 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR14A8.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3060 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\itnqknf5.cmd | text | |
MD5:— | SHA256:— | |||
| 3060 | WINWORD.EXE | C:\Users\admin\Desktop\~$NVOICE.doc | pgc | |
MD5:93A44B45219D2465E693C09A4B379AFD | SHA256:2F6A708419EDCADB0B2056B85E6FFDDC719CDC820640927C28026344B767CE91 | |||
| 3060 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:— | SHA256:— | |||
| 3060 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\INVOICE.LNK | lnk | |
MD5:— | SHA256:— | |||
| 3060 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{68183ADA-99B9-4013-8936-C070C36A56EE}.tmp | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
2
DNS requests
1
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2968 | saver.scr | POST | 200 | 200.63.40.2:80 | http://chuxagama.com/web-obtain/Panel/five/index.php | PA | binary | 4.27 Mb | malicious |
2968 | saver.scr | POST | 200 | 200.63.40.2:80 | http://chuxagama.com/web-obtain/Panel/five/index.php | PA | text | 2 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2968 | saver.scr | 200.63.40.2:80 | chuxagama.com | Panamaserver.com | PA | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
chuxagama.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2968 | saver.scr | A Network Trojan was detected | ET TROJAN AZORult Variant.4 Checkin M2 |
2968 | saver.scr | A Network Trojan was detected | MALWARE [PTsecurity] AZORult HTTP Header |
2968 | saver.scr | A Network Trojan was detected | MALWARE [PTsecurity] AZORult encrypted PE file |
2968 | saver.scr | A Network Trojan was detected | MALWARE [PTsecurity] AZORult HTTP Header |
2968 | saver.scr | A Network Trojan was detected | MALWARE [PTsecurity] AZORult client request |
2 ETPRO signatures available at the full report